Cryptographic Key Management in Delay Tolerant Networks: A Survey
Abstract
:1. Introduction
2. Background
2.1. Preliminaries
- Identity Based Cryptography (IBC)—Shamir first introduced IBC in 1985 [7]. In this cryptographic approach, user identifier information such as email address, IP address, and so forth are used as a public key for encryption and verification of digital signatures instead of certificates. In addition, in IBC, the Private Key Generator (PKG) is the central authority (similar to a Certificate Authority, CA in PKIs) which generates the private keys for participants.
- Public Key Infrastructure (PKI)—Traditional asymmetric or public key cryptography widely and effectively used in the Internet and a plethora of business realms relies on a PKI. The latter depends on the availability and security of a CA, a central control point that everyone trusts.
2.2. DTN Characteristics and Key Management
- Deep space networks [13]—They are characterized by extremely long delays that typically cause memory and/or storage exhaustion.
- Sensor-based networks [13]—Their idiosyncrasies include extremely low end-node power, memory, and CPU capability.
- Terrestrial wireless networks [14]—This ilk of networks is characterized by high mobility and changes in signal strength.
- Vehicular AdHoc networks [15]—They exhibit mobility, self-organization, distributed communication, and road-pattern restrictions.
- Satellite networks [16]—They are characterized by long delays and high rate of packet loss.
- Rural area DTN [18]—They are distinguished by opportunistic behaviour, sporadic and isolated message transmission.
2.3. Security in Real DTN Implementations
- ION [21]—JPL’s implementation of the BP. It implements the BSP Bundle Authentication Block (BAB), Bundle Confidentiality Block (PCB) and Bundle Integrity Block (PIB) security blocks in versions greater than 3.0.0.
- IBR-DTN [22]—BP implementation for embedded systems, which relies on the BSP specification.
- ByteWalla [23]—BP implementation for Android devices. It implements the BSP PCB security block with AES in Galois Counter Mode (GCM).
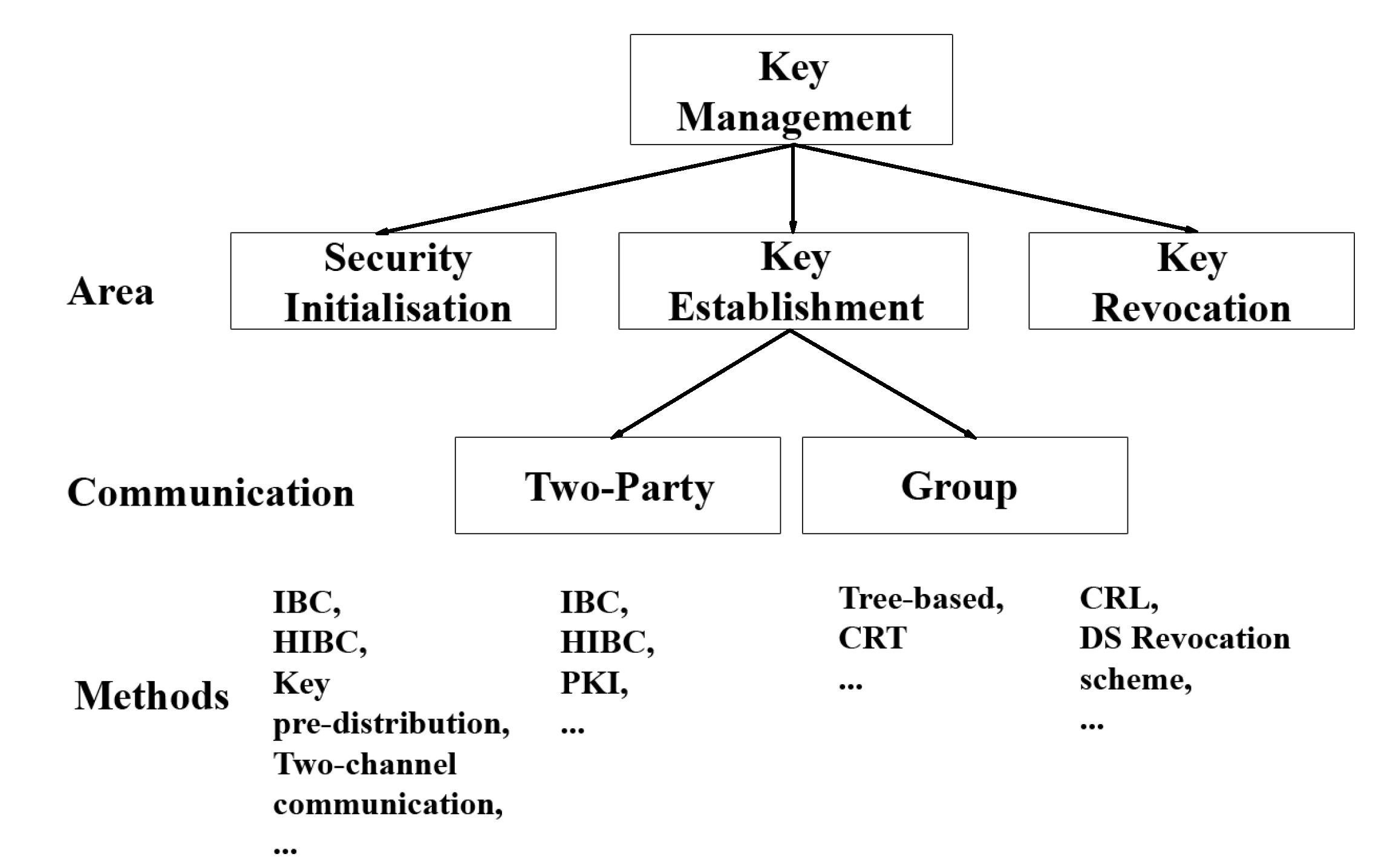
3. Key Management Taxonomy in DTNs
3.1. Security Initialization
3.2. Key Establishment
3.2.1. Two-Party Communication
3.2.2. Group Communication
- Forward secrecy (FS)—requires that users who left the group and know a contiguous subset of old group keys cannot discover subsequent group keys. This ensures that a member cannot decrypt data sent immediately after it leaves the group.
