Abstract
In this note we introduce different levels of decay in the Goyal, Galeotti and Kamphorst (GGK) insider-outsider model of network formation. First, we deal with situations where the amount of decay is sufficiently low to avoid superfluous connections in strict Nash networks and we examine the architectures of strict Nash networks. We show that centrality and small diameter are robust features of strict Nash networks. Then, we study the Nash and efficient networks when the decay vanishes.
1. Introduction
Social networks play a vital role in the diffusion of information across society in setting as diverse as referral networks for jobs (Granovetter, 1974) and assessing quality of products ranging from cars to computers (Rogers an Kincaid, 1981). The role played by networks has led researchers to develop theories of network formation. Several models have been proposed which address different types of network situations.
Our paper deals with the two-way flow connections model introduced by Bala and Goyal (2000a). In this model a player i can access a player j directly by forming a costly link with j. Moreover, through her link with j, player i accesses other players that player j is accessing on her own. Finally the link formed by player i creates a similar flow of information to player j, and hence the name two-way flow model. A phone call is a typical example given to illustrate this type of situation.
In the basic two-way flow model of Bala and Goyal (2000a), the transmission of information between two players is independent of the distance between these players in the network, that is there is no decay. Moreover, players are homogeneous, that is each player i benefits identically from accessing other players and all the costs associated with the setting of links do not depend on the identity of the initiator and the receiver of the link. In this context, Bala and Goyal (2000a) find that the set of equilibrium networks is very small, i.e., only the empty network and the inward-pointing star (a star network where the player at the center forms all the links) can be strict Nash networks.
Now in many situations they are delays as well as lowering of quality, when information is transmitted through a series of agents, making decay a significant factor. Moreover individuals are often heterogeneous. For instance some of them may be more interesting in a particular issue and therefore better informed which makes them more valuable as contacts.
In this paper, we focus on the impact of the introduction of both decay and players heterogeneity on the architectures of networks that will be formed in equilibrium. We ask what are the predictable patterns of networks that will emerge when players have the opportunity to set links between each other, in presence of decay in the flow of resources and players heterogeneity.1
Our paper revisits the insider-outsider model introduced by GGK (2006) and refines some of their results. The authors introduce heterogeneity of players in the two-way flow model of Bala and Goyal (2000a). More precisely, they assume that players belong to different groups and costs of forming links within groups is lower than costs of forming inter-groups links. The model is called the insider-outsider model in their paper. GGK (2006) first consider the transmission of value to be independent of the length of the paths between players, that is there is no decay. Then they introduce a small amount of decay into their framework to test the robustness of their findings.2 They show that for very small amount of decay and for intermediate costs of intra-groups and inter-groups links3, the empty network and the interlinked periphery-sponsored stars network are the only strict Nash networks. Note that a interlinked periphery-sponsored stars network satisfies two conditions. First, in each group there exists a player, called the center player, such that all other players of the group, called the periphery players, form a link with the center player. Second, there exists a player belonging to one group who forms a link with the center player of the other group.
In the paper we elaborate on the insider-outsider model introduced by GGK (2006) concerning decay in two directions. First, we deal with situations where the amount of decay is sufficiently low to avoid superfluous links in strict Nash networks and we examine the architectures of strict Nash networks. We show that in this situation the set of non-empty strict Nash networks is larger than in GGK (2006). It includes three other types of architectures in addition to interlinked periphery-sponsored stars networks. It is interesting to note that all these architectures share similar structural properties, namely small diameter and high asymmetries in centrality of players, since these properties are also features of equilibrium networks in the homogeneous model of Bala and Goyal (2000a) and the insider-outsider model without decay of GGK (2006). Second, we refine the result of GGK (2006) by assuming that the decay is sufficiently close to 1. More precisely, the class of interlinked periphery-sponsored stars networks, that the authors show as the unique non-empty strict Nash network contains two types of architectures. In the first one, the inter-groups link is sponsored by the center of a star, while in the second one this link is sponsored by a periphery player. We show that if the amount of decay is very low, then the second type of architecture cannot be strict Nash networks. So only the first type of architecture can be non-empty strict Nash networks. This result is important since it shows that strict Nash networks are also efficient networks when the amount of decay is low enough.4
2. Model Setup
We consider a society in which individuals are divided into pre-specified groups and costs of forming links within the groups are lower as compared to costs of forming inter-groups links. To simplify, we assume that there are only 2 groups. Let be the set of players belonging to group t, . The set of players is . As in GGK (2006), we assume that .5 In the following we will assume that players who belong to the same group are similar and players who belong to different groups are different. In this paper the fact that two players are similar will allow them to have relationships which are less costly than the relationships between two players who are different. Indeed, if two players are similar they can communicate quickly (they speak the same language), while if two players are different (they speak different languages) the communication takes time and is most costly.
