Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images
Abstract
:1. Introduction
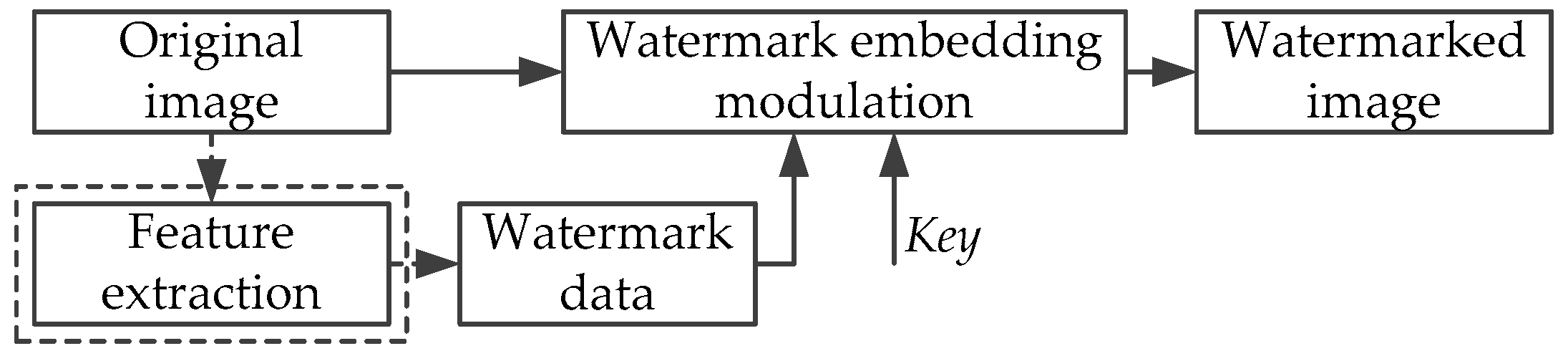
2. Basic Principles and Characteristics of Semi-Fragile Watermark
- Balance between robustness and fragility.On the one hand, after experiencing malicious tampering, such as collage attack, constant average attack, and statistical analysis attack, a watermark should be able to make an alarm response to show its fragility; on the other hand, after experiencing reasonable image-processing operations, such as JPEG compression, brightness adjustment, affine transform, filtering, and noise addition, a watermark should be able to accept them to show its robustness. Therefore, the watermark embedded into the semi-fragile watermarking algorithms must balance the robustness and the fragility well.
- Invisibility.After embedding watermark into the image, the quality of the image cannot have obvious degeneration, and the embedded watermark needs to be invisible to ensure that the original image is not damaged.
- Blind detection.Sometimes people cannot find the original image in many applications, and even if sometimes the original image is provided by a third party, people still cannot believe it. So this requires that content authentication algorithms can achieve the detection process without original images.
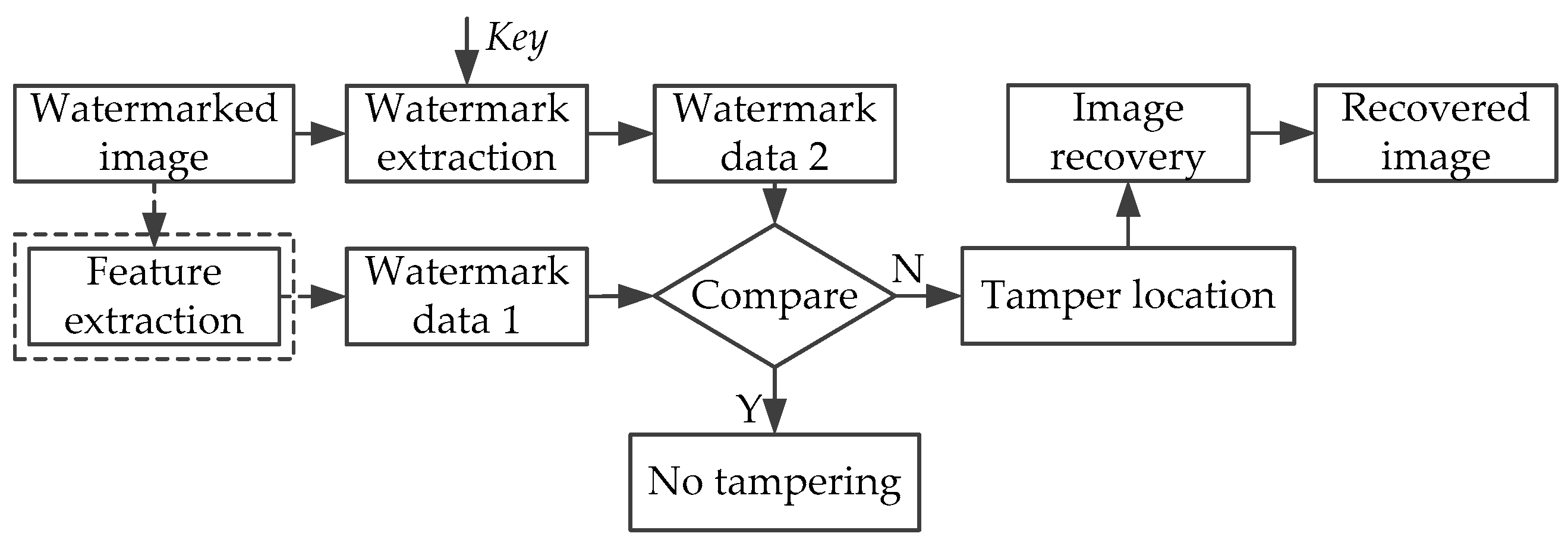
- Localization and recoverability.If the image has been maliciously tampered with, the algorithm should be able to accurately determine and locate the tampered regions, and then recover it using the recovery data.
- Security.Attacks on the security of watermarks are intentional, and the next step is to threaten the robustness of the watermark. Semi-fragile watermarking algorithms should be able to resist malicious tampering, and cannot be easily detected, imitated, tampered with or fabricated by unauthorized parties.
- Versatility.Versatility, which is also known as ease of use. If a watermarking algorithm has good performance, it should be applicable to a variety of file formats and media formats.
3. Common Attacks
