Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming
Abstract
:1. Introduction
- Two novel hybrid secure transmission schemes, i.e., TAS-SSC-ZFB and TAS-SSC-NAN, are proposed for securing the data transmission in WSNs while achieving low feedback requirements and examination costs.
- Exact closed-form expressions for the secrecy outage probability and effective secrecy throughput are derived for the proposed schemes, which provide an efficient and convenient approach to characterize the secrecy performance of the considered network.
- Using these closed-form expressions, the optimal switching threshold is determined and the optimal power allocation factor between the BS and CJ is obtained for both schemes to minimize the secrecy outage probability. In addition, the optimal secrecy rate is decided for both schemes to maximize the effective secrecy throughput. Our findings demonstrate that the TAS-SSC-ZFB scheme outperforms the TAS-SSC-NAN scheme in terms of both secrecy outage probability and effective secrecy throughput, while the TAS-SSC-NAN scheme is more robust than the TAS-SSC-ZFB scheme.
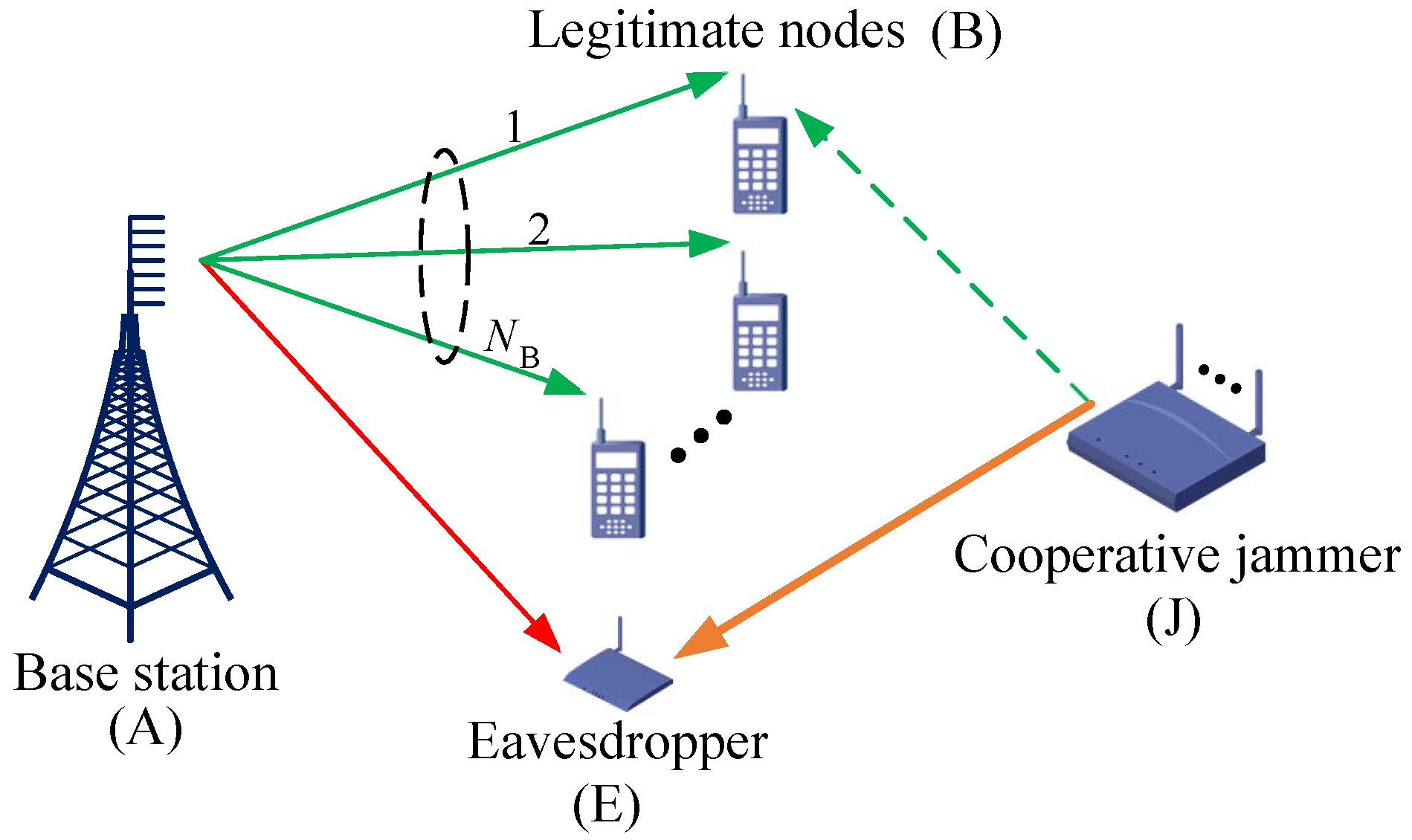
