A Tree Based Broadcast Scheme for (m, k)-firm Real-Time Stream in Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Work
2.1. Real-Time Protocols
2.2. Broadcast Routing Protocols
3. Proposed Scheme: FRBP
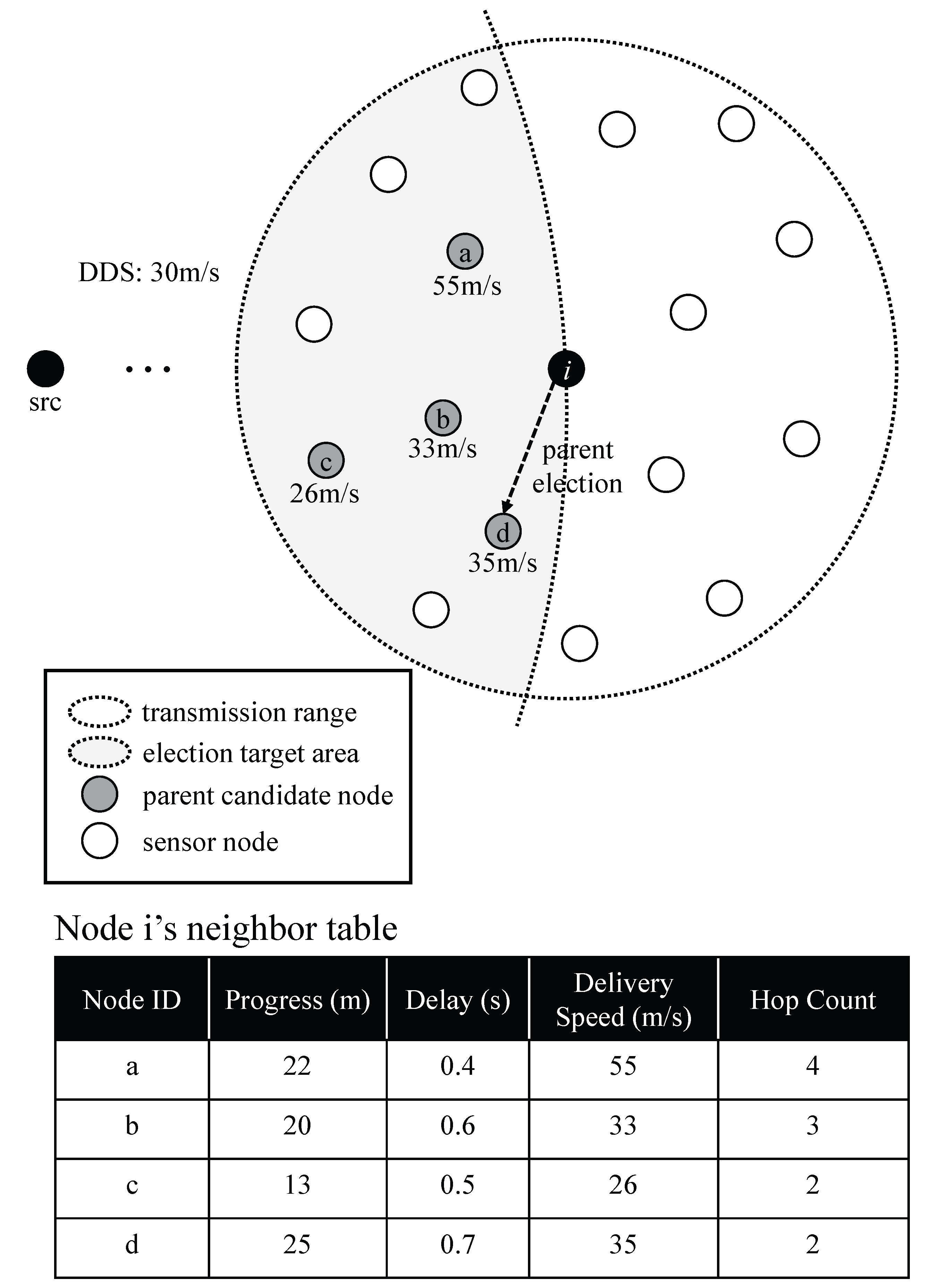
3.1. Real-Time Broadcast Tree Construction
| Algorithm 1 Real-time broadcasting tree construction |
|
3.2. Data Transmission through the Real-Time Broadcast Tree
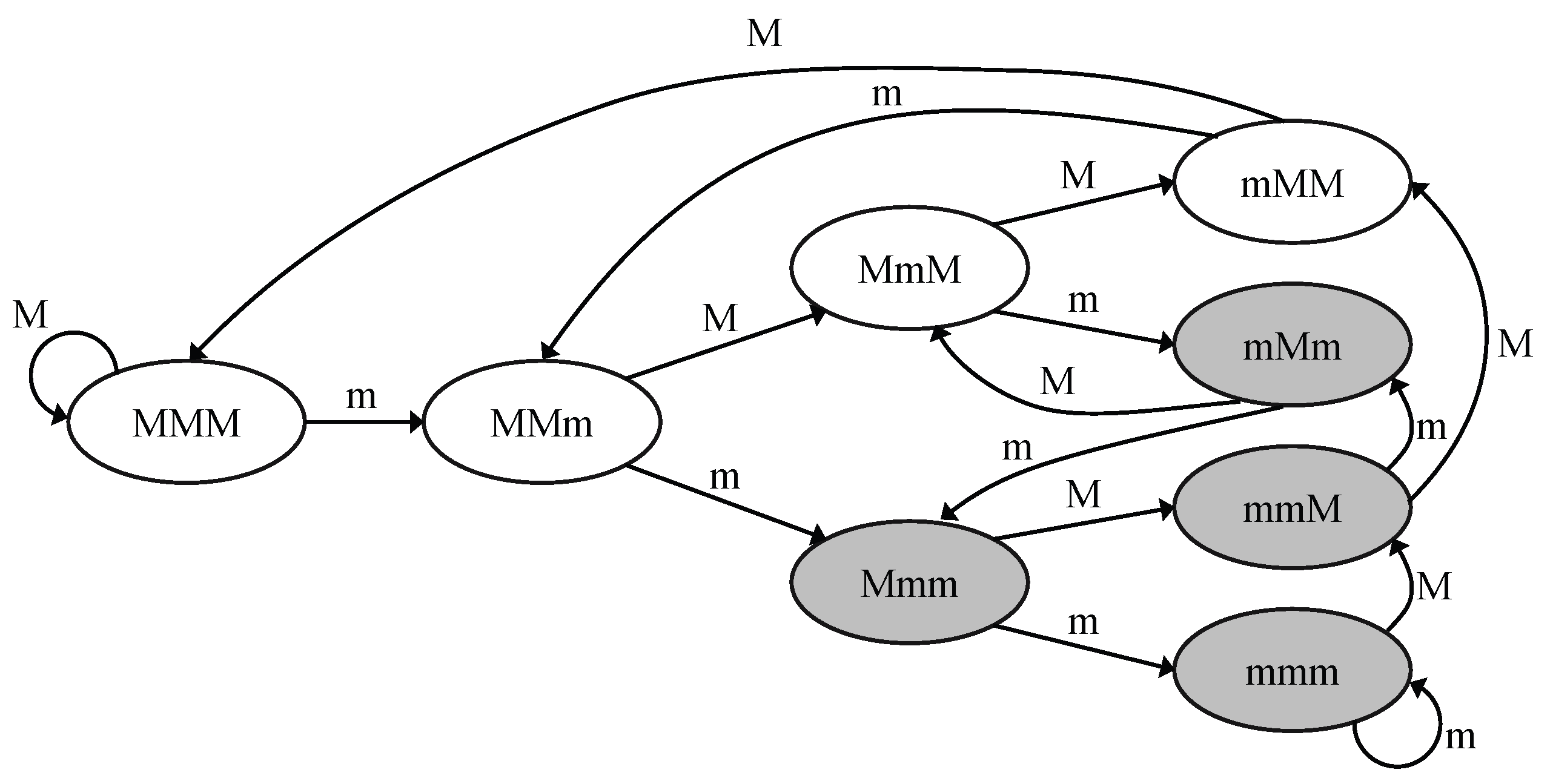
3.3. Local Real-Time Failure Avoidance and Recovery
| Algorithm 2 Real-time failure avoidance |
|
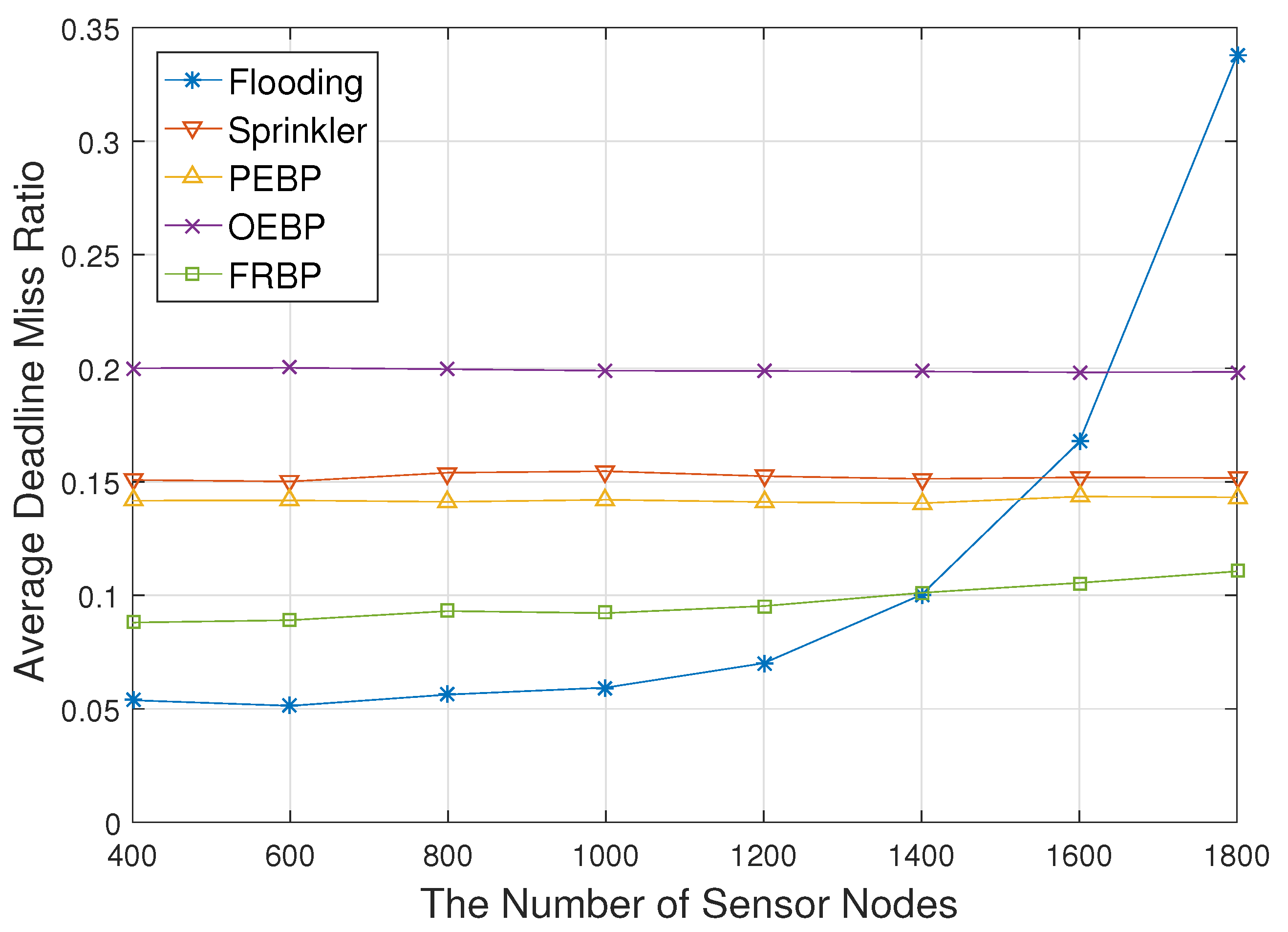
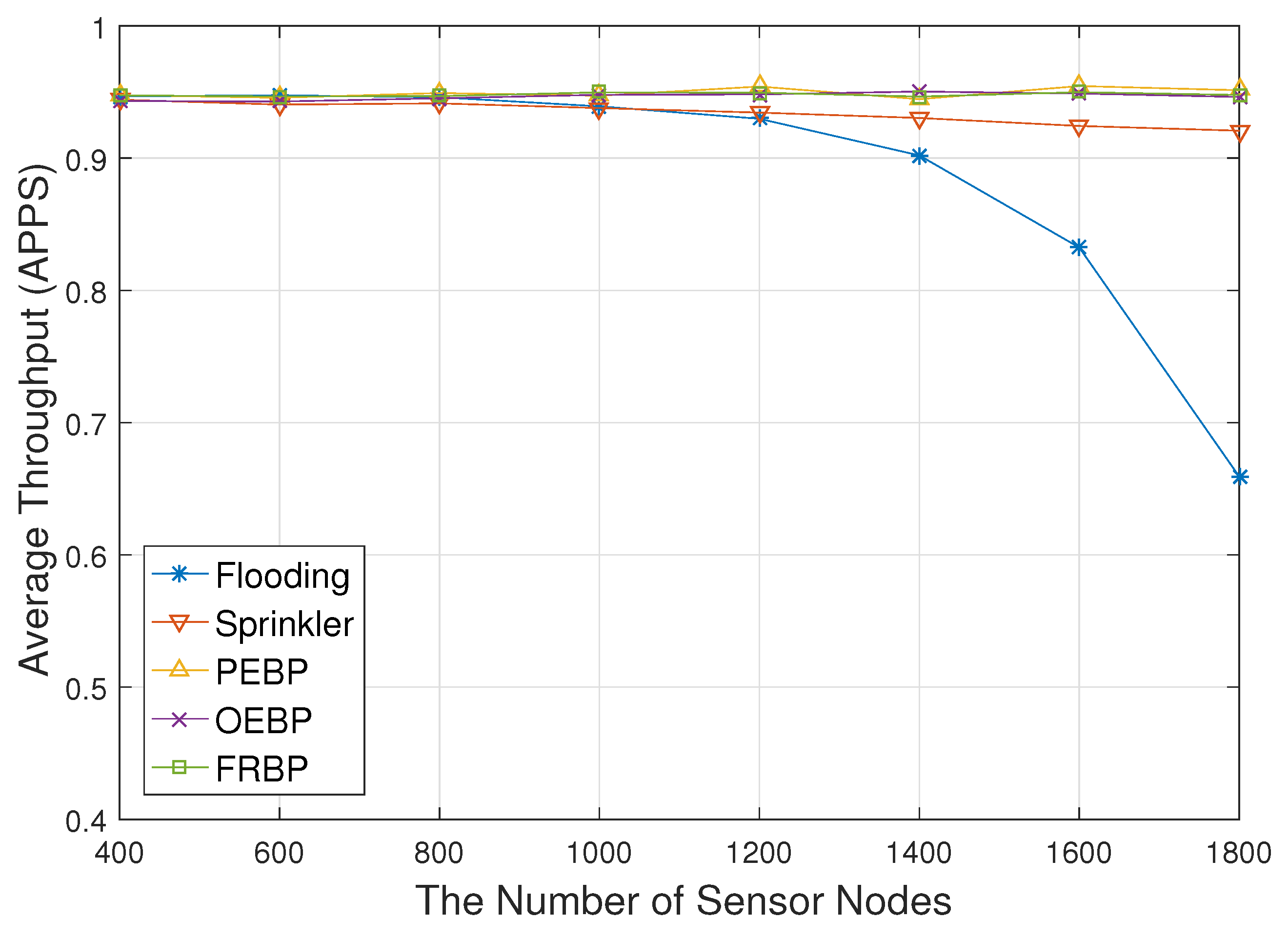
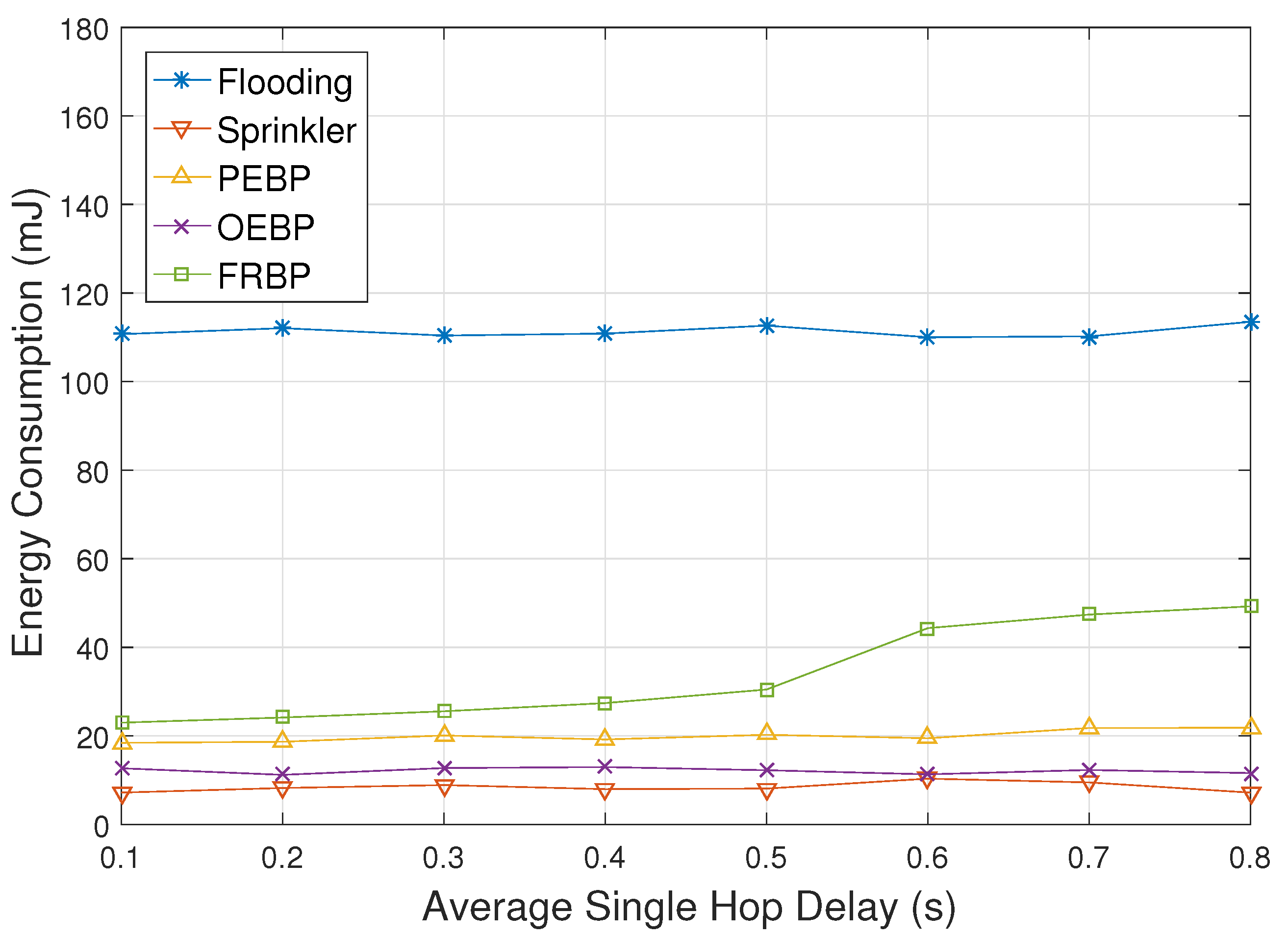
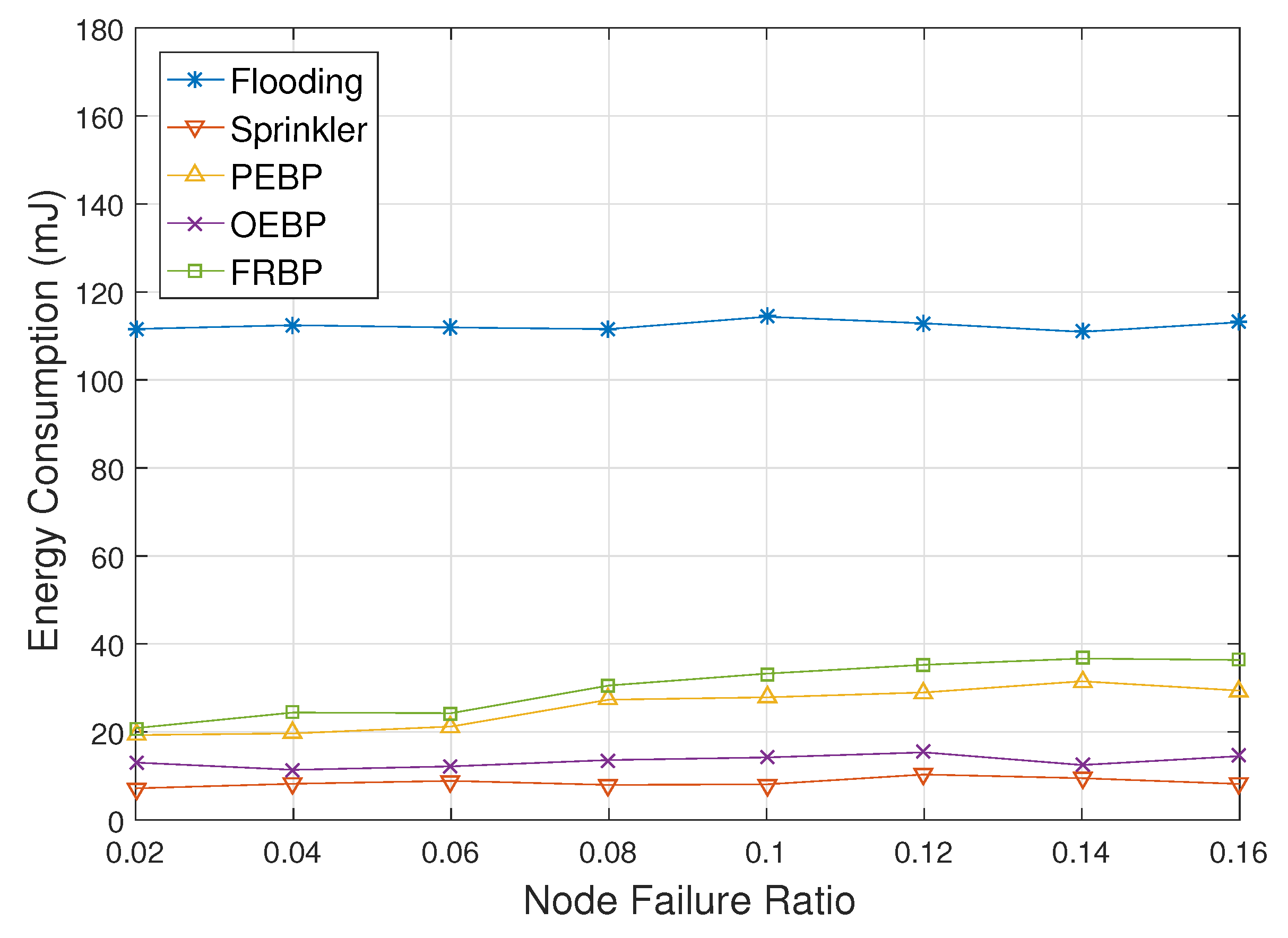
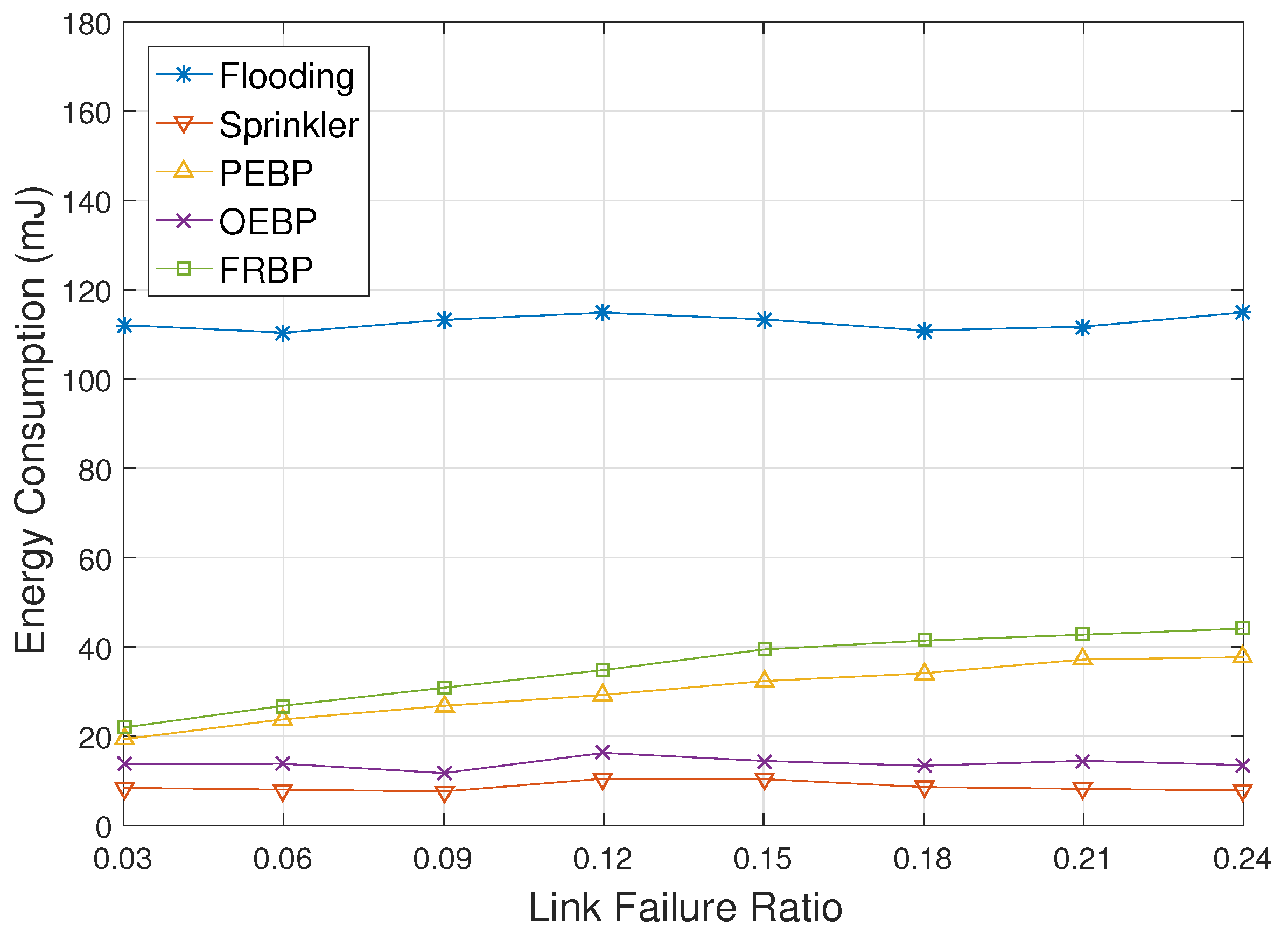
4. Performance Evaluation
5. Conclusions and Further Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Li, Y.; Chen, C.; Song, Y.; Wang, Z. Real-time QoS support in wireless sensor networks: A survey. In Proceedings