Opportunistic Capacity-Based Resource Allocation for Chunk-Based Multi-Carrier Cognitive Radio Sensor Networks
Abstract
:1. Introduction
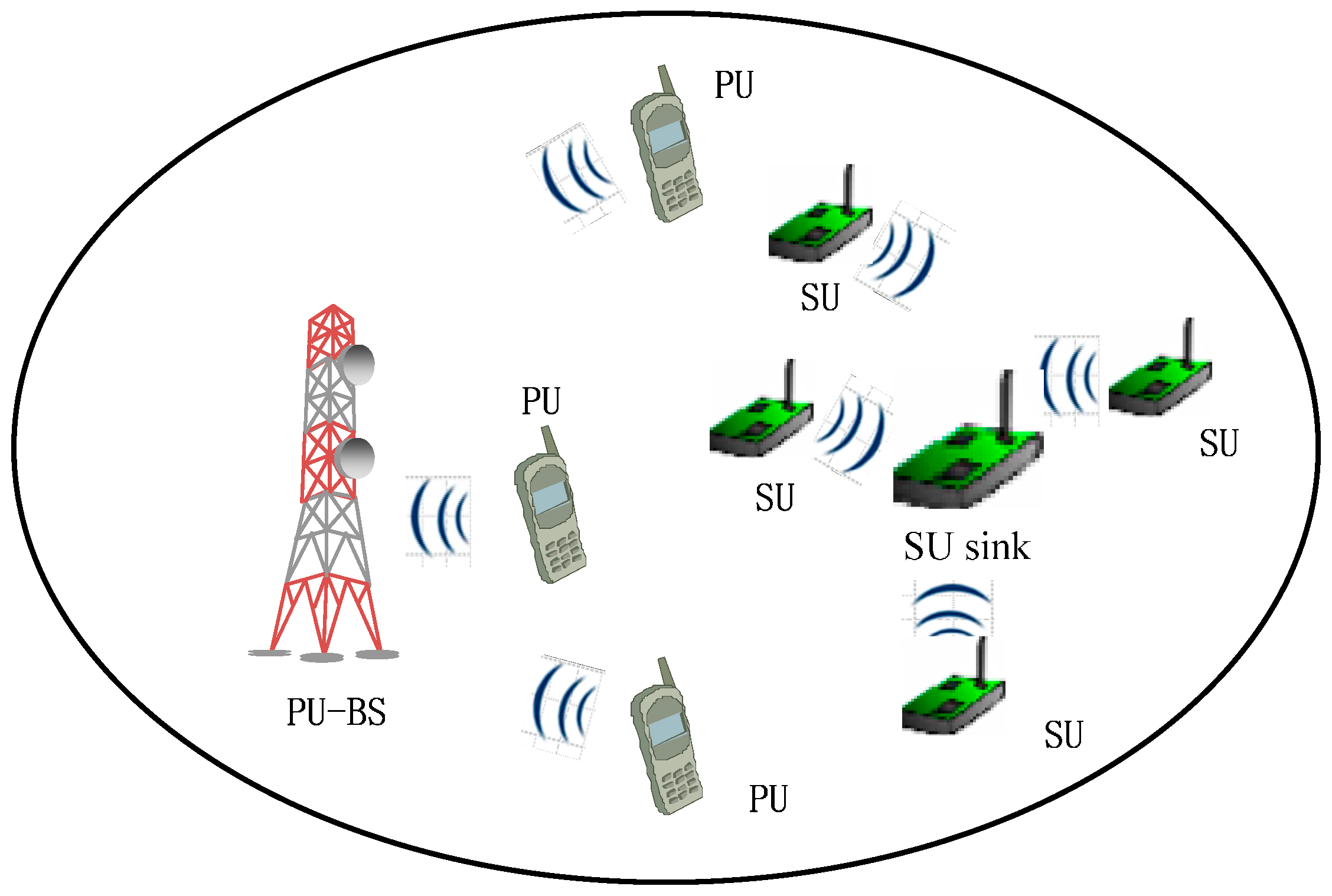
2. System Model
3. Opportunistic Capacity Model for Chunks
4. Opportunistic Capacity-Based Resource Allocation for Chunk-Based Multi-Carrier CRSNs
4.1. Opportunistic Capacity-Based Resource Allocation Model
4.2. Simplification and Solution
