Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey
Abstract
:1. Introduction
2. Game Theory: A Brief Overview
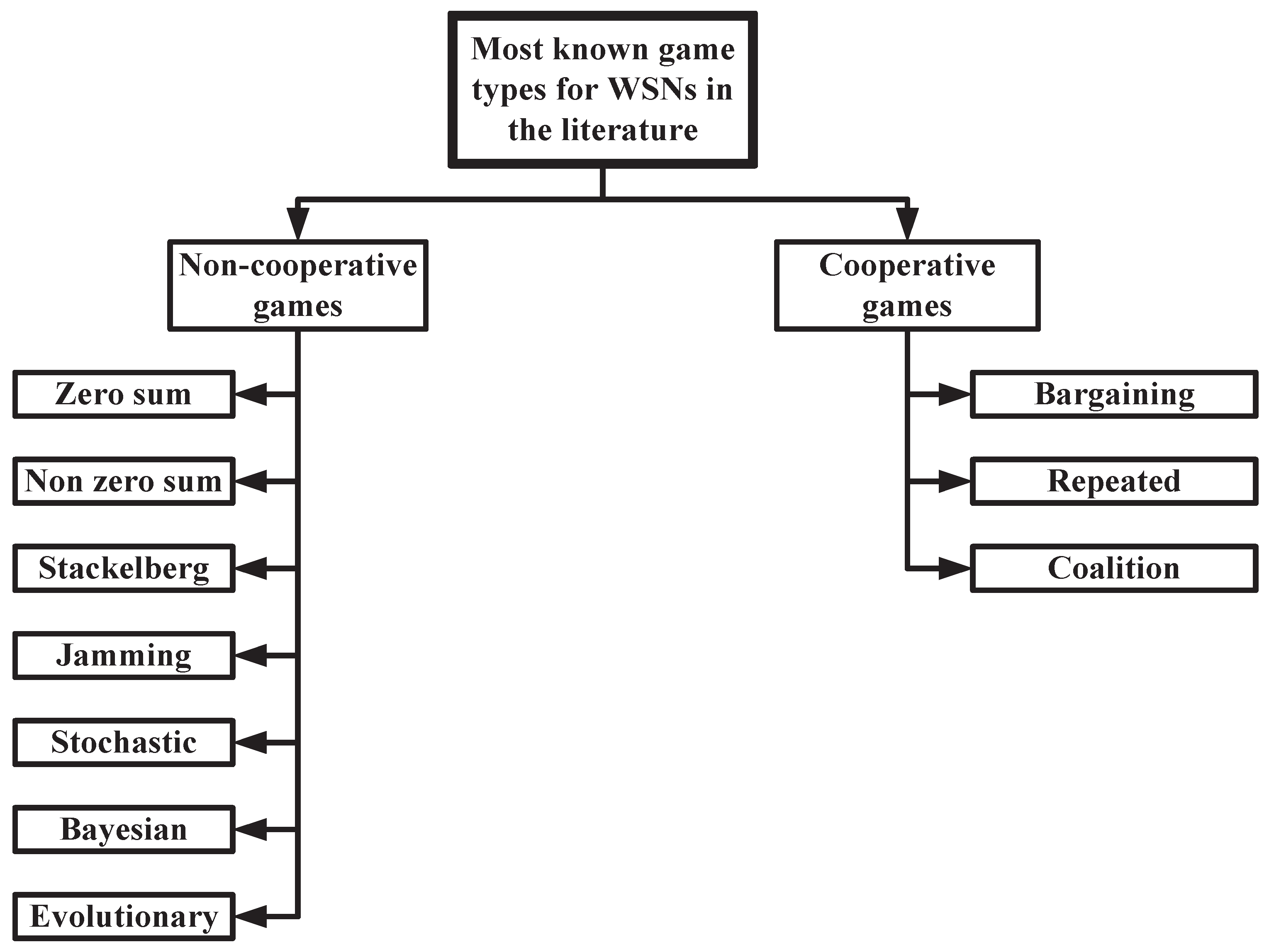
3. Games Theory for WSNs Security
3.1. Cooperative Games
3.1.1. Bargaining Game
3.1.2. Repeated Game
3.1.3. Coalition Game
3.2. Non-Cooperative Games
3.2.1. Zero-Sum Game
3.2.2. Nonzero-Sum Game
3.2.3. Stackelberg Game
3.2.4. Jamming Game
3.2.5. Stochastic Game
3.2.6. Bayesian Game
3.2.7. Evolutionary Game
3.3. Security in WSNs: Requirements
- Confidentiality: A transmitted data to a specific sensor node must not be understood by any other node in WSNs.
- Integrity: The transmitted and received data must not be maliciously altered by the participant sensor nodes in WSNs.
- Authentication: A sensor node uses the data authentication to verify that the received data is actually sent by the claimed sender in WSNs.
- Authorization: The authorization is used to guarantee that the authorized sensor nodes are only able to perform certain operations in WSNs.
- Availability: The WSN services must be available whenever the WSN users need them.
- Freshness: The data produced by the WSN sensor nodes must be neoteric.
- Forward and backward secrecy: Forward secrecy is used to prevent a sensor node that has left a WSN from reading any future data. Backward secrecy means preventing a new comer to a WSN from reading any previous data.
4. Game Theory Defense Strategies Against WSN Attacks
4.1. WSN Attack Types vs. Corresponding Layer
4.2. Internal and External Attacks
4.3. Clear and Passive Attacks
4.3.1. Clear Attack
4.3.2. Passive Attack
4.4. Cooperative and Non-Cooperative Games
4.4.1. Cooperative Games
- Bargaining Game: A bargaining game is presented in [42] through the cooperating nodes, resulting in a Nash Bargaining Solution and Reliability in Wireless Body Sensor Networks (WBSNs). This seeks to promote the cooperation between the nodes to maximize the performance in a multi-hop WBSN and hence, the utility function distinguishes the allocated bandwidths. Three main parameters should be taken into consideration: dynamic nature, quality-of-service (QoS), and fairness of resource allocation. In [44], the power allocation problem is addressed using bargaining NE leading to cooperative relaying. The proposed model aims at achieving the optimal signal-to-noise ratio (SNR) in WSNs. In [45], the authors propose the bargaining game to attain the optimal energy management policy for a solar-powered sensor node. The proposed model obtains the optimal sleep and wake up mode for the participant sensor nodes based on the bargaining NE by treating the selfish nodes that conserve energy through blocking packets with high probability. The players’ utility function is denoted by the combination between the probability of an active mode, a sleep mode, a listen mode, a packet block, and a packet drop for the two competitive players.
- Repeated Game: In [49], the authors propose a game theoretic approach based on repeated game to investigate the selfish nodes throughout in CSMA/CA network. The model stimulates the selfish nodes to cooperate leading to the Pareto optimality NE. In this model, the utility function is presented as the difference between the throughput and a punishment factor of the participant nodes.In [85], the authors propose a specific technique controlled by the network base station to be able to detect and prevent the selfish behavior of nodes. This technique works in parallel with the Core Mesh Routing Protocol (CMP) without disrupting its functionality using a game-theoretic approach based on a repeated game to detect and prevent the selfish behavior. This game uses the power consumption as an indicator of the game utility/payoff function. Increasing the utility is considered as a positive signpost of honesty and trustworthiness and vice versa if selfish behavior is presented. Consequently, the base station investigates the utility function to ensure that whether the node is capable of going to sleep or not. The utility concentrates on the transmission cost which is based on the forwarded data. Hence, the node with the increased utility/payoff has a higher chance of going to sleep.In [77], a repeated game is presented targeting a defense against passive DoS attack. This model applies a defense strategy at the routing layer to promote cooperation through rewarding the cooperating nodes and accumulating reputation values over time, while punishing non-cooperative passive attackers. To reach this goal, each node plays a repeated game executing series of Nash Equilibria on a utility function that balances between cooperation gain represented by the reputation value and the cost of forwarding packets to check the routing security.
