Practical Attacks on Mobile Cellular Networks and Possible Countermeasures
Abstract
:1. Introduction
2. Mobile Cellular Network Basics
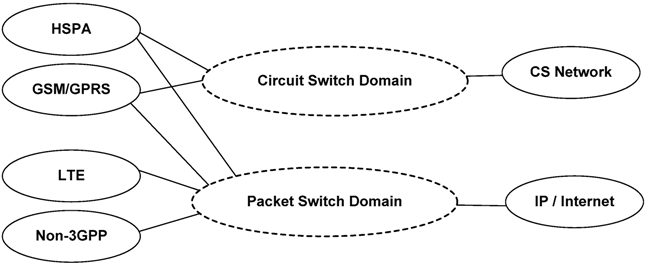
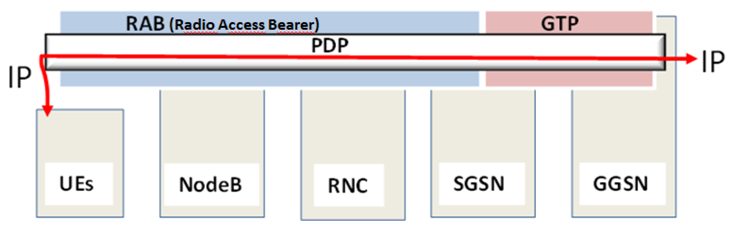
2.1. 3G Mobility Management for Data Communication
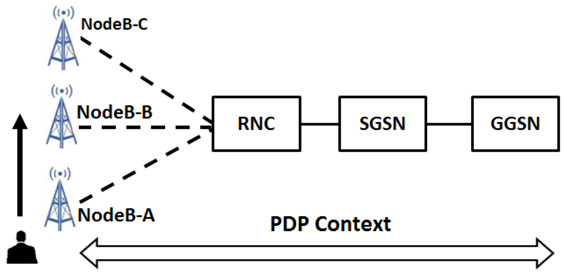
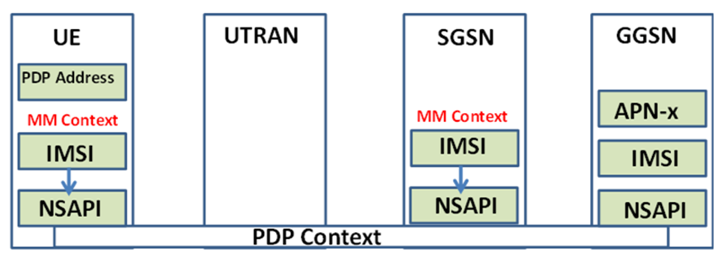

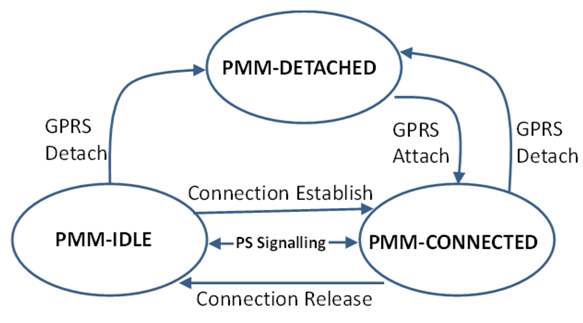
2.2. Paging
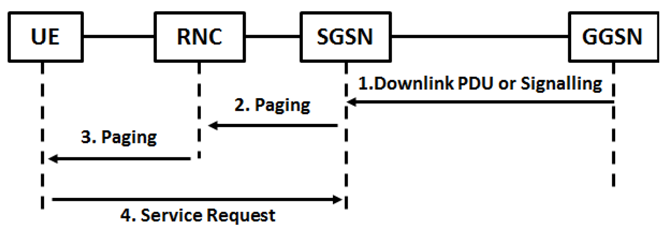
- The GGSN sends a packet, destined for the UE in PPM-idle state, to the SGSN;
- Upon getting packets from the GGSN, the SGSN sends a Paging Request message that includes the IMSI number, RA, etc., to the RNC belonging to the RA where the UE is located;
- The RNC passes the paging requests to the UE;
- Upon getting the paging request message, the UE’s state changes from PMM-idle to PMM-connected. Also, the UE sends paging request packets back to the SGSN.