| Algorithm 1: The pseudocode for solving algorithm: two step solving algorithm |
 |
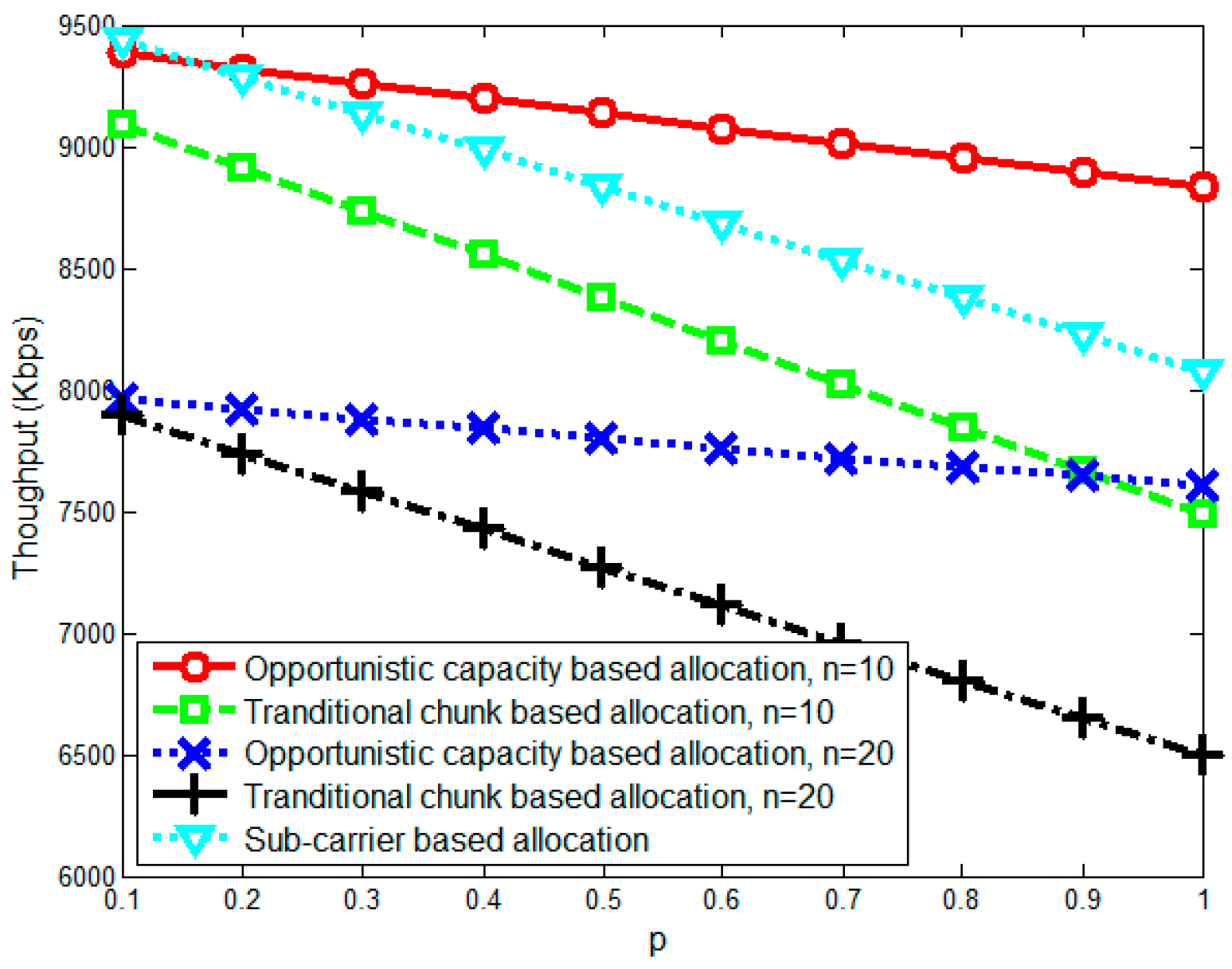
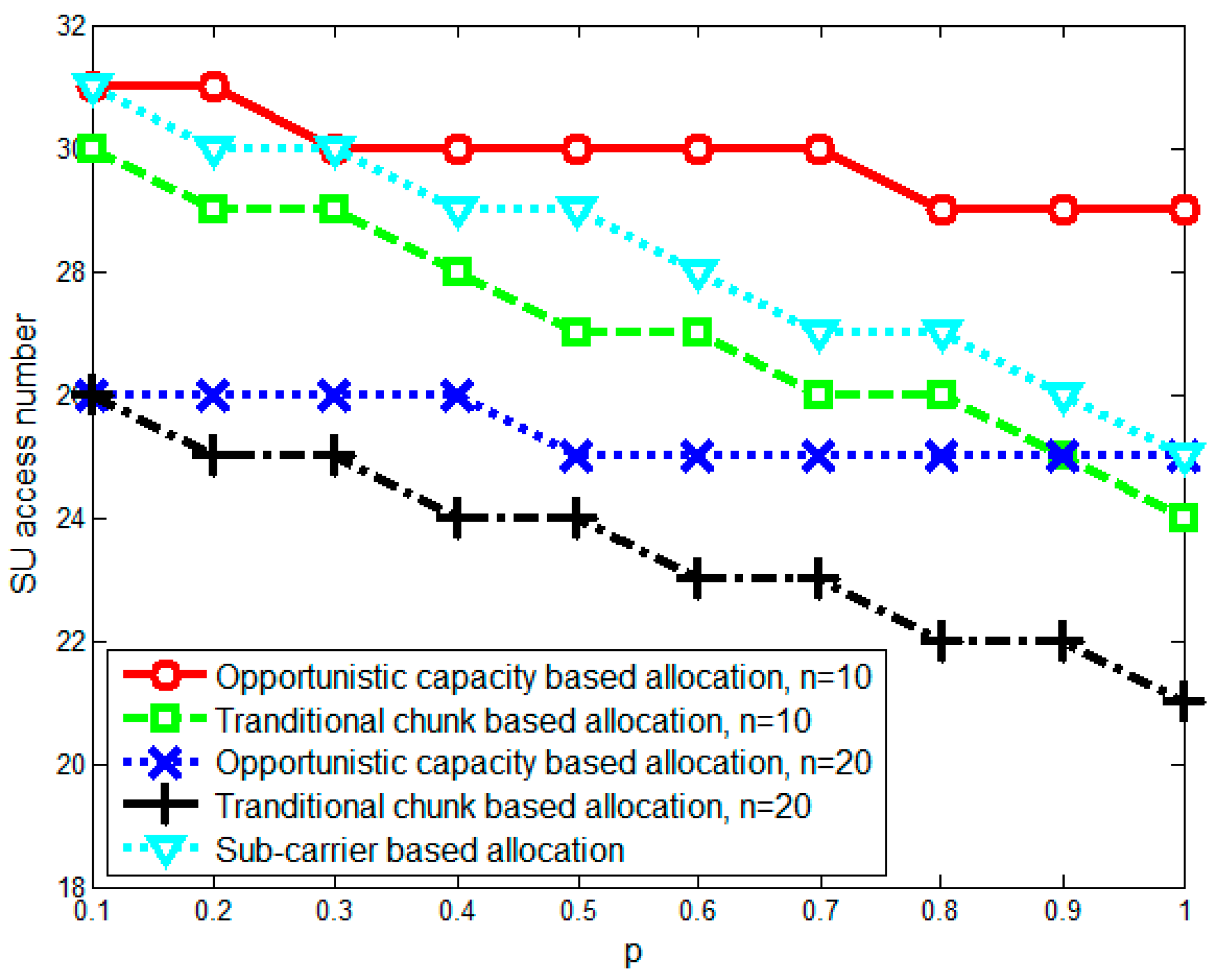
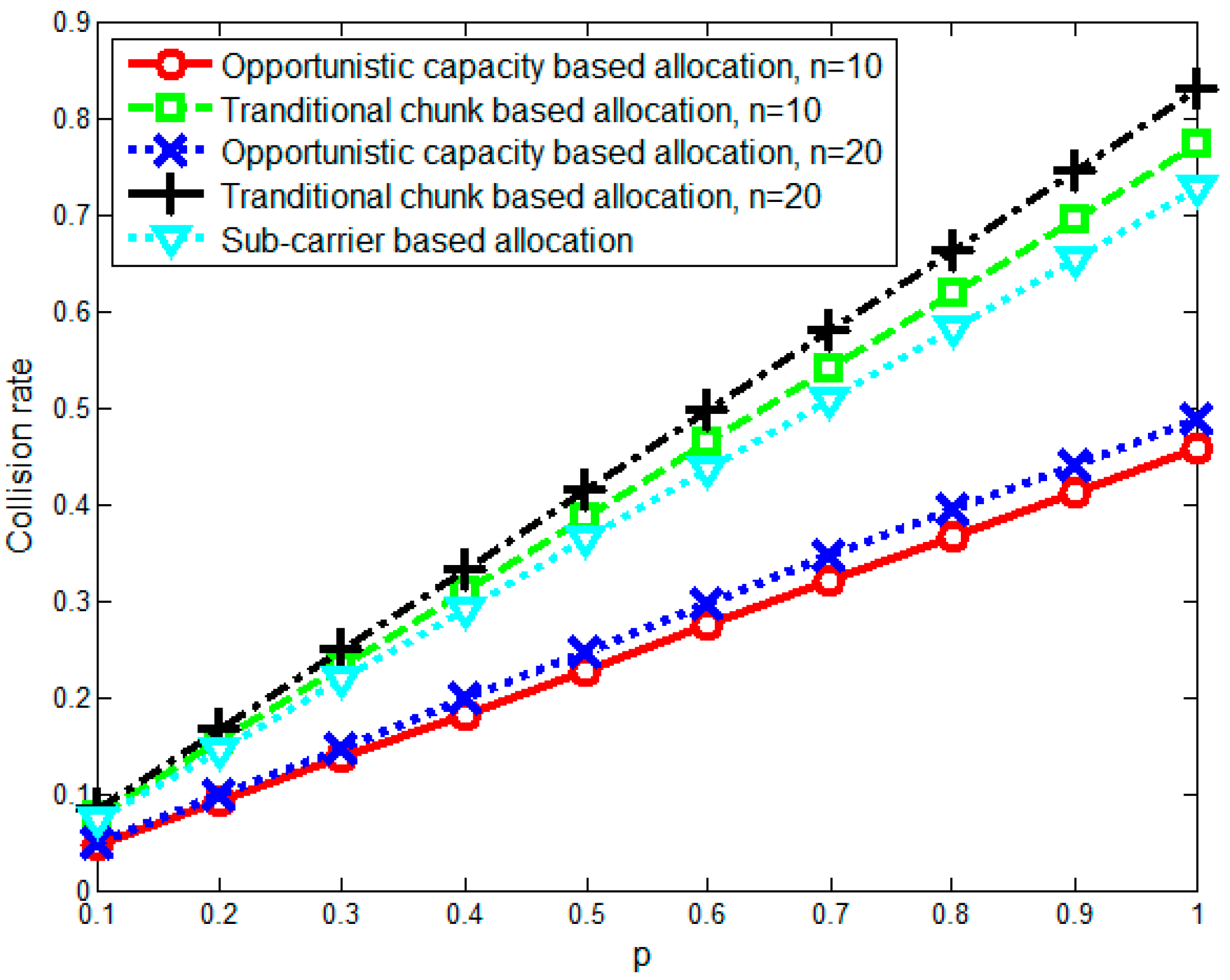
5. Simulation Results
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Iqbal, M.; Naeem, M.; Anpalagan, A.; Ahmed, A.; Azam, M. Wireless Sensor Network Optimization: Multi-Objective Paradigm. Sensors 2015, 15, 17572–17620. [Google Scholar] [CrossRef] [PubMed]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless Sensor Network Survey. Comput. Netw. 2008, 12, 2292–2330. [Google Scholar] [CrossRef]
- Mustapha, I.; Mohd, A.B.; Rasid, M.F.; Sali, A.; Mohamad, H. An Energy-Efficient Spectrum-Aware Reinforcement Learning-Based Clustering Algorithm for Cognitive Radio Sensor Networks. Sensors 2015, 15, 19783–19818. [Google Scholar] [CrossRef] [PubMed]
- Lin, Y.; Wang, C.; Wang, J.X.; Dou, Z. A Novel Dynamic Spectrum Access Framework Based on Reinforcement Learning for Cognitive Radio Sensor Networks. Sensors 2016, 16, 1675. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.X.; Hong, Z.M.; Wang, G.D.; Huang, J. High-Order Hidden Bivariate Markov Model: A Novel Approach on Spectrum Prediction. In Proceedings of the 2016 International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 27–31.
