1. Introduction
It has been widely acknowledged that waveform design is critically important for radar performance in areas such as target detection, clutter suppression, and target identification, especially when in the presence of channel noise and clutter [
1,
2]. However, optimal radar waveform is highly task-dependent and is also affected by the model of the target and surrounding environments. In the 1960s, some early research on radar waveform optimization was conducted [
1,
2,
3,
4,
5]. All the early works assumed a point target model. However, as radar bandwidth and range resolution improve, the illuminated target usually exceeds one resolution cell. Thus, the point target assumption does not hold and should be replaced by an extended target model [
6]. Therefore, the paper considers waveform design for extended targets.
Generally, radar waveform design methods can be broken into four categories: (1) information theory based design [
7,
8,
9,
10,
11,
12,
13,
14]; (2) ambiguity-function based design [
15,
16,
17]; (3) detection-probability based design [
18,
19,
20]; and (4) signal-to-clutter-plus-noise ratio (SCNR) based design [
21,
22,
23,
24,
25,
26,
27]. Information theoretic methods were inspired by the very essence of radar—acquiring target related information [
7]. Mutual information (MI) criteria between the target return and the target impulse response (TIR) was later used for radar parameter estimation and target identification [
8,
9,
10,
11,
12,
13,
14]. The relationship between minimum mean squared error and MI metrics was discussed in [
9,
11], and the case of multiple extended targets was considered in [
12]. Ambiguity-function based methods [
15,
16,
17] design the transmitted waveform by reshaping its ambiguity function—suppressing the Doppler-range (angle-Doppler-range, in the MIMO radar case) region where targets might emerge. These methods require prior information about the range and Doppler distribution of clutter and/or jamming—which is more than the statistical characteristics that would be needed in the detection-probability and SCNR based methods. However, the methods based on ambiguity functions deal mainly with point targets, which is somewhat off the topic of this paper.
The basic idea of detection-probability based methods is to optimize the transmitted waveform to maximize detection probability for a given false alarm rate. It has been shown that a simple single-tone signal is optimal if the target’s Doppler is unknown and is uniformly distributed over the Doppler bandwidth [
18]. Steven Kay [
19] obtained an analytical solution of the optimal waveform for Gaussian-distributed point target using the Neyman-Pearson criterion. The results in [
19] were heuristically extended to the multistatic radar case [
20]. However, detection probability based methods encounters difficulties with extended targets and waveform-dependent clutter, because in these cases the explicit probability density function of the radar return is hard to obtain, and further analysis becomes very difficult. Fortunately, we can resort to SCNR based methods, whose optimization criterion is to maximize the output SCNR. Bell derived an eigen-waveform solution for a clutter-free environment with energy constraints, for the first time [
8]. However, in practice, radar returns are usually contaminated by clutter coupled with the transmitted waveform. This coupling poses a big challenge for optimal waveform design. To overcome the problem, Pillai [
22,
23] proposed an iterative algorithm—which is also called the
eigen-iterative algorithm in some literature—to determine the optimal transmit pulse and receiver impulse response. This iterative technique was later extended to the discrete time domain [
24] and the multiple-input multi-output (MIMO) radar case [
26]. However, the technique in [
22,
23,
24] is flawed, in that it cannot guarantee a non-decreasing SCNR at each iteration step. Chen
et al. [
26] solved this problem under a total energy constraint through alternate optimization, improving the SCNR at each iteration, and thus guaranteeing its convergence.
However, much existing work [
8,
10,
11,
12,
13,
14,
16,
17,
18,
19,
20,
22,
23,
24,
25,
26,
27] is based on the assumption that radar transmitted signals can be modulus-arbitrary—something which is still difficult to implement in present radar systems—limited by the linear range of the radio frequency (RF) power amplifier and the capabilities of present RF antennas [
5,
21,
28,
29]. Accordingly, the design of radar waveform with limited dynamic range was considered in [
5,
28], and constant-modulus waveform design was discussed in [
21,
29]. Note that constant-modulus waveform is important for power efficient radars, such as airborne and spaceborne radars. In [
21], an adaptive phase-coded waveform design was proposed, but it did not take the clutter into account, which hampered its practicability. Reference [
29] optimizes a phase-modulated waveform by approaching the optimal energy spectral density in the mean-square sense, but the method requires prior knowledge of the power spectral density of channel noise and clutter. In this paper, we further extend the design of constant-modulus waveforms in discrete time domain in the presence of clutter.
