1. Introduction
Radio frequency identification technology is able to recognize objects and people automatically, and it can also automatically obtain related data of recognized objects, which is the non-contract recognition technique [
1]. Because of this, the recognition of radio frequency identification (RFID) does not only need the artificial interference, but also work well in the severe environment. Recently, most RFID systems are based on the electric induction [
2]. Attaching a RFID tag on an object, which involves the information of this object, the dedicated recognition terminal can recognize this attached object through reading the tag. In addition, since RFID products read data does not require light source and can pass through external material, and the service life is durable, compared with bar code, RFID products have more advantages [
3].
By now, RFID has been used into many areas, such as supply chain management, electric passport, credit card, driving license [
4,
5], vehicle system (charging system, keyless entry systems), entrance guard card (building gate, public transport) and health care. Especially, in the USA, Japan, and other developed countries, they have equipped with advanced and mature RFID systems [
6]. Some retailers have invested RFID technology, and also authorized RFID producers to attach tag on their goods, so that the low-budget RFID tags are pervasively produced. Wal-Mart passed a resolution, which producers must sufficiently take advantage of the RFID, attaching RFID tags on all products to reduce manpower and material resources [
7].
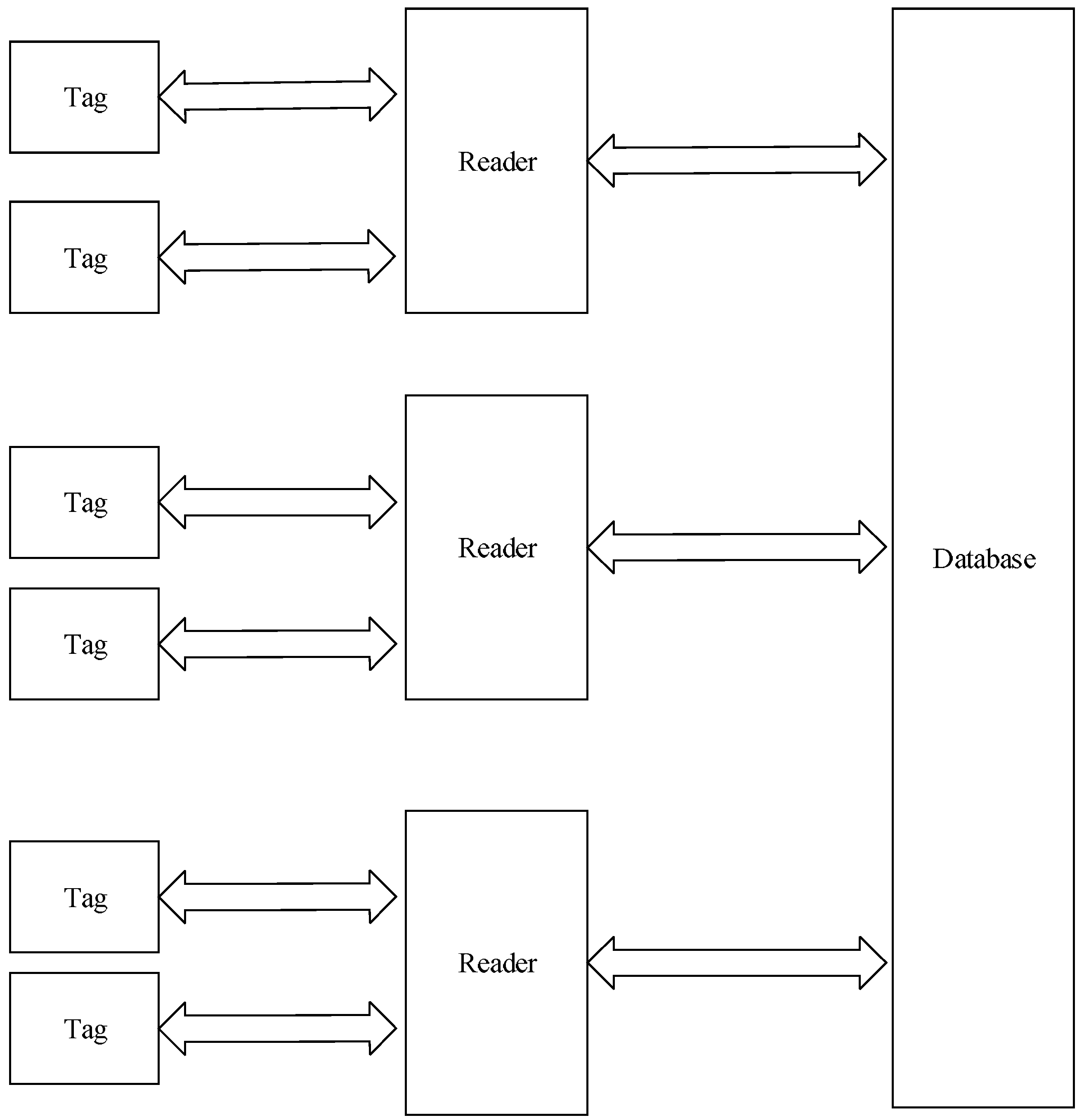
Generally, a typical RFID framework is composed of a reader, tag and a database [
8], which is shown in
Figure 1.
- (1)
Reader: The main function is to transfer energy to the tag via radio frequency and read data of tag or write data to tag [
9]. In common RFID systems, reader still needs to exchange data with database. A reader is composed of the oscillating circuit, communication channel, and controller.