2. System Model and Transmission Protocol
2.1. System Model
2.2. Secure Transmission Schemes
2.2.1. Zero-Forcing Beamforming
2.2.2. Null-Space Artificial Noise
2.3. Achievable Secrecy Rate
3. Secrecy Performance Analysis
3.1. Preliminaries
3.2. Secrecy Outage Probability
3.3. Effective Secrecy Throughput
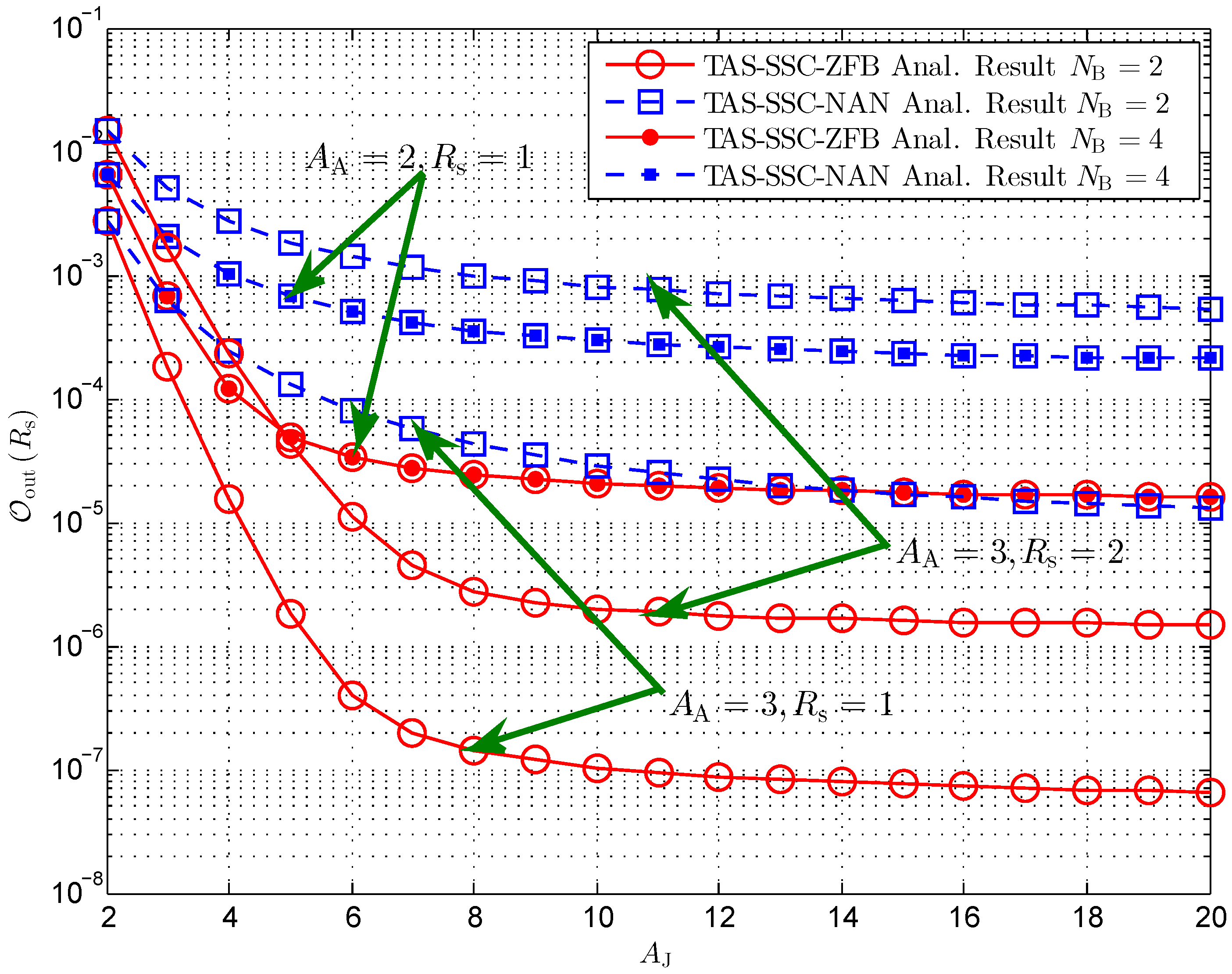
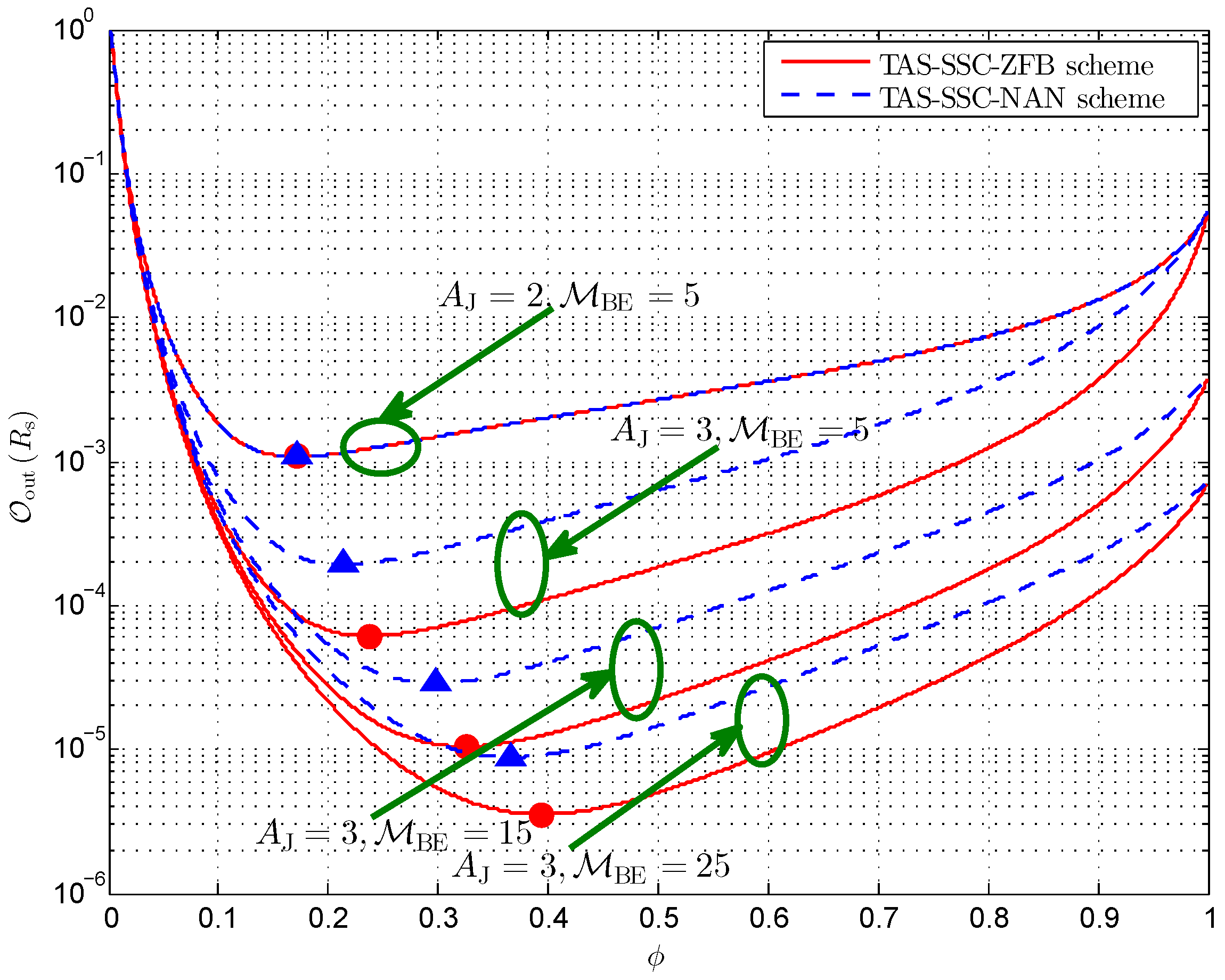
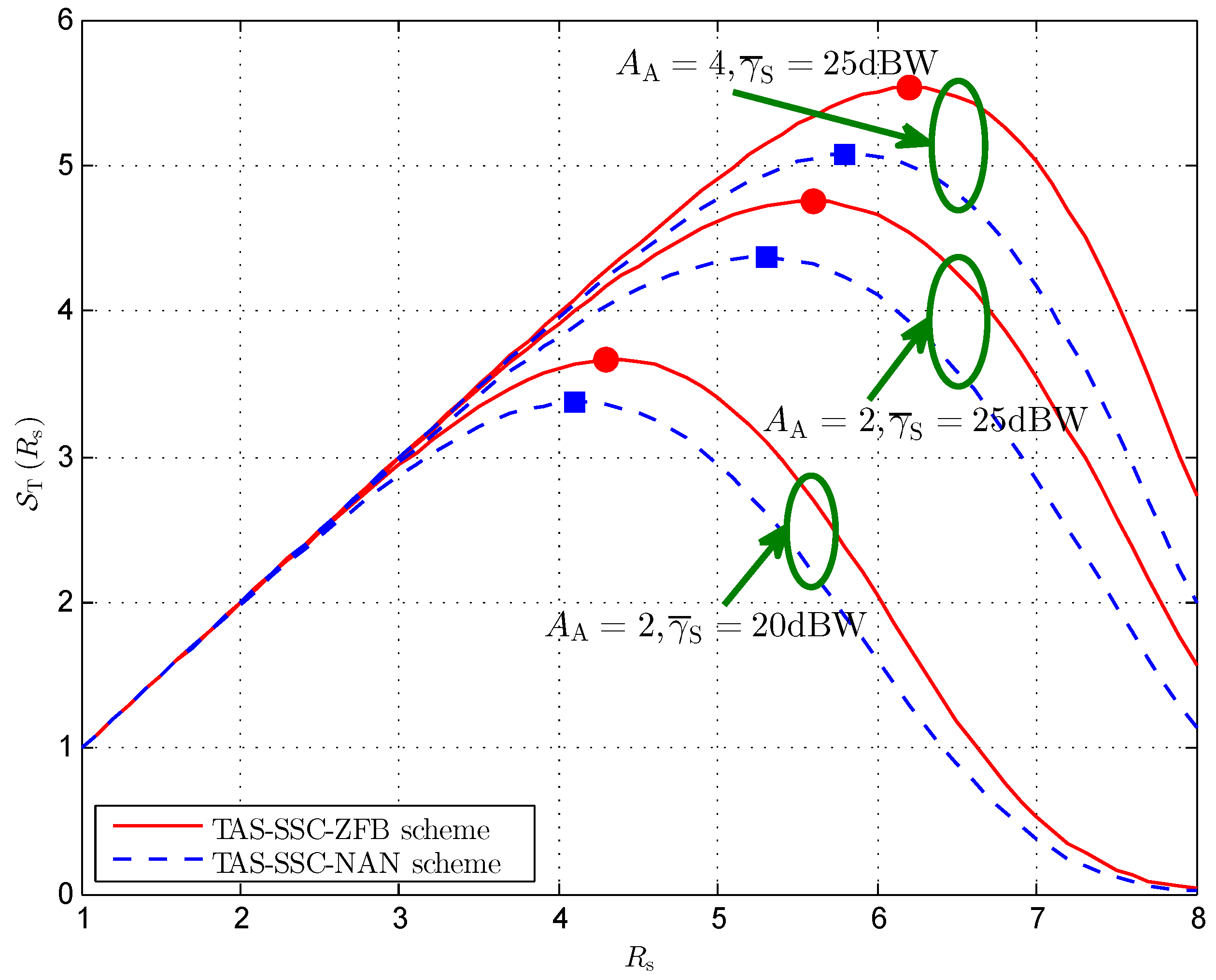
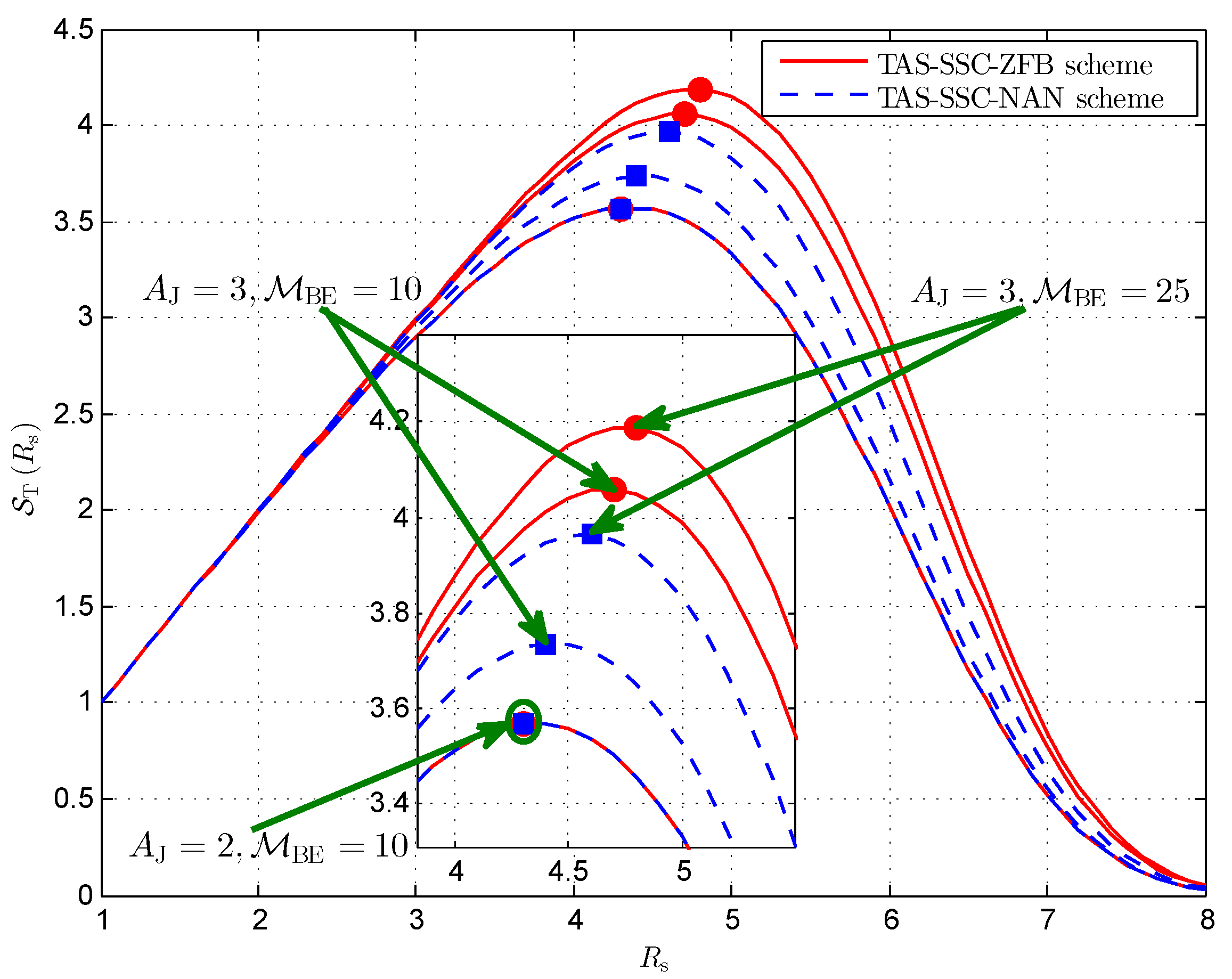
4. Simulations and Discussions
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Deng, Y.; Wang, L.; Elkashlan, M.; Nallanathan, A.; Mallik, R.K. Physical layer security in three-tier wireless sensor networks: A stochastic geometry approach. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1128–1138. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Sun, L.; Ren, P.; Du, Q.; Wang, Y. Fountain-coding aided strategy for secure cooperative transmission in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2016, 12, 291–300. [Google Scholar] [CrossRef]
- Liau, Q.Y.; Leow, C.Y.; Ding, Z. Physical layer security using two-path successive relaying. Sensors 2016, 16, 846. [Google Scholar] [CrossRef] [PubMed]
