Mobility-Enhanced Reliable Geographical Forwarding in Cognitive Radio Sensor Networks
Abstract
:1. Introduction
2. Motivation
3. Related Work
| Symbol | Definition |
|---|---|
| SU reception threshold | |
| PU reception threshold | |
| S | SU received signal |
| PU’s hypothetical idle state | |
| PU’s hypothetical active state | |
| additive white Gaussian noise (AWGN) | |
| probability of detecting PU activity | |
| probability of false detection of PU activity | |
| PU signal waveform | |
| spectrum sensing decision threshold | |
| n | number of SUs |
| SU’s transmission power | |
| SU’s transmission reference distance | |
| α | path-loss exponential |
| PU’s transmission radius | |
| base station’s keep-out radius | |
| Interference on channel i | |
| mobility-induced guard (mguard) distance | |
| PU transmission power on channel i | |
| ℜ | transmission range of an SU transceiver pair |
| υ | relative speed of SUs |
| PU’s transmission period | |
| PU’s arrival time | |
| PU’s absence time | |
| channel transition probability of ON to OFF state | |
| channel transition probability of OFF to ON state | |
| number of channels | |
| period for spectrum sensing | |
| period for channel switching | |
| channel access period | |
| event radius | |
| maximum route negotiation time | |
| achievable spatio-temporal data rate on channel i | |