As is well known, the TIR is highly range and orientation sensitive [
6]. Small variations in target range or orientation relative to the radar might lead to significant TIR changes. Therefore, we think that a deterministic and precisely known TIR is not realistic. Instead, we consider the TIR in a statistical way. This assumption has also been made in [
8,
9,
10,
11,
12,
13,
14,
18,
19,
20,
26,
29,
30]. Note that, as will be demonstrated later, our methods are suitable for the deterministic target model as well. In addition, we concentrate on single-input single-output (SISO) radar in this paper: the extension of our methods to the MIMO radar case is straightforward.
The main contributions of this paper are summarized as follows. We propose two iterative constant-modulus waveform design methods, both using alternate optimization of the transmitted waveform and the receiving filter. One of these methods yields arbitrary-phase waveforms, while the other yields quadrature phase shift keying (QPSK) waveforms. We also discuss the relationship between a non-convex optimization problem and the corresponding convex problem that results after semi-definite relaxation (SDR), which could be instructive to similar optimization problems in signal processing fields.
The rest of the paper is organized as follows.
Section 2 presents the radar signal model and formulates the signal design problem. In
Section 3, two iterative constant-modulus waveform design methods are proposed. Detailed performance analysis of our methods is provided in
Section 4. In
Section 5, we show the results of numerical simulations and demonstrate the effectiveness of our proposed algorithms. Finally, conclusions are presented in
Section 6.
Notations: Vectors and matrices are denoted by boldface lowercase and uppercase letters, respectively. Superscript T, *, and H denote transpose, conjugation and Hermitian transpose of a vector/matrix, respectively. is the unity matrix, whereas and ( and ) indicate () matrices whose elements are all 0 and 1, respectively. The subscript may be omitted if it does not cause confusion in the matrix/vector size. represents the element of matrix A located at the mth row and nth column. or represents the nth component of vector z. denotes the segment of from the ith element to jth element. denotes the expected value of a random variable. We write , , and for the real part, imaginary part and modulus of a complex scalar/matrix, respectively. denotes the ith largest eigenvalue of A and denotes the corresponding eigenvector. () means that matrix A is Hermitian positive semi-definite (positive definite). means that . is the imaginary unit. and designate the complex and real normal distributions, respectively.
2. Signal Model and Problem Formulation
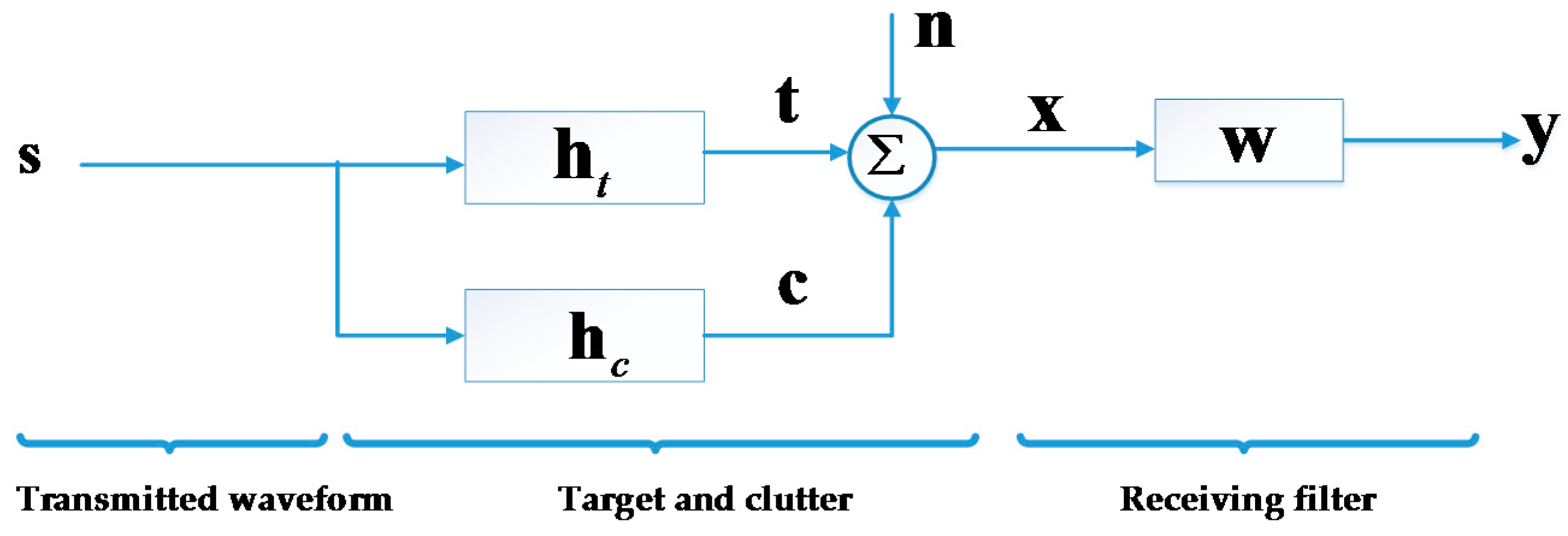
In this paper, we use the discrete baseband signal model illustrated in
Figure 1. In this figure,
denotes the transmitted waveform;
and
are the impulse response of target and clutter, respectively;
denotes the sum of noise and interference/jamming with covariance matrix
;
denotes the returns from target and ambient clutter, while
