Protection Intensity Evaluation for a Security System Based on Entropy Theory
Abstract
:1. Introduction
1.1. Motivation
1.2. Contribution
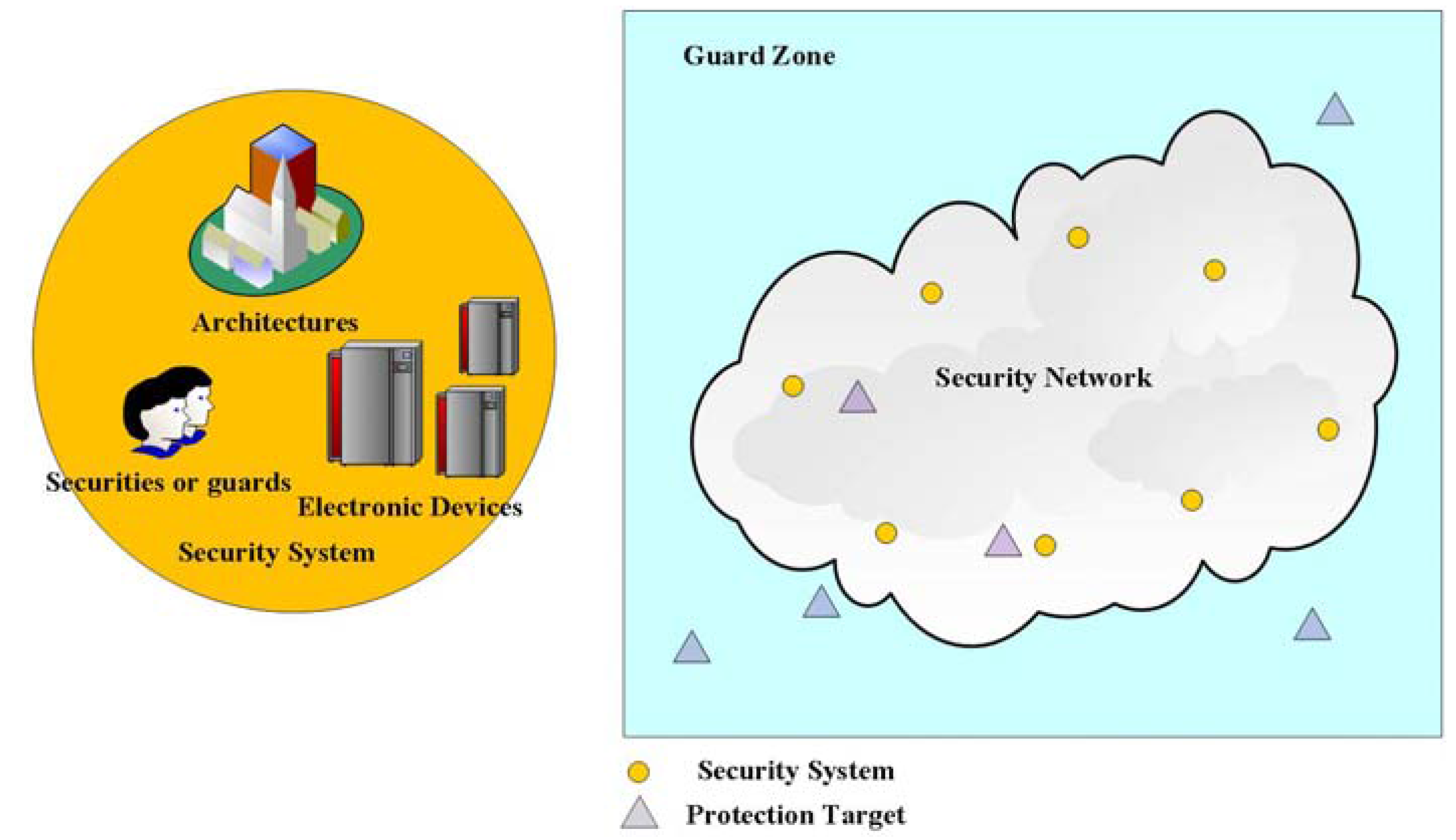
1.3. Paper Organization
2. Related Work
3. Protection Effectiveness Estimation of Security Systems Based on Entropy Theory
3.1. Brief Effectiveness Estimation Method for a Security System

| Security System | Detection | Defense | Response | Effectiveness |
|---|---|---|---|---|
| S1 | 0.9 | 0.8 | 0.9 | 0.87 |
| S2 | 0.7 | 0.75 | 0.85 | 0.77 |
| S3 | 0.9 | 0.5 | 0.7 | 0.7 |
3.2. Introduction of Related Theories