3.1. Collage Attack
3.2. Statistical Analysis Attack
3.3. Vector Quantization Attack
4. Evaluation Indexes
4.1. Evaluation of the Invisibility of Watermark
4.2. Tamper Detection Accuracy
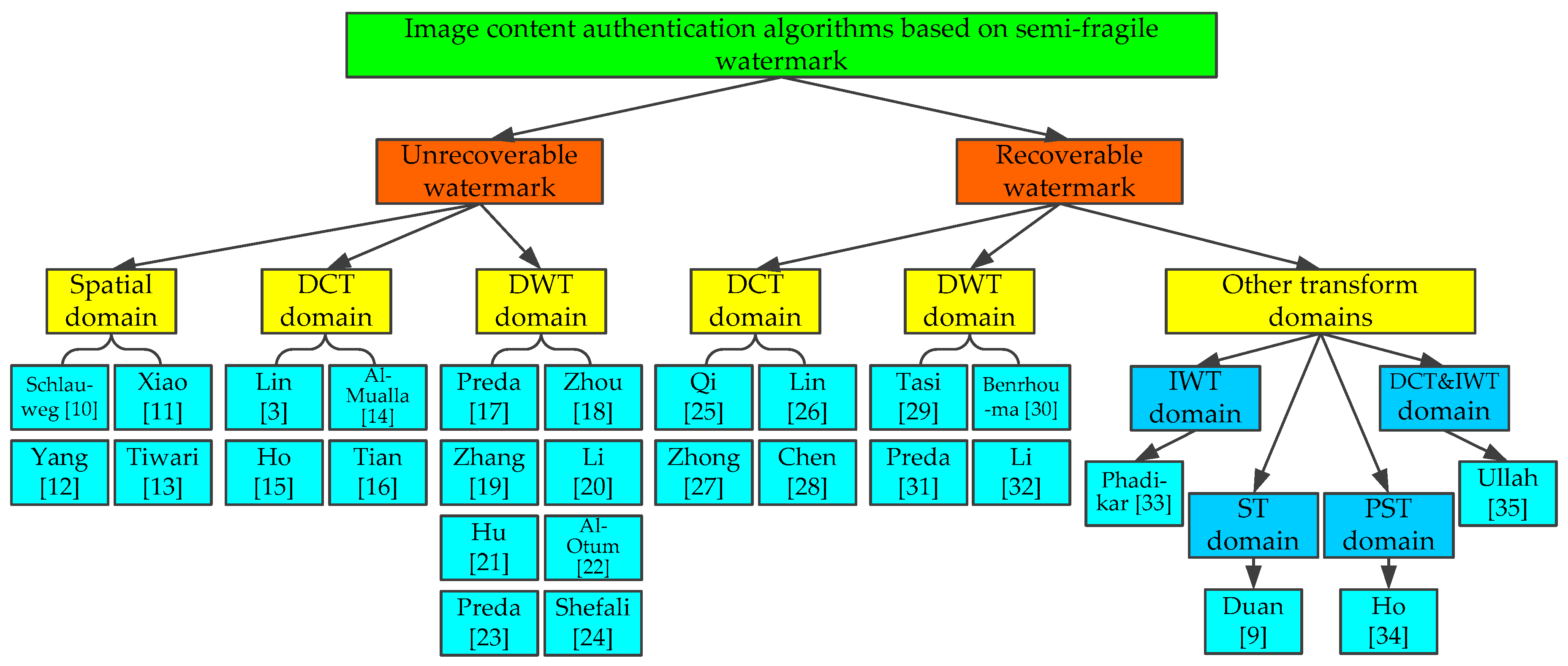
5. Overview on Semi-fragile Watermarking Algorithms
5.1. Unrecoverable Semi-Fragile Watermarking Algorithms
5.1.1. Spatial Domain
5.1.2. Transform Domain
- DCT DomainSince the block DCT is the basis of JPEG compression, it is possible to embed semi-fragile watermarks into DCT domains to enhance the ability to resist JPEG compression. Lin et al. [3] put forward a semi-fragile watermarking algorithm using spread spectrum technology. The correlation about pixel differences in spatial domains is performed by the detector, which is modified. The watermarking information is embedded into the low- and medium-frequency areas in the DCT domain. Under moderate compression, the tamper detection accuracy of the algorithm in this paper can reach to 75%, while under light compression the accuracy can reach to 90%. In smooth areas, the algorithm can perform well, but in edge or texture areas, its performance is no longer good. To enhance the functions of the algorithm in [3], Al-Mualla proposed a method that can not only adjust to the watermarking strength but the detector type based on the image content characteristics [14]. The algorithm can improve the correlation calculation in edge or texture areas. The watermark embedded in the textured blocks is stronger than in other kinds of blocks. Compared with the algorithm in [3], this algorithm has a much smaller number of false positives, especially in edge and texture areas. However, the switching in the algorithm may lead to lower PSNR.Many watermarking algorithms in DCT domains implement the processes of watermark generation and embedding based on important properties of JPEG compression [15,16]. In [15], Ho and Li put forward a watermarking algorithm that embedded watermarks in the DCT domain. The corresponding sign and size of coefficients in the DCT domain are changeless before and after JPEG compression. Based on this point, the