3. Threats on Cellular Networks
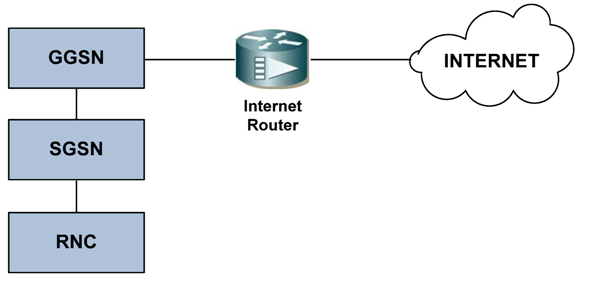
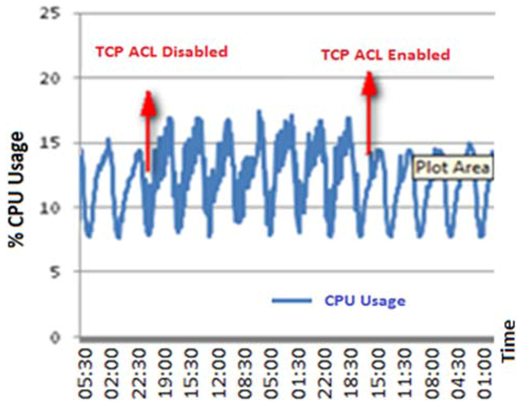
4. Measuring the Effect of the DoS Attack on 3G Networks
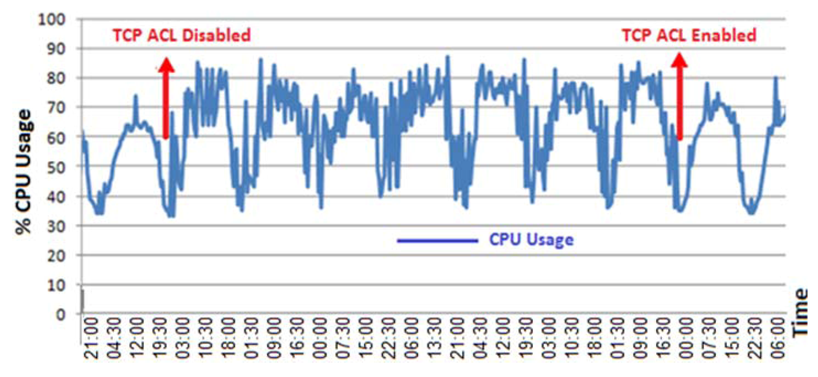
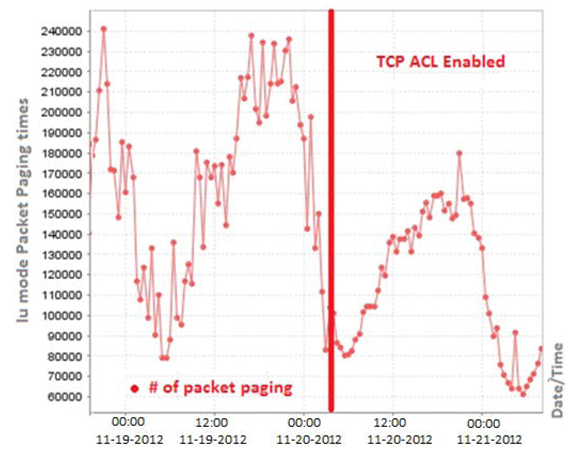
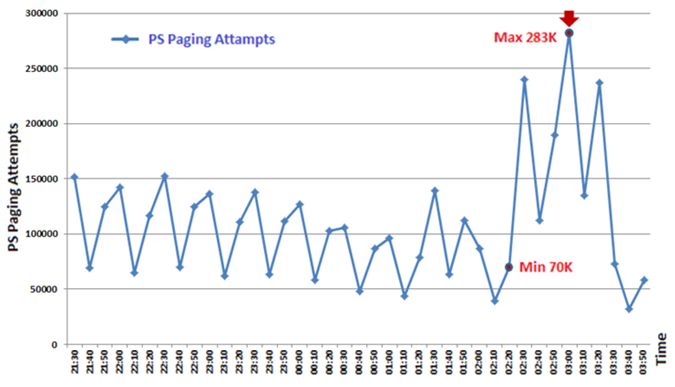
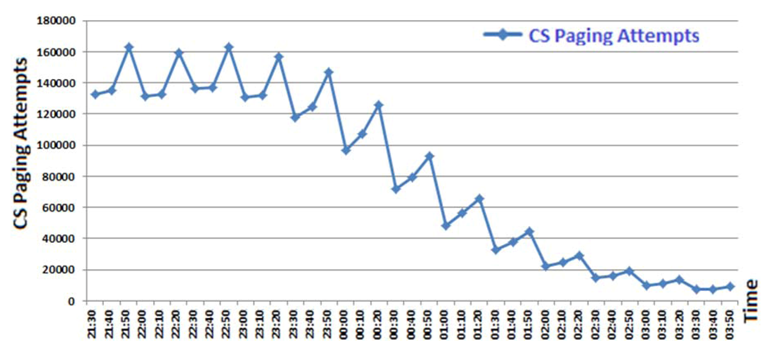
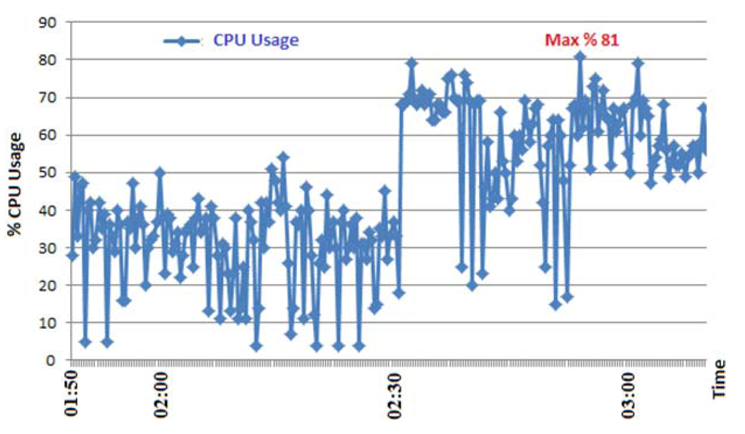
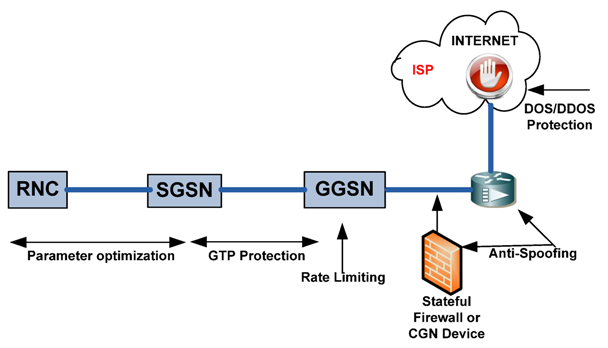
5. Countermeasures against 3/4G Security Threats
- Stateful IP packet filtering could be applied on the Internet border of the mobile network. This task could be achieved by an Internet router with firewall feature with both TCP and UDP stateful packet filtering functionality. A second option is to use a firewall device between the GGSN and the Internet router. The packet filtering device must be stateful for TCP and UDP, and drop all unnecessary traffic from the Internet to the mobile operator or to the customers. The drawback of the stateful firewall solution is the limitations in a firewall’s session state table;
- Configuration should be done against IP address spoofing [29] on the IP packet filter device or the Internet router;
- The flooding and the DoS/DDoS type of attacks are the most dangerous and effective ways to destroy target devices. They could be performed individually or organized, e.g., using a botnet [30,31]. A high number of connection requests could put most stateful firewalls out of service due to limitations in their state tables. Therefore, a DoS/DDoS protection service or product should be used against attacks coming from the Internet. Generally, it is recommended that DDoS protection is placed in the ISP’s side [32];
- Mobile to mobile traffic could cause spreading of worms and viruses. This can be dangerous for both mobile devices and mobile operators, especially when worms/viruses act in an organized manner forming a botnet. Therefore, mobile to mobile traffic should be filtered by the GGSN or an IP filtering device;
- Malware [33] or botnet members can generate flooding traffic to their victims such as mobile devices or operators, causing service interruptions on core network devices. Hence, rate limiting [34] should be applied to mobile user traffic on the GGSN or an IP packet filtering device should be used to avoid this threat;
- Directerd broadcast [35] traffic must be denied on the GGSN to protect against DDoS attacks;
- RA and LA scope optimization should be done according to the best practices to decrease paging effects;
- Parameter optimization on RNC and SGSN should be done according to the best practices to decrease the PS paging effect;
- Mobile operators could locate the GTP aware firewall products between the SGSN and the GGSN to block attacks coming through the GTP protocol;
- The PS and the CS paging control channels should be isolated to prevent the CS paging from being overloaded by the PS paging channel under attack. Hence, at least voice communication service would not be affected in the case of an attack against the PS paging channel.