Each player is assumed to possess some information of value to other players. She can augment her information by communicating with other people. This communication is made possible via pair-wise links. A strategy of player , , is a vector , where for each player . We say that player i has formed a link with player j in g iff . We assume throughout the paper that the link allows both players i and j to access each other’s information. The set of strategies of player i is denoted by . The set is the set of pure strategies of all players. A strategy profile can be represented as a directed network. We use () to refer to the network obtained when the link is added (removed) from g. Given a network , let denote the network obtained when all of player i’s links are removed from g. Let . For a network g, a chain between player k and player j, , is a finite sequence of distinct players such that and , . The distance between i and j in g is given by the number of links in the shortest chain between i and j (if there is no chain between two players i and j in g we set ). The diameter of a network g is . Let be the couples of players who belong to the group that are at maximal distance in g. A network g is minimal if whenever there is a chain between i and j in . A network g is connected if . Moreover we say that a group of players , , is connected in g if for any two players . A network g is minimally connected if it is connected and minimal. The subnetwork , , of g is a network which consists of the players in and such that for all . Finally, we say that a player i is an end player if for one player , and for all players .
We now define five networks architectures that play a role in our results. A periphery-sponsored star (PSS) is a network g in which there exists a center player, , such that for all , and there are no other links. A center interlinked periphery-sponsored stars (CIPSS) is a network g in which is a PSS for each and there is a link between the two centers. A non center interlinked periphery-sponsored stars (NCIPSS) is a network in which is a PSS for each , and a non center player of a PSS forms a link with the center player of the other PSS. It is worth noting that CIPSS and NCIPSS are not treated as distinct architectures in GGK (2006), since the authors called both these architectures interlinked periphery-sponsored stars. A mixed star (MS) is similar to a PSS except that there is a unique player called such that instead of . A interlinked mixed stars network (IMS) is a network in which is a MS, is a PSS, and forms a link with . A distance 3 interlinked periphery-sponsored stars network (D3PSS) is a network such that is a PSS, and there are two players in , say and , such that is a PSS, and . Figure 1 below depicts these architectures. In this figure, players in group are denoted by 0 and players in group are denoted by 1. In the following, we denote the set of networks which consists of all PSS, all CIPSS, all NCIPSS, all IMS, and all D3PSS, by .
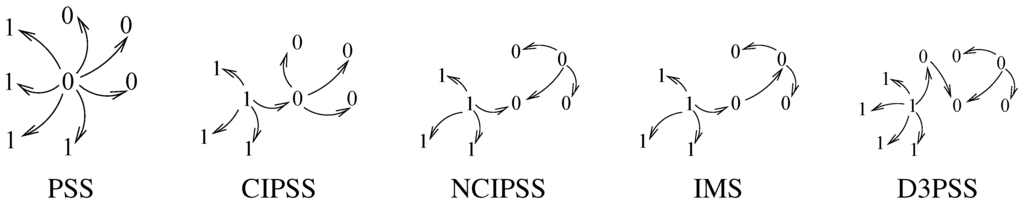
Figure 1.
Networks architectures.
To complete the definition of a normal-form game of network formation, we specify the payoffs. Let () be the costs incurred by a player , , when she forms a link with a player (). We assume that . Let be the value of the decay parameter. Define as the set of players who are observed by player i in the network g. The payoff obtained by player , , in a network g is given by:
Note that this payoff function is identical to the one in GGK (2006) in their insider-outsider model with decay. In this payoff function we take into account the three following assumptions: (i) the value that player i obtains from player j does not depend on the group of j, (ii) the value that player i obtains from player j depends on the distance between i and j, and (iii) the cost that player i incurs for a link with player j depends on whether i and j belong to the same group or not.
The strategy is said to be a best response of player i to the network if:
The set of all of player i’s best responses to is denoted by . A network g is said to be a Nash network if for each player . We define a strict best response and a strict Nash network by replacing ‘≥’ with ‘>’. The set of non-empty strict Nash networks is denoted by .