w denotes the receiving filter vector. In a practical radar system,
is converted to an analog waveform, modulated to RF, and transmitted. Inversely, the returns are received, demodulated and down-sampled to a discrete vector signal. In this paper, we focus on the discrete baseband signal in the time domain and do not discuss continuous signals or the frequency domain further.
As shown in
Figure 1, we model the clutter return
c as the output of a random linear time invariant (LTI) filter whose impulse response
can be regarded as a wide sense stationary (WSS) random vector with covariance matrix
. As mentioned in
Section 1, we consider
in a statistical way [
8,
9,
10,
11,
12,
13,
14,
18,
19,
20,
26,
29,
30] and its covariance matrix is denoted as
. We have assumed that the target is static (or equivalently, that the Doppler shift has been precisely measured and compensated), which is also implied in
Figure 1. The assumption of the zero-Doppler target has also been made in [
8,
9,
10,
11,
12,
13,
14,
19,
22,
23,
24,
25,
26,
27,
29]. According to [
19], if we obtain the optimal waveform with this model, improved performance will result with the optimized waveform in the moving target case as well. We will explore the moving target case in the future.
According to our model, the returns can be formulated as:
where
denotes the convolution operator. The matrix form of Equation (1) is:
where
and
are the target and clutter convolution matrices, and are shown in Equations (3) and (4), respectively. Note that the differences between Equations (3) and (4) come from the ubiquity of the clutter, because anything in the illuminated area of the radar that does not interest us can be viewed as clutter [
26]. From Equation (3), we obtain
, where
. We use function
to represent the relationship between
and
.
From Equation (4), we define vector as:
It is apparent that , , and , which are the length of , , and , respectively, satisfy the following identities:
Using Equation (2), the receiver output can be expressed as:
where the target return is
, and the sum of the clutter return and channel noise is
. Considering the statistical property of the clutter and target, it is necessary to take the expectation value of the clutter return and target return. Thus, the SCNR of the output signal can be written as:
where, for notational simplicity, we let
Define
,
, and
. With the fact that
, we have
Letting
,
can then be written as
. It follows that
Moreover, the definition of
produces
, and
Use
to represent the relationship between
and
in Equation (12). Define
, and
, then we have
, and
It should be noted that, even though Equations (8) and (10)–(14) are obtained based on the statistical target assumption, they also hold for the deterministic extended target. The only difference is that the rank of
in the deterministic case will be 1. Equations (10)–(14) provide an easy analytical way to compute matrices
,
,
, and
, whereas the randomization method presented in [
26] to compute these matrices suffers from inaccuracy and heavy computation. On the basis of Equations (8) and (10)–(14), our next goal is to optimize
s under the constant-modulus constraint, to maximize SCNR.