- Coalition Game: In [84], a defense strategy is introduced to predict the attacks and their effect using cooperating camera sensors. The model is based on a threshold for the probability of error of the captured scene. This approach provides a solution for false alarm, energy conservation, early attack prediction, and selfish behavior detection.
4.4.2. Non-Cooperative Games
- Zero-sum Game: In [76], a game-theoretic approach based on zero-sum game was presented seeking routing secured against external intruders. The authors have developed the utility function as a combination of the energy consumption, probability of malicious nodes, and probability of dropped packets between check nodes (one or more through the forward path) to maximize the probability of attack detection. Intrusion detection framework for smart phone systems is proposed in [41] at which two players play a non-cooperative constant-sum game with complete information to achieve NE that leads to a defense strategy for the security server. In this game, the defender wishes to enhance the security level but the attacker wants to deteriorate it. The model gathers data and checks if the security server monitors attack or not, then calculates the payoff per each case using node ID as a node identity.Furthermore, in [87], the authors propose an intrusion packet detection at which the classical zero-sum game is chosen as a natural model for the behavior of the attacker/defender strategies. The utility functions for both the attacker and defender take into consideration the probability of detection. In [53], a zero-sum game is proposed to mitigate the selective forwarding attack in which the infected nodes turn malicious and select some packet to drop based on a stochastic formulation. The model utility function is the difference between the defense energy budget supplied by the IDS for all participant nodes and the attack energy budget applied to turn those nodes into malicious. In [52], the authors formulate a zero-sum game aiming at maximizing the transmission capacity in underwater sensor network based on the mitigation of jammers. The utility function of this game is maximized to achieve the optimal SNR based on two observers sensor nodes against the effect of the disruption caused by the jammer.
- Nonzero-sum Game: In [82], a nonzero-sum game is proposed to detect the malicious nodes and their effect (e.g., dropping packets and routing error message to misdirect the path) due to the DoS attack impact. Two defense strategies are developed. The first strategy is based on dynamic source routing that aims at maximizing the payoff. The second strategy focuses on reputation and cooperation between neighbors which also aims at maximizing the payoff and enhancing the defense strategy. However, the developed algorithms suffer from unnecessary added cost in the utility function of the defender, and this cost is mainly related to continuous defending of nodes even when no attack is encountered. In [81], the authors introduce a defense strategy based on a nonzero-sum game and achieve NE using a Markov decision process to predict the most vulnerable sensor node. In [54], the proposed defense strategy aims at detecting and correcting the malicious sensor nodes that drop packets based on a nonzero-sum game using periodic collusion-resistant punishment mechanism. The model stimulates the detected malicious node(s) to react benevolently.
- Stackelberg Game: In [2], the attack-defense interactions are modeled using a Stackelberg game, and the NE condition is derived which is sufficient to ensure that the sensed data are truthful within a nominal error bound. The defense strategy gives an authority to the defender to be the decision maker. The model is based on a thresholding defense strategy against the attacks. The thresholding is correlated to the trust score of the data items observed by the sensor nodes to detect the effect of the followers (attacker). In [56], the authors propose a Stackelberg game for detecting the reactive jamming attack in wireless networks aiming at maximizing the signal-to-interference-noise ratio (SINR). The reactive jammer seeks to inject noise like legitimate signal at receiver. The utility function is represented by the resulting SINR, while a linear power penalty is used as a punishment for jammer and legitimate nodes. In [57], a Stackelberg game is developed to confront the external attacks manipulations based on energy defense budget against the corresponding energy attack budget. The utility function represents the resultant of the defense and attack energy budgets.
- Jamming Game: In [58], the authors propose a jamming game that is fundamentally inspired from the zero-sum game framework due to the uniqueness of NE. More concretely, the authors study the jamming impact on the Orthogonal Frequency Division Multiplexing (OFDM) system when the jammer is situated close to the base station. The utility function is the combination of the power level of the uncontrolled environmental noise at i-th state, the costs of power usage for transmitter and jammer, and fading channel gains for transmitter and jammer. In [59], a jamming game is proposed to mitigate the DoS attack (jamming attack) in underwater sensor network. The legal player utility function is maximized based on a combination of its power level, SINR, and transmission costs. The game model is classified into two cases. In the former case, the game is presented as a static jamming game that owns a single NE. In the latter case, the game is represented by a dynamic jamming game which is derived based on a Markov decision process. In other work, the jamming game is used to treat the complexity constraints of implanted biomedical sensors [60,61]. In these models, the utility function is presented in two cases. In the former case, the authors study a fixed strategy in which the jammer may or may not jam the i-th player. In the latter case, a mixed transmission strategy is used for the i-th player.
- Stochastic Game: In [64], the authors propose a new framework for wireless nodes virtualization in which the service providers and network operators are responsible for the QoS and spectrum management, respectively. The proposed model can handle the unknown dynamics in traffic characteristics and channel conditions. In addition, the network operator is responsible for calculating the NE based on the conjectural price of the communicating nodes leading to the optimal resource management.
- Bayesian Game: In [66], a Bayesian game is proposed to analyze the interactions between pairs of attacking/defending nodes. The Nash equilibrium is studied for the attacker/defender game through two scenarios, namely, static and dynamic. In fact, the dynamic Bayesian model represents the more realistic approach that allows the network defender to continuously update his decision for the existing malicious nodes. Furthermore, the dynamic scenario provides energy-efficient monitoring strategies for the defender. A new approach is suggested called Bayesian hybrid detection that adopts lightweight monitoring and heavyweight monitoring mechanisms. The lightweight monitoring is utilized to estimate the adversary’s actions, while the heavyweight monitoring acts as a last resort of defense.
- Evolutionary Game: In [67], the authors propose a data aggregation model called evolutionary game-based data aggregation model (EGDAM) in WSNs. The model uses a weighting method based on the pixel-level fusion between homogeneous sensor nodes to adapt the unreliable information from the nodes. In [68], an evolutionary game is used to maintain the cooperation in static and mobile multi-class WSNs, with each class managed by a different authority. Two scenarios are considered for the packet forwarding. In the former scenario, the packet forwarding is between mobile classes in which the game formulation is based on iterated prisoner dilemma. In the later scenario, the packet forwarding is between spatially dispersed stationary classes.In [69], building reliable and survivable networks with fault tolerance is reviewed based on bio-robustness of different biological scales, i.e., gene, molecular networks, immune systems, population, and community. In [70], dynamic hybrid fault models are proposed to achieve the reliability and fault tolerance for WSNs based on the evolutionary game. The dynamic models provide real-time prediction and fault-tolerance. The dynamics of the proposed models are involved into the time-dependent failure rate and time-dependent failure modes. The utility function of the proposed evolutionary game is formulated as reliability or survivability of the WSN in which a sensor node can be sacrificed to achieve the optimal network sustainability. The same concept of dynamic hybrid fault models has been extended [74] and extensively studied in [73].In [72], the WSN sensors are mapped as a biological population using evolutionary game in which the payoff function is represented by reliability of players. The dragonfly adult concept has been studied in [75] to guarantee optimal channel time sharing in WSNs using evolutionary game. Consequently, selfish behavior of nodes can be treated. The utility function is called fitness function that is represented by the sensors’ targets. In [71], the authors propose a defense strategy for WSNs aiming at reaching a stable state between the defender and the attacker using evolutionary game. More specifically, the sensor nodes can be active and dynamic to adjust their defense strategy. The payoff function is represented by a combination of some parameters of defender and attacker, e.g., reward of successive forwarded packets, security measuring cost, successful attack, failure attack, attacking cost, and probability of successful attack attempts.