of the Annual 7th IFAC International Conference on Fieldbuses and Networks in Industrial and Embedded Systems, Toulouse, France, 7–9 November 2007; pp. 373–380. [Google Scholar]
- Akyildiz, I.F.; Vuran, M.C. Wireless Sensor Networks; John Wiley and Sons, Ltd.: River Street Hoboken, NJ, USA, 2010. [Google Scholar]
- Chennakesavula, P.; Ebenezer, J.; Murty, S.S. Real-time routing protocols for wireless sensor networks: A survey. In Proceedings of the Fourth International Workshop on Wireless & Mobile Networks (WIMo), Coimbatore, India, 26–28 October 2012; pp. 141–158. [Google Scholar]
- Alanazi, A.; Elleithy, K. Real-time QoS routing protocols in wireless multimedia sensor networks: Study and analysis. Sensors 2015, 15, 22209–22233. [Google Scholar] [CrossRef] [PubMed]
- He, T.; Stankovic, J.A.; Lu, C.; Abdelzaher, T. SPEED: A stateless protocol for real-time communication in sensor networks. In Proceedings of the 23rd IEEE International Conference on Distributed Computing Systems, Providence, RI, USA, 19–22 May 2003; pp. 46–55. [Google Scholar]
- Li, B.; Kim, K. An (m, k)-firm real-time aware fault-tolerant mechanism in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2012, 8, 905740. [Google Scholar] [CrossRef]
- Felemban, E.; Lee, C.; Ekici, E. MMSPEED: Multipath Multi-SPEED Protocol for QoS guarantee of reliability and timeliness in wireless sensor networks. IEEE Trans. Mob. Comput. 2006, 5, 738–754. [Google Scholar] [CrossRef]
- Chipara, O.; He, Z.; Xing, G.; Chen, Q.; Wang, X.; Lu, C.; Stankovic, J.; Abdelzaher, T. Real-time power-aware routing in sensor networks. In Proceedings of the 14th IEEE International Workshop on Quality of Service, New Haven, CT, USA, 19–21 June 2006; pp. 83–92. [Google Scholar]
- Kandris, D.; Tsioumas, P.; Tzes, A.; Nikolakopoulos, G.; Vergados, D. Power conservation through energy efficient routing in wireless sensor networks. Sensors 2009, 9, 7320–7342. [Google Scholar] [CrossRef] [PubMed]