3.3. Protection Effectiveness Evaluation Model Based on Entropy

3.4. Mutual Protection of Multiple Security Systems

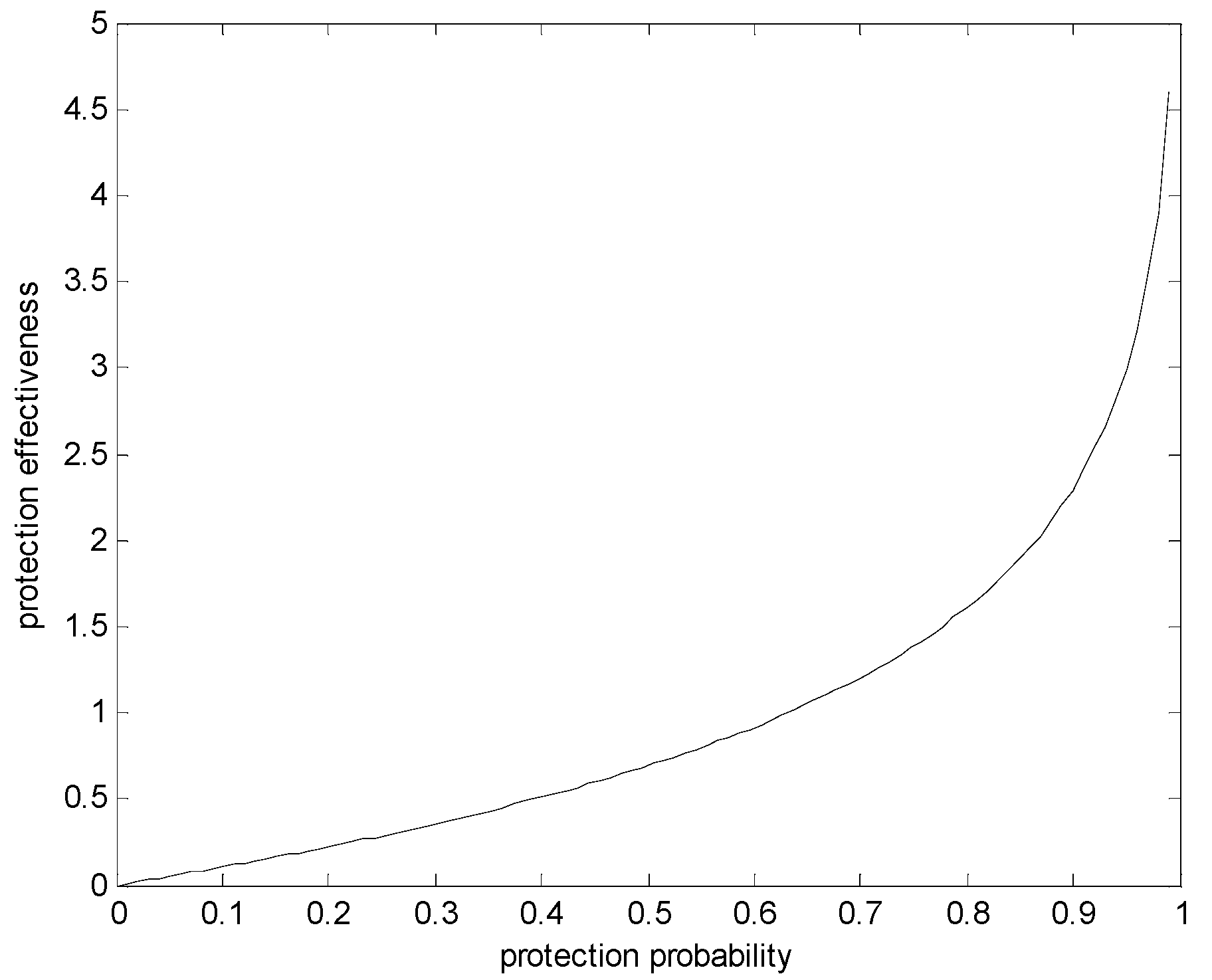


| Security System | Detection | Defense | Response | Effectiveness | Pi |
|---|---|---|---|---|---|
| S1 | 0.9 | 0.8 | 0.9 | 2.0715 | 0.8744 |
| S2 | 0.7 | 0.75 | 0.85 | 1.4958 | 0.7759 |
| S3 | 0.9 | 0.5 | 0.7 | 1.3999 | 0.7534 |
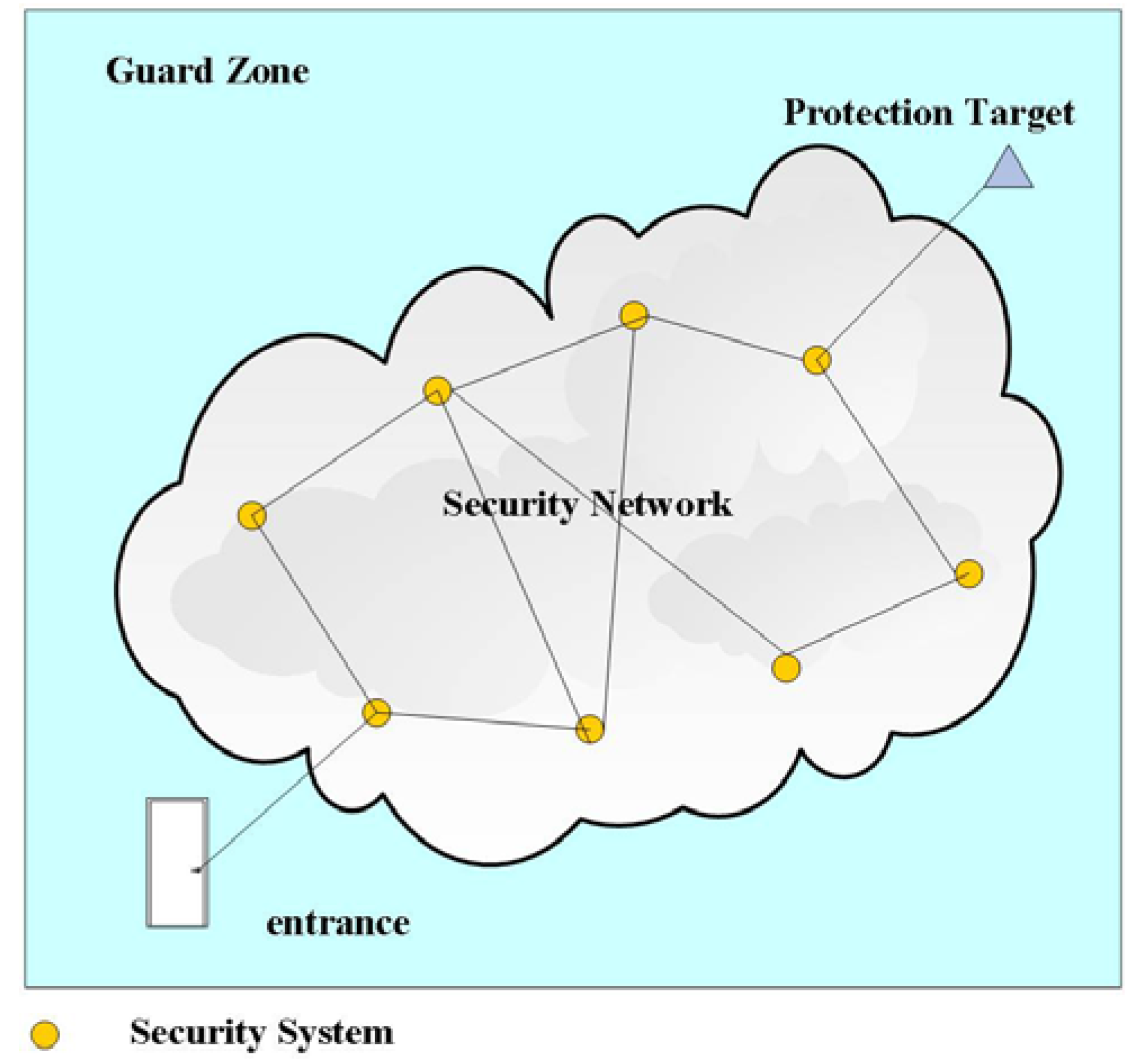
4. Protection Intensity Evaluation Model