5. Results
In this section, we demonstrate the effectiveness of the proposed methods. The simulation parameters are as follows. The length of
is
, while the phase coding length of the transmitted waveform is
. Without any loss of generality, we let the noise covariance matrix be
, with
. The sample number in the randomization approach is
K = 10,000. As in [
26], we use a random phase-coded signal as the initial transmitted waveform.
is modeled as being the covariance matrix of the output of a linear time invariant (LTI) filter with impulse response
, whose input signal is complex Gaussian white noise with unit variance.
is assumed to be:
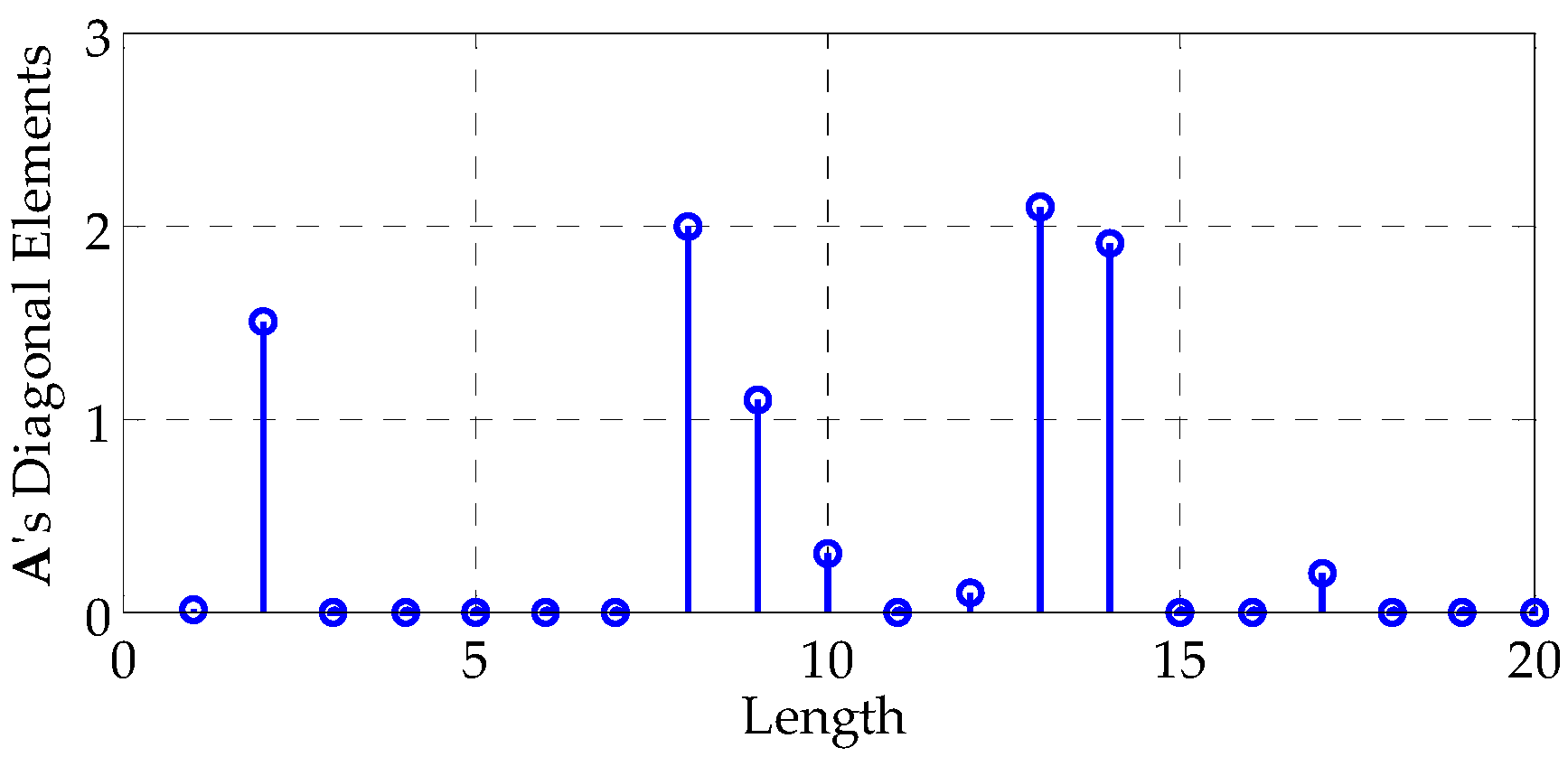
The element values of
are illustrated graphically in
Figure 3a. We denote the matrix in
Figure 3a by
and further let
=
, where
can be considered to be the clutter power. Thereby, we define the clutter-to-noise ratio (CNR) as
. Without specific statements, CNR is set to 10 dB. The iteration number starts at 1 and increases every time we compute Equation (16).