| spatio-temporal availability of channel i | |
| packet transmission period | |
| θ | scaling factor |
| SU’s node energy | |
| minimum allowed SU node energy | |
| data channels in route request packet |
4. MROR System and Network Model
4.1. Network Model
4.2. Mobility-Enhanced Channel Availability Modeling
4.2.1. PU Protection
4.2.2. Channel Estimation
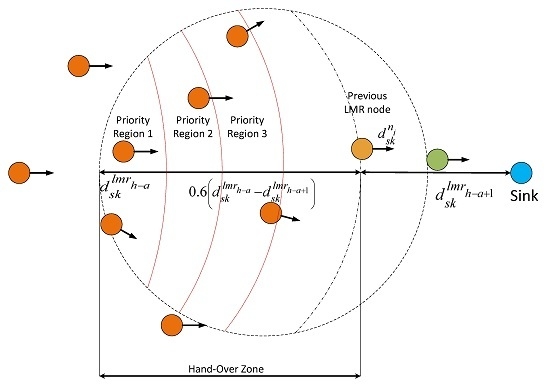
4.2.3. Route Stability
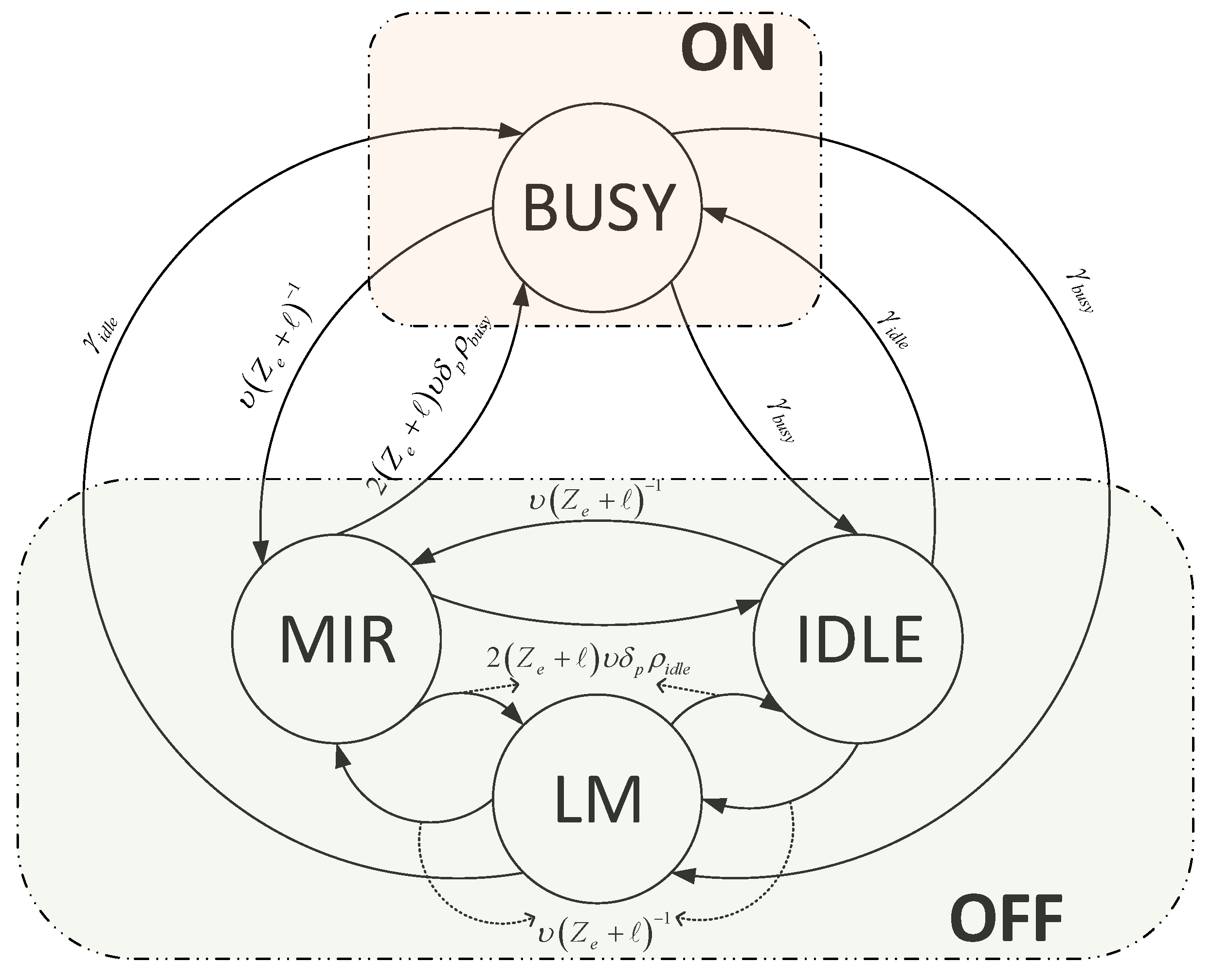
4.3. Channel Pool Update
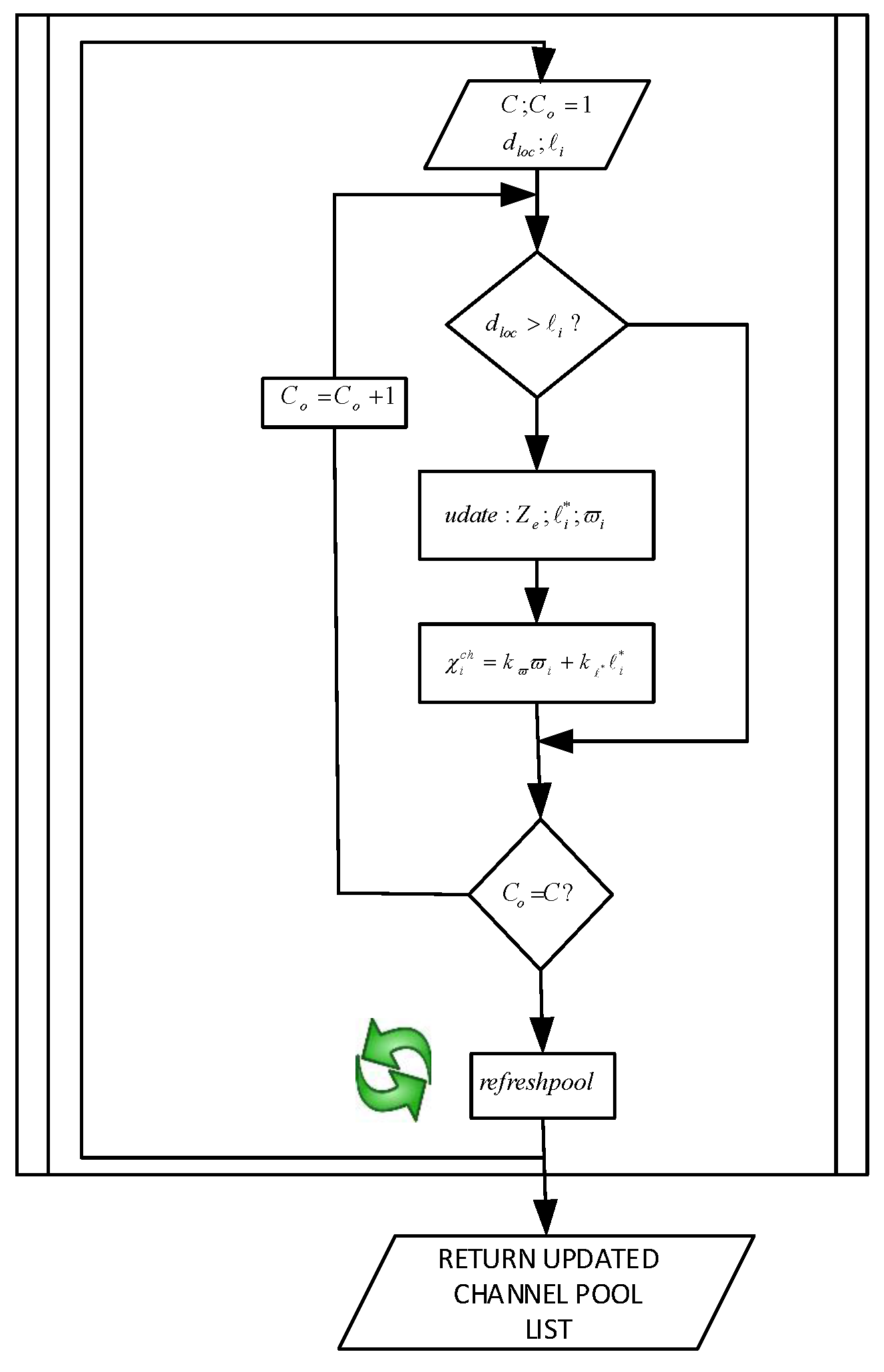
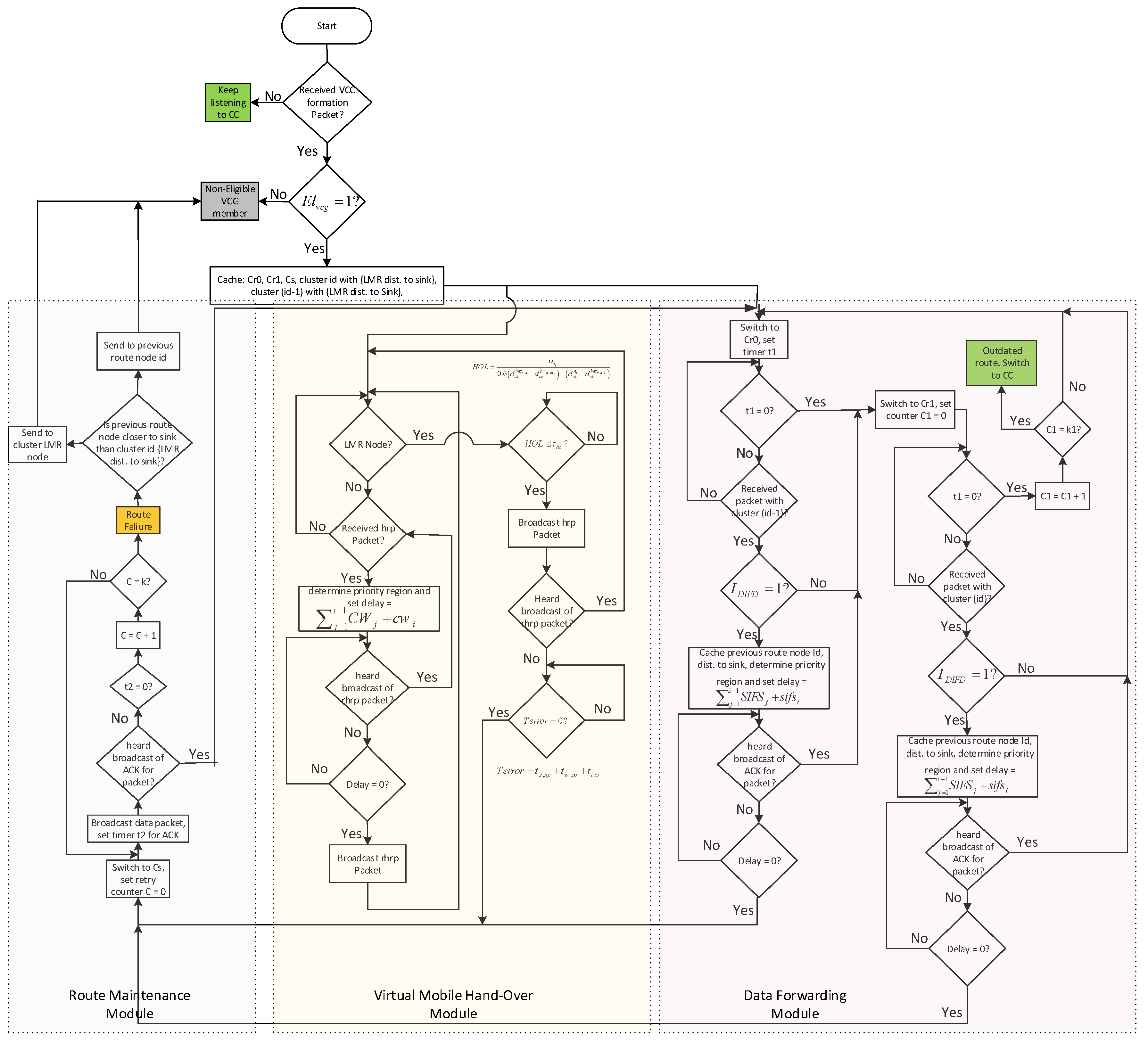
5. MROR: Mobile Reliable Opportunistic Routing for CRSN
5.1. Channel Selection and Route Request Initiation
