A Digital-Twin-Based Detection and Protection Framework for SDC-Induced Sinkhole and Grayhole Nodes in Satellite Networks
Abstract
:1. Introduction
- By carrying out fault injection experiments and SDC error analysis for each program, we establish a satellite network fault model under SEU. Also, we discuss the generation mechanism of SH and GH nodes induced by SDC errors by analyzing a typical satellite network routing mechanism and the behavior of satellites in each routing phase, providing theoretical support for subsequent detection and protection methods.
- We propose a digital-twin-based detection and protection framework for SH and GH nodes induced by SDC errors. Before the actual data transmission, the proposed framework does all that it can to detect the SH and GH nodes induced by SDC errors in the satellite network and recovers the fault nodes, which provides technical support for the availability and reliability of the satellite network.
- We propose a detection algorithm of SH and GH nodes based on digital twin routing data, which can complete the detection before data forwarding. In the simulated Iridium network environment, the experiment results show that the accuracy of the proposed detection method is 98–100%, and the additional time cost of routing convergence caused by the proposed framework is 3.1–28.2%.
2. Related Work
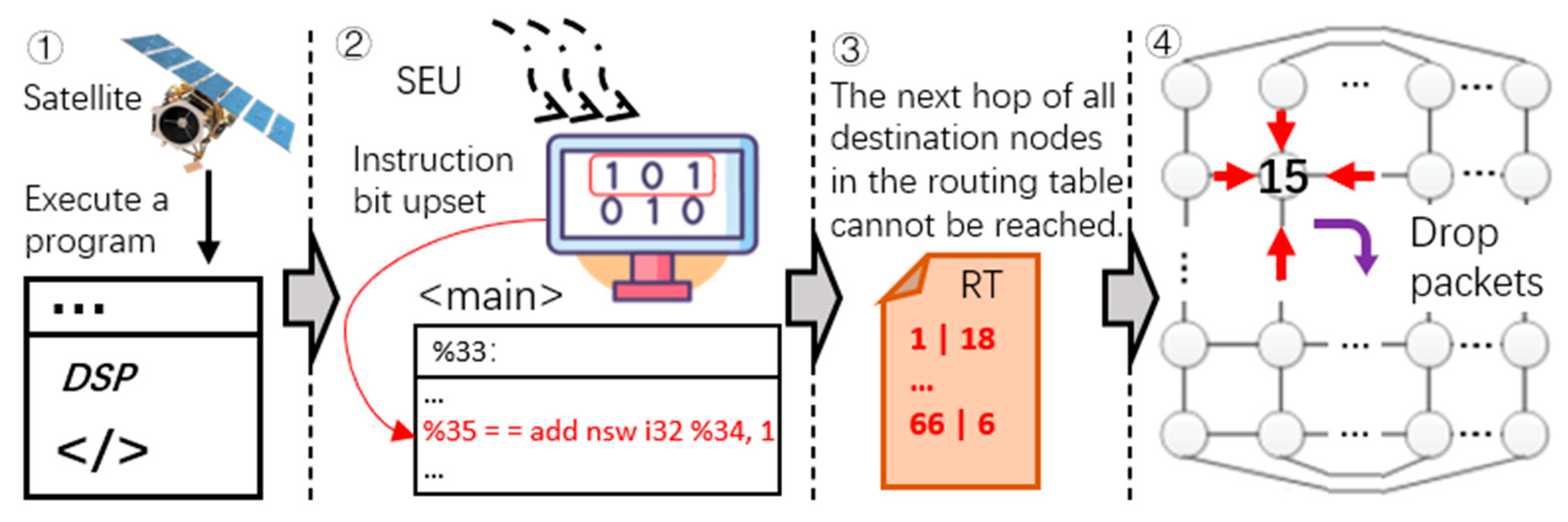
3. Fault Model and SH and GH Node Generation Mechanism
3.1. Satellite Network Fault Model under SEU
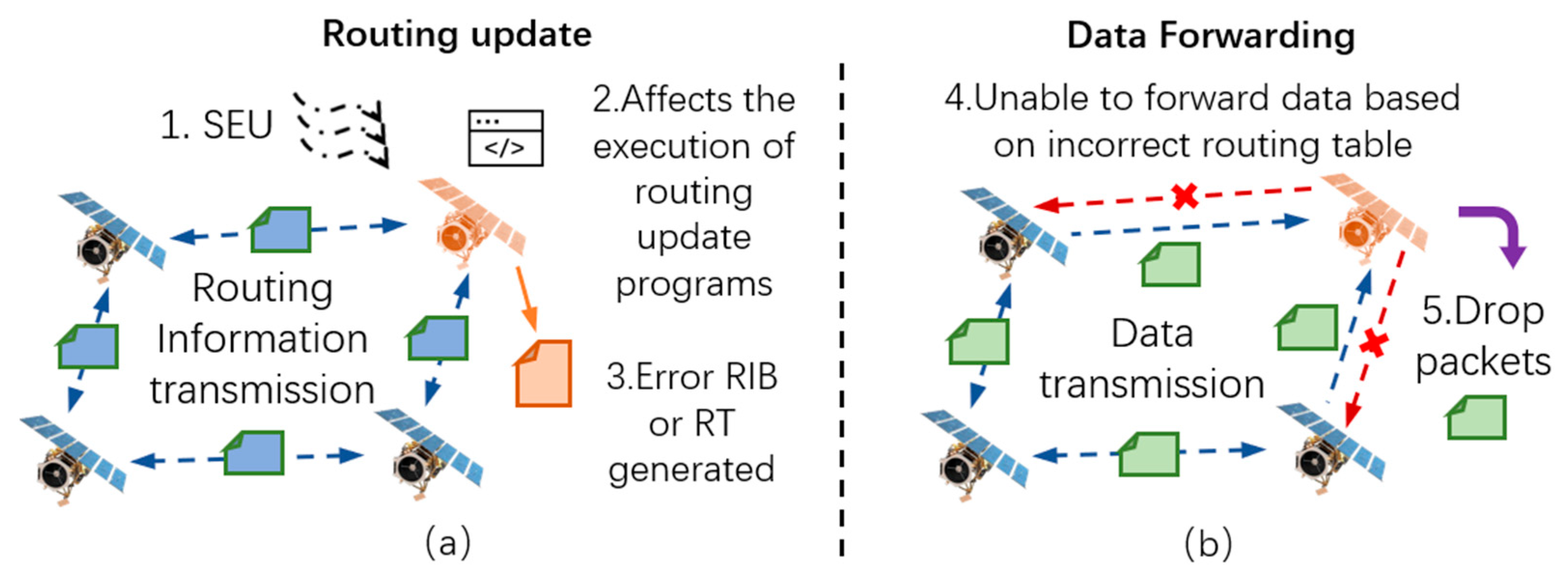
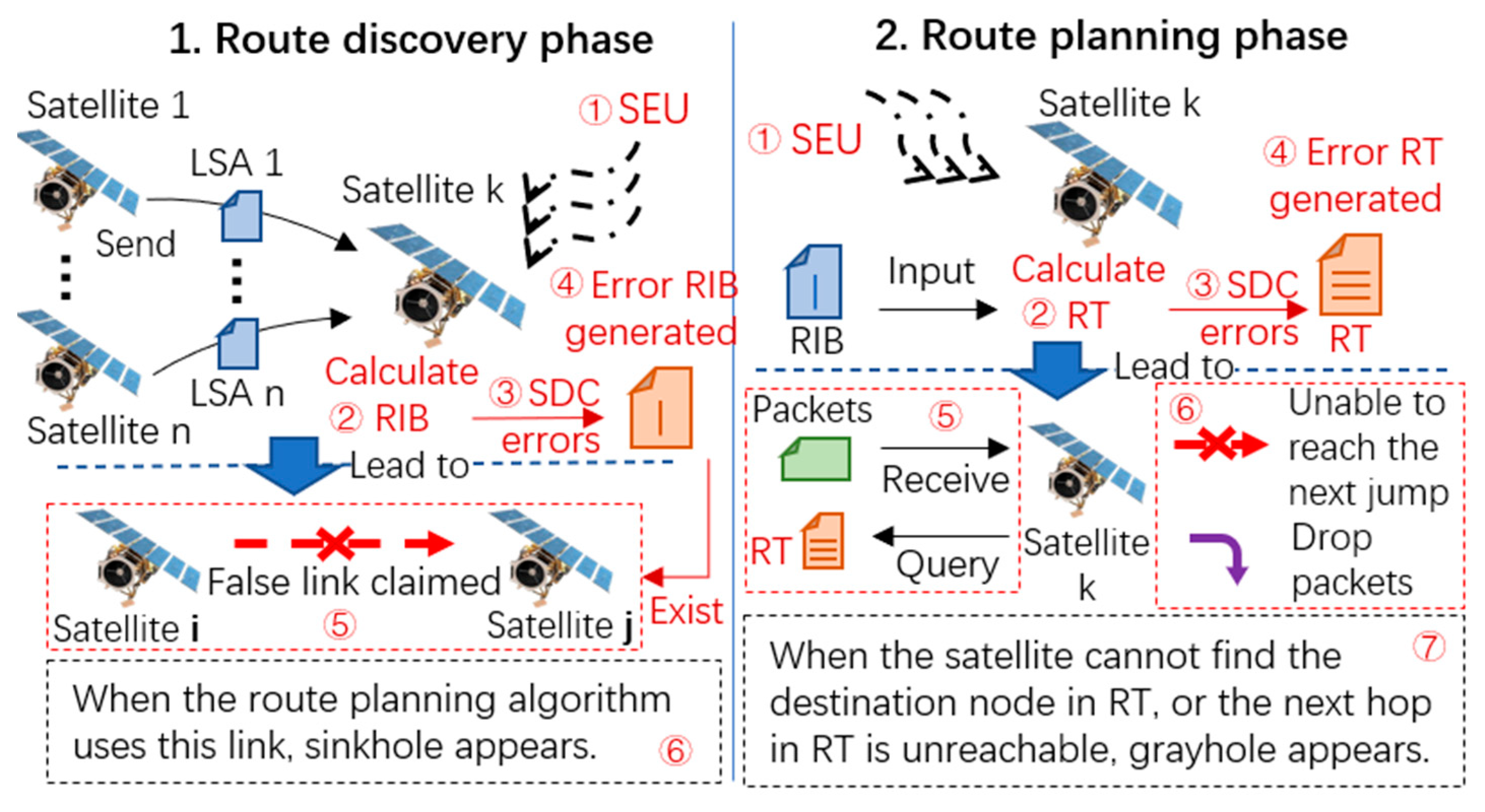
3.2. SH Node Generation Mechanism
3.3. GH Node Generation Mechanism
4. The Digital-Twin-Based Detection and Protection Framework
