The Survey on Near Field Communication
Abstract
:1. Introduction
2. NFC Technology Essentials
2.1. NFC as a Contributor Technology
2.2. NFC Communication
2.3. NFC Smartphones

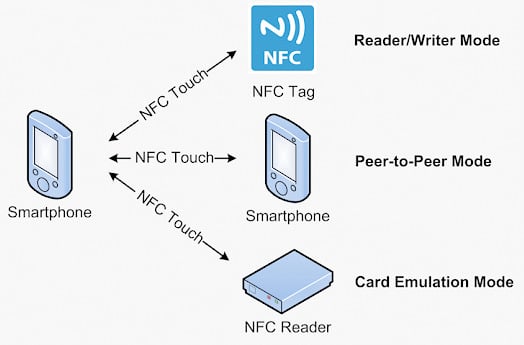
2.4. NFC Operating Modes
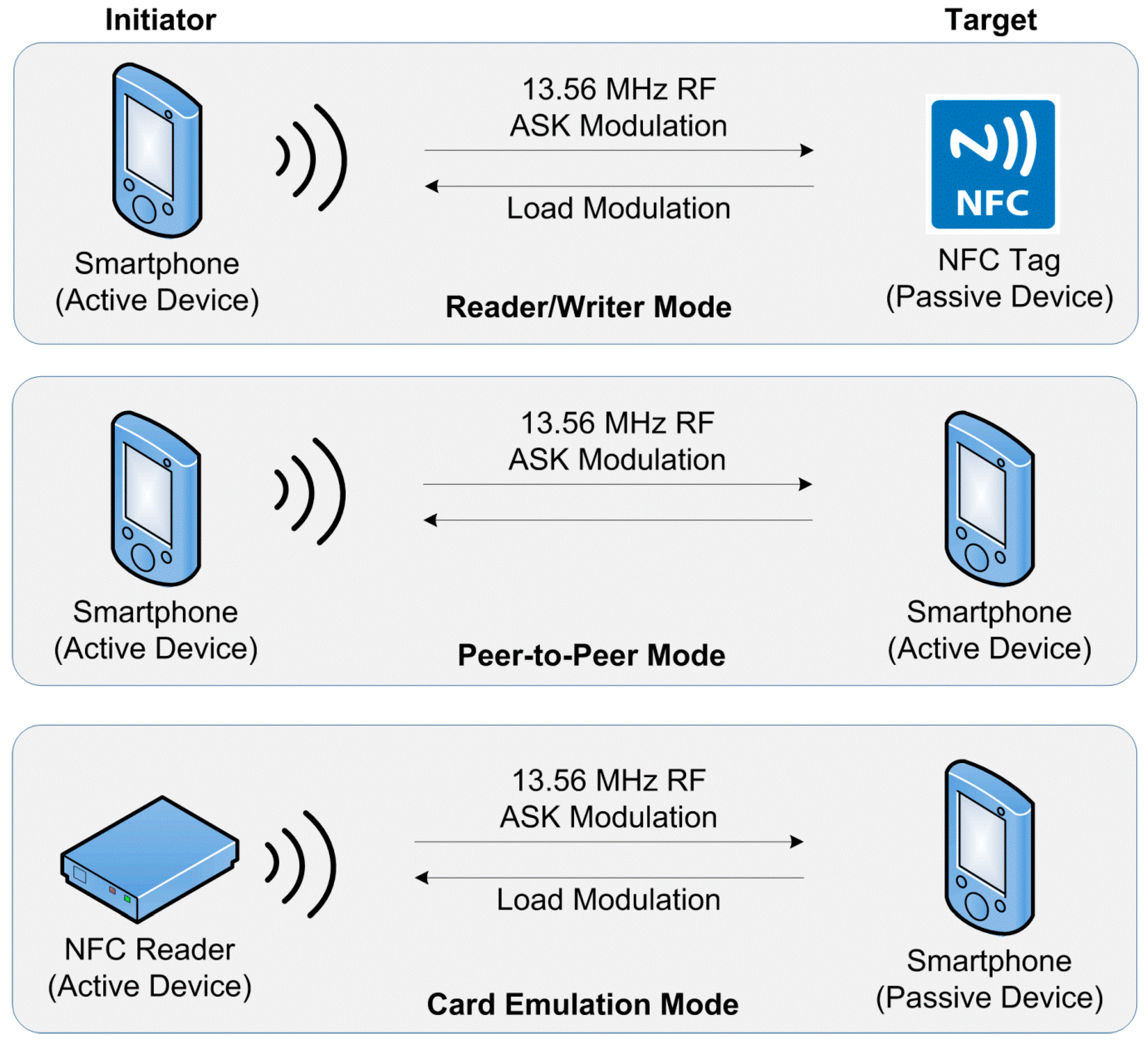
2.4.1. Reader/Writer Mode Communication Essentials

2.4.2. Peer-to-Peer Mode Communication Essentials

2.4.3. Card Emulation Mode Communication Essentials

2.5. Further Research Opportunities
- Development of alternative protocols for NFC additional to SNEP for promoting P2P transactions.
- Extended investigation of LLCP with a simulation model.
- Exploration of low-power modulation schemes.
- Design of new modulation and coding techniques for NFC.
- Analysis of low energy consumption models on NFC readers.
- Development of simulation models for NFC tags as transponders.
- Examination of NFC Dynamic Tags which enable dynamic data, rather than NFC Static Tags.
- Integration of NFC technology with OS and novel NFC Stack Architecture models.
- Development of Quality of Service mechanisms in NFC context.
3. Secure Element
3.1. SE Essentials and Alternatives
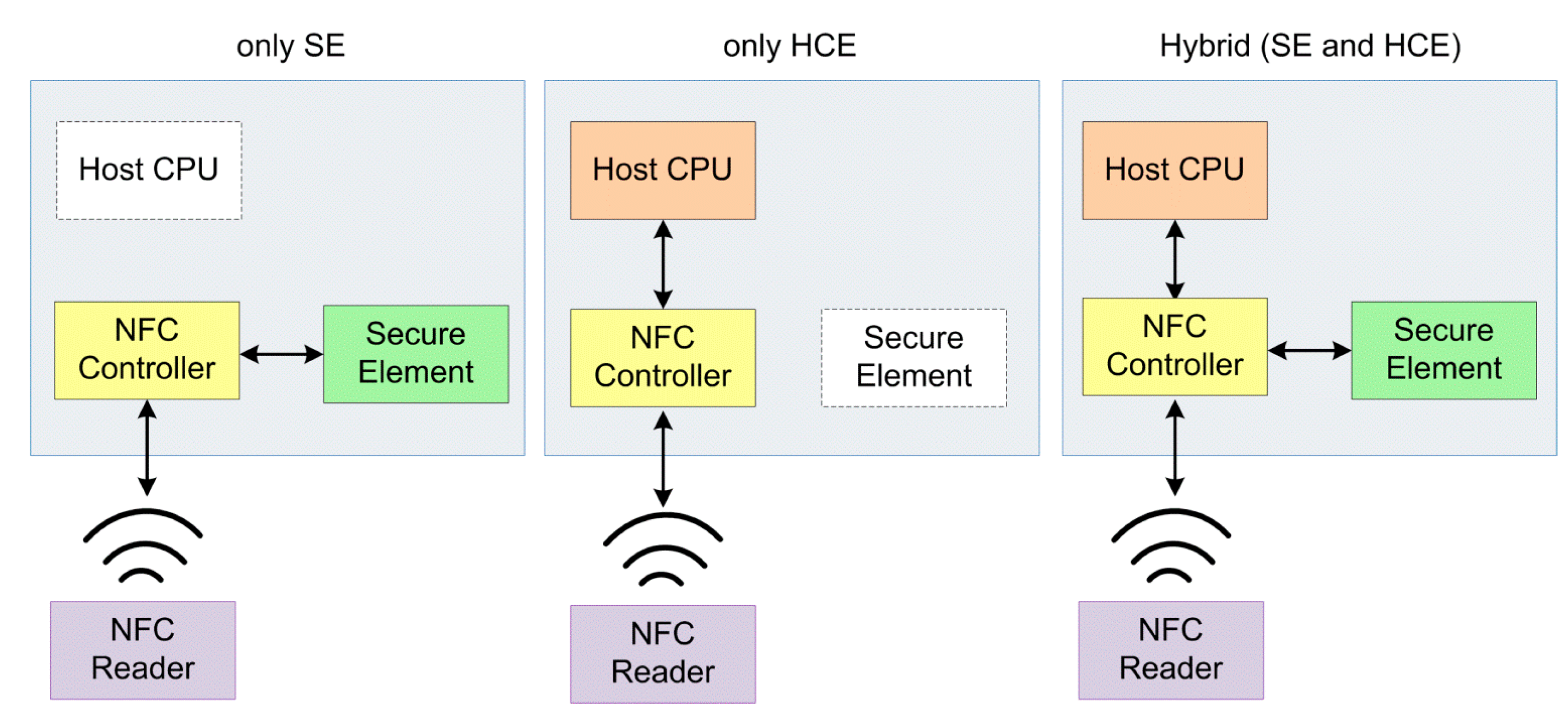
3.2. SE Management
3.3. Further Research Opportunities
- Secure communication protocols for Cloud-based HCE transactions.
- Cloud-based reliable HCE architectures.
- Use cases and prototype implementations of Cloud-based HCE (e.g., access control, ticketing).
- Performance analysis of Cloud-based HCE.
- SE access control models for Smartphone Oss.
- Alternative models for HCE.
- Methods to enhance HCE security.
- Performance and security comparisons of UICC, embedded SE and HCE.
- Connectivity between Cloud-based HCE and Smartphone.
- Cloud based HCE’s off-line running models.
4. NFC Applications in Service Domains
4.1. Healthcare Applications
- (a)
- Healthcare Management Systems.
- (b)
- Diagnosis and Medication by Professionals.
- (c)
- Specific applications for the Disabled, Elderly, and People with Chronic Diseases.
- (d)
- Self-Diagnosis and Medication.
4.1.1. Healthcare Management Systems
4.1.2. Diagnosis and Medication by Professionals
4.1.3. Applications for Disabled, Elderly, and People with Chronic Diseases
4.1.4. Self-Diagnosis and Medication
4.1.5. Further Research Opportunities
- A complete healthcare management system by NFC and prototype implementation.