4.1. All Security Systems Protection Intensity

4.2. Closest Security Systems Protection Intensity

4.3. Path Protection Intensity




 , and the protection intensity along the path is
, and the protection intensity along the path is  .
.
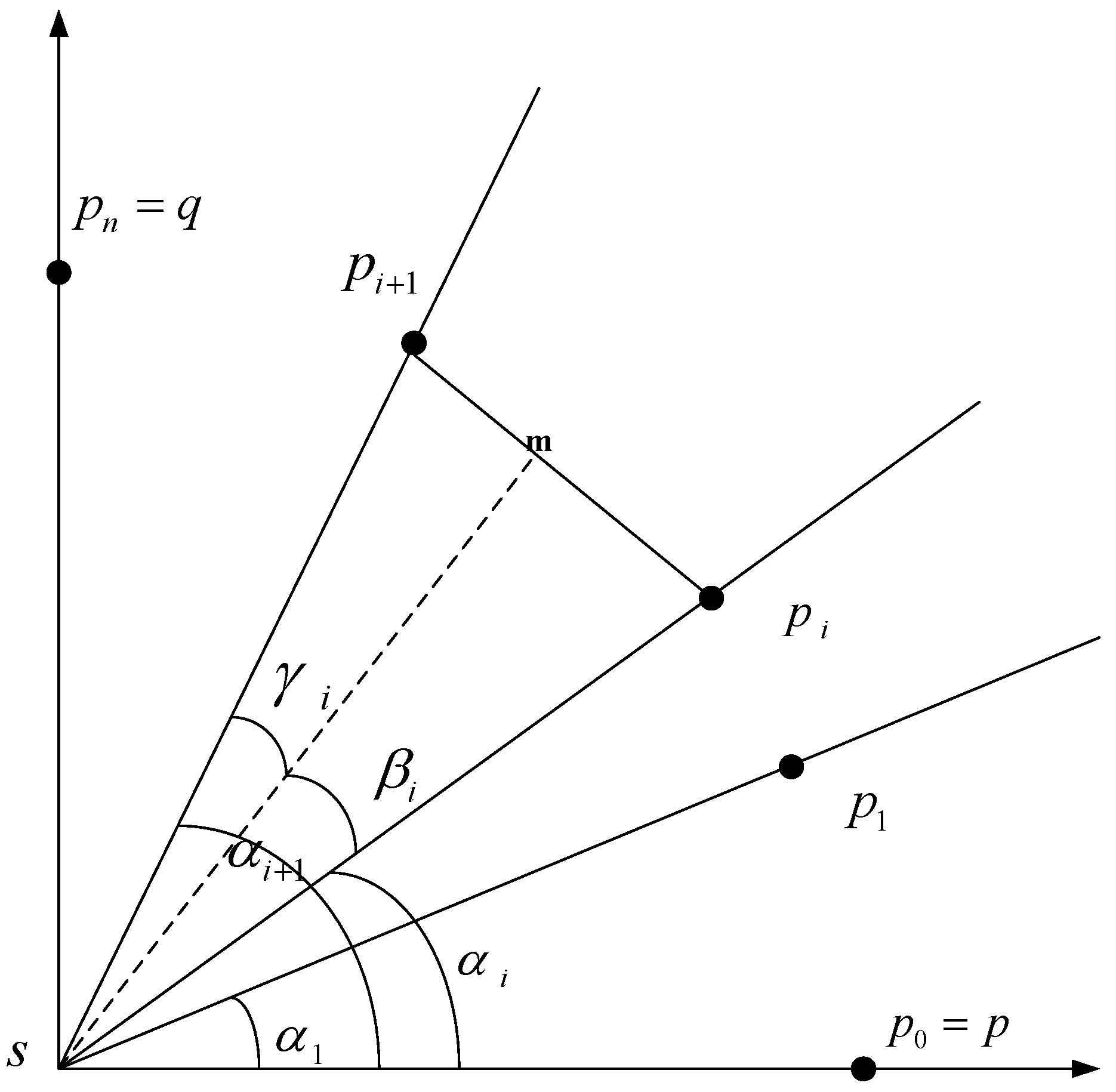




 .
.
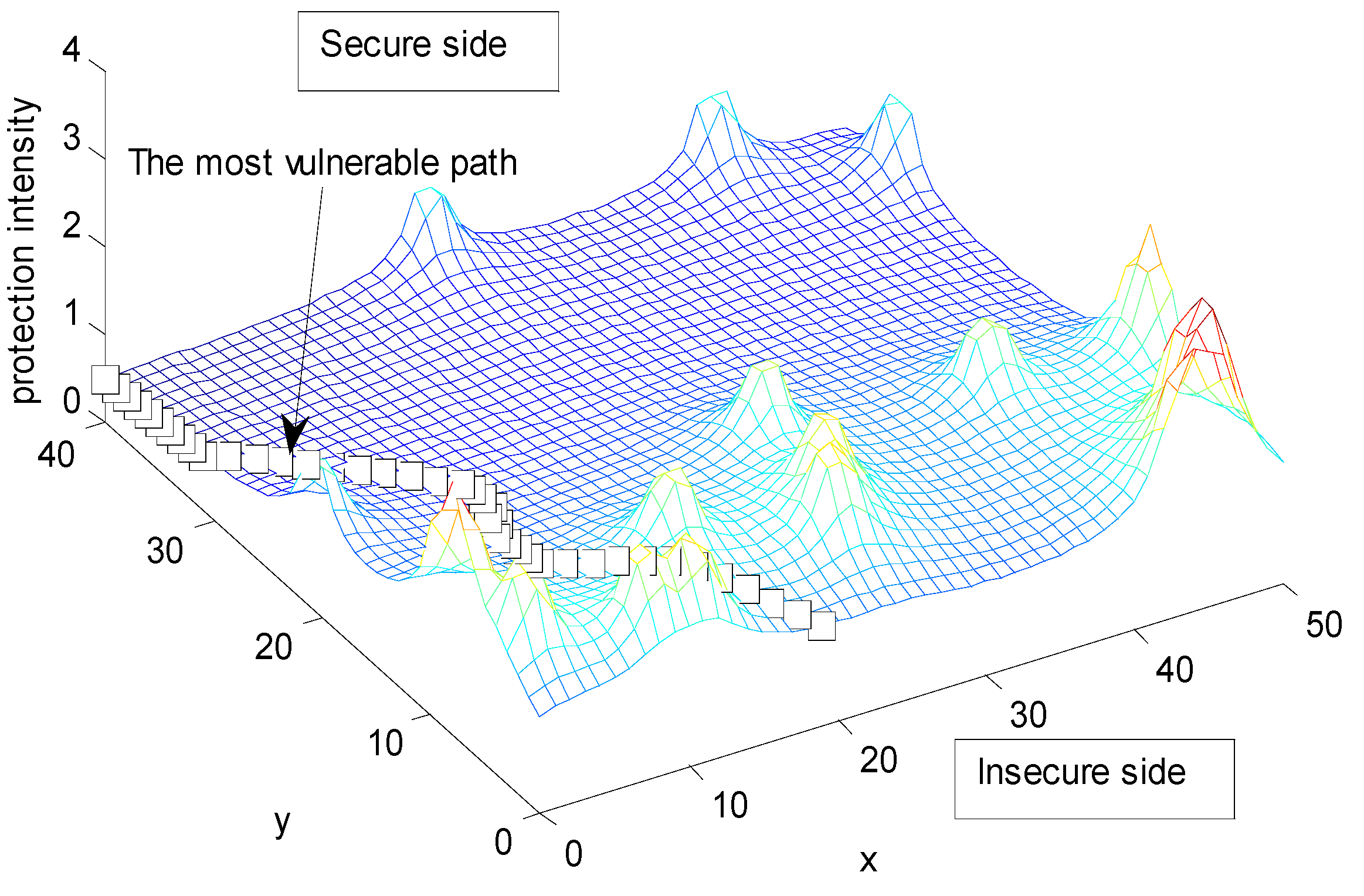
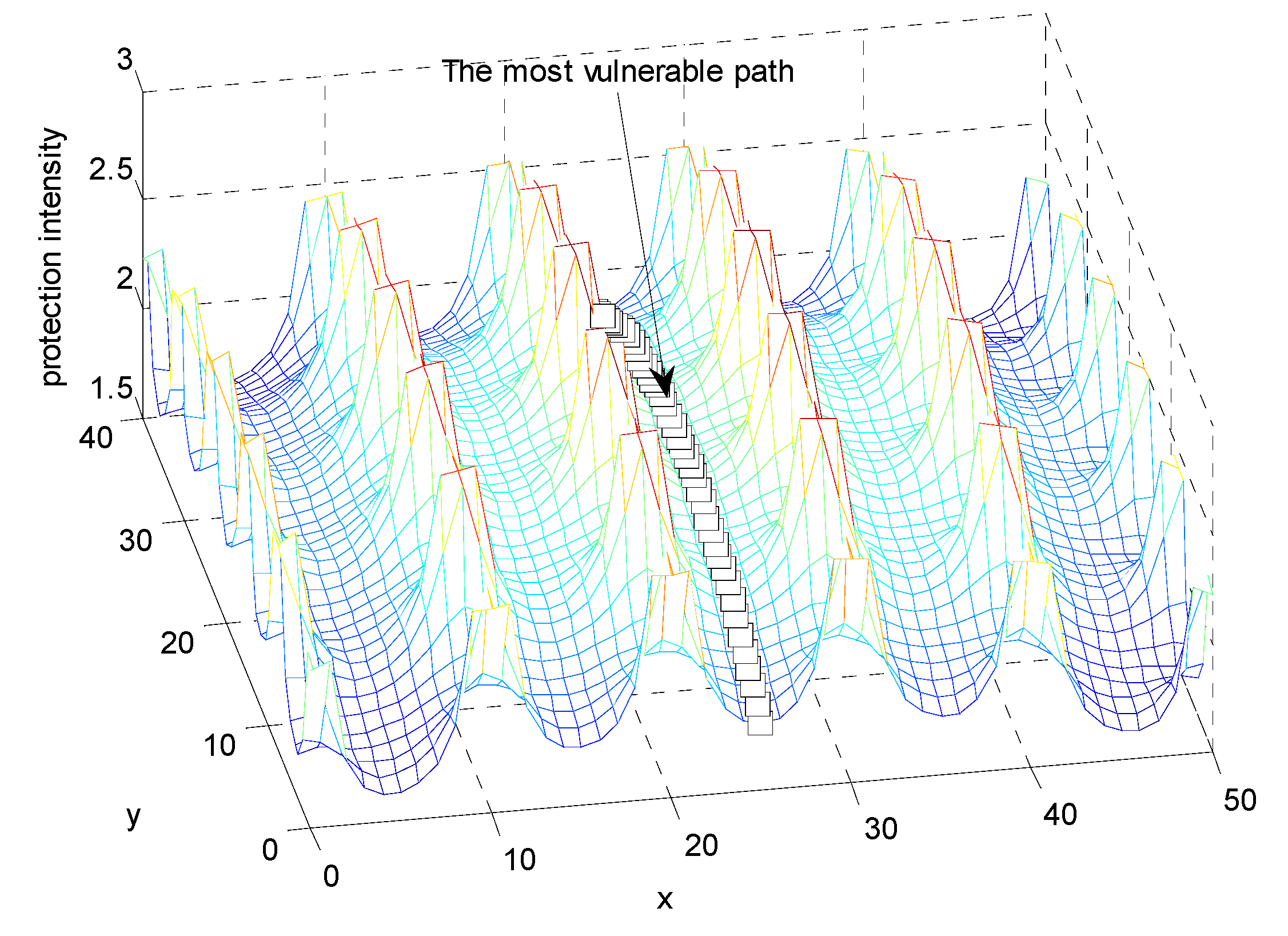
5. An Algorithm for Calculating Minimal Protection Intensity Path
- (1)
- Transform the continuous problem domain to a discrete one;
- (2)
- Apply graph theoretic abstraction;
- (3)
- Compute the minimal protection intensity path using Dijkstra’s Single Source Shortest Path algorithm.