4.1. Data Description in the Framework
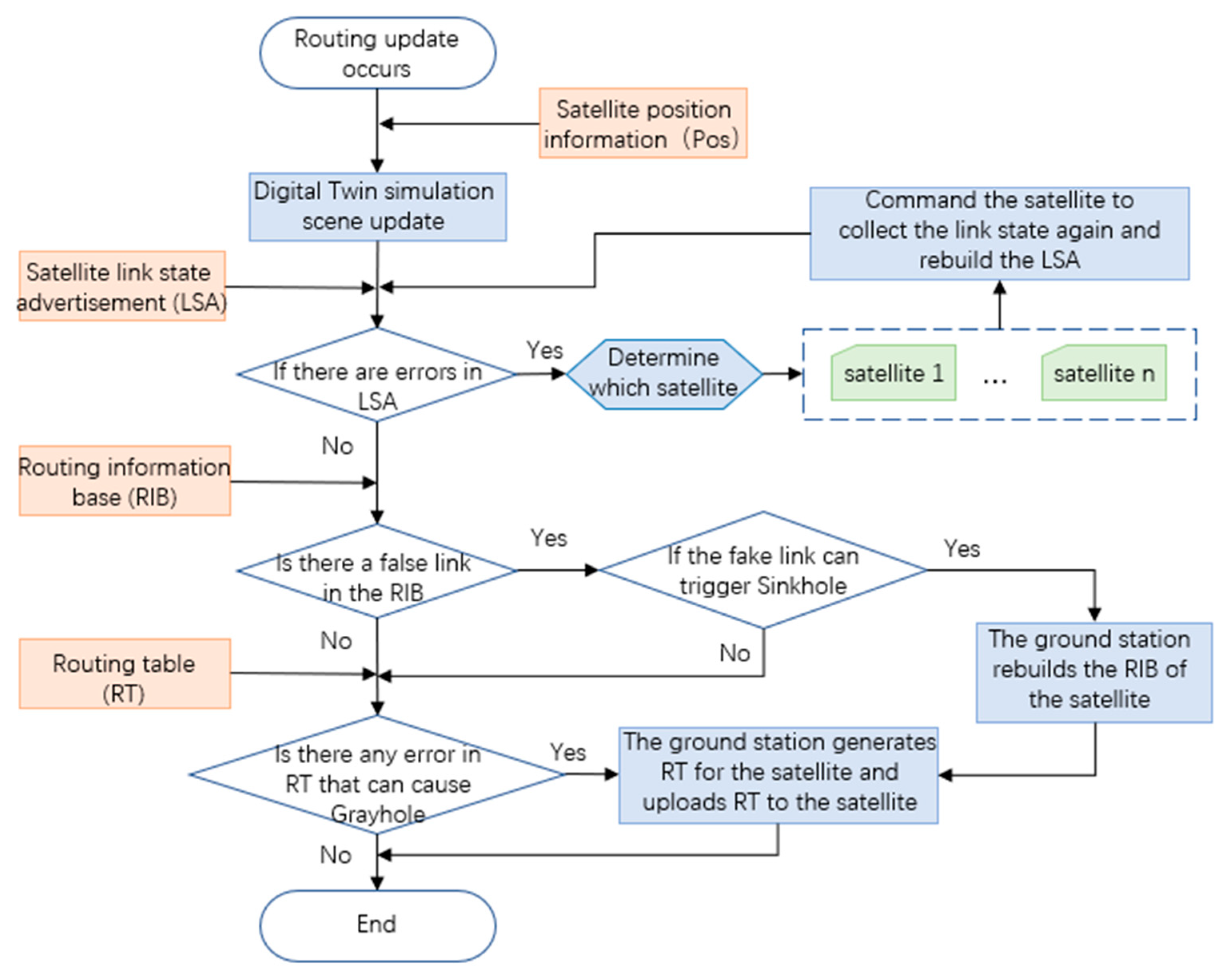
4.2. Detection and Protection Framework
4.3. The Detection and Protection Method in the Framework
4.3.1. Overall Workflow
4.3.2. SH Detection and Protection Method
| Algorithm 1 SH detection algorithm |
| Input: |
| Output: if_Sinkhole_exist |
| Start |
End |
4.3.3. GH Detection and Protection Method
| Algorithm 2 GH detection algorithm |
| Input: |
| Output: if_Grayhole_exist |
| Start |
End |
5. Simulations and Discussions
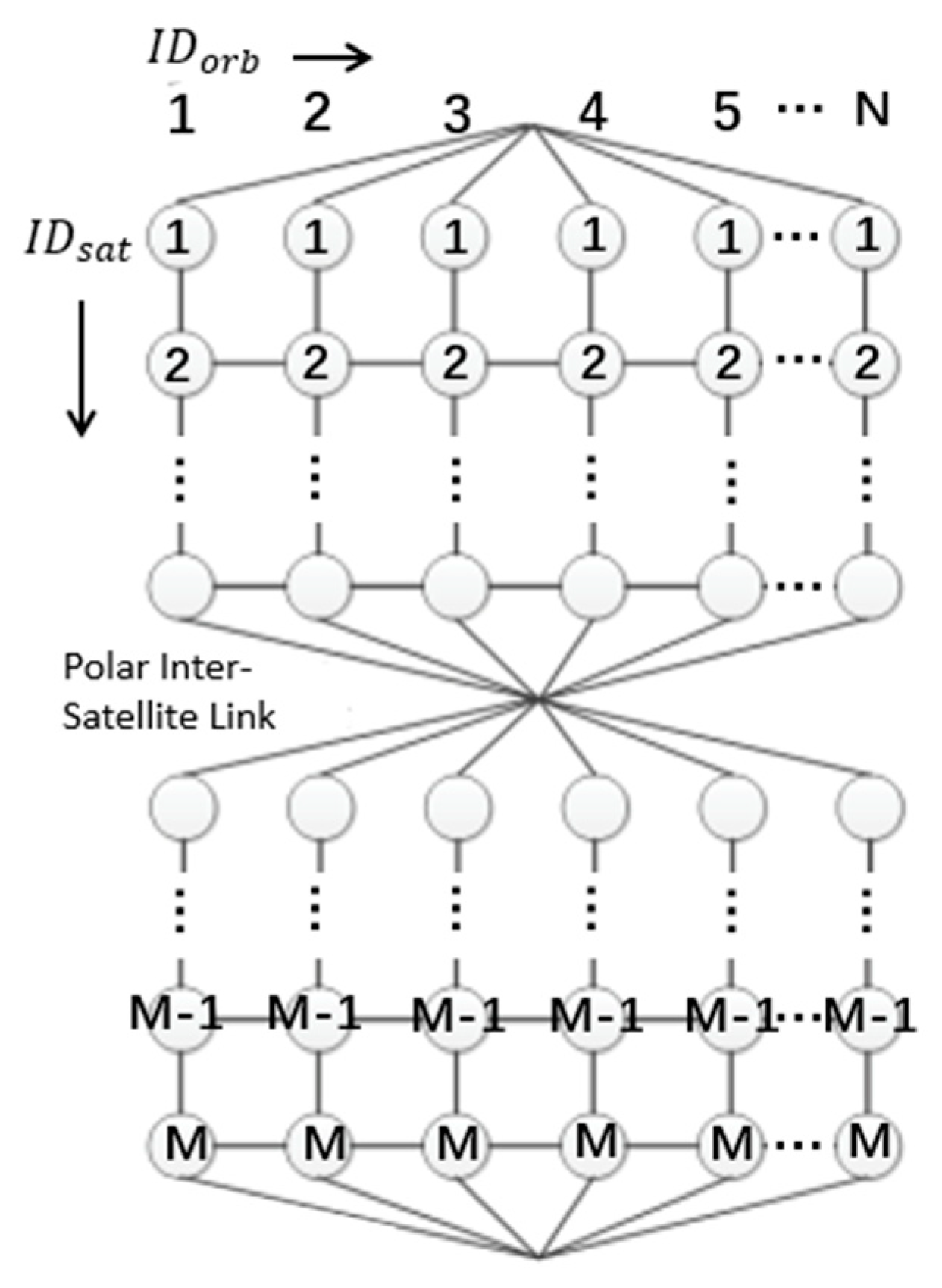