- Access control of doctors and health institutions to patient records on SEs of smartphones.
- Managing medical data (i.e., how and where to store which part of the information).
- Medical data structure and format.
- Medical care of patients at home.
- NFC based healthcare system requirements for elderly and disabled people.
- Re-designing NFC capable medical devices (i.e., a smartphone could easily get the measured data, or the device can get the patient data from the smartphone, etc.).
- Cloud HCE based health card applications and prototype implementations.
4.2. Location Based Services
4.2.1. Tracking Applications
4.2.3. Identification and Access Control Applications
4.2.4. Further Research Opportunities
- Integrating wireless sensors with NFC for tracking user behavior and enabling valuable services.
- Identification and access control use cases and prototype implementations in diverse areas.
- Usability studies of LBSs.
4.3. Financial Applications
4.3.1. Payment, E-Money and E-Wallet Applications
4.3.2. Ticketing Applications
4.3.3. Coupon Applications
4.3.4. Loyalty Applications
4.3.5. Further Research Opportunities
- E-Wallet use cases and implementations including loyalty cards and coupons.
- HCE based financial applications and prototype implementations.
- Usability studies of NFC-based financial applications and their comparison with non-NFC alternatives.
4.4. Social Networking Applications
Further Research Opportunities
- Usability of NFC in profile and status updates on social networks.
- Information dissemination using NFC technology.
- Requirements for building NFC-based social network systems.
- Conservation of privacy on social networks.
4.5. Entertainment Applications
Further Research Opportunities
- Pleasure gained by playing NFC enabled games.
- Privacy concerns in peer-to-peer games.
- Technical requirements for NFC-based games.
- Learning systems by NFC-based games.
4.6. Education Applications
Further Research Opportunities
4.7. Miscellaneous NFC Applications
5. NFC Security
- Security of NFC Tags.
- Security of NFC Readers.
- Security of Secure Elements.
- Security of NFC Communication.
5.1. Security of NFC Tags
5.2. Security of NFC Readers
5.3. Security of SEs
5.4. Security of RF Communication
| Vulnerabilities and Attacks | Countermeasures | |
|---|---|---|
| NFC Tags | Tag Manipulation (i.e., NFC Worms, Phishing, DoS Attacks) |
|
| Tag Cloning and Tag Impersonation |
| |
| Tag Replacement and Tag Hiding |
| |
| RF Communication | Eavesdropping |
|
| MIM Attack |
| |
| Relay Attack |
| |
| Data Corruption |
| |
| Data Modification |
| |
| Data Insertion |
| |
| SE | DoS Attack |
|
| Relay attack |
| |
| By passing the applet PINs those controlled by Smartphone applications |
| |
| Vulnerabilities in applets caused by erroneous codes |
| |
| Cloning an asset (e.g., ticket, coupon) |
|
5.5. Further Research Opportunities
- Studies on new authentication protocols and analysis of recently developed tags for eliminating obstacles on off-line and on-line authentication of NFC tags.
- Creating new protocols/mechanisms on off-line and on-line authentication of NFC tags.
- Analyzing security of off-line and on-line authentication of NFC tags.
- Development of security mechanisms for protecting NDEF records within a tag.
- Formal security analysis of proposed applications.
- Experimental security analysis of HCE.
- Security analysis of protocols that makes use Cloud-based HCE.
- Preventing DoS attacks on SEs.
- Experimental comparison of SE alternatives in terms of vulnerability.
- Mechanisms to prevent relay attacks on SEs.
- Mechanisms for preventing the PIN bypass of SE applets that are controlled by smartphone applications.
- Proposal of NFC specific alternative key exchange protocols to prevent various attacks on RF communication.
- Mechanisms to provide user’s privacy.
- Exploration of various NFC service domains in terms of privacy, sensitivity and ethical issues.
6. Usability
6.1. Overall Usability of NFC Services
6.2. Usability of NFC Based Financial Services
- (a)
- product-related factors (perceived usefulness, perceived ease of use, compatibility, perceived security and privacy risk, perceived cost of use, trialability, and additional value of NFC mobile payment);
- (b)
- personal-related factors (personal innovativeness in new technologies, absorptive capacity);
- (c)
- trust based factors; and
- (d)
- attractiveness of alternatives. The authors made use of five academic and 10 practitioner customers. The authors conclude that:
- Customers are unlikely to adopt NFC mobile payments unless Service Providers shed some light on the outstanding characteristics and differentiation of NFC-based mobile payment.
- It is beneficial for the entrepreneurs and Service Providers to classify the market into different segmentations, customize, promote and offer services to suit the specific needs of consumers.
6.3. Usability of NFC Based Healthcare Services
6.4. Further Research Opportunities
- Usability analysis of NFC interaction in various service domains.
- Comparisons of the usability of NFC operating modes.
- Analysis of the NFC wow effect.
7. NFC Ecosystem and Business Models
- Although NFC technology warrants the separation of various applications on the same SE with a high security and minimal risk of interference, certain security specifications prohibit this coexistence. Thus, the management of multiple applications on the same chip is also an unresolved issue.
- OTA service provisioning is a great benefit of mobile technology, which is used to manage SEs without being physically connected to it [263]. However, diverse technical OTA solutions exist with different capabilities that are not interoperable with each other.
- Currently, different SE alternatives are available in the market, hence different NFC service options exist; each actor proposes a different business model that brings more advantage to that actor than others. For example MNO’s propose SIM-based models, since they can control these cards and hence can receive more profit if this model is used, whereas a mobile handset manufacturer provides embedded hardware-based SE models and NFC services to gain more control in the NFC business environment.
Further Research Opportunities
- Development of sustainable ecosystem model alternatives for NFC services including revenue-cost analysis, SE usage, competency and feasibility analysis.
- Examination of proposed NFC applications’ business impacts and models based on various theoretical frameworks.
- Exploration of HCE-based NFC services business models.
- Analysis of business and economic performance of complex NFC applications such as NFC payment, ticketing and transportation.
- Exploration of business case opportunities based on demography, regulation, market structure, and infrastructure readiness etc.
- Identification of liability issues, customer care, and division of other related roles and responsibilities between key stakeholders.
8. Conclusions
Conflicts of Interest
References
- Ok, K.; Coskun, V.; Aydin, M.N.; Ozdenizci, B. Current Benefits and Future Directions of NFC Services. In Proceedings of the IEEE International Conference on Education and Management Technology, Cairo, Egypt, 2–4 November 2010; pp. 334–338.
- Ok, K.; Aydin, M.N.; Coskun, V.; Ozdenizci, B. Exploring Underlying Values of NFC Applications. In Proceedings of the Third International Conference on Information and Financial Engineering, Singapore; 2011; pp. 290–294. [Google Scholar]
- Coskun, V.; Ozdenizci, B.; Ok, K. A Survey on Near Field Communication (NFC) Technology. Wirel. Personal Commun. 2013, 71, 2259–2294. [Google Scholar] [CrossRef]
- Palma, D.; Agudo, J.E.; Sánchez, H.; Macías, M.M. An Internet Of Things Example: Classrooms Access Control Over Near Field Communication. Sensors 2014, 14, 6998–7012. [Google Scholar] [CrossRef] [PubMed]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A Survey on Sensor Networks. Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Tezcan, H.; Cayirci, E.; Coskun, V. A distributed scheme for 3D space coverage in tactical underwater sensor networks. In Proceedings of the Military Communications Conference (MILCOM), Monterey, CA, USA, November 2004; pp. 697–703.
- Atzori, L.; Lera, A.; Morabito, G. The Internet of Things: A Survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Coskun, V.; Ok, K.; Ozdenizci, B. Near Field Communication (NFC): From Theory to Practice, 1st ed.; John Wiley and Sons: London, UK, 2012. [Google Scholar]
- Bravo, J.; Hervas, R.; Nava, S.W.; Chavira, G.; Sanchez, C. Towards Natural Interaction By Enabling Technologies: A Near Field Communication Approach. In Proceedings of the Workshops of the First European Conference on Ambient Intelligence, Darmstadt, Germany, 7–10 November 2007; pp. 338–351.
- Chen, M.Y. Context-Aware for Smartphone Sensing in Over-the-Counter Market: Ambient Intelligence in Mobile Stock Markets. In Proceedings of Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Taichung, Taiwan, 3–5 July 2013; pp. 641–646.
- Cheong, S.N.; Chai, I.; Logeswaran, R. Near Field Communication Mobiquitous Learning System. In Proceedings of the International Conference on Advanced Computer Science Applications and Technologies (ACSAT), Kuching, Malaysia, 23–24 December 2013; pp. 490–494.
- Lai, X.; Liu, Q.; Wei, X.; Wang, W.; Zhou, G.; Han, G. A Survey of Body Sensor Networks. Sensors 2013, 13, 5406–5447. [Google Scholar] [CrossRef] [PubMed]
- Fahier, N; Fang, W. An Advanced Plug-and-Play Network Architecture for Wireless Body Area Network Using HBC, Zigbee and NFC. In Proceedings of the IEEE International Conference on Consumer Electronics—Taiwan (ICCE-TW), Taipei, Taiwan, 26–28 May 2014; pp. 165–166.
- Yi, W.J.; Saniie, J. Smart Mobile System for Body Sensor Network. In Proceedings of the IEEE International Conference on Electro/Information Technology (EIT), Rapid City, SD, USA, 9–11 May 2013; pp. 1–4.
- Urien, P. Cloud of Secure Elements: An Infrastructure for the Trust of Mobile NFC Services. In Proceedings of the 10th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Larnaca, Cyprus, 8–10 October 2014; pp. 213–218.
- Pourghomi, P.; Saeed, M.Q.; Ghinea, G. Trusted Integration of Cloud-Based NFC Transaction Players. In Proceedings of the 9th International Conference on Information Assurance and Security (IAS), Gammarth, Tunisia, 4–6 December 2013; pp. 6–12.
- Coskun, V.; Ozdenizci, B.; Ok, K.; Alsadi, M. NFC Loyal System on the Cloud. In Proceedings of the 7th International Conference on Application of Information and Communication Technologies (AICT), Baku, Soviet Azerbaijan, 23–25 October 2013; pp. 1–5.
