Fast and Secure Implementation of Modular Exponentiation for Mitigating Fine-Grained Cache Attacks
Abstract
:1. Introduction
2. Background
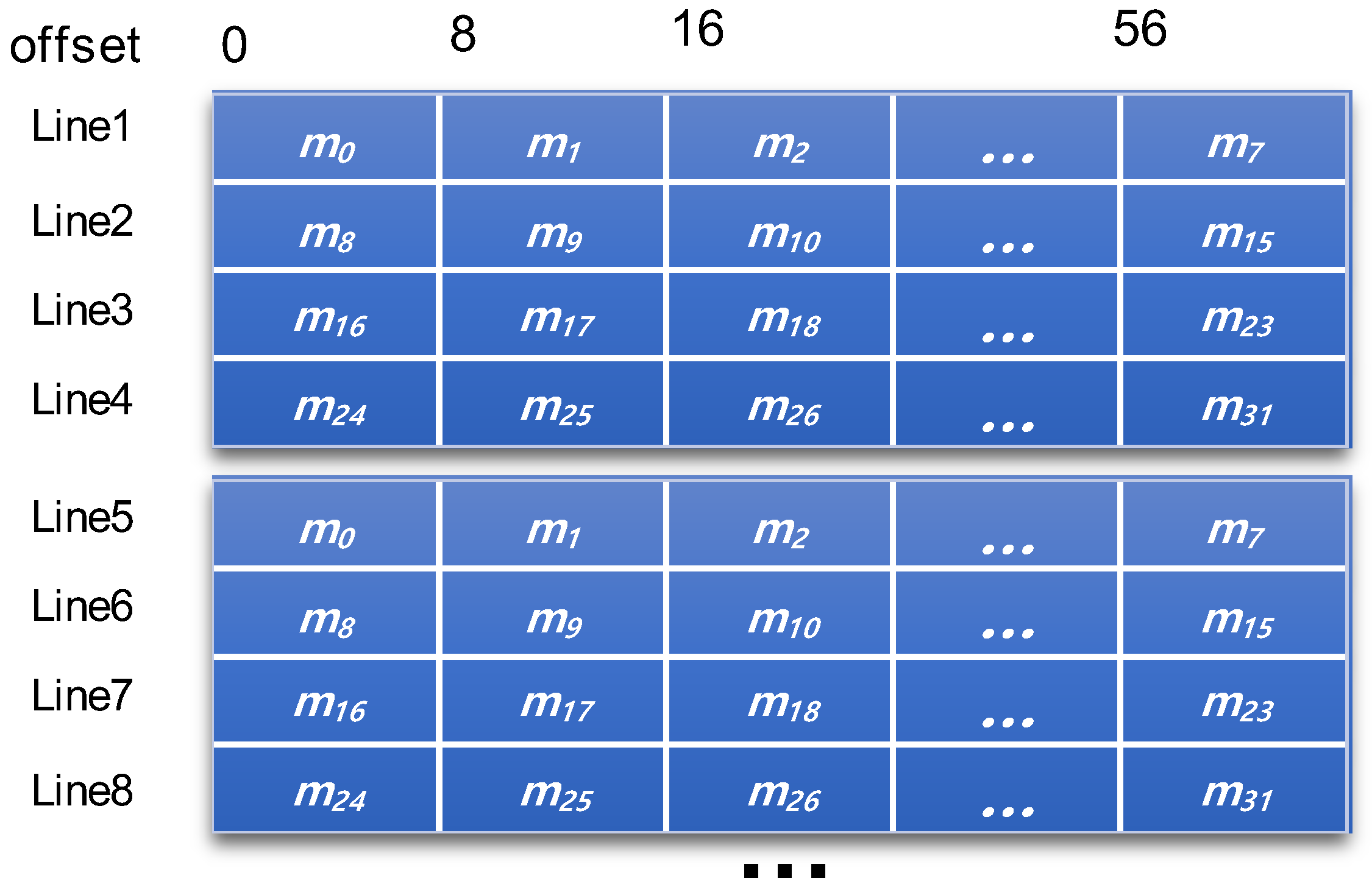
2.1. Scatter-Gather Implementation
| Algorithm 1 Fixed-window exponentiation |
| Require:k-bit exponent , window size w, base b, modulus n |
| Ensure: mod n |
| 1: procedure Exponentiation() |
| 2: // Pre-computation phase |
| 3: |
| 4: for to do |
| 5: mod n |
| 6: end for |
| 7: |
| 8: // Exponentiation phase |
| 9: |
| 10: for to 0 do |
| 11: for to w do |
| 12: mod n |
| 13: end for |
| 14: mod n |
| 15: end for |
| 16: return r |
| 17: end procedure |
2.2. Fine-Grained Cache Attack and Its Countermeasure
2.2.1. Fine-Grained Cache Attack
2.2.2. Constant-Time Gather Procedure
3. Permute-Scatter-Gather Implementation
3.1. Threat Model
3.2. Overview and Design Goals
- Resistance against fine-grained cache attacks. No information about the actually accessed multiplier should be revealed to adversaries who can observe memory accesses with bank-level granularity.