- Mehmood, A.; Song, H.; Lloret, J. In Multi-agent based framework for secure and reliable communication among open clouds, Network Protocols and Algorithms. Macrothink Inst. 2014, 6, 60–76. [Google Scholar]
- Butun, I.; Erol-Kantarci, M.; Kantarci, B.; Song, H. Cloud-centric multi-level authentication as a service for secure public safety device networks. IEEE Commun. Mag. 2016, 54, 47–53. [Google Scholar] [CrossRef]
- Trappe, W. The challenges facing physical layer security. IEEE Commun. Mag. 2015, 53, 16–20. [Google Scholar] [CrossRef]
- Xu, Q.; Ren, P.; Song, H.; Du, Q. Security enhancement for IoT communications exposed to eavesdroppers with uncertain locations. IEEE Access 2016, 4, 2840–2853. [Google Scholar] [CrossRef]
- Curiac, D.I. Wireless sensor network security enhancement using directional antennas: State of the art and research challenges. Sensors 2016, 16, 488. [Google Scholar] [CrossRef] [PubMed]
- Song, H.; Rawat, D.B.; Jeschke, S.; Brecher, C. Cyber-Physical Systems: Foundations, Principles and Applications, 1st ed.; Elsevier/Academic Press: Boston, MA, USA, 2016. [Google Scholar]