- Backward secrecy (BS)—mandates that a new user that joins the group and knows a contiguous subset of group keys cannot discover preceding group keys. This ensures that a member cannot decrypt data sent before it joins the group.
- Collusion freedom (CF)—requires that any set of fraudulent users who have much information about past keys should be incapable of deducing the current used group key.
- Key independence (KI)—requires that a passive adversary who knows any proper subset of group keys cannot compromise other past or future group keys. That is, the combination of backward and forward secrecy yields key independence.
3.3. Key Revocation
3.4. Standardisation Efforts
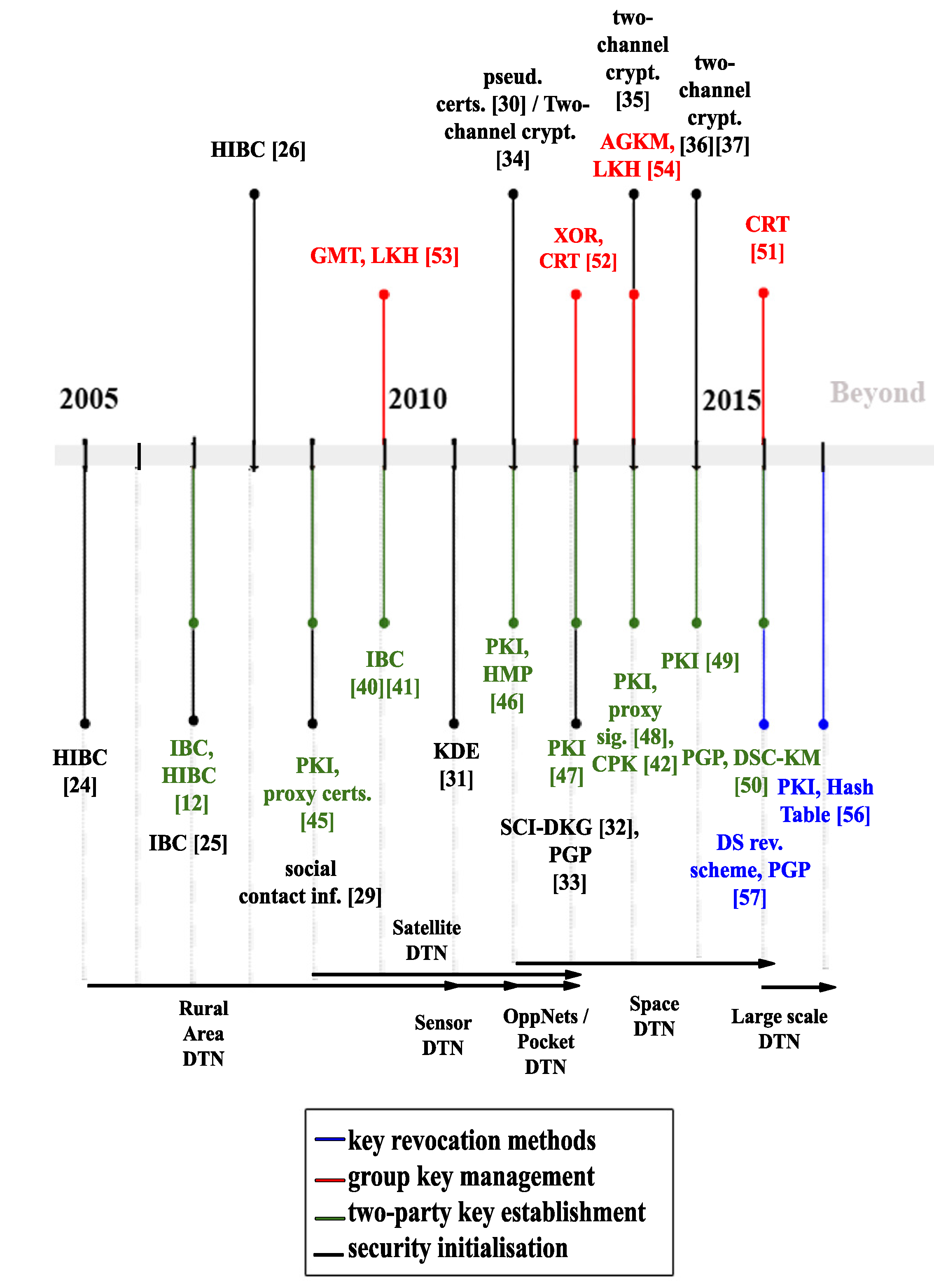
4. Discussion
5. Alternative Key Management Taxonomies in DTNs
5.1. Require or Not Trusted Third Party (TTP)
- Require TTP—Works such as [45,46,47,48,49] are based on PKI solutions mandate a TTP, and thus a CA. Works such as [12,24,25,26,40,41] that are founded on IBC solutions, require a TTP too, namely the PKG. In addition, schemes in group key management that rely on LKH such as [52,54], necessitate a TTP known as Key Distribution Center (KDC). Moreover, the work in [42], which is based on CPK, eliminates the need for online TTP and only needs an off-line PKG.