feature codes are extracted as watermarking information. To enhance the ability to resist malicious tampering, the algorithm uses the nine-neighborhood system to ensure that the nondeterministic block dependency is implemented. If the host image is quantized to the predetermined QF firstly, it can accept any further compression with the shorter quantization step size. The reason is that the initial quantization coefficients can be accurately re-quantified by using the original step size. According to the invariance principle of DCT coefficients in JPEG image compression process, Tian and Wang carried out the processes of watermark generation and embedding modulation [16]. Under the condition that the embedding intensity of watermarking information is not increased, the watermarked image can be protected more effectively when faced with transform domain attacks. In this algorithm, the judgment about the false alarm area is added, and the five-neighborhood strategy is combined to realize the correlation between the image blocks, which increases the security of the algorithm and the accuracy of the localization for tampered areas. In addition, this method has the ability to tolerate a certain degree of JPEG compression, but no other non-malignant tampering is involved in the paper.To avoid cut-and-paste attacks, Preda and Vizireanu [17] proposed a semi-fragile watermarking algorithm based on JPEG compression in the DCT domain. The watermarking information is generated by a pseudo-random sequence that combines the secret key with block-dependent properties, and then it is embedded into the low-frequency DCT coefficients selected by the key based on the modified quantization index modulation method. To resist the JPEG compression with high quality factor, the algorithm quantizes the selected DCT coefficients by using the JPEG quantization matrix before embedding the watermark. The algorithm has good invisibility and high accuracy of tampering localization. In terms of and , it has achieved good performance as well. In addition, the algorithm can be extended into color images easily.
