A Privacy Preserving Framework for Worker’s Location in Spatial Crowdsourcing Based on Local Differential Privacy
Abstract
1. Introduction
- We propose a new framework that protects the location privacy of workers in SC. In comparison with other solutions, workers’ locations are obfuscated locally with noises in the proposed framework so that our framework does not require the participation of any trusted third parties for data collection and privacy processing, and the workers can customize their privacy requirements.
- We design a task assignment algorithm that assign workers to tasks with obfuscated locations.
- We conduct experiments on real-world datasets which show that the proposed framework has privacy guarantees and modest overhead performance.
2. Related Work
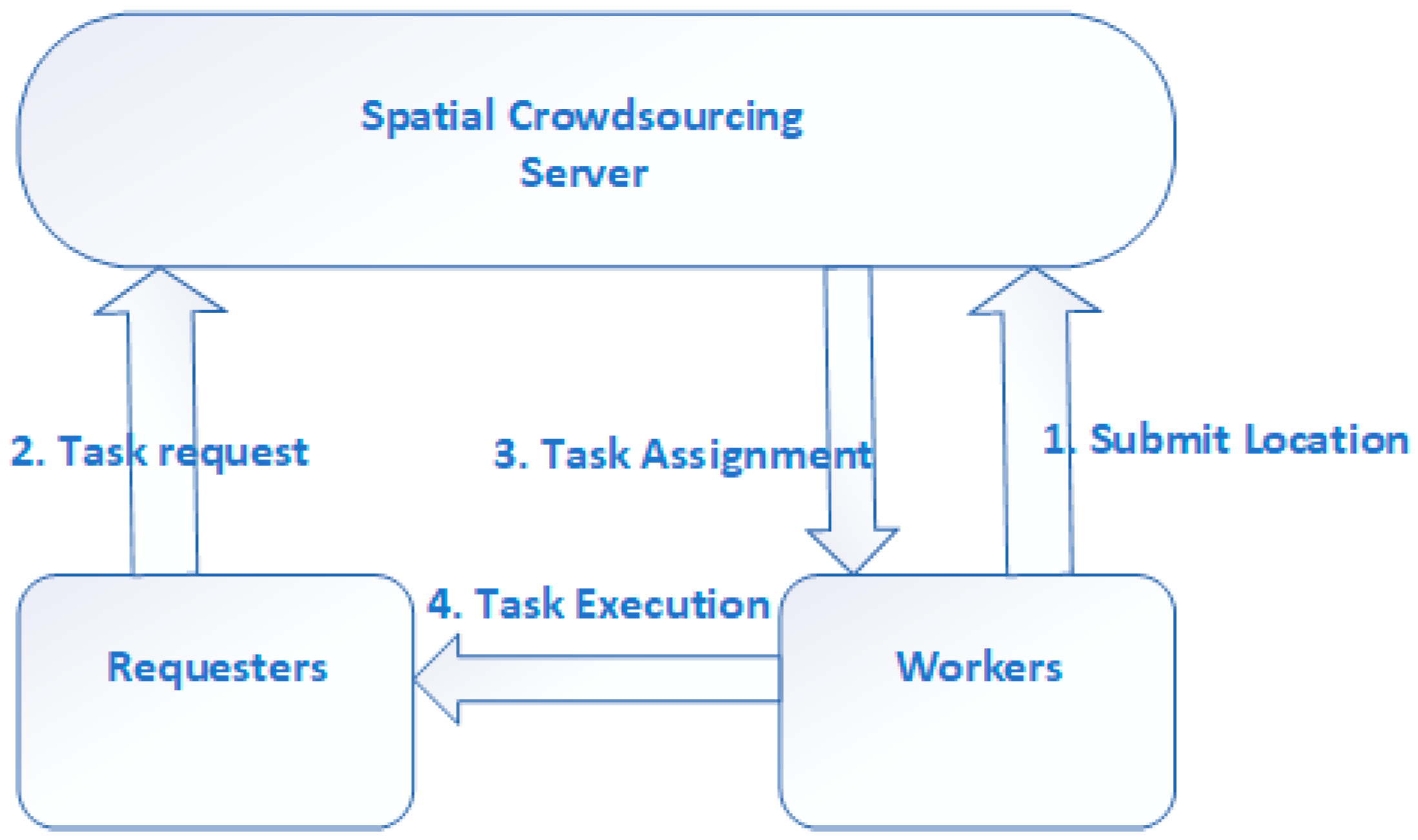
3. Threat Model and Privacy Protection Framework
3.1. Threat Model
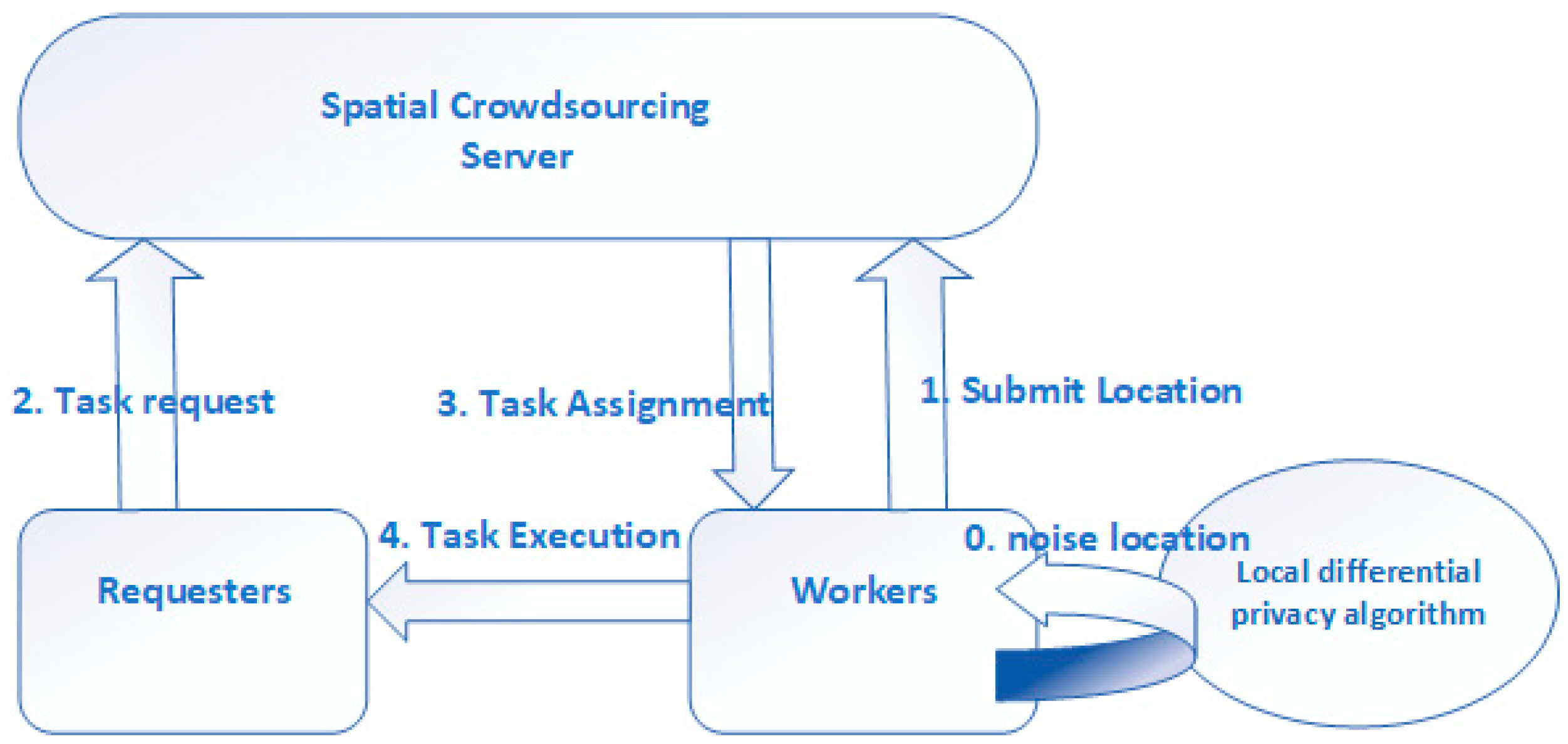
3.2. Privacy Protection Framework
4. Noisy Location with Local Differential Privacy
4.1. Definition Local Differential Privacy on Location (LDPL)
4.2. Achieve Local Differential Privacy on Location
4.2.1. Generating Noise Point
| Algorithm 1 Noisy Point Generate Algorithm |
| Input: privacy budget Output: (r, θ) 01. θ = random [0, 2π) 02. p = random [0,1) 03. r = 04. return (r, θ) |
4.2.2. Remapping Noisy Point to Worker’s Location
| Algorithm 2 Worker’s Noisy Location Generate Algorithm |
| Input: worker’s real location l0 Output: worker’s noisy location l0′ 01. θ = random [0, 2π) 02. p = random [0,1) 03. r = 04. l0′ = l0 + (r * cos (θ), r * sin (θ)) 05. return l0′ |
5. Experimental
5.1. Design Goals and Performance Metrics
5.2. Experimental Methodology