- Computational efficiency. Performance degradation in modular exponentiation due to applying this method should be minimized.
- Adaptability. It should be easily integrated into the existing implementation (e.g., OpenSSL library) without significant modification of source codes.
3.3. Implementation
- Permute step: In this step, a permutation P is randomly generated from , the set of all permutations. The generation process is conducted along with the precomputation phase of modular exponentiation algorithm (Algorithm 1).
- Scatter step: This step is the same as the scatter procedure in the OpenSSL, except that the scattering location of a multiplier with an index idx is determined by P(idx).
- Gather step: This step is the same as the gather procedure in the OpenSSL, except that the gathering location of a multiplier with an index idx is determined by P(idx).
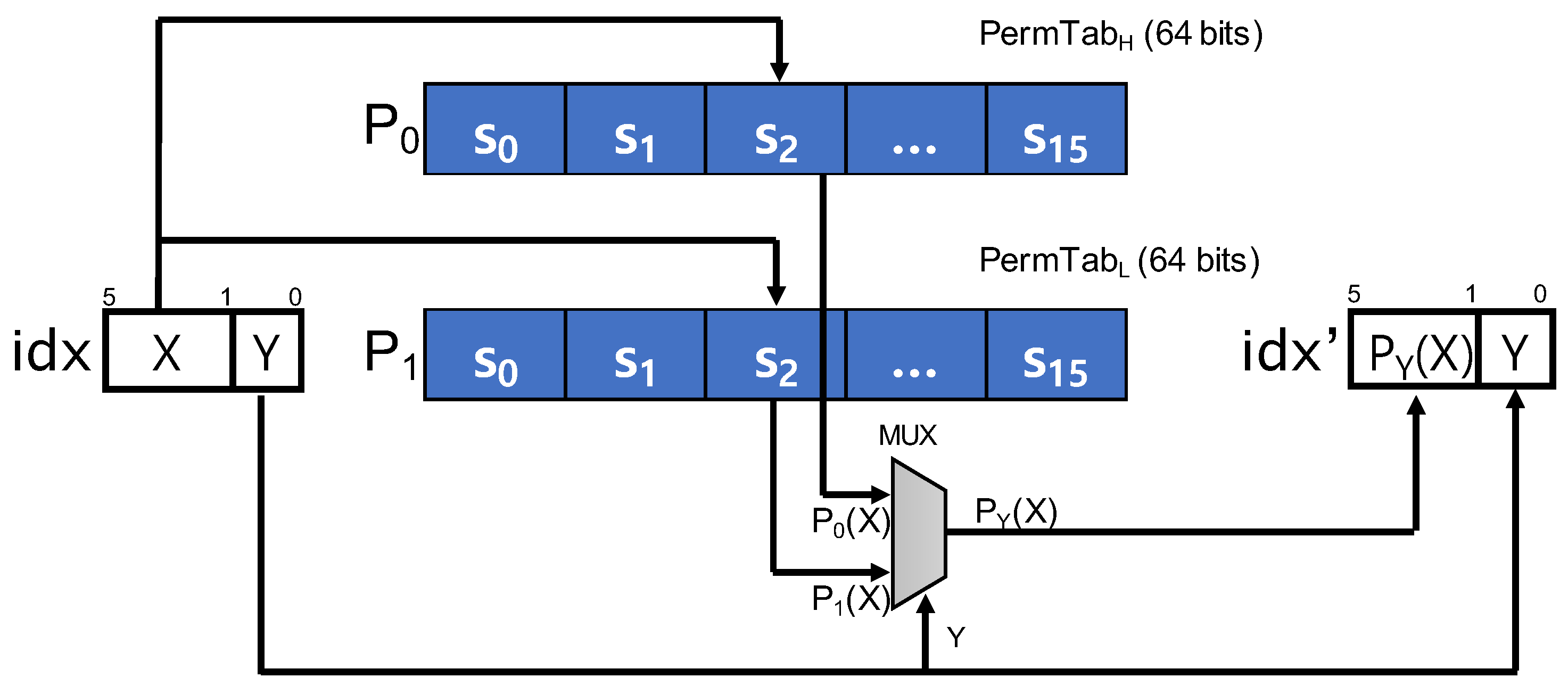
3.3.1. Challenging Issue
3.3.2. Constant-Time Permutation
4. Evaluation
4.1. Resistance Against Fine-Grained Cache Attacks
4.2. Adaptability
4.3. Computational Efficiency
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Liu, F.; Yarom, Y.; Ge, Q.; Heiser, G.; Lee, R.B. Last-level cache side-channel attacks are practical. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–20 May 2015; pp. 605–622. [Google Scholar]
- Irazoqui, G.; Eisenbarth, T.; Sunar, B. S$A: A shared cache attack that works across cores and defies VM sandboxing—And its application to AES. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 591–604. [Google Scholar]
- Gulmezoglu, B.; Irazoqui, G.; Eisenbarth, T.; Sunar, B. Cache Attacks Enable Bulk Key Recovery on the Cloud. In Proceedings of the International Conference on Cryptographic Hardware and Embedded Systems (CHES 2016), Santa Barbara, CA, USA, 17–19 August 2016; pp. 368–388. [Google Scholar]
- Disselkoen, C.; Kohlbrenner, D.; Porter, L.; Tullsen, D. PRIME+ABORT: A Timer-Free High-Precision L3 Cache Attack using Intel TSX. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 51–67. [Google Scholar]
- Yarom, Y.; Falkner, K. Flush + Reload: A High Resolution, Low Noise, L3 Cache Side-Channel Attack. In Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 719–732. [Google Scholar]
- Yarom, Y.; Benger, N. Recovering OpenSSL ECDSA Nonces Using the Flush + Reload Cache Side-Channel Attack; IACR Cryptol. ePrint Archive, Report 2014/140; International Association for Cryptologic Research: Santa Barbara, CA, USA, 2014. [Google Scholar]
- Berk, G.; Inci, M.S.; Irazoqui, G.; Eisenbarth, T.; Sunar, B. A Faster and More Realistic Flush + Reload Attack on AES. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design (COSADE 2015), Graz, Austria, 14–15 April 2015; pp. 111–126. [Google Scholar]