5.2. Centralised, Decentralised and Distributed
6. Open Research Challenges
- Key Management—As already mentioned, cryptographic key management is the major open issue in DTNs and especially in deep space communications. Section 3 presents and categorises all the schemes proposed until now. Constraints in resources such as memory, power, storage, computation, and bandwidth in DTN nodes put additional challenges on the key management. Resource-conscious key management techniques become a necessity in DTNs. The key management issues that require further research are listed below:
- ‒
- Security initialisation—Security initialisation is an expensive procedure and considering the dynamic nature of DTNs is difficult to handle. As already discussed, the two main approaches are with either a TTP or self-organised. Both approaches have their advantages and disadvantages.
- ‒
- Key update/key lifetime—Key lifetime is difficult to choose and must vary based on the different constraints of DTN environments. For instance, if the key update period is too long, the corresponding key may be exposed. If it is is too short, frequent updates can add large overhead.
- ‒
- Key storage—Considering storage limitations in DTNs in general, and sensor or deep space DTNs in particular, each node must handle the number of possible keying material stored, based on a number of factors, including the number of neighbors, key validity, key expiration, key usage rate, length as well as other stored bundles. Apart from the volume, private keys must be stored securely to avoid compromisation.
- ‒
- Key revocation—Key revocation is impractical in DTNs due to the nature of DTNs. Different approaches must be used instead, depending on the specific network constraints.
- Handling Replays—In DTN networks, due to scarce network resources, the replayed volume of messages must be reduced to the minimum possible. However, this is not always the case due to various DTN scenarios (i.e., authentication scenarios) where at least some replay messages are desirable. Moreover, the huge delays in such networks, complicates handling replays, and therefore the formulation of a DTN replay protection scheme becomes very challenging.
- Traffic Analysis—There are not any security services for protecting/deterring against traffic analysis. However, for some disruption tolerant networks such as military ones, hiding traffic is rather a sine qua non.
- Routing Protocol Security—There are no well-documented DTN routing protocols, so DTN routing protocol security is an open issue. However, some of the existing security features of the underlying protocols can be used.
- Multicast Security—Currently, there is no mechanism to separate between a multicast and anycast endpoint. DTN security architecture does not address the security aspects of enabling a DTN node to register with a particular multicast or anycast endpoint identifier at all.
- Performance Issues—Security within a DTN imposes both bandwidth utilization costs on the communication links and computational costs at the nodes. In addition, there may be certain limitations regarding how much CPU, storage, energy, and so on can be devoted to security, and the amount of computation costs will undoubtedly depend on the underlying algorithms and their associated parameters.
- Naming—DTN naming is a hard open issue to cope with [9]. For instance, how names are to be used in routing, and the ways this will be mapped to the underlying routing of each convergence layer network, remains unclear. A properly constructed naming system can aid in simplifying both routing and security. That is, for security and resource allocation reasons, one would overwhelmingly prefer to be able to uniquely identify a source as well as to determine which group or groups this source may belong to.
7. Conclusions & Future Research
Author Contributions
Conflicts of Interest
Abbreviations
| DTNs | Delay Toleran Networks |
| BP | Bundle Protocol |
| PKI | Public Key Infrastructure |
| IBC | Identity Based Cryptography |
| PKC | Public-Key Cryptography |
| PKG | Private Key Generator |
| CA | Certificate Authority |
| IPN | InterPlanetary Networking |
| BSP | Bundle Security Protocol |
| BAB | Bundle Authentication Block |
| PIB | Payload Integrity Block |
| PCB | Payload Confidentiality Block |
| GCM | Galois Counter Mode |
| HIBC | Hierarchical Identity Based Cryptography |
| OppNets | Opportunistic Networks |
| DKE | Distributed Key Establishment |
| CRL | Certificate Revocation List |
| SKC | Secret Key Crypography |
| WoT | Web of Trust |
| DVD | Dynamic Virtual Digraph |
| BSP | Bundle Security Protocol |
| BP | Bundle Protocol |
| SOK | Sakai-Ohgishi-Kasahara |
| LCF | Leverage of Common Friends |
| CPK | Combined Public Key |
| ECC | Elliptic Curves Cryptography |
| PGP | Pretty Good Privacy |
| HMP | Horsters-Michels-Petersen |
| ESKTS | Efficient and Scalable Key Transport Scheme |