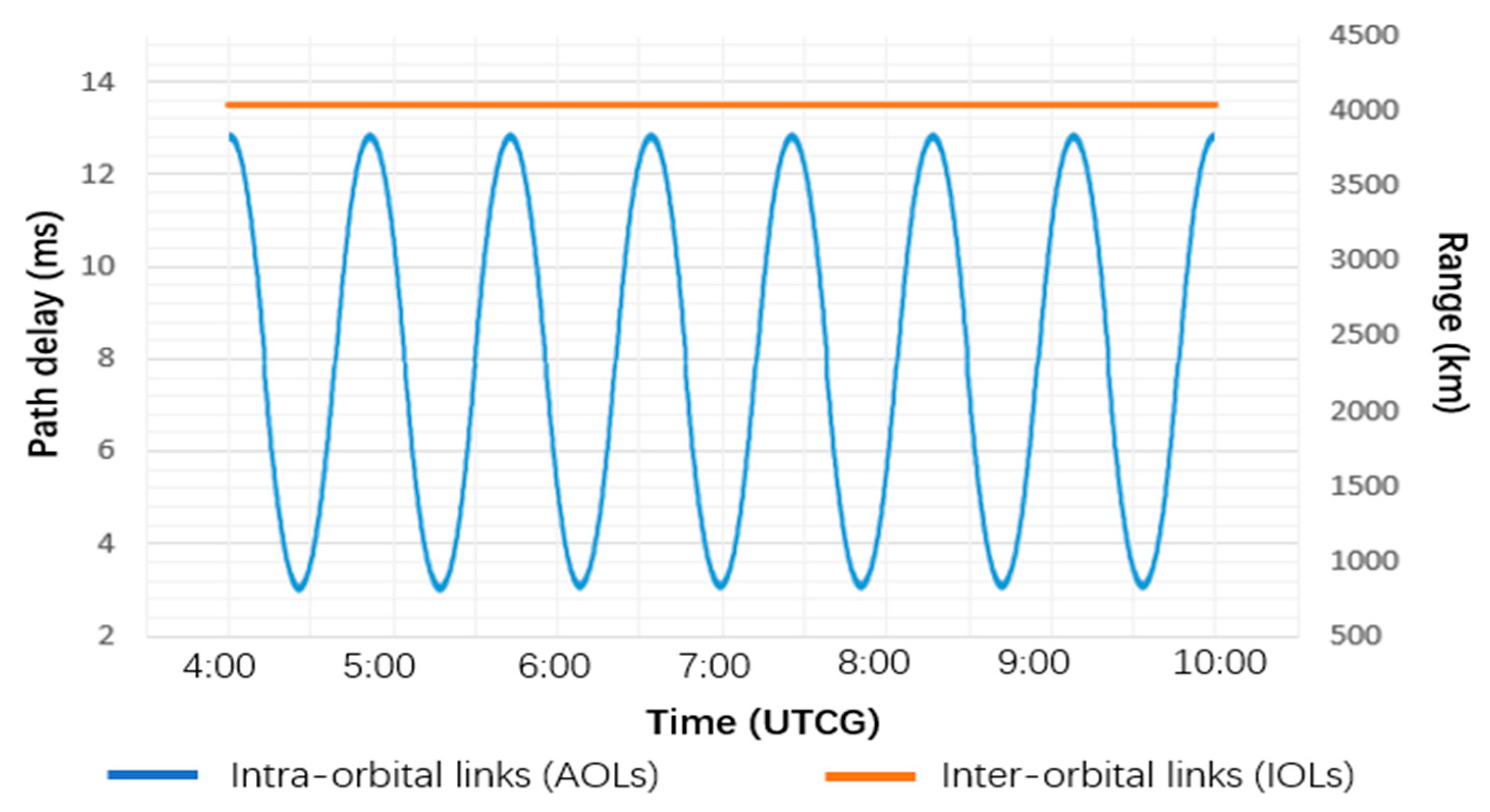
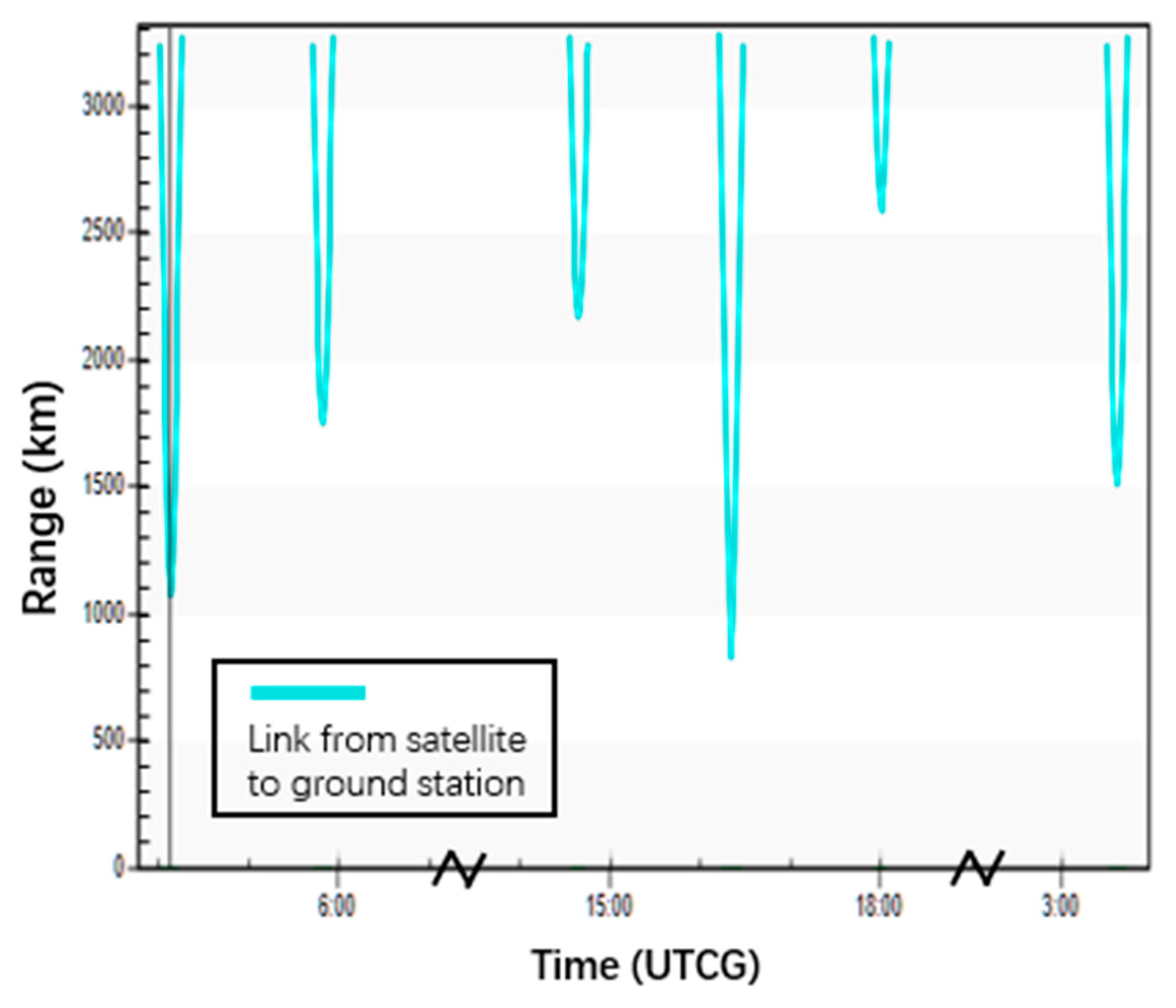
5.1. Simulation Setup
- (a)
- Route discovery phase
- (b)
- Route planning phase
5.2. Evaluation of Detection Capability
- TP (True Positive): During GH/SH detection, the detection algorithm detects positive samples as positive samples;
- TN (True Negative): During GH/SH detection, the detection algorithm detects negative samples as negative samples;
- FN (False Negative): During GH/SH detection, the detection algorithm detects positive samples as negative samples, that is, the model fails to identify that the sample has a GH/SH node;