- Coskun, V.; Ok, K.; Ozdenizci, B. Professional NFC Application Development for Android, 1st ed.; John Wiley Sons, Wrox: London, UK, 2013. [Google Scholar]
- ECMA 340: Near Field Communication Interface and Protocol 1 (NFCIP-1), ECMA International. Available online: http://www.ecma-international.org/publications/standards/Ecma-340.htm (accessed on 13 April 2015).
- ECMA 352: Near Field Communication Interface and Protocol 2 (NFCIP-2), ECMA International. Available online: http://www.ecma-international.org/publications/standards/Ecma-352.htm (accessed on 13 April 2015).
- Felica. Available online: http://www.sony.net/Products/felica/ (accessed on 13 April 2015).
- ISO/IEC14443, Identification cards—Contactless integrated circuit cards—Proximity cards. Available online: http://www.iso.org/iso/catalogue_detail.htm?csnumber=39693 (accessed on 13 April 2015).
- Gossar, M.; Stark, M.; Gebhart, M.; Pribyl, W.; Soser, P. Investigations to Achieve Very High Data Rates for Proximity Coupling Devices at 13.56 MHz and NFC Applications. In Proceedings of the 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 71–76.
- Park, S.; Park, S.; Park, J.; Baek, D. Design of 13.56 MHz ASK Transmitter for Near Field Communication Using a DLL Architecture. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Seoul, Korea (South), 20–23 May 2012; pp. 1760–1762.
- Al-Kadi, G.; van de Beek, R.; Ciacci, M.; Kompan, P.; Stark, M. A 13.56 Mbps PSK Receiver for Very High Data Rate 13.56 MHz Smart Card and NFC Applications. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 13–16 January 2012; pp. 180–182.
- Gebhart, M.; Wobak, M.; Merlin, E.; Chlestil, C. Active Load Modulation for Contactless Near-Field Communication. In Proceedings of the IEEE International Conference on RFID-Technologies and Applications (RFID-TA), Nice, France, 5–7 November 2012; pp. 228–233.
- Man, F.; Shuqiang, X.; Lenan, W. Research on High-Speed NFC Transmission Based on High-Efficiency EBPSK Modulation. In Proceedings of the 5th International Conference on Wireless, Mobile and Multimedia Networks (ICWMMN 2013), Beijing, China, 22–25 November 2013; pp. 119–122.
- Stark, M.; Gebhart, M. How to Guarantee Phase-Synchronicity in Active Load Modulation for NFC and Proximity. In Proceedings of the 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Kang, E.; Won Hong, S.; Seog Han, D. Improved Speed NFC with Rotated QPSK Constellation and Hidden Data Transmission. In Proceedings of IEEE International Symposium on the Broadband Multimedia Systems and Broadcasting (BMSB), Seoul, Korea, 27–29 June 2012; pp. 1–2.
- Azad, U.; Wang, Y.E. Direct Antenna Modulation (DAM) For Enhanced Capacity Performance of Near-Field Communication (NFC) Link. IEEE Trans. Circuits Syst. I Regul. Pap. 2014, 61, 902–910. [Google Scholar] [CrossRef]
- Brown, T.W.C.; Diakos, T. On the Design of NFC Antennas for Contactless Payment Applications. In Proceedings of the 5th European Conference on Antennas and Propagation (EUCAP), Rome, Italy, 11–15 April 2011; pp. 44–47.
- Gebhart, M.; Szoncso, R. Optimizing Design of Smaller Antennas for Proximity Transponders. In Proceedings of the IEEE Second International Workshop on Near Field Communication, Monaco, 20 April 2010; pp. 77–82.
- Ohmura, N.; Takase, E.; Ogino, S.; Okano, Y.; Arai, S. Optimize Pattern of Magnetic Sheet Attached on NFC/HF-RFID Antenna. In Proceedings of the International Symposium on Intelligent Signal Processing and Communications Systems (ISPACS), Naha, Japan, 12–15 November 2013; pp. 627–631.
- Smierzchalski, M.; Collardey, S.; Mahdjoubi, K. A novel metamaterial-based RFID antenna with efficient of operating distance. In Proceedings of the 6th European Conference on Antennas and Propagation (EUCAP), Prague, Czech, 26–30 March 2012; pp. 3038–3041.
- Lee, B.; Kim, B.; Harackiewicz, F.J.; Mun, B.; Lee, H. NFC Antenna Design For Low-Permeability Ferromagnetic Material. IEEE Antennas Wirel. Propag. Lett. 2014, 13, 59–62. [Google Scholar]
- Gebhart, M.; Baier, T.; Facchini, M. Automated Antenna Impedance Adjustment for Near Field Communication (NFC). In Proceedings of the 12th International Conference on Telecommunications (ConTEL), Zagreb, Yugoslavia, 26–28 June 2013; pp. 235–242.
- Ohmura, N.; Takase, E.; Ogino, S.; Okano, Y.; Arai, S. Material Property of On-Metal Magnetic Sheet Attached on NFC/HF-RFID Antenna and Research of Its Proper Pattern and Size on. In Proceedings of the International Symposium on Antennas Propagation (ISAP), Nanjing, China, 23–25 October 2013; pp. 1158–1161.
- Tanabe, Y.; Chang, T.; Yeh, A.; Poon, A. A Small Dual-Band Asymmetric Dipole Antenna for 13.56 MHz Power and 2.45 GHz Data Transmission. IEEE Antennas Wirel. Propag. Lett. 2014, 13, 1120–1123. [Google Scholar] [CrossRef]
- Lee, W.S.; Kim, D.Z.; Yu, J.W. Multi-Functional High-Isolation Dual Antenna for Controllable Wireless Charging and NFC Communication. Electron. Lett. 2014, 50, 912–913. [Google Scholar] [CrossRef]
- Gebhart, M.; Neubauer, R.; Stark, M.; Warnez, D. Design of 13.56 MHz Smartcard Stickers with Ferrite for Payment and Authentication. In Proceedings of the 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 59–64.
- Mujal, J.; Ramon, E.; Díaz, E.; Carrabina, J.; Calleja, A.; Martínez, R.; Teres, L. Inkjet Printed Antennas for NFC Systems. In Proceeding of the 17th IEEE International Conference on Electronics, Circuits, and Systems (ICECS), Athens, Greece, 12–15 December 2010; pp. 1220–1223.
- Pachler, W.; Grosinger, J.; Bosch, W.; Holweg, G.; Popovic, K.; Blumel, A.; List-Kratochvil, E.J. A Silver Inkjet Printed Ferrite NFC Antenna. In Proceedings of the Antennas and Propagation Conference (LAPC), Loughborough, UK, 10–11 November 2014; pp. 95–99.
- Warnick, K.F.; Gottula, R.B.; Shrestha, S.; Smith, J. Optimizing Power Transfer Efficiency and Bandwidth for Near Field Communication Systems. IEEE Trans. Antennas Propag. 2013, 61, 927–933. [Google Scholar] [CrossRef]
- Brown, T.W.; Diakos, T.; Briffa, J.A. Evaluating the Eavesdropping Range of Varying Magnetic Field Strengths in NFC Standards. In Proceedings of the 7th European Conference on Antennas and Propagation (EuCAP), Gothenburg, Sweden, 8–12 April 2013; pp. 3525–3528.
- Chen, Y.S.; Chen, S.Y.; Li, H.J. Analysis of Antenna Coupling in Near-Field Communication Systems. IEEE Trans. Antennas Propag. 2010, 58, 3327–3335. [Google Scholar] [CrossRef]
- Muehlmann, U.; Gebhart, M.; Wobak, M. Mutual Coupling Modeling Of NFC Antennas By Using Open-Source CAD/FEM Tools. In Proceedings of the IEEE International Conference on RFID-Technologies and Applications (RFID-TA), Nice, France, 5–7 November 2012; pp. 393–397.
- Schober, A.; Ciacci, M.; Gebhart, M. An NFC Air Interface Coupling Model for Contactless System Performance Estimation. In Proceedings of the 12th International Conference on Telecommunications (ConTEL), Zagreb, Yugoslavia, 26–28 June 2013; pp. 243–250.
- Yoon, S.K.; Kim, S.J.; Kwon, U.K.; Lee, J.C. Advanced Near Field Communication with Resonant Coupling. In Proceedings of the IEEE 11th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2014; pp. 269–274.
- Menghin, M.; Druml, N.; Kipperer, B.; Steger, C.; Weiss, R.; Bock, H.; Haid, J. Energy Efficiency By Using Field Strength Scaling for Multi-Transponder Applications. In Proceedings of the 12th International Conference on Telecommunications (ConTEL), Zagreb, Yugoslavia, 26–28 June 2013; pp. 263–270.
- Wang, M.; Guo, Y.X.; Wu, W. Equivalent Circuit Analysis of Inductively Coupled NFC Antennas. In Proceedings of the IEEE Antennas and Propagation Society International Symposium (APSURSI), Memphis, TN, USA, 6–11 July 2014; pp. 1540–1541.
- Bauernfeind, T.; Renhart, W.; Schemthanner, S.; Gebhart, M.; Preis, K. Equivalent Circuit Parameter Extraction for Controlled Detuned NFC Antenna Systems Utilizing Thin Ferrite Foils. In Proceedings of the 12th International Conference on Telecommunications (ConTEL), Zagreb, Yugoslavia, 26–28 June 2013; pp. 251–256.
- Cho, J.H.; Cole, P.H.; Kim, S. An NFC Transceiver Using an Inductive Powered Receiver for Passive, Active, RW and RFID Modes. In Proceedings of the International SoC Design Conference (ISOCC), Busan, Korea, 22–24 November 2009; pp. 456–459.
- Roland, M.; Witschnig, H.; Merlin, E.; Saminger, C. Automatic Impedance Matching for 13.56 MHz NFC Antennas. In Proceedings of the 6th International Symposium on Communication Systems, Networks and Digital Signal Processing, Graz, Austria, 25 July 2008; pp. 288–291.
- Li, D.; Shen, M.; Huangfu, J.; Long, J.; Tao, Y.; Wang, J.; Ran, L. Wireless Sensing System-On-Chip For Near-Field Monitoring of Analog and Switch Quantities. IEEE Trans. Ind. Electron. 2012, 59, 1288–1299. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, H.; Dai, Y.; Min, H. An NFC System with High Sensitivity Based on SDR. In Proceedings of the IEEE 10th International Conference on ASIC (ASICON), Shenzhen, China, 28–31 October 2013; pp. 1–4.