| DSC-KM | Digital Signature Chains Key Management Scheme |
| FS | Forward secrecy |
| BS | Backward secrecy |
| CF | Collusion freedom |
| KI | Key independence |
| LKH | Logical Key Hierarchy |
| CRT | Chinese Remainder Theorem |
| AGKM | Autonomic Group Key Management |
| OMPK | One-encryption-Key Multi-decryption-Key |
| ONE | Opportunistic Networking Environment |
| DS | Distributed Signing |
| ESB | Extension Security Block |
| ASB | Abstract Security Block |
| CCSDS | Consultative Committee for Space Data Systems |
| SBSP | Streamlined Bundle Security Protocol |
| BIBE | Bundle-in-Bundle encapsulation |
| BPSec | Bundle Protocol Security Specification |
| TTP | Trusted Third Party |
| KDC | Key Distribution Center |
References
- Wu, B.; Wu, J.; Cardei, M. A Survey of Key Management in Mobile Ad Hoc Networks. In Handbook of Research on Wireless Security; IGI Global: Hershey, PA, USA, 2010. [Google Scholar]
- Menesidou, S.; Vardalis, D.; Katos, V. Automated key exchange protocol evaluation in delay tolerant networks. Comput. Secur. 2016, 59, 1–8. [Google Scholar] [CrossRef]
- Cerf, V.; Burleigh, S.; Hooke, V.; Torgerson, L.; Durst, R.; Scott, K.; Fall, K.; Weiss, H. Delay-Tolerant Networking Architecture; Rfc4838; DTN Research Group: New York, NY, USA, 2007. [Google Scholar]
- Scott, K.; Burleigh, S. Bundle Protocol Specification; Rfc5050; DTN Research Group: New York, NY, USA, 2007. [Google Scholar]
- Warthman, F. Delay-Tolerant Networks (DTNs): A Tutorial; Technical Report; DTNs: Los Angeles, CA, USA, 2003. [Google Scholar]
- Adams, C.; Lloyd, S. Understanding PKI: Concepts, Standards, and Deployment Considerations, 2nd ed.; Addison-Wesley Longman Publishing Co., Inc.: Boston, MA, USA, 2002. [Google Scholar]
- Shamir, A. Identity-based Cryptosystems and Signature Schemes. In Proceedings of CRYPTO 84 on Advances in Cryptology; Springer: New York, NY, USA, 1985; pp. 47–53. [Google Scholar]
- Law, Y.W.; Corin, R.; Etalle, S.; Hartel, P.H. A Formally Verified Decentralized Key Management Architecture for Wireless Sensor Networks. In Proceedings of the Personal Wireless Communications (PWC 2003), Venice, Italy, 23–25 September 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 27–39. [Google Scholar]
- Ivancic, W. Security analysis of DTN architecture and Bundle Protocol Specification for space-based networks. In Proceedings of the Aerospace Conference, Big Sky, MT, USA, 6–13 March 2010; pp. 6–13. [Google Scholar]
- Zamani, A.; Zubair, S. Secure and Efficient Key Management Scheme in MANETs. OSR J. Comput. Eng. 2014, 16, 146–158. [Google Scholar]
- Fall, K. A delay-tolerant network architecture for challenged internets. In Proceedings of the ACM SIGCOMM 2003 Conference on Applications Technologies, Architectures, and Protocols for Computer Communication, Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar]
- Kate, A.; Zaverucha, G.; Hengartner, U. Anonymity and security in delay tolerant networks. In Proceedings of the Securecomm 2007, Nice, France, 17–21 September 2007; pp. 504–513. [Google Scholar]
- Ochiai, H.; Ishizuka, H.; Kawakami, Y.; Esaki, H. A DTN-Based Sensor Data Gathering for Agricultural Applications. IEEE Sens. J. 2011, 11, 2861–2868. [Google Scholar] [CrossRef]
- Mashhadi, A.; Ben Mokhtar, S.; Capra, L. Habit: Leveraging human mobility and social network for efficient content dissemination in Delay Tolerant Networks. In Proceedings of the 2009 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks & Workshops, Kos, Greece, 15–19 June 2009; pp. 1–6. [Google Scholar]
- Burgess, J.; Gallagher, B.; Jensen, D.; Levine, B. MaxProp: Routing for Vehicle-Based Disruption-Tolerant Networks. In Proceedings of the INFOCOM 2006—25th IEEE International Conference on Computer Communications, Barcelona, Spain, 23–29 April 2006; pp. 1–11. [Google Scholar]
- Caini, C.; Cruickshank, H.; Farrell, S.; Marchese, M. Delay- and Disruption-Tolerant Networking (DTN): An Alternative Solution for Future Satellite Networking Applications. Proc. IEEE 2011, 99, 1980–1997. [Google Scholar] [CrossRef]
- Chitre, M.; Shahabudeen, S.; Freitag, L.; Stojanovic, M. Recent advances in underwater acoustic communications and networking. In Proceedings of the OCEANS 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 1–10. [Google Scholar]
- Husni, E. Rural Internet service system based on Delay Tolerant Network (DTN) using train system. In Proceedings of the 2011 International Conference on Electrical Engineering and Informatics, Bandung, Indonesia, 17–19 July 2011; pp. 1–5. [Google Scholar]
- Voyiatzis, A. A Survey of Delay- and Disruption-Tolerant Networking Applications. J. Internet Eng. 2012, 5, 331–344. [Google Scholar]
- Sourceforge: Delay Tolerant Networking. Available online: http://sourceforge.net/projects/dtn/files/DTN2/ (accessed on 7 June 2017).
- Interplanetary Overlay Network DTN (ION-DTN). Available online: http://sourceforge.net/projects/ion-dtn/ (accessed on 7 June 2017).