4.5. Defense Strategies Classification
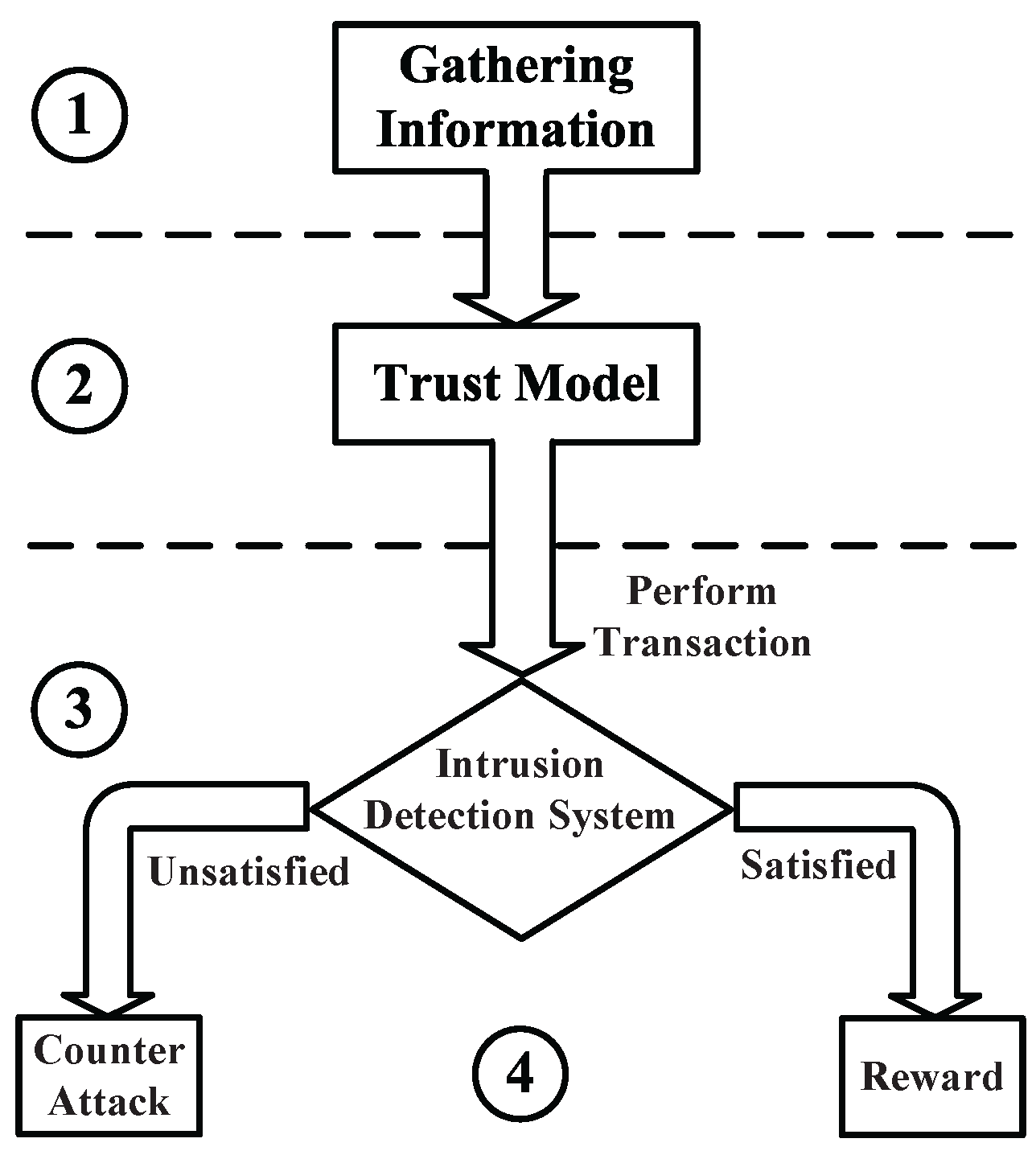
5. Game Theory-Based General Trust Model
6. Applicable Future Trends
6.1. Evolutionary Game for WSNs Security
- The evolutionarily stable strategies (ESS) or evolutionary equilibrium assists in the NE perfection, specifically when multiple Nash equilibria exist.
- The evolutionary game modeling is suitable for human scenarios with agents that may not have hyper-rational or strong rational behavior.
- The evolutionary game is based on an evolutionary process due to its dynamic nature, which organizes the dynamics of interactions among agents in the population. In other words, the strategy adaptation continues over time. On the contrary, most of the traditional non-cooperative games are evolved in a static setting [21].
6.2. Intelligent Attacks
6.3. Attractive WSNs Applications
6.3.1. Cognitive Radio Sensor Networks (CRSNs)
6.3.2. Wireless Underground or Underwater Sensor Networks
6.3.3. Smart Grid Networks
6.3.4. Energy Harvesting
6.3.5. Wireless Body Area Networks (WBANs)
6.3.6. Cyber Physical Systems (CPSs)
7. Conclusions
Conflicts of Interest
Abbreviations
| BBNs | Body-to-Body networks |
| C | Cooperative |
| CPS | Cyber Physical System |
| CR | Cognitive Radio |
| CRSN | Cognitive Radio Sensor Network |
| CSMA/CA | Carrier Sense Multiple Access/Collision Avoidance |
| CMP | Core Mesh Routing Protocol |
| Clr | Clear |
| DoS | Denial of Service |
| ESS | Evolutionary Stable Strategies |
| Ex | External |
| EGDAM | Evolutionary Game based Data Aggregation |
| In | Internal |
| IDS | Intrusion Detection System |
| NE | Nash Equilibrium |
| NZS | Nonzero-sum |
| NC | Non cooperative |
| OFDM | Orthogonal Frequency Division Multiplexing |
| PU | Primary User |
| P | Passive |
| QoS | Quality of Service |
| SDN | Software-defined Networking |
| SHEM | Smart Home Energy Management |
| SIM | Socially-aware Interference Mitigation |
| SINR | Signal to Interference Noise Ratio |
| S-LEARN | Self-Learning |
| SNR | Signal to Noise Ratio |
| SSDF | Spectrum Sensing Data Falsification |
| SU | Secondary User |
| UWSNs | Underwater Sensor Networks |
| WBAN | Wireless Body Area Network |
| WSNs | Wireless Sensor Networks |
| ZS | Zero-sum |
References
- Mármol, F.G.; Pérez, G.M. Providing trust in wireless sensor networks using a bio-inspired technique. Telecommun. Syst. 2011, 46, 163–180. [Google Scholar] [CrossRef]
- Lim, H.S.; Ghinita, G.; Bertino, E.; Kantarcioglu, M. A game-theoretic approach for high-assurance of data trustworthiness in sensor networks. In Proceedings of the 28th International Conference on Data Engineering (ICDE), Arlington, VA, USA, 1–5 April 2012; pp. 1192–1203.
- Rani, V.U.; Sundaram, K.S. Review of trust models in wireless sensor networks. Int. J. Comput. Inf. Syst. Control Eng. 2014, 8, 371–377. [Google Scholar]
- Lopez, J.; Roman, R.; Agudo, I.; Fernandez-Gago, C. Trust management systems for wireless sensor networks: Best practices. Comput. Commun. 2010, 33, 1086–1093. [Google Scholar] [CrossRef]
- Pingel, F.; Steinbrecher, S. Multilateral secure cross-community reputation systems for internet communities. In Trust, Privacy and Security in Digital Business; Springer: Milano, Italy, 2008; pp. 69–78. [Google Scholar]
- Ganeriwal, S.; Balzano, L.K.; Srivastava, M.B. Reputation-based framework for high integrity sensor networks. ACM Trans. Sens. Netw. 2008, 4, 15. [Google Scholar] [CrossRef]
- Boukerch, A.; Xu, L.; El-Khatib, K. Trust-based security for wireless ad hoc and sensor networks. Comput. Commun. 2007, 30, 2413–2427. [Google Scholar] [CrossRef]
- Zhang, J.; Shankaran, R.; Orgun, M.A.; Varadharajan, V.; Sattar, A. A trust management architecture for hierarchical wireless sensor networks. In Proceedings of the 35th Conference on Local Computer Networks (LCN), Denver, CO, USA, 10–14 October 2010; pp. 264–267.
