Using Proven Reference Monitor Patterns for Security Evaluation
Abstract
:1. Introduction
The very first reference to design patterns in a security context was a presentation by Deborah Frincke at NISSC 1996. The presentation discussed the security ramifications of some of the original 23 Design Patterns. Her basic idea was that one could start with a security requirement on a pattern, and decompose it into constituent object requirements. In this way, if a proof were developed at the pattern level, it could be reused in tandem with the pattern. This was a powerful idea, but limited to patterns that were not originally intended to address security requirements. Unfortunately, this work was not continued, and was never published.—Darrell M. Kienzle, et al. [2]
2. Definitions and Context
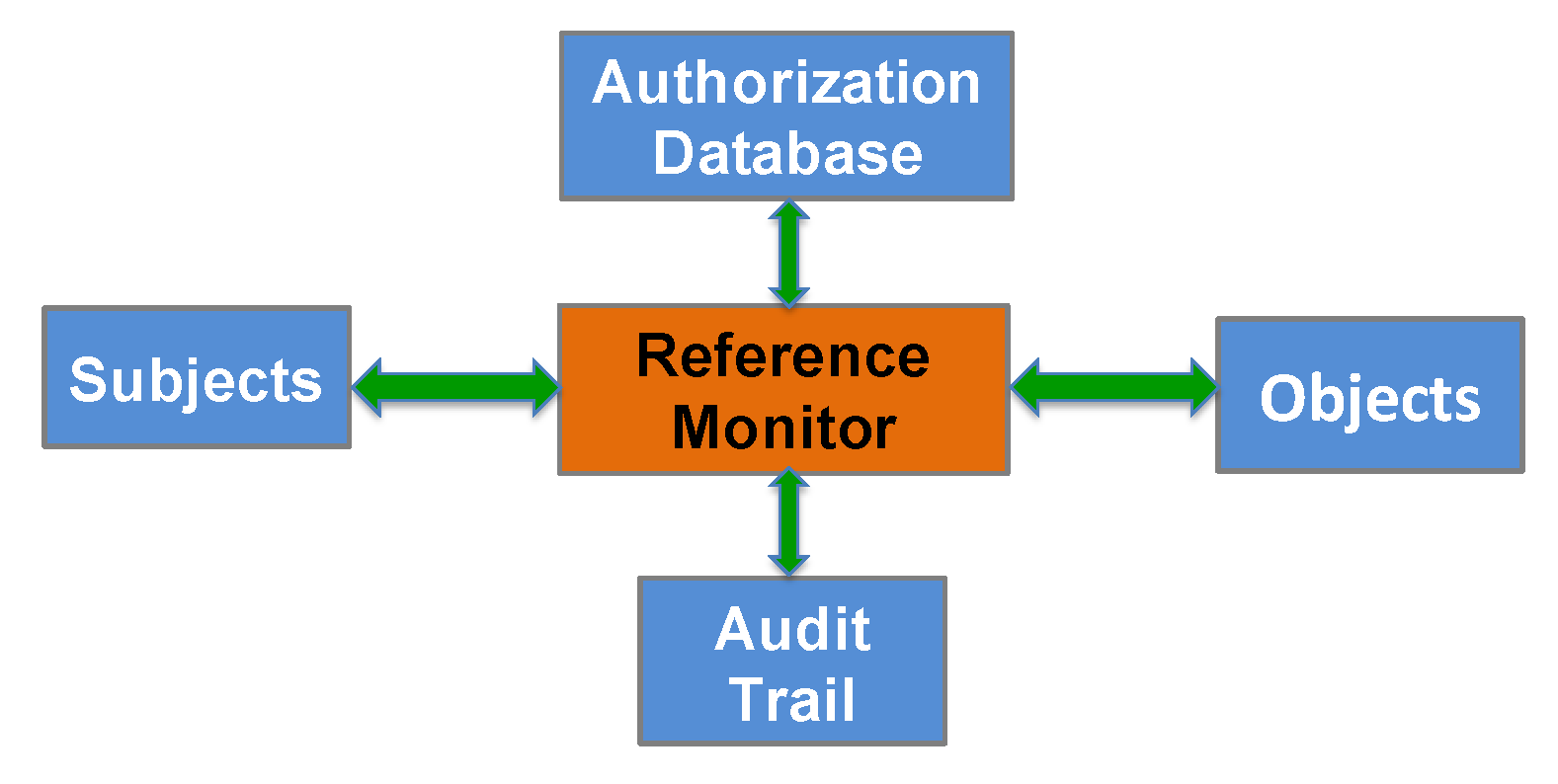
2.1. The Reference Monitor Subjects and Objects Foundation
2.2. A Secure System Must Mitigate Adversarial Attacks, Including Subversion
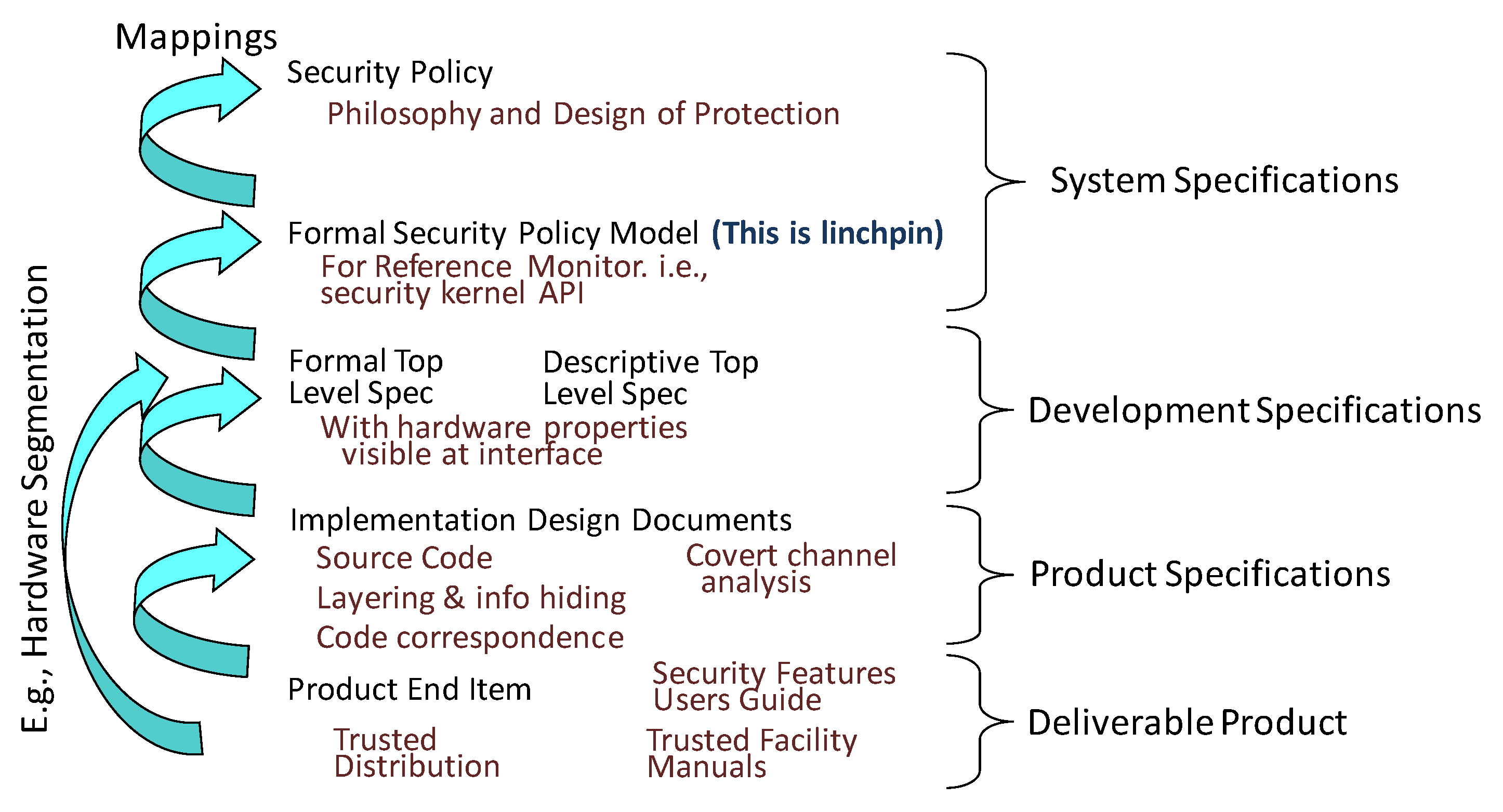
2.3. Encompassing Codification for Evaluation
- Formal Top-Level Specification (FTLS) [6] (Section 4.1.4.4). The FTLS precisely defines the security kernel API as the basis for a high degree of assurance that the implementation is correct.
- Show that FTLS is consistent with the model [6] (Section 4.1.3.2.2). This is evidence in the form of a mathematical proof that both the model and kernel interface are correct representations of the security policy.
- Formal covert channel analysis [6] (Section 4.1.3.1.3). Formal analysis techniques must be used to identify and analyze covert channels.
- Penetration testing based on the FTLS [6] (Section 4.1.3.2.1). Penetration is based on mapping of the FTLS to source code.
- Hardware and firmware included in FTLS [6] (Section 4.1.3.2.2). This provides a complete definition of the execution environment for applications running on the kernel.
- Code correspondence [6] (Section 4.1.3.2.1). Mapping of the FTLS to kernel source code to provide evidence of correct implementation and the absence of artifices from subversion.
- Strict configuration management [6] (Section 4.1.3.2.3). Strict configuration control to address subversion of tools and design documentation, as well as of source and object code.