- Sheng, G.; Wang, Y.; Lv, Z.; Song, H. Multiple-antenna systems and multiuser communications: Fundamentals and an overview of software-based modeling techniques. Comput. Electr. Eng. 2016. [Google Scholar] [CrossRef]
- Xu, D.; Ren, P.; Sun, L.; Song, H. Precoder-and-receiver design scheme for multi-user coordinated multi-point in LTE-A and fifth generation systems. IET Commun. 2016, 10, 292–299. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Renzo, M.D. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Yang, N.; Yan, S.; Yuan, J.; Malaney, R.; Subramanian, R.; Land, I. Artificial noise: Transmission optimization in multi-input single-output wiretap channels. IEEE Trans. Commun. 2015, 63, 1771–1783. [Google Scholar] [CrossRef]
- Yang, N.; Elkashlan, M.; Duong, T.Q.; Yuan, J.; Malaney, R. Optimal transmission with artificial noise in MISOME wiretap channels. IEEE Trans. Veh. Technol. 2016, 65, 2170–2181. [Google Scholar] [CrossRef]
- Yang, N.; Yeoh, P.L.; Elkashlan, M.; Schober, R.; Collings, I.B. Transmit antenna selection for security enhancement in MIMO wiretap channels. IEEE Trans. Commun. 2013, 61, 144–154. [Google Scholar] [CrossRef]