- Alzaid, H.; Foo, E.; Nieto, J.G. RSDA: Reputation-based secure data aggregation in wireless sensor networks. In Proceedings of the Ninth International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Otago, New Zealand, 1–4 December 2008; pp. 419–424.
- Li, X.; Zhou, F.; Du, J. LDTS: A lightweight and dependable trust system for clustered wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 924–935. [Google Scholar] [CrossRef]
- Shao, N.; Zhou, Z.; Sun, Z. A lightweight and dependable trust model for clustered wireless sensor networks. In Cloud Computing and Security; Springer: Beijing, China, 2015; pp. 157–168. [Google Scholar]
- Chen, D.; Chang, G.; Sun, D.; Li, J.; Jia, J.; Wang, X. TRM-IoT: A trust management model based on fuzzy reputation for internet of things. Comput. Sci. Inf. Syst. 2011, 8, 1207–1228. [Google Scholar] [CrossRef]
- Ozdemir, S. Functional reputation based reliable data aggregation and transmission for wireless sensor networks. Comput. Commun. 2008, 31, 3941–3953. [Google Scholar] [CrossRef]
- Chae, Y. Redeemable Reputation Based Secure Routing Protocol for Wireless Sensor Networks. PhD Thesis, University of Rhode Island, Kingston, RI, USA, 2012. [Google Scholar]
- Xiang, G.; Jianlin, Q.; Jin, W. Research on trust model of sensor nodes in WSNs. Procedia Eng. 2012, 29, 909–913. [Google Scholar] [CrossRef]
- Bao, F.; Chen, I.R.; Chang, M.; Cho, J.H. Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE Trans. Netw. Serv. Manag. 2012, 9, 169–183. [Google Scholar] [CrossRef]
- Srinivasan, A.; Teitelbaum, J.; Wu, J. DRBTS: Distributed reputation-based beacon trust system. In Proceedings of the 2nd IEEE International Symposium on Dependable, Autonomic and Secure Computing, Indianapolis, IN, USA, 29 September–1 October 2006; pp. 277–283.
- Dogan, G.; Avincan, K. MultiProTru: A kalman filtering based trust architecture for two-hop wireless sensor networks. Peer-to-Peer Netw. Appl. 2016, 1–14. [Google Scholar] [CrossRef]
- Wang, B.; Wu, Y.; Liu, K.R. Game theory for cognitive radio networks: An overview. Comput. Netw. 2010, 54, 2537–2561. [Google Scholar] [CrossRef]
- Roy, S.; Ellis, C.; Shiva, S.; Dasgupta, D.; Shandilya, V.; Wu, Q. A survey of game theory as applied to network security. In Proceedings of the 43rd Hawaii International Conference on System Sciences (HICSS), Kauai, HI, USA, 5–8 January 2010; pp. 1–10.
- Han, Z. Game Theory in Wireless and Communication Networks: Theory, Models, and Applications; Cambridge University Press: Cambridge, UK, 2012. [Google Scholar]
- Shan, X.; Zhuang, J. Hybrid defensive resource allocations in the face of partially strategic attackers in a sequential defender–attacker game. Eur. J. Oper. Res. 2013, 228, 262–272. [Google Scholar] [CrossRef]
- Shan, X.; Zhuang, J. Subsidizing to disrupt a terrorism supply chain [mdash] a four-player game. J. Oper. Res. Soc. 2013, 65, 1108–1119. [Google Scholar] [CrossRef]
- Xu, J.; Zhuang, J. Modeling costly learning and counter-learning in a defender-attacker game with private defender information. Ann. Oper. Res. 2016, 236, 271–289. [Google Scholar] [CrossRef]
- Rao, N.S.; Poole, S.W.; Ma, C.Y.; He, F.; Zhuang, J.; Yau, D.K. Defense of Cyber Infrastructures Against Cyber-Physical Attacks Using Game-Theoretic Models. Risk Anal. 2015, 36, 694–710. [Google Scholar] [CrossRef] [PubMed]
- Guan, P.; Zhuang, J. Modeling Resources Allocation in Attacker-Defender Games with “Warm Up” CSF. Risk Anal. 2015, 36, 776–791. [Google Scholar] [CrossRef] [PubMed]
- Shan, X.; Zhuang, J. Modeling Credible Retaliation Threats in Deterring the Smuggling of Nuclear Weapons Using Partial Inspection-A Three-Stage Game. Decis. Anal. 2014, 11, 43–62. [Google Scholar] [CrossRef]
- Akkarajitsakul, K.; Hossain, E.; Niyato, D.; Kim, D.I. Game theoretic approaches for multiple access in wireless networks: A survey. Commun. Surv. Tutor. 2011, 13, 372–395. [Google Scholar] [CrossRef]
- Shi, H.Y.; Wang, W.L.; Kwok, N.M.; Chen, S.Y. Game theory for wireless sensor networks: A survey. Sensors 2012, 12, 9055–9097. [Google Scholar] [CrossRef] [PubMed]
- Benmammar, B.; KRIEF, F. Game theory applications in wireless networks: A survey. In Proceedings of the 13th International Conference on Software Engineering, Parallel and Distributed Systems (SEPADS’14), Gdansk, Poland, 15–17 May 2014; pp. 15–17.
- Harn, L. Group authentication. IEEE Trans. Comput. 2013, 62, 1893–1898. [Google Scholar] [CrossRef]
- Shen, S.; Yue, G.; Cao, Q.; Yu, F. A survey of game theory in wireless sensor networks security. J. Netw. 2011, 6, 521–532. [Google Scholar] [CrossRef]
- Yu, Y.; Li, K.; Zhou, W.; Li, P. Trust mechanisms in wireless sensor networks: Attack analysis and countermeasures. J. Netw. Comput. Appl. 2012, 35, 867–880. [Google Scholar] [CrossRef]
- Sun, Y.L.; Han, Z.; Yu, W.; Liu, K.R. A trust evaluation framework in distributed networks: Vulnerability analysis and defense against attacks. INFOCOM 2006, 6, 1–13. [Google Scholar]
- Sun, Y.; Han, Z.; Liu, K.R. Defense of trust management vulnerabilities in distributed networks. Commun. Mag. 2008, 46, 112–119. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J.; Vasilakos, A.V. ReTrust: Attack-resistant and lightweight trust management for medical sensor networks. IEEE Trans. Inf. Technol. Biomed. 2012, 16, 623–632. [Google Scholar] [PubMed]
- Komathy, K.; Narayanasamy, P. Trust-based evolutionary game model assisting AODV routing against selfishness. J. Netw. Comput. Appl. 2008, 31, 446–471. [Google Scholar] [CrossRef]
- Kamhoua, C.; Pissinou, N.; Miller, J.; Makki, S.K. Mitigating routing misbehavior in multi-hop networks using evolutionary game theory. In Proceedings of the Globecom Workshops (GC Wkshps), Miami, FL, USA, 6–10 December 2010; pp. 1957–1962.
- Tembine, H.; Altman, E.; El-Azouzi, R. Delayed evolutionary game dynamics applied to medium access control. In Proceedings of the International Conference on Mobile Adhoc and Sensor Systems (MASS), Pisa, Italy, 8–11 December 2007; pp. 1–6.