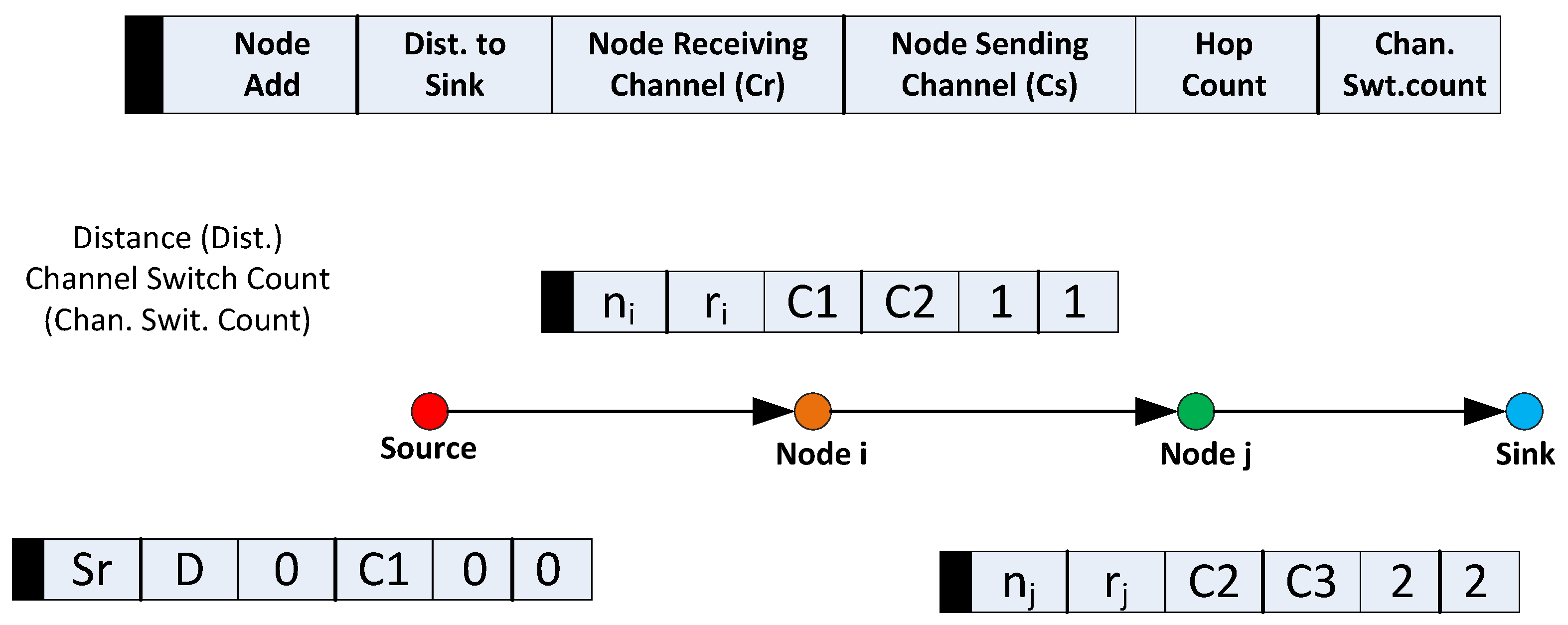
5.2. Route Request
5.3. Route Selection
5.4. VCG Formation
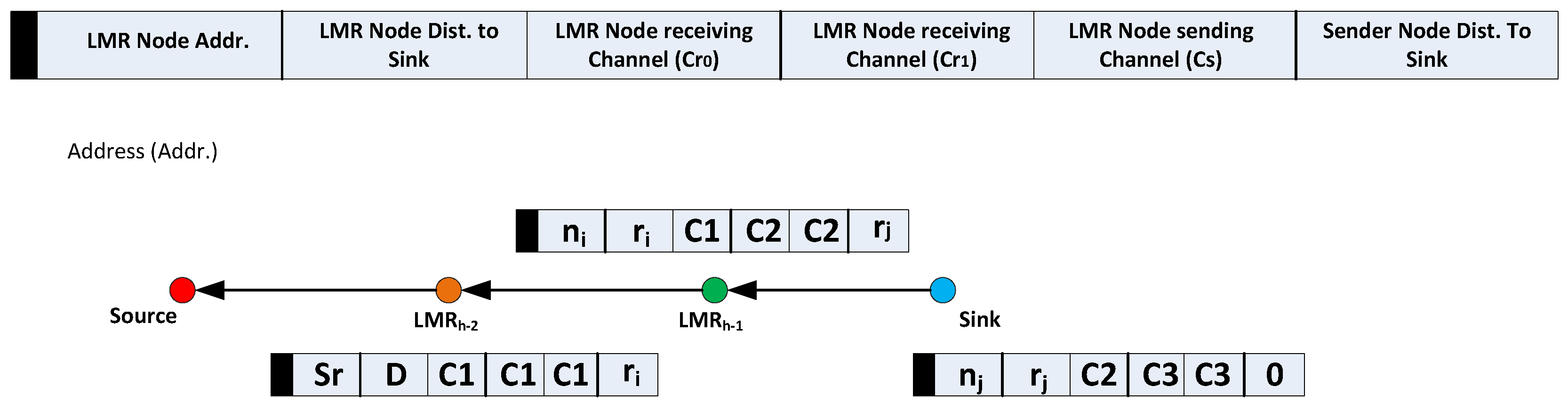

5.5. VMH Zoning System
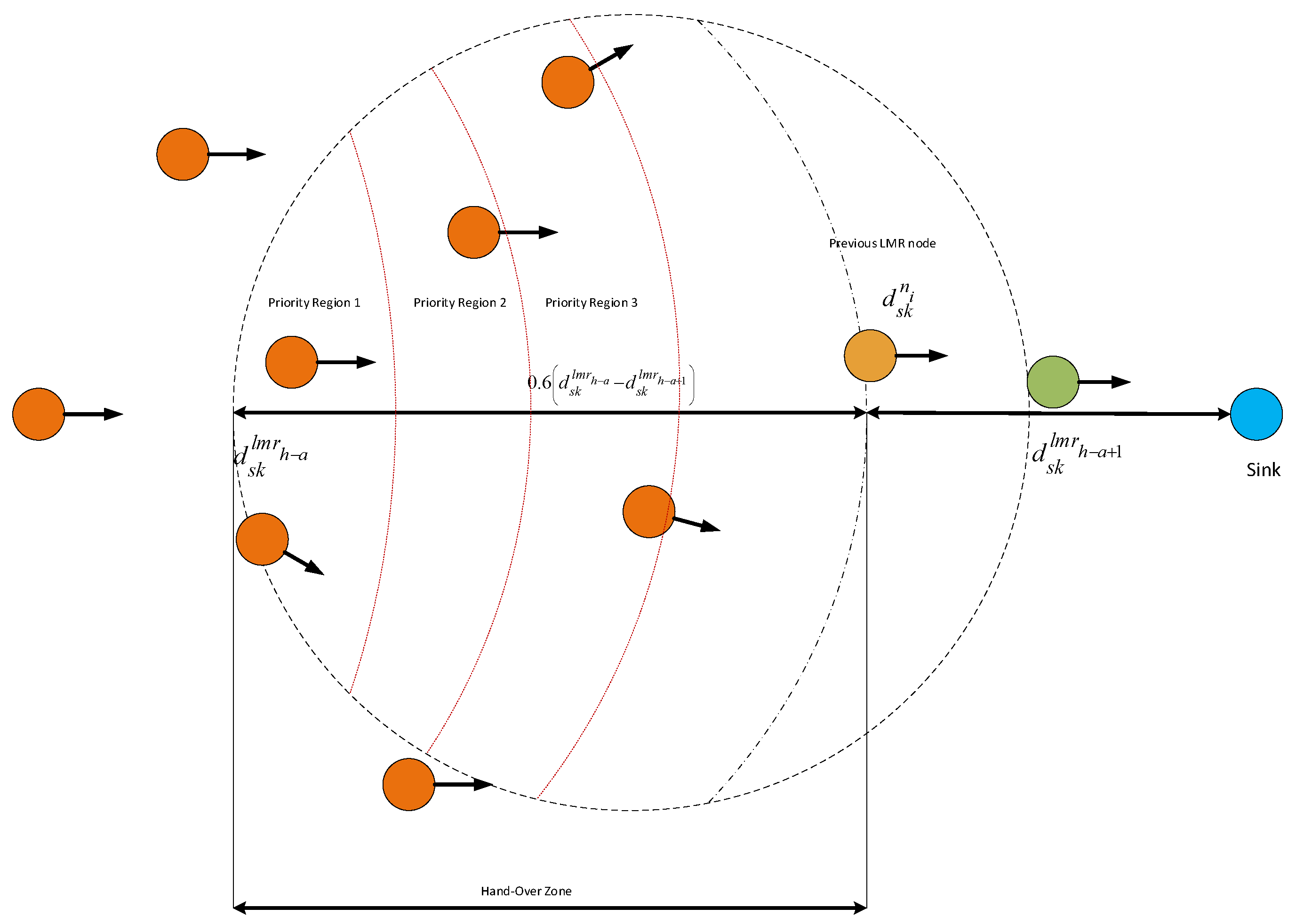

5.6. VCG-Based Data Forwarding Initiative Determination
5.7. Receiver Contention Prioritization

5.8. Route Maintenance
6. Performance Evaluation
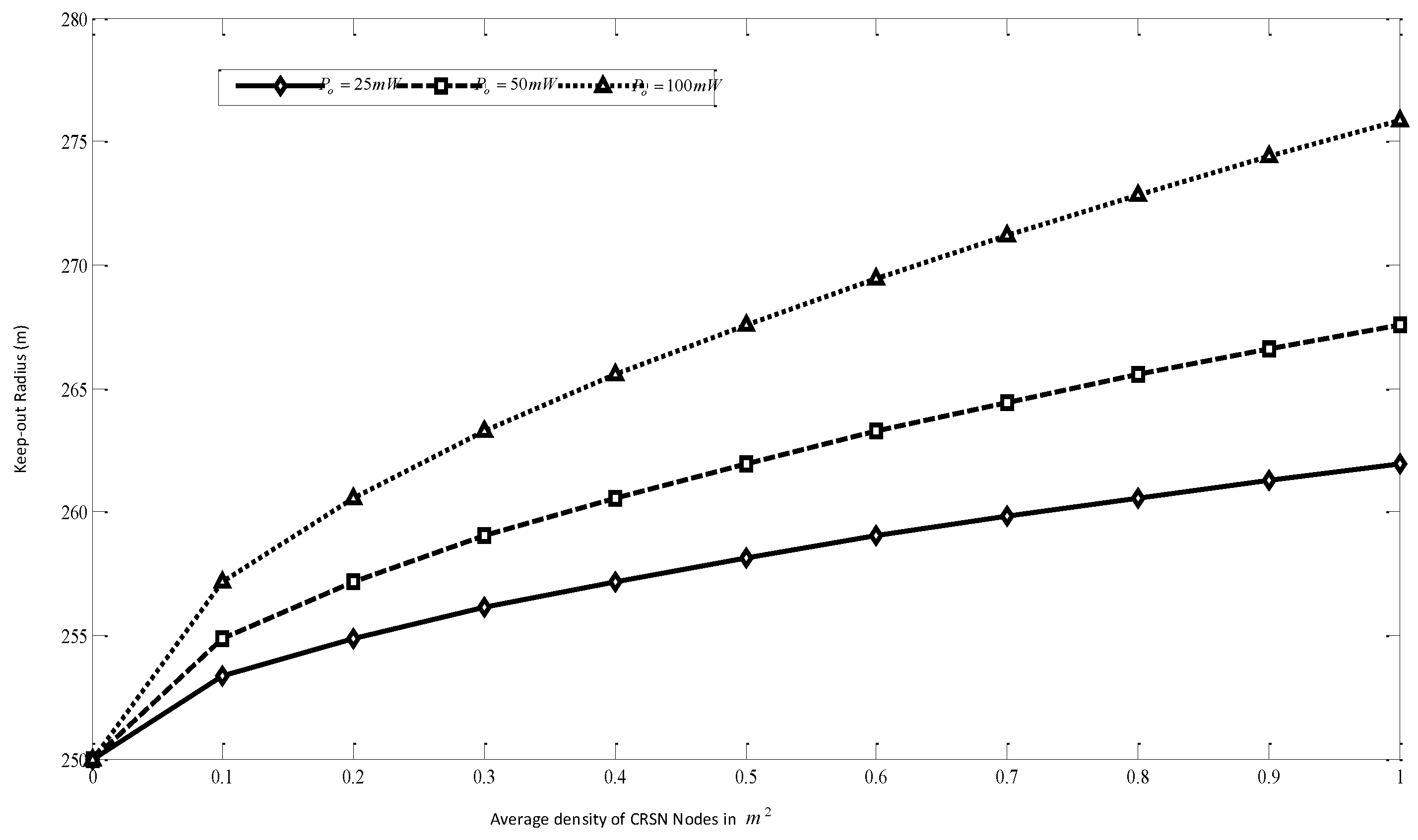
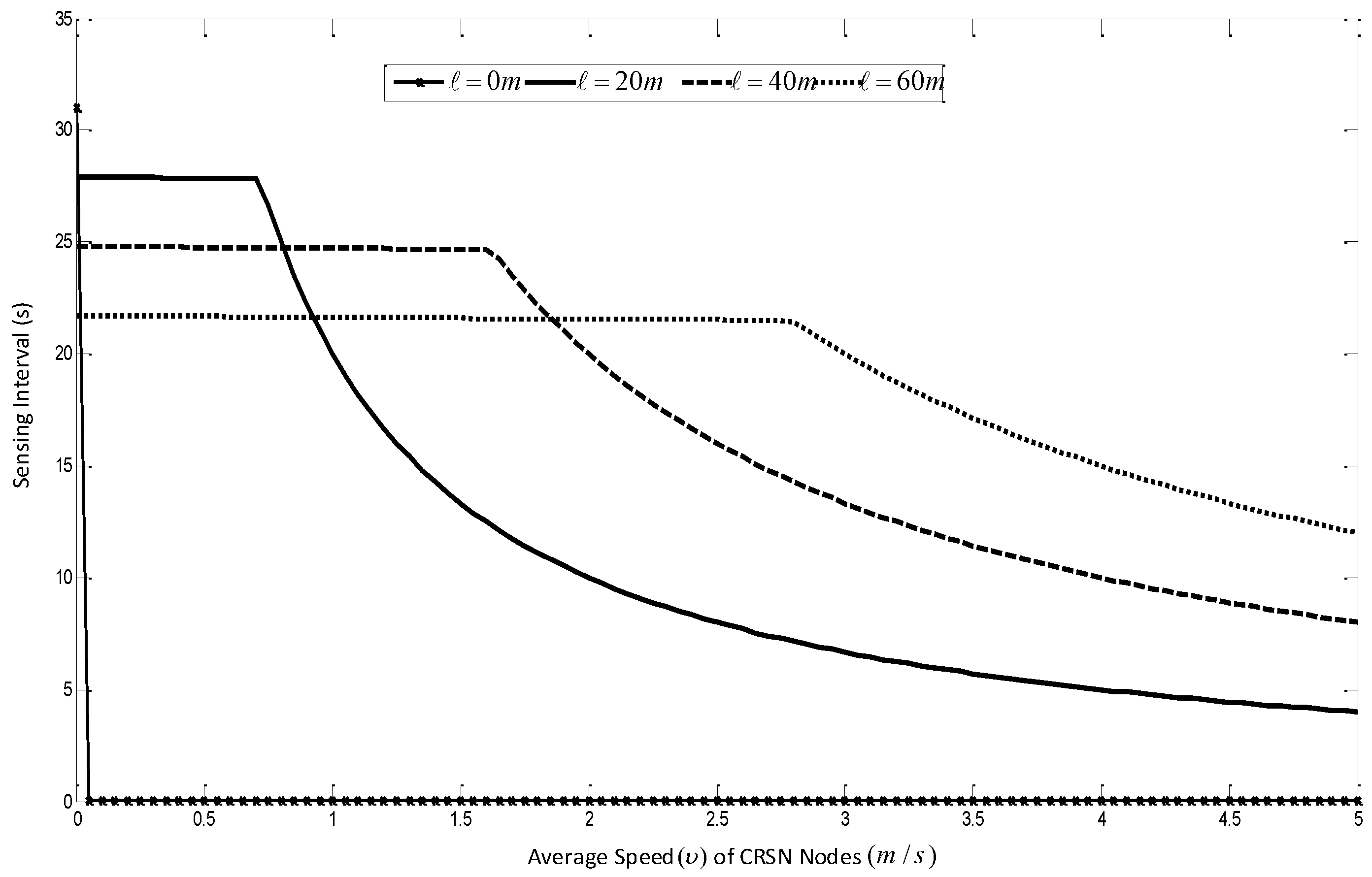
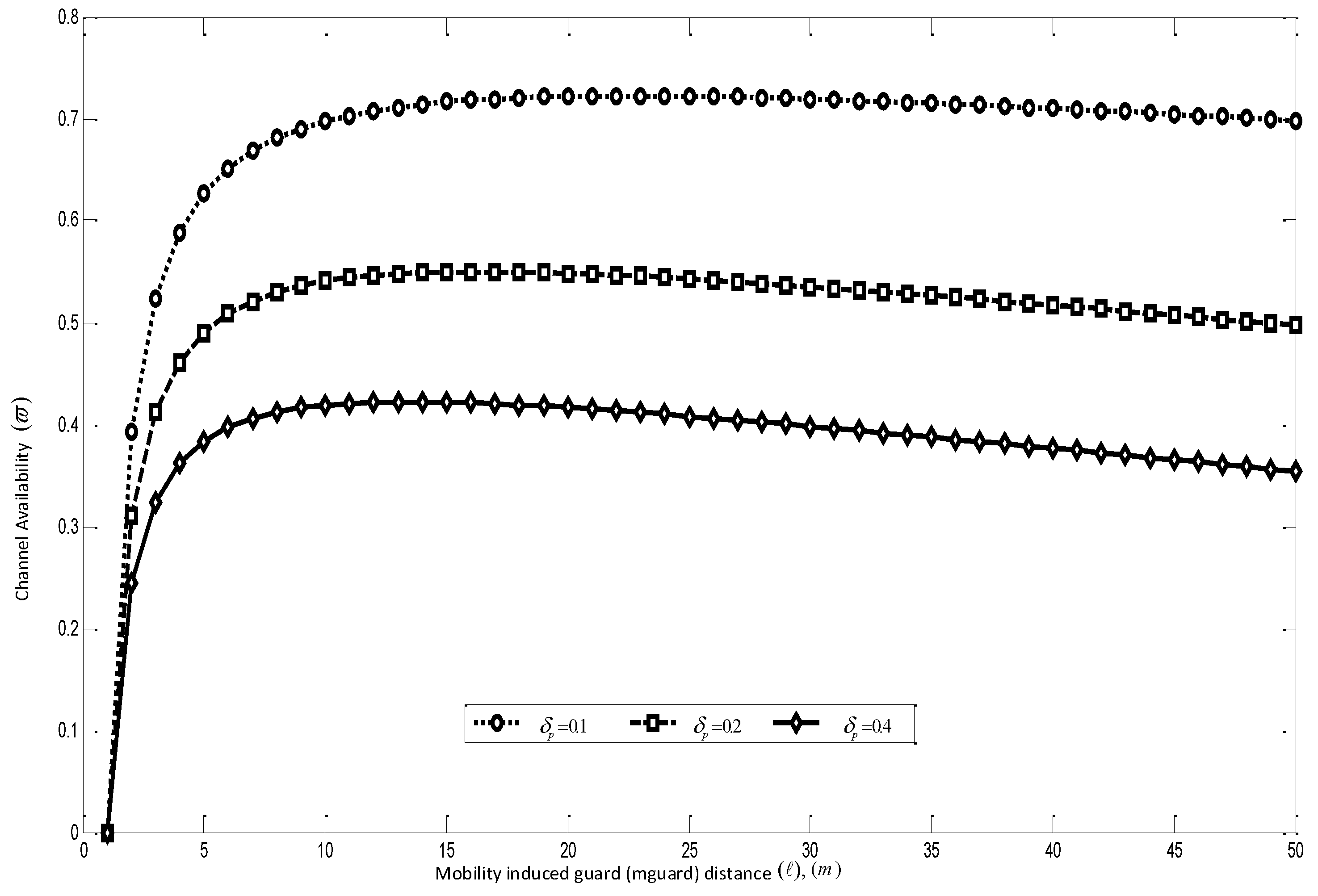
- Throughput: This metric is used to measure the time performance of the considered application. The throughput is computed as the number of bits-per-second received at the sink. Since certain protocols allow multiple copies to reach the sink, thus unique packets out of the total packets the sink receives are considered in computing the throughput.
- Goodput: Goodput is a measure of the reliability of communication in the considered network. It is computed as the ratio of total unique packets the sink receives by the number of packets sent from the source nodes of each stream.
- Energy efficiency: Energy efficiency is computed as the ratio of the number of packets the sink receives by the total energy consumed by the protocol in the network.
- Route Stability Ratio: Route stability ratio is the ratio of unsuccessful routes between each node in the network to the number of all possible routes.