- DWT DomainDCT is a global transform from spatial domain to frequency domain for an image, while DWT is a local transform with the capability of multi-scale analysis. Because the DWT has the advantages of both spatial domain and DCT domain, it has become the focus and hotspot in the current research. Zhou et al. [18] combined the spatial domain method with the DWT domain method to propose a semi-fragile watermarking algorithm. The signature is extracted using the spatial domain approach and the watermarking information is inserted by the frequency domain method. The extracted signatures are encoded by the ECC method to eliminate the errors created by normal image processing operations that may bring about changes in the image signatures. To strengthen the security of the watermarking algorithm, the private keys are used to encrypt and decrypt the watermark. This algorithm controls the fragility of the system by adjusting the size of quantization step, and it can resist the traditional image compression. However, since the algorithm extracts the mean value of the pixels in every block as the watermarking information, when the maximum or minimum block is tampered with, the size of quantization step may be altered and then the accurate location of the tampered areas cannot be achieved.The algorithms in DWT domains can also be compatible with JPEG2000 compression [19] and JPEG compression [20]. In [19], J. Zhang and C. T. Zhang proposed a semi-fragile digital watermarking method for JPEG2000 image content authentication. This algorithm combined with JPEG2000 encoder and decoder carries out the processes of the watermark generation and embedding modulation based on the invariant parameters in JPEG2000 image compression process. The tampered regions are located by the wavelet transform characteristic so that the reliability of the image authentication system can be improved. This algorithm selects the important coefficients in DWT domain to achieve the embedding modulation of the watermarking information. The size of the macroblock can be adjusted adaptively according to texture features of the image, so the algorithm can be carried out effectively in both the texture areas and the flat areas of the image. The algorithm can tolerate the normal natural images with the compression code larger than 0.5 bits per pixel (bpp). When the code rate is less than 0.5 bpp, there is a significant distortion in a considerable part of image. In [20], according to the fact that the size relationship of the adjacent wavelet coefficients in high frequency is not changed after JPEG compression, Li and Huang proposed a novel semi-fragile watermarking algorithm against the JPEG compression. The algorithm has high watermarking capacity and good anti-JPEG compression performance. At the same time, it can also accurately locate the tampered areas. To obtain a higher PSNR value, the watermarking information is embedded in sub-bands with smaller variance of adjacent coefficients. The algorithm uses parametric integer wavelets to decompose the image and scramble the watermark before embedding. In this way, it becomes difficult for the attacker to get any information about the watermarking information, so the security of the authentication system can be ensured.To distinguish normal image-processing operations from malicious tampering, Hu and Chen [21] extracted the image characteristics in low-frequency regions of the wavelet domain to obtain two watermarks. One is mainly used to complete the localization of the tampered areas and the other is mainly used to distinguish the normal image processing operations and malicious tampering. Thus, an effective image selection authentication mechanism is provided. The generation and the embedding of the watermark are carried out in the image itself, and two watermark tamper evaluation functions are introduced, which can be used to achieve the purpose of distinguishing attacks. Al-Otum et al. [22] also put forward a semi-fragile watermarking algorithm that can detect and classify the tamper attacks. The algorithm is an improved algorithm based on the quantization approach in the DWT domain, which adopts the multi-scale expansion bits with adjustable watermarking location to embed the random watermarking bit sequence into the DWT low frequency sub-bands of the 2nd DWT levels (LL2, LLLH1, and LLHL1). It can locate the tampered areas accurately and classify the type of the attacks. However, the algorithm has not been developed to process color images and has not been examined to deal with geometric attacks. Many of the semi-fragile watermarking algorithms based on block operations in the transform domain are susceptible to local tamper attacks.To eliminate the drawbacks of block-based algorithms, Preda proposed an improved semi-fragile watermarking algorithm that can locate the tampered areas precisely by using the DWT method and permuting wavelet coefficients randomly [23]. Through the quantization, the watermarking data is embedded into DWT coefficients, and the key is embedded into wavelet coefficients of the watermark, which improves the security of the algorithm. Also, the algorithm can resist the mild-to-moderate JPEG compression. In addition, semi-fragile watermarking algorithms not only can be adopted to tamper detection and localization, but also can have other performance. Shefali and Deshpande [24] put forward a semi-fragile watermarking algorithm to protect image information, which not only could detect the tampered areas in images, but also could be used to declare authentication and authorization. By using DWT, the grayscale still image is decomposed into frequency domain, and multiple, multilevel and multi-energy watermarks are embedded in the image for multi-purposes. Additionally, the use of cryptographic keys increases the security of the system.To improve the security of the watermark, Qi and Xin [25] proposed a semi-fragile watermarking algorithm based on singular value. The watermark in this algorithm is composed of two parts. One is the singular-value-based sequence related to the content, and the other is the private-key-based sequence that is irrelevant to the content. Then the algorithm carries out a series of exclusive-or (XOR) operations on the two parts to obtain the secure watermark. Combined with the adaptive quantization approach, the generated watermark is embedded into a 4 × 4 block of each approximate sub-band. The authentication system of the algorithm has three levels, containing five measures used to quantify the results of the image content authentication. In addition, after undergoing the mild-to-severe image-processing operations that make no changes to the image content, the algorithm can still detect malicious tampering and locate the tampered areas accurately. However, it cannot resist geometric attacks.