- Zhang, Y.; Guizani, M. Game Theory for Wireless Communications and Networking; CRC press: Boca Raton, FL, USA, 2011. [Google Scholar]
- Yang, F.; Zhou, X.; Jia, G.; Zhang, Q. A non-cooperative game approach for intrusion detection in smartphone systems. In Proceedings of the Eighth Annual Communication Networks and Services Research Conference (CNSR), Montreal, QC, Canada, 11–14 May 2010; pp. 146–151.
- Pal, R.; Gupta, B.; Cianca, E.; Patel, A.; Kaligotla, S.; Gogar, A.; Wardana, S.; Lam, V.T.; Ganguly, B. Playing ‘games’ with human health the role of game theory in optimizing reliability in wireless health networks. In Proceedings of the 3rd International Symposium on Applied Sciences in Biomedical and Communication Technologies (ISABEL), Rome, Italy, 7–10 November 2010; pp. 1–5.
- Colell, A.M. Bargaining games. In Cooperation: Game-Theoretic Approaches; Springer: Berlin, Germany, 1997; pp. 69–90. [Google Scholar]
- Zhang, G.; Gu, J.; Liu, P.; Ding, E. Cooperative communication strategy for wireless sensor networks based on cooperative game theory. J. Wuhan Univ. Technol. 2010, 32, 133–136. [Google Scholar]
- Niyato, D.; Hossain, E.; Rashid, M.M.; Bhargava, V.K. Wireless sensor networks with energy harvesting technologies: A game-theoretic approach to optimal energy management. IEEE Wirel. Commun. 2007, 14, 90–96. [Google Scholar] [CrossRef]
- Vane, H.R.; Mulhearn, C. The Nobel Memorial Laureates in Economics: An Introduction to Their Careers and Main Published Works; Edward Elgar Publishing: Northampton, MA, USA, 2005. [Google Scholar]
- Osborne, M.J.; Rubinstein, A. A Course in Game Theory; MIT Press: Cambridge, UK, 1994. [Google Scholar]
- Liu, K.R.; Wang, B. Cognitive Radio Networking and Security: A Game-Theoretic View; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Čagalj, M.; Ganeriwal, S.; Aad, I.; Hubaux, J.P. On selfish behavior in CSMA/CA networks. In Proceedings of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM 2005), New York, NY, USA, 13–17 March 2005; Volume 4, pp. 2513–2524.
- Saad, W.; Han, Z.; Debbah, M.; Hjørungnes, A.; Başar, T. Coalitional game theory for communication networks. Signal Proc. Mag. 2009, 26, 77–97. [Google Scholar] [CrossRef]
- Khayatian, H.; Saadat, R.; Mirjalily, G. Distributed power allocation based on coalitional and noncooperative games for wireless networks. In Proceedings of the 5th International Symposium on Telecommunications (IST), Tehran, Iran, 4–6 December 2010; pp. 367–372.
- Vadori, V.; Scalabrin, M.; Guglielmi, A.V.; Badia, L. Jamming in Underwater Sensor Networks as a Bayesian Zero-Sum Game with Position Uncertainty. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Reddy, Y.B.; Srivathsan, S. Game theory model for selective forward attacks in wireless sensor networks. In Proceedings of the 17th Mediterranean Conference on Control and Automation (MED), Thessaloniki, Greece, 24–26 June 2009; pp. 458–463.
- Estiri, M.; Khademzadeh, A. A game-theoretical model for intrusion detection in wireless sensor networks. In Proceedings of the 23rd Canadian Conference on Electrical and Computer Engineering (CCECE), Calgary, AB, Canada, 2–5 May 2010; pp. 1–5.
- Karapistoli, E.; Economides, A.A. Defending jamming attacks in wireless sensor networks using stackelberg monitoring strategies. In Proceedings of the IEEE/CIC International Conference on Communications in China (ICCC), Shanghai, China, 13–15 October 2014; pp. 161–165.
- Tang, X.; Ren, P.; Wang, Y.; Du, Q.; Sun, L. Securing wireless transmission against reactive jamming: A stackelberg game framework. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Abdalzaher, M.S.; Seddik, K.; Muta, O.; Abdelrahman, A. Using Stackelberg game to enhance node protection in WSNs. In Proceedings of the 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 853–856.
- Altman, E.; Avrachenkov, K.; Garnaev, A. A jamming game in wireless networks with transmission cost. In Network Control and Optimization; Springer: Berlin, Germany, 2007; pp. 1–12. [Google Scholar]
- Xiao, L.; Li, Q.; Chen, T.; Cheng, E.; Dai, H. Jamming games in underwater sensor networks with reinforcement learning. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Moussavinik, H.; Byun, S.S.; Balasingham, I. On the steady state in multiuser multiband IR-UWB without NBI detection. In Proceedings of the 6th International Symposium on Wireless Communication Systems (ISWCS), Siena, Italy, 7–10 September 2009; pp. 522–525.
- Moussavinik, H.; Byun, S.S.; Balasingham, I. Towards robustness in multiband/multiuser IR-UWB: Overcoming unknown NBI via FEC and subband scheduling. In Proceedings of the 11th International Conference on Advanced Communication Technology (ICACT), Phoenix Park, Ireland, 15–18 February 2009; Volume 3, pp. 1947–1949.
- Shapley, L.S. Stochastic games. Proc. Natl. Acad. Sci. USA 1953, 39, 1095–1100. [Google Scholar] [CrossRef] [PubMed]
- Susu, A.E.; Acquaviva, A.; Atienza, D.; De Micheli, G. Stochastic modeling and analysis for environmentally powered wireless sensor nodes. In Proceedings of the 6th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks and Workshops (WiOPT), Berlin, Germany, 1–3 April 2008; pp. 125–134.
- Fu, F.; Kozat, U.C. Stochastic game for wireless network virtualization. IEEE/ACM Trans. Netw. (ToN) 2013, 21, 84–97. [Google Scholar] [CrossRef]
- Nguyen, K.C.; Alpcan, T.; Başar, T. Stochastic games for security in networks with interdependent nodes. In Proceedings of the 9th International Conference on Game Theory for Networks (GameNets), Istanbul, Turkey, 13–15 May 2009; pp. 697–703.
- Liu, Y.; Comaniciu, C.; Man, H. A Bayesian game approach for intrusion detection in wireless ad hoc networks. In Proceedings of the ACM Workshop on Game Theory for Communications and Networks, Pisa, Italy, 11–13 October 2006.
- Lin, J.; Xiong, N.; Vasilakos, A.V.; Chen, G.; Guo, W. Evolutionary game-based data aggregation model for wireless sensor networks. IET Commun. 2011, 5, 1691–1697. [Google Scholar] [CrossRef]
- Crosby, G.V.; Pissinou, N. Evolution of cooperation in multi-class wireless sensor networks. In Proceedings of the Local Computer Networks (LCN), Dublin, Ireland, 15–18 Octpber 2007; pp. 489–495.
- Ma, Z.S.; Krings, A.W. Bio-robustness and fault tolerance: A new perspective on reliable, survivable and evolvable network systems. In Proceedings of the Aerospace Conference, Big Sky, MT, USA, 1–8 March 2008; pp. 1–20.
- Ma, Z.S.; Krings, A.W. Dynamic hybrid fault models and the applications to wireless sensor networks (WSNs). In Proceedings of the 11th ACM International Symposium on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Vancouver, BC, Canada, 27–31 October 2008; pp. 100–108.
- Qiu, Y.; Chen, Z.; Xu, L. Active defense model of wireless sensor networks based on evolutionary game theory. In Proceedings of the 6th International Conference on Wireless Communications Networking and Mobile Computing (WiCOM), Chengdu, China, 23–25 September 2010; pp. 1–4.