We will now test and verify the performances of the proposed Algorithms 1 and 2 in two cases: the statistical target case and the deterministic target case.
5.1. Statistical Target Case
In this subsection, we consider a statistical
. To guarantee positive semi-definiteness, we generate
using
where
is a matrix whose elements are generated as independent and identically distributed (i.i.d.) circular complex Gaussian random variables with unit variance, except for the diagonal elements, which are shown in
Figure 4. Note that this approach to generate
is similar to the one in [
26]. The considered target has five significant reflection centers and is similar to the SR-71 aircraft model [
25].
Figure 3b illustrates the elements in
. The diagonal elements of
(and
) can naturally be chosen differently. The parameters chosen here are simply a common example.
As a contrast, we also present the waveform design technique with the total energy constraint proposed in [
26]—which also cyclically optimizes the transceiver pair, but uses Equation (18) to compute
s in terms of
w—instead of solving the complicated optimization problems posed by Equation (19) or (21). Consequently, it cannot guarantee the constant modulus property, which hampers the practicability of the designed waveforms. Nevertheless, the absence of the constant modulus constraint leads to a better SCNR performance with extra degrees of freedom. Additionally, to highlight the advantages of our optimization technique, we define the following discrete LFM signal:
We take in our simulation. Correspondingly, we set the vector obtained with Equation (16) as the matched filter for .