- Trusted distribution [6] (Section 4.1.3.2.4). This addresses supply chain subversion by confirming that each customer’s kernel software, firmware and hardware are exactly what were evaluated.
The totality of protection mechanisms within a computer system—including hardware, firmware, and software—the combination of which is responsible for enforcing a security policy. A TCB consists of one or more components that together enforce a unified security policy over a product or system. The ability of a trusted computing base to correctly enforce a security policy depends solely on the mechanisms within the TCB and on the correct input by system administrative personnel of parameters (e.g., a user’s clearance) related to the security policy.—National Computer Security Center [6]
2.4. Well-Defined Security Software Engineering Process
Each layer of the design implements some abstraction in part by making calls on lower layers. In no case does a lower layer invoke or depend upon higher layer abstractions. By making lower layers unaware of higher abstractions, we reduced the total number of interactions in the system and thereby reduce the overall complexity. Furthermore, each layer can be tested in isolation from all higher layers, allowing debugging to proceed in an orderly fashion, rather than haphazardly throughout the system.—Paul A. Karger, et al. [15] (p. 1154)
2.5. MAC Policy Is Key to Security Architecture of Large Systems
2.6. Systematic Composition Is Key to Distributed Systems
Like a stand-alone system, the network as a whole possesses a single TCB, referred to as the NTCB, consisting of the totality of security-relevant portions of the network. But, unlike a stand-alone system, the design and evaluation of the network rests on an understanding of how the security mechanisms are distributed and allocated to various components, in such a way that the security policy is supported reliably in spite of (1) the vulnerability of the communication paths and (2) the concurrent, asynchronous operation of the network components.—National Computer Security Center [5] (Section I.4.2)
2.6.1. TCB Subsets
2.6.2. Partitioned TCB