6. Experimental Section
6.1. Grid Based Guard Field
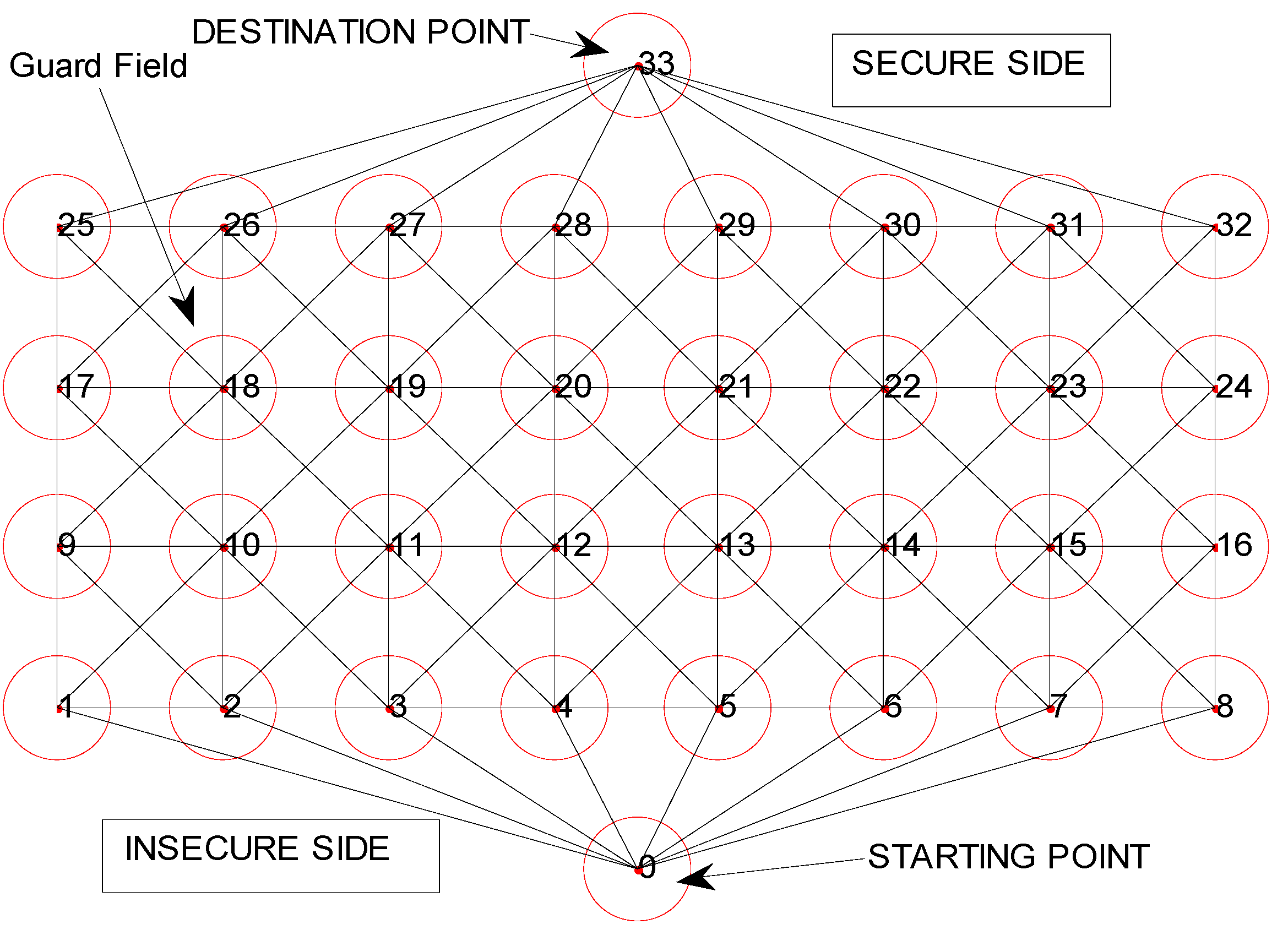

6.2. Uniformly Distributed Random Security System Deployment
| S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | S10 | |
| X | 11.96 | 1.94 | 46.60 | 25.31 | 15.16 | 45.82 | 40.01 | 8.62 | 23.80 | 26.34 |