- FP (False Positive): During GH/SH detection, the detection algorithm detects negative samples as positive samples, that is, the model misreports that the sample has a GH/SH node;
- Accuracy: ac = TP + TN/(TP + TN + FP + FN);
- Precision: pr = TP/(TP + FP);
- Recall: re = TP/(TP + FN).
- (1)
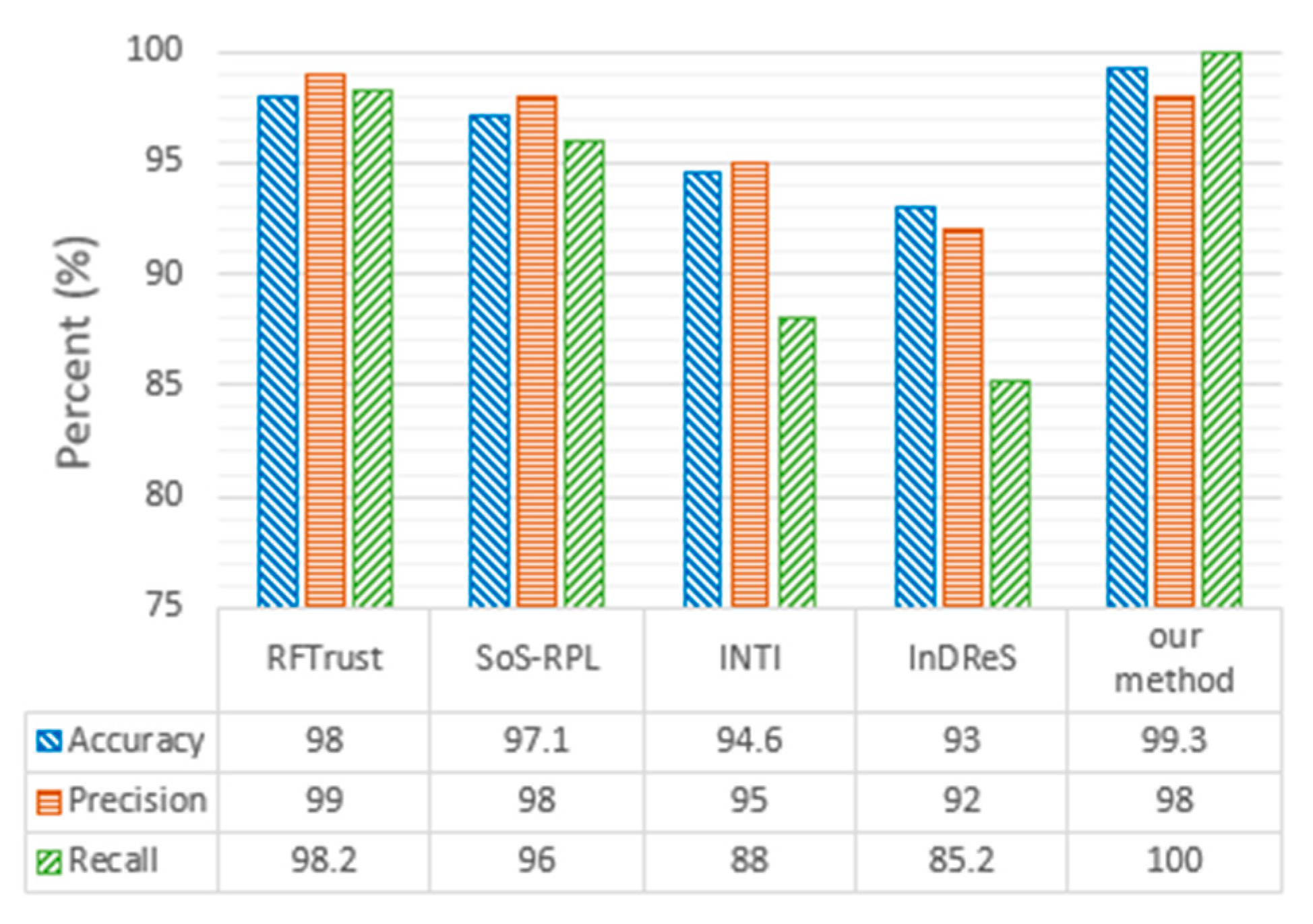
- Evaluation of SH detection capability
- RFTrust [17] considers packet delivery ratio, average delay, and energy consumption, and uses Random Forest and subjective logic to detect SHs.