In the context of a larger system, however, it may well be (and usually is) the case that the set of policy-related features to be supported by the component need not be the complete set required for a stand-alone system: features not supplied by one component for the system are supplied by another … In order to limit the number of component types we break the “maximal” set of policy-related features, defined by the TCSEC for A1 systems, into four relatively independent categories which can be characterized as supporting Mandatory Access Controls (MAC), Discretionary Access Controls (DAC), Audit, and Identification and Authentication … these categories will be given the one-letter designations M, D, A, and I, respectively.—National Computer Security Center [5] (Section A.1.1)
It turns out that, for a multilevel security policy, the only trusted control information that needs to be exchanged is the access class of the network objects; the transmitting kernel inserts an access class label on a message based on the access class of the subject that created the message, and the receiving kernel uses that access class to determine who on its own system may read the message. If the trusted network service operates at the transport layer, a label is required only when the virtual circuit is established, and not on each message that is exchanged over that circuit. The kernels must still trust each other to insert and obey the access class labels according to their common policy, but no information other than the labels need be managed or exchanged between the kernels.—Morrie Gasser [19] (Section 13.5)
3. Results
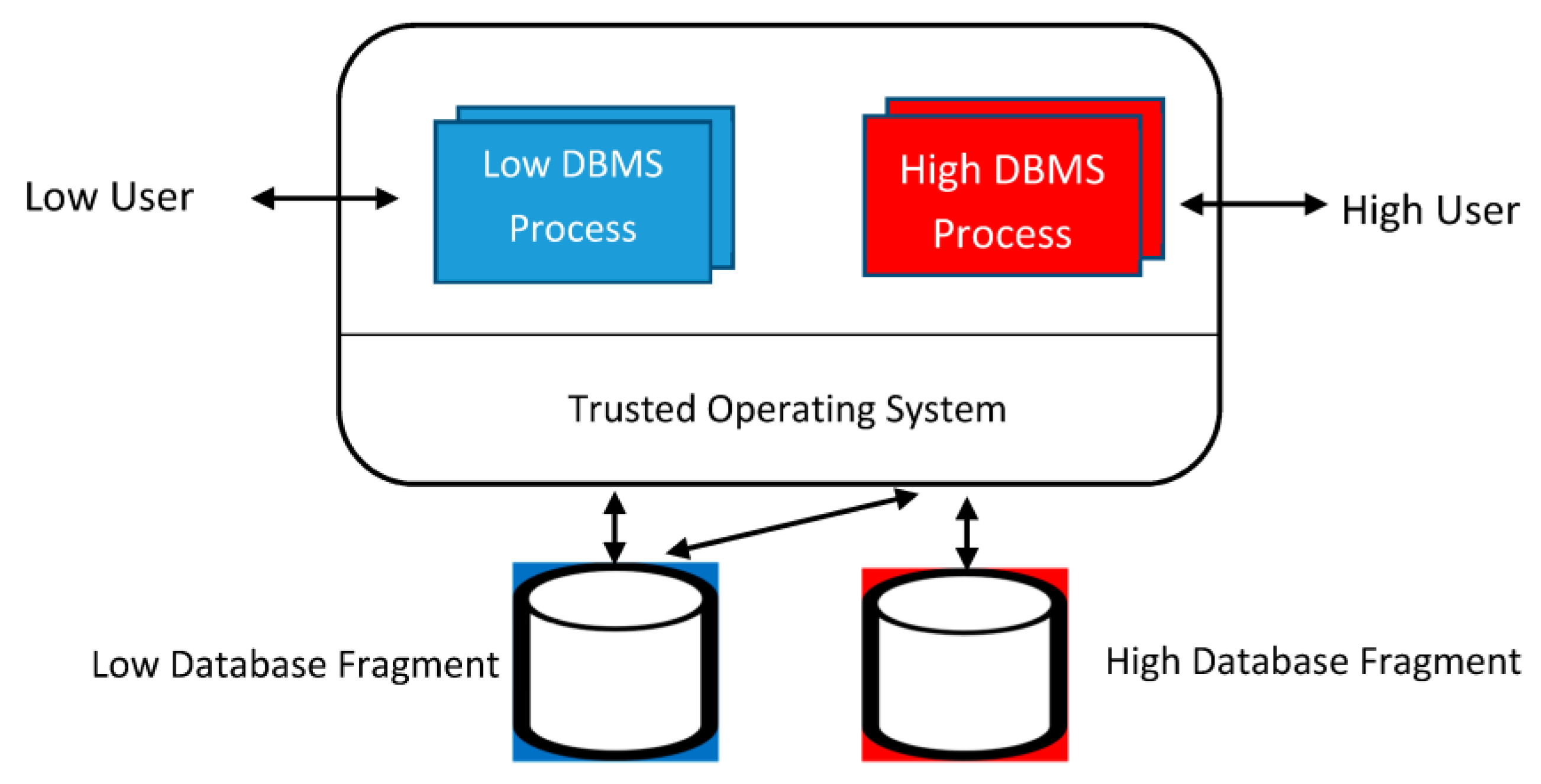
3.1. Commercial Secure Oracle DBMS System
In building multilevel database systems, providing such assurance is especially challenging because large, complex mechanisms may be involved in policy enforcement. Achieving Class A1 assurance for a multilevel database system is possible only if the portion of the system enforcing mandatory security is small and isolated and does not depend on the large database machinery for its correct enforcement.—Linda Vetter, et al. [20]