- Li, W.; Zhou, D.; Li, M.; Nguyen, B.P.; Zeng, X. Near-Field Communication Transceiver System Modeling and Analysis Using Systemc/Systemc-AMS with the Consideration of Noise Issues. IEEE Trans. Large Scale Integr. (VLSI) Syst. 2013, 21, 2250–2261. [Google Scholar] [CrossRef]
- Dieng, M.; Azais, F.; Comte, M.; Bernard, S. Study of Adaptive Tuning Strategies for NFC Transmitter Module. In Proceedings of the 19th International Mixed-Signals, Sensors and Systems Test Workshop (IMS3TW), Porto Alegre, Brazil, 17–19 September 2014; pp. 1–6.
- Zhang, L.; Xu, H.; Min, H. NFC Quadrature Carrier Cancelling Receiver Design and Implementation. In Proceedings of the 12th IEEE International Conference on Solid-State and Integrated Circuit Technology (ICSICT), Guilin, China, 28–31 October 2014; pp. 1–4.
- Druml, N.; Menghin, M.; Basagic, R.; Steger, C.; Weiss, R.; Bock, H.; Haid, J. NIZE-A Near Field Communication Interface Enabling Zero Energy Standby For Everyday Electronic Devices. In Proceedings of the IEEE 8th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 8–10 October 2012; pp. 261–267.
- Menghin, M.; Druml, N.; Steger, C.; Weiss, R.; Bock, H.; Haid, J. The PTF-Determinator: A Run-Time Method Used to Save Energy in NFC-Systems. In Proceedings of the Fourth International EURASIP Workshop on RFID Technology (EURASIP RFID), Torino, Italy, 27–28 September 2012; pp. 92–98.
- Druml, N.; Menghin, M.; Steger, C.; Weiss, R.; Genser, A.; Bock, H.; Haid, J. Adaptive Field Strength Scaling: A Power Optimization Technique for Contactless Reader/Smart Card Systems. In Proceedings of the 15th Euromicro Conference on Digital System Design (DSD), İzmir, Turkey, 5–8 September 2012; pp. 616–623.
- Menghin, M.; Druml, N.; Steger, C.; Weiss, R.; Bock, R.; Haid, J. NFC-Dynfs: A Way to Realize Dynamic Field Strength Scaling during Communication. In Proceedings of the IEEE 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Madlmayr, G.; Dillinger, O.; Langer, J.; Scharinger, J. Management of Multiple Cards in NFC Devices. In Proceedings of 8th IFIP WG 8.8/11.2 International Conference (CARDIS 2008), London, UK, 8–11 September 2008; pp. 149–161.
- ETSI TS 102 613, Smart Cards; UICC - Contactless Front-end (CLF) Interface; Part 1: Physical and data link layer characteristics, Technical Specification, ETSI TS. Available online: http://www.etsi.org/deliver/etsi_ts/102600_102699/102613/07.03.00_60/ts_102613v070300p.pdf (accessed on 13 April 2015).
- ECMA 373: Near Field Communication Wired Interface (NFC-WI), ECMA International. Available online: http://www.ecma-international.org/publications/standards/Ecma-373.htm (accessed on 13 April 2015).
- NFC Stepping Stones 2011, SIM Alliance, White Paper. Available online: http://simalliance.org/nfc/nfc-technical-releases/ (accessed on 13 April 2015).
- NFC Forum. Available online: http://www.nfc-forum.org/ (accessed on 13 April 2015).
- NFC Controller Interface (NCI), NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Xiao, K.; Luo, L. A Novel Mobile Device NFC Stack Architecture. In Proceedings of the 11th International Conference on Dependable, Autonomic and Secure Computing, Chengdu, China, 21–22 December 2013; pp. 169–173.
- NFC Logical Link Control Protocol LLCP, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Type 1 Tag Operation, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Type 2 Tag Operation, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Type 3 Tag Operation, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Type 4 Tag Operation, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- NFC Data Exchange Format (NDEF), NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- NFC Record Type Definition (RTD), NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- RTD Smart Poster Record Type Definition, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- RTD Text Record Type Definition, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- RTD URI Record Type Definition, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- RTD Signature Record Type Definition, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- NFC Analog, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- NFC Digital Protocol, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- NFC Activity, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Roland, M.; Langer, J. Digital Signature Records for the NFC Data Exchange Format. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 71–76.
- NFC Connection Handover, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Touch the Future with a Smart Touch, VTT, White Paper. Available online: http://www.vtt.fi/inf/pdf/tiedotteet/2009/T2492.pdf (accessed on 13 April 2015).
- Ali, W.; ElKilani, W.; Hadhoud, M. Simulation of NFCIP-1 Protocol over NS-2. In Proceedings of the 7th International Conference on Informatics and Systems (INFOS), Cairo, Egypt, 28–30 March 2010; pp. 1–6.
- Grunberger, S.; Langer, J. Analysis and Test Results of Tunneling IP Over NFCIP-1. In Proceedings of the First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 93–97.
- Lotito, A.; Mazzocchi, D. OPEN-NPP: An Open Source Library to Enable P2P over NFC. In Proceedings of the 4th International Workshop on Near Field Communication (NFC), Helsinki, Finland, 13 March 2012; pp. 57–62.
- Siira, E.; Tormanen, V. The Impact of NFC on Multimodal Social Media Application. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 51–56.
- Urien, P. LLCPS: A New Security Framework Based on TLS for NFC P2P Applications in the Internet of Things. In Proceedings of the Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2013; pp. 845–846.
- Urien, P. LLCPS: A New Secure Model for Internet of Things Services Based on the NFC P2P Model. In Proceedings of the IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 21–24 April 2014; pp. 1–6.
- Simple NDEF Exchange Protocol, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Lotito, A.; Mazzocchi, D. OPEN-SNEP Project: Enabling P2P over NFC using NPP and SNEP. In Proceedings of the 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Monteiro, D.M.; Rodrigues, J.J.; Lloret, J. A Secure NFC Application for Credit Transfer among Mobile Phones. In Proceedings of International Conference on Computer, Information and Telecommunication Systems (CITS), Amman, Jordan, 14–16 May 2012; pp. 1–5.
- NFC Forum Personal Health Device Communication, NFC Forum, Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/ (accessed on 13 April 2015).
- Anwar, W.; Lindskog, D.; Zavarsky, P.; Ruhl, R. Redesigning Secure Element Access Control for NFC Enabled Android Smartphones Using Mobile Trusted Computing. In Proceedings of the International Conference on Information Society (i-Society), Toronto, ON, Canada, 24–26 June 2013; pp. 27–34.
- Urien, P.; Kiennert, C. A New Cooperative Architecture for Sharing Services Managed By Secure Elements Controlled by Android Phones with IP Objects. In Proceedings of the International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 404–409.
- Reveilhac, M.; Pasquet, M. Promising Secure Element Alternatives for NFC Technology. In Proceedings of the First International Workshop on Near Field Communication, Hagenberg, Austria, 24–26 February 2009; pp. 75–80.
- Alternatives for Banks to Offer Secure Mobile Payments, White Paper, Mobey Forum. Available online: http://www.mobeyforum.org/Press-Documents/Press-Releases/Alternatives-for-Banks-to-offer-Secure-Mobile-Payments (accessed on 13 April 2015).
- Host Card Emulation, A Smart Card Alliance Mobile NFC Council White Paper. Available online: http://www.smartcardalliance.org/publications-host-card-emulation-101/ (accessed on 13 April 2015).
- GlobalPlatform Card Specification, GlobalPlatform. Available online: http://www.globalplatform.org/specificationscard.asp (accessed on 13 April 2015).
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Over-The-Internet: Efficient Remote Content Management for Secure Elements in Mobile Devices. In Proceedings of the First Conference on Mobile and Secure Services, Gainesville, FL, USA, 20–21 February 2015; pp. 1–5.
- Alimi, V. A Novel Scheme for On-Demand Distribution of Secure Element Keys. In Proceedings of the World Congress on Computer and Information Technology, Sousse, Tunisia, 22–24 June 2013; pp. 1–5.
- Alimi, V. An Ontology-Based Framework to Model a Globalplatform Secure Element. In Proceedings of the 4th International Workshop on Near Field Communication (NFC), Helsinki, Finland, 13 March 2012; pp. 25–30.
- Ozdenizci, B.; Alsadi, M.; Ok, K.; Coskun, V. Classification of NFC Applications in Diverse Service Domains. Int. J. Comput. Commun. Eng. (IJCCE) 2013, 2, 614–620. [Google Scholar] [CrossRef]
- Gune, A.; Bhat, A.; Pradeep, A. Implementation of NFC Based Healthcare Management System. In Proceedings of the IEEE Symposium on Industrial Electronics and Applications (ISIEA), Kutching, Malaysia, 22–25 September 2013; pp. 195–199.
- Engel, T.; Koennings, M.; von Heydebrand, N.; Goswami, S.; Krcmar, H. A NFC-based Concept for Medication Related Patient Services. In Proceedings of the European Conference on Smart Objects, Systems and Technologies (SmartSysTech), Erlangen/Nuremberg, Germany, 11–12 June 2013; pp. 1–10.
- Sethia, D.; Gupta, D.; Mittal, T.; Arora, U.; Saran, H. NFC based secure mobile healthcare system. In Proceedings of the IEEE Sixth International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 6–10 January 2014; pp. 1–6.
- Dunnebeil, S.; Kobler, F.; Koene, P.; Leimeister, J.M.; Krcmar, H. Encrypted NFC Emergency Tags Based on the German Telematics Infrastructure. In Proceedings of the IEEE 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 50–55.
- Mey, Y.S.; Sankaranarayanan, S. Near field communication based patient appointment. In Proceedings of the IEEE International Conference on Cloud Ubiquitous Computing Emerging Technologies (CUBE), Pune, India, 15–16 November 2013; pp. 98–103.
- Sankarananrayanan, S.; Wani, S.M.A. NFC Enabled Intelligent Hospital Appointment and Medication Scheduling. In Proceedings of the International Conference on Information and Communication Technology (ICoICT), Bandung, Indonesia, 28–30 May 2014; pp. 24–29.
- Morak, J.; Hayn, D.; Kastner, P.; Drobics, M.; Schreier, G. Near field communication technology as the key for data acquisition in clinical research. In Proceedings of the IEEE First International Workshop on Near Field Communication (NFC’09), Hagenberg, Austria, 24 February 2009; pp. 15–19.