5.2.1. Experimental Data Set
5.2.2. Task Assignment Algorithm
| Algorithm 3 Task assignment algorithm |
| Input: Task t, workers’ dataset, MTD, Output: MR 01. Init MR = {}, U = 0 02. add nearest workers to MR 03. calculate utility U 04. if U > EU, return MR 05. if the radius of MR MTD, return MR 06. go to step 02 |
5.2.3. Evaluation Methodology
5.3. Analysis
5.3.1. Assignment Success Rate
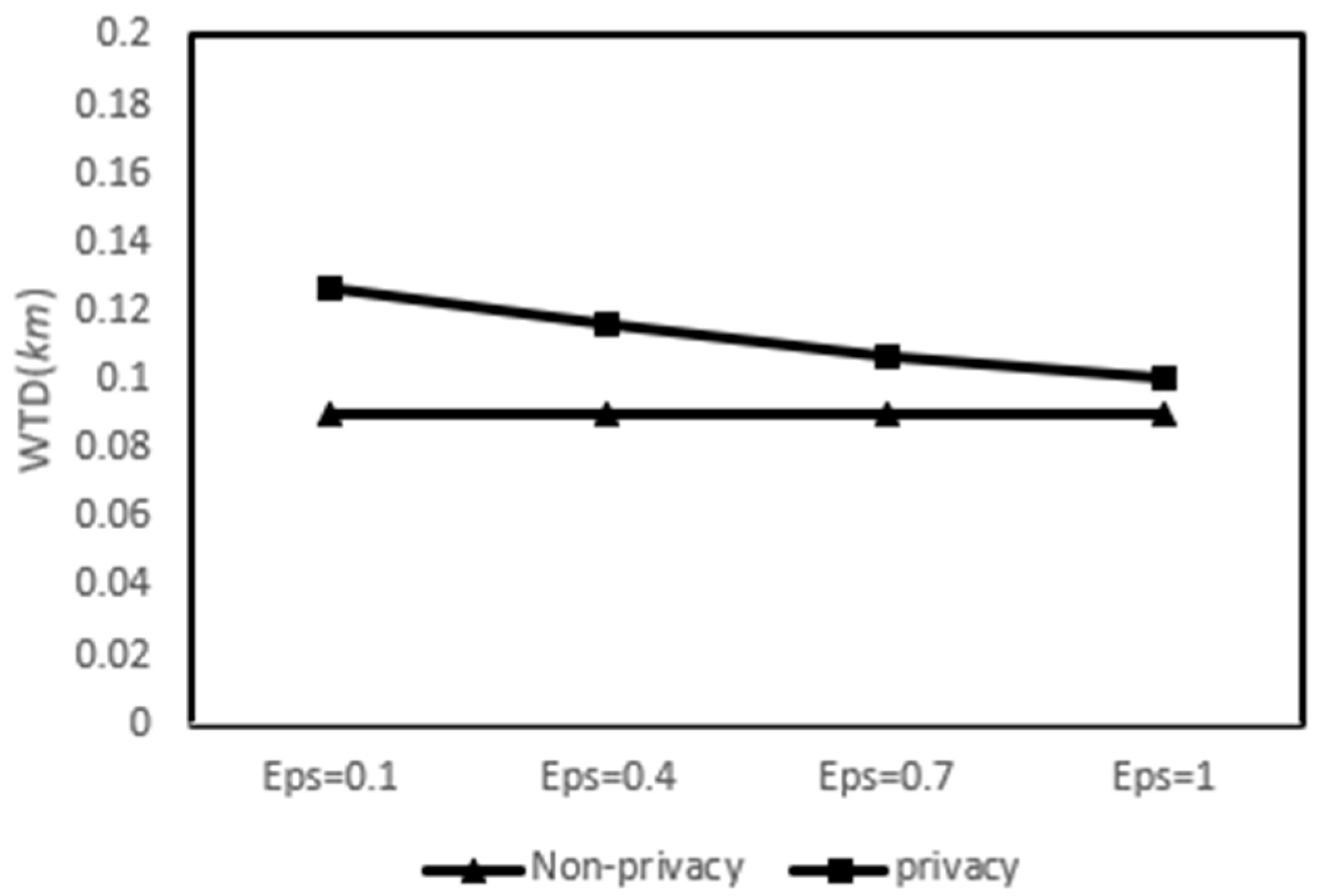
5.3.2. Worker Travel Distance
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kazemi, L.; Shahabi, C. GeoCrowd:enabling query answering with spatial crowdsourcing. In Proceedings of the International Conference on Advances in Geographic Information Systems, Redondo Beach, CA, USA, 6–9 November 2012; pp. 189–198. [Google Scholar]
- Gruteser, M.; Grunwald, D. Anonymous Usage of Location-Based Services Through Spatial and Temporal Cloaking. In Proceedings of the International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 31–42. [Google Scholar]
- Gedik, B.; Liu, L. Location Privacy in Mobile Systems: A Personalized Anonymization Model. In Proceedings of the IEEE International Conference on Distributed Computing Systems, Columbus, OH, USA, 6–10 June 2005; pp. 620–629. [Google Scholar]
- Mokbel, M.F.; Chow, C.Y.; Aref, W.G. The new Casper:query processing for location services without compromising privacy. In Proceedings of the International Conference on Very Large Data Bases, Seoul, Korea, 12–15 September 2006; pp. 763–774. [Google Scholar]
- Bamba, B.; Liu, L.; Pesti, P.; Wang, T. Supporting Anonymous Location Queries in Mobile Environments with PrivacyGrid. In Proceedings of the International Conference on World Wide Web, Beijing, China, 21–25 April 2008; pp. 237–246. [Google Scholar]