We describe our approach to multilevel database security and show that we can support element-level labeling in a Class A1 database system without the need to verify the entire database system, or even most of it. We achieve both the high degree of assurance required for Class A1 and the flexibility of element-level labeling by layering the TCB, where the lowest TCB layer is a Reference Monitor enforcing mandatory security; and by decomposing multilevel relations into single-level relations that are managed by the Reference Monitor.—Teresa F. Lunt, et al. [22]
3.2. Honeywell Multics Commercial Mainframe
DOCKMASTER is a (Multics-based) subscription service of the National Computer Security Center (NCSC), that they consider an “Information Security Showcase.” Its large repertoire of available services (its user’s manual is over one hundred pages) includes E-mail, electronic bulletin boards, and allows hands-on software evaluation. Its Evaluated Products List rates computers and computer security products. Users can access online documents (such as the Orange Book), participate in online discussions, and learn about computer security conferences. Users can connect to DOCKMASTER through MILNET (part of the Internet), TYMNET (a packet switching service), and local dial-in.—Multicians.org [27]
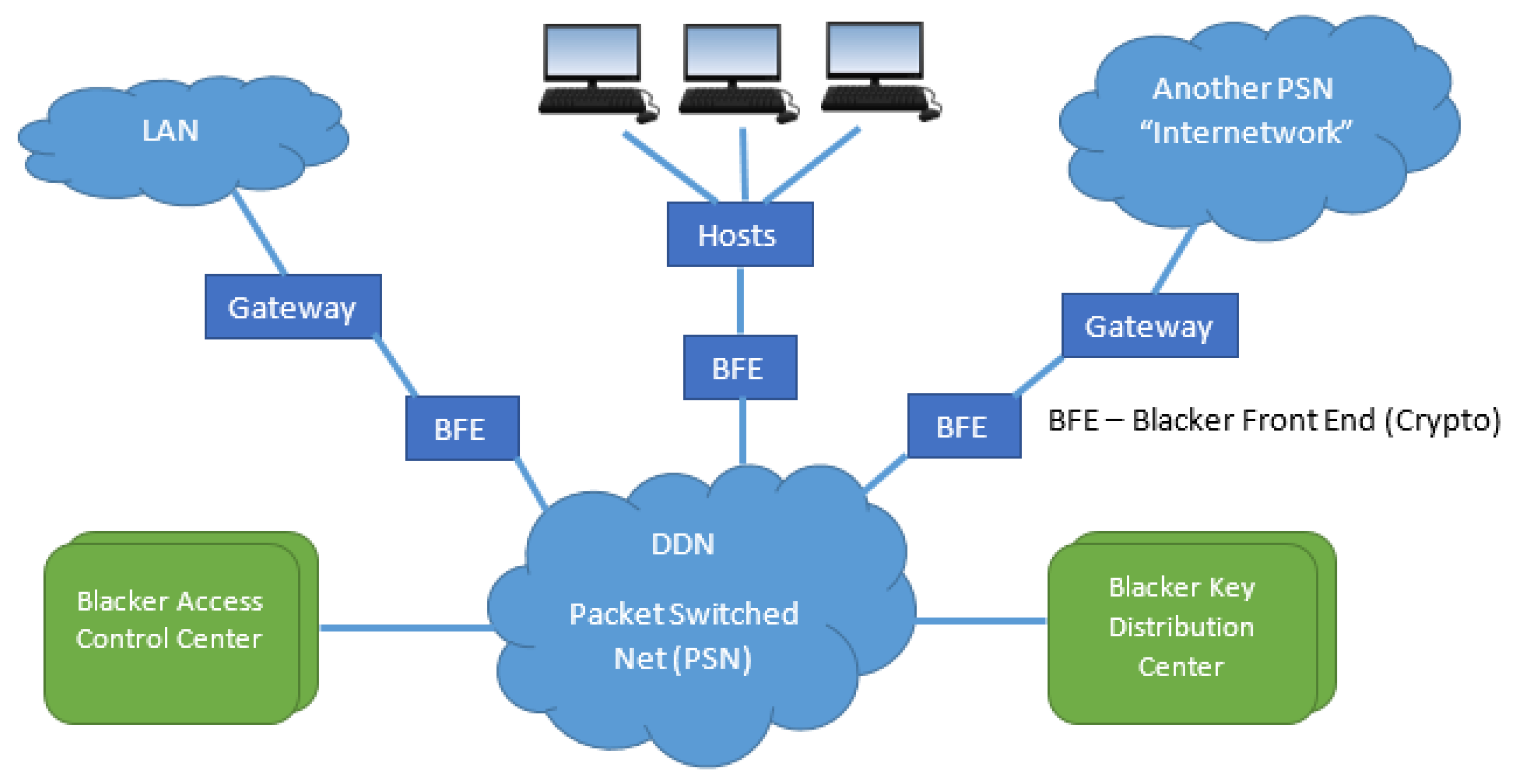
3.3. Government BLACKER Secure Network Infrastructure
Assurance is concerned with guaranteeing or providing confidence that features to address Data Confidentiality threats have been implemented correctly and that the control objectives of each feature have been actually and accurately achieved. Blacker is an example of such an application of a TCB for high assurance of data confidentiality.—National Computer Security Center [5] (p.190)
One of the first applications of the GEMSOS security kernel was for an MLS wide-area network called BLACKER, which was successfully evaluated against the Class Al under the Trusted Computer System Evaluation Criteria (TCSEC). In the BLACKER system, the GEMSOS security kernel along with other trusted components, is used as the basis for trust for critical cryptographic and key distribution functions that maintain communications separation by cryptographic means.—National Computer Security Center [31] (p. 5)
3.4. Government Pentagon Enterprise Management Information System