- Kandris, D.; Tsagkaropoulos, M.; Politis, I.; Tzes, A.; Kotsopoulos, S. Energy efficient and perceived QoS aware video routing over wireless multimedia sensor networks. Ad Hoc Netw. 2011, 9, 591–607. [Google Scholar] [CrossRef]
- Zhao, L.; Kan, B.; Xu, Y.; Li, X. FT-SPEED: A fault-tolerant, real-time routing protocol for wireless sensor networks. In Proceedings of the 2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–25 September 2007; pp. 2531–2534. [Google Scholar]
- Park, H.; Lee, J.; Park, S.; Oh, S.; Kim, S. Multicast protocol for real-time data dissemination in wireless sensor networks. IEEE Commun. Lett. 2011, 15, 1291–1293. [Google Scholar] [CrossRef]
- Hamdaoui, M.; Ramanathan, P. A dynamic priority assignment technique for streams with (m, k)-firm deadlines. IEEE Trans. Comput. 1995, 44, 1443–1451. [Google Scholar] [CrossRef]
- Intanagonwiwat, C.; Govindan, R.; Estrin, D. Directed diffusion: A scalable and robust communication paradigm for sensor networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 56–67. [Google Scholar]
- Naik, V.; Arora, A.; Sinha, P.; Zhang, H. Sprinkler: A reliable and energy efficient data dissemination service for extreme scale wireless networks of embedded devices. IEEE Trans. Mob. Comput. 2007, 6, 777–789. [Google Scholar] [CrossRef]
- Madhusudhana, V.; Gururaj, S.P. A Survey-An Efficient Flooding Scheme for Mitigating Broadcast Storm Problem in Wireless Sensor Network. Int. J. Adv. Res. Comput. Eng. Technol. 2015, 4, 2417–2421. [Google Scholar]
- Chakraborty, S.; Chakraborty, S.; Nandi, S.; Karmakar, S. A Reliable and Total Order Tree Based Broadcast in Wireless Sensor Network. In Proceedings of the 20nd International Conference on Computer & Communication Technology (ICCCT), Allahabad, India, 15–17 September 2011; pp. 618–623. [Google Scholar]
- Clark, B.; Colbourn, C.; Johnson, D. Unit disk graphs. Discret. Math. 1990, 86, 165–177. [Google Scholar] [CrossRef]