- IBR-DTN. Available online: https://www.ibr.cs.tu-bs.de/projects/ibr-dtn/ (accessed on 7 June 2017).
- DTN-Bytewalla. Available online: https://sourceforge.net/projects/bytewalla/ (accessed on 7 June 2017).
- Seth, A.; Keshav, S. Practical Security for Disconnected Nodes. In Proceedings of the First International Conference on Secure Network Protocols, Boston, MA, USA, 6 November 2005; IEEE Computer Society: Washington, DC, USA, 2005; pp. 31–36. [Google Scholar]
- Asokan, N.; Kostiainen, K.; Ginzboorg, P.; Ott, J.; Luo, C. Applicability of Identity-based Cryptography for Disruption-tolerant Networking. In Proceedings of the 1st International MobiSys Workshop on Mobile Opportunistic Networking, San Juan, PR, USA, 11 June 2007; ACM: New York, NY, USA, 2007; pp. 52–56. [Google Scholar]
- Patra, R.; Surana, S.; Nedevschi, S. Hierarchical identity based cryptography for end-to-end security in DTNs. In Proceedings of the 2008 4th International Conference on Intelligent Computer Communication and Processing, Cluj-Napoca, Romania, 28–30 August 2008; pp. 223–230. [Google Scholar]
- Wood, L.; Eddy, W.; Holiday, P. A bundle of problems. In Proceedings of the Aerospace conference 2009, Big Sky, MT, USA, 7–14 March 2009; pp. 1–14. [Google Scholar]
- Farrell, S.; Symington, S.; Weiss, H.; Lovell, P. Delay-Tolerant Networking Security Overview; Draft-Irtf-Dtnrg-Sec-Overview-06, Expires: September 2009; DTN Research Group: New York, NY, USA, 2009. [Google Scholar]
- El Defrawy, K.; Solis, J.; Tsudik, G. Leveraging Social Contacts for Message Confidentiality in Delay Tolerant Networks. In Proceedings of the 2009 33rd Annual IEEE International Computer Software and Applications Conference, Seattle, WA, USA, 20–24 July 2009; Volume 1, pp. 271–279. [Google Scholar]
- Shikfa, A.; Önen, M.; Molva, R. Local Key Management in Opportunistic Networks. Int. J. Commun. Netw. Distrib. Syst. 2012, 9, 97–116. [Google Scholar] [CrossRef]
- Du, J.; Kranakis, E.; Nayak, A. Distributed Key Establishment in Disruption Tolerant Location Based Social Wireless Sensor and Actor Network. In Proceedings of the 2011 Ninth Annual Communication Networks and Services Research Conference, Ottawa, ON, Canada, 2–5 May 2011; IEEE Computer Society: Washington, DC, USA, 2011; pp. 109–116. [Google Scholar]
- Xie, Y.; Wang, G. Practical distributed secret key generation for delay tolerant networks. Concurr. Comput. Pract. Exp. 2013, 25, 2067–2079. [Google Scholar] [CrossRef]
- Djamaludin, C.; Foo, E.; Corke, P. Establishing initial trust in autonomous Delay Tolerant Networks without centralised PKI. Comput. Secur. 2013, 39, 299–314. [Google Scholar] [CrossRef]
- Jia, Z.; Lin, X.; Tan, S.H.; Li, L.; Yang, Y. Public Key Distribution Scheme for Delay Tolerant Networks Based on Two-channel Cryptography. J. Netw. Comput. Appl. 2012, 35, 905–913. [Google Scholar] [CrossRef]
- Lv, X.; Mu, Y.; Li, H. Non-Interactive Key Establishment for Bundle Security Protocol of Space DTNs. IEEE Trans. Inf. Forensics Secur. 2014, 9, 5–13. [Google Scholar] [CrossRef]
- Jadhav, C.; Dhainje, B.; Pradeep, K. Secure Key Establishment for Bundle Security Protocol of Space DTNs in Noninteractive manner. Int. J. Comput. Sci. Inf. Technol. 2015, 6, 944–946. [Google Scholar]
- Mukundhan, E.; Veeramani, M. Bundle Security Protocol of Space DTNs Using Cryptographic Algorithm. Int. J. Comput. Tech. 2015, 2, 51–54. [Google Scholar]
- Mashatan, A.; Stinson, D.R. Practical Unconditionally Secure Two-channel Message Authentication. Des. Codes Cryptogr. 2010, 55, 169–188. [Google Scholar] [CrossRef]
- Symington, S.; Farrell, S.; Weiss, H.; Lovell, P. Bundle Security Protocol Specification; Rfc6257; DTN Research Group: New York, NY, USA, 2011. [Google Scholar]
- Ahmad, N.; Cruickshank, H.; Sun, Z. ID Based Cryptography and Anonymity in Delay/Disruption Tolerant Networks. LNICST 2010, 43, 265–275. [Google Scholar]
- Van Besien, W. Dynamic, Non-interactive Key Management for the Bundle Protocol. In Proceedings of the 5th ACM Workshop on Challenged Networks, Chicago, IL, USA, 20–24 September 2010; ACM: New York, NY, USA, 2010; pp. 75–78. [Google Scholar]
- Ding, Y.; Zhou, X.; Cheng, Z.; Zeng, W. Efficient Authentication and Key Agreement Protocol with Anonymity for Delay Tolerant Networks. Wirel. Pers. Commun. 2013, 70, 1473–1485. [Google Scholar] [CrossRef]