This paper discusses the development of a large-scale Management Information System (MIS) at the A1 certification level, as discussed in the Trusted Network Interpretation (TNI) of the Trusted Computer System Evaluation Criteria known as the TNI. The system design uses three commercial off-the-shelf (COTS) products as a basis for a distributed Trusted Computing Base (TCB) using a component architecture as discussed in the TNI. Several extensions to these COTS products that are necessary to enable the system to meet specific requirements are discussed.—Daniel Gambel, et al. [32]
The SCPE consists of two separate types of components configured on two different Gemini models. The first is the Access Control Module (ACM), which provides most of the I/A functions for the system and the I/A associated mandatory supporting policies. The ACM validates the user’s logonid and password, determines the user’s acceptable Mandatory Access Control (MAC) session domain/range from the user’s clearance and the terminal classification range…
The second type of SCPE component is the Communications Control Module (CCM). The CCM’s major role is to enforce the MAC policy. The CCMs are also responsible for communication and communication management services between the HSRP user community and the hosts.—Daniel Gambel, et al. [32]
The use of a COTS TCB has several positive aspects. The foremost of these is simply that in building the system, we do not have to start from scratch but can build upon the foundation provided by the A1 TCB. The advantages of this are far reaching in cost and time…
Another advantage of using a COTS TCB concerns the Assurance Evidence. Assurance Evidence consists of the documentation required … for A1 certification. This includes the Formal Top Level Specification (FTLS), the Descriptive Top Level Specification (DTLS), the Trusted Distribution Plan (TDP), the Covert Channel Analysis (CCA), the Policy Model (PM), and the Code Correspondence (CC) as well as user’s guide and testing documentation. In the A1 development process, the development of this documentation is more time consuming than the development of the software. By using a COTS TCB, we can take advantage of the vendor-developed Assurance Evidence.—Daniel Gambel, et al. [32]
3.5. Research Prototypes Hosted on the GEMSOS™ Security Kernel
3.5.1. Source-Code Compatible Secure Linux
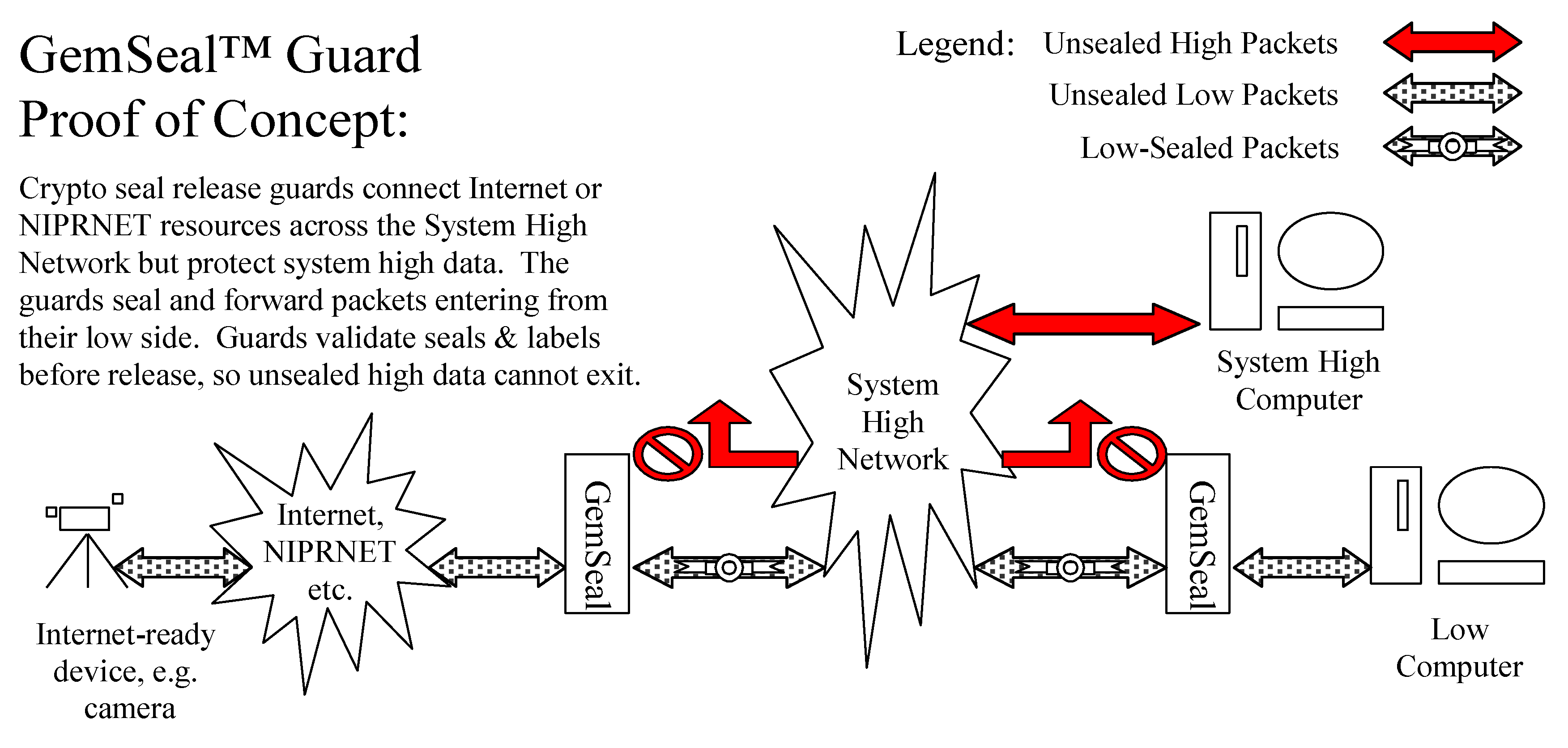