5.2. Recoverable Semi-Fragile Watermarking Algorithms
5.2.1. DCT Domain
5.2.2. DWT Domain
5.2.3. Other Transform Domains
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Cox, I.J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Lu, C.S.; Liao, H.Y.M. Multipurpose watermarking for image authentication and protection. IEEE Trans. Image Process. 2001, 10, 1579–1592. [Google Scholar] [PubMed]
- Lin, E.T.; Podilchuk, C.I.; Delp, E.J. Detection of image alterations using semifragile watermarks. In Proceedings of the SPIE—Security and Watermarking of Multimedia Contents II, San Jose, CA, USA, 24–26 January 2000; pp. 152–163. [Google Scholar]
- Castiglione, A.; Pizzolante, R.; De Santis, A.; Carpentieri, B.; Castiglione, A.; Palmieri, F. Cloud-based adaptive compression and secure management services for 3D healthcare data. Future Gener. Comput. Syst. 2015, 43–44, 120–134. [Google Scholar] [CrossRef]
- Podilchuk, C.I.; Delp, E.J. Digital watermarking: Algorithms and applications. IEEE Signal Process. Mag. 2001, 18, 33–46. [Google Scholar] [CrossRef]
- Cayre, F.; Fontaine, C.; Furon, T. Watermarking security: Theory and practice. IEEE Trans. Signal Process. 2005, 53, 3976–3987. [Google Scholar] [CrossRef]
- Fridrich, J.; Goljan, M.; Memon, N. Further attacks on Yeung-Mintzer fragile watermarking scheme. In Proceedings of the SPIE—Security and Watermarking of Multimedia Contents II, San Jose, CA, USA, 24–26 January 2000; pp. 428–437. [Google Scholar]
- Wong, P.W.; Memon, N. Secret and public key authentication watermarking schemes that resist vector quantization attack. In Proceedings of the SPIE—Security and Watermarking of Multimedia Contents II, San Jose, CA, USA, 24–26 January 2000; pp. 417–427. [Google Scholar]
- Duan, G.D.; Zhao, X.; Li, J.P.; Liao, J.M. A novel semi-fragile digital watermarking algorithm for image content authentication, localization and recovery. Acta Electron. Sin. 2010, 38, 842–847. [Google Scholar]
- Schlauweg, M.; Pröfrock, D.; Müller, E.; Palfner, T. Quantization-based semi-fragile public-key watermarking for secure image authentication. In Proceedings of the SPIE—Mathematics of Data/Image Coding, Compression, and Encryption VIII, with Applications, San Diego, CA, USA, 1–3 August 2005; pp. 41–51. [Google Scholar]
- Xiao, J.; Wang, Y. A semi-fragile watermarking tolerant of Laplacian sharpening. In Proceedings of the International Conference on Computer Science and Software Engineering, Wuhan, China, 12–14 December 2008; pp. 579–582. [Google Scholar]
- Yang, H.F.; Sun, X.M.; Sun, G. A semi-fragile watermarking algorithm using adaptive least significant bit substitution. Inf. Technol. J. 2010, 9, 20–26. [Google Scholar]
- Tiwari, A.; Sharma, M.; Tamrakar, R.K. Watermarking based image authentication and tamper detection algorithm using vector quantization approach. AEU Int. J. Electron. Commun. 2017, 78, 114–123. [Google Scholar] [CrossRef]
- Al-Mualla, M.E. Content-adaptive semi-fragile watermarking for image authentication. In Proceedings of the 14th IEEE International Conference on Electronics, Circuits and Systems, Marrakech, Morocco, 11–14 December 2007; pp. 1256–1259. [Google Scholar]
