Layered Location-Based Security Mechanism for Mobile Sensor Networks: Moving Security Areas
Abstract
:1. Introduction
2. Models and Assumptions
2.1. Network Model
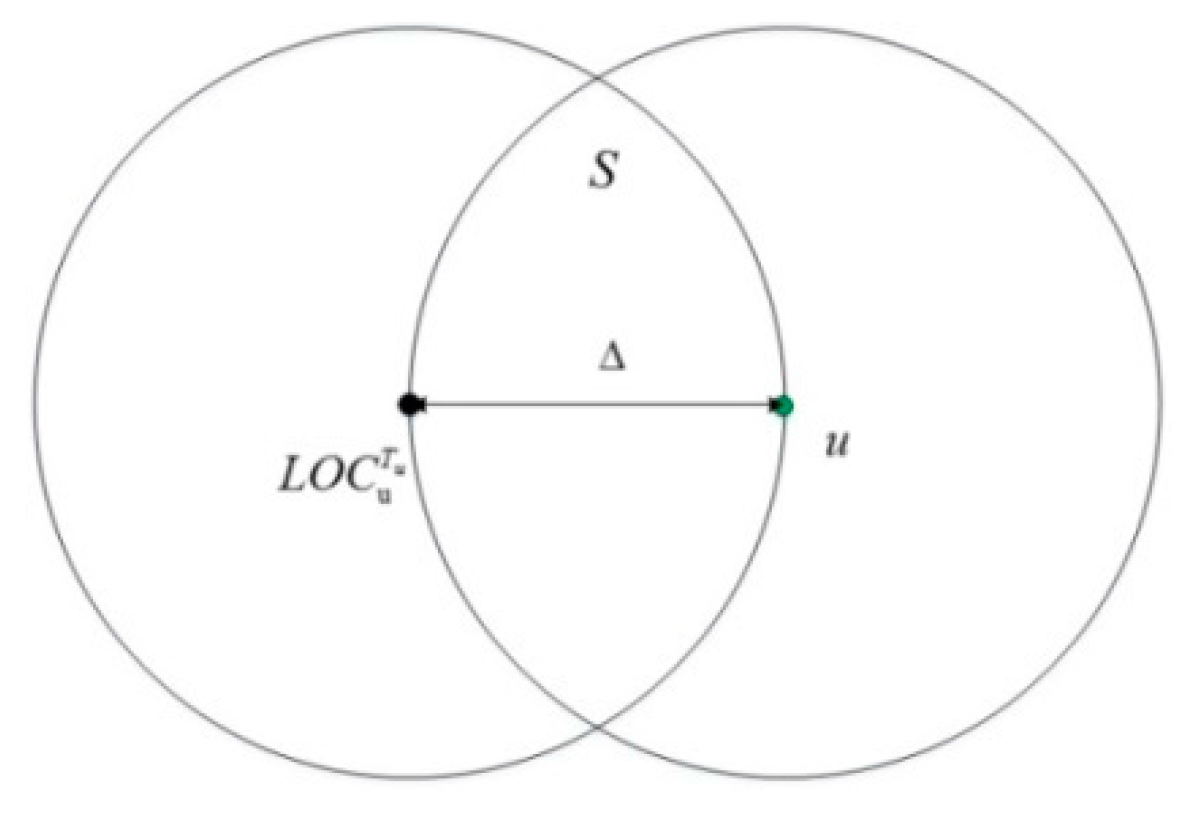
2.2. Security Model
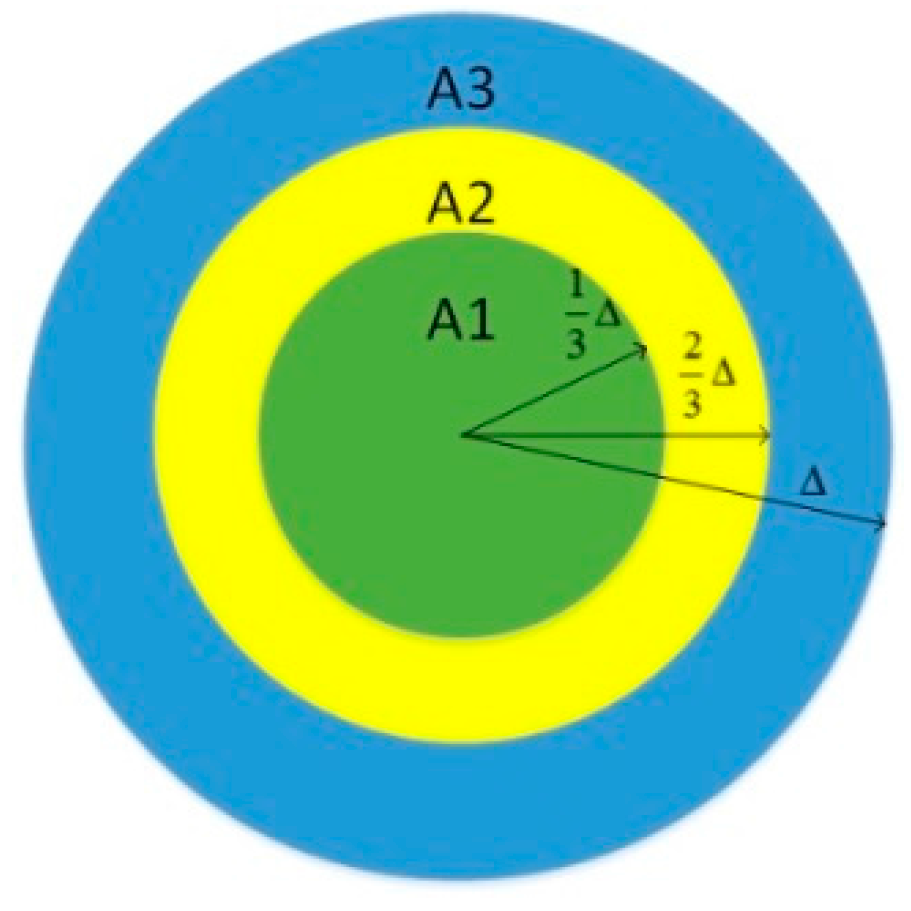
3. The Security Mechanism
3.1. Local Detection
3.1.1. LD-1 Mechanism
| u→*: () |
| v→u: () |
| u→v: |
3.1.2. LD-2 Mechanism
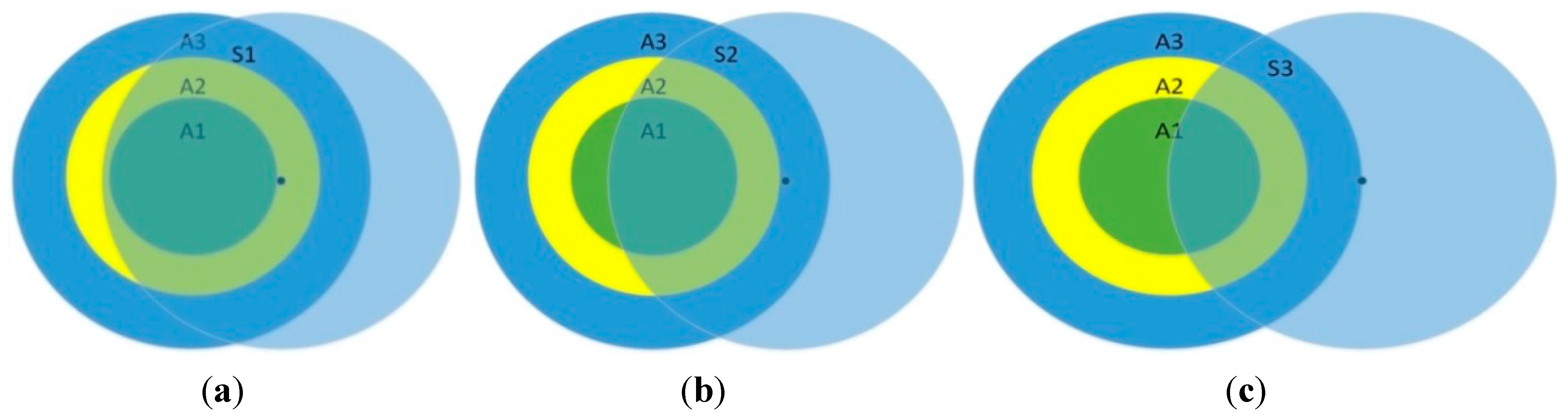