| Y | 2.01 | 3.95 | 1.82 | 8.3 | 8.82 | 3.21 | 13.47 | 2.17 | 5.40 | 15.47 |
| S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | S10 | |
| X | 43.19 | 45.30 | 21.80 | 41.06 | 0 | 0 | 0 | 50 | 50 | 50 |
| Y | 0 | 0 | 40 | 40 | 20.64 | 9.01 | 7.34 | 35.01 | 12.71 | 10.93 |
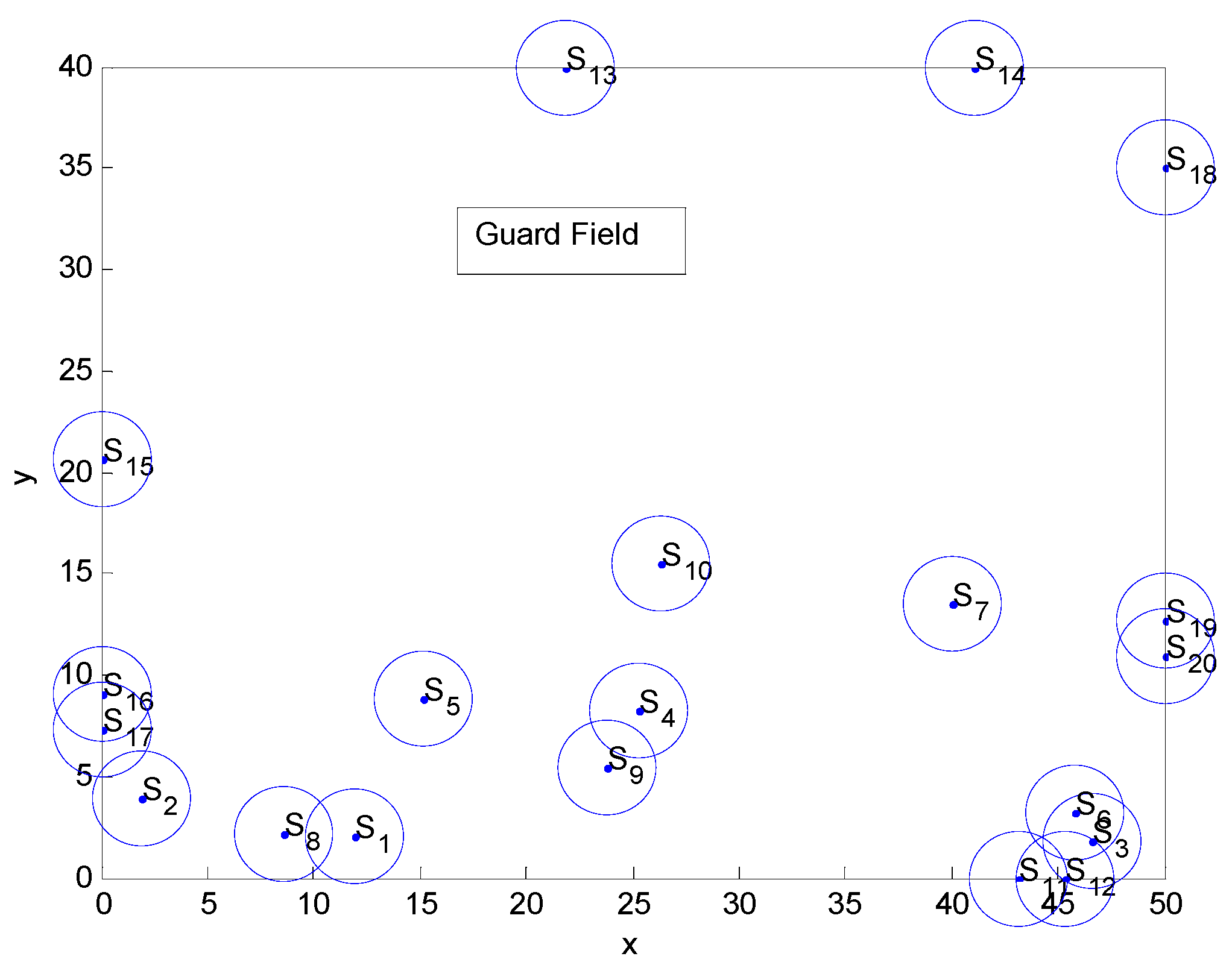
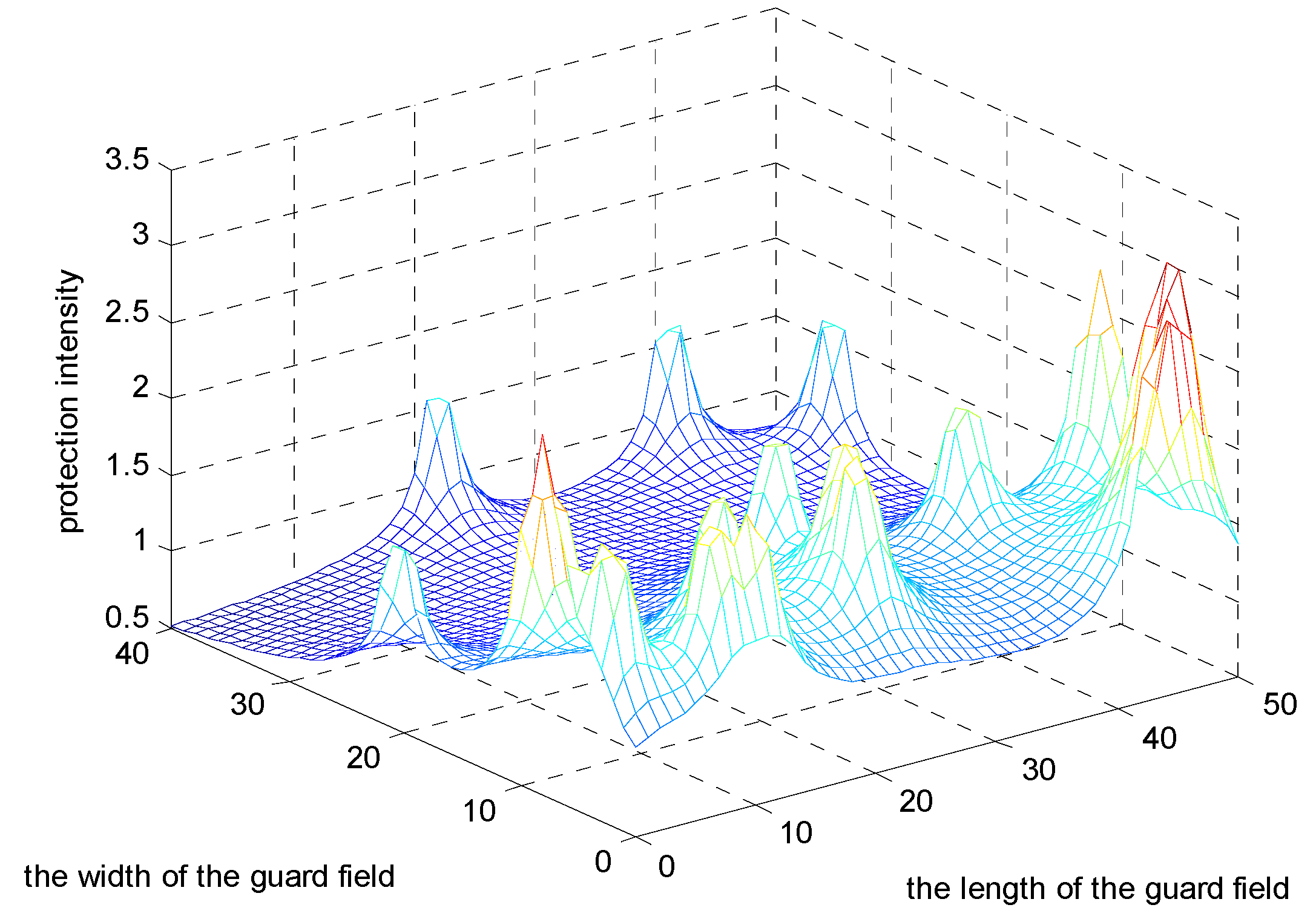