- Pentland, A.; Fletcher, R.; Hasson, A. DakNet: Rethinking connectivity in developing nations. Computer 2004, 37, 78–83. [Google Scholar] [CrossRef]
- Le, Z.; Vakde, G.; Wright, M. PEON: Privacy-enhanced opportunistic networks with applications in assistive environments. In Proceedings of the 2nd International Conference on PErvsive Technologies Related to Assistive Environments, Corfu, Greece, 09–13 June 2009; ACM Press: New York, NY, USA, 2009; pp. 1–8. [Google Scholar]
- Bhutta, N.; Ansa, G.; Johnson, E.; Ahmad, N.; Alsiyabi, M.; Cruickshank, H. Security analysis for Delay/Disruption Tolerant satellite and sensor networks. In Proceedings of the 2009 International Workshop on Satellite and Space Communications (IWSSC), Siena, Italy, 9–11 September 2009; pp. 385–389. [Google Scholar]
- Menesidou, S.A.; Katos, V. Authenticated Key Exchange (AKE) in Delay Tolerant Networks. In Proceedings of the 27th IFIP International Information Security and Privacy Conference, Crete, Greece, 4–6 June 2012; Gritzalis, D., Furnell, S., Theoharidou, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 376, pp. 49–60. [Google Scholar]
- Johnson, E.; Cruickshank, H.; Sun, Z. Providing Authentication in Delay/Disruption Tolerant Networking (DTN) Environment. In Personal Satellite Services; Pillai, P., Shorey, R., Ferro, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Bhutta, N.; Cruickshank, H.; Sun, Z. An Efficient, Scalable Key Transport Scheme (ESKTS) for Delay/Disruption Tolerant Networks. Wirel. Netw. 2014, 20, 1597–1609. [Google Scholar] [CrossRef]
- Rajan, G.; Cho, G. Applying a Security Architecture with Key Management Framework to the Delay/Disruption Tolerant Networks. Int. J. Secur. Its Appl. 2015, 9, 327–336. [Google Scholar] [CrossRef]
- Andrade, D.D.; Albini, L.C.P. Fully Distributed Public Key Management through Digital Signature Chains for Delay and Disrupt Tolerant Networks. In Proceedings of the 2016 IEEE 13th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Brasilia, Brazil, 10–13 October 2016; pp. 316–324. [Google Scholar]
- Gupta, M. Group Key Exchange Management in Delay Tolerant Network. Int. J. Comput. Appl. 2016, 144, 16–19. [Google Scholar] [CrossRef]
- Edelman, P.; Donahoo, M.; Sturgill, D. Secure group communications for Delay-Tolerant Networks. In Proceedings of the 2010 International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 8–11 Novemebr 2010; pp. 1–8. [Google Scholar]
- Xu, G.; Chen, X.; Du, X. Chinese Remainder Theorem based DTN group key management. In Proceedings of the 2012 IEEE 14th International Conference on Communication Technology (ICCT), Chengdu, China, 9–11 November 2012; pp. 779–783. [Google Scholar]
- Zhou, J.; Song, M.; Song, J.; Zhou, X.; Sun, L. Autonomic Group Key Management in Deep Space DTN. Wirel. Pers. Commun. 2014, 77, 269–287. [Google Scholar] [CrossRef]
- Barskar, R.; Chawla, M. A Survey on Efficient Group Key Management Schemes in Wireless Network. Indian J. Sci. Technol. 2016, 9. [Google Scholar] [CrossRef]
- Bhutta, M.; Cruickshank, H.; Sun, Z. Public-key infrastructure validation and revocation mechanism suitable for delay/disruption tolerant networks. IET Inf. Secur. 2016, 11, 16–22. [Google Scholar] [CrossRef]
- Djamaludin, C.; Foo, E.; Camtepe, S.; Corke, P. Revocation and update of trust in autonomous delay tolerant networks. Comput. Secur. 2016, 60, 15–36. [Google Scholar] [CrossRef]
- Farrell, S. DTN Key Management Requirements; Draft-Farrell-Dtnrg-Km-00, Expires: December 2007; DTN Research Group: New York, NY, USA, 2007. [Google Scholar]
- Birrane, S. Streamlined Bundle Security Protocol Specification; Draft-Irtf-Dtnrg-Sbsp-01, Expires: November 2014; DTN Research Group: New York, NY, USA, 2014. [Google Scholar]
- CCSDS. Space Mission Key Management Concept; Report, CCSDS 350.6-G-1, Green Book, Issue 1; CCSDS: Darmstadt, Germany, 2011. [Google Scholar]
- Templin, F. Delay Tolerant Networking Security Key Management—Problem Statement; Draft-Templin-Dtnskmps-00, Expires: September 2014; Network Working Group: Ottawa, ON, Canada, 2014. [Google Scholar]
- Templin, F. DTN Security Key Management—Requirements and Design; Draft-Templin-Dtnskmreq-00, Expires: August 2015; Network Working Group: Ottawa, ON, Canada, 2015. [Google Scholar]