- Guo, S.; He, L.; Gu, Y.; Jiang, B.; He, T. Opportunistic flooding in low-duty-cycle wireless sensor networks with unreliable links. IEEE Trans. Comput. 2014, 63, 2787–2802. [Google Scholar]
- Changa, D.; Cho, K.; Choi, N.; Kwon, T.T.; Choi, Y. A probabilistic and opportunistic flooding algorithm in wireless sensor networks. Comput. Commun. 2012, 35, 500–506. [Google Scholar] [CrossRef]
- Byeon, S.; Seo, H.; Kim, J. Contribution-level-based opportunistic flooding for wireless multihop networks. J. Korean Inst. Inf. Sci. Eng. 2015, 42, 791–800. [Google Scholar] [CrossRef]
- Luo, J.; Hu, J.; Wu, D.; Li, R. Opportunistic routing algorithm for relay node selection in wireless sensor networks. IEEE Trans. Ind. Inf. 2015, 11, 112–121. [Google Scholar] [CrossRef]
- Zhang, L.; Sanchez, E.; Rebaudengo, M. Evaluation framework of opportunistic flooding in wireless sensor networks. In Proceedings of the International Conference on Embedded and Ubiquitous Computing, Melbourne, Australia, 24–24 October 2011; pp. 87–94. [Google Scholar]