- (2)
Tag: According to the self-contained power or not, tag is classified into active tag, semi-passive tag and passive tag; based on the frequency, tag is classified into low-frequency tag, high-frequency tag and ultrahigh frequency tag [
10]. By various applications, the proper tags are needed to be chosen.
- (3)
Database: It stores all information of tags which indicate all objects.
Mechanism of RFID systems: Firstly, reader sends signals via antenna, and tag receives signal and sends internal tag data. Then, reader receives and verifies the tag data. Finally, reader sends verification result to the host computer which is connected to a database.
Because RFID has the advantages of supporting dynamic real-time communication, fast recognition, easy to read, low cost, it is widely applied into various areas. Nevertheless, when RFID brings convenience, at the same time, its security problem is gradually exposed. In detail, during a simple write and read process, especially for the read or write on a passive tag, the read or write operation will happen when tag is close to a reader with the information exchange. Later, with the existence of a large number of fake and counterfeit RFID products, although researchers continuously find anti-fake measures, it is unable to completely eradicate them. Fake and counterfeit products make massive loss for world politics, economy, and culture, it has been a worldwide problem [
11]. Clone tag is a kind of serious security threat for RFID systems. If attackers acquire the complete information of a tag, they could be able to obtain the unique identifier. In addition of this identifier, tag has no other identify, clone tag is therefore difficult to distinguish from the real one. In addition, as long as the legal tag data is obtained, attacker can launch such copy or clone attack.
In this case, researchers have taken measures to defend against clone attack, such as tag deactivation, encryption algorithms [
12], identify verification [
13] and hash code [
14]. Reference [
15] showed a mutual RFID verification protocol by using the elliptic curve cryptograph (ECC), which depends on ECC to enhance the ability of anti-clone. In the literature [
16], authors gave a tag encryption algorithm without storage of the secret key. Instead, it depends on the hash value stored in the host computer. Reference [
17] gave another RFID verification protocol based on hash, which provides already modified identifier to increase the privacy of verification. These mentioned protocols above rely on the security code which involve tag and the host computer, as well as one-way hash function.
Since the small and limited storage space in the tag, those solutions are based on the complex encryption algorithm which is similar to the hash function and it cannot be applied into the low-cost tag [
18]. In such low-cost RFID systems, the biggest challenge to guarantee the security and privacy comes from the sparse tag resource [