- Ho, C.K.; Li, C.T. Semi-fragile watermarking scheme for authentication of JPEG images. In Proceedings of the International Conference on Information Technology: Coding and Computing, Las Vegas, NV, USA, 5–7 April 2004; pp. 7–11. [Google Scholar]
- Tian, B.; Wang, W. New semi-fragile watermarking for JPEG image authentication. J. Comput. Appl. 2007, 27, 132–134. [Google Scholar]
- Preda, R.O.; Vizireanu, D.N. Watermarking-based image authentication robust to JPEG compression. Electron. Lett. 2015, 51, 1873–1875. [Google Scholar] [CrossRef]
- Zhou, X.; Duan, X.H.; Wang, D.X. A semi-fragile watermark scheme for image authentication. In Proceedings of the 10th International Multimedia Modelling Conference, Brisbane, Australia, 5–7 January 2004; pp. 374–377. [Google Scholar]
- Zhang, J.; Zhang, C.T. Semi-fragile digital watermarking algorithm for JPEG2000 image authentication. Acta Electron. Sin. 2004, 32, 157–160. [Google Scholar]
- Li, C.; Huang, J.W. A semi-fragile image watermarking resisting to JPEG. J. Softw. 2006, 17, 315–324. [Google Scholar] [CrossRef]
- Hu, Y.P.; Chen, Z.G. Wavelet semi-fragile watermarking algorithm for image authentication. Acta Electron. Sin. 2006, 34, 653–657. [Google Scholar]
- Al-Otum, H.M. Semi-fragile watermarking for grayscale image authentication and tamper detection based on an adjusted expanded-bit multiscale quantization-based technique. J. Vis. Commun. Image Represent. 2014, 25, 1064–1081. [Google Scholar] [CrossRef]
- Preda, R.O. Semi-fragile watermarking for image authentication with sensitive tamper localization in the wavelet domain. Meas. J. Int. Meas. Confed. 2013, 46, 367–373. [Google Scholar] [CrossRef]
- Shefali, S.; Deshpande, S.M. Information security through semi-fragile watermarking. In Proceedings of the International Conference on Computational Intelligence and Multimedia Applications, Sivakasi, Tamil Nadu, India, 13–15 December 2007; pp. 235–239. [Google Scholar]
- Qi, X.J.; Xin, X. A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J. Vis. Commun. Image Represent. 2015, 30, 312–327. [Google Scholar] [CrossRef]
- Lin, C.Y.; Chang, S.F. Semi-fragile watermarking for authenticating JPEG visual content. In Proceedings of the SPIE—Security and Watermarking of Multimedia Contents II, San Jose, CA, USA, 24–26 January 2000; pp. 140–151. [Google Scholar]
- Zhong, H.; Jiao, L.C. Semi-fragile watermarking technology in DCT domain. J. Comput. 2005, 28, 1549–1557. [Google Scholar]
- Chen, F.; He, H.J.; Huo, Y.R. Self-embedding watermarking scheme against JPEG compression with superior imperceptibility. Multimed. Tools Appl. 2017, 76, 9681–9712. [Google Scholar] [CrossRef]
- Tsai, M.J.; Chien, C.C. A wavelet-based semi-fragile watermarking with recovery mechanism. In Proceedings of the IEEE International Symposium on Circuits and Systems, Seattle, WA, USA, 18–21 May 2008; pp. 3033–3036. [Google Scholar]
- Benrhouma, O.; Hermassi, H.; Belghith, S. Tamper detection and self-recovery scheme by DWT watermarking. Nonlinear Dyn. 2014, 79, 1817–1833. [Google Scholar] [CrossRef]
- Preda, R.O.; Marcu, I.; Ciobanu, A. Image authentication and recovery using wavelet-based dual watermarking. UPB Sci. Bull. 2015, 77, 199–212. [Google Scholar]
- Li, C.L.; Zhang, A.H.; Liu, Z.F.; Liao, L.; Huang, D. Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimed. Tools Appl. 2015, 74, 10581–10604. [Google Scholar] [CrossRef]