- Ma, Z.; Krings, A.W. Insect population inspired wireless sensor networks: A unified architecture with survival analysis, evolutionary game theory, and hybrid fault models. In Proceedings of the International Conference on BioMedical Engineering and Informatics (BMEI), Sanya, China, 27–30 May 2008; Volume 2, pp. 636–643.
- Ricardo, V. Fault-Tolerant Wireless Sensor Networks Using Evolutionary Games. PhD Thesis, University of New Mexico, Albuquerque, NM, USA, 2012. [Google Scholar]
- Ma, Z.S.; Krings, A.W. Dynamic hybrid fault modeling and extended evolutionary game theory for reliability, survivability and fault tolerance analyses. IEEE Trans. Reliab. 2011, 60, 180–196. [Google Scholar] [CrossRef]
- Ma, Z.S.; Krings, A.W.; Hiromoto, R.E. Dragonfly as a model for UAV/MAV flight and communication controls. In Proceedings of the Aerospace Conference, Big Sky, MT, USA, 7–14 March 2009; pp. 1–8.
- Reddy, Y.B. A game theory approach to detect malicious nodes in wireless sensor networks. In Proceedings of the Third International Conference on Sensor Technologies and Applications (SENSORCOMM), Athens, Greece, 18–23 June 2009; pp. 462–468.
- Agah, A.; Asadi, M.; Das, S.K. Prevention of DoS Attack in Sensor Networks using Repeated Game Theory. In Proceedings of the ICWN, Las Vegas, NV, USA, 26–29 June 2006; pp. 29–36.
- Wang, Y.; Attebury, G.; Ramamurthy, B. A survey of security issues in wireless sensor networks. Commun. Surv. Tutor. 2006, 8, 1–23. [Google Scholar] [CrossRef]
- Rassam, M.A.; Maarof, M.A.; Zainal, A. A survey of intrusion detection schemes in wireless sensor networks. Am. J. Appl. Sci. 2012, 9, 1636. [Google Scholar]
- Li, Y.; Shi, L.; Cheng, P.; Chen, J.; Quevedo, D.E. Jamming attack on Cyber-Physical Systems: A game-theoretic approach. In Proceedings of the 3rd Annual International Conference on Cyber Technology in Automation, Control and Intelligent Systems (CYBER), Nanjing, China, 26–29 May 2013; pp. 252–257.
- Agah, A.; Das, S.K.; Basu, K.; Asadi, M. Intrusion detection in sensor networks: A non-cooperative game approach. In Proceedings of the Third International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 August–1 September 2004; pp. 343–346.
- Agah, A.; Basu, K.; Das, S.K. Preventing DoS attack in sensor networks: A game theoretic approach. In Proceedings of the International Conference on Communications (ICC), Seoul, Korea, 16–20 May 2005; Volume 5, pp. 3218–3222.
- Agah, A.; Das, S.K.; Basu, K. A game theory based approach for security in wireless sensor networks. In Proceedings of the International Conference on Performance, Computing, and Communications, Phoenix, AZ, USA, 15–17 April 2004; pp. 259–263.
- Czarlinska, A.; Kundur, D. Reliable event-detection in wireless visual sensor networks through scalar collaboration and game-theoretic consideration. IEEE Trans. Multimedia 2008, 10, 675–690. [Google Scholar] [CrossRef]
- Ben Abid, I.; Boudriga, N. Game theory for misbehaving detection in wireless sensor networks. In Proceedings of the International Conference on Information Networking (ICOIN), Bangkok, Thailand, 28–30 January 2013; pp. 60–65.
- Misra, S.; Krishna, V.P.; Abraham, K.I. Energy efficient learning solution for intrusion detection in wireless sensor networks. In Proceedings of the 2010 Second International Conference on Communication Systems and Networks, Bangalore, India, 5–9 January 2010; pp. 1–6.
- Kodialam, M.; Lakshman, T. Detecting network intrusions via sampling: A game theoretic approach. In Proceedings of the Twenty-Second Annual Joint Conference of the IEEE Computer and Communications, INFOCOM 2003, San Francisco, CA, USA, 30 March–3 April 2003; Volume 3, pp. 1880–1889.
- Slater, D.; Tague, P.; Poovendran, R.; Li, M. A game-theoretic framework for jamming attacks and mitigation in commercial aircraft wireless networks. In Proceedings of the American Institute of Aeronautics and Astronautics, AIAA Infotech at Aerospace Conference, Washington, DC, USA, 6–9 April 2009; pp. 1880–1889.
- Xiao, L.; Chen, Y.; Lin, W.S.; Liu, K. Indirect reciprocity security game for large-scale wireless networks. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1368–1380. [Google Scholar] [CrossRef]
- Chen, L.; Leneutre, J. Fight jamming with jamming–A game theoretic analysis of jamming attack in wireless networks and defense strategy. Comput. Netw. 2011, 55, 2259–2270. [Google Scholar] [CrossRef]
- Hao, D.; Adhikari, A.; Sakurai, K. Mixed-Strategy game based trust management for clustered wireless sensor networks. In Trusted Systems; Springer: Beijing, China, 2011; pp. 239–257. [Google Scholar]
- An, B.; Tambe, M. Game theory for security: An important challenge for multiagent systems. In Multi-Agent Systems; Springer: Utrecht, The Netherlands, 2011; pp. 17–30. [Google Scholar]
- Luo, Y.; Szidarovszky, F.; Al-Nashif, Y.; Hariri, S. A game theory based risk and impact analysis method for intrusion defense systems. In Proceedings of the International Conference on Computer Systems and Applications (AICCSA), Rabat, Morocco, 10–13 May 2009; pp. 975–982.
- Zhu, Q.; Başar, T. Game-theoretic approach to feedback-driven multi-stage moving target defense. In Decision and Game Theory for Security; Springer: Fort Worth, TX, USA, 2013; pp. 246–263. [Google Scholar]
- Wang, J.; Smith, G. A cross-layer authentication design for secure video transportation in wireless sensor network. Int. J. Secur. Netw. 2010, 5, 63–76. [Google Scholar] [CrossRef]
- Khirwadkar, T.S. Defense Against Network Attacks Using Game Theory. PhD Thesis, University of Illinois at Urbana-Champaign, Champaign, IL, USA, 2011. [Google Scholar]
- Konorski, J. A game-theoretic study of CSMA/CA under a backoff attack. IEEE/ACM Trans. Netw. (TON) 2006, 14, 1167–1178. [Google Scholar] [CrossRef]
- Czarlinska, A.; Luh, W.; Kundur, D. Attacks on sensing in hostile wireless sensor-actuator environments. In Proceedings of the Global Telecommunications Conference (GLOBECOM), Washington, DC, USA, 26–30 November 2007; pp. 1001–1005.
- Laszka, A.; Johnson, B.; Grossklags, J. Mitigation of targeted and non-targeted covert attacks as a timing game. In Decision and Game Theory for Security; Springer: Fort Worth, TX, USA, 2013; pp. 175–191. [Google Scholar]
- Jha, S.; Tripakis, S.; Seshia, S.A.; Chatterjee, K. Game theoretic secure localization in wireless sensor networks. In Proceedings of the International Conference on the Internet of Things (IOT), Cambridge, MA, USA, 6–8 October 2014; pp. 85–90.
- Vovk, V.G. A game of prediction with expert advice. In Proceedings of the ACM Eighth Annual Conference on Computational Learning Theory, New York, NY, USA, 5–8 July 1995; pp. 51–60.