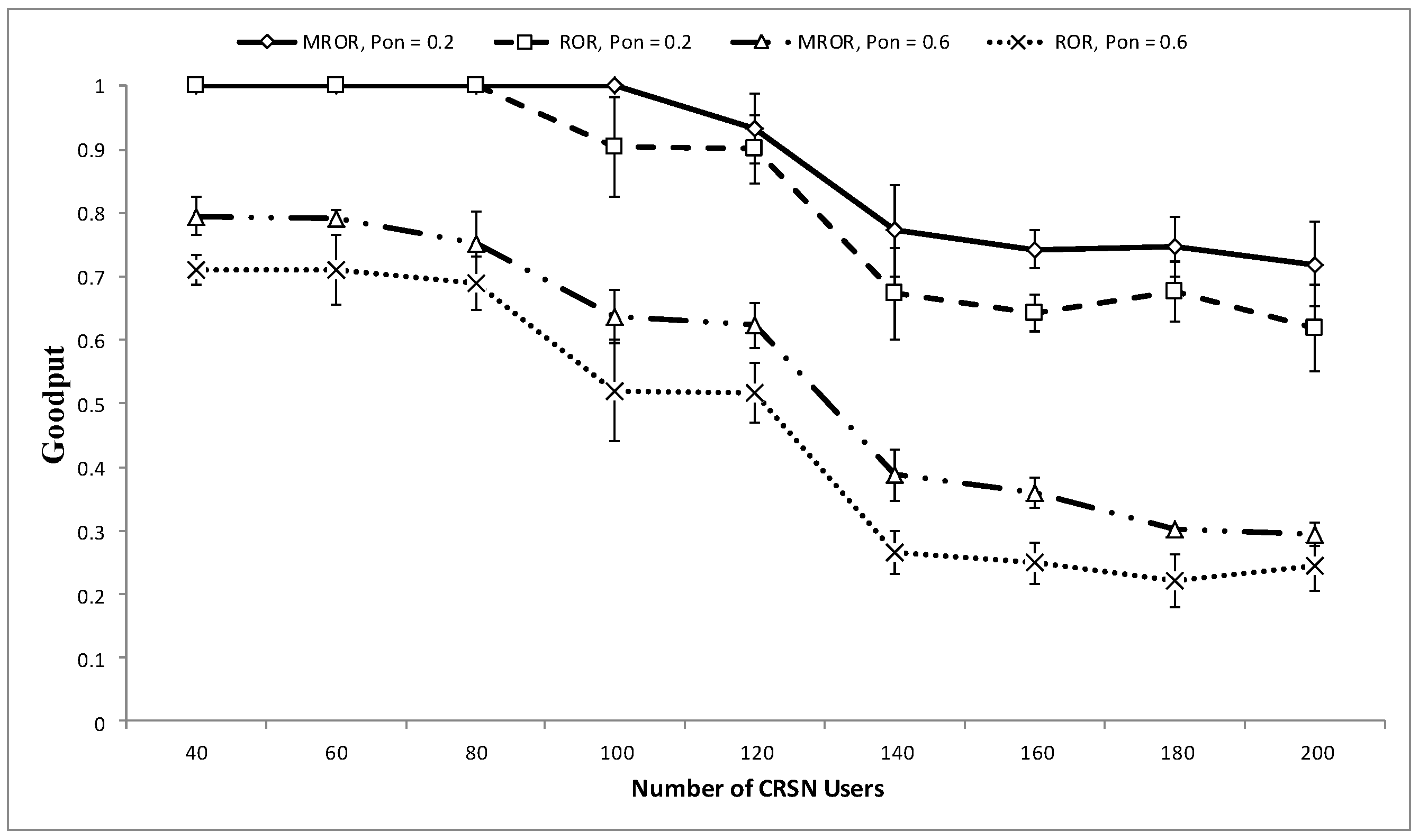
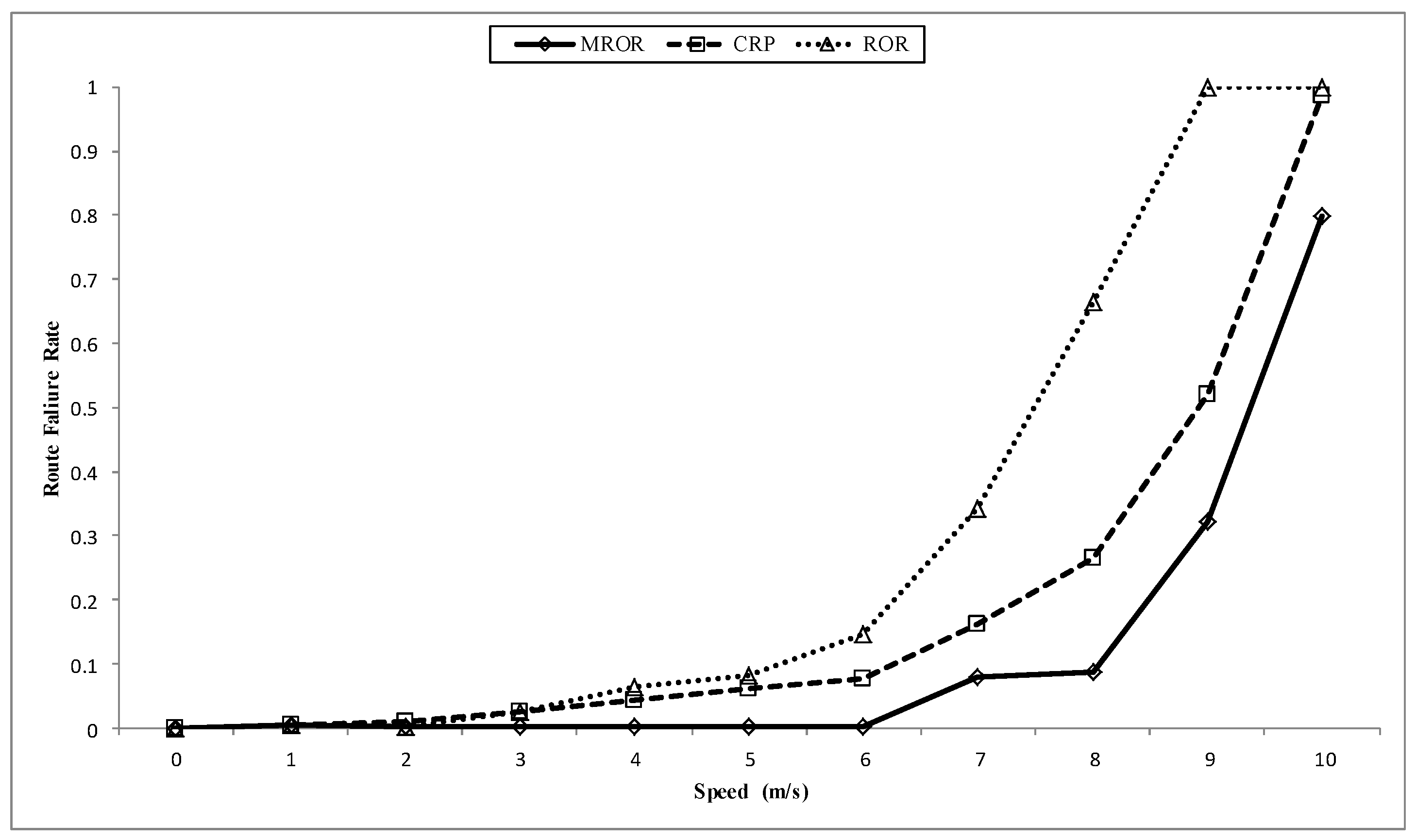
7. MROR Comparison
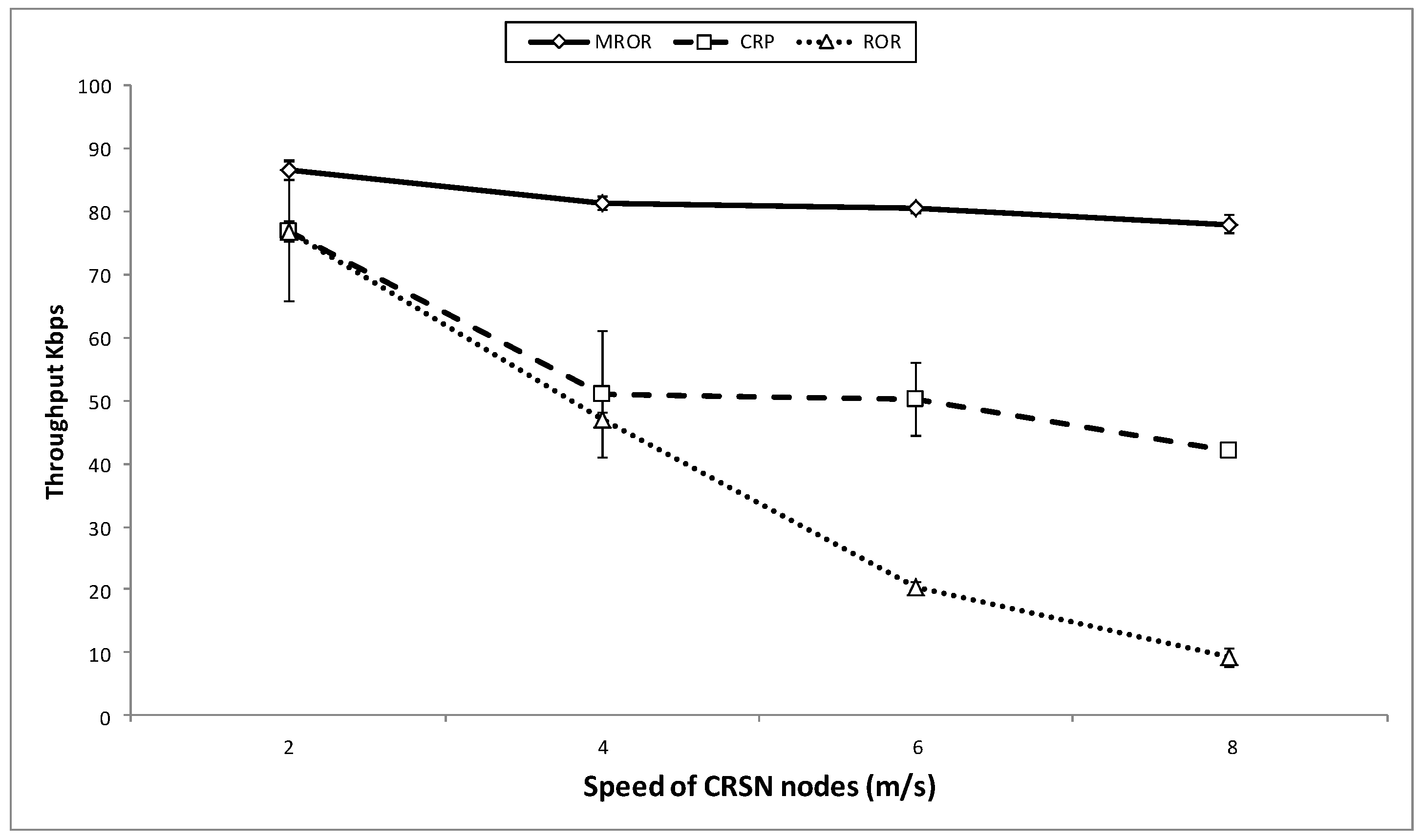

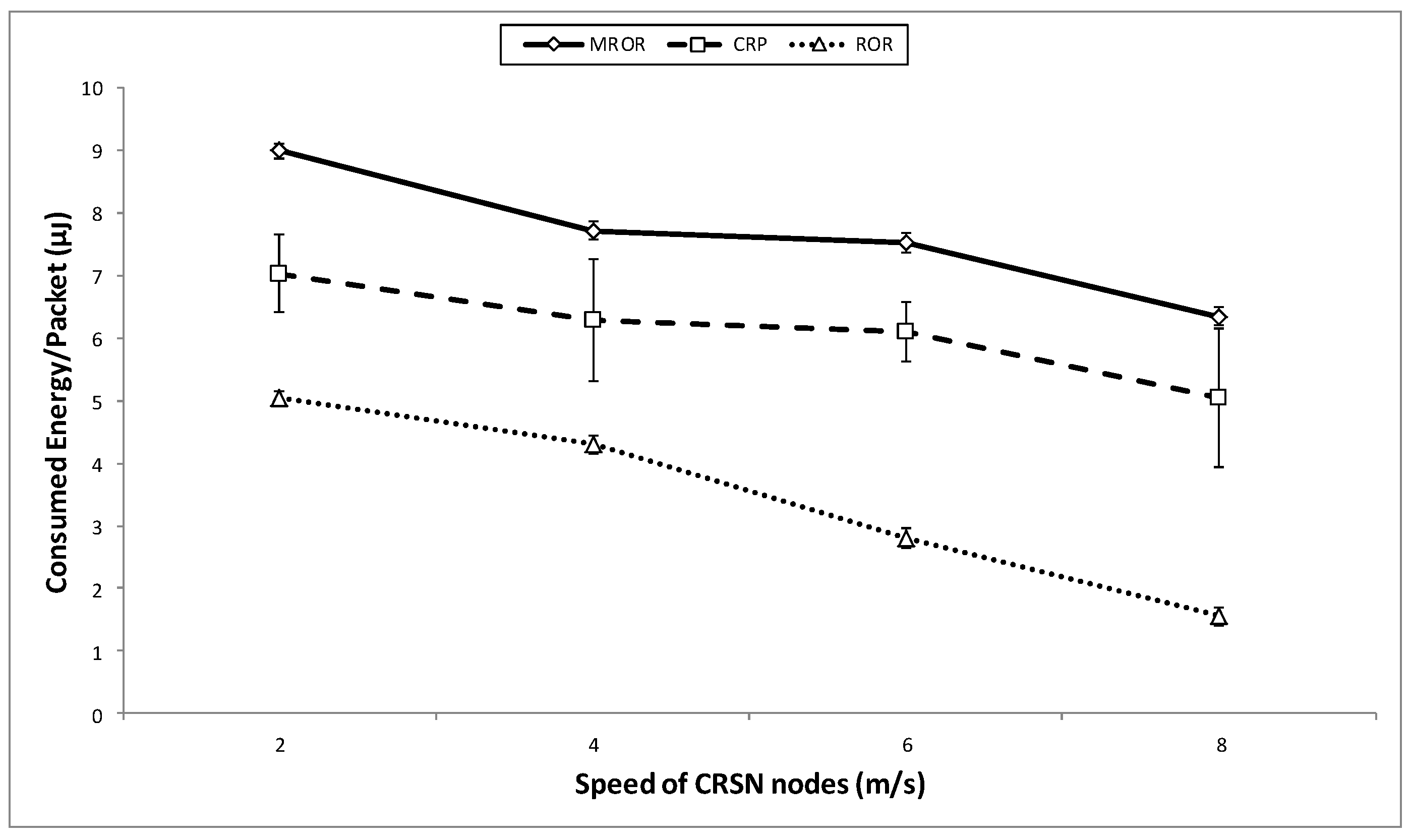
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Berg-Insight. Retail M2M and IoT Applications. Available online: http://www.berginsight.com/Report PDF/ProductSheet/bi-retail4-ps.pdf (accessed on 24 May 2015).
- Cisco. Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update 2014–2019 White Paper; Cisco Systems, Inc.: San Jose, CA, USA, 2014. [Google Scholar]
- Akan, O.B.; Karli, O.; Ergul, O. Cognitive radio sensor networks. IEEE Netw. 2009, 23, 34–40. [Google Scholar] [CrossRef]
- Joshi, G.P.; Nam, S.Y.; Kim, S.W. Cognitive radio wireless sensor networks: Applications, challenges and research trends. Sensors 2013, 13, 11196–11228. [Google Scholar] [CrossRef] [PubMed]
- Youssef, M.; Ibrahim, M.; Abdelatif, M.; Chen, L.; Vasilakos, A.V. Routing metrics of cognitive radio networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 92–109. [Google Scholar] [CrossRef]
- Ning, G.; Duan, J.; Su, J.; Qiu, D. Spectrum sharing based on spectrum heterogeneity and multi-hop handoff in centralized cognitive radio networks. In Proceedings of the 2011 20th IEEE Annual Wireless and Optical Communications Conference (WOCC), Newark, NJ, USA, 15–16 April 2011; pp. 1–6.