- Ding, G.R.; Wu, Q.H.; Yao, Y.D.; Wang, J.L.; Chen, Y.Y. Kernel-Based Learning for Statistical Signal Processing in Cognitive Radio Networks: Theoretical Foundations, Example Applications, and Future Directions. IEEE Signal Process. Mag. 2013, 4, 126–136. [Google Scholar] [CrossRef]
- Sun, H.J.; Nallanathan, A.; Wang, C.X.; Chen, Y.F. Wideband Spectrum Sensing for Cognitive Radio Networks: A Survey. IEEE Wirel. Commun. 2013, 2, 74–81. [Google Scholar]
- Sharma, S.K.; Bogale, T.E.; Chatzinotas, S.; Ottersten, B.; Le, L.B.; Wang, X.B. Cognitive Radio Techniques Under Practical Imperfections: A Survey. IEEE Commun. Surv. Tutor. 2015, 4, 1858–1884. [Google Scholar] [CrossRef]
- Akan, O.B.; Karli, O.B.; Ergul, O. Cognitive Radio Sensor Networks. IEEE Netw. 2009, 4, 34–40. [Google Scholar] [CrossRef]
- Goh, H.G.; Kwong, K.H.; Shen, C.; Michie, C.; Andonovic, I. CogSeNet: A Concept of Cognitive Wireless Sensor Network. In Proceedings of the 2010 IEEE Conference on Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2010; pp. 939–940.
- Ding, G.R.; Wang, J.L.; Wu, Q.H.; Song, F.; Chen, Y.Y. Spectrum Sensing in Opportunity-Heterogeneous Cognitive Sensor Networks: How to Cooperate? IEEE Sens. J. 2013, 11, 4247–4255. [Google Scholar] [CrossRef]
- Filio, O.; Primak, S.; Kontorovich, V.; Shami, A. On a Cognitive Radio Network’s Random Access Game with a Poisson Number of Secondary Users. IEEE Commun. Lett. 2015, 10, 1818–1821. [Google Scholar] [CrossRef]
- Namvar, N.; Afghah, F. Spectrum Sharing in Cooperative Cognitive Radio Networks: A Matching Game Framework. In Proceedings of the 2015 Information Sciences and Systems (CISS), Baltimore, MD, USA, 18–20 March 2015; pp. 309–413.
- Li, Y.; Zhao, L.L.; Wang, C.G.; Daneshmand, A.; Hu, Q. Aggregation-Based Spectrum Allocation Algorithm in Cognitive Radio Networks. In Proceedings of the 2012 Network Operations and Management Symposium (NOMS), Maui, HI, USA, 16–20 April 2012; pp. 506–509.
- Teotia, V.; Kumar, V.; Minz, S. Conflict Graph Based Channel Allocation in Cognitive Radio Networks. In Proceedings of the 2015 Reliable Distributed Systems Workshop (SRDSW), Montreal, QC, Canada, 28–30 September 2015; pp. 52–56.
- Wu, F.; Mao, Y.; Leng, S.; Huang, X. A Carrier Aggregation Based Resource Allocation Scheme for Pervasive Wireless Networks. In Proceedings of the 2011 Autonomic and Secure Computing (DASC), Sydney, Australia, 12–14 December 2011; pp. 196–201.
- Li, C.B.; Liu, W.; Liu, Q.; Li, C. Spectrum Aggregation Based Spectrum Allocation for Cognitive Radio Networks. In Proceedings of the 2014 Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 1626–1631.
- Jalaeian, B.; Zhu, R.; Motani, M. An Optimal Scheduling Framework for Concurrent Transmissions in Wireless Cognitive Radio Networks. Telecommun. Syst. 2015, 1, 169–177. [Google Scholar] [CrossRef]
- Saleem, Y.; Rehmani, M.H. Primary Radio User Activity Models for Cognitive Radio Networks: A Survey. J. Netw. Comput. Appl. 2014, 1, 1–16. [Google Scholar] [CrossRef]
- Riihijärvi, J.; Nasreddine, J.; Mähönen, P. Impact of Primary User Activity Patterns on Spatial Spectrum Reuse Opportunities. In Proceedings of the 2010 European Wireless Conference (EW), Lucca, Italy, 12–15 April 2010; pp. 962–968.
- Csurgai, L.; Bito, J. Primary and Secondary User Activity Models for Cognitive Wireless Network. In Proceedings of the 2011 International Conference on Telecommunications (ConTEL), Zagreb, Croatia, 15–17 June 2011; pp. 301–306.
- Khabazian, M.; Aissa, S.; Tadayon, N. Performance Modeling of a Two-Tier Primary-Secondary Network Operated with IEEE 802.11 DCF Mechanism. IEEE Trans. Wirel. Commun. 2012, 9, 3047–3057. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, J. Chunk-Based Resource Allocation in OFDMA Systems—Part I: Chunk Allocation. IEEE Trans. Commun. 2009, 9, 2734–2744. [Google Scholar]
- Zhu, H.; Wang, J. Chunk-Based Resource Allocation in OFDMA Systems—Part II: Joint Chunk, Power and Bit Allocation. IEEE Trans. Commun. 2012, 2, 499–509. [Google Scholar] [CrossRef]
- Zhao, Y.X.; Anjum, M.N.; Song, M.; Xu, X.H.; Wang, G.D. Optimal Resource Allocation for Delay Constrained Users in Self-Coexistence WRAN. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 6–10 December 2015; pp. 387–391.