- Yan, S.; Yang, N.; Malaney, R.; Yuan, J. Transmit antenna selection with Alamouti coding and power allocation in MIMO wiretap channels. IEEE Trans. Wirel. Commun. 2014, 13, 1656–1667. [Google Scholar] [CrossRef]
- Huang, Y.; Al-Qahtani, F.; Duong, T.; Wang, J.; Xiao, C. Secure transmission in spectrum sharing MIMO channels with generalized antenna selection over Nakagami-m channels. IEEE Access 2016, 4, 4058–4065. [Google Scholar] [CrossRef]
- Zhu, J.; Zou, Y.; Wang, G.; Yao, Y.D.; Karagiannidis, G.K. On secrecy performance of antenna-selection-aided MIMO systems against eavesdropping. IEEE Trans. Veh. Technol. 2016, 65, 214–225. [Google Scholar] [CrossRef]
- Yeoh, P.L.; Elkashlan, M.; Kim, K.J.; Duong, T.Q.; Karagiannidis, G.K. Transmit antenna selection in cognitive MIMO relaying with multiple primary transceivers. IEEE Trans. Veh. Technol. 2016, 65, 483–489. [Google Scholar] [CrossRef]
- Pan, G.; Lei, H.; Deng, Y.; Fan, L.; Yang, J.; Chen, Y.; Ding, Z. On secrecy performance of MISO SWIPT systems with TAS and imperfect CSI. IEEE Trans. Commun. 2016, 64, 3831–3843. [Google Scholar] [CrossRef]