- Samar, P.; Wicker, S.B. On the behavior of communication links of a node in a multi-hop mobile environment. In Proceedings of the 5th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Tokyo, Japan, 24–26 May 2004; pp. 145–156.
- Liu, B.; Brass, P.; Dousse, O.; Nain, P.; Towsley, D. Mobility improves coverage of sensor networks. In Proceedings of the 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Urbana-Champaign, IL, USA, 25–28 May 2005; pp. 300–308.
- Cacciapuoti, A.S.; Caleffi, M.; Paura, L. Reactive routing for mobile cognitive radio ad hoc networks. Ad Hoc Netw. 2012, 10, 803–815. [Google Scholar] [CrossRef]
- Huang, X.; Lu, D.; Li, P.; Fang, Y. Coolest path: Spectrum mobility aware routing metrics in cognitive ad hoc networks. In Proceedings of the 2011 31st IEEE International Conference on Distributed Computing Systems (ICDCS), Minneapolis, MN, USA, 20–24 June 2011; pp. 182–191.
- Chowdhury, K.R.; Akyildiz, I.F. CRP: A routing protocol for cognitive radio ad hoc networks. IEEE J. Sel. Areas Commun. 2011, 29, 794–804. [Google Scholar] [CrossRef]
- Chowdhury, K.R.; Felice, M.D. Search: A routing protocol for mobile cognitive radio ad-hoc networks. Comput. Commun. 2009, 32, 1983–1997. [Google Scholar] [CrossRef]
- Zubair, S.; Fisal, N. Reliable geographical forwarding in cognitive radio sensor networks using virtual clusters. Sensors 2014, 14, 8996–9026. [Google Scholar] [CrossRef] [PubMed]
- Jin, X.; Zhang, R.; Sun, J.; Zhang, Y. TIGHT: A geographic routing protocol for cognitive radio mobile ad hoc networks. IEEE Trans. Wirel. Commun. 2014, 13, 4670–4681. [Google Scholar] [CrossRef]
- Salim, S.; Moh, S. On-demand routing protocols for cognitive radio ad hoc networks. EURASIP J. Wirel. Commun. Netw. 2013, 2013, 1–10. [Google Scholar] [CrossRef]
- Min, A.W.; Shin, K.G. Impact of mobility on spectrum sensing in cognitive radio networks. In Proceedings of the 2009 ACM Workshop on Cognitive Radio Networks, Beijing, China, 21 September 2009; pp. 13–18.
- Woo, A.; Tong, T.; Culler, D. Taming the underlying challenges of reliable multihop routing in sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 14–27.
- Zhao, J.; Govindan, R. Understanding packet delivery performance in dense wireless sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 1–13.
- Zubair, S.; Fisal, N.; Abazeed, M.B.; Salihu, B.A.; Khan, A.S. Lightweight distributed geographical: A lightweight distributed protocol for virtual clustering in geographical forwarding cognitive radio sensor networks. Int. J. Commun. Syst. 2015, 28, 1–18. [Google Scholar] [CrossRef]
- Huang, J.; Wang, S.; Cheng, X.; Liu, M.; Li, Z.; Chen, B. Mobility-assisted routing in intermittently connected mobile cognitive radio networks. IEEE Trans. Parall. Distrib. Syst. 2014, 25, 2956–2968. [Google Scholar] [CrossRef]
- Cacciapuoti, A.S.; Caleffi, M.; Paura, L.; Rahman, M.A. Channel availability for mobile cognitive radio networks. J. Netw. Comput. Appl. 2015, 47, 131–136. [Google Scholar] [CrossRef]
- Moore, D.; Leonard, J.; Rus, D.; Teller, S. Robust distributed network localization with noisy range measurements. In Proceedings of the 2nd international conference on Embedded networked sensor systems, Baltimore, MD, USA, 3–5 November 2004; pp. 50–61.
- Zhao, M.; Wang, W. WSN03-4: A Novel Semi-Markov Smooth Mobility Model for Mobile Ad Hoc Networks. In Proceedings of the IEEE 2006 Global Telecommunications Conference, San Francisco, CA, USA, 27 November–1 December 2006; pp. 1–5.
- Simon, G. Probabilistic Wireless Network Simulator. Available online: http://www.isis.vanderbilt.edu/projects/nest/prowler/ (accessed on 12 May 2015).
- Digham, F.F.; Alouini, M.S.; Simon, M.K. On the energy detection of unknown signals over fading channels. IEEE Trans. Commun. 2007, 55, 21–24. [Google Scholar] [CrossRef]
- Vu, M.; Devroye, N.; Tarokh, V. On the primary exclusive region of cognitive networks. IEEE Trans. Wirel. Commun. 2009, 8, 3380–3385. [Google Scholar] [CrossRef]
- Wellens, M.; Riihijärvi, J.; Mähönen, P. Evaluation of adaptive MAC-layer sensing in realistic spectrum occupancy scenarios. In Proceedings of the 2010 IEEE Symposium on New Frontiers in Dynamic Spectrum, Singapore, 6–9 April 2010; pp. 1–12.
- Wang, W.; Zhao, M. Joint effects of radio channels and node mobility on link dynamics in wireless networks. In Proceedings of the 27th IEEE Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008.
- Min, A.W.; Kim, K.H.; Singh, J.P.; Shin, K.G. Opportunistic spectrum access for mobile cognitive radios. In Proceedings of the 2011 IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 2993–3001.
- Lee, W.Y.; Akyildiz, I.F. Optimal spectrum sensing framework for cognitive radio networks. IEEE Trans. Wirel. Commun. 2008, 7, 3845–3857. [Google Scholar]
- Lien, S.Y.; Tseng, C.C.; Chen, K.C. Carrier sensing based multiple access protocols for cognitive radio networks. In Proceedings of the IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 3208–3214.
- Seada, K.; Zuniga, M.; Helmy, A.; Krishnamachari, B. Energy-efficient forwarding strategies for geographic routing in lossy wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 108–121.
- Zhang, Y.; Fromherz, M.; Kuhn, L. Rmase: Routing Modeling Application Simulation Environment, Rmase is Implemented as an Application in Prowler; Palo Alto Research Center (PARC) Inc.: Palo Alto, CA, USA, 2009. [Google Scholar]
- Zhang, Y.; Simon, G.; Balogh, G. High-level sensor network simulations for routing performance evaluations. In Proceedings of the Third International Conference on Networked Sensing Systems, Chicago, IL, USA, 31 May–2 June 2006.
- Simon, G.; Volgyesi, P.; Maróti, M.; Lédeczi, Á. Simulation-based optimization of communication protocols for large-scale wireless sensor networks. In Proceedings of the 2003 IEEE Aerospace Conference, Big Sky, MT, USA, 8–15 March 2003; Volome 3.
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zubair, S.; Syed Yusoff, S.K.; Fisal, N. Mobility-Enhanced Reliable Geographical Forwarding in Cognitive Radio Sensor Networks. Sensors 2016, 16, 172. https://doi.org/10.3390/s16020172
Zubair S, Syed Yusoff SK, Fisal N. Mobility-Enhanced Reliable Geographical Forwarding in Cognitive Radio Sensor Networks. Sensors. 2016; 16(2):172. https://doi.org/10.3390/s16020172
Chicago/Turabian StyleZubair, Suleiman, Sharifah Kamilah Syed Yusoff, and Norsheila Fisal. 2016. "Mobility-Enhanced Reliable Geographical Forwarding in Cognitive Radio Sensor Networks" Sensors 16, no. 2: 172. https://doi.org/10.3390/s16020172