3.2. Overall Detection
4. Analysis
4.1. Security Analysis
4.1.1. Replication Attack
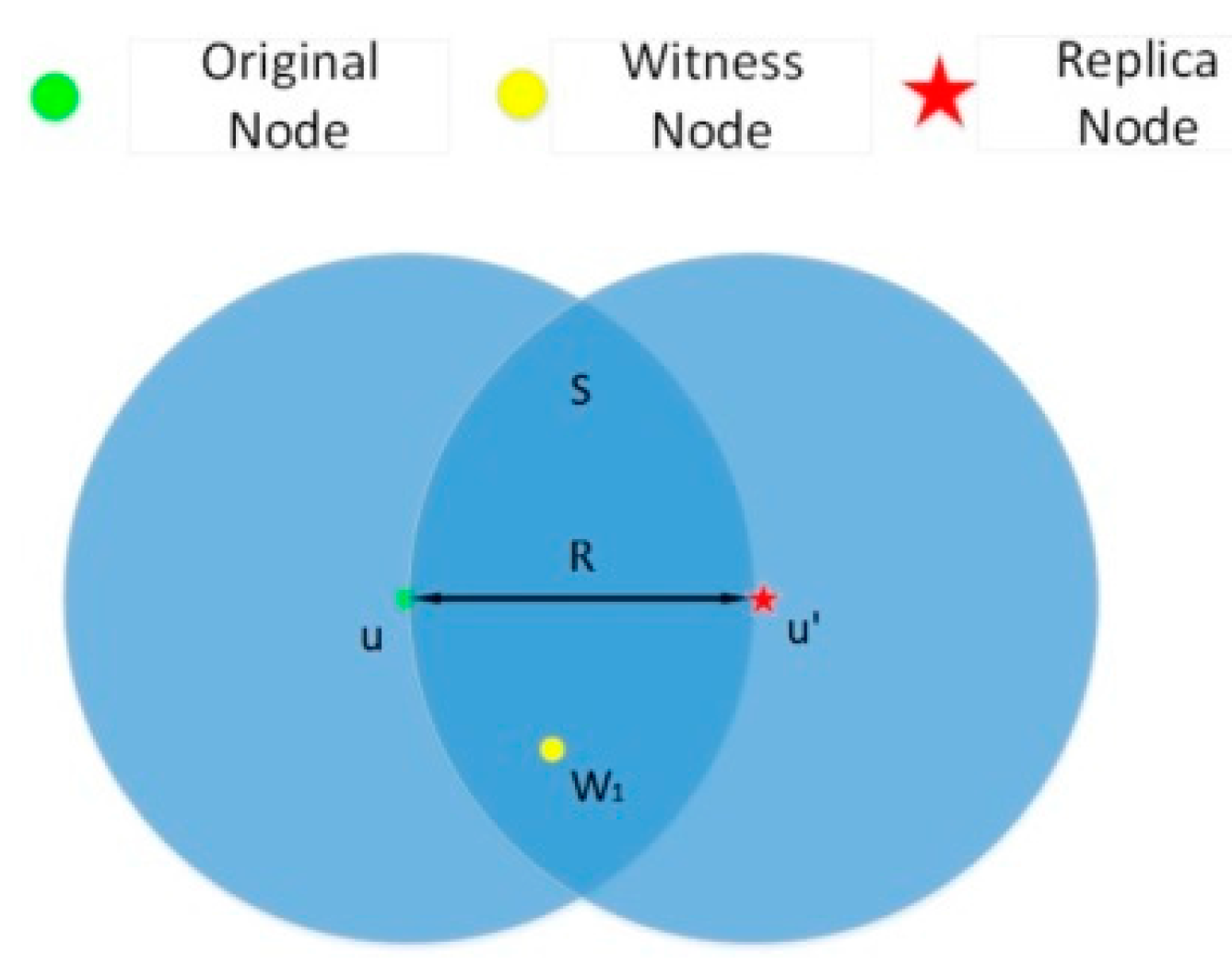

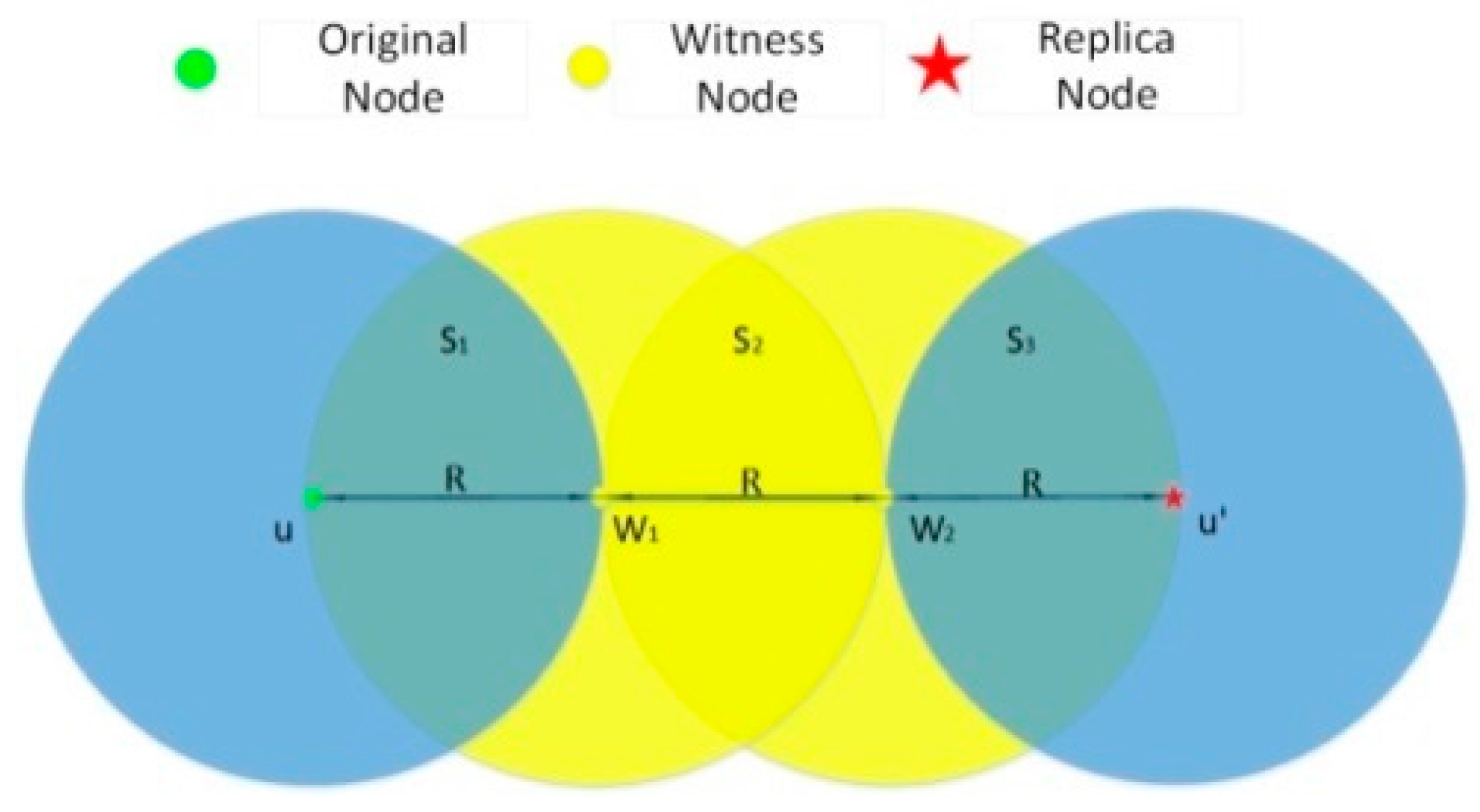
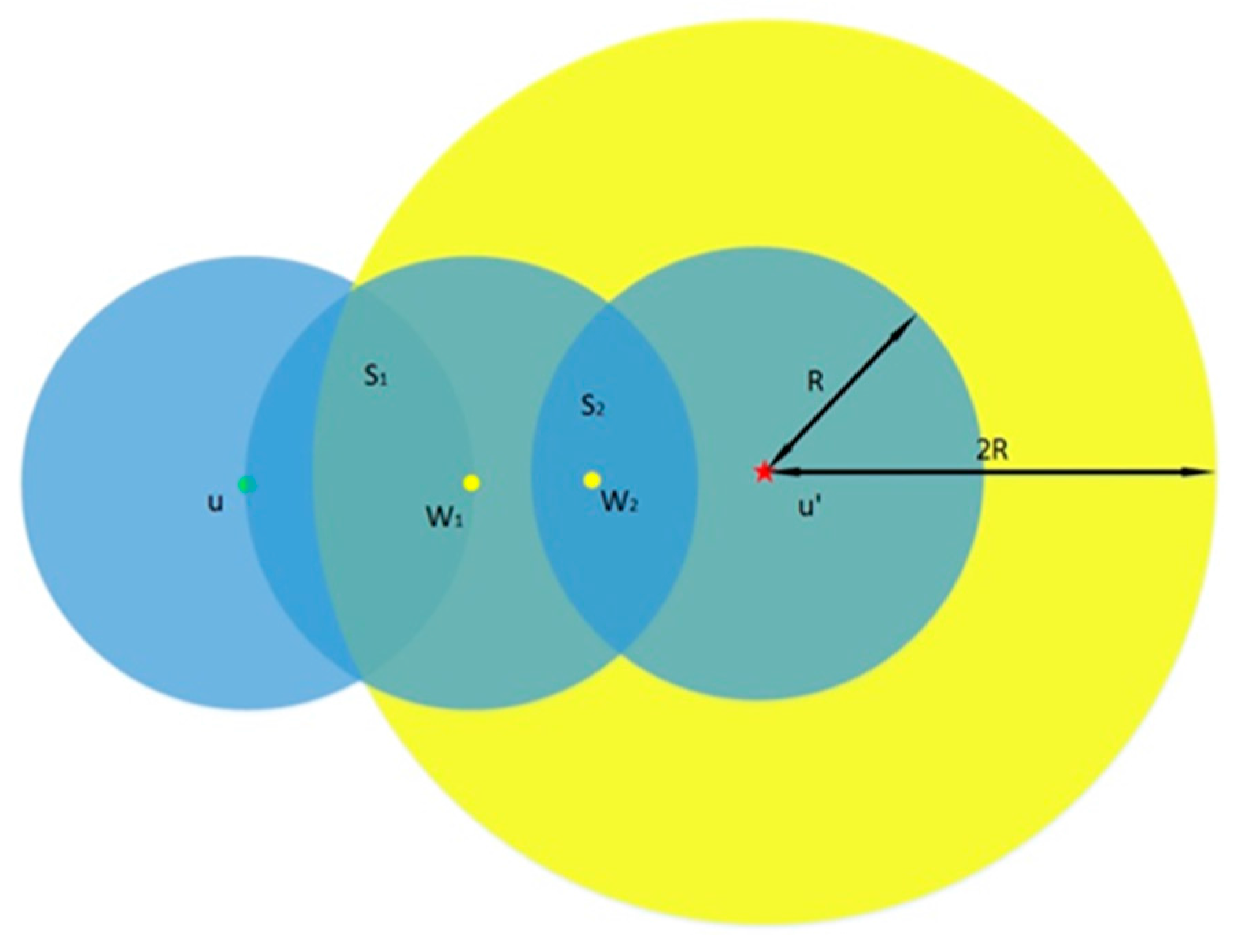

4.1.2. Sybil Attack
4.1.3. Wormhole Attack
4.2. Overhead Analysis

| Scheme | CommO | CompO | SO | AA | SNT |
|---|---|---|---|---|---|
| LBK [1] | — | — | — | SA/RA/WA etc. | Static Networks |