- SoS-RPL [18] defines two features (DI-RANK and DV-RANK) to detect SHs, and features can be updated by exchanging routing graph information.
- INTI [33] estimates the reputation of the node to detect SH attacks. Reputation is the belief that nodes establish by iterations, actions, or information exchange between them.
- InDReS [34] considers QoS Metrics and uses a constraint-based specification model to detect SH attacks.
- (2)
- Evaluation of GH detection capability
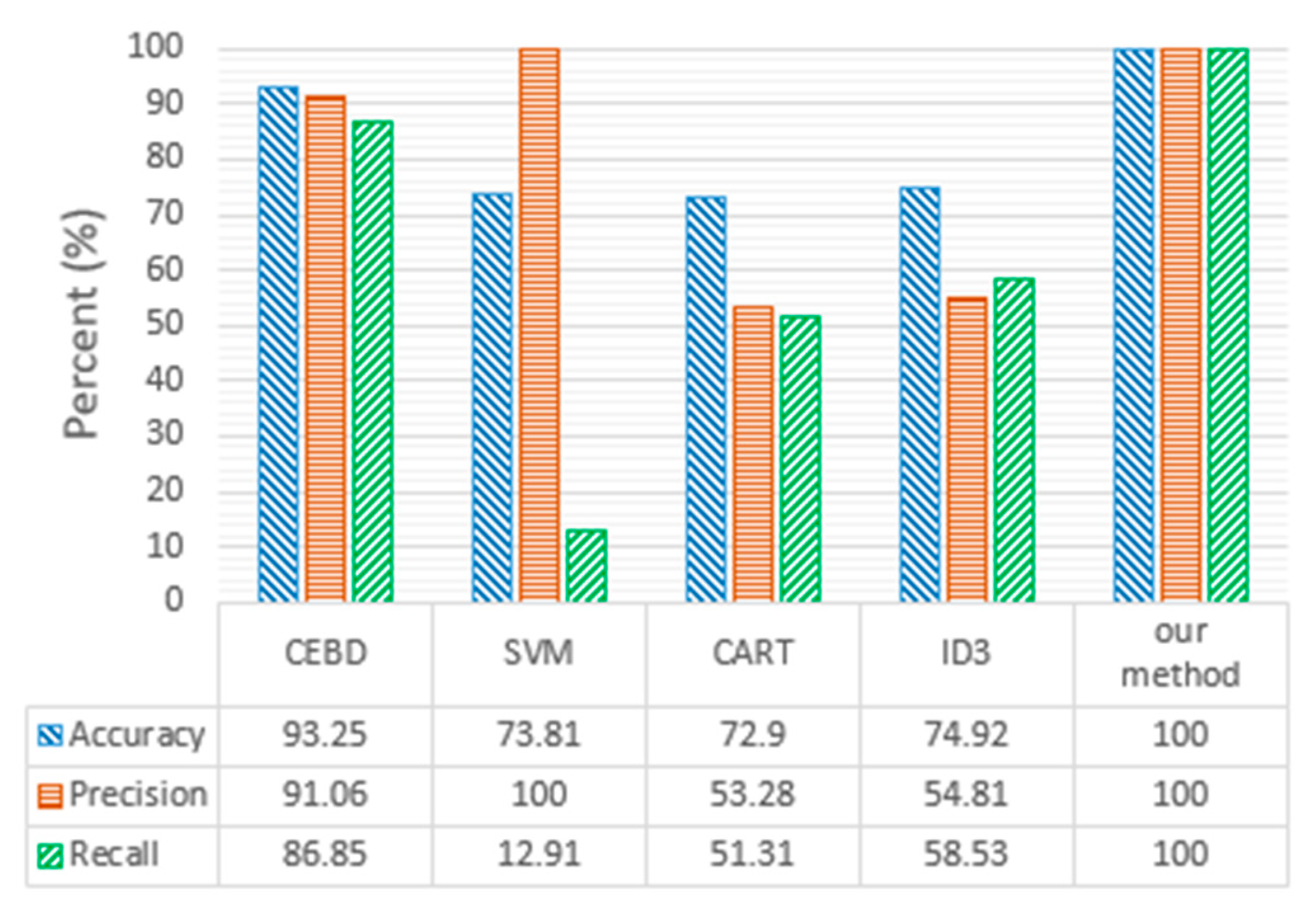
- CEBD [6] is an extensible GH detection framework, which collects and analyzes data exchanged between nodes and constructs neural-network-based behavior classifiers to distinguish Blackhole behaviors from rational behaviors.
- Other classifiers, including SVM, CART, and ID3, can also be exploited in the CEBD framework as a comparative method.