- Fontecha, J.; Hervas, R.; Bravo, J.; Villarreal, V. An NFC approach for nursing care training. In Proceedings of the IEEE 3rd International Workshop on Near Field Communication (NFC’11), Hagenberg, Austria, 22 February 2011; pp. 38–43.
- Jara, A.J.; Lopez, P.; Fern’ndez, D.; Ubeda, B.; Zamora, M.A.; Skarmeta, A.F.G. Interaction of Patients with Breathing Problems through NFC in Ambient Assisted Living Environments. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Palermo, Italy, 4–6 July 2012; pp. 892–897.
- Özcanhan, M.H.; Dalkılıç, G.; Utku, S. Cryptographically Supported NFC Tags in Medication for Better Inpatient Safety. J. Med. Syst. 2014, 38, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Ivanov, R. Blind-Environment Interaction through Voice Augmented Objects. J. Multimodal User Interfaces 2014, 8, 345–365. [Google Scholar] [CrossRef]
- Jerabek, M.; Krcal, J. Expansion of Information System with NFC Technology for Visually Impaired Passengers. In Proceedings of the Second International Conference on Informatics and Applications (ICIA), Lodz, Poland, 23–25 September 2013; pp. 306–310.
- Jerabek, M.; Krcal, J.; Zelinka, T. Specification of Requirements for Visually Impaired Persons in Services in Transportation Electronic Information System. Syst. Cybern. Inform. 2014, 12, 59–63. [Google Scholar]
- Zmily, A.; Abu-Saymeh, D. Alzheimer’s Disease Rehabilitation Using Smartphones to İmprove Patients’ Quality of Life. In Proceedings of the 7th International Conference on Pervasive Computing Technologies for Healthcare, Venice, Italy, 5–8 May 2013; pp. 393–396.
- De la Guía, E.; Lozano, M.D.; Penichet, V.R. Cognitive Rehabilitation Based on Collaborative and Tangible Computer Games. In Proceedings of the 7th International Conference on Pervasive Computing Technologies for Healthcare Venice, Italy, 5–8 May 2013; pp. 389–392.
- Prinz, A.; Menschner, P.; Altmann, M.; Leimeister, J.M. inSERT—An NFC-based Self Reporting Questionnaire for Patients with Impaired Fine Motor Skills. In Proceedings of the 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 26–31.
- Prinz, A.; Menschner, P.; Leimeister, J.M. Electronic data capture in healthcare-NFC as easy way for self-reported health status information. Health Policy Technol. 2012, 1, 137–144. [Google Scholar] [CrossRef]
- Alabdulhafith, M.; Sampangi, R.V.; Sampalli, S. NFC-enabled smartphone application for drug interaction and drug allergy detection. In Proceedings of the IEEE 5th International Workshop on on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Alabdulhafith, M.; Sampalli, S. NFC-based Framework for Checking the Five Rights of Medication Administration. Procedia Comput. Sci. 2014, 37, 434–438. [Google Scholar] [CrossRef]
- Morak, J.; Schwarz, M.; Hayn, D.; Schreier, G. Feasibility of mHealth and Near Field Communication technology based medication adherence monitoring. In Proceedings of the Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), San Diego, CA, USA, 28 August–1 September 2012; pp. 272–275.
- Vergara, M.; Díaz-Hellín, P.; Fontecha, J.; Hervás, R.; Sánchez-Barba, C.; Fuentes, C.; Bravo, J. Mobile prescription: An NFC-based proposal for AAL. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 27–32.
- Morak, J.; Schreier, G. Design and Evaluation of Near Field Communication (NFC) Technology Based Solutions for mHealth Challenges. Mob. Health 2015, 5, 813–838. [Google Scholar]
- Koutkias, V.; Kilintzis, V.; Beredimas, N.; Maglaveras, N. Leveraging medication safety through mobile computing: Decision support and guidance services for adverse drug event prevention. In Proceedings of the EAI 4th International Conference on Wireless Mobile Communication and Healthcare (Mobihealth), Athens, Greece, 3–5 November 2014; pp. 19–22.
- Jara, A.J.; Alcolea, A.F.; Alsaedy, M.; Zamora, M.A.; Gómez-Skarmeta, A.F. Drugs interaction checker based on IoT. In Proceedings of the Conference on Internet of Things (IoT), Tokyo, Japan, 20 November–1 December 2010; pp. 1–8.
- Koene, P.; Köbler, F.; Leimeister, J.M.; Krcmar, H. Touch’n’Document—A Nutrition Management System on an NFC-tagged TFT-display. In Proceedings of the International Conference on Health Informatics, Rome, Italy, 26–29 January 2011.
- Yamashita, K.; Izumi, S.; Nakano, M.; Fujii, T.; Konishi, T.; Kawaguchi, H.; Kimura, H.; Marumoto, K.; Fuchikami, T.; Fujimori, Y.; et al. 38 μA wearable biosignal monitoring system with near field communication. In Proceedings of the IEEE 11th International Conference on New Circuits and Systems (NEWCAS), Paris, France, 16–19 June 2013; pp. 1–4.
- Moon, Y.J.; Park, J.H.; Song, W.C.; Lee, D.K.; Choi, D. NFC-based personal information management for U-health. In Proceedings of the IEEE ICCE-China Workshop (ICCE-China), Shenzhen, China, 11–13 April 2013; pp. 39–20.
- Izumi, S.; Kawaguchi, H.; Yoshimoto, M.; Fujimori, Y. Normally-off technologies for healthcare appliance. In Proceedings of the IEEE 19th Asia and South Pasific Design Automation Conference (ASP-DAC), Singapore, 20–23 January 2014; pp. 17–20.
- Raffaeli, L.; Gambi, E.; Spinsante, S. Smart TV based ecosystem for personal e-health services. In Proceedings of the IEEE 8th International Symposium on Medical Information and Communication Technology (ISMICT), Firenze, Italy, 2–4 April 2014; pp. 1–5.
- Zhang, H.; Li, J. NFC in medical applications with wireless sensors. In Proceedings of the IEEE International Conference on Electrical and Control Engineering (ICECE), Yichang, China, 16–18 September 2011; pp. 718–721.
- Opperman, C.A.; Hancke, G.P. A generic NFC-enabled measurement system for remote monitoring and control of client-side equipment. In Proceedings of the IEEE 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 44–49.
- Bittins, B.; Sieck, J. Multimodal and collaborative localisation service for diverse environments. In Proceedings of the IEEE 1st International Symposium on Wireless Systems (IDAACS-SWS), Offenburg, Germany, 20–21 September 2012; pp. 28–33.
- Ho, T.; Chen, R. Leveraging NFC and LBS technologies to improve user experiences. In Proceedings of the IEEE International Joint Conference on Service Sciences (IJCSS), Tapei, Taiwan, 25–27 May 2011; pp. 17–21.
- Siira, E.; Tuikka, T.; Tormanen, V. Location-based mobile Wiki using NFC tag infrastructure. In Proceedings of the IEEE First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 56–60.
- Köbler, F.; Koene, P.; Krcmar, H.; Altmann, M.; Leimeister, J.M. LocaTag—An NFC-based system enhancing instant messaging tools with real-time user location. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 57–61.
- Teufl, P.; Zefferer, T.; Kreuzhuber, S.; Lesjak, C.M. Trusted Location Based Services. In Proceedings of the IEEE International Conference for Internet Technology and Secured Transactions, Kuala Lumpur, Malaysia, 5–8 December 2010; pp. 185–192.
- Nandwani, A.; Edwards, R.; Coulton, P. Contactless check-ins using implied locations: A NFC solution simplifying business to consumer interaction in location based services. In Proceedings of the IEEE International Conference on Electronics Design, Systems and Applications (ICEDSA), Kuala Lumpur, Malaysia, 5–6 November 2012; pp. 39–44.
- Ozdenizci, B.; Ok, K.; Coskun, V.; Aydin, M.N. Development of an indoor navigation system using NFC technology. In Proceedings of the Fourth International Conference on Information and Computing (ICIC), Phuket Island, Thailand, 25–27 April 2011; pp. 11–14.
- Ozdenizci, B.; Coskun, V.; Ok, K. NFC Internal: An Indoor Navigation System. Sensors 2015, 15, 7571–7595. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Edwan, E.; Bourimi, M.; Joram, N.; Al-Qudsi, B.; Ellinger, F. NFC/INS integrated navigation system: The promising combination for pedestrians’ indoor navigation. In Proceedings of the International Symposium on Fundamentals of Electrical Engineering (ISFEE), Bucharest, Romania, 28–29 November 2014; pp. 1–5.
- Hammadi, O.A.; Hebsi, A.A.; Zemerly, M.J.; Ng, J.W. Indoor localization and guidance using portable smartphones. In Proceedings of the 2012 IEEE/WIC/ACM International Joint Conferences on Web Intelligence and Intelligent Agent Technology, Macau, China, 4–7 December 2012; pp. 337–341.
- Lam, K.Y.; Ng, J.K.; Wang, J.T. A Business Model for Personalized Promotion Systems on Using WLAN Localization and NFC Techniques. In Proceedings of the 27th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Barcelona, Spain, 25–28 March 2013; pp. 1129–1134.
- Teh, P.-L.; Ling, H.-C.; Cheong, S.-N. NFC Smartphone Based Access Control System Using Information Hiding. In Proceedings of the IEEE Conference on Open Systems (ICOS), Kuching, Malaysia, 2–4 December 2013; pp. 13–17.
- Derawi, M.O.; Witte, H.; McCallum, S.; Bours, P. Biometric access control using Near Field Communication and smart phones. In Proceedings of the 5th IAPR International Conference on Biometrics (ICB), New Delhi, India, 29 March–1 April 2012; pp. 490–497.
- Mohandes, M.A. Mobile Technology for Socio-Religious Events: A Case Study of NFC Technology. Technol. Soc. Mag. 2015, 34, 73–79. [Google Scholar] [CrossRef]
- Fernández, M.J.L.; Fernández, J.G.; Aguilar, S.R.; Selvi, B.S.; Crespo, R.G. Control of attendance applied in higher education through mobile NFC technologies. Expert Syst. Appl. 2013, 40, 4478–4489. [Google Scholar] [CrossRef]
- Ervasti, M.; Isomursu, M.; Kinnula, M. Experiences from NFC supported school attendance supervision for children. In Proceedings of the Third International Conference on Mobile Ubiquitous Computing, Systems, Services and Technologies (UBICOMM’09), Sliema, Malta, 11–16 October 2009; pp. 22–30.