| TDD [3] | O(1) | O(N) | RA | Mobile Networks | |
| SDD [3] | O(1) | O(1) | O(N) | RA | Mobile Networks |
| HIP [5] | O(d2h) | O(d3h) | O(d2h + dh) | RA | Mobile Networks |
| HOP [5] | O(d2h) | O(d3h) | O(d2h + dh) | RA | Mobile Networks |
| XED [15] | O(1) | O(1) | O(N) | RA | Mobile Networks |
| EDD [15] | O(1) | O(1) | O(1) | RA | Mobile Networks |
| Patrol Detection [20] | O(n) & | O(1) | — | RA | Static & Mobile Networks |
| MSA_LD-1 | O(1) | O(1) | O(1) | SA/RA/WA etc. | Mobile Networks |
| MSA_LD-2 | O(1) | O(1) | O(N) | SA/RA/WA etc. | Mobile Networks |
| MSA_OD | O(1) | O(N) | SA/RA/WA etc. | Mobile Networks |
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zhang, Y.; Liu, W.; Lou, W.; Fang, Y. Location-based compromise-tolerant security mechanisms for wireless sensor networks. IEEE J Sel. Areas Commun. 2006, 24, 247–260. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Zhang, Y. LEDS: Providing location-aware end-to-end data security in wireless sensor networks. IEEE Trans. Mob. Comput. 2008, 7, 585–598. [Google Scholar] [CrossRef]
- Xing, K.; Cheng, X. From time domain to space domain: Detecting replica attacks in mobile ad hoc networks. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9.
- Xue, K.; Xiong, W.; Hong, P.; Lu, H. NBK: A novel neighborhood based key distribution scheme for wireless sensor networks. In Proceedings of the Fifth International Conference on Networking and Services, Valencia, Spain, 20–25 April 2009; pp. 175–179.
- Duan, M.; Xu, J. An efficient location-based compromise-tolerant key management scheme for sensor networks. Inf. Process. Lett. 2011, 111, 503–507. [Google Scholar] [CrossRef]
- Conti, M.; Di Pietro, R.; Spognardi, A. Clone wars: Distributed detection of clone attacks in mobile WSNs. J. Comput. Syst. Sci. 2014, 80, 654–669. [Google Scholar] [CrossRef]
- Yi, J.; Yang, S.; Cha, H. Multi-hop-based monte carlo localization for mobile sensor networks. In Proceedings of the 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, San Diego, CA, USA, 18–21 June 2007; pp. 162–171.
- Koo, J.; Yi, J.; Cha, H. Localization in mobile ad hoc networks using cumulative route information. In Proceedings of the 10th international conference on Ubiquitous computing, New York, NY, USA, 21 September 2008; pp. 124–133.
- Savvides, A.; Han, C.C.; Strivastava, M.B. Dynamic fine-grained localization in ad-hoc networks of sensors. In Proceedings of the 7th annual international conference on Mobile computing and networking, New York, NY, USA, 16 July 2001; pp. 166–179.
- Park, M.; Gao, Y. Error and performance analysis of MEMS-based inertial sensors with a low-cost GPS receiver. Sensors 2008, 8, 2240–2261. [Google Scholar] [CrossRef]
- Hyytiä, E.; Lassila, P.; Virtamo, J. Spatial node distribution of the random waypoint mobility model with applications. IEEE Trans. Mob. Comput. 2006, 5, 680–694. [Google Scholar] [CrossRef]
- Mahmoud, M.E.; Shen, X.S. Esip: Secure incentive protocol with limited use of public-key cryptography for multihop wireless networks. IEEE Trans. Mob. Comput. 2011, 10, 997–1010. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Advances in Cryptology—CRYPTO 2001; Kilian, J., Ed.; Springer Berlin Heidelberg: Santa Barbara, CA, USA, 2001; Volume 2139, pp. 213–229. [Google Scholar]
- Cressie, N. Statistics for Spatial Data; John Wiley & Sons: Hoboken, NJ, USA, 2015; pp. 112–209. [Google Scholar]
- Yu, C.-M.; Tsou, Y.-T.; Lu, C.-S.; Kuo, S.-Y. Localized algorithms for detection of node replication attacks in mobile sensor networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 754–768. [Google Scholar]
- Wang, Z.; Wang, Y.; Ma, M.; Wu, J. Efficient localization for mobile sensor networks based on constraint rules optimized Monte Carlo method. Comput. Netw. 2013, 57, 2788–2801. [Google Scholar] [CrossRef]
- Ho, J.W.; Wright, M.; Das, S.K. Fast detection of mobile replica node attacks in wireless sensor networks using sequential hypothesis testing. IEEE Trans. Mob. Comput. 2011, 10, 767–782. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and counter measures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Li, Z.; Gong, G. Randomly directed exploration: An efficient node clone detection protocol in wireless sensor networks. In Proceedings of the IEEE 6th International Conference on Mobile Adhoc and Sensor Systems, Macau, China, 12–15 October 2009; pp. 1030–1035.
- Wang, L.M.; Shi, Y. Patrol detection for replica attacks on wireless sensor networks. Sensors 2011, 11, 2496–2504. [Google Scholar] [CrossRef] [PubMed]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Zhang, H.; Wu, L.; Zhou, C. Layered Location-Based Security Mechanism for Mobile Sensor Networks: Moving Security Areas. Sensors 2015, 15, 24886-24902. https://doi.org/10.3390/s151024886
Wang Z, Zhang H, Wu L, Zhou C. Layered Location-Based Security Mechanism for Mobile Sensor Networks: Moving Security Areas. Sensors. 2015; 15(10):24886-24902. https://doi.org/10.3390/s151024886
Chicago/Turabian StyleWang, Ze, Haijuan Zhang, Luqiang Wu, and Chang Zhou. 2015. "Layered Location-Based Security Mechanism for Mobile Sensor Networks: Moving Security Areas" Sensors 15, no. 10: 24886-24902. https://doi.org/10.3390/s151024886