19]. To solve this problem, some lightweight encryption algorithms without hash function are put forward, and the method to identify clone tag as well [
20,
21]. Lehtonen raised a method based on statistics to detect clone tag from the RFID track [
22]. Zannetti showed a method to detect clone attack with the protection of privacy [
23].
Another anti-clone tag method is proposed by using the PUF technique. PUF technique is a breakthrough of the semi-conductor security techniques. PUF is a “biometric” identification technique in chips, which is also called the “chip DNA” technique [
24]. PUF obtains the unique secrets from each chip. This secret information can be used to verify the authenticity of a chip, in the safe-guarding and anti-counterfeiting area, PUF has great application perspective. In the production of each chip, the tiny difference among chips unavoidably exist, although the chip design and production are the same, it is impossible to produce two chips which are completely same, so that PUF techniques can enhance anti-clone function [
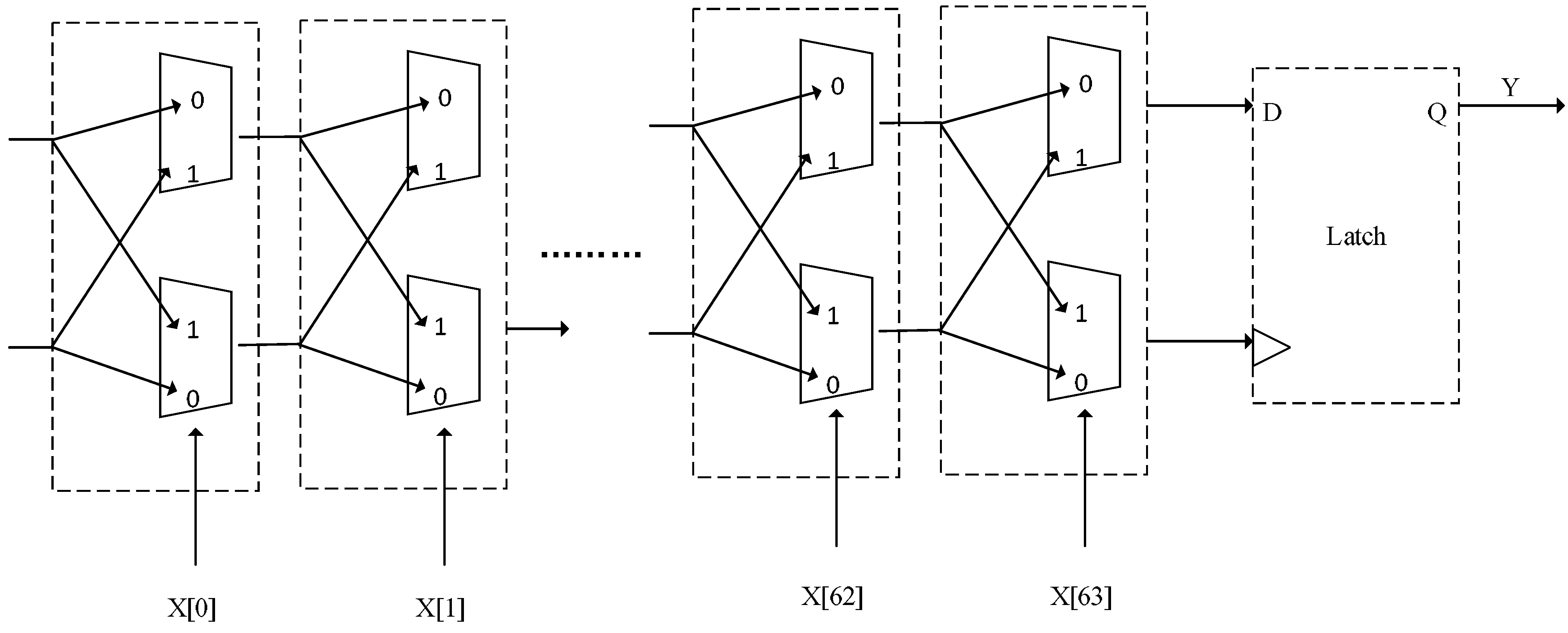
25]. The PUF judge circuit is shown as
Figure 2 [
26]. In
Figure 2, the circuit is a decision-based PUF delay circuit. After inputting X[0], the circuit generates two delay paths whose length are equal, and the input signal is sent to the two paths at the same time. The decision module will choose the path that the input signal first reaches the destination. If the signal which is connected to the D point arrives firstly, it will output 1, otherwise it will output 0. Different physical manufacturing processes result in different outcomes which will give rather different outputs to the same input. PUF circuit receives a search command as an input signal and produces a unique serial feedback, which is verified by command/response mechanism. Different PUF circuits have various delay features, so that their transport speed is different and time of two signals passing PUF is different. The tail of a PUF circuit is an arbiter, and is able to judge the statue of signals before and after to output “1” or “0”. A same signal passing two different PUF circuits can produce different outputs, and because that input signal determines the transport rout in PUF circuit, the different input signals are corresponding to different outputs.
In 2010, Kulseng proposed a lightweight mutual verification protocol based on PUF [
27]. This lightweight protocol uses the PUF and linear feedback shift register (LFSR), rather than uses the complex plus and minus operations, which is very suitable for low-cost RFID tag, but it indicates the security problems of lightweight mutual verification [
28].
This paper is structured as follows: section I introduces related research results about RFID security.
Section 2 describes Kulseng’s lightweight mutual verification protocol and the shortcomings of this protocol.
Section 3 introduces our lightweight mutual verification protocol.