- Duckham, M.; Kulik, L. A Formal Model of Obfuscation and Negotiation for Location Privacy; Springer: Berlin/Heidelberg, Germany, 2005; pp. 152–170. [Google Scholar]
- Xue, M.; Kalnis, P.; Pung, H.K. Location Diversity: Enhanced Privacy Protection in Location Based Services. In Proceedings of the International Symposium on Location and Context Awareness, Tokyo, Japan, 7–8 May 2009; pp. 70–87. [Google Scholar]
- Kido, H.; Yanagisawa, Y.; Satoh, T. Protection of Location Privacy using Dummies for Location-based Services. In Proceedings of the International Conference on Data Engineering Workshops, Tokyo, Japan, 3–4 April 2005; p. 1248. [Google Scholar]
- Shankar, P.; Ganapathy, V.; Iftode, L. Privately querying location-based services with SybilQuery. In Proceedings of the 11th International Conference on Ubiquitous Computing, Orlando, FL, USA, 30 September–3 October 2009; pp. 31–40. [Google Scholar]
- Dwork, C. Differential privacy. In Proceedings of the International Colloquium on Automata, Languages, and Programming, Prague, Czech Republic, 9–13 July 2018; pp. 1–12. [Google Scholar]
- To, H.; Ghinita, G.; Fan, L.; Shahabi, C. Differentially Private Location Protection for Worker Datasets in Spatial Crowdsourcing. IEEE Trans. Mobile Comput. 2017, 16, 934–949. [Google Scholar] [CrossRef]
- Duchi, J.C.; Jordan, M.I.; Wainwright, M.J. Local Privacy and Statistical Minimax Rates. In Proceedings of the IEEE Symposium on Foundations of Computer Science, Berkeley, CA, USA, 26–29 October 2013; pp. 429–438. [Google Scholar]