- Park, K.H.; Wang, T.; Alouini, M.S. On the jamming power allocation for secure amplify-and-forward relaying via cooperative jamming. IEEE J. Sel. Areas Commun. 2013, 31, 1741–1750. [Google Scholar] [CrossRef]
- Xiong, J.; Cheng, L.; Ma, D.; Wei, J. Destination aided cooperative jamming for dual-hop amplify-and-forward MIMO untrusted relay systems. IEEE Trans. Veh. Technol. 2016, 65, 7274–7284. [Google Scholar] [CrossRef]
- Chen, X.; Chen, J.; Zhang, H.; Zhang, Y.; Yuen, C. On secrecy performance of a multi-antenna jammer aided secure communications with imperfect CSI. IEEE Trans. Veh. Technol. 2016, 65, 8014–8024. [Google Scholar] [CrossRef]
- Hao, D.; Hui-Ming, W.; Wei, G.; Wenjie, W. Secrecy transmission with a helper: To relay or to jam. IEEE Trans. Inf. Forensics Secur. 2015, 10, 293–307. [Google Scholar]
- Zheng, C.; Cumanan, K.; Ding, Z.; Johnston, M.; Le Goff, S.Y. Secrecy rate optimizations for a MIMO secrecy channel with a cooperative jammer. IEEE Trans. Veh. Technol. 2015, 64, 1833–1847. [Google Scholar]