- Bucicoiu, M.; Tapus, N. Easy attendance: Location-Based authentication for students integrated with moodle. In Proceedings of the 11th Roedunet International Conference (RoEduNet), Sinaia, Romania, 17–19 January 2013; pp. 1–4.
- Shen, C.W.; Wu, Y.C.J.; Lee, T.C. Developing a NFC-equipped smart classroom: Effects on attitudes toward computer science. Comput. Hum. Behav. 2014, 30, 731–738. [Google Scholar] [CrossRef]
- Rodrigues, H.; José, R.; Coelho, A.; Melro, A.; Ferreira, M.C.; Monteiro, M.P.; Ribeiro, C. MobiPag: Integrated Mobile Payment, Ticketing and Couponing Solution Based on NFC. Sensors 2014, 14, 13389–13415. [Google Scholar] [CrossRef] [PubMed]
- Dias, J.; Nuno Matos, J.; Oliveira, A. The Charge Collector System. Procedia Technol. 2014, 17, 130–137. [Google Scholar] [CrossRef]
- Schamberger, R.; Madlmayr, G.; Grechenig, T. Components for an interoperable NFC mobile payment ecosystem. In Proceedings of the 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–5.
- Coneland, R.; Crespi, N. Wallet-on-wheels—Using vehicle’s identity for secure mobile money. In Proceedings of the 17th International Conference on Intelligence in Next Generation Networks (ICIN), Venice, Italy, 15–16 October 2013; pp. 102–109.
- Google Wallet. Available online: https://www.google.com/wallet/ (accessed on 13 April 2015).
- Apple Pay. Available online: https://www.apple.com/apple-pay/ (accessed on 13 April 2015).
- Ghìron, S.L.; Sposato, S.; Medaglia, C.M.; Moroni, A. NFC ticketing: A prototype and usability test of an NFC-based virtual ticketing application. In Proceedings of the First International Workshop on Near Field Communication (NFC’09), Hagenberg, Austria, 24 February 2009; pp. 45–50.
- Neefs, J.; Schrooyen, F.; Doggen, J.; Renckens, K. Paper ticketing vs. Electronic Ticketing based on off-line system ‘Tapango’. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 3–8.
- Widmann, R.; Grunberger, S.; Stadlmann, B.; Langer, J. System integration of NFC ticketing into an existing public transport infrastructure. In Proceedings of the 2012 4th International Workshop on Near Field Communication (NFC), Helsinki, Finland, 13 March 2012; pp. 13–18.
- Nasution, S.M.; Husni, E.M.; Wuryandari, A.I. Prototype of train ticketing application using near field communication (NFC) technology on Android device. In Proceedings of the 2012 International Conference on System Engineering and Technology (ICSET), Bandung, Indonesia, 11–12 September 2012; pp. 1–6.
- Wu, W.J.; Lee, W.H. An NFC E-ticket system with offline authentication. In Proceedings of the 2013 9th International Conference on Information, Communications and Signal Processing (ICICS), Tainan, Taiwan, 10–13 December 2013; pp. 1–5.
- Cha, S.C.; Joung, Y.J.; Tseng, Y.C.; Huang, S.C.; Chen, G.H.; Tseng, C.T. Ensuring the integrity and non-repudiation of remitting e-invoices in conventional channels with commercially available NFC devices. In Proceedings of the 2014 15th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Las Vegas, NV, USA, 30 June–2 July 2014; pp. 1–6.
- Saminger, C.; Grunberger, S.; Langer, J. An NFC ticketing system with a new approach of an inverse reader mode. In Proceedings of the 2013 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–5.
- Dominikus, S.; Aigner, M. mCoupons: An application for near field communication (NFC). In Proceedings of the 21st International Conference on Advanced Information Networking and Applications Workshops Volume: 2, Niagara Falls, ON, Canada, 21–23 May 2007; pp. 421–428.
- Hsiang, H.C.; Kuo, H.C.; Shih, W.K. A secure mCoupon scheme using near field communication. Int. J. Innov. Comput. Inf. Control 2009, 5, 3901–3909. [Google Scholar]
- Hsiang, H.C. A Secure and Efficient Authentication Scheme for M-Coupon Systems. In Proceedings of the 2014 8th International Conference on Future Generation Communication and Networking (FGCN), Haikou, China, 20–23 December 2014; pp. 17–20.
- Sánchez-Silos, J.J.; Velasco-Arjona, F.J.; Ruiz, I.L.; Gomez-Nieto, M.A. An NFC-Based Solution for Discount and Loyalty Mobile Coupons. In Proceedings of the 2012 4th International Workshop on Near Field Communication (NFC), Helsinki, Finland, 13 March 2012; pp. 45–50.
- Borrego-Jaraba, F.; Garrido, P.C.; García, G.C.; Ruiz, I.L.; Gómez-Nieto, M.Á. A Ubiquitous NFC Solution for the Development of Tailored Marketing Strategies Based on Discount Vouchers and Loyalty Cards. Sensors 2013, 13, 6334–6354. [Google Scholar] [CrossRef] [PubMed]
- Ozdenizci, B.; Coskun, V.; Aydin, M.N.; Ok, K. NFC loyal: A beneficial model to promote loyalty on smart cards of mobile devices. In Proceedings of the 2010 International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 8–11 November 2010; pp. 1–6.
- Ozdenizci, B.; Ok, K.; Coskun, V. NFC Loyal for Enhancing Loyalty Services through Near Field Communication. Wirel. Pers. Commun. 2013, 68, 1923–1942. [Google Scholar] [CrossRef]
- Coskun, V.; Ozdenizci, B.; Ok, K.; Alsadi, M.; Soylemezgiller, F. Design and Development of NFC Enabled Loyalty System. In Proceedings of the 6th International Conference of Advanced Computer Systems and Networks: Design and Application, Lviv, Ukraine, 16–18 September 2013; pp. 42–45.
- Ozdenizci, B.; Ok, K.; Alsadi, M.; Coskun, V.; Soylemezgiller, F. Development of NFC enabled loyalty application: Technical and business opportunities. Acad. J. Sci. (AJS) 2014, 3, 141–149. [Google Scholar]
- Ninomiya, H.; Ito, E.; Flanagan, B.; HIrokawa, S. Bridging SNS ID and User Using NFC and SNS. In Proceedings of the 2012 International Conference on Anti-Counterfeiting, Security and Identification (ASID), Taipei, Taiwan, 24–26 August 2012; pp. 1–5.
- Ninomiya, H.; Flanagan, B.; Ito, E.; Hirokawa, S. Near friends communication encouragement system using NFC and SNS. In Proceedings of the 2012 IIAI International Conference on Advanced Applied Informatics (IIAIAAI), Fukuoka, Japan, 20–22 September 2012; pp. 145–148.
- Fressancourt, A.; Hérault, C.; Ptak, E. NFCSocial: Social networking in mobility through IMS and NFC. In Proceedings of the 2009 First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 24–29.
- Kneißl, F.; Rottger, R.; Sandner, U.; Leimeister, J.M.; Krcmar, H. All-i-touch as combination of NFC and lifestyle. In Proceedings of the 2009 First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 51–55.
- Gaito, S.; Quadri, C.; Rossi, G.P.; Zignani, M. THINPLE-the new online Sociality is built on top of NFC-based Contacts. In Proceedings of the 2012 IFIP Wireless Days (WD), Dublin, Ireland, 21–23 November 2012; pp. 1–5.
- Doan, A.; Ramakrishnan, R.; Halevy, A.Y. Crowdsourcing systems on the world-wide web. Commun. ACM 2011, 54, 86–96. [Google Scholar] [CrossRef]
- Barron, J.P.G.; Manso, M.A.; Alcarria, R.; Gomez, R.P. A mobile crowdsourcing platform for urban infrastructure maintenance. In Proceedings of the 2014 Eighth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Birmingham, UK, 2–4 July 2014; pp. 358–363.
- Lochrie, M.; Burnett, D.; Coulton, P. Using NFC check-ins to crowd curate music preferences. In Proceedings of the 2013 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- McDonald’s adds NFC games to restaurant tables. Available online: http://www.nfcworld.com/2013/07/15/324977/mcdonalds-adds-nfc-games-to-restaurant-tables/ (accessed on 13 April 2015).
- Broll, G.; Graebsch, R.; Scherr, M.; Boring, S.; Holleis, P.; Wagner, M. Touch to Play—Exploring Touch-Based Mobile Interaction with Public Displays. In Proceedings of the 2011 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 15–20.
- Christin, D.; Buttner, C.; Repp, N. CachedSensing: Exploring and documenting the environment as a treasure hunt. In Proceedings of the 2012 IEEE 37th Conference on Local Computer Networks Workshops (LCN Workshops), Clearwater, FL, USA, 22–25 October 2012; pp. 973–981.
- Garrido, P.C.; Miraz, G.M.; Ruiz, I.L.; Gomez-Nieto, M.A. Near field communication in the development of ubiquitous games. In Proceedings of the 2010 International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 8–11 November 2010; pp. 1–7.
- Brassai, B.; Varga, B.; Simon, K.; Torok-Vistai, T. GeoQuesting: Mobile adventure game and web-based game editor. In Proceedings of the 2014 IEEE 12th International Symposium on Intelligent Systems and Informatics (SISY), Subotica, Serbia, 11–13 September 2014; pp. 99–103.
- Nandwani, A.; Coulton, P. NFC mobile parlor games enabling direct player to player interaction. In Proceedings of the 2011 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 21–25.
- Idowu, S.; Hagos, D.H.; Tesfay, W.B.; Famurewa, A.; Rana, J.; Synnes, K. NexTrend: Context-Aware Music-Relay Corridors Using NFC Tags. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Taichung, Taiwan, 3–5 July 2013; pp. 573–578.
- Ebner, M.; Maierhuber, M. Near Field Communication-Which Potentials Does NFC Bring for Teaching and Learning Materials? Int. J. Interact. Mob. Technol. (IJIM) 2013, 7, 9–14. [Google Scholar] [CrossRef]
- Miraz, G.M.; Ruiz, I.L.; Gómez-Nieto, M.A. How NFC can be used for the compliance of European higher education area guidelines in European universities. In Proceedings of the 2009 First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 3–8.