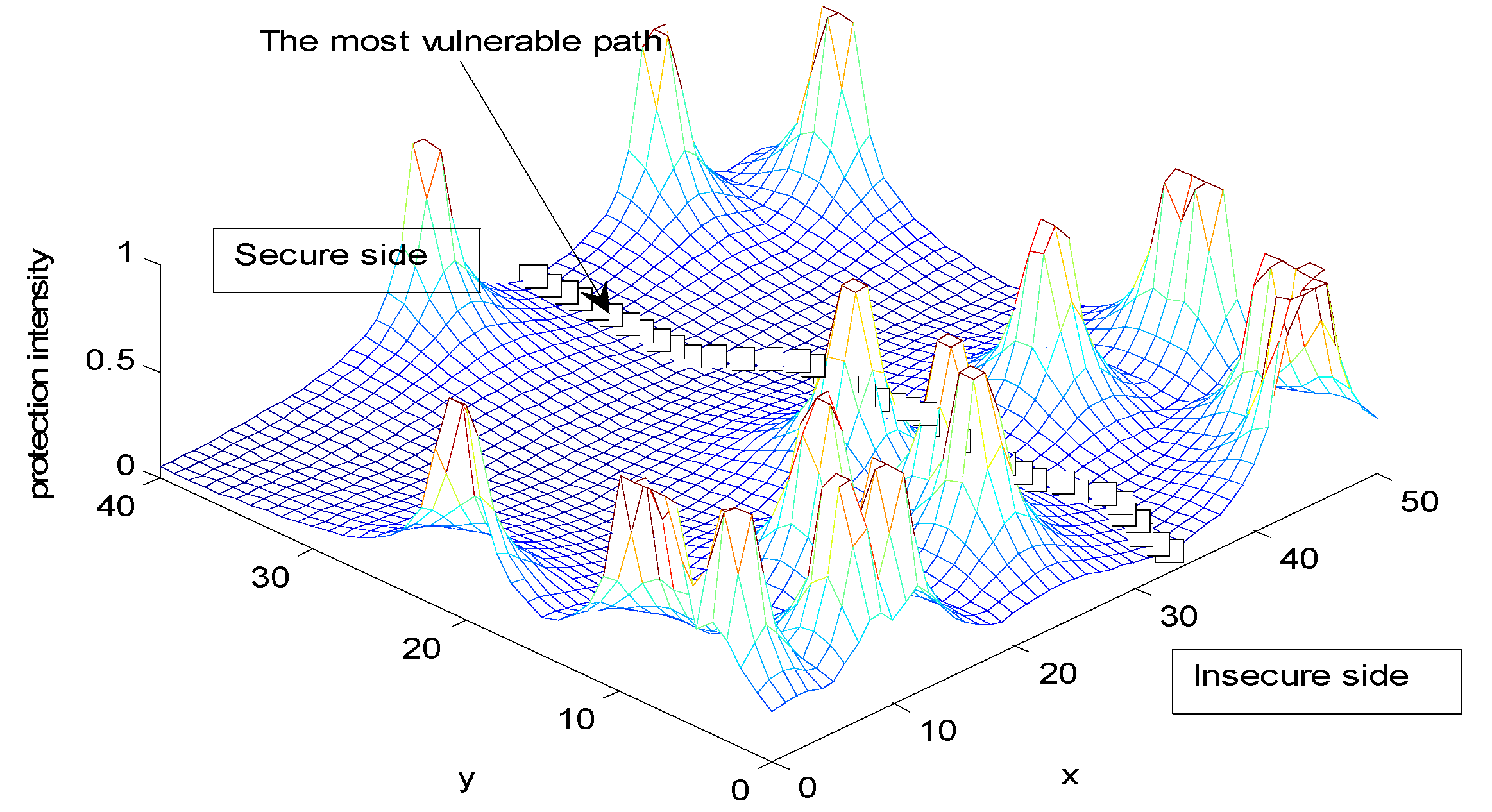
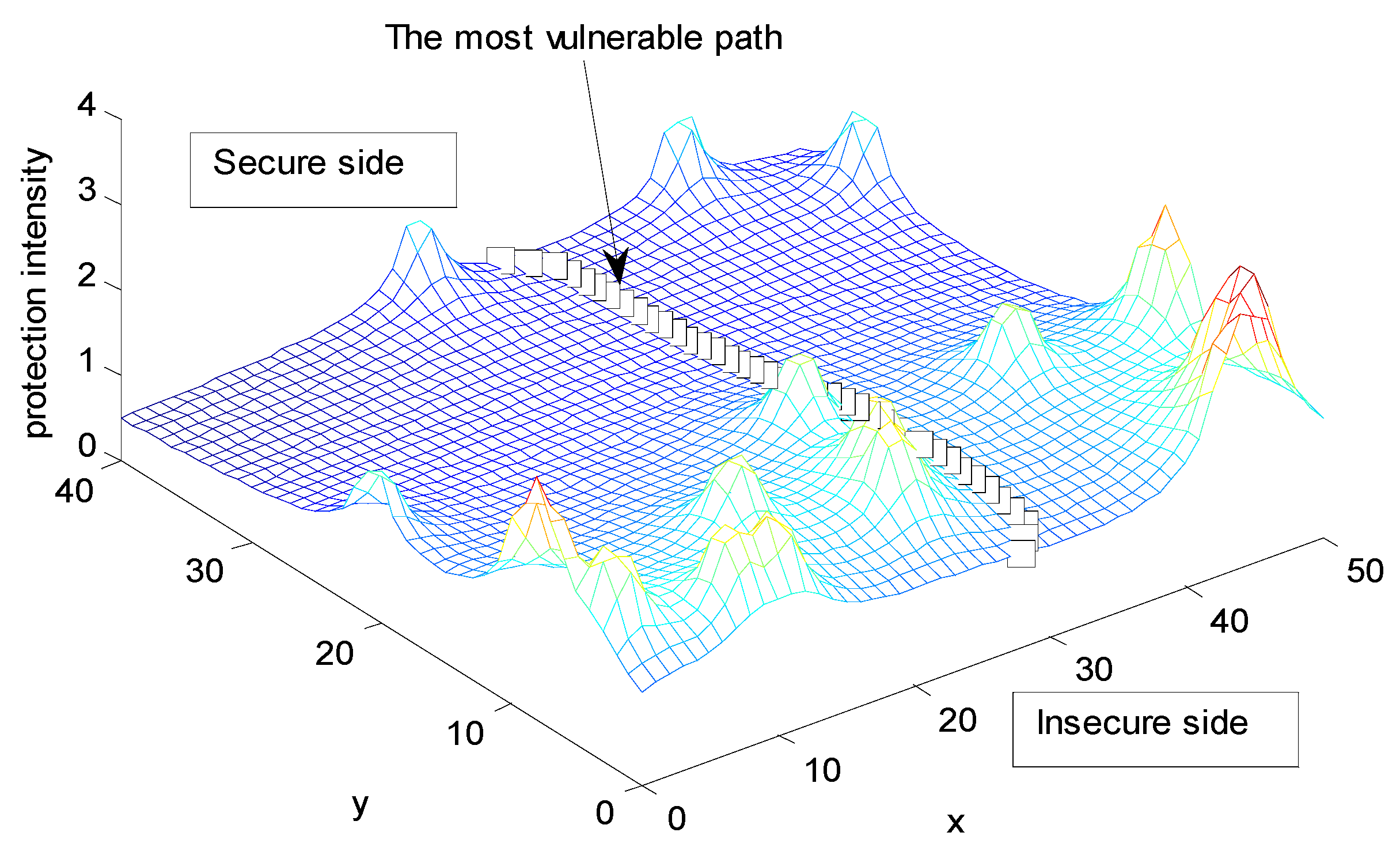
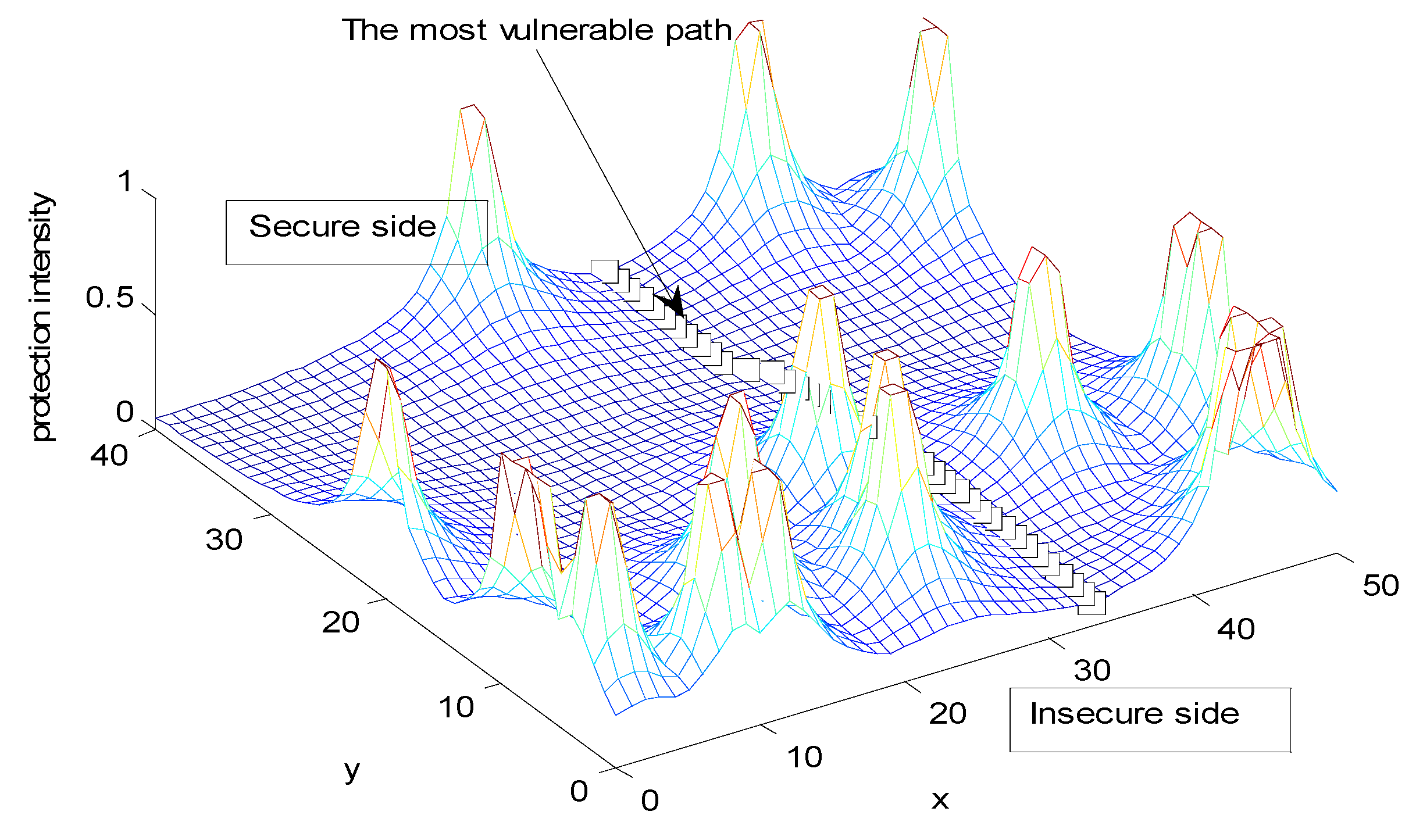
6.3. Deterministic Security System Placement