A network g is said to be an efficient network if it maximizes the total payoffs of players, that is , for all .
3. Results
Let be the value of the decay parameter such that a non-empty strict Nash network is minimal.6 We are interested by the second point of Proposition 4.3 of GGK (pg.365, 2006) where the authors choose such that . We will show that if , then it is possible to obtain a more precise characterization of strict Nash networks than the one proposed by GGK. It is worth noting that if , then each end player sponsors her link in a strict Nash network. We now present a technical remark which is useful in several proofs.
Remark 1
(R1) If , , and , then .
Indeed, if player replaces the link by the link , then obtains a payoff greater or equal to the payoff she obtains in g.
The proposition that follows shows that a non-empty strict Nash network is minimally connected.
We first present a lemma that is used in the proposition. The proof of this lemma is put in Appendix.
Lemma 1
Let and . Suppose in which there are four players , such that . If there is a chain between i and which goes through players j and , then and , .
Proposition 1
Suppose and . A non-empty strict Nash network is minimally connected.
Proof
Let be the set of players in who form no links with any player, and let be the set of players in who received a link from a player in . Suppose and . It follows that g is minimal. We now show that if , then g is connected.
First we show that if player has formed a link, then all players in must observe her. To introduce a contradiction, assume that there exist in g two players, , , and a player , such that and . Since and plays a strict best response, we have by linearity of the payoff function: . Hence player does not play a strict best response in g. Therefore, , a contradiction. It follows that either no player has formed a link in , , or there exists a chain between all players who belong to . Formally, for each , we have either or is connected in g.
We now use this result to show that g is connected. We consider two cases.
- Suppose and , that is there are no links between the two groups. We will show in the following that such a situation cannot happen.First, since g is non-empty, we cannot have simultaneously and . Suppose that , for one . In that case, we know from the point above that is connected.Second, we show in two steps that constitutes a PSS. We begin to show that if , then . To introduce a contradiction, suppose that . In that case there exist two distinct players such that . We have: (i) since , (ii) there is a chain between and which goes through and , (iii) players , , , and belong to . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. A contradiction. Thus we can conclude that constitutes a star. In this star, each end player sponsors her link with the center, since . So constitutes a PSS.Third, we show that . Indeed, since , a player strictly gains by forming a link with the center of the PSS formed by the group . It follows that , which contradicts the assumption .
- Suppose or in g. We assume wlog that there are players and such that . Since a player in has formed a link, is connected. We now show that g is connected. To introduce a contradiction suppose g is not connected. In that case there exists a player such that . We have: since and player obtains more resources due to the link with than through her link with . It follows that does not play a strict best response, a contradiction. Thus we conclude that g is connected.
The previous proposition means that in a non-empty strict Nash network, each player i obtains some resources of all other players. Obviously, each player i does not obtain all the resources of other players because of the decay.
The proposition that follows deals with the diameter of non-empty strict Nash networks. We first present a lemma that is used in the proposition. This lemma shows that if there are several links between players of different groups in a strict Nash network, then there is a group, say , such that players in are not directly linked with players who belong to .
Lemma 2
Let and . Suppose and . If and , then or .
The proof of the lemma is put in Appendix.
Proposition 2
Suppose and . Let .
- 1.
- If g contains one inter-groups link: with and , then and , for .
- 2.
- If g contains several inter-groups links between the two groups, then .
Proof
Suppose and . We know from Proposition 1 that a non-empty strict Nash network is minimally connected. We prove successively the two parts of the proposition.
