Multi-Layer Approach for the Detection of Selective Forwarding Attacks
Abstract
:1. Introduction
2. Related Works
- Resending the packet by using another route causes energy consumption and delays during the detection.
- Transmission of the acknowledgement packet and one-way key packet also cause energy consumption.
- The scheme lacks scalability.
- The scheme spends much effort on detecting the attack thus it lacks efficiency.
- The LWSS scheme could not detect the attacks under some certain conditions.
- Sending the acknowledgment causes wasted energy.
- There is no commitment to reliability if the packet is dropped.
- The network has a static topology. Therefore, the LWD scheme will not detect the attack if there is a change in the type of topology.
- There is no guarantee of reliability.
- The detection scheme is not work if a node is compromised.
- There is no data resend method if the packet is dropped.
- The SDT scheme cannot detect a malicious node if more than two.
- The scheme is not convenient for sensor-caused malicious nodes and the BS cannot compromise.
- The topology is static thus any change will affect the efficiency of the scheme.
- The scheme accuracy is low.
3. Problem Identification
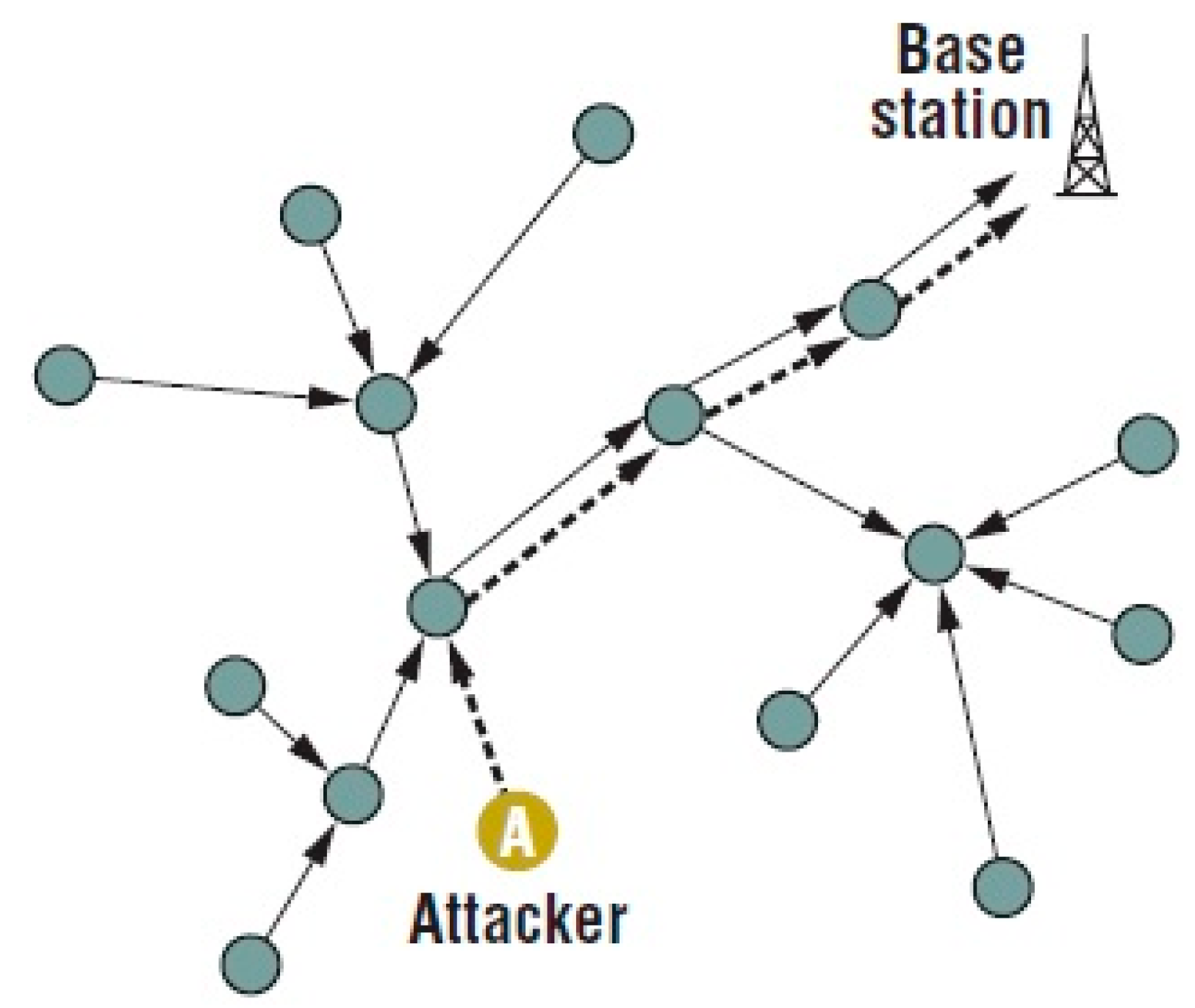
4. Proposed System
4.1. Assumptions
4.2. Selective Forwarding Detection (SFD) Using Multi-Layers
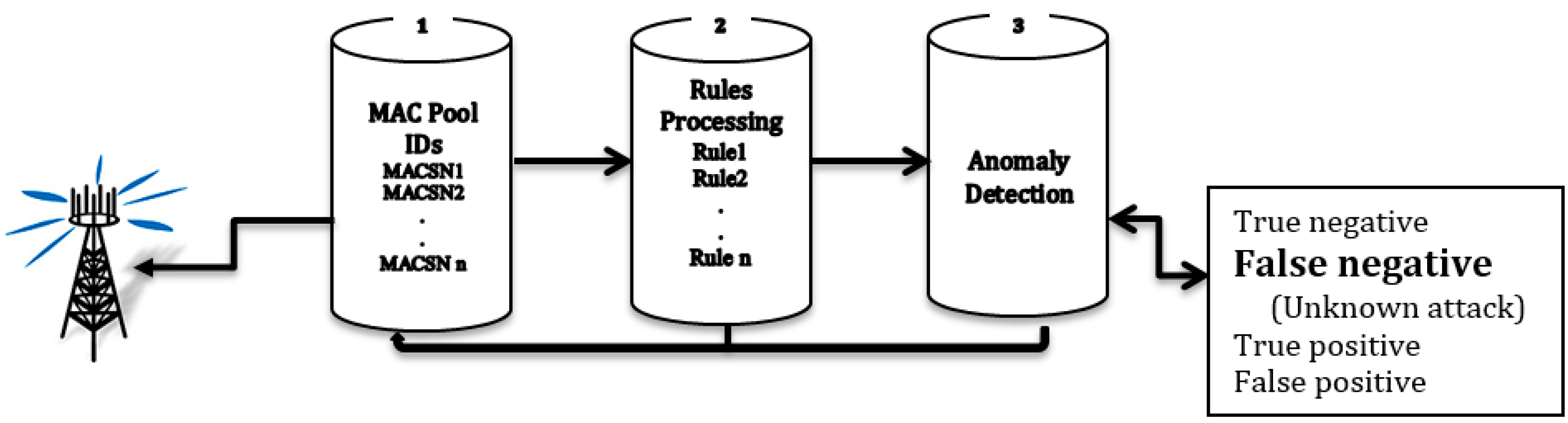

4.3. Selective Forwarding Detection (SFD) Algorithms
4.3.1. MAC Pool of IDs Layer
| Algorithm 1. MAC Pool of IDs Layer |
1. Input = (MP: Mac Pool) 2. Network parameter = (SN: sensor node, RT: route, TSN: Total sensor node) 3. For (SN = 0; SN <= TSN; SN++) 4. Set SN = SN + 1 5. If SN ∈ MP then 6. Set SN = 0 // the node is declared as malicious node not allowed for communication. 7. Rejected 8. Dropped 9. Else if SN = 1 // Node is declared as a legitimate node and allowed for communication 10. Accept 11. Store 12. Set SN = RT 13. SN → RP 14. End if 15. End else 16. End for |
4.3.2. Rules Processing Layer
| Algorithm 2. Rules Processing Layer |
1. Input = (RP: Rules Process) 2. Output = (DT: Selective Forwarding Detector, RU: Rules) 3. Network parameter = (SN: Sensor node, RT: Route) 4. Attacking parameter = (SFAT: Attacker) 5. RL1 = Rules based in IDS (RL1IDS) 6. RP ⊆ RL1IDS 7. Set RL1 >= RU // 90% from the rules 8. For (SFAT = RL1; SFAT <= RP; SFAT ++) 9. If SFAT ⊆ RP then 10. DT → SFAT 11. Attack alert 12. Rejected 13. Dropped 14. Else if (SFAT ⊄ RP) then 15. Set SN = RT 16. SN → AD 17. End if 18. End else 19. End for |
| Rule No. | Rule Description |
|---|---|
| Rule1 | Each node wait to see if the neighbor node forward the message or not. |
| Rule2 | The node that will receives message has to checks the transfer’s identity to make sure it is not change during transferring. |
| Rule3 | Each node makes sure that the next node has a shared key for negotiation. |
| Rule4 | Each node has a message route when it wants to transfer to other node. |
| Rule5 | Each sensor node must have ACKs. |
| Rule6 | Each sensor node must have the same ACK that use. |
| Rule7 | Each node has not created a new response before the previous one transfer. |
| Rule8 | Each node has to send the message using the correct route. |
| Rule9 | Each sensor node only communicates with other sensor nodes that locate in the same topology. |
4.3.3. Anomaly Detection Layer Based on Intrusion Detection System
| Algorithm 3. Anomaly Detection Layer Based on IDS |
1. Input = (AD: Anomaly Detection) 2. Output = (DT: Selective Forwarding Detector) 3. Network parameter = (SN: Sensor node, RT: Route) 4. Attacking parameter = (SFAT: Attacker) 5. RL2 = Anomaly detection based in IDS (RL2IDS) 6. AD ⊆ RL2IDS 7. For (RL2 = 0; RL2 <= AD; RL2 ++) 8. RL2 = RL2 + 1 9. If RL2 ∈ AD then 10. Compute FN 11. FN = 1/N ∑ FN 12. M = 1 13. Set Alert 14. Rejected 15. Dropped 16. Else if RL2 ∉ AD then 17. No Attack 18. Set SN = RT 19. Return 20. SN → MP 21. Declared 22. End if 23. End else 24. End for |
5. Reliable, Energy Efficient and Scalable (RES) Model
6. Results and Discussion
| Parameters | Description |
|---|---|
| Transmission Range | 35 m |
| Sensing Range of node | 30 m |
| Initial energy of a node | 5 J |
| Bandwidth of node | 60 Kb/Sec |
| Number of legitimate sensors | 120 |
| Number of Malicious nodes | 80 |
| Size of network | 800 × 800 m2 |
| Buffering capacity | 45 Packets buffering capacity at each node |
| Data Packet size | 128 bytes |
| Simulation time | 27 min |
| Tx energy | 15.2 mW |
| Rx energy | 11.8 mW |
| Power Intensity | −18 dBm to 13 dBm. |
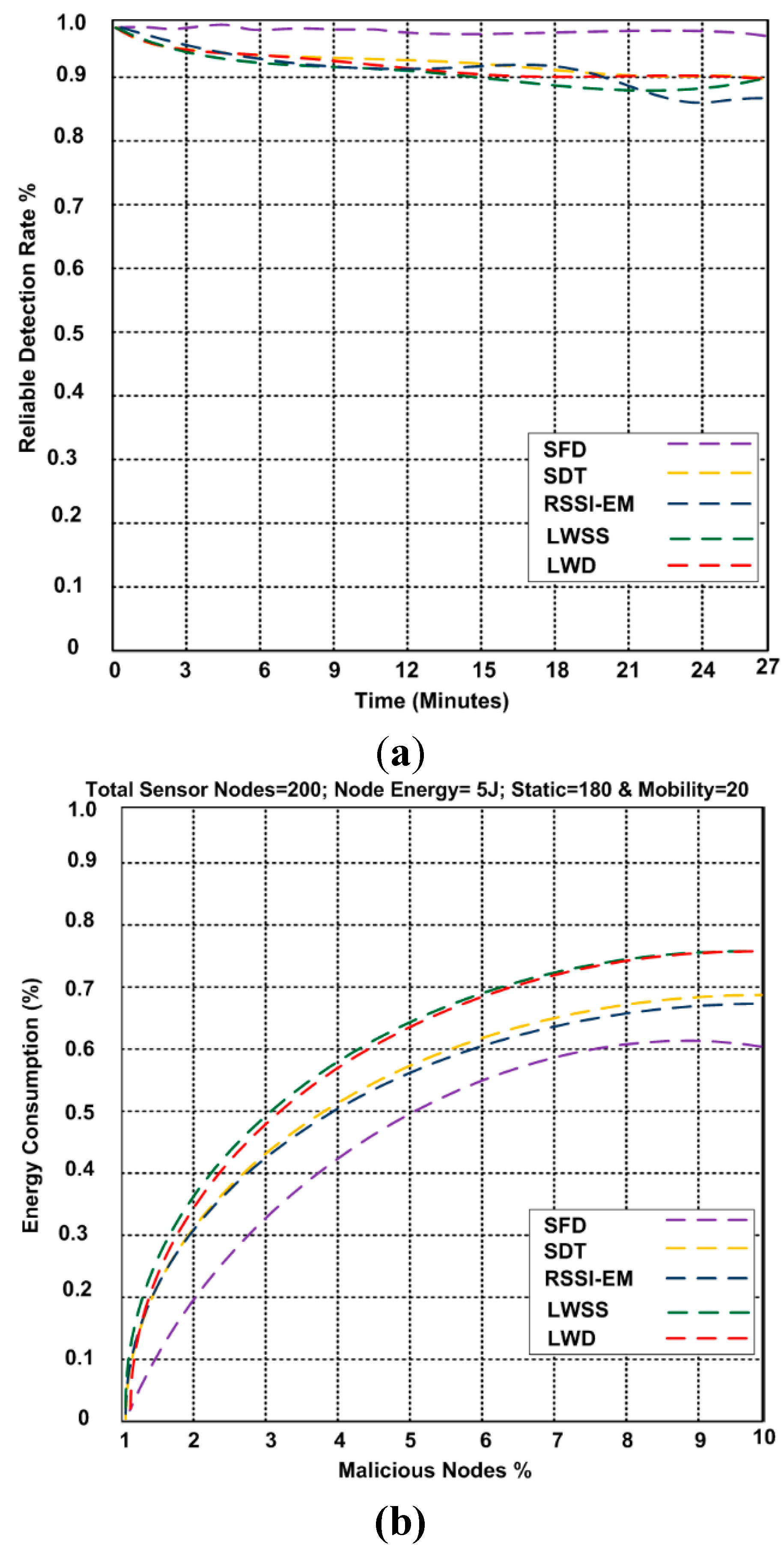
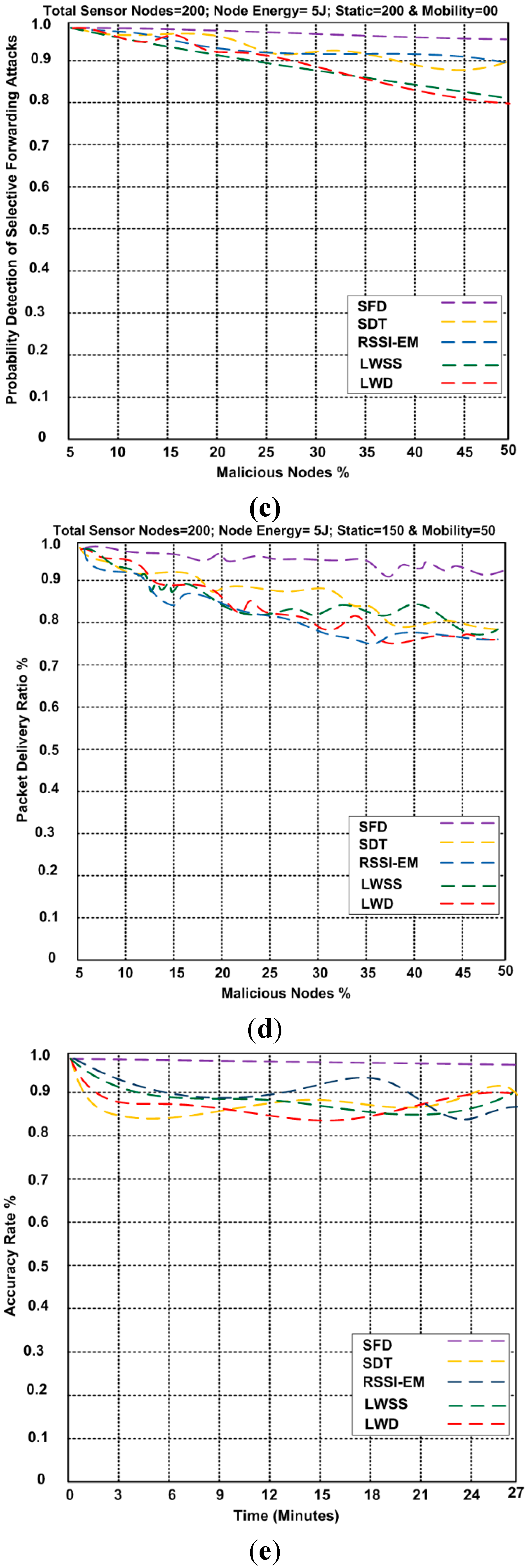
7. Conclusions
Author Contributions
Conflicts of Interest
References
- Akyildiz, I.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Mamun, Q. A Qualitative Comparison of Different Logical Topologies for Wireless Sensor Networks. Sensors 2012, 12, 14887–14913. [Google Scholar] [CrossRef] [PubMed]
- Pathan, A.-S.K.; Lee, H.-W.; Hong, C.S. Security in Wireless Sensor Networks: Issues and Challenges. In Proceedings of the 8th International Conference Advanced Communication Technology, Dublin, Ireland, 20–22 February 2006; Volume 2, pp. 1043–1048.
- Perrig, A.; Stankovic, J.; Wagner, D. Security in Wireless Sensor Networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Kaplantzis, S.; Shilton, A.; Mani, N.; Sekercioglu, Y.A. Detecting Selective Forwarding Attacks in Wireless Sensor Networks using Support Vector Machines. In Proceedings of the 3rd International Conference on Intelligent Sensors, Sensor Networks and Information, Melbourne, Australia, 3–6 December 2007; pp. 335–340.
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Martins, D.; Guyennet, H. Wireless Sensor Network Attacks and Security Mechanisms: A Short Survey. In Proceedings of the 13th International Conference on Network-Based Information Systems (NBiS), Gifu, Japan, 14–16 September 2010; Volume 1, pp. 313–320.
- Wang, S.-S.; Chen, Z.-P. LCM: A link-aware clustering mechanism for energy-efficient routing in wireless sensor networks. IEEE Sens. J. 2013, 13, 728–736. [Google Scholar] [CrossRef]
- Yu, B.; Xiao, B. Detecting Selective Forwarding Attacks in Wireless Sensor Networks. In Proceedings of the 20th International Parallel and Distributed Processing Symposiun, Rhodes Island, Greece, 25–29 April 2006; pp. 1–8.
- Xiao, B.; Yu, B.; Gao, C. CHEMAS: Identify Suspect Nodes in Selective Forwarding Attacks. J. Parallel Distrib. Comput. 2007, 67, 1218–1230. [Google Scholar] [CrossRef]
- Hai, T.H.; Huh, E.-N. Detecting Selective Forwarding Attacks in Wireless Sensor Networks Using Two-Hops Neighbor Knowledge. In Proceedings of the Seventh IEEE International Symposium on Network Computing and Applications, Cambridge, MA, USA, 10–12 July 2008; pp. 325–331.
- Deng, H.; Sun, X.; Wang, B.; Cao, Y. Selective Forwarding Attack Detection using Watermark in Wireless Sensor Networks. In Proceedings of the International Colloquium on Computing, Communications Control, and Management, Sanya, China, 8–9 August 2009; pp. 109–113.
- Tumrongwittayapak, C.; Varakulsiripunth, R. Detecting Sinkhole Attack and Selective Forwarding Attack in Wireless Sensor Networks. In Proceedings of the 7th International Conference on Information, Communications and Signal Processing, Macau, China, 8–10 December 2009; pp. 1–5.
- Geetha, V.; Chandrasekaran, K. Enhanced Beta Trust Model for Identifying Insider Attacks in Wireless Sensor Networks. Int. J. Comput. Sci. Netw. Secur. 2013, 13, 14–19. [Google Scholar]
- Sridevi, K.J. Message Authentication in Sensor Networks Using En-Route Filtering. Int. J. Adv. Netw. Appl. 2015, 6, 127–131. [Google Scholar]
- Duan, J.Q.; Yang, D.; Zhu, H.Q.; Zhang, S.D.; Zhao, J. TSRF: A Trust-Aware Secure Routing Framework in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2014, 2014. [Google Scholar] [CrossRef]
- Cui, B.; Yang, S.J. NRE: Suppress Selective Forwarding Attacks in Wireless Sensor Networks. In Proceedings of the IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 229–237.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alajmi, N.; Elleithy, K. Multi-Layer Approach for the Detection of Selective Forwarding Attacks. Sensors 2015, 15, 29332-29345. https://doi.org/10.3390/s151129332
Alajmi N, Elleithy K. Multi-Layer Approach for the Detection of Selective Forwarding Attacks. Sensors. 2015; 15(11):29332-29345. https://doi.org/10.3390/s151129332
Chicago/Turabian StyleAlajmi, Naser, and Khaled Elleithy. 2015. "Multi-Layer Approach for the Detection of Selective Forwarding Attacks" Sensors 15, no. 11: 29332-29345. https://doi.org/10.3390/s151129332