Section 4 uses GNY logic analysis to prove the availability of our protocol.
Section 5 executes the security analysis on our protocol.
Section 6 simulates our lightweight mutual verification protocol and evaluate it in the experiments.
Section 7 gives the performance analysis. At last, we conclude the paper.
3. Proposed Protocol
Due to the shortcoming of Kulseng’s lightweight mutual verification protocol that is based on the PUF, we will introduce our proposed protocol in this section. Some definitions of proposed protocol are shown in
Table 1 at the previous section.
In this protocol, RFID tag is embedded with the PUF module, which makes each RFID tag to produce a unique secret key based on its own circuit, so as to defend against the clone attack. Initially, each RFID tag stores three values: ①
, ②
and ③
. The first value is the dedicated secret value of the tag; the second value is the IDS used during the mutual verification between the tag and the host computer; the third one is the shared secret key by the reader and the tag. After each verification, the secret key
, shared secret key
and FID would be updated. For each tag, the database stores two set of values:
and
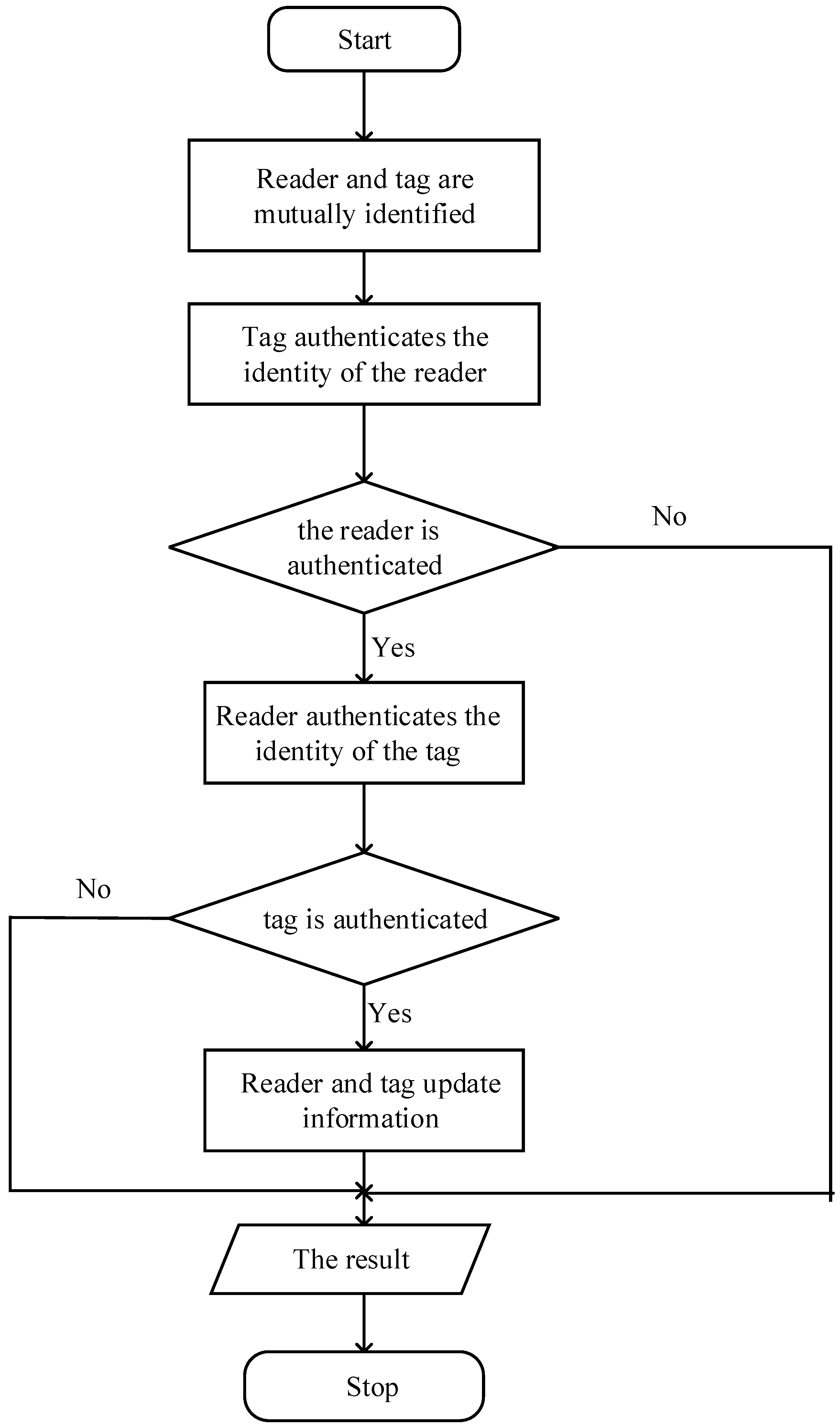
. The later value set is the current tag value, and the prior value set is the tag value of the last communication. This verification protocol contains three parts: tag recognition, mutual verification and update. Tag recognition is to verify the tag’s authenticity; mutual verification is to use the verified tag to verify reader’s authenticity; update is to store the latest secret key for the following verification.
Figure 4 shows the certification process of proposed protocol.
In this paper, the backstage database cannot meet the requirements because it should store all the tag information resulting in a very large amount of data. In order to solve the above problems, the HBase of big data technology is used to store the data. HBase which is a distributed and column-oriented is an open source database. A table in HBase can have hundreds of millions of rows and millions of columns, and the data in each unit can have multiple versions for backup.
3.1. Tag Verification
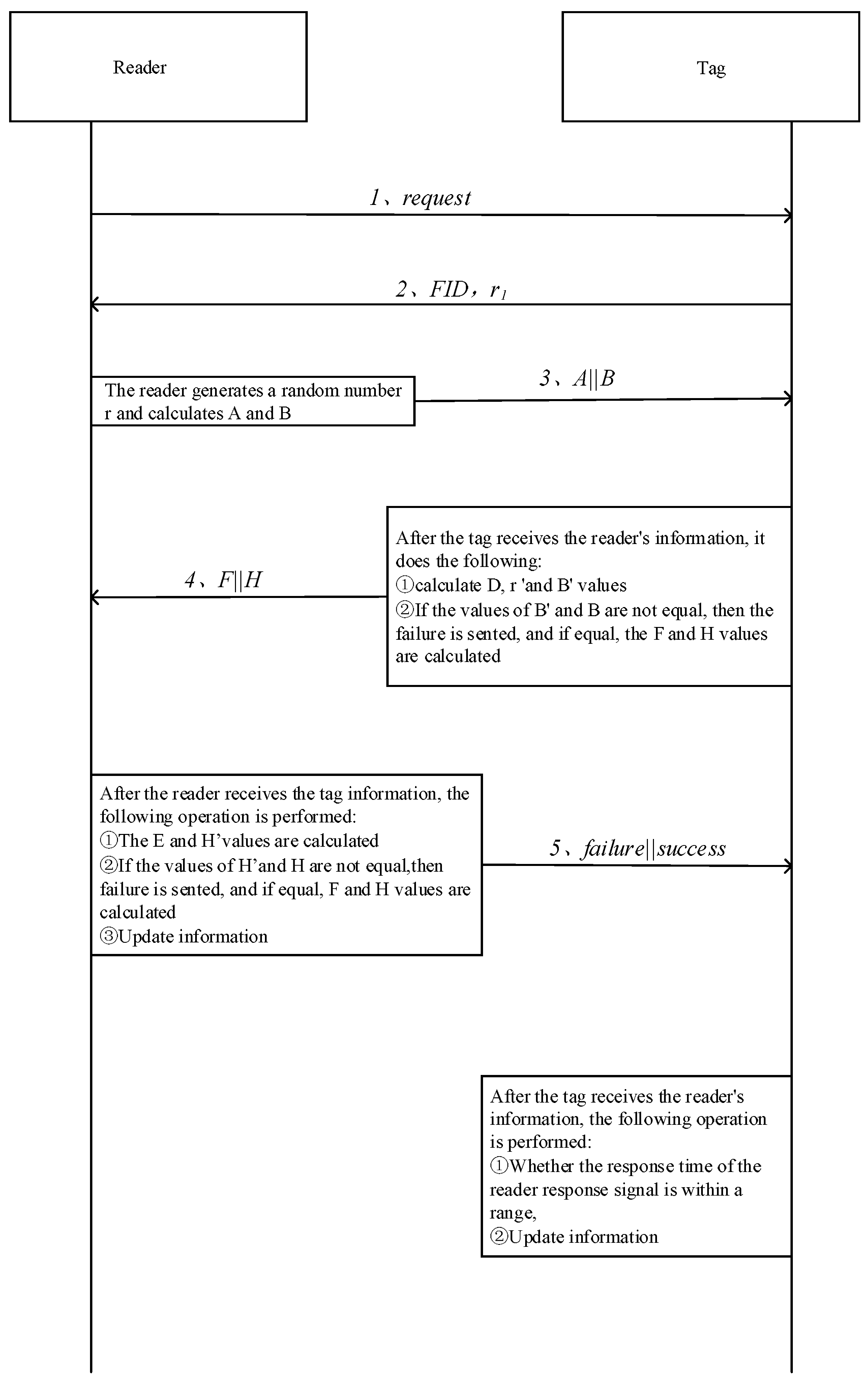
In the tag verification process, reader firstly sends a search request to tag, after receiving the request, tag produces a random number, and sends with FID to the reader. After receiving the random number and F, reader uses FID to search data in the host database. If it means that the database contains this FID, and this tag can be verified without being attacked previously. In addition, the reader uses to execute mutual verification with the tag. However, in the previous verification, tag might be intercepted, resulting in the update of the database, while the tag data is not updated. In this case, reader uses to execute the mutual verification with this tag. If both of the new and old FID cannot match with the FID of the reader, this protocol stops.