- Phadikar, A.; Maity, S.P.; Mandal, M. Novel wavelet-based QIM data hiding technique for tamper detection and correction of digital images. J. Vis. Commun. Image Represent. 2012, 23, 454–466. [Google Scholar] [CrossRef]
- Ho, A.T.S.; Zhu, X.Z.; Guan, Y.L. Image content authentication using pinned sine transform. EURASIP J. Adv. Signal Process. 2004, 14, 2174–2184. [Google Scholar] [CrossRef] [Green Version]
- Ullah, R.; Alquhayz, H.A. Intelligent watermarking scheme for image authentication and recovery. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 216–223. [Google Scholar] [CrossRef]
| Algorithm | Domain | Size of Host Image | Block Size or Number of Layers | Content-Based Watermark | Embedded Position |
|---|---|---|---|---|---|
| [10] | Spatial | 512 × 512 | 4 × 4 | Yes | Spatial domain pixels |
| [11] | -- | 3 × 3 | No | LSB | |
| [12] | 256 × 256 | 4 × 4 | No | LSB | |
| [13] | 512 × 512 | 4 × 4 | No | Spatial domain pixels | |
| [3] | DCT | -- | 8 × 8 | No | Low and medium frequency areas in DCT domain |
| [14] | 512 × 512 | 8 × 8 | No | Each block in DCT domain | |
| [15] | 248 × 248 | 8 × 8 | Yes | DCT coefficients | |
| [16] | 512 × 512 | 8 × 8 | Yes | 4 nonzero maximum frequency coefficients in DCT coefficient array | |
| [17] | 512 × 512 | 8 × 8 | No | Low frequency areas in DCT domain | |
| [18] | DWT | 256 × 256 | 16 × 16 1 layer | Yes | LL |
| [19] | 512 × 512 | 5 layers | Yes | DWT main coefficients | |
| [20] | 512 × 512 | 1 layer | No | LH1, HL1 | |
| [21] | 512 × 512 | 3 layers | Yes | LH2, HL2, HH2 | |
| [22] | 512 × 512 | 4 × 4 2 layers | No | LL2, LLLH1, LLHL1 | |
| [23] | Various sizes | 3 layers | Yes | LH2, HL2, HH2 | |
| [24] | -- | 2 layers | Yes | LL2 | |
| [25] | 512 × 512 | 4 × 4, 8 × 8 1 layer | Yes | LL of each block in wavelet domain |
| Algorithm | Non-Malicious Tampering | QF of Resisting to JPEG (%) | PSNR of Watermarked Image (dB) | The Ability of Tamper Detection and Location |
|---|---|---|---|---|
| [10] | JPEG | QF ≥ 55 | 37.1–41.0 | -- |
| [11] | Laplacian sharpening | -- | 57.8 | Location accuracy: in units of 3 × 3 pixels |
| [12] | JPEG, low pass filtering, Laplacian sharpening, and salt and pepper noise | QF ≥ 95 | 38.01–40.51 | -- |
| [13] | JPRG, median filtering, low pass filtering, salt and pepper noise, blurring, and rotation | QF ≥ 70 | 42.0 | RFP = 0.024%, RFN = 0.12%, RTP = 99.8% |
| [3] | JPEG | QF ≥ 50 | 36.67 | Location accuracy: in units of 16 × 16 pixels. When QF ≥ 60%, RTP ≥ 93%. |
| [14] | JPEG | QF ≥ 50 | 35.53 | RFP = 13.9%, RFN = 10.4% |
| [15] | JPEG | QF ≥ 50 | 37.2 | -- |
| [16] | JPEG | QF ≥ 50 | -- | RFP = 0 |
| [17] | JPEG | QF ≥ 50 | 44.63 | RFP = 0, RFN = 0.26% |
| [18] | JPEG | -- | 47.12 | -- |
| [19] | JPEG, JPEG2000, median filtering, salt and pepper noise, and Gaussian noise | QF ≥ 40 | 48.28 | -- |
| [20] | JPEG | QF ≥ 60 | 30.0–44.2 | -- |
| [22] | Gaussian noise, salt and pepper noise, cyclic filtering, median filtering, and JPEG | QF ≥ 50 | 48.0–56.0 | Location accuracy: in units of 8 × 8 pixels |
| [23] | JPEG | QF ≥ 80 | 34.26–66.20 | Location accuracy: in units of 2 × 2 pixels |
| [24] | JPEG2000 | QF ≥ 40 | 51.0–62.0 | -- |