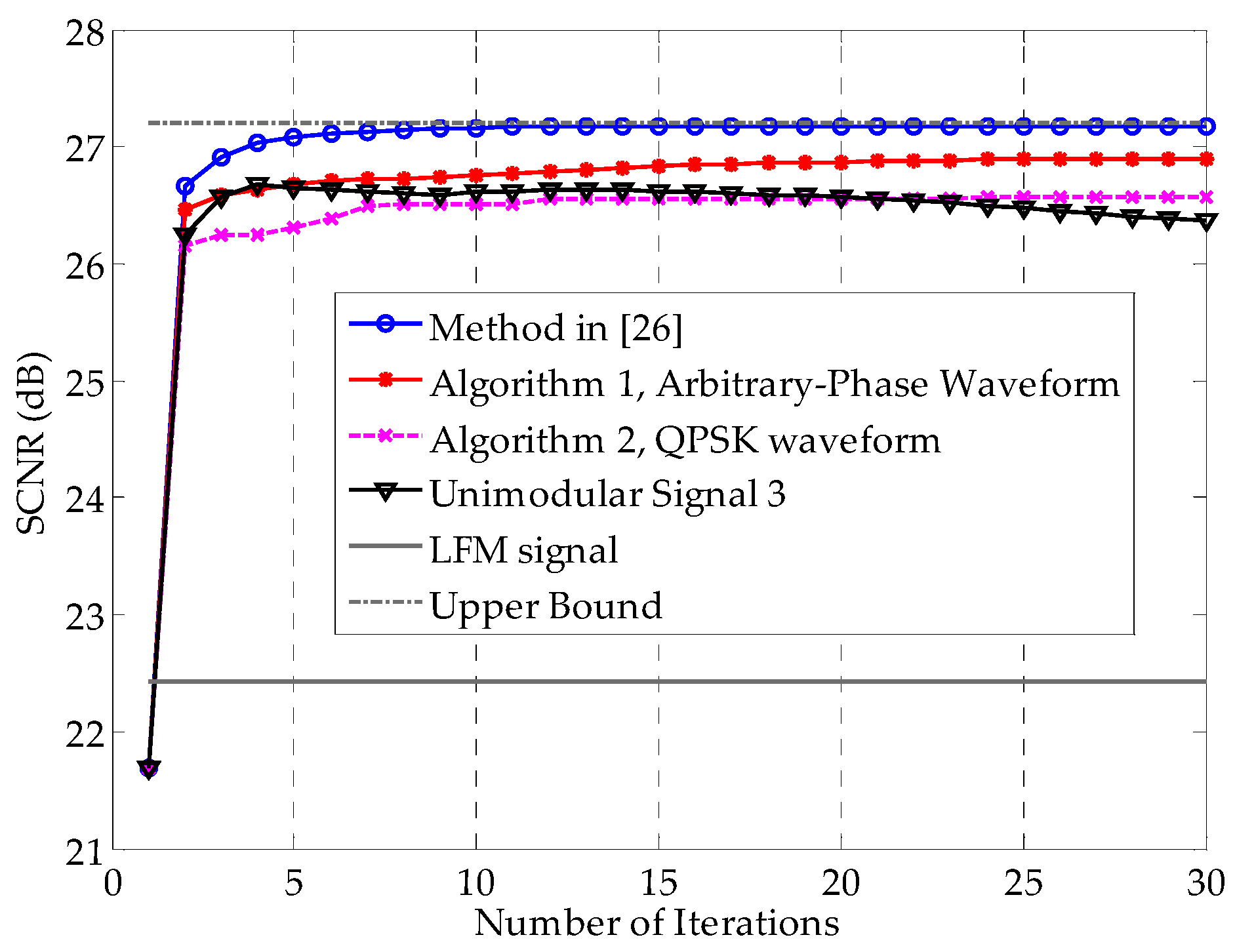
Figure 5 shows the SCNR performances as a function of the number of iterations. The method in [
26], as was expected, converges to the best SCNR among these methods, benefiting from the additional degree of freedom offered by the envelope flexibility. Note that Algorithm 1 also converges fast and has only a 0.28 dB SCNR performance loss compared with the method in [
26] after convergence. Generally speaking, with the benefit of the constant modulus property, the SCNR loss of 0.28 dB is tolerable. Compared with the method in [
26], Algorithm 2 shows a 0.61 dB SCNR loss, with improved implementation. The Unimodular Signal 3, which uses the phases of the results of method in [
26], requires fewer computations, without any convex optimization problems to solve. However, its performance cannot be trusted, even though it performs moderately in this example. As
Figure 5 shows, it might end up with a worse result than Algorithm 2. Nevertheless, it also implies that a unimodular signal with the phases of the first iteration’s result using the method in [
26] is a reasonable initial waveform for Algorithm 1.
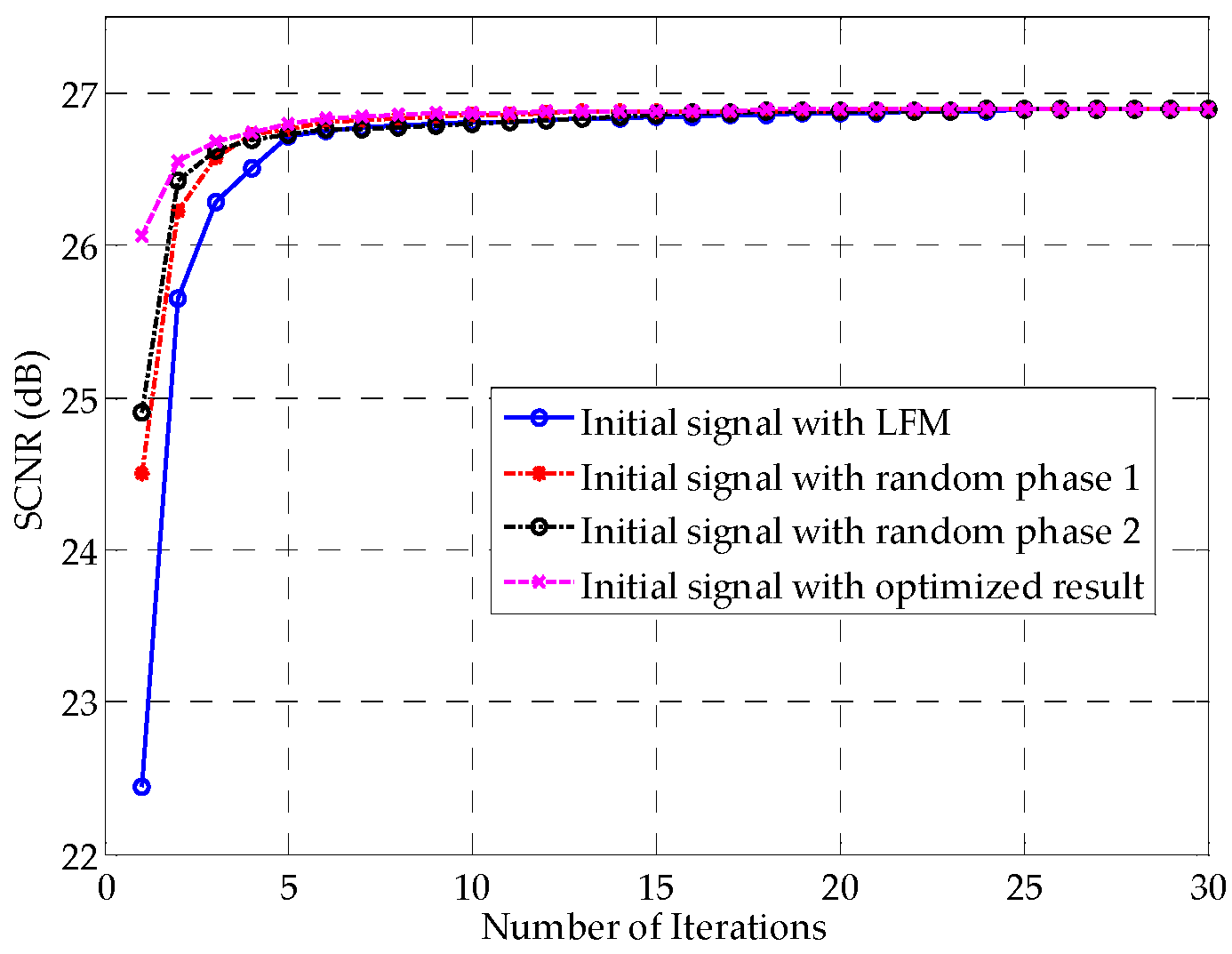
Figure 6 verifies this notion. Among the four initially used waveforms, the one with the preliminary optimized result of the method in [
26]—plotted with the red dashed line—converges the fastest. The LFM signal represented in Equation (36) has the worst initial SCNR and converges the slowest in this example, revealing that the LFM signal is not as advantageous for extended targets as it is for point targets.