| Numbers | Under the JA intensity model | Under the JC intensity model | ||||
|---|---|---|---|---|---|---|
| Cross | Square | Triangle | Cross | Square | Triangle | |
| 36 | 8.1493 | 7.5140 | 7.7412 | 93.5196 | 84.6675 | 92.8218 |
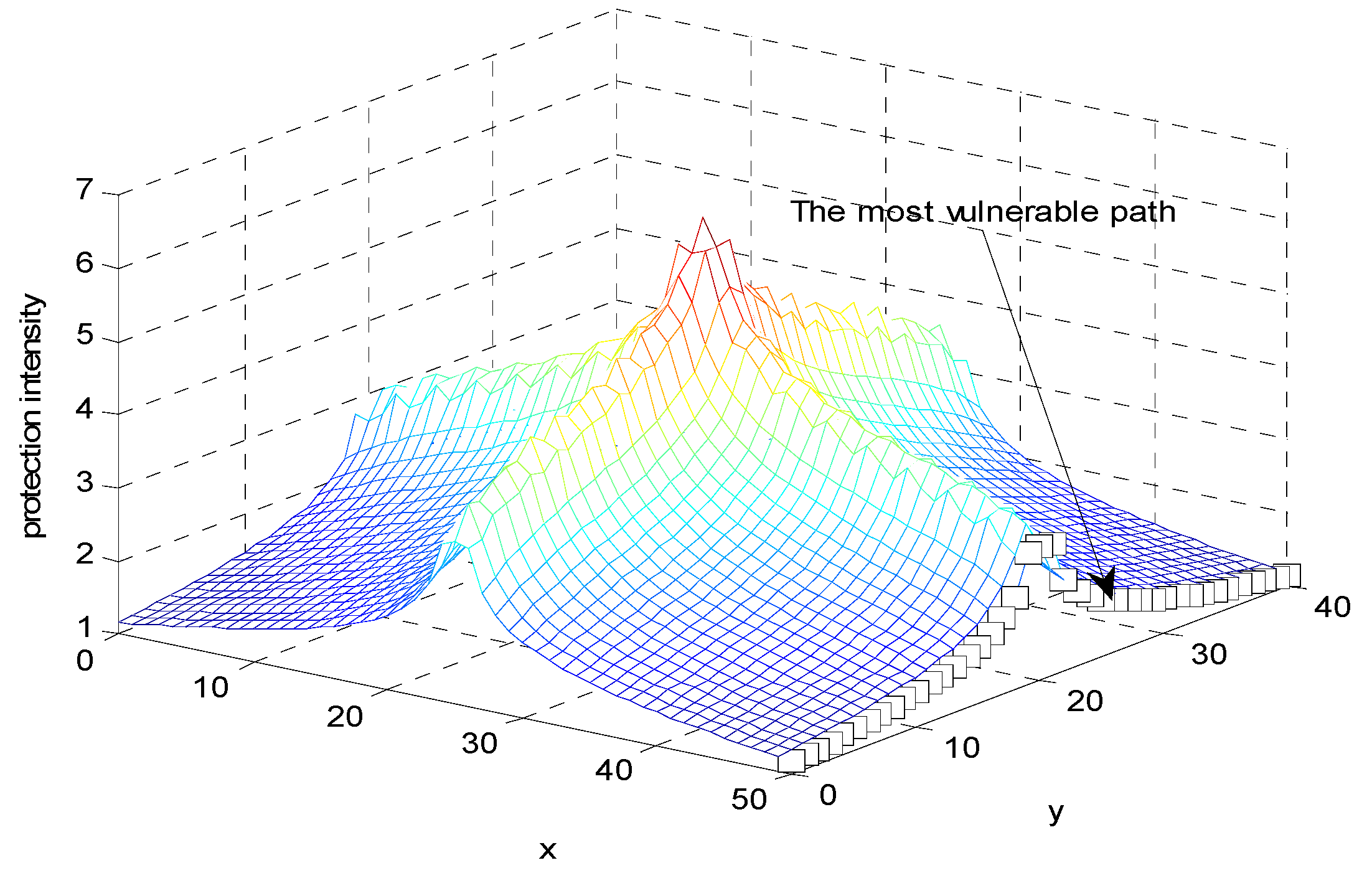