3.2. Mutual Verification
The purposes of Mutual verification is to verify the identity of both tag and reader. Reader firstly produces a random number
, combining FID, secret key
, shared key
and random number
according to the Equations (1) and (2) to calculate A and B. Then, reader sends A||B to the RFID tag.
After receiving A||B, tag calculates D and E by Equations (3) and (4), Equation (5) deduces the random number
of the reader and further uses
to obtain
by Equation (6).
Then, tag compares whether
and
are equal or not. If not, the reader is fake, and verification terminates; otherwise, the reader passes the verification, and the protocol goes on for the next step. At the same time, with previously calculated D, E and deduced random number
, by Equation (7) F is calculated, which is also used to deduce the random number
, F and FID of the tag. By Equation (8). H is calculated and F||H is sent to reader.
After receiving F||H, by Equation (9), reader deduces secret key
of the tag, and this deduced key is used to obtain
random number
and secret key
. With Equation (10),
is calculated. Then, using the FID of this tag,
, random number
, by Equation (11).
is calculated.
At this moment, reader compares whether and are equal or not. If it is equal, the tag has been verified before and the mutual verification terminates. If not, this tag is fake, and the verification stops.
3.3. Update Process
After verifying the tag, update starts. During this process, firstly, the host database updates, then the tag updates. The process of updating the database is classified into two cases. In the tag update, if the database uses
and FID to match, the host database does not need to update; if the database uses
and
of the tag to match, the database should be updated in following way:
If reader sends success command to the tag, and the processing time of the reader is within the acceptable range, the tag would be updated in the following ways, which is shown in
Figure 5.
4. Proof of Security
In this section, we use GNY logic [
29] to prove our protocol. The GNY logic was proposed by Gong, Needham and Yahalom in 1990. It is a logic that analyzes the authentication protocol. The GNY logic uses a completely different state search tool, which includes a collection of beliefs maintained by each subject and a collection of inference rules that get new beliefs from the old beliefs. BAN logic has a very simple, intuitive set of rules, so it is easy to use. As it is pointed out in the reference [
29], GNY logic can be used to find serious errors in the protocol, which has attracted widely attention by security researchers. The application of GNY logic has epoch-making significance. It greatly promoted the development of formal verification of security protocols, and inspired many methods of formal verification of security protocols.
4.1. GNY Logic Expression
A|B: A trusts message B.
A|∇B: A receives message B.
A|~B: A sends message B.
AB: A has message B.
(B, C): connecting message B and message C.
#(B): message B is the latest, which means that message B has never been sent before.
{B}k: message B is encrypted by secret key k.
: A and D share secret key k to communicate, which means only A and D or the trusted third party know the secret key k.
4.2. Principle of the GNY Deduction
Principle 1:
Principle 1 indicates: if A trusts that message B is the latest, then it can be deduced that A also trusts the connection between B and C is the latest, and the mapping is trusted as the latest by A whose image is B.
Principle 2:
Principle 2 indicates: If A has message B and C, then it can be deduced that A not only has the connection between B and C, but also the mapping whose image is message B and message C.
Principle 3:
Principle 3 indicates: If A not only has message B, but also trusts that B is the latest message, then, it can be deduced that A also trusts that the equation containing B is the latest.
Principle 4:
Principle 4 indicates: If A received message B, then A has message B can be deduced.
Principle 5:
Principle 5 indicates: A trusts that the secret key K is shared by A and D, and A previously received encrypted B by secret key K. A has the connection between message B and secret key K. A trusts that the connection between message B and secret key K is the latest, then, A trusts that D previously sent the connection between message B and the secret key K, and A also trusts that D used to send encrypted B by K.
4.3. Protocol Process
Protocol (1): R→T: request
Protocol (2): T→R: FID
Protocol (3): R→T:
Protocol (4): T→R:
Protocol (5): R→T: success/failure
4.4. Specifically Describe the Protocol above by Using the GNY Logic Language
Protocol (1): T|∇ request
Protocol (2): R|∇ FID
Protocol (3):
Protocol (4): R|∇
Protocol (5): T|∇ success/failure
4.5. Assumption
- (1)
- (2)
- (3)
- (4)
- (5)
- (6)
- (7)
- (8)
4.6. Target Formulas to Be Proven
- (1)
- (2)
(1) Prove
S1: by principle:
and assumption (4)
, we can deduce:
S2: by principle:
and assumption (3)
, we can deduce:
S3: by principle:
and the above corollary, we can deduce:
S4: by principle:
and protocol (3), we can deduce:
S5: by principle:
and assumption (7) and (8), we can deduce:
S7: by the definition, we can also deduce:
(2) prove
S1: by principle:
and assumption (6)
, there is:
S2: by principle:
and assumption (5)
, there is:
S3: by principle:
and the corollary above, there is:
S4: by principle:
and protocol (4), there is:
S5: by principle:
and assumption (7) and (8), we can deduce:
S6: according to the definition, we can deduce:
S7: by definition, there is:
5. Security Analysis
This section analyses the possible attacks and the security of this protocol.