- Let , with only one inter-groups link. We assume that this link is formed by with , that is .First, we show that . To introduce a contradiction, we assume that there are such that . There are two cases.(a) Let , with . There are players such that . In that case: (i) we have since , (ii) there exists a chain between players and which contains players and , and (iii) . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. A contradiction.(b) Suppose now that if , then either , or . In other words, the player who has formed a link with a player in , is always one of the two players at maximal distance in . In the following we deal with . Note first that since is an end player and , has formed a link with a player, say , who belongs to the chain between and in g. There are two cases.(b1) Suppose player has formed a link in g with a player, say , who belongs to the chain between and . In such a case we have (i) , (ii) there is a chain between players and which contains players and , and (iii) . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. A contradiction.(b2) Suppose player has formed no links in g with a player who belongs to the chain between and . In that case, there is a player, say , who has formed the link with and belongs to the chain between and .We show that the link is the only link player has formed in g. Indeed, suppose has formed a link with a player say . Suppose does not belong to the chain between and . We have and by point (a) we know that g is not strict Nash. Suppose now that belongs to the chain between and . We have (i) , (ii) there is a chain between and which contains players and , and (iii) . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.Since the link is the only link that player has formed in g, it follows that there is a player who belongs to the chain between and such that . However in this situation player does not play a strict best response, by (R1). Consequently . A contradiction.Second we show that . Using arguments similar to those for it is easy to see that . We now show that . To introduce a contradiction suppose that . We divide the proof into two cases.(a) Suppose there are such that . So there are players such that . In that case: (i) we have since , (ii) there is a chain between and which contains players and , and (iii) we have . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.(b) Suppose now that if , then either , or . In the following we deal with . Since is an end player, she has formed a link with a player who belongs to the chain between and . In such a case we have (i) , (ii) there exists a chain between players and which contains players and , and (iii) , and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.The conclusion follows.
- We now consider a minimally connected strict Nash network g in which there are more than one inter-groups link. The arguments which allow to obtain the contradiction in this part are very similar to the arguments used in the previous part. Therefore we briefly show the way to use Lemma 1 in the proof. We know from Lemma 2 that there exists one player who belongs to one group, say , such that is involved in all the inter-groups links.We first deal with players in and show that for all . Let be the set of players such that . By assumption we have . Moreover we know that we have for all .To introduce a contradiction, we suppose that . Since g is connected there are players and a player such that . Let be an end player such that belongs to the chain between and . By construction there is a player such that . Note that we can have and . Moreover, since , we have .Either is an end player, and since , or there exists an end player such that . In the second case by construction and since , we have for one player .If is an end player, then Lemma 1 is contradicted for players and g cannot be a strict Nash network. If is not an end player, then Lemma 1 is contradicted for players and g cannot be a strict Nash network. It follows that . It is worth noting that for all since .We now deal with players in and show that for all . To introduce a contradiction, suppose there is an end player , such that . Since g is connected and there is a player such that . In that case Lemma 1 is contradicted for players , since . Therefore g is not a strict Nash network. The result follows.To conclude, since for all we have .
It follows from the previous proposition that the maximal diameter of strict Nash networks is equal to five. It is worth noting that small diameter also characterizes non-empty strict Nash networks in the model with no decay of GGK (2006). The proposition that follows gives an exact characterization of strict Nash networks. We first present two lemmas that are used in the proposition. The proofs of these lemmas are put in Appendix.
Lemma 3
Suppose and . Suppose g is a non-empty strict Nash network and there is only one inter-groups link.
- 1.
- If there is such that , then g is a D3PSS.
- 2.
- If for each we have , then g is a CIPSS, a NCIPSS or a IMS .
Lemma 4
Suppose and . Suppose g is a strict Nash network and there are several inter-groups links. Then g is a PSS.
Proposition 3
Suppose and . Then, . Moreover, there exists such that for any , CIPSS are the only networks in .
Proof
Suppose , and . Lemmas 3 and 4 establish that . Concerning the second part of the proposition, GGK (2006, Proposition 4.3 part (2a), pg.365) showed that for δ sufficiently close to 1, only interlinked periphery-sponsored stars networks can be candidates as strict Nash networks.
It is easy to check that in a CIPSS, g, no player has an incentive to change her strategy when δ is sufficiently close to 1. Therefore, .
We now show that if δ is sufficiently close to 1, then a NCIPSS cannot be strict Nash. Indeed, suppose a NCIPSS, g, in which players and are respectively the centers of the stars formed with players in and . Let player be the player such that . Let , be a periphery player. If deletes her link with and forms a link with , then the change in ’s payoffs is . Consequently, for any , we have , and . The result follows.
It follows from the previous proposition that in all non-empty strict Nash architectures few players play a key role in the flow of resources. More precisely, we can distinguish two types of players, end players and non-end players. If one player of the first type is deleted, then only her own resources will not be accessed by other players. This is very different for the second type of players. As an illustration suppose a population with 100 players, that contains two groups, denoted by , of 50 players each. We know from Proposition 3 that there are only at most 4 players who are not end players in a non-empty strict Nash network. Suppose we delete one of these players, say , . Then this will prevent players of group the access to resources of at least 47 players of the group . In that sense, non end players have a significant role in the flow of resources in the network, by contrast with end players. It is worth noting that asymmetries in players centrality also characterizes non-empty strict Nash networks in the model with no decay of GGK (2006).