| Protections | PROS | CONS |
|---|---|---|
| DDoS Protection on ISP | Effective DDoS protection | Extra cost |
| Stateful Firewall | Effective and flexible IP filtering | Session state table limitations, Point of failure |
| CGN | Blocking unwanted traffic from the Internet | NAT table limitations, Lack of IP filtering, Point of failure |
| GTP Firewall | GTP attack protection | Extra cost, Point of failure |
| Parameter Optimization | No-cost and protection | N/A |
| User Isolation | Preventing organized internal attacks | Unforeseen UE-to-UE communication |
| Rete Limiting | Decreases the effect of attacks | N/A |
6. Conclusions
Acknowledgments
Conflicts of Interest
References
- CBS Interactive Web Page. Japan First Country Where Data Revenues Exceed Voice. Available online: http://www.zdnet.com/japan-first-country-where-data-revenues-exceed-voice-7000011817 (accessed on 28 July 2013).
- Ghosh, A.; Ratasuk, R.; Mondal, B.; Mangalvedhe, N.; Thomas, T. LTE-advanced: Next-generation wireless broadband technology. IEEE Wirel. Commun. 2010, 17, 10–22. [Google Scholar]
- Technology Marketing Corporation Web Page. Mobile Revenue will Double by 2016, but Traffic will Increase Tenfold. Available online: http://www.tmcnet.com/topics/articles/2012/05/16/290655-mobile-revenue-will-double-2016-but-traffic-will.htm (accessed on 28 July 2013).
- Itwire Web Page. Asia Pacific Mobile Data Revenues Tipped to Exceed Voice in 2016. Available online: http://www.itwire.com/your-it-news/mobility/49878-asia-pacific-mobile-data-revenues-tipped-to-exceed-voice-in-2016 (accessed on 28 July 2013).
- Nagy, M.; Kotosová, M. An IP Based Security Threat in Mobile Networks. In Proceedings of the 35th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2012.
- Ricciato, F. Unwanted traffic in 3G networks. ACM SIGCOMM Comput. Commun. Rev. 2006, 36, 53–56. [Google Scholar] [CrossRef]
- Ricciato, F.; Coluccia, A.; D’Alconzo, A. A review of DoS attack models for 3G cellular networks from a system-design perspective. Comput. Commun. 2010, 33, 551–558. [Google Scholar] [CrossRef]
- Serror, J.; Zang, H.; Bolot, J.C. Impact of Paging Channel Overloads or Attacks on a Cellular Network. In Proceedings of the ACM Workshop on Wireless Security (WiSe 06), Los Angeles, CA, USA, 29 September 2006.
- Whitehouse, O.; Murphy, G. Attacks and Counter Measures in 2.5G and 3G Cellular IP Networks; White Paper; Juniper Networks: Sunnyvale, CA, USA, 2004. [Google Scholar]
- Wu, Z.; Zhou, X.; Yang, F. Defending against DoS Attacks on 3G Cellular Networks via Randomization Method. In Proceedings of the 2010 International Conference on Educational and Information Technology (ICEIT 2010), Chongqing, China, 17–19 September 2010.
- Lee, P.P.C.; Bu, T.; Woo, T. On the Detection of Signaling DoS Attacks on 3G Wireless Networks. In Proceedings of the 26th IEEE International Conference on Computer Communications (INFOCOM 2007), Anchorage, AK, USA, 6–12 May 2007.
- Zhao, B.; Chi, C.; Gao, W.; Zhu, S.; Cao, G. A Chain Reaction DoS Attack on 3G Networks: Analysis and Defenses. In Proceedings of the 28th IEEE International Conference on Computer Communications (INFOCOM 2009), Rio de Janeiro, Brazil, 19–25 April 2009.
- Cheng, C.M.; Kung, H.T.; Tan, K.S. Use of Spectral Analysis in Defense against DoS Attacks. In Proceedings of the Global Telecommunications Conference 2002, Taipei, Taiwan, 17–21 November 2002.
- The European Telecommunications Standards Institute (ETSI). Technical Specification: 3GPP TS 25.331, version 8.1.0; ETSI: Valbonne, France, 2008. Available online: http://www.etsi.org/deliver/etsi_ts/125300_125399/125331/08.01.00_60/ts_125331v080100p.pdf (accessed on 28 July 2013).
- Eng, K.Y.; Ali, A.M.; Baradello, C.; Turner, J.; Vlack, D.; Walters, S.M. Packet Switching vs. Circuit Switching in Future Integrated Services Digital Networks. In Proceedings of the 7th IEEE International Conference on Computer Communications; New Orleans, LA, USA: 27–31 March 1988.