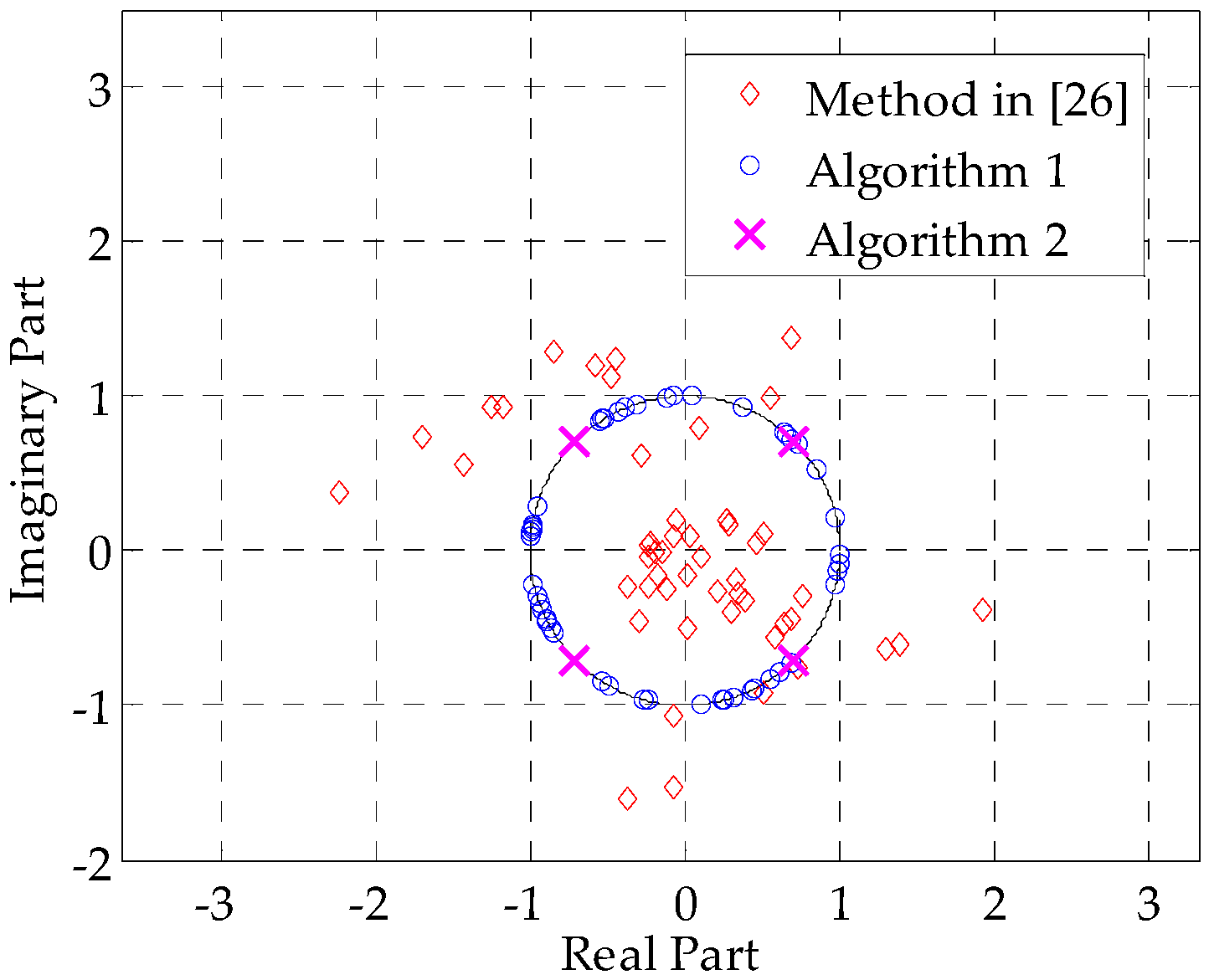
Figure 7 presents the real and imaginary parts of the optimized signals obtained by different methods. One can clearly see that the method in [
26]—marked by red diamonds—cannot guarantee the constant modulus property of the designed signal. In contrast, the results of Algorithm 1 are unimodular and lie on the unit circle, whereas the results of Algorithm 2 are fixed to four phase points, which validates our constraints for the constant-modulus signal and QPSK signal.
Figure 8 shows the SCNR performances of different methods, as a function of CNR. It is intuitive that, as the CNR increases, the SCNR performance worsens correspondingly. One can see that Algorithms 1 and 2 can closely approximate the upper bound over a large range of CNRs. Compared with the LFM signal in
Figure 8, our optimization technique could achieve approximately a 5 dB SCNR gain.
5.2. Deterministic Target Case
In this subsection, we assume that the TIR
is deterministic and known. For demonstration,
is set as the sequence shown in
Figure 4. In this case,
is a rank-one matrix. The other parameters remain the same as in
Section 5.1. We now briefly introduce a discrete-time version of the
eigen-iterative algorithm in [
22]. This algorithm was not discussed in
Section 5.1, because it is not easily extended to a statistical target case. In this case of a deterministic and known TIR, the SCNR expression is reduced from Equation (8) to
where function
is defined in
Section 2. Similar with Equation (15), the optimal receiving filter in terms of
s is
Substituting Equation (38) into Equation (37) yields:
To maximize the new objective function in Equation (39), it seems that we just need to take
s as:
However, the matrix in Equation (40) is also a function of
s. The authors in [
22] proposed to cyclically update
s to approach the optimally transmitted waveform using Equation (40). However, as pointed out in [
26], the method in [
22] cannot ensure performance improvements as iterations go on. Also note that the method cannot achieve the largest eigenvalue of
as its output SCNR, because the signal
s obtained with Equation (40), which would be the waveform for the next cycle, is not the
s in Equation (39).
Figure 9 shows the SCNR performances as a function of the iteration index in the deterministic target case. One can see that Algorithms 1 and 2 are well suited for the deterministic target case. The optimized QPSK signal performed better than both the method in [
22] and LFM signal, even though it can only choose from four phase points. Compared with other methods, the method in [
22] suffers from performance degradation and fluctuations. As mentioned earlier, the LFM signal in Equation (36) does not perform well in the deterministic extended target, and performed even worse than the initial random-phase signal in this example.
Figure 10 shows the SCNR performances as functions of CNR in the range 0–40 dB. We do not include the method in [
22] in this example, because it did not converge. It can be seen that Algorithms 1 and 2 can closely approximate the method in [
26] for a large range of CNRs, even though they are restricted to constant modulus—once again demonstrating the effectiveness of the proposed methods.