We now give an example of parameter values such that all networks are strict Nash networks.
Example 1
Suppose . It can be checked that non minimal networks cannot be strict Nash. Moreover, it can be checked that all networks are strict Nash networks.
We now show that for the same range of costs as in Proposition 3, if the decay parameter is sufficiently close to 1, then CIPSS are efficient networks.
Proposition 4
Suppose . Then there exists such that for any , CIPSS are efficient networks.
Proof
Let g be an efficient network. First, we show that there exists sufficiently close to 1 such that there is at most one link between players in and players in in g. Suppose that there is no decay, that is . In that case, we are in the situation studied by GGK (2006, p.369). Consequently, (a) each component part of an efficient network is minimal; (b) if g is non-empty and efficient, then it is either minimally connected with 1 inter-groups link and intra-groups links or partially connected with each group generating a minimal connected component. Since , g is connected by Proposition 1. The above observations hold when is sufficiently close to 1. Suppose now that . To introduce a contradiction, suppose that there are two links between players and players in g. If one of these links is replaced by a link between two players who belong to the same group, then the difference in total cost is , and the difference in the total gross payoff cannot exceed . Clearly for all , there is sufficiently close to 1 such that . Second, we show that CIPSS are efficient networks. We know that an efficient network is minimally connected and contains one link between the two groups. Let E be the set of minimally connected networks which contain one link between the two groups. E is the set of networks candidate to be efficient. All the networks in E contain the same number of links. Consequently, we do not need to take into account total cost of setting links in networks , but only the gross total payoff: . Only the distance between the players plays a role in this function. Let . We have:
Since each is minimally connected, it contains links. It follows that in each we have . We know that in there is at most one link between players in and players in . Let this link be between and . In that case, all players cannot be at distance 2 of players . Consequently, for any , , where is the total number of couples, is the number of couples at distance 1, and is the number of other couples which cannot be at distance 2. In CIPSS networks there are couples of players who belong to . Since all couples which do not belong to belong to in a CIPSS, the result follows.
Recall that the class of interlinked periphery-sponsored stars networks that GGK (2006) find as the unique non-empty strict Nash networks, contains two types of architectures, namely CIPSS and NCIPSS. It is easy to see why NCIPSS are less efficient than CIPSS. Indeed, recall that in NCIPSS there exists a link between a periphery player, say , and the center player of the star formed by the other group, say . Suppose that this link is replaced by a link between the two center players, and say . It is easy to see that the loss of the total value obtained by is the same as the additional value obtained by , while the total value obtained by each player increases. Therefore our result shows that if δ is high enough, then non-empty strict Nash networks are also efficient networks.
4. Conclusion
Heterogeneity of players and imperfect transitivity of information flows are central features of economic and social networks. In this note we re-examine the insider-outsider model of GGK (2006) which takes these features into account, by allowing for different degrees of decay in information flows. We refine the results of GGK (2006) paper for the case decay is low and costs of intra-group and inter-group links are intermediate. We find new strict Nash architectures for higher values of decay. It is interesting to note that all these architectures have small diameter and high asymmetries with regard to centrality of players, since these properties are also features of equilibrium networks in the GGK (2006) insider-outsider model with no decay. We also refine the results of GGK (2006) insider-outsider model when δ is sufficiently close to 1. We show for this case that only one type of interlinked periphery-sponsored stars networks can be strict Nash networks. It follows from this result that equilibrium networks are also efficient networks when δ is sufficiently close to 1.
In this note, we restrict our study to situations in which there are only two groups of players. Future research may consider introducing a higher number of groups in the model to examine the robustness of our finding concerning centrality and diameters of strict Nash networks as well as the compatibility between strict Nash and efficient networks.