- Gruss, D.; Spreitzer, R.; Mangard, S. Cache Template Attacks: Automating Attacks on Inclusive Last-Level Caches. In Proceedings of the 24th USENIX Security Symposium, Washington, DC, USA, 12–14 August 2015; pp. 897–912. [Google Scholar]
- Gruss, D.; Maurice, C.; Wagner, K.; Mangard, S. Flush+Flush: A Fast and Stealthy Cache Attack. In Proceedings of the 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA 2006), Berlin, Germany, 13–14 July 2016; pp. 279–299. [Google Scholar]
- Zhang, Y.; Juels, A.; Reiter, M.K.; Ristenpart, T. Cross-Tenant Side-Channel Attacks in PaaS Clouds. In Proceedings of the 2014 SIGSAC ACM Conference on Computer and Communications Security (CCS 2014), Scottsdale, AR, USA, 3–7 November 2014; pp. 990–1003. [Google Scholar]
- Ge, Q.; Yarom, Y.; Cock, D.; Heiser, G. A Survey of Microarchitectural Timing Attacks and Countermeasures on Contemporary Hardware. J. Cryptogr. Eng. 2018, 8, 1–27. [Google Scholar] [CrossRef]
- Garman, C.; Green, M.; Kaptchuk, G.; Miers, I.; Rushanan, M. Dancing on the Lip of the Volcano: Chosen Ciphertext Attacks on Apple iMessage. In Proceedings of the 25th USENIX Security Symposium is sponsored by USENIX, Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- García, C.P.; Brumley, B.B. Constant-Time Callees with Variable-Time Callers. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 83–98. [Google Scholar]
- Genkin, D.; Valenta, L.; Yarom, Y. May the Fourth Be With You: A Microarchitectural Side Channel Attack on Several Real-World Applications of Curve25519. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security (CCS 2017), Dallas, TX, USA, 30 October–3 November 2017; pp. 845–858. [Google Scholar]
- Kaufmann, T.; Pelletier, H.; Vaudenay, S.; Villegas, K. When constant-time source yields variable-time binary: Exploiting curve25519-donna built with MSVC 2015. In Proceedings of the 15th International Conference on Cryptology and Network Security (CANS 2016), Milan, Italy, 14–16 November 2016; pp. 573–582. [Google Scholar]
- Gopal, V.; Guilford, J.; Ozturk, E.; Feghali, W.; Wolrich, G.; Dixon, M. Fast and Constant-Time Implementation of Modular Exponentiation. In Proceedings of the Embedded Systems and Communications Security, Niagara Falls, NY, USA, 27 September 2009. [Google Scholar]
- Ronald, L.; Rivest, A.S.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [Green Version]
- OpenSSL. OpenSSL, Cryptography and SSL/TLS Toolkit. Available online: https://www.openssl.org/ (accessed on 5 August 2018).