- Zhao, R.; Huang, Y.; Wang, W.; Lau, V.K.N. Ergodic achievable secrecy rate of multiple-antenna relay systems with cooperative jamming. IEEE Trans. Wirel. Commun. 2016, 15, 2537–2551. [Google Scholar] [CrossRef]
- Li, Z.; Jing, T.; Ma, L.; Huo, Y.; Qian, J. Worst-case cooperative jamming for secure communications in CIOT networks. Sensors 2016, 16, 339. [Google Scholar] [CrossRef] [PubMed]
- Zhang, T.; Huang, Y.; Cai, Y.; Yang, W. Secure transmission in spectrum sharing relaying networks with multiple antennas. IEEE Commun. Lett. 2016, 20, 824–827. [Google Scholar] [CrossRef]
- Huang, Y.; Wang, J.; Zhong, C.; Duong, T.Q.; Karagiannidis, G.K. Secure transmission in cooperative relaying networks with multiple antennas. IEEE Trans. Wirel. Commun. 2016, 15, 6843–6856. [Google Scholar] [CrossRef]
- Shaqfeh, M.; Alnuweiri, H.; Alouini, M.S. Multiuser switched diversity scheduling schemes. IEEE Trans. Commun. 2012, 60, 2499–2510. [Google Scholar] [CrossRef]
- Holter, B.; Alouini, M.S.; Oien, G.E.; Hong-Chuan, Y. Multiuser switched diversity transmission. In Proceedings of the IEEE Vehicular Technology Conference, Los Angeles, CA, USA, 26–29 September 2004; pp. 2038–2043.