- Sharma, M.; Singh, Y.; Kumar, N. Opportunistic routing in wireless sensor networks: A comparative analysis. J. Basic Appl. Eng. Res. 2014, 1, 94–98. [Google Scholar]
- The NS-3 Consortium. The ns-3 Network Simulator. Available online: http://www.nsnam.org/ (accessed on 1 August 2017).
- Hill, J.; Culler, D. Mica: A wireless platform for deeply embedded networks. IEEE Micro 2002, 22, 12–24. [Google Scholar] [CrossRef]




| Parameter | Value |
|---|---|
| Simulator | NS-3 |
| Transmission range | 30 m |
| MAC layer | IEEE 802.11 b |
| Network size | 500 m × 500 m |
| The default number of nodes | 1000 |
| Transmitting/receiving power | 3.12 J/2.34 J |
| Desired delivery time deadline | 10 s |
| Desired delivery speed | 70 m/s |
| Real-time requirement | (4, 5)-firm |
| The number of simulation rounds | 20 |
| The number of packets in a round | 80 |
| Packet generation rate | Constant Bit Rate (CBR), 1 packet/s |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, H.; Kim, B.-S.; Kim, K.H.; Shah, B.; Kim, K.-I. A Tree Based Broadcast Scheme for (m, k)-firm Real-Time Stream in Wireless Sensor Networks. Sensors 2017, 17, 2578. https://doi.org/10.3390/s17112578
Park H, Kim B-S, Kim KH, Shah B, Kim K-I. A Tree Based Broadcast Scheme for (m, k)-firm Real-Time Stream in Wireless Sensor Networks. Sensors. 2017; 17(11):2578. https://doi.org/10.3390/s17112578
Chicago/Turabian StylePark, HoSung, Beom-Su Kim, Kyong Hoon Kim, Babar Shah, and Ki-Il Kim. 2017. "A Tree Based Broadcast Scheme for (m, k)-firm Real-Time Stream in Wireless Sensor Networks" Sensors 17, no. 11: 2578. https://doi.org/10.3390/s17112578
APA StylePark, H., Kim, B.-S., Kim, K. H., Shah, B., & Kim, K.-I. (2017). A Tree Based Broadcast Scheme for (m, k)-firm Real-Time Stream in Wireless Sensor Networks. Sensors, 17(11), 2578. https://doi.org/10.3390/s17112578