5.1. Mutual Verification
Mutual verification: Reader verifies the tag, and tag reversely verifies the reader. For some verification protocols, they just verify the tag, without the verification of the reader, which results in a security issue. If attacker uses a reader which is not been verified by a tag, the RFID system data would be leaked, or even the system would be damaged irreparably, such as desynchronization attack and DDos attack.
- (1)
Reader forgery
The third step of the proposed protocol is to send message A||B to RFID tag, according to the Equations (3) and (4), tag calculates the values of D and E, and tag deduces the random number of the reader with Equation (5), where deduced is also used to generate by Equation (6). Then, and B of the reader are compared to verify the reader, in which value of A and value of B are calculated by the random number of the tag, random number of the reader, FID of the tag and the shared secret key and secret key These values would be updated after each round to prepare for the next round, and this is because the original values should be secreted so that the attacker cannot produce a fake reader.
- (2)
Tag forgery
The fourth step of our protocol is to send message F||H to the reader, reader deduces the secret key of the tag by Equation (9), and uses deduced secret key , its random number , secret key and Equation (10) to calculate . Then reader uses of the tag, , and random number to produce by Equation (9), by which reader compares H and the calculated to complete the verification of the reader. In this process, F and H are calculated by the deduced random number by the tag, the secret key produced by PUF and the tag signature FID. After each round verification, these values would be updated for the following verification. As long as the initial values are in secret, attacker cannot produce a fake tag.
Above all, this protocol can guarantee the mutual verification between reader and tag.
5.2. Data Confidentiality and Tag Anonymity
During the verification process, the internal data of either tag or reader should be transferred in cipher text, and the data about tag identity should also be cipher text in transition. Although attacker has intercepted some data of the tag or the reader, attacker is not allowed to deduce any message about the identity of reader and tag.
The critical steps of our protocol are the second, third and fourth step. In the second step, tag sends its FID to the reader, which is just alias and has no relation with the real identity of the tag, and it would be updated after each verification round. Although attacker intercepts this alias, it cannot obtain any effective identity message of the tag. The third and the fourth steps send the A||B of the reader to the tag, and send F||H of the tag to the reader respectively. The previous mutual verification has analyzed the random number of the tag, random number of the reader, FID of the tag and the shared secret key and secret key obtained by calculation. As long as the initialization is in secret, attacker cannot calculate those values. Although attacker can intercept them, those intercepted values cannot be used to deduce the secret key and deduce the tag identity.
Above all, this protocol guarantees the data confidentiality and the integrity of the whole RFID system.
5.3. Steal Attack
Attacker steals the data of the reader and the tag to make the data cannot be received by either tag or reader, as a way to damage the RFID system.
Assume that attacker steals the last message (failure/success) from reader to the tag, and promotes reader to update the secret key of the database except for the secret key of the tag. In this way, the data of tag and the database are not synchronous. Our protocol solves this problem by maintaining the FID and secret key and of the last verification. Even the tag cannot update its secret key value, the database can find its FID.
In summary, this protocol can defend against steal attack.
5.4. Replay Attack
Attacker iteratively sends the message that has been received by the reader to cheat reader, which would make reader to response so that the RFID system is damaged.
Assume the attacker intercepts the message during a mutual verification: ①; ②A||B; ③F||H. Then, attacker intercepts the last message from reader to the tag (failure/success), and the reader updates the secret value of the database as a result, except for the secret key of tag. In the next verification round, attacker firstly sends that are intercepted previously to the reader. After receiving those message, reader searches this FID and finds that it matches to a . Later, reader generates the random number and produce A||B by equation. If attacker can send the previously obtained F||H to activate a forgery verification, however, during this verification, the random number generated by the reader is different from the random number produced in the last round, which results in the difference between H and , so that the tag verification will fail. Above all, this protocol defends against replay attack.
5.5. Backtracking Attack
When a RFID tag is deciphered, attacker cannot deduce previous verification information by this current verification.
Assume that an attacker cracks the current verification process, and obtains the FID of the tag and the secret value ). However, attacker cannot deduce previous secret key values in verification because these secret key values are updated with the random number after each verification round.
Therefore, this protocol guarantees the safety against the backtracking.
5.6. Clone Attack
Attacker copies the legal tag to obtain a clone tag, which contains all information of the copied tag, including the unique ID, data and algorithms stored in tag. In other words, when reader sends a random number and a request to the tag, clone tag can response to the reader in a same way as the legal tag. Thus, simple encryption algorithms and increase of the complexity of the verification algorithms cannot prevent against clone attack.
Our protocol is based on PUF technique to achieve the mutual verification. In the previous introduction of the PUF technique, we have analyzed its safety. Although attacker launches attack on reader or tag, and obtains the secret key of the tag: {}, attacker cannot produce a clone tag with these values. This is because PUF technique is by deriving the difference among chips during manufacture, which causes the different outputs. In this way, clone attack can be prevented against by our protocol.
5.7. Desynchronization Attack
Attacker triggers the update of tag by some means except for the update of the reader or vice-versa. As a result, the desynchronization between the data of the database and the tag data exists, and tag cannot be verified by the reader in following verification.
Attack one: Modifying message A or message B
Assume attacker is intercepting a verification process, until the reader sending A||B to the tag, attacker modifies this message into , and then sends it the tag. After receiving , tag firstly deduces the random number of the reader by , by which tag calculates . Then, tag judges if = as a way to verify reader. Because attacker modifies message B into , reader cannot be successfully verified, which defends against the desynchronization caused by modifying message A or message B.
Attack two: Modifying message F or message H.
Assume attacker is intercepting a verification process, until confirmation of the identity of the reader, tag calculates message F||H and sends it to reader to verify. At this moment, attacker modifies this message into , and sends the modified message to reader. After receiving , reader firstly deduces the secret key by then reader calculates After this, reader judges if = or not to verify the tag. Because attacker modifies message H into , reader cannot verify tag successfully, so that both tag and reader cannot update their own data, which thus solves the problem of desynchronization caused by modifying F or modifying H.
Compared with previous Kulseng’s lightweight mutual verification protocol,
Table 2 shows the advantages of our protocol.
6. Experiments
This section shows the secure tag verification in a RFID system according to our protocol. We simulate to construct a vehicle cargo invading detection system, and all vehicles of this system carry RFID tags. With ultrahigh frequency RFID reader, the tag of a vehicle would be recorded, which information is recorded by the database and operating platform executes the secure verification via our protocol.
Ultrahigh frequency reader: Impinj R420. Air interface protocol: EPC global UHF Class 1 Gen 2/ISO 18000-6C, using Autopilot technique of the Speedway Revolution, which is able to automatically optimize the performance of the reader in any environment to maintain the best performance. Autopilot technique has following features:
Automatically setting—Optimize the deployment of reader to achieve the best performance.
Low load circulation—Reduce radio-frequency interference, power dissipation, energy cost.
Dynamic antennae switch—Increase handling capacity, enhance the reader to more effective work.
Speedway Revolution RFID reader also supports power over Ethernet (PoE), increases the flexibility of its application, so that the deployment is simplified and does not need AC power supply. As a result, the cost is dramatically reduced. Reader is equipped with the capability of the best flexibility in receiving, anti-interference and product and carrier offset capability.
RFID tag: Impinj H47, which supports air interface protocol EPC Class 1 Gen 2/ISO18000-6C; working frequency: 860~960 MHz, read distance is decided by the reader emit power. The tag can be fixed on the object in a sticker manner, and is easy to be read for obtaining information.
Platform construction tools: Java development platform.
Operating system: Windows 10.
In this section, we mainly discuss the RFID readers of what frequency we choose. Different frequency readers are limited by different distance when readers read tags’ information. If the distance is too long, the reader cannot read the information of the tag, which will lead to the occurrence of missed reading. The counterfeiters can mix the real and fake tags together and put the fake tags out of the range to allow them to cheat the reader. Therefore, it is important to discuss how to use this protocol in terms of different frequencies and ranges of RFID readers.
In the experiments, to verify the impact of using high frequency reader and the ultrahigh frequency reader on the system alarm’s success rate, in the cases with different distance between the tag and the reader, through experiencing 100 times experimental result analysis, the results are shown by
Figure 6, we can conclude: within 10 cm from high frequency RFID reader, the number of successfully finding the clone tag are: 100, 100, 100, 99, 99, 100, 98, 97, 94. The distance between the reader and tag is over the best reading distance 8 cm, because the Mifare card data cannot be effectively read and the success rate dramatically decreases.