3.5.2. GemSeal™ Guard Secure Network Interface Proof of Concept
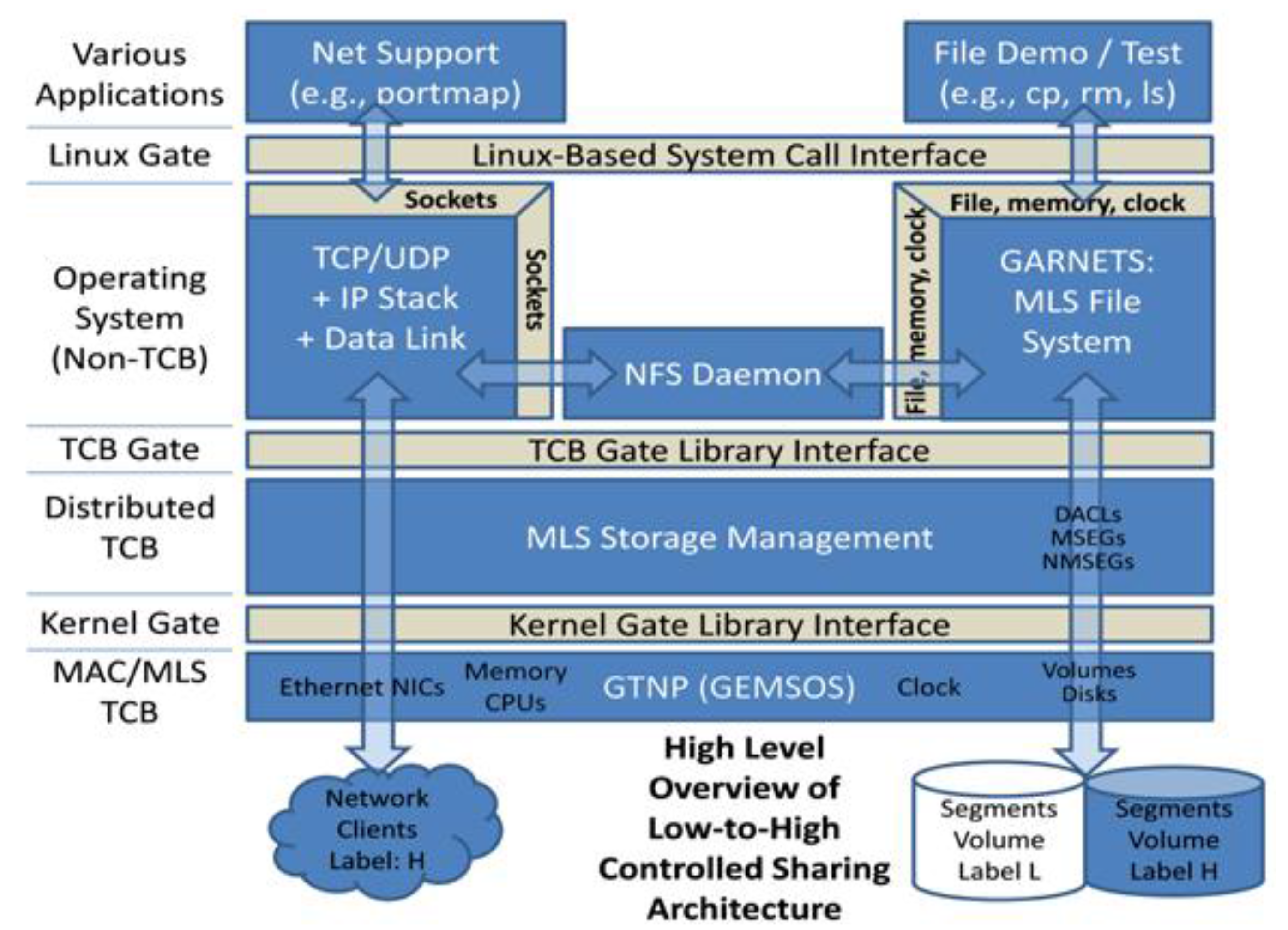
3.5.3. Secure File Service for Cloud Prototype
4. Discussion
4.1. Recap of Key Elements of Reference Monitor-Based Security Patterns
4.1.1. Trusted Computing Base
4.1.2. Subjects
Hierarchically-Ordered Protection Domains: Protection Rings
Security Kernel
4.1.3. Objects: Segments
4.1.4. Policy Taxonomy: “MAID” Map to Reference Monitor
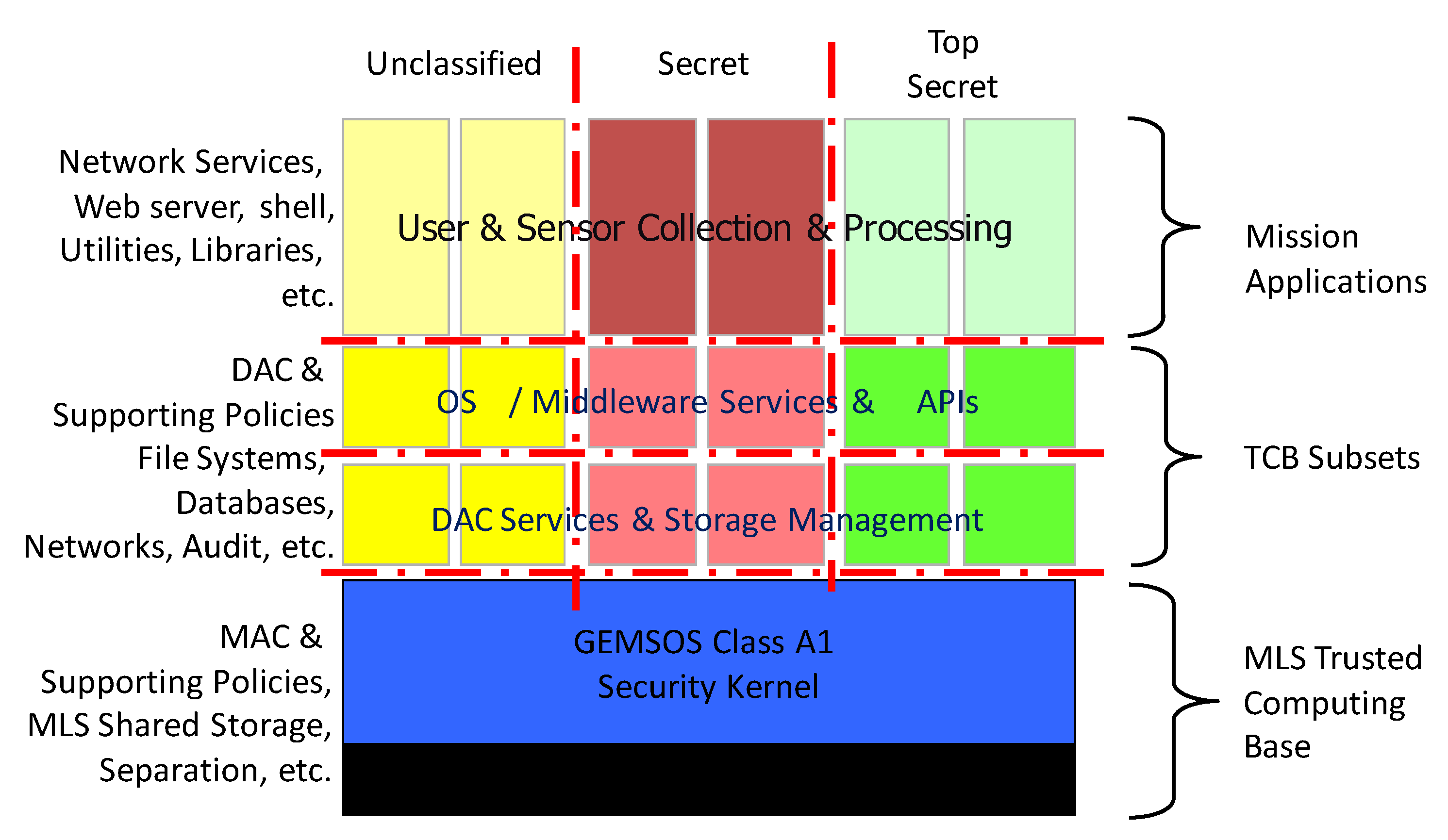
4.1.5. Composition of TCB Subsets
4.1.6. Composition of TCB Partitions
Policy Allocation to Network Components: 16 Combinations
Incremental Evaluation
Secure Interconnecting Channels
4.1.7. Balanced Assurance
4.1.8. Security Software Engineering
4.2. Delivery Architecture
5. Conclusions
While customers may want improved security, they usually have second thoughts when security features adversely affect other, “more important” features. Since few customers are willing to pay extra for security, vendors have had little incentive to invest in extensive security enhancements … demand is fairly weak and can easily evaporate if the features should have an adverse impact on cost or any other functions.—Morrie Gasser [19]
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| DBMS: | Database Management System |
| MAC: | Mandatory Access Control |
| MLS: | Multilevel Security |
| OEM: | Original Equipment Manufacturer |
| OS: | Operating System |
| TCB: | Trusted Computing Base |
| TCSEC: | Trusted Computer System Evaluation Criteria |
| TNI: | Trusted Network Interpretation (of the TCSEC) |
References
- Ito, Y.; Washizaki, H.; Yoshizawa, M.; Fukazawa, Y.; Okubo, T.; Kaiya, H.; Hazeyama, A.; Yoshioka, N.; Fernandez, E.B. Systematic Mapping of Security Patterns Research. In Proceedings of the 22nd Conference on Pattern Languages of Programs Conference 2015 (PLoP 2015), Pittsburgh, PA, USA, 24–26 October 2015.
- Kienzle, D.M.; Elder, D.T.; Edwards-Hewitt, J. Security Patterns Template and Tutorial. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.131.2464&rep=rep1&type=pdf (accessed on 21 January 2016).
- Anderson, J.P. Computer Security Technology Planning Study; USAF Electronics Systems Division: Bedford, MA, USA, 1972. [Google Scholar]