- Vovk, V.; Zhdanov, F. Prediction with expert advice for the Brier game. J. Mach. Learn. Res. 2009, 10, 2445–2471. [Google Scholar]
- Perrig, A.; Stankovic, J.; Wagner, D. Security in wireless sensor networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Agah, A.; Das, S.K. Preventing DoS attacks in wireless sensor networks: A repeated game theory approach. IJ Netw. Secur. 2007, 5, 145–153. [Google Scholar]
- Kamhoua, C.A.; Pissinou, N.; Makki, K. Game theoretic modeling and evolution of trust in autonomous multi-hop networks: Application to network security and privacy. In Proceedings of the International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–6.
- Shila, D.M.; Anjali, T. A game theoretic approach to gray hole attacks in wireless mesh networks. In Proceedings of the Military Communications Conference (MILCOM), San Diego, CA, USA, 16–19 November 2008; pp. 1–7.
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Lin, W.S.; Zhao, H.V.; Liu, K. Cooperation stimulation strategies for peer-to-peer wireless live video-sharing social networks. IEEE Trans. Image Proc. 2010, 19, 1768–1784. [Google Scholar] [CrossRef] [PubMed]
- Chen, R.; Bao, F.; Chang, M.; Cho, J.H. Integrated social and QoS trust-based routing in delay tolerant networks. Wirel. Pers. Commun. 2012, 66, 443–459. [Google Scholar] [CrossRef]
- Alpcan, T.; Başar, T. A game theoretic analysis of intrusion detection in access control systems. In Proceedings of the 43rd Conference on Decision and Control (CDC), Atlantis, Paradise Island, Bahamas, 14–17 December 2004; Volume 2, pp. 1568–1573.
- Fallah, M.S. A puzzle-based defense strategy against flooding attacks using game theory. IEEE Trans. Dependable Secure Comput. 2010, 7, 5–19. [Google Scholar] [CrossRef]
- Sallhammar, K.; Knapskog, S.J.; Helvik, B.E. Using Stochastic Game Theory to Compute the Expected Behavior of Attackers. PhD Thesis, Norwegian University of Science and Technology, Trondheim, Norway, 2005. [Google Scholar]
- Agah, A.; Basu, K.; Das, S.K. Enforcing security for prevention of DoS attack in wireless sensor networks using economical modeling. In Proceedings of the International Conference on Mobile Adhoc and Sensor Systems Conference, Washington, DC, USA, 7 November 2005; pp. 1–8.
- Agah, A.; Das, S.K.; Basu, K. A non-cooperative game approach for intrusion detection in sensor networks. In Proceedings of the 60th Vehicular Technology Conference (VTC), Los Angeles, CA, USA, 26–29 September 2004; Volume 4, pp. 2902–2906.
- Movahedi, Z.; Hosseini, Z.; Bayan, F.; Pujolle, G. Trust-distortion Resistant Trust Management Frameworks on Mobile Ad hoc Networks: A Survey. Commun. Surv. Tutor. 2015, 18, 1287–1309. [Google Scholar] [CrossRef]
- Mármol, F.G.; Pérez, G.M. TRMSim-WSN, trust and reputation models simulator for wireless sensor networks. In Proceedings of the International Conference on Communications (ICC), Dresden, Germany, 14–18 June 2009; pp. 1–5.
- Misra, S.; Krishna, P.V.; Abraham, K.I. A simple learning automata-based solution for intrusion detection in wireless sensor networks. Wirel. Commun. Mob. Comput. 2011, 11, 426–441. [Google Scholar] [CrossRef]
- Shen, S.; Huang, L.; Fan, E.; Hu, K.; Liu, J.; Cao, Q. Trust dynamics in WSNs: An evolutionary game-theoretic approach. J. Sens. 2016, 10.1155, 1–11. [Google Scholar] [CrossRef]
- Doebeli, M.; Hauert, C.; Killingback, T. The evolutionary origin of cooperators and defectors. Science 2004, 306, 859–862. [Google Scholar] [CrossRef] [PubMed]
- Hofbauer, J.; Sigmund, K. Evolutionary game dynamics. Bull. Am. Math. Soc. 2003, 40, 479–519. [Google Scholar] [CrossRef]
- Foster, D.; Young, P. Stochastic evolutionary game dynamics. Theor. Popul. Biol. 1990, 38, 219–232. [Google Scholar] [CrossRef]
- Ahmad, A.; Ahmad, S.; Rehmani, M.H.; Hassan, N.U. A survey on radio resource allocation in cognitive radio sensor networks. Commun. Surv. Tutor. 2015, 17, 888–917. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, T.; Song, L.; Han, Z. Interference Improves PHY Security for Cognitive Radio Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 609–620. [Google Scholar] [CrossRef]
- Fragkiadakis, A.G.; Tragos, E.Z.; Askoxylakis, I.G. A survey on security threats and detection techniques in cognitive radio networks. Commun. Surv. Tutor. 2013, 15, 428–445. [Google Scholar] [CrossRef]
- Al-Talabani, A.; Nallanathan, A.; Nguyen, H.X. Enhancing secrecy rate in cognitive radio via game theory. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Han, L.; Gao, F.; Zhang, K.; Zhang, S. Sequential detection aided modulation classification in cognitive radio networks. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Li, Y.; Cao, B.; Daneshmand, M.; Zhang, W. Cooperative spectrum sharing with energy-save in cognitive radio networks. In Proceedings of the Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Zhang, N.; Lu, N.; Cheng, N.; Mark, J.W.; Shen, X.S. Cooperative spectrum access towards secure information transfer for CRNs. IEEE J. Sel. Areas Commun. 2013, 31, 2453–2464. [Google Scholar] [CrossRef]
- Gavrilovska, L.; Krco, S.; Milutinovic, V.; Stojmenovic, I.; Trobec, R. Application and Multidisciplinary Aspects of Wireless Sensor Networks: Concepts, Integration, and Case Studies; Springer Science & Business Media: London, UK, 2010. [Google Scholar]
- Vadlamani, S.; Eksioglu, B.; Medal, H.; Nandi, A. Jamming attacks on wireless networks: A taxonomic survey. Int. J. Prod. Econom. 2016, 172, 76–94. [Google Scholar] [CrossRef]
- Kamath, G.; Shi, L.; Song, W.Z.; Lees, J. Distributed travel-time seismic tomography in large-scale sensor networks. J. Parallel Distrib. Comput. 2016, 89, 50–64. [Google Scholar] [CrossRef]
- Premarathne, U.S.; Khalil, I.; Atiquzzaman, M. Trust based reliable transmission strategies for smart home energy management in cognitive radio based smart grid. Ad Hoc Netw. 2016, 41, 15–29. [Google Scholar] [CrossRef]
- Seah, W.K.; Eu, Z.A.; Tan, H.P. Wireless sensor networks powered by ambient energy harvesting (WSN-HEAP)-Survey and challenges. In Proceedings of the 1st International Conference on Wireless Communication, Vehicular Technology, Information Theory and Aerospace & Electronic Systems Technology Wireless (VITAE), Aalborg, Denmark, 17–20 May 2009; pp. 1–5.
- Hawa, M.; Darabkh, K.A.; Al-Zubi, R.; Al-Sukkar, G. A self-learning MAC protocol for energy harvesting and spectrum access in cognitive radio sensor networks. J. Sens. 2016, 2016. [Google Scholar] [CrossRef]
- Maghsudi, S.; Hossain, E. Distributed User Association in Energy Harvesting Small Cell Networks: A Probabilistic Model, Cornell University, 2016. arXiv preprint arXiv:1601.07795. Available online: http://arxiv.org/abs/1601.07795 (accessed on 27 January 2016).