| [25] | JPEG, JPEG2000, blurring, Gaussian low pass filtering, salt and pepper noise and median filtering | QF ≥ 30 | 41.39 | Location accuracy: in units of 12 × 12 pixels |
| Algorithm | Domain | Size of Host Image | Block Size or Number of Layers | Content-Based Watermark | Embedded Position |
|---|---|---|---|---|---|
| [26] | DCT | 256 × 256 | 8 × 8 | Yes | DCT coefficients |
| [27] | 256 × 256 | 8 × 8 | Yes | Low frequency coefficients in DCT domain | |
| [28] | 512 × 512 | 8 × 8 | Yes | Middle frequency coefficients in DCT domain | |
| [29] | DWT | 512 × 512 | 2 layers | Yes | Authentication watermark→LH2 Recovery watermark→HH1, HH2 |
| [30] | 256 × 256 | 4 × 4 1 layer | Yes | High frequency coefficients in the DWT domain | |
| [31] | 512 × 512 | 2 layers | Yes | Authentication watermark→LH2, HL2, HH2 Recovery watermark→LH1, HL1, HH1 | |
| [32] | 512 × 512 | 16 × 16, 2 layers | Yes | LH2, HL2, HH2 | |
| [33] | IWT | 512 × 512 | 2 layers | Yes | LH2, HL2, LH1, HL1 |
| [34] | PST | 512 × 512 | 8 × 8 | Yes | Each sine transformed pinned-field block |
| [9] | ST | 512 × 512 | 8 × 8 | Yes | Authentication watermark→middle frequency areas of ST domain Recovery watermark→LSB |
| [35] | DCT and IWT | 512 × 512 | 3 layers | Yes | Authentication watermark→LL3 Recovery watermark→LH2, HL2 |
| Algorithm | Non-Malicious Tampering | QF of Resisting to JPEG (%) | PSNR of Watermarked Image (dB) | PSNR of Recovered Image (dB) | The Ability of Tamper Detection and Location |
|---|---|---|---|---|---|
| [26] | JPEG and brightness adjustment. | QF ≥ 50 | 40.7 | 37.0 | RFP = 0. The performance of the RFN is also excellent. |
| [27] | JPEG and AWGN noise. | QF ≥ 50 | 39.45 | -- | RFP = 0. When the number of tampered sub-blocks is large, the RFN will be very low. |
| [28] | JPEG | QF ≥ 50 | 36.8–42.6 | 32.0 | RTP ≥ 96% |
| [29] | JPEG and AWGN noise. | QF ≥ 50 | 39.5 | 30.7 | -- |
| [30] | JPEG, resizing, noising, and filtering. | QF ≥ 80 | 24.73–40.19 | 14.22–51.70 | RFP = 0.26%, RTP = 56.55% |
| [31] | Salt and pepper noise, JPEG, Gaussian noise, and brightening | QF ≥ 70 | 41.5 | 40.1 | Location accuracy: in units of 4 × 4 pixels. RFN = 0 |
| [32] | JPEG and Gaussian noise. | QF ≥ 50 | 36.0 | 16.8–20.5 | RFP = 0–20%, RFN = 0–55% |
| [33] | JPEG, filtering, scaling, cropping, deletion, and mixed attacks. | QF ≥ 70 | 35.02–35.57 | 31.18–34.92 | For JPEG compression and noise attacks, RFP = 0; for smooth attacks, RFP = 0.84%. |
| [34] | JPEG and wavelet compression. | QF ≥ 40 | ≥33.0 | -- | When QF ≥ 40%, RTP ≥ 96%. |
| [9] | JPEG and Gaussian noise. | QF ≥ 75 | 33.0 | -- | When the tampered area reaches to 20%, RFP = 0, RFN ≤ 10%. |
| [35] | JPEG | QF ≥ 70 | 44.0 | -- | -- |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, X.; Wang, C.; Zhou, X. Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images. Future Internet 2017, 9, 56. https://doi.org/10.3390/fi9040056
Yu X, Wang C, Zhou X. Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images. Future Internet. 2017; 9(4):56. https://doi.org/10.3390/fi9040056
Chicago/Turabian StyleYu, Xiaoyan, Chengyou Wang, and Xiao Zhou. 2017. "Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images" Future Internet 9, no. 4: 56. https://doi.org/10.3390/fi9040056