- Viswanathan, K.; Templin, F. Architecture for a Delay-and-Disruption Tolerant Public-Key Distribution Network (PKDN); Draft-Viswanathan-Dtnwg-Pkdn-00, Expires: February 2016; Network Working Group: Ottawa, ON, Canada, 2015. [Google Scholar]
- Birrane, E.; McKeever, K. Bundle Protocol Security Specification; Draft-Ietf-Dtn-Bpsec-04, JHU/APL; Network Working Group: Ottawa, ON, Canada, 2017. [Google Scholar]
- Farrell, S.; Cahill, V. Security considerations in space and delay tolerant networks. In Proceedings of the Second IEEE International Conference on Space Mission Challenges for Information Technology, Madrid, Spain, 27–29 September 2006; pp. 8–38. [Google Scholar]
- Fumy, W. Key Management Techniques. State of the Art in Applied Cryptography, Course on Computer Security and Industrial Cryptography—Revised Lectures; Springer: London, UK, 1998; pp. 142–162. [Google Scholar]
- Challal, Y.; Seba, H. Group Key Management Protocols: A Novel Taxonomy. Int. J. Comput. Electr. Autom. Control Inf. Eng. 2008, 2, 105–118. [Google Scholar]
| Scheme | Crypto-Graphy | Methods/Protocols/Schemes | DTN Network | Evaluation Method | Architecture | Year |
|---|---|---|---|---|---|---|
| Seth, A., and Keshav, S. [24] | PKC/SKC | HIBC, Gentry-Silverberg HIBC (HIBE and HIBS),authorized distribution | Rural Area DTN | N/A | Centralised | 2005 |
| Asokan, N., Kostiainen, K., Ginzboorg, P., Ott, J.and Luo, C. [25] | PKC/SKC | IBC, cellular authentication infrastructure | Rural Area DTN | Theoretical | Centralised | 2007 |
| Patra, R., Surana, S., and Nedevschi, S. [26] | PKC | HIBC | Network-agnostic | N/A | Centralised | 2008 |
| El Defrawy, K., Solis, J., and Tsudik, G. [29] | PKC | social contact information | Rural Area DTN | Simulation | Decentralised/Distributed | 2009 |
| Du, J. and Kranakis, E., and Nayak, A. [31] | PKC/SKC | key pre-distribution, neighbor distributed key establishment (DKE) | Sensor and Actor Network DTN(DTLBS-WSAN) | Theoretical, Simulation | Decentralised/Distributed | 2011 |
| Shikfa, A., Önen, M., and Molva, R. [30] | PKC | self-organised, pseudonym certificates, encapsulated signatures | Opportunistic Networks | Theoretical | Decentralised/Distributed | 2012 |
| Jia, Z., Lin, X., Tan, S., Li, L., and Yang, Y. [34] | PKC | two-channel cryptography, dynamic virtual digraph (DVD) | pocket DTN | Simulation | Decentralised/Distributed | 2012 |
| Xie, Y., and Wang, G. [32] | SKC | distributed secret key generation system, self-certified identity | Network-agnostic | Simulation | Decentralised/Distributed | 2013 |
| Djamaludin, C.I., Foo, E., and Corke, P. [33] | PKC | PGP, Leverage of Common Friends (LCF) method | Network-agnostic | Simulation | Decentralised/Distributed | 2013 |
| Lv, X. and Mu, Y. and Li, H. [35] | PKC | two-channel cryptography, time evolving model | Space DTN | Simulation | Decentralised/Distributed | 2014 |
| Jadhav, C., Dhainje, P., and Pradeep, D. [36] | PKC | two-channel cryptography, time evolving model | Space DTN | N/A | Decentralised/Distributed | 2015 |
| Mukundhan E. and Veeramani, M.E. [37] | PKC | two-channel cryptography, time evolving mode | Space DTN | N/A | Decentralised/Distributed | 2015 |
| Scheme | Crypto-Graphy | Key Manage-Ment Area | Methods/Protocols/Schemes | DTN Network | Evaluation Method | Architecture | Year |
|---|---|---|---|---|---|---|---|
| Kate, A., Zaverucha, G., and Hengartner, U. [12] | PKC/SKC | key agreement | IBC, Sakai-Ohgishi-Kasahara (SOK) key agreementscheme and HIBC (HIBE and HIBS) | Rural Area DTN | Simulation | Centralised | 2007 |
| Van Besien, W.L. [41] | PKC/SKC | key pre-distribution, key distribution | IBC bilinear maps over elliptic curves | Network-agnostic | N/A | Centralised | 2010 |
| Ahmad, N., Cruickshank, H., and Sun, Z. [40] | PKC/SKC | key agreement | IBC | Rural Area DTN | N/A | Centralised | 2010 |
| Ding, Y., Zhou, X., Cheng, Z., and Zeng, W. [42] | PKC/SKC | key agreement | CPK (Combined Public Key), AKP protocol, ECC | Network-agnostic | Theoretical | Centralised | 2013 |
| Scheme | Crypto-Graphy | Key Manage-Ment Area | Methods/ Protocols/Schemes | DTN Network | Evaluation Method | Architecture | Year |
|---|---|---|---|---|---|---|---|
| Bhutta, M., Ansa, G. and Johnson, E., Ahmad, N.,Alsiyabi, M. and Cruickshank, H. [45] | PKC/SKC | key predistribution, manual keys,key establishment | PKI, proxy certificates | Satellite and Sensor DTN | N/A | Centralised | 2009 |