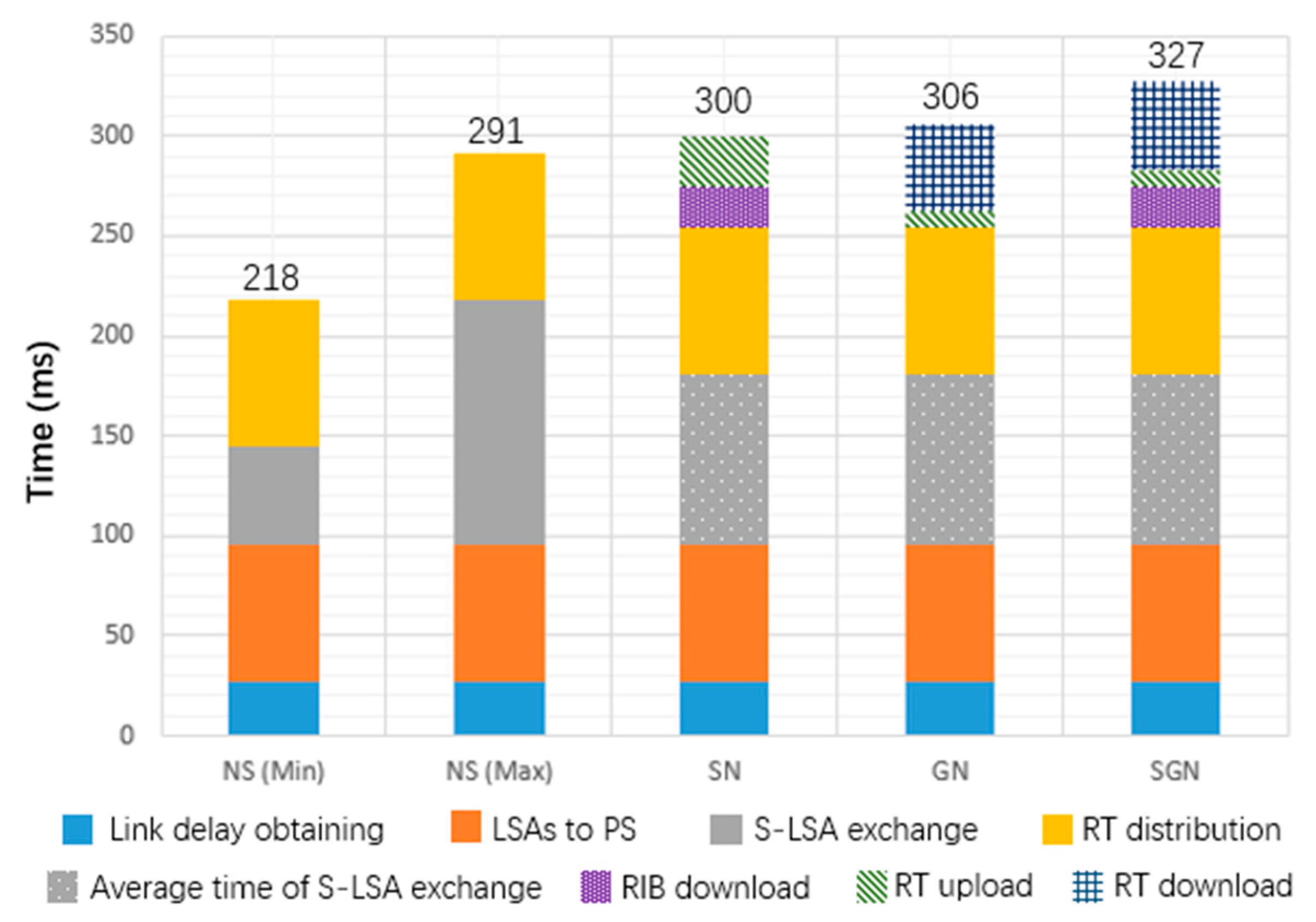
5.3. Evaluation of Performance and Cost
- (1)
- Overall computing overhead
- (2)
- Total time cost of the routing update process
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- SPE.txt, U.S. Department of Commerce, NOAA, Space Weather Prediction Center. Available online: https://www.ngdc.noaa.gov/stp/satellite/goes/doc/SPE.txt (accessed on 11 October 2022).
- James, B.; Quinn, H.; Wirthlin, M.; Goeders, J. Applying compiler-automated software fault tolerance to multiple processor platforms. IEEE Trans. Nucl. Sci. 2020, 67, 321–327. [Google Scholar] [CrossRef]
- Yan, Z.; Zhuang, Y.; Zheng, W.; Gu, J. Multi-Bit Data Flow Error Detection Method Based on SDC Vulnerability Analysis. ACM Trans. Embed. Comput. Syst. 2022; just accepted. [Google Scholar] [CrossRef]
- Hóu, Z.; Li, Q.; Foo, E. A Digital Twin Runtime Verification Framework for Protecting Satellites Systems from Cyber Attacks. In Proceedings of the 26th International Conference on Engineering of Complex Computer Systems (ICECCS), Hiroshima, Japan, 26 March 2022; pp. 117–122. [Google Scholar]
- Chen, L.; Tang, F.; Li, X.; Yang, L.T.; Cao, L. Dynamical control domain division for software defined satellite-ground integrated vehicular networks. IEEE Trans. Net. Sