SmartVeh: Secure and Efficient Message Access Control and Authentication for Vehicular Cloud Computing
Abstract
:1. Introduction
- (1)
- We provide a secure message access control framework in VCC based on hierarchical ABE (HABE). The framework consists of a trusted authority (TA), and a group of AAs which request secret parameters from the TA and generate persistent attribute keys or dynamic attribute keys for vehicles independently. Thus, vehicles can share confidential messages with other vehicles which satisfy the pre-defined access policy.
- (2)
- We utilize ABS to enforce message authentication, which can authenticate messages by verifying whether the signer’s attributes satisfy the predicate policy. It also ensures message integrity by checking and maintaining the anonymity of vehicles.
- (3)
- We present a secure outsourcing construction in VCC by delegating the heavy computations from resource-limited OBUs to the cloud server and RSUs, which means that the computation complexity of OBUs is independent of the number of attributes.
2. Related Works
3. Technical Preliminaries
3.1. Bilinear Map
- (1)
- Computability. There is a polynomial time algorithm to compute for any .
- (2)
- Bilinearity. For all and , we have .
- (3)
- Non-degeneracy. There exists such that .
3.2. Access Tree
3.3. Ciphertext-Policy, Attribute-Based Encryption
- (1)
- Setup(): On input of a security parameter , the algorithm outputs a public key PK and a master key MK.
- (2)
- KeyGen(MK, PK, S): On input of the master key MK, public key PK and a set S of attributes, the algorithm outputs a secret key SK.
- (3)
- Enc(PK, M, Ta): On input of the public key PK, a message M and an access policy Ta, the algorithm outputs a ciphertext CT.
- (4)
- Dec(PK, CT, SK): On input of the public key PK, a ciphertext CT associated with an access policy Ta and a secret key SK, the algorithm outputs the message M if .
3.4. Attribute-Based Signature
- (1)
- Setup(). On input of a security parameter , AA generates the public key PK and master key MK.
- (2)
- KeyGen(MK, PK, S). On input of the master key MK, public key PK, and a set of attributes S, AA generates the secret key SK.
- (3)
- Sign(PK, SK, M, Tc). On input of the public key PK, a secret key SK of signer, a message M and a predicate policy Tc, the signer generates a signature ST for M.
- (4)
- Verify(PK, M, Tc, ST). On input of the public key PK, a message M, a predicate policy Tc and a signature ST, the verifier checks ST. If the signer’s attributes satisfy Tc, it outputs true.
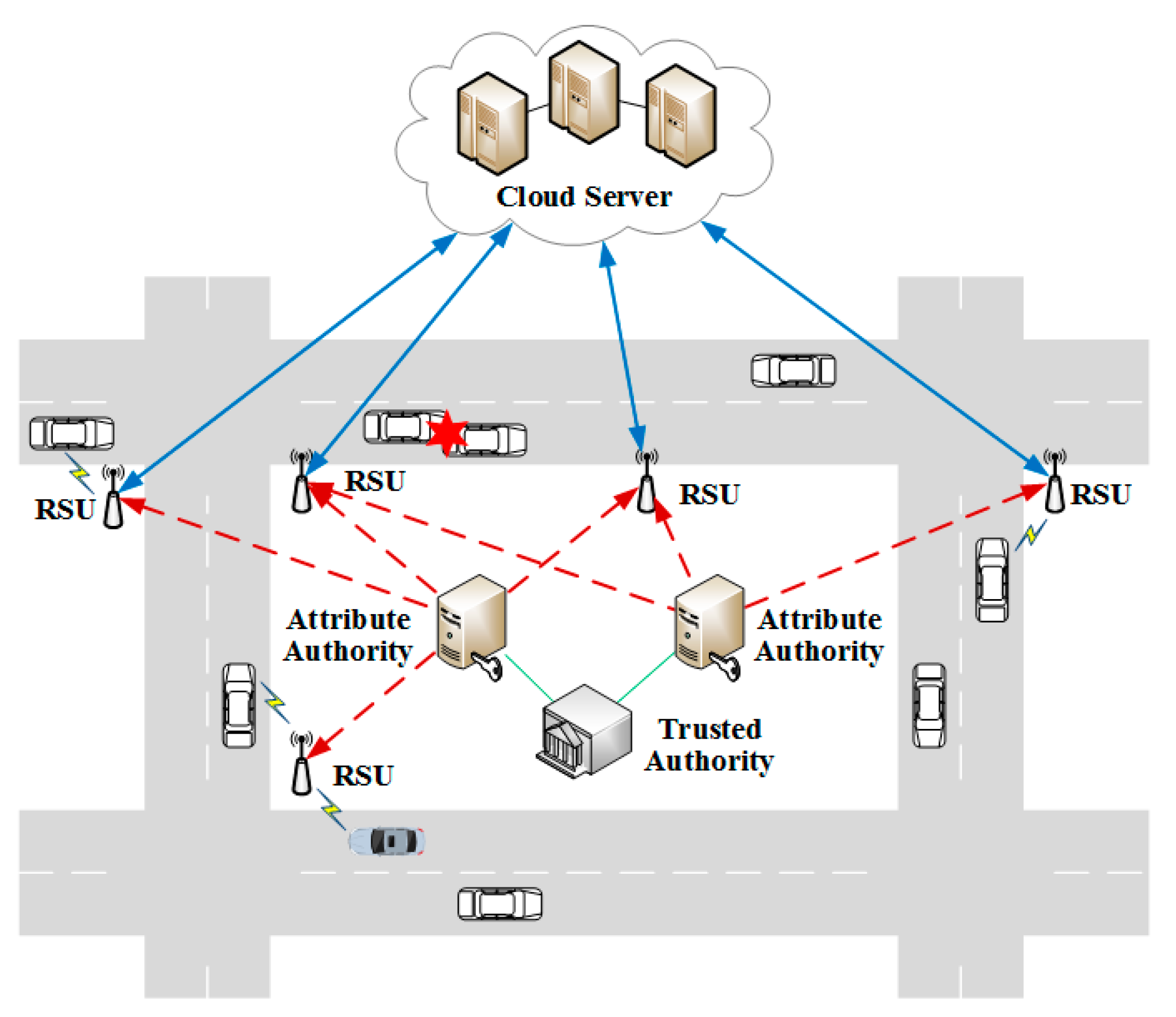
4. System Overview
4.1. System Framework
4.2. Security Model
- (1)
- Message confidentiality. The messages should be transmitted in encrypted form, and the vehicles which cannot satisfy the access policy defined by the message sender should not be allowed to access the plaintext of the message. Meanwhile, the cloud server and RSUs cannot recover the broadcast message.
- (2)
- Fine-grained access control. The vehicle can enforce an access policy for each broadcast message, which designates the messages that the vehicle is allowed to access.
- (3)
- Message authentication. If message sender’s attributes could not satisfy the predicate policy, the message broadcast should not succeed.
- (4)
- Collusion resistance. The message access should not be successful if either of the vehicles cannot satisfy the access policy alone. Further, even if unauthorized vehicles collude with the RSU, the access should not take effect.
4.3. System Definition
- (1)
- : On input of a security parameter , the TA outputs a system public key PK and a master key MK.
- (2)
- : On input of PK and MK, a set of attributes of AA, the TA outputs the master secret key MSK for AA.
- (3)
- : On input of PK and MSK, a set of managed attributes of the vehicle, the AA outputs the secret key for each vehicle.
- (4)
- : On input of PK, access policies in different AAs, the cloud server outputs a partially encrypted ciphertext .
- (5)
- : On input of PK, a message M and a partial ciphertext , the vehicle outputs a ciphertext .
- (6)
- : On input of a ciphertext CT, a predicate policy and an outsourced secret key which is a part of secret key, the cloud server outputs a signing token SN and a partial signature .
- (7)
- : Given a partial signature and secret key SK, the vehicle generates a thorough signature ST.
- (8)
- : On input of a signature ST, a signing token SN and a predicate policy , the RSU outputs true if the sender vehicle’s attributes satisfy .
- (9)
- : On input of PK, a ciphertext CT, a outsourced secret key which is also a part of secret key, the RSU outputs a partially decrypted ciphertext if the attribute set satisfies the access policy.
- (10)
- : The vehicle takes a and a secret key as input, and outputs the plaintext M.
5. Construction of SmartVeh
5.1. System Setup
5.2. Authority Setup
5.3. Key Generation
5.4. Message Broadcasting
5.4.1. Cloud Encryption
5.4.2. Vehicle Encryption
5.4.3. Cloud Signing
- (1)
- If , the cloud server computes , and .
- (2)
- If , the cloud server computes , and .
5.4.4. Vehicle Signing
5.5. Message Decryption
5.5.1. RSU Verifying
- (1)
- If x is a leaf node, then we set . If , thenIf , then
- (2)
- If x is a non-leaf node, the algorithm computes as follows. It calls the algorithm for each child node n of x, and outputs the result as .
5.5.2. RSU Decryption
- (1)
- If x is a leaf node, then we let and compute the following. If , thenIf , then .
- (2)
- If x is a non-leaf node, the algorithm computes the following. It calls for each child node n of x, and generates the result as . Let be an arbitrary -sized set of child nodes such that . Similar to the verifying process, the algorithm computes as follows.
5.5.3. Vehicle Decryption
6. Security Analysis
6.1. Message Confidentiality
6.2. Fine-Grained Access Control
6.3. Message Authentication
6.4. Collusion Resistance
7. Performance Analysis
7.1. Functionality Comparisons
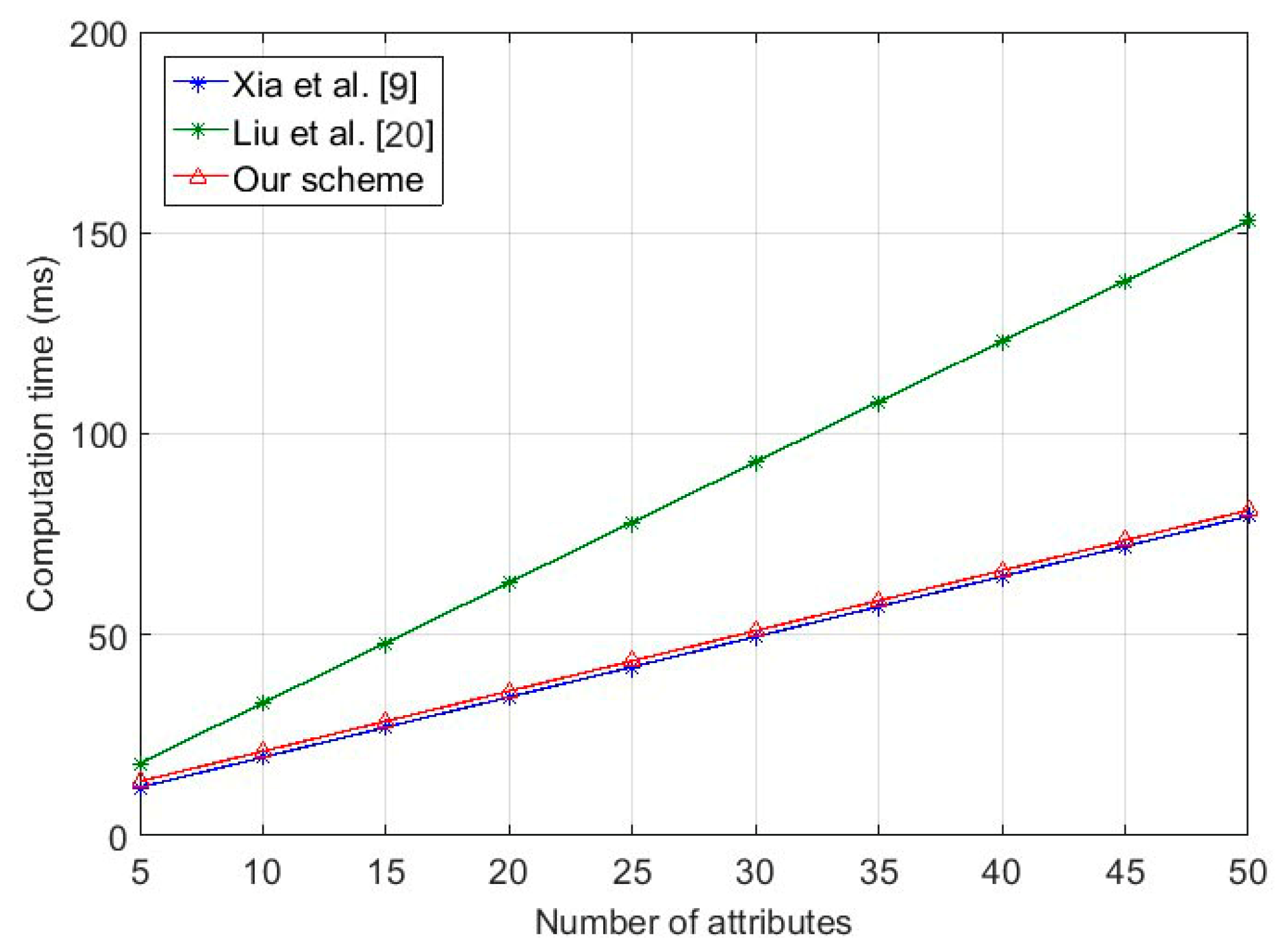
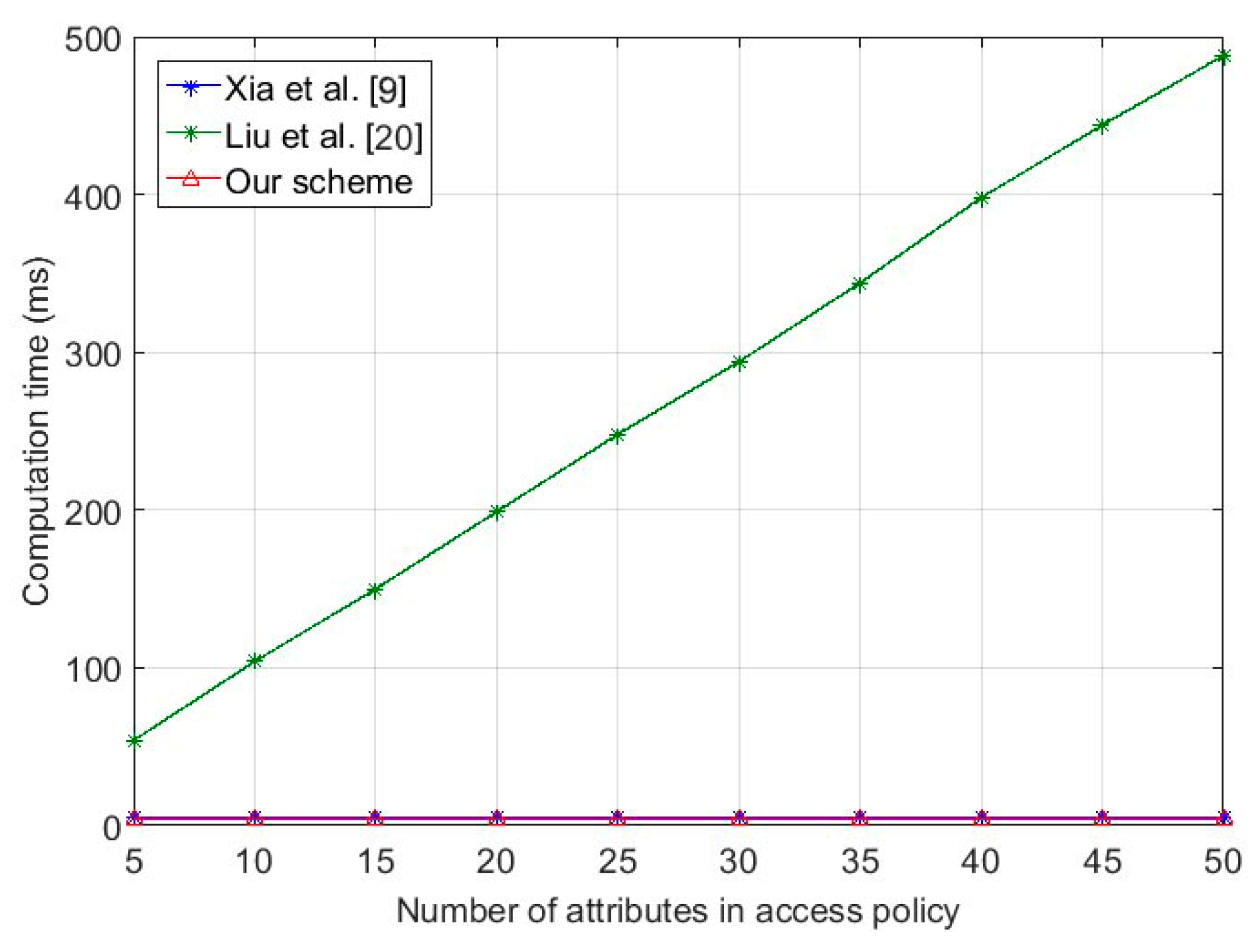
7.2. Performance Analysis
7.3. Simulation Evaluation
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Li, X.; Qiao, C.; Yu, X.; Wagh, A.; Sudhaakar, R. Toward effective service scheduling for human drivers in vehicular cyber-physical systems. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1775–1789. [Google Scholar] [CrossRef]
- Lee, U.; Lee, J.; Park, J.S.; Gerla, M. FleaNet: A virtual market place on vehicular networks. IEEE Trans. Veh. Technol. 2010, 59, 344–355. [Google Scholar]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient adaptive resource management for real-time vehicular cloud services. IEEE Trans. Cloud Comput. 2016, PP. [Google Scholar] [CrossRef]
- Cordeschi, N.; Amendola, D.; Shojafar, M.; Baccarelli, E. Distributed and adaptive resource management in cloud-assisted cognitive radio vehicular networks with hard reliability guarantees. Veh. Commun. 2015, 2, 1–12. [Google Scholar] [CrossRef]
- Alam, K.; Saini, M.; Saddik, A. tNote: A social network of vehicles under Internet of Things. In Proceedings of the 1st International Conference on Internet of Vehicles (IOV 2014), Beijing, China, 1–3 September 2014; pp. 227–236. [Google Scholar]
- Smaldone, S.; Han, L.; Shankar, P.; Iftode, L. RoadSpeak: Enabling voice chat on roadways using vehicular social networks. In Proceedings of the 1st Workshop on Social Network Systems, Glasgow, Scotland, 1 April 2008; pp. 43–48. [Google Scholar]
- Huang, Q.; Ma, Z.; Yang, Y.; Fu, J.; Niu, X. EABDS: Attribute-based secure data sharing with efficient revocation in cloud computing. Chin. J. Electron. 2015, 24, 862–868. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Xia, Y.; Chen, W.; Liu, X.; Zhang, L.; Li, X.; Xiang, Y. Adaptive multimedia data forwarding for privacy preservation in vehicular ad-hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2629–2641. [Google Scholar] [CrossRef]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the decryption of ABE ciphertexts. In Proceedings of the 20th USENIX Conference on Security, San Francisco, CA, USA, 8–12 August 2011; p. 34. [Google Scholar]
- Maji, H.; Prabhakaran, M.; Rosulek, M. Attribute-based signatures. In Proceedings of the 11th Cryptographers’ Track at the RSA Conference 2011: Topics in Cryptology, San Francisco, CA, USA, 14–18 February 2011; pp. 376–392. [Google Scholar]
- Pietrowicz, S.; Shim, H.; Crescenzo, G.D.; Zhang, T. VDTLS—Providing secure communications in vehicle networks. In Proceedings of the INFOCOM Workshops 2008, Phoenix, AZ, USA, 13–18 April 2008; pp. 1–6. [Google Scholar]
- Mallissery, S.; Pai, M.; Pai, R.; Smitha, A. Cloud enabled secure communication in vehicular ad-hoc networks. In Proceedings of the 2014 International Conference on Connected Vehicles and Expo, Vienna, Austria, 3–7 November 2014; pp. 596–601. [Google Scholar]
- Nema, M.; Stalin, S.; Tiwari, R. RSA algorithm based encryption on secure intelligent traffic system for VANET using Wi-Fi IEEE 802.11p. In Proceedings of the 2015 International Conference on Computer, Communication and Control, Indore, India, 10–12 September 2015; pp. 1–5. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Huang, D.; Verma, M. ASPE: Attribute-based secure policy enforcement in vehicular ad hoc networks. Ad Hoc Netw. 2009, 7, 1526–1535. [Google Scholar] [CrossRef]
- Ruj, S.; Nayak, A.; Stojmenovic, I. Improved access control mechanism in vehicular ad hoc networks. In Proceedings of the 10th International Conference on Ad-Hoc, MOBILE, and Wireless Networks, Paderborn, Germany, 18–20 July 2011; pp. 191–205. [Google Scholar]
- Yeh, L.; Chen, Y.; Huang, J. ABACS: An attribute-based access control system for emergency services over vehicular ad hoc networks. IEEE J. Select. Areas Commun. 2011, 29, 630–643. [Google Scholar] [CrossRef]
- Liu, X.; Shan, Z.; Zhang, L.; Ye, W.; Yan, R. An efficient message access quality model in vehicular communication networks. Signal Process. 2016, 120, 682–690. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J. Distributed aggregate privacy-preserving authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2017, 18, 516–526. [Google Scholar] [CrossRef]
- Sánchez-García, J.; García-Campos, J.M.; Reina, D.G.; Toral, S.L.; Barrero, F. On-siteDriverID: A secure authentication scheme based on Spanish eID cards for vehicular ad hoc networks. Future Gener. Comput. Syst. 2016, 64, 50–60. [Google Scholar] [CrossRef]
- Kang, Q.; Liu, X.; Yao, Y.; Wang, Z.; Li, Y. Efficient authentication and access control of message dissemination over vehicular ad hoc network. Neurocomputing 2016, 181, 132–138. [Google Scholar] [CrossRef]
- Chim, T.; Yiu, S.; Hui, L.; Li, V. VSPN: VANET-based secure and privacy-preserving navigation. IEEE Trans. Comput. 2014, 63, 510–524. [Google Scholar] [CrossRef]
- Zhang, P.; Chen, Z.; Liu, J.; Liang, K.; Liu, H. An efficient access control scheme with outsourcing capability and attribute update for fog computing. Future Gener. Comput. Syst. 2016, 78, 753–762. [Google Scholar] [CrossRef]
- Huang, Q.; Yang, Y.; Shen, M. Secure and efficient data collaboration with hierarchical attribute-based encryption in cloud computing. Future Gener. Comput. Syst. 2017, 72, 239–249. [Google Scholar] [CrossRef]
- Studer, A.; Shi, E.; Bai, F.; Perrig, A. Tacking together efficient authentication, revocation, and privacy in VANETs. In Proceedings of the 6th Annual IEEE Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Rome, Italy, 22–26 June 2009; pp. 1–9. [Google Scholar]
- Liu, X.; Xia, Y.; Chen, W.; Xiang, Y.; Hassan, M.; Alelaiwi, A. SEMD: Secure and efficient message dissemination with policy enforcement in VANET. J. Comput. Syst. Sci. 2016, 82, 1316–1328. [Google Scholar] [CrossRef]
- Ma, H.; Zhang, R.; Wan, Z.; Lu, Y.; Lin, S. Verifiable and exculpable outsourced attribute-based encryption for access control in cloud computing. IEEE Trans. Dependable Secur. Comput. 2017, 14, 679–692. [Google Scholar] [CrossRef]
- The Pairing-Based Cryptography Library. Available online: http://crypto.stanford.edu/pbc (accessed on 24 December 2017).

| Functions | Yeh et al. [19] | Liu et al. [28] | Chim et al. [24] | Xia et al. [9] | Liu et al. [20] | Our Scheme |
|---|---|---|---|---|---|---|
| Message confidentiality | CP-ABE | CP-ABE | CP-ABE | CP-ABE | HABE | HABE |
| Hierarchical authorities | No | No | No | No | Yes | Yes |
| Persistent attribute key generation | - | - | - | Every | Once | Once |
| Anonymous authentication | No | No | IBS with pseudonym | No | ABS | ABS |
| Encryption outsourcing | No | No | No | No | No | Yes |
| Decryption outsourcing | No | Yes | No | Yes | No | Yes |
| Signing outsourcing | - | - | No | - | No | Yes |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, Q.; Yang, Y.; Shi, Y. SmartVeh: Secure and Efficient Message Access Control and Authentication for Vehicular Cloud Computing. Sensors 2018, 18, 666. https://doi.org/10.3390/s18020666
Huang Q, Yang Y, Shi Y. SmartVeh: Secure and Efficient Message Access Control and Authentication for Vehicular Cloud Computing. Sensors. 2018; 18(2):666. https://doi.org/10.3390/s18020666
Chicago/Turabian StyleHuang, Qinlong, Yixian Yang, and Yuxiang Shi. 2018. "SmartVeh: Secure and Efficient Message Access Control and Authentication for Vehicular Cloud Computing" Sensors 18, no. 2: 666. https://doi.org/10.3390/s18020666
APA StyleHuang, Q., Yang, Y., & Shi, Y. (2018). SmartVeh: Secure and Efficient Message Access Control and Authentication for Vehicular Cloud Computing. Sensors, 18(2), 666. https://doi.org/10.3390/s18020666