| Menesidou, S.A., and Katos, V. [46] | PKC/SKC | key agreement | PKI, HMP protocol | Space DTN | N/A | Centralised | 2012 |
| Johnson, E., Cruickshank, H., and Sun, Z. [47] | PKC | key pre-distribution | PKI | Satellite DTN | Simulation | Centralised | 2013 |
| Bhutta, M., Cruickshank HS., and Sun Z. [48] | PKC/SKC | key distribution | PKI, proxy signatures, Symmetric Key Transport,Efficient, Scalable Key Transport Scheme (ESKTS) | Network-agnostic | Simulation | Centralised | 2014 |
| Rajan, G., and Cho, G. [49] | PKC/SKC | key distribution | PKI | Network-agnostic | N/A | Centralised | 2015 |
| Andrade, D., and Albini, C. [50] | PKC | key establishment | PGP, DSC-KM | Network-agnostic | Simulation | Decentralised/Distributed | 2016 |
| Scheme | Crypto- Graphy | Security Properties | Methods/Protocols/Schemes | DTN Network | Evaluation Method | User Join Message Cost | User Leave Message Cost | Architecture | Year |
|---|---|---|---|---|---|---|---|---|---|
| Edelman, P., Donahoo, M., and Sturgill, D. [52] | PKC | FS, BS, KI, CF | Group Membership Tree (GMT), Logical Key Hierarchy (LKH), key graphs | Network-agnostic | Simulation | O (log n) | O (log n) | Centralised | 2010 |
| Xu, Gl, Chen, X., and Du, X. [53] | SKC | FS (one-to-manyscenario),BS, CF | XOR, Chinese Remainder Theorem, Chinese Remainder DTN Group Key(CRDGK) scheme, time-based group key management scheme | Network-agnostic | Simulation | O (1) | O (1) | Centralised | 2012 |
| Zhou, J., Song, M.m Song. J., Zhou, X.,and Sun, L. [54] | PKC | FS, BS, KI, CF | autonomic group key management (AGKM) scheme, Logical KeyHierarchy (LKH), one-encryption-key multi-decryption-key key protocol | Space DTN | Theoretical Proof, Simulation | O (log n) | O (1) | Centralised | 2014 |
| Gupta [51] | PKC | FS, BS, CF | Modified version of Chinese Remainder Theorem | Network-agnostic | Theoretical Proof, Simulation | O (1) | O (1) | Centralised | 2016 |
| Scheme | Crypto-Graphy | Methods/Protocols/Schemes | DTN Network | Evaluation Method | Architecture | Year |
|---|---|---|---|---|---|---|
| Djamaludin, C.I., Foo, E.,Camtepe, S. and Corke, P. [57] | PKC | DS revocation scheme, PGP,△CRL | Large scale DTNs(e.g., MANET, VANET) | Simulation | Decentralised/Distributed | 2016 |
| Bhutta, M. and Sun, Z. [56] | PKC | PKI, Hash Table, CRL | Network-agnostic | Simulation | Centralised | 2017 |
| Title | Naming Conventions | Released Date | Expiration Date |
|---|---|---|---|
| DTN Key Management Requirements [58] | draft-farrell-dtnrg-km-00 | June 2007 | December 2007 |
| Delay-Tolerant Networking Security Overview [28] | draft-irtf-dtnrg-sec-overview-06 | March 2009 | September 2009 |
| Bundle Security Protocol Specification [39] | RFC6257 | May 2011 | - |
| Space Mission Key Management Concept [60] | CCSDS 350.6-G-1 | November 2011 | - |
| Delay Tolerant Networking Security Key Management - Problem Statement [61] | draft-templin-dtnskmps-00 | March 2014 | September 2014 |
| Streamlined Bundle Security Protocol Specification [59] | draft-irtf-dtnrg-sbsp-01 | May 2014 | November 2014 |
| DTN Security Key Management - Requirements and Design [62] | draft-templin-dtnskmreq-00 | February 2015 | August 2015 |
| Architecture for a Delay-and-Disruption Tolerant Public-Key Distribution Network (PKDN) [63] | draft-viswanathan-dtnwg-pkdn-00 | August 2015 | February 2016 |
| Bundle Protocol Security Specification [64] | draft-ietf-dtn-bpsec-04 | March 2017 | September 2017 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Menesidou, S.A.; Katos, V.; Kambourakis, G. Cryptographic Key Management in Delay Tolerant Networks: A Survey. Future Internet 2017, 9, 26. https://doi.org/10.3390/fi9030026
Menesidou SA, Katos V, Kambourakis G. Cryptographic Key Management in Delay Tolerant Networks: A Survey. Future Internet. 2017; 9(3):26. https://doi.org/10.3390/fi9030026
Chicago/Turabian StyleMenesidou, Sofia Anna, Vasilios Katos, and Georgios Kambourakis. 2017. "Cryptographic Key Management in Delay Tolerant Networks: A Survey" Future Internet 9, no. 3: 26. https://doi.org/10.3390/fi9030026
APA StyleMenesidou, S. A., Katos, V., & Kambourakis, G. (2017). Cryptographic Key Management in Delay Tolerant Networks: A Survey. Future Internet, 9(3), 26. https://doi.org/10.3390/fi9030026