- Schumacher, M.; Fernandez, E.; Hybertson, D.; Buschmann, F. Security Patterns: Integrating Security and Systems Engineering; John Wiley & Sons: Hoboken, NJ, USA, 2005; pp. 253–258. [Google Scholar]
- NCSC-TG 005: Trusted Network Interpretation. National Computer Security Center: Fort Meade, FL, USA, 1987; Available online: http://ftp.mirrorservice.org/sites/ftp.wiretapped.net/pub/security/info/reference/ncsc-publications/rainbow-books/NCSC-TG-005.pdf (accessed on 27 January 2016).
- Department of Defense Trusted Computer System Evaluation Criteria (DoD 5200.28-STD). United States National Computer Security Center: Fort Meade, FL, USA, 1985; Available online: http://ftp.mirrorservice.org/sites/ftp.wiretapped.net/pub/security/info/reference/ncsc-publications/rainbow-books/5200.28-STD.pdf (accessed on 27 January 2016).
- USAF Electronics System Division. Multilevel Security Issues and Answers: An Evaluation of the AFSC Program (MCI-75-8); Hanscom AFB: Bedford, MA, USA, 1975; Unpublished work. [Google Scholar]
- Schell, R.R. A University Education Cyber Security Paradigm Shift. In Presented at the National Initiative for Cybersecurity Education (NICE), San Diego, CA, USA, 3–4 November 2015; Available online: https://www.fbcinc.com/e/nice/ncec/presentations/Schell.pdf (accessed on 29 January 2016).
- Anderson, E.A.; Irvine, C.E.; Schell, R.R. Subversion as a Threat in Information Warfare. J. Inf. Warf. 2004, 3, 51–64. [Google Scholar]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Dijkstra, E.W. Notes on Structured Programming; Technical Report 70-WSK-03; Technische Hogeschool Enidhoven: Enidhoven, The Netherlands, 1970. [Google Scholar]
- Bell, D.E.; LaPadula, L.J. Computer Security Model: Unified Exposition and Multics Interpretation (ESD-TR-75-306); Hanscom AFB: Bedford, MA, USA, 1975. [Google Scholar]
- Schell, R.R.; Brinkley, D.L. Evaluation Criteria for Trusted Systems. In Information Security: An Integrated Collection of Essays; Abrams, M.D., Jajodia, S., Podell, H.J., Eds.; IEEE Computer Society Press: Los Alamitos, CA, USA, 1995; pp. 137–159. [Google Scholar]
- Common Criteria for Information Technology Security Evaluation, version 3.1 revision 4, 2012. Available online: https://www.commoncriteriaportal.org/files/ccfiles/CCPART1V3.1R4.pdf (accessed on 29 January 2016).