- Rios-Aguilar, S.; González-Crespo, R.; de-la-Fuente-Valentin, L. Anonymous Assessment Information System for Higher Education Using Mobile Devices. In Proceedings of the 2014 IEEE 14th International Conference on Advanced Learning Technologies (ICALT), Athens, Greece, 7–10 July 2014; pp. 157–161.
- Bueno-Delgado, M.V.; Pavon-Marino, P.; De-Gea-Garcia, A.; Dolon-Garcia, A. The smart university experience: An NFC-based ubiquitous environment. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Palermo, Italy, 4–6 July 2012; pp. 799–804.
- Garrido, P.C.; Miraz, G.M.; Ruiz, I.L.; Gomez-Nieto, M.A. Use of NFC-based pervasive games for encouraging learning and student motivation. In Proceedings of the 2011 3rd International Workshop on Near Field Communication (NFC), Hagenberg, Austria, 22 February 2011; pp. 32–37.
- Wang, C.C.; Wei, C.R. The Implementation of a Context-Aware Mobile Japanese Conversation Learning System Based on NFC-enabled Smartphones. In Proceedings of the 2014 IIAI 3rd International Conference on Advanced Applied Informatics (IIAIAAI), Kitakyushu, Japan, 31 August–4 September 2014; pp. 313–317.
- Ruiz, L. NFC solution for access to bibliographic sources. In Proceedings of the 2012 IEEE Global Engineering Education Conference (EDUCON), Marrakech, Morocco, 17–20 April 2012; pp. 1–7.
- Broll, G.; Vodicka, E.; Boring, S. Exploring multi-user interactions with dynamic NFC-displays. Pervasive Mob. Comput. 2013, 9, 242–257. [Google Scholar] [CrossRef]
- Hardy, R.; Rukzio, E.; Wagner, M.; Paolucci, M. Exploring expressive NFC-based mobile phone interaction with large dynamic displays. In Proceedings of the 2009 First International Workshop on Near Field Communication, Hagenberg, Austria, 24 February 2009; pp. 36–41.
- Volland, D.; Noyen, K.; Kayikci, O.; Ackermann, L.; Michahelles, F. Switching the role of NFC tag and reader for the implementation of Smart Posters. In Proceedings of the 2012 4th International Workshop on Near Field Communication (NFC), Helsinki, Finland, 13 March 2012; pp. 63–68.
- Pesonen, J.; Horster, E. Near field communication technology in tourism. Tour. Manag. Perspect. 2012, 4, 11–18. [Google Scholar] [CrossRef]
- Hsieh, M.Y.; Wu, T.Y.; Tsai, Y.T.; Shih, C.H.; Li, K.C. Interactive design using non-touch technologies for group trip. In Proceedings of the 2012 International Symposium on Intelligent Signal Processing and Communications Systems (ISPACS), New Taipei, Taiwan, 4–7 November 2012; pp. 216–221.
- Yan-Guang, C.; Ya-ming, Z.; Tao, Z.; Yi, Y. A Hybrid Ontology Knowledge Integration for Farm-based Tourism with NFC. In Proceedings of the Fourth International Conference on Instrumentation and Measurement, Computer, Communication and Control, Harbin, China, 18–20 September 2014; pp. 548–553.
- Basili, A.; Liguori, W.; Palumbo, F. NFC Smart Tourist Card: Combining Mobile and Contactless Technologies towards a Smart Tourist Experience. In Proceedings of the 2014 IEEE 23rd International WETICE Conference (WETICE), Parma, Italy, 23–25 June 2014; pp. 249–254.
- Paradowski, D.; Kruger, A. Modularization of mobile shopping assistance systems. In Proceedings of the 2013 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6.
- De Luca, G.; Lillo, P.; Mainetti, L.; Mighali, V.; Patrono, L.; Sergi, I. The use of NFC and Android technologies to enable a KNX-based smart home. In Proceedings of the 2013 21st International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Primosten, Croatia, 18–20 September 2013; pp. 1–7.
- Di Rosa, E.; Benente, F. “Excavate and learn”: Enhancing visitor experience with touch and NFC. In Proceedings of the 2013 Digital Heritage International Congress (Volume: 2), Marseille, France, 28 October–1 November 2013; pp. 689–692.
- Jara, A.J.; Skarmeta, A.F.; Parra, M.C. Enabling Participative Marketing through the Internet of Things. In Proceedings of the 2013 27th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Barcelona, Spain, 25–28 March 2013; pp. 1301–1306.
- Argueta, D.; Lu, Y.T.; Ma, J.; Rodriguez, D.; Yang, Y.H.; Phan, T.; Jeon, W. Enhancing the restaurant dining experience with an NFC-enabled mobile user interface. Mob. Comput. Appl. Serv. 2014, 130, 314–321. [Google Scholar]
- Ramanathan, R.; Imtiaz, J. NFC in industrial applications for monitoring plant information. In Proceedings of the 2013 Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013; pp. 1–4.
- Lee, S.; Lee, T.; Kim, K.H.; Hong, M. A fast and efficient wireless AP connection approach based on NFC Tag. In Proceedings of the 2013 International Conference on ICT Convergence, Jeju, Korea, 14–16 October 2013; pp. 1076–1077.
- Caimei, H.; Zhikun, H.; Yuefeng, Y.; Jian, W.; Ruonan, Y. Design of reverse search car system for large parking lot based on NFC technology. In Proceedings of the 26th Chinese Control and Decision Conference, Changsha, China, 31 May–2 June 2014; pp. 5054–5056.
- Ang, J.T.; Chin, S.W.; Chin, J.H.; Choo, Z.X.; Chang, Y.M. iSCAPS-Innovative Smart Car Park System integrated with NFC technology and e-Valet function. In Proceedings of the 2013 World Congress on Computer and Information Technology (WCCIT), Sousse, Tunisia, 22–24 June 2013; pp. 1–6.
- Ok, K.; Coskun, V.; Aydin, M.N. Usability of mobile voting with NFC technology. In Proceedings of IASTED International Conference on Software Engineering, Innsbruck, Austria, 16–18 February 2010; pp. 151–158.
- Mulliner, C. Vulnerability Analysis and Attacks on NFC-Enabled Mobile Phones. In Proceedings of the International Conference on Availability, Reliability and Security, Fukuoka, Japan, 16–19 March 2009; pp. 695–700.
- Roland, M.; Langer, J.; Scharinger, J. Security Vulnerabilities of the NDEF Signature Record Type. In Proceedings of the 3rd International Workshop on Near Field Communication, Hagenberg, Austria, 22 February 2011; pp. 65–70.
- Saeed, M.Q.; Walter, C.D. Off-line NFC Tag Authentication. In Proceedings of the International Conference Internet Technology and Secured Transactions, London, UK, 10–12 December 2012; pp. 730–735.
- Lehtonen, M.; Staake, T.; Michahelles, F. From Identification to Authentication–A Review of RFID Product Authentication Techniques. In Networked RFID Systems and Lightweight Cryptography; Springer: Berlin/Heidelberg, Germany, 2008; pp. 169–187. [Google Scholar]
- Saeed, M.Q.; Bilal, Z.; Walter, C.D. An NFC Based Consumer-Level Counterfeit Detection Framework. In Proceedings of the Eleventh Annual International Conference on Privacy, Security and Trust (PST), Tarragona, Spain, 10–12 July 2013; pp. 135–142.
- Plos, T.; Hutter, M.; Feldhofer, M.; Stiglic, M.; Cavaliere, F. Security-Enabled Near-Field Communication Tag With Flexible Architecture Supporting Asymmetric Cryptography. IEEE Trans. Large Scale Integr. (VLSI) Syst. 2012, 21, 1965–1974. [Google Scholar] [CrossRef]
- Mitrokotsa, A.; Rieback, M.R.; Tanenbaum, A.S. Classification of RFID Attacks. J. Inf. Syst. Front. 2010, 12, 491–505. [Google Scholar] [CrossRef]
- Roland, M.; Langer, J.; Scharinger, J. Practical Attack Scenarios on Secure Element-Enabled Mobile Devices. In Proceedings of the 4th International Workshop on Near Field Communication, Helsinki, Finland, 13 March 2012; pp. 19–24.
- Alimi, V.; Vernois, S.; Rosenberger, C. Analysis of Embedded Applications by Evolutionary Fuzzing. In Proceedings of the International Conference on High Performance Computing Simulation (HPCS), Bologna, Spain, 21–25 July 2014; pp. 551–557.
- Roland, M.; Langer, J.; Scharinger, J. Applying Relay Attacks to Google Wallet. In Proceedings of the 5th International Workshop on Near Field Communication, Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Ceipidor, U.B.; Medaglia, C.M.; Marino, A.; Morena, M.; Sposato, S.; Moroni, A.; Morgia, M.L. Mobile ticketing with NFC management for transport companies.Problems and solutions. In Proceedings of the 5th International Workshop on Near Field Communication, Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Abu-Saymeh, D.; Abou-Tair, D.D.; Zmily, A. An Application Security Framework for Near Field Communication. In Proceedings of 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 396–403.
- Cheong, S.N.; Ling, H.C.; Teh, P.L. Secure Encrypted Steganography Graphical Password Scheme For Near Field Communication Smartphone Access Control System. Expert Syst. Appl. 2014, 41, 3561–3568. [Google Scholar] [CrossRef]
- Alshehri, A.; Briffa, J.A.; Schneider, S.; Wesemeyer, S. Formal Security Analysis of NFC M-Coupon Protocols Using Casper/FDR. In Proceedings of the 5th International Workshop on Near Field Communication, Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Eun, H.; Lee, H.; Oh, H. Conditional privacy preserving security protocol for NFC applications. IEEE Trans. Consumer Electron. 2013, 59, 153–160. [Google Scholar] [CrossRef]
- Chattha, N.A. NFC-Vulnerabilities and Defense. In Proceedings of the Conference on Information Assurance and Cyber Security, Rawalpindi, Pakistan, 12–13 June 2014; pp. 35–38.
- Haselsteiner, E.; Breitfuß, K. Security in Near Field Communication (NFC) Strengths and Weaknesses. Available online: http://events.iaik.tugraz.at/RFIDSec06/Program/papers/002%20-%20Security%20in%20NFC.pdf (accessed on 13 April 2015).