- Brickell, E. Technologies to improve platform security. In Proceedings of the Workshop on Cryptographic Hardware and Embedded Systems, Nara, Japan, 28 September–1 October 2011. [Google Scholar]
- Brickell, E. The impact of cryptography on platform security. In Proceedings of the CT-RSA 2012, San Francisco, CA, USA, 27 February–2 March 2012. [Google Scholar]
- Yarom, Y.; Genkin, D.; Heninger, N. CacheBleed: A Timing Attack on OpenSSL Constant Time RSA. J. Cryptogr. Eng. 2017, 7, 99–112. [Google Scholar] [CrossRef]
- Bos, J.; Coster, M. Addition chain heuristics. In Proceedings of the Conference on the Theory and Application of Cryptology CRYPTO, Santa Barbara, CA, USA, 20–24 August 1989. [Google Scholar]
- Ernie Brickell, G.G.; Seifert, J.P. Mitigating cache/timing based side-channels in AES and RSA software implementations. In Proceedings of the RSA Conference 2006 Session DEV-203, San Jose, CA, USA, 13–17 February 2006. [Google Scholar]
- Fog, A. The Microarchitecture of Intel, AMD and via CPUs: An Optimization Guide for Assembly Programmers and Compiler Makers; Technical University of Denmark: Lyngby, Denmark, 2016. [Google Scholar]
- Intel. Intel 64 and IA-32 Architectures Optimization Reference Manual (April 2018); Intel: Santa Clara, CA, USA, 2018. [Google Scholar]
- Intel. Intel 64 and IA-32 Architectures Software Developer Manuals (March 2018); Intel: Santa Clara, CA, USA, 2018. [Google Scholar]