References
- Galeotti, A.; Goyal, S.; Kamphorst, J. Network Formation with Heterogeneous Players. Game. Econ. Behav. 2006, 54, 353–372. [Google Scholar] [CrossRef]
- Bala, V.; Goyal, S. A Noncooperative Model of Network Formation. Econometrica 2000a, 68, 1181–1230. [Google Scholar] [CrossRef]
- Bala, V.; Goyal, S. A Strategic Analysis of Network Reliability. Rev. Econ. Design 2000b, 68, 205–228. [Google Scholar]
- Granovetter, M.S. Getting a Job: A Study of Contacts and Careers; Harvard University Press: Cambridge, MA, USA, 1974. [Google Scholar]
- Rogers, E.; Kincaid, D.L. Communication Network: Toward a New Paradigm for Research; Free Press: New York, NY, USA, 1981. [Google Scholar]
- Wasserman, S.; Faust, K. Social Network Analysis: Methods and Applications; Cambridge University Press: Cambridge, UK, 1994. [Google Scholar]
Appendix
Proof of Lemma 1
Let , , and be four different players. We define as the gross payoff that player j obtains in a network g. Let g be a strict Nash network. Since , it follows that g is minimal. We suppose that and there is a chain between and which goes through players and . Let and .
We have
since player is closer to player than player in .
We set . We assume that and we focus on player (if this assumption is not true, then we use the same kind of arguments but we focus on player ).
We now show that and , , otherwise . We have two cases.
1) Suppose and belong to the same group , . Then the cost that player incurs when she forms a link with is equal to the cost that incurs when she forms a link with . Moreover, we have
and
We have . It follows that player does not play a strict best response and . Therefore, and do not belong to the same group .
2) Suppose and do not belong to the same group. We must show that belongs to the same group as and belongs to the same group as . Let and .
First, we show that and do not belong to the same group, say . To introduce a contradiction, suppose , we have:
since player plays a best response in g. Likewise we have
Since player plays a strict best response in g. By summing the two previous inequalities we obtain:
that is
which is not true since is closer to than , and is closer to than , a contradiction. Second by using the same kind of arguments, we show that it is not possible to have and . The result follows.
Proof of Lemma 2
Suppose . First, since and , we know by Proposition 1 that g is minimally connected. We prove the lemma by contradiction. Suppose there are four players, and , , such that . We have two possibilities which we analyze in turn.
- The two inter-groups links are sponsored by two players who belong to the same group. Suppose wlog that and . Since g is minimally connected, there are four cases which we analyze in turn.C1. There is a chain between and which contains players and . We know that we have also (i) , . (ii) , . When C1 and (i) are valid, it is not possible for (ii) to be valid simultaneously by Lemma 1.C2. There is a chain between and which does not contain and . In that case, there exists a player such that , otherwise player does not play a strict best response since . Either k is an end player, and since , or there exists an end player such that . Suppose k is an end player. We have (i) , (ii) there is a chain between and k which contains players , (iii) , . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. Next suppose the end player is . Then there is a player such that (since ). So we have (i) , (ii) there is a chain between and which contains players , (iii) , . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.C3. There is a chain between and which does not contain players and . This case is symmetric to C2.C4. There is a chain between and which does not contain players and . In that case, there exist players such that , otherwise players and do not play a strict best response since . This gives rise to two situations: either both and are end players, or at least one is not an end player. If both and are end players, we have (i) , (ii) there is a chain between and which contains players and , (iii) . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.Suppose now wlog that is not an end player. Then there exists an end player . By construction and since , we have also for one player such that . Therefore we have (i) , (ii) there is a chain between and which contains players and , (iii) and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.
- The two inter-groups links are sponsored by players who belong to two distinct groups. Suppose wlog that , . Since g is minimally connected, as before there are four cases which we analyze in turn.C1’. There is a chain between and which contains players and . In that case, there exists a player such that , otherwise player does not play a strict best response since . Either k is an end player, and (since ), or there exists an end player such that . In the second case by construction and since , we have also for one player such that . In the first case, by using Lemma 1 for players , it is easy to check that g cannot be a strict Nash network. In the second case we obtain the same result for players .C2’. There is a chain between and which does not contain and . We have (i) , (ii) there is a chain between and which contains players and , (iii) , and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.C3’. There is a chain between and which does not contain and . In that case, there exist players such that , otherwise players do not play a strict best response since . This gives rise to two situations: (I) both and are end players, and (II) at least one is not an end player.(I) Both and are end players. We have , since . We show that , . Indeed we have (i) , (ii) there is a chain between and which contains players and , (iii) , . By Lemma 1, (i), (ii) and (iii) can be simultaneously satisfied only if and .We now focus on players and to obtain a contradiction when , .