- Karger, P.A.; Zurko, M.E.; Bonin, D.W.; Mason, A.H.; Kahn, C.E. A retrospective on the VAX VMM security kernel. IEEE Trans. Softw. Eng. 1991, 17, 1147–1165. [Google Scholar] [CrossRef]
- Brinkley, D.L.; Schell, R.R. Concepts and Terminology for Computer Security. In Information Security: An Integrated Collection of Essays; IEEE Computer Society Press: Los Alamitos, CA, USA, 1995; pp. 40–97. Available online: http://www.acsa-admin.org/secshelf/book001/02.pdf (accessed on 21 January 2016).
- Bell, D.E. Looking Back at the Bell-La Padula Model. In Proceedings of the 21st Annual Computer Security Applications Conference (ACSAC’05), Tucson, AZ, USA, 5–9 December 2005; pp. 337–351.
- Shockley, W.R.; Schell, R.R. TCB subsets for incremental evaluation. In Proceedings of the Third Aerospace Computer Security Conference, Orlando, FL, USA, 7–11 December 1987; pp. 131–139.
- Gasser, M. Building a Secure Computer System; Van Nostrand Reinhold Company: New York, NY, USA, 1988. [Google Scholar]
- Vetter, L.; Smith, G.; Lunt, T.F. TCB subsets: The next step. In Proceedings of the Fifth Annual Computer Security Applications Conference, Tucson, AZ, USA, 4–8 December 1989; pp. 216–221.
- Schell, R.; Tao, T.F.; Heckman, M. Designing the GEMSOS security kernel for security and performance. In Proceedings of the 8th National Computer Security Conference, Gaithersburg, MD, USA, 30 September–3 October 1985; Volume 30, pp. 108–119. Available online: http://www.mrheckman.com/yahoo_site_admin/assets/docs/DesigningTheGemsosSecurityKernel-OCR-120409-DRAFT.158131458.pdf (accessed on 29 January 2016).
- Lunt, T.F.; Denning, D.E.; Schell, R.R.; Heckman, M.; Shockley, W.R. Element-level classification with A1 assurance. Comput. Secur. 1988, 7, 73–82. [Google Scholar] [CrossRef]
- National Security Agency, Evaluated Products List, Trusted Oracle7, Class B1, United States National Computer Security Center, 5 April 1994. Available online: http://webapp1.dlib.indiana.edu/virtual_disk_library/index.cgi/1347159/FID1806/epl/entries/csc-epl-94-004.html (accessed on 27 January 2016).
- Final Evaluation Report, Honeywell Information Systems, Multics MR11.0, National Computer Security Center, CSC-EPL-85/003, 1 June 1986. Available online: http://www.multicians.org/multics-fer.pdf (accessed on 29 January 2016).
- Lipner, S.B. Security assurance. Commun. ACM 2015, 58, 24–26. [Google Scholar] [CrossRef]
- Site History: AFDSC. Available online: http://www.multicians.org/site-afdsc.html (accessed on 29 January 2016).
- Site History: DOCKMASTER. Available online: http://www.multicians.org/site-dockmaster.html (accessed on 29 January 2016).
- Karger, P.A.; Schell, R.R. Thirty years later: Lessons from the Multics security evaluation. In Proceedings of the 18th Annual Computer Security Applications Conference, Las Vegas, NV, USA, 9–13 December 2002.
- Schiller, W.L. Design and Abstract Specification of a Multics Security Kernel; MITRE Corp.: Bedford, MA, USA, 1977; Volume 1. [Google Scholar]
- Weissman, C. BLACKER: Security for the DDN examples of A1 security engineering trades. In Proceedings of the 1992 IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 4–6 May 1992; pp. 286–292.
- Final Evaluation Report, Gemini Computers, Incorporated, Gemini Trusted Network Processor, Version 1.01, National Computer Security Center, NCSC-FER-94/008, 28 June 1995. Available online: http://webapp1.dlib.indiana.edu/virtual_disk_library/index.cgi/1347159/FID1806/library/fers/ncsc-fer-94-008.pdf (accessed on 29 January 2016).
- Gambel, D.; Walter, S.; Fordham, M. HSRP—A1’ing a large-scale management information system. In Proceedings of the 7th Computers in Aerospace Conference, Monterey, CA, USA, 3–5 October 1989; American Institute of Aeronautics and Astronautics, Inc.: Reston, VA, USA, 1989; pp. 920–923. [Google Scholar]
- National Security Agency, Evaluated Products List, GTNP Version 1.01, Class A1, United States National Computer Security Center, 6 September 1994. Available online: http://webapp1.dlib.indiana.edu/virtual_disk_library/index.cgi/1347159/FID1806/EPL/ENTRIES/CSC-EPL-94-008.HTML (accessed on 27 January 2016).
- Irvine, C.E. A multilevel file system for high assurance. In Proceedings of the 1995 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 8–10 May 1995; pp. 78–87.
- Heckman, M.R.; Schell, R.R.; Reed, E.E. A high-assurance, virtual guard architecture. In Proceedings of the 2012 IEEE Military Communications Conference, MILCOM 2012, Orlando, FL, USA, 29 October–1 November 2012; pp. 1–9.
- Heckman, M.R.; Schell, R.R.; Reed, E.E. A multi-level secure file sharing server and its application to a multi-level secure cloud. In Proceedings of the 2015 IEEE Military Communications Conference, MILCOM 2015, Tampa, FL, USA, 26–28 October 2015; pp. 1224–1229.
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Heckman, M.R.; Schell, R.R. Using Proven Reference Monitor Patterns for Security Evaluation. Information 2016, 7, 23. https://doi.org/10.3390/info7020023
Heckman MR, Schell RR. Using Proven Reference Monitor Patterns for Security Evaluation. Information. 2016; 7(2):23. https://doi.org/10.3390/info7020023
Chicago/Turabian StyleHeckman, Mark R., and Roger R. Schell. 2016. "Using Proven Reference Monitor Patterns for Security Evaluation" Information 7, no. 2: 23. https://doi.org/10.3390/info7020023