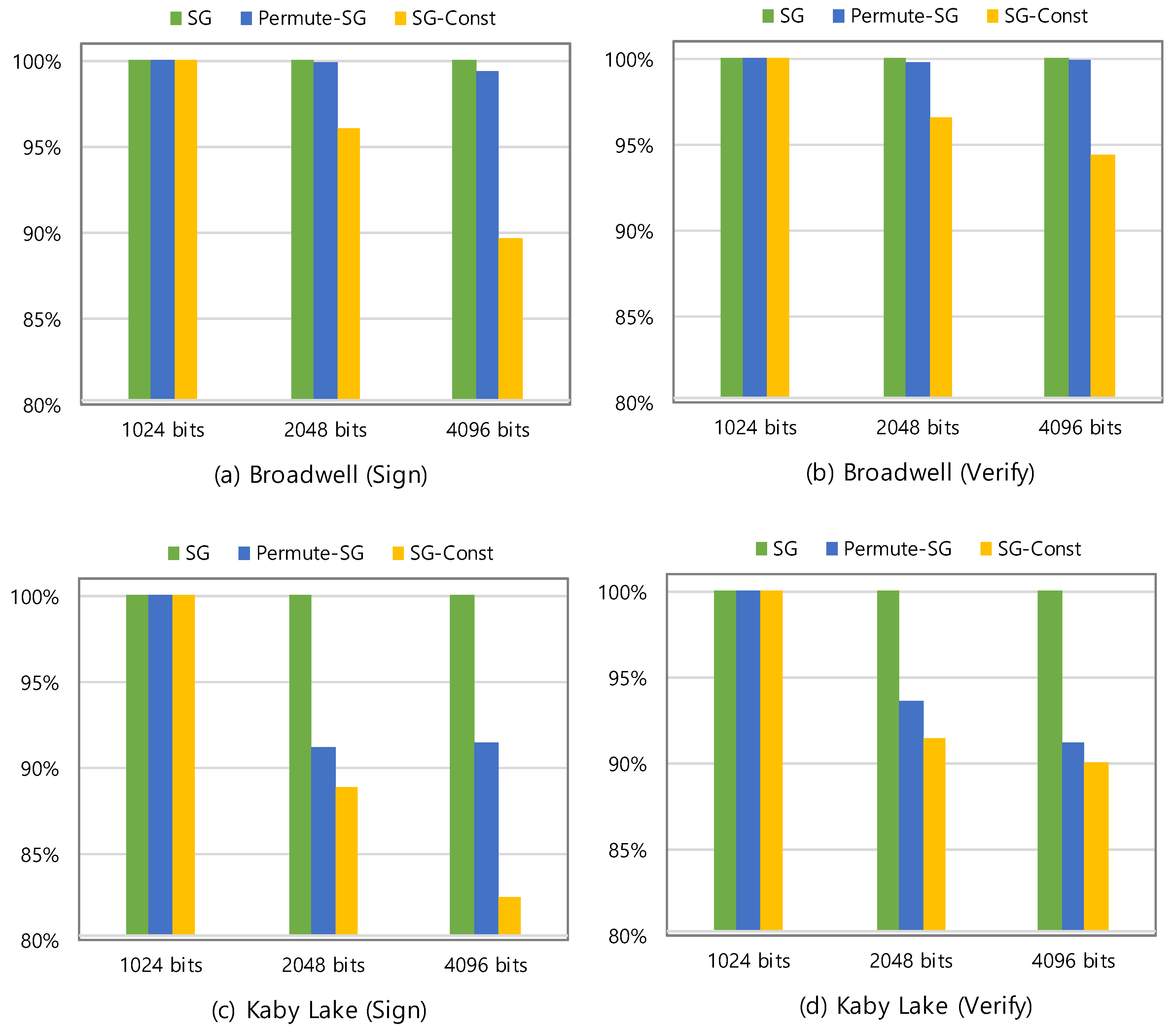
| (a) Benchmark on Xeon E5-2620v4 (Broadwell) | ||||||
| RSA Bits | SG | SG-Const | Permute-SG | |||
| sign/s | verify/s | sign/s | verify/s | sign/s | verify/s | |
| 1024 | 6698.2 | 96,683.1 | 6702.4 | 96,869.6 | 6555.4 | 96,262.6 |
| 2048 | 903.8 | 28,983.1 | 868.3 | 27,985.6 | 902.7 | 28,934.8 |
| 4096 | 126.4 | 7835.7 | 113.3 | 7400 | 125.7 | 7831.7 |
| (b) Benchmark on Core i7-7820HQ (Kaby Lake) | ||||||
| RSA Bits | SG | SG-Const | Permute-SG | |||
| sign/s | verify/s | sign/s | verify/s | sign/s | verify/s | |
| 1024 | 7442.1 | 108,685.8 | 7101.9 | 97,294.2 | 7544.7 | 103,288.5 |
| 2048 | 999.6 | 31,684.9 | 889.0 | 28,972.2 | 911.6 | 29,650.9 |
| 4096 | 140.9 | 8748.2 | 116.3 | 7877.3 | 128.9 | 7977.5 |
© 2018 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shin, Y. Fast and Secure Implementation of Modular Exponentiation for Mitigating Fine-Grained Cache Attacks. Appl. Sci. 2018, 8, 1304. https://doi.org/10.3390/app8081304
Shin Y. Fast and Secure Implementation of Modular Exponentiation for Mitigating Fine-Grained Cache Attacks. Applied Sciences. 2018; 8(8):1304. https://doi.org/10.3390/app8081304
Chicago/Turabian StyleShin, Youngjoo. 2018. "Fast and Secure Implementation of Modular Exponentiation for Mitigating Fine-Grained Cache Attacks" Applied Sciences 8, no. 8: 1304. https://doi.org/10.3390/app8081304