- Meharouech, A.; Elias, J.; Mehaoua, A. A two-stage game theoretical approach for interference mitigation in body-to-body networks. Comput. Netw. 2016, 95, 15–34. [Google Scholar] [CrossRef] [Green Version]
- Yi, C.; Zhao, Z.; Cai, J.; de Faria, R.L.; Zhang, G.M. Priority-aware pricing-based capacity sharing scheme for beyond-wireless body area networks. Comput. Netw. 2016, 98, 29–43. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, H. A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop. Sensors 2016, 16, 443. [Google Scholar] [CrossRef] [PubMed]
- Shan, X.; Zhuang, J. Cost of equity in homeland security resource allocation in the face of a strategic attacker. Risk Anal. 2013, 33, 1083–1099. [Google Scholar] [CrossRef] [PubMed]

| Attack Type | Attacked Layer | P/Clr Attack | Ex/In Attack | Attack Feature | Attack Consequences | Defense Strategy | Game Type |
|---|---|---|---|---|---|---|---|
| Jamming [55,56,59,88,89,90] | L1 [76,78,79] | Clr | Ex | Interfere with radio frequencies | Disrupt whole/portion of the network | Stackelberg [55,56]/Repeated [88]/Evolutionary [89]/Jamming [59,90] | NC/C/NC/NC |
| Tampering [91] | L1 [76,78,79] | Clr | Ex/In | Extract cryptographic keys | Create/replace existing node | Repeated [91] | C |
| Sniffing [92,93,94] | L2 [95] | Clr | Ex | Overhear essential data from neighboring nodes | Penetration network secrecy | Stackelberg [92]/ZS [93,94] | NC |
| Collisions [89] | L2 [76,78,79] | P | In | Simultaneous transmission on the same frequency | Change in portion of data, Checksum mismatch at receiver | Evolutionary [89] | NC |
| Exhaustion [96] | L2 [76,78,79] | Clr | In/Ex | Naive implementation may continuously attempt to retransmit the corrupted packets | Resource exhaustion | Repeated [96] | C |
| Unfairness [42,97] | L2 [78,79] | P | In | Considered weak DoS, Intermittent exploiting the resources | Miss transmission deadline for other nodes in a real-time MAC protocol | Repeated [97]/Bargaining [42] | C |
| Stealthy [98,99] | L2 [78] | Clr | In | Compromise a node and inject false data through that node. | Make the network accept false data | ZS [98]/NZS [99] | NC |
| Energy Drain [76,98] | L2 [78] | Clr | In/Ex | Request from neighboring node to respond after massive traffic transmission | Paralyze the whole network | ZS [76,98] | NC |
| Conflicting behavior [100,101,102] | L3 [103] | Clr | In | Perform differently with different nodes | Decrease trust value of nodes by conflicting their reputation | Repeated [100,101,102] | C |
| Blackhole [82,104] | L3 [103] | Clr | In/Ex | Attract the whole traffic to be routed through it by advertising itself as the shortest route and drop all received message | Block the traffic to the sink, Expand crisis by easily combining with other extra attacker | Repeated [82,104] | C |
| Spoofed, altered, replayed information [66,89] | L3 [76,78,79] | Clr | In/Ex | Disrupt the network traffic | Create routing loop, Extend or shorten source route, Error message generation | Bayesian [66] Evolutionary [89] | NC |
| Selective forwarding [53,76,87,89] | L3 [76,78,79] | Clr | In/Ex | Transmit certain packets and drop others | A malfunction occurs in transmission process | NZS [53]/ZS [76,87]/Evolutionary [89] | NC |
| Sinkhole [82,105] | L3 [76,78,79] | Clr | In | Compromise a node and then attract the surrounding nodes to use it as next node | Lose huge number of packets, Retransmit lost packets, Increase delay, Exhaust nodes | NZS [82]/Evolutionary [105] | NC |
| Sybil [66,89,106] | L3 [76,78,79] | Clr | In | One node presents more than one ID | Exhaust nodes’ power | Stochastic [106]/Bayesian [66]/Evolutionary [89] | NC |
| Wormhole [82] | L3 [76,78,79] | Clr | In | Low-latency that links between two portions of the network where the messages replayed | Paralyze the whole network, Network traffic jamming | NZS [82] | NC |
| Hello flood | L3 [76,78,79,107] | Clr | Ex | Use high powered- transmitter to deceive neighbors that it has the trajectory towards the base station | The neighbor believe that attacker, Control the data flow | ZS /NZS | NC |
| Acknowledgment spoofing [66,89] | L3 [76,78,79] | Clr | In | Spoof the ACKs of overhead packets destined for neighboring nodes in order to provide false information to those neighboring nodes | Disrupt and confuse routing mechanism | Stochastic [66]/Evolutionary [89] | NC |
| Badmouthing [108] | L3 [109] | Clr | In | Propagate negative reputation information about good nodes | Block valid path by confusing reputation system | Repeated [108] | C |
| Goodmouthing (opposite Badmouthing behavior) | L3 [109] | Clr | In | Propagate positive reputation information about bad nodes | Block valid path by confusing reputation system | Repeated | C |
| Whitewashing | L3 [109] | Clr | In | Re-enter the network with new ID and fresh reputation | deteriorate the defense of reputation mechanism | Evolutionary | NC |
| Flooding [77,110,111] | L4 [76,78,79] | Clr | Ex | An attacker may repeatedly make new connection requests until the resources required by each connection are exhausted or reach a maximum limit | System traffic congestion, Cause channel capacity deterioration | Repeated [77,110,111] | C |
| Desynchronization | L4 [76,78,79] | Clr | Ex | Refers to the disruption of an existing connection | Repeatedly spoof messages to an end host, causing that host to request the retransmission of missed frames | Repeated | C |
| Intelligent behavior [112] | - | Clr | In | Selectively provide services good or bad, high or low values of recommendation according to threshold of trust rating | Disrupt trust system order indistinguishably, Increase the cost of reputation evaluation | Stochastic [112] | NC |
| DoS [77,82,104,110,113,114] | L1-L4 [76,78] | Clr | In/Ex | Prevent any part of WSNs from functioning correctly or in a timely manner | Split the network grid and take control of part of the network by inserting a new sink node jam and tampering network | Repeated [77,104,110]/NZS [82,113,114] | C/NC |
| ON-OFF | - | Clr | In | Behave well or badly by exploiting the dynamic properties of trust through time-domain inconsistent behaviors | Remain undetected while causing damage | Evolutionary | NC |
| Attack Type | Features |
|---|---|
| Badmouthing attack | Grants negative feedback on a node in order to disrupt its reputation. |
| Goodmouthing attack | Grants positive feedback about a malicious entity. |
| ON-OFF attack | Occurs when an adversary attempts to initiate a security attack or a mixture of attacks based irregular manner in order to make its reputation acceptable. |
| Sybil attack | Occurs when a node in a network claims multiple identities. |
| Whitewashing attack | Exists when an attacker resets a poor reputation by re-entering the system with a new identity. |
| Stealthy attack | Operates quietly, hides the evidence of its actions, disrupts the traffic stream from arriving the destination through malicious behavior at third party node. |
| Conflicting behavior attack | Deteriorates the reputation of good nodes by performing differently for different peers. |
| Intelligent behavior attack | Uses different behaviors based on unfixed strategy to manipulate good nodes. |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdalzaher, M.S.; Seddik, K.; Elsabrouty, M.; Muta, O.; Furukawa, H.; Abdel-Rahman, A. Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey. Sensors 2016, 16, 1003. https://doi.org/10.3390/s16071003
Abdalzaher MS, Seddik K, Elsabrouty M, Muta O, Furukawa H, Abdel-Rahman A. Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey. Sensors. 2016; 16(7):1003. https://doi.org/10.3390/s16071003
Chicago/Turabian StyleAbdalzaher, Mohamed S., Karim Seddik, Maha Elsabrouty, Osamu Muta, Hiroshi Furukawa, and Adel Abdel-Rahman. 2016. "Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey" Sensors 16, no. 7: 1003. https://doi.org/10.3390/s16071003