- ECMA 385: NFC-SEC (NFCIP-1 Security Services and Protocol), ECMA International. Available online: http://www.ecma-international.org/publications/files/ECMA-ST/ECMA-385.pdf (accessed on 13 April 2015).
- Elbaoury, A.; Mohsen, A.; Ramadan, M.; Youssef, M. Practical Provably Secure Key Sharing For Near Field Communication Devices. In Proceedings of the International Conference on Computing, Networking and Communications, San Diego, CA, USA, 28–31 January 2013; pp. 750–755.
- Jung, M.S. A Study on Electronic-Money Technology Using Near Field Communication. Symmetry 2014, 7, 1–14. [Google Scholar] [CrossRef]
- Urien, P.; Piramuthu, S. Elliptic Curve-Based RFID/NFC Authentication with Temperature Sensor Input for Relay Attacks. Decis. Support Syst. 2014, 59, 28–36. [Google Scholar] [CrossRef]
- Ceipidor, U.B.; Medaglia, C.M.; Marino, A.; Sposato, S.; Moroni, A. KerNeeS: A Protocol for Mutual Authentication between NFC Phones and POS Terminals for Secure Payment Transactions. In Proceedings of the 9th International ISC Conference on Information Security and Cryptology (ISCISC), Tabriz, Iran, 13–14 September 2012; pp. 115–120.
- Urien, P.; Piramuthu, S. Framework and Authentication Protocols for Smartphone, NFC, and RFID in Retail Transactions. In Proceedings of the IEEE Eighth International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Melbourne, Australia, 2–5 April 2013; pp. 77–82.
- Abughazalah, S.; Markantonakis, K.; Mayes, K. Secure Mobile Payment on NFC-Enabled Mobile Phones Formally Analysed Using CasperFDR. In Proceedings of the IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications, Beijing, China, 24–26 September 2014; pp. 422–431.
- Thammarat, C.; Chokngamwong, R.; Techapanupreeda, C.; Kungpisdan, S. A Secure Lightweight Protocol for NFC Communications with Mutual Authentication Based on Limited-Use of Session Keys. In Proceedings of the International Conference on Information Networking, Siem Reap, Cambodia, 12–14 January 2015; pp. 133–138.
- Druml, N.; Menghin, M.; Kuleta, A.; Steger, C.; Weiss, R.; Bock, H.; Haid, J. A Flexible and Lightweight ECC-Based Authentication Solution for Resource Constrained Systems. In Proceedings of the 17th Euromicro Conference on Digital System Design, Verona, Italy, 27–29 August 2014; pp. 372–378.
- Urien, P. EMV-TLS, A Secure Payment Protocol for NFC Enabled Mobiles. In Proceedings of the 2014 International Conference on Collaboration Technologies and Systems, Minneapolis, MN, USA, 19–23 May 2014; pp. 203–21.
- Vincent, J.; Alimi, V.; Plateaux, A.; Gaber, C.; Pasquet, M. A Mobile Payment Evaluation Based on a Digital Identity Representation. In Proceedings of the International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 410–418.
- Luo, J.N.; Yang, M.H.; Yang, M.C. An Anonymous Car Rental System Based on NFC. In Proceedings of the International Symposium on Biometrics and Security Technologies, Chengdu, China, 2–5 July 2013; pp. 97–104.
- Rukzio, E.; Leichtenstern, K.; Callaghan, V.; Holleis, P.; Schmidt, A.; Chin, J. An Experimental Comparison of Physical Mobile Interaction Techniques: Touching, Pointing and Scanning. In Proceedings of 8th International Conference (UbiComp 2006), Orange County, CA, USA, 17–21 September 2006; pp. 87–104.
- Broll, G.; Vodicka, E.; Boring, S. Exploring Multi-User Interactions With Dynamic NFC-Displays. Pervasive Mob. Comput. 2013, 9, 242–257. [Google Scholar] [CrossRef]
- Chen, L.; Pan, G.; Li, S. Touch-driven Interaction between Physical Space and Cyberspace with NFC. In Proceedings of the International Conference on and 4th International Conference on Cyber, Physical and Social Computing, Internet of Things, Dalian, China, 19–22 October 2011; pp. 258–265.
- Chen, K.; Chang, M. User Acceptance of ‘Near Field Communication’ Mobile Phone Service: An Investigation Based on the ‘Unified Theory of Acceptance and Use of Technology’ Model. Serv. Ind. J. 2013, 33. [Google Scholar] [CrossRef]
- Mehmood, F.; Hassannezhad, M.; Abbas, T. Analytical Investigation of Mobile NFC Adaption With SWOT-AHP Approach: A Case of Italian Telecom. Procedia Technol. 2014, 12, 535–541. [Google Scholar] [CrossRef]
- Franssila, H. User Experiences and Acceptance Scenarios of NFC Applications in Security Service Field Work. In Proceedings of the Second International Workshop on Near Field Communication (NFC), Monaco, 20 April 2010; pp. 39–44.
- Broll, G.; Palleis, H.; Richter, H.; Wiethoff, A. Exploring Multimodal Feedback for an NFC-Based Mobile Shopping Assistant. In Proceedings of the 5th International Workshop on Near Field Communication, Zurich, Switzerland, 5 February 2013; pp. 1–6.
- Thomas, J.P.; Andreas, S.; Frédéric, T.; Elgar, F. NFC Based Service Innovation in Retail: An Explorative Study. In Proceedings of the 17th European Conference on Information Systems, Verona, Italy, 8–10 June 2009; pp. 1–9.
- Pham, T.T.T.; Ho, J.C. What Are The Core Drivers In Consumer Adoption of NFC-Based Mobile Payments? A Proposed Research Framework. In Proceedings of the International Conference on Management of Engineering Technology (PICMET), Kanazawa, Japan, 27–31 July 2014; pp. 3041–3049.
- Alshahrani, A.M.; Colchester, U.K.; Walker, S. NFC performance in mobile payment service compared with a SMS -based solution. In Proceedings of the International Conference on Green Computing, Communication and Conservation of Energy, Chennai, India, 12–14 December 2013; pp. 282–286.
- Ceipidor, U.B.; Medaglia, C.M.; Opromolla, A.; Volpi, V.; Moroni, A.; Sposato, S. A Survey about User Experience Improvement in Mobile Proximity Payment. In Proceedings of the 4th International Workshop on Near Field Communication, Helsinki, Finland, 13 March 2012; pp. 51–56.
- Leong, L.Y.; Hew, T.S.; Tan, G.W.H.; Ooi, K.B. Predicting the Determinants of the NFC-Enabled Mobile Credit Card Acceptance: A Neural Networks Approach. Expert Syst. Appl. 2013, 40, 5604–5620. [Google Scholar] [CrossRef]
- Häikiö, J.; Wallin, A.; Isomursu, M.; Ailisto, H.; Matinmikko, T.; Huomo, T. Touch-Based User Interface for Elderly Users. In Proceedings of the 9th International Conference on Human Computer Interaction with Mobile Devices and Services, Singapore, 11–14 September 2007; pp. 289–296.
- Two In Three Phones to Come With NFC in 2018, NFC World. Available online: http://www.nfcworld.com/2014/02/12/327790/two-three-phones-come-nfc-2018/ (accessed on 13 April 2015).
- Madlmayr, G.; Langer, J.; Scharinger, J. Managing an NFC Ecosystem. In Proceedings of the 7th International Conference on Mobile Business, Barcelona, Spain, 7–8 July 2008; pp. 95–101.
- Akram, R.N.; Markantonakis, K.; Mayes, K. Building the Bridges—A Proposal for merging different Paradigms in Mobile. In Proceedings of the Eighth International Conference on Computational Intelligence and Security (CIS), Guangzhou, China, 17–18 November 2012; pp. 646–652.
- Benyó, B.; Sódor, B.; Fordos, G.; Kovács, L.; Vilmos, A. A Generalized Approach for NFC Application Development. In Proceedings of the Second International Workshop on Near Field Communication, Monaco, 20 April 2010; pp. 45–50.
- Aziza, H. NFC Technology in Mobile Phone Next-Generation Services. In Proceedings of the Second International Workshop on Near Field Communication, Monaco, 20 April 2010; pp. 21–26.
- Akram, R.N.; Markantonakis, K.; Sauveron, D. Collaborative and Ubiquitous Consumer Oriented Trusted Service Manager. In Proceedings of the 13th International Conference on Trust, Security and Privacy in Computing and Communications, Beijing, China, 24–26 September 2014; pp. 448–456.
- Benyo, B.; Vilmos, A.; Kovacs, K.; Kutor, L. NFC Applications and Business Model of the Ecosystem. In Proceedings of the 16th IST Mobile and Wireless Communications Summit, Budapest, Hungary, 1–5 July 2007; pp. 1–5.
- Ok, K.; Coskun, V.; Ozdenizci, B.; Aydin, M.N. A Role-Based Service Level NFC Ecosystem Model. Wirel. Pers. Commun. 2013, 68, 811–841. [Google Scholar] [CrossRef]
- Ozdenizci, B.; Aydin, M.N.; Coskun, V.; Ok, K. NFC Research Framework: A Literature Review and Future Research Directions. In Proceedings of the 14th International Business Information Management Association Conference on Global Business Transformation through Innovation and Knowledge Management, Istanbul, Turkey, 23–24 June 2010; pp. 23–24.
- Ozdenizci, B.; Aydin, M.N.; Coskun, V.; Ok, K. Design Science in NFC Research. In Proceedings of IEEE International Conference for Internet Technology and Secured Transactions, London, UK, 8–11 November 2010; pp. 1–6.
- The Host Card Emulation in Payments: Options for Financial Institutions, Mobey Forum, White Paper. Available online: http://www.mobeyforum.org/whitepaper/the-host-card-emulation-in-payments-options-for-financial-institutions/ (accessed on 13 April 2015).
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Coskun, V.; Ozdenizci, B.; Ok, K. The Survey on Near Field Communication. Sensors 2015, 15, 13348-13405. https://doi.org/10.3390/s150613348
Coskun V, Ozdenizci B, Ok K. The Survey on Near Field Communication. Sensors. 2015; 15(6):13348-13405. https://doi.org/10.3390/s150613348
Chicago/Turabian StyleCoskun, Vedat, Busra Ozdenizci, and Kerem Ok. 2015. "The Survey on Near Field Communication" Sensors 15, no. 6: 13348-13405. https://doi.org/10.3390/s150613348