- Yang, M.; Guo, D.; Huang, Y.; Duong, T.Q.; Zhang, B. Physical layer security with threshold-based multiuser scheduling in multi-antenna wireless networks. IEEE Trans. Commun. 2016. [Google Scholar] [CrossRef]
- Yang, M.; Guo, D.; Huang, Y.; Duong, T.Q.; Zhang, B. Secure multiuser scheduling in downlink dual-hop regenerative relay networks over Nakagami-m fading channels. IEEE Trans. Wirel. Commun. 2016. [Google Scholar] [CrossRef]
- Hong-Chuan, Y.; Alouini, M.S. Performance analysis of multibranch switched diversity systems. IEEE Trans. Commun. 2003, 51, 782–794. [Google Scholar] [CrossRef]
- Al-Qahtani, F.S.; Zhong, C.; Alnuweiri, H.M. Opportunistic relay selection for secrecy enhancement in cooperative networks. IEEE Trans. Commun. 2015, 63, 1756–1770. [Google Scholar] [CrossRef]
- Fan, L.; Zhang, S.; Duong, T.Q.; Karagiannidis, G.K. Secure switch-and-stay combining (SSSC) for cognitive relay networks. IEEE Trans. Commun. 2016, 64, 70–82. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Zou, Y.; Wang, X.; Shen, W. Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J. Sel. Areas Commun. 2013, 31, 2099–2111. [Google Scholar] [CrossRef]
- Wang, L.; Kim, K.J.; Duong, T.Q.; Elkashlan, M.; Poor, H.V. Security enhancement of cooperative single carrier systems. IEEE Trans. Inf. Forensics Secur. 2015, 10, 90–103. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Suraweera, H.A.; Tellambura, C.; Poor, H.V. Cooperative beamforming and user selection for improving the security of relay-aided systems. IEEE Trans. Commun. 2016, 63, 5039–5051. [Google Scholar] [CrossRef]
- Yang, M.; Zhang, B.; Huang, Y.; Guo, D.; Yi, X. Ergodic secrecy capacity for downlink multiuser networks using switch-and-examine combining with post-selection scheduling scheme. IET Electron. Lett. 2016, 52, 720–722. [Google Scholar] [CrossRef]
- Ding, Z.; Leung, K.K.; Goeckel, D.L.; Towsley, D. On the application of cooperative transmission to secrecy communications. IEEE J. Sel. Areas Commun. 2012, 30, 359–368. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Elsevier/Academic Press: Amsterdam, The Netherlands, 2007. [Google Scholar]


© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, M.; Zhang, B.; Huang, Y.; Yang, N.; Guo, D.; Gao, B. Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming. Sensors 2016, 16, 1908. https://doi.org/10.3390/s16111908
Yang M, Zhang B, Huang Y, Yang N, Guo D, Gao B. Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming. Sensors. 2016; 16(11):1908. https://doi.org/10.3390/s16111908
Chicago/Turabian StyleYang, Maoqiang, Bangning Zhang, Yuzhen Huang, Nan Yang, Daoxing Guo, and Bin Gao. 2016. "Secure Multiuser Communications in Wireless Sensor Networks with TAS and Cooperative Jamming" Sensors 16, no. 11: 1908. https://doi.org/10.3390/s16111908