- Xu, D.; Li, Q. Energy Efficient Joint Chunk and Power Allocation for Chunk-Based Multi-Carrier Cognitive Radio Networks. In Proceedings of the 2015 Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 568–572.
- Xu, D.; Li, Q.; Sun, X. Resource Allocation for Chunk-Based Multi-Carrier Cognitive Radio Networks. In Proceedings of the 2014 International Symposium on Wireless Personal Multimedia Communications (WPMC), Sydney, Australia, 7–10 September 2014; pp. 445–450.
- Zhao, Y.X.; Pradhan, J.; Wang, G.D.; Huang, J. Experimental Approach: Two-Stage Spectrum Sensing Using GNU Radio and USRP to Detect Primary User’s Signal. In Proceedings of the 2016 Annual ACM Symposium on Applied Computing (SAC), Pisa, Italy, 4–8 April 2016; pp. 2165–2170.
- López, M.; Casadevall, F. Time-Dimension Models of Spectrum Usage for the Analysis, Design, and Simulation of Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2013, 5, 2091–2104. [Google Scholar] [CrossRef]
- Chen, X.L. Queue Theory in Modern Communications; Electronic Industry Press: Beijing, China, 1999; pp. 145–146. [Google Scholar]
- Ibe, O. Markov Processes for Stochastic Modeling; Chapman & Hall: London, UK, 2013; pp. 173–174. [Google Scholar]
- Casella, G.; Berger, R.L. Statistical Inference; Duxbury: Belmont, MA, USA, 2002; pp. 284–287. [Google Scholar]
- Foschini, G.J.; Salz, J. Digital Communications over Fading Radio Channels. Bell Syst. Tech. J. 1983, 2, 429–456. [Google Scholar] [CrossRef]
- Liu, B.D.; Zhao, R.Q. Stochastic Programming and Fuzzy Programming; Tsinghua University Press: Beijing, China, 1998; pp. 66–67. [Google Scholar]
- Wang, R.; Lau, V.K.N.; Lv, L.J.; Chen, B. Joint Cross-Layer Scheduling and Spectrum Sensing for OFDMA Cognitive Radio Systems. IEEE Trans. Wirel. Commun. 2009, 5, 2410–2416. [Google Scholar] [CrossRef]
- Ding, G.R.; Wu, Q.H.; Wang, J.L. Sensing Confidence Level-Based Joint Spectrum and Power Allocation in Cognitive Radio Networks. Wirel. Pers. Commun. 2013, 1, 283–298. [Google Scholar] [CrossRef]
- Stephen, B.; Lieven, V. Convex Optimization; Cambridge University Press: London, UK, 2004; pp. 445–454. [Google Scholar]


| Parameters | Values |
|---|---|
| Maximum tolerable error rate | |
| SU number | 40 |
| Sub-carrier bandwidth | 20 KHz |
| Sub-carrier number | 400 |
| Sub-carrier number in each chunk | 10–20 |
| Rician fading channel factor | 3 |
| Noise power | −111 dBm |
| Chunk capacity change rate | 0.1~1 |
© 2017 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, J.; Zeng, X.; Jian, X.; Tan, X.; Zhang, Q. Opportunistic Capacity-Based Resource Allocation for Chunk-Based Multi-Carrier Cognitive Radio Sensor Networks. Sensors 2017, 17, 175. https://doi.org/10.3390/s17010175
Huang J, Zeng X, Jian X, Tan X, Zhang Q. Opportunistic Capacity-Based Resource Allocation for Chunk-Based Multi-Carrier Cognitive Radio Sensor Networks. Sensors. 2017; 17(1):175. https://doi.org/10.3390/s17010175
Chicago/Turabian StyleHuang, Jie, Xiaoping Zeng, Xin Jian, Xiaoheng Tan, and Qi Zhang. 2017. "Opportunistic Capacity-Based Resource Allocation for Chunk-Based Multi-Carrier Cognitive Radio Sensor Networks" Sensors 17, no. 1: 175. https://doi.org/10.3390/s17010175