- Suppose . Let . We have (i) , (ii) there is a chain between and which contains players and , (iii) , and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. Let . By the same reasoning we obtain a contradiction.
- Suppose . Let be the sequence of players in the chain between and in g, with and .(a) We first show that , if , then for . By construction we have . Suppose . Then we have: (i) , (ii) there is a chain between and which contains players and , (iii) . By Lemma 1, (i), (ii) and (iii) can not be simultaneously valid if . The result follows.(b) We now show that if , then for . By (a) we have . It follows that we have (i) , (ii) there is a chain between and in g which contains players and , (iii) , . By Lemma 1, (i), (ii) and (iii) can be simultaneously valid only if .It follows that since . A contradiction since we know that .(II) At least one of players or is not an end player. Suppose w.l.o.g. that is not an end player. Then there exists an end player , such that . By construction and since , we have also for one player such that . Therefore we have (i) , (ii) there is a chain between and which contains players and , (iii) , . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.C4’. There is a chain between and which does not contain players and . In that case, there exists a player such that , otherwise player does not play a strict best response since . Either k is an end player, and since , or there exists an end player such that . Let k be an end player. We have (i) , (ii) there is a chain between and k which contains players and , (iii) , and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1. Next let the end player be . Then there is a player such that (since ). We have (i) , (ii) there is a chain between and which contains players and , (iii) , and . When (i) and (ii) are valid, it is not possible for (iii) to be valid simultaneously by Lemma 1.
Proof of Lemma 3
Suppose and . Let g be a strict Nash network such that there is only one inter-groups link, say the link formed by player with player , . Since and , we know from Proposition 1 that g is minimally connected. We prove successively the two parts of the lemma.
- We assume that . First, we characterize the architecture of . Let and be such that . Let . We know by the proof of Proposition 2 1.(a) that if , then either , or . Likewise, we know that and is involved only in two links otherwise there is , with and . Consequently, and we call the player in . By R1, does not form a link with . It follows that player forms a link with . Finally, we have and since for all players who belong to this set we have .Second, we characterize the architecture of . We show that all players has formed a link with . Indeed, we know by Proposition 2 that , that is this subnetwork is a star. We now show that is the center of this star. To introduce a contradiction assume that a player is the center of this star. We have and player has an incentive to replace her link with by a link with in g. A contradiction. As each player is an end player, each player has formed a link with since . The result follows.
- Assume that for each , we have . By using the same arguments as in the previous point, we can show that the subnetwork formed by players of group is a star with as the center and each player forming her link with . Concerning the architecture of the star formed by players of group , we can have two cases: (i) Either is the center of the star, or (ii) a player is the center of the star. In case of (i), all players are end players and have formed a link with . So g is a CIPSS. In case of (ii), all players are end players and have formed a link with . Regarding the link between k and , we can have either , or . If , then g is a NCIPSS, and if , then g is a IMS.
Proof of Lemma 4
Suppose and . Let g be a non-empty strict Nash network. We know by Proposition 2 that g is a star. In that case, each periphery player sponsors her link with the center since . Consequently, g is a PSS.
- 1.It is worth noting that decay is just one way of modelling deficiencies in information transmission. Another way is to introduce imperfect reliability of links (see Bala and Goyal, 2000b, for a paper dealing with this).
- 2.Note that Bala and Goyal (2000a) also introduce decay in their basic model. However the authors still assume that players are homogeneous.
- 3.In what follows intermediate costs of intra-groups and inter-groups links has the following interpretation: costs of intra-groups links are such that no player i can have any incentive to form a link with a player j when this link allows i to access only to resources of j; costs of inter-groups links are not so high that this always prevents players to form inter-groups links.
- 4.It is also important from of the point of view of centrality of players in the network. Indeed, while in the first type of architectures, only the players at the center of the stars play a central role in the flow of resources between players, in the second type a third player plays a significant role, since this player allows ressources to flow between the two groups. It follows that in both cases centrality values of the players differ. Note that we refer here to the notion of betweeness centrality, presented by Faust and Wasserman (1994 chapter 5).
- 5.The assumption allows to simplify the proof of Proposition 3.
- 6.Note that for all costs of linking, there always exists a high enough such that if , then no player can have an incentive to form a link with a player she already indirectly accesses in the network.
© 2010 by the authors; licensee MDPI, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).