6.4. Effect of Numbers of Security Systems on the Minimal Protection Intensity


7. Conclusions
Acknowledgments
Conflict of Interest
References
- Kenyon, K.M. Digging up Jericho; Benn: London, UK, 1957. [Google Scholar]
- Garcia, M.L. The Design and Evaluation of Physical Protection Systems; Butterworth-Heinemann: Boston, MA, USA, 2001. [Google Scholar]
- Bennett, H.A.; Olascoaga, M.T. Evaluation Methodology For Fixed-Site Physical Protection Systems. Nucl. Mater. Manag. 1980, 9, 403–410. [Google Scholar]
- Darby, J.L.; Simpkins, B.E.; Key, B.R. Seapath, a microcomputer code for evaluating physical security effectiveness using adversary sequence diagrams. Nucl. Mater. Manag. 1986, 15, 242–245. [Google Scholar]
- Hicks, M.J.; Snell, M.S.; Sandoval, J.S.; Potter, C.S. Physical protection systems cost and performance analysis: A case study. IEEE Aero. El. Syst. Mag. 1999, 14, 9–13. [Google Scholar] [CrossRef]
- Doyon, L.R. Stochastic modeling of facility security-systems for analytical solutions. Comput. Ind. Eng. 1981, 5, 127–138. [Google Scholar] [CrossRef]
- Fischer, R.; Halibozek, E.; Walters, D. Introduction to Security, 9th ed.; Elsevier: Boston, MA, USA, 2012. [Google Scholar]
- Schneider, W.J.; Grassie, R.P. Countermeasures Development in the Physical Security Design Process: An Anti-Terrorist Perspective. In Proceedings of 1989 International Carnahan Conference on Security Technology, Zurich, Switzerland, 3–5 October 1989; IEEE: Zurich, Switzerland, 1989; pp. 297–302. [Google Scholar]
- Kobza, J.E.; Jacobson, S.H. Probability models for access security system architectures. J. Oper. Res. Soc. 1997, 48, 255–263. [Google Scholar] [CrossRef]
- Jacobson, S.H.; Kobza, J.E.; Easterling, A.S. A detection theoretic approach to modeling aviation security problems using the knapsack problem. IIE Trans. 2001, 33, 747–759. [Google Scholar] [CrossRef]
- Pollet, J.; Cummins, J. All Hazards Approach for Assessing Readiness of Critical Infrastructure. In Proceedings of IEEE Conference on Technologies for Homeland Security, Boston, MA, USA, 11–12 May 2009; pp. 366–372.
- Shan, X.; Zhuang, J. Cost of equity in homeland security resource allocation in the face of a strategic attacker. Risk Anal. 2012, 33, 1083–1099. [Google Scholar] [CrossRef] [PubMed]
- Xu, P.; Su, X.; Wu, J.; Sun, X.; Zhang, Y.; Deng, Y. Risk analysis of physical protection system based on evidence theory. J. Inf. Comput. Sci. 2010, 7, 2871–2878. [Google Scholar]
- Nikoofal, M.E.; Zhuang, J. Robust allocation of a defensive budget considering an attacker’s private information. Risk Anal. 2012, 32, 930–943. [Google Scholar] [CrossRef] [PubMed]
- Hausken, K.; Zhuang, J. The timing and deterrence of terrorist attacks due to exogenous dynamics. J. Oper. Res. Soc. 2012, 63, 726–735. [Google Scholar] [CrossRef]
- Golalikhani, M.; Zhuang, J. Modeling Arbitrary Layers of Continuous-Level Defenses in Facing with Strategic Attackers. Risk Anal. 2011, 31, 533–547. [Google Scholar] [CrossRef] [PubMed]
- Zhuang, J.; Bier, V.M.; Alagoz, O. Modeling secrecy and deception in a multiple-period attacker-defender signaling game. Eur. J. Oper. Res. 2010, 203, 409–418. [Google Scholar] [CrossRef]
- Zhuang, J.; Bier, V.M. Balancing terrorism and natural disasters-defensive strategy with endogenous attacker effort. Oper. Res. 2007, 55, 976–991. [Google Scholar] [CrossRef]
- Shan, X.; Zhuang, J. Hybrid defensive resource allocations in the face of partially strategic attackers in a sequential defenderʼCattacker game. Eur. J. Oper. Res. 2013, 228, 262–272. [Google Scholar] [CrossRef]
- Clausius, R. The Mechanical Theory of Heat: With Its Application to the Steam-engine and to the Physical Properties of Bodies; Van Voorst: London, UK, 1867. [Google Scholar]
- Sandler, S.I. Chemical, Biochemical, and Engineering Thermodynamics; Wiley: New York, NY, USA, 2006. [Google Scholar]
- Shannon, C.E. A mathematical theory of communication. SIGMOBILE Mob. Comput. Commun. Rev. 2001, 5, 3–55. [Google Scholar] [CrossRef]
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Lv, H.; Hu, R.; Chen, J.; He, Z.; Chen, S. Protection Intensity Evaluation for a Security System Based on Entropy Theory. Entropy 2013, 15, 2766-2787. https://doi.org/10.3390/e15072766
Lv H, Hu R, Chen J, He Z, Chen S. Protection Intensity Evaluation for a Security System Based on Entropy Theory. Entropy. 2013; 15(7):2766-2787. https://doi.org/10.3390/e15072766
Chicago/Turabian StyleLv, Haitao, Ruimin Hu, Jun Chen, Zheng He, and Shihong Chen. 2013. "Protection Intensity Evaluation for a Security System Based on Entropy Theory" Entropy 15, no. 7: 2766-2787. https://doi.org/10.3390/e15072766