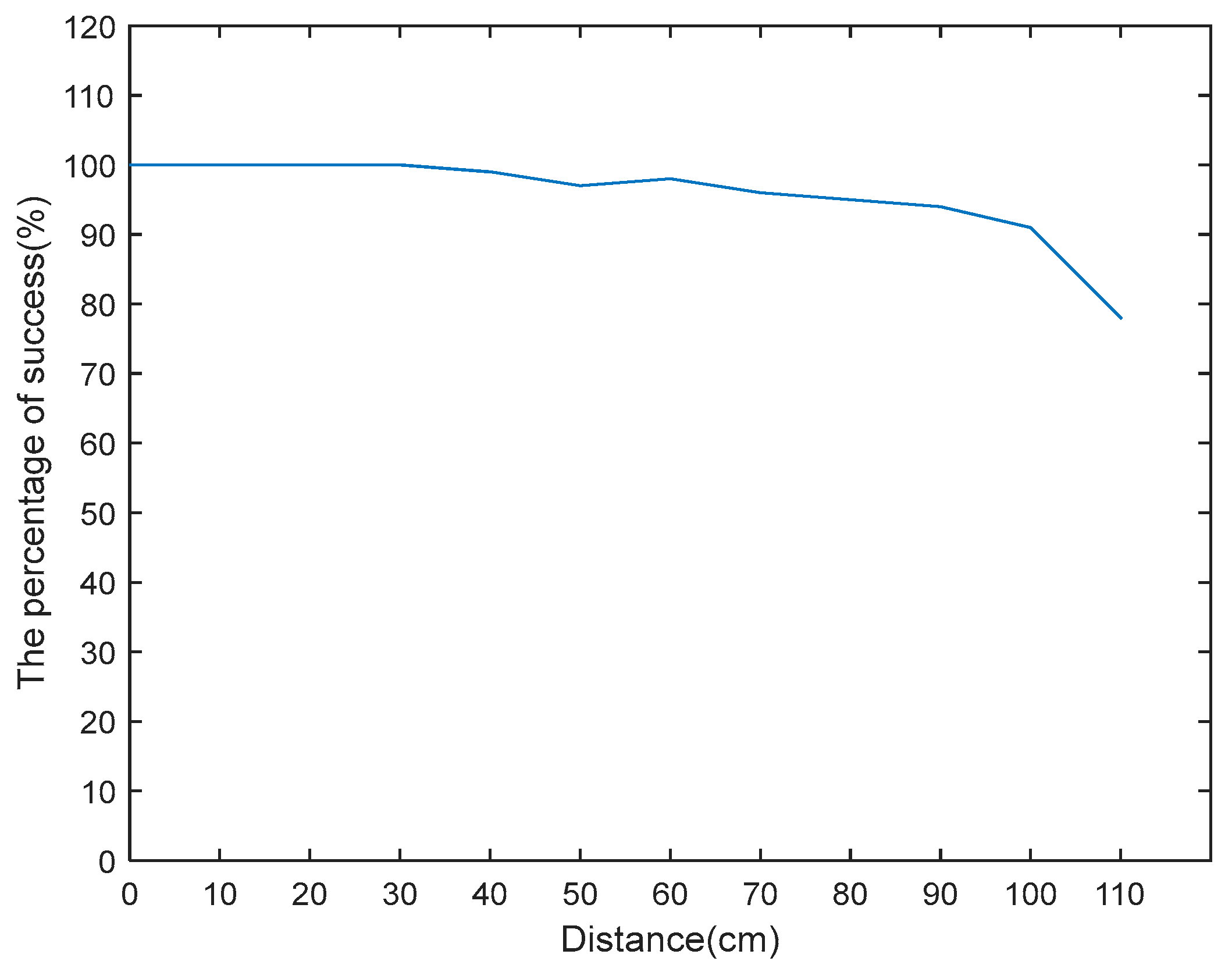
As shown in
Figure 7, in conclusion: within 110 cm from the RFID ultrahigh frequency reader, times of the reader being attacked are respectively: 100, 100, 100, 100, 99, 97, 98, 96, 95, 94, 91, 78. When the effective distance is bigger than the nominal range 100 cm, because reader cannot obtain the tag data, success rate obviously reduces. Experimental sample data is given in
Figure 7.
This experiment indicates when the high frequency reader is located over the nominal reading range, which is more than 8 cm, the performance dramatically falls, the rate of invading tag dramatically reduces. With our experimental sample, comprehensive success rate is 91.90%; while the ultrahigh frequency reader’s performance slightly reduces when the distance is over the nominal reading distance, when the distance is over 90 cm, the performance of the reader begins to reduce. In comparison, ultrahigh frequency RFID reader of the original system performs better in detecting fake tag.
7. Performance Analysis
By calculating the costs of time and storage space for a complete certification process of backstage database, reader and tag are used to judge the performance of the proposed protocol. In this section, the reader and the backend database are viewed as a whole for the convenience of analysis, which is called the reader side. For the protocol presented in this paper, the data stored in the tag, reader, and back-end database is a unit of 96 bits, let L substitute for 96 bits. defines as the number of PUF function operations. defines as the number of times when a random number is generated. defines as the number of XOR operation.defines as the number of times of the loop left movement, defines as the number of join operation, defines as the number of AND operation, and defines as the number of F function operation. Then the complete certification process will be analyzed in the term of its complexity.
Firstly, we analyze the time complexity.
For the RFID tag, in tag verification phase, a random number of is generated in the tag recognition phase, so the time complexity of the tag is ; in the process of authenticating the reader of Mutual Verification phase, there are four operations by a tag, such as . So in the process of authenticating the reader of Mutual Verification phase, the time complexity of the tag is ). In the process of authenticating the tag of Mutual Verification phase, there are three operations by a tag, such asand. So in the process of authenticating the tag of Mutual Verification phase, the time complexity of the tag is ). In the whole Mutual Verification phase, the time complexity of the tag is ). In the update phase, there are two operations by a tag, such as and . Thus, the time complexity of the tag is ) in the update phase.
For the reader side, in the process of authenticating the reader of Mutual Verification phase, there are three operations by the reader side, such as
and
. So in the process of authenticating the reader of Mutual Verification phase, the time complexity of the reader side is
). In the process of authenticating the tag of Mutual Verification phase, there are three operations by the reader side, such as
. So in the process of authenticating the tag of Mutual Verification phase, the time complexity of the reader side is
). So in the whole Mutual Verification phase, the time complexity of the reader side is
). In the update phase, there are two operations by the reader side, such as
and
. So in the update phase, the time complexity of the reader side is
).
Table 3 and
Table 4 give the results of the time cost analysis of our protocol and the K protocol.
Secondly, we analyze the space complexity.
For the RFID tag, there are some data in a tag, such as . Thus, the space complexity of a tag is 3L.
For the reader side, there are some data in the reader side, such as
. So the space complexity of the reader side is 9 L. The comparison results are shown in the
Table 5.
In our protocol, it only uses some simple operations, such as XOR operation, the loop left movement operation, JOIN operation, and AND operation. In addition to PUF circuit by the arbiter judged by two signal circuit who arrives firstly, the amount of calculation is very small. So our protocol meets the requirements of low cost in computational overhead. To sum up, although the protocol proposed in this paper is more complex than the K protocol, its security is much higher than that of K protocol. Therefore, this protocol has found a good balance between performance and security.