- Killalea, T. Recommended Internet Service Provider Security Services and Procedures; BCP 46 and RFC 3013; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2000. [Google Scholar]
- Lyman, C.A. Computer communication standarts. ACM SIGCOMM Comput. Commun. Rev. 1984, 14, 46–52. [Google Scholar] [CrossRef]
- Ericsson Inc, GPRS System Survey. In Student Book; LZT 123 5347 R4A; Ericsson: Stockholm, Sweden, 2005.
- Ozugur, T. Multiobjective Hierarchical Location and Routing Area Optimization in GPRS and UMTS Networks. In Proceedings of the 2002 IEEE International Conference on Communications (ICC 2002), New York, NY, USA, 28 April–2 May 2002.
- Leavitt, N. Mobile phones: The next frontier for hackers? Computer 2005, 38, 20–23. [Google Scholar]
- Becher, M.; Freiling, F.C.; Hoffmann, J.; Holz, T. Mobile Security Catching Up? Revealing the Nuts and Bolts of the Security of Mobile Devices. In Proceedings of the 2011 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 22–25 May 2011.
- Newman, D. Benchmarking Terminology for Firewall Performance; RFC 2647; Internet Engineering Task Force (IETF): Fremont, CA, USA, 1999. [Google Scholar]
- The 3rd Generation Partnership Project (3GPP) Technical Specification Group. In Technical Specification; 23.060 V6.11.0; 3GPP: Valbonne, France, 2005.
- Leavitt, N. Malicious code moves to mobile devices. IEEE Comput. 2000, 33, 16–19. [Google Scholar] [CrossRef]
- Dagon, D. Mobile phones as computing devices: The viruses are coming! IEEE Pervasive Comput. 2004, 3, 11–15. [Google Scholar] [CrossRef]
- Mobile Marketer Web Page. Top Mobile Security Threats for 2013. Available online: http://www.mobilemarketer.com/cms/news/strategy/14518.html (accessed on 28 July 2013).
- Egevang, K.; Francis, P. The IP Network Address Translator (NAT); RFC 1631; Internet Engineering Task Force (IETF): Fremont, CA, USA, 1994. [Google Scholar]
- Jiang, S.; Carpenter, B. An Incremental Carrier-Grade NAT (CGN) for IPv6 Transition; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2011. [Google Scholar]
- Ferguson, P.; Senie, D. Network Ingress Filtering: Defeating Denial of Service Attacks which Employ IP Source Address Spoofing. BCP 38 and RFC 2827; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2000. [Google Scholar]
- Tyagi, A.K.; Aghila, G. A wide scale survey on botnet. Int. J. Comput. Appl. 2011, 34, 9–22. [Google Scholar]
- Sharma, R.K.; Chandel, G.S. Botnet detection and resolution challenges: A survey paper. Int. J. Comput. Inf. Technol. Bioinforma. 2009, 1, 10–15. [Google Scholar]
- Douligeris, C.; Mitrokotsa, A. DDoS attacks and defense mechanisms: Classification and state-of-the-art. Comput. Netw. 2004, 44, 643–666. [Google Scholar] [CrossRef]
- Lawton, G. Is it finally time to worry about mobile malware? IEEE Comput. 2008, 41, 12–14. [Google Scholar] [CrossRef]
- Morrow, C.; Jones, G. Filtering and Rate Limiting Capabilities for IP Network Infrastructure. Available online: https://tools.ietf.org/html/draft-ietf-opsec-filter-caps-09 (accessed on 28 July 2013).
- The European Telecommunications Standards Institute (ETSI). Technical Specification; 3GPP TS 29.060 V9.3.0 (2010-06); ETSI: Valbonne, France. Available online: http://www.etsi.org/deliver/etsi_ts/129000_129099/129060/09.03.00_60/ts_129060v090300p.pdf (accessed on 28 July 2013).
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Oğul, M.; Baktır, S. Practical Attacks on Mobile Cellular Networks and Possible Countermeasures. Future Internet 2013, 5, 474-489. https://doi.org/10.3390/fi5040474
Oğul M, Baktır S. Practical Attacks on Mobile Cellular Networks and Possible Countermeasures. Future Internet. 2013; 5(4):474-489. https://doi.org/10.3390/fi5040474
Chicago/Turabian StyleOğul, Murat, and Selçuk Baktır. 2013. "Practical Attacks on Mobile Cellular Networks and Possible Countermeasures" Future Internet 5, no. 4: 474-489. https://doi.org/10.3390/fi5040474
APA StyleOğul, M., & Baktır, S. (2013). Practical Attacks on Mobile Cellular Networks and Possible Countermeasures. Future Internet, 5(4), 474-489. https://doi.org/10.3390/fi5040474