- Kasiviswanathan, S.P.; Lee, H.K.; Nissim, K.; Raskhodnikova, S.; Smith, A. What Can We Learn Privately? In Proceedings of the IEEE Symposium on Foundations of Computer Science, Philadelphia, PA, USA, 25–28 October 2008; pp. 531–540. [Google Scholar]
- Andrés, M.E.; Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Geo-indistinguishability: Differential privacy for location-based systems. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 901–914. [Google Scholar]
- Dwork, C. A Firm Foundation for Private Data Analysis. Commun. ACM 2011, 54, 86–95. [Google Scholar] [CrossRef]
- Dwork, C.; Mcsherry, F.; Nissim, K.; Smith, A. Calibrating Noise to Sensitivity in Private Data Analysis. Lect. Notes Comput. Sci. 2012, 3876, 265–284. [Google Scholar]

| Tasks | Workers | Workers/km2 |
|---|---|---|
| 151,000 | 6100 | 35 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dai, J.; Qiao, K. A Privacy Preserving Framework for Worker’s Location in Spatial Crowdsourcing Based on Local Differential Privacy. Future Internet 2018, 10, 53. https://doi.org/10.3390/fi10060053
Dai J, Qiao K. A Privacy Preserving Framework for Worker’s Location in Spatial Crowdsourcing Based on Local Differential Privacy. Future Internet. 2018; 10(6):53. https://doi.org/10.3390/fi10060053
Chicago/Turabian StyleDai, Jiazhu, and Keke Qiao. 2018. "A Privacy Preserving Framework for Worker’s Location in Spatial Crowdsourcing Based on Local Differential Privacy" Future Internet 10, no. 6: 53. https://doi.org/10.3390/fi10060053
APA StyleDai, J., & Qiao, K. (2018). A Privacy Preserving Framework for Worker’s Location in Spatial Crowdsourcing Based on Local Differential Privacy. Future Internet, 10(6), 53. https://doi.org/10.3390/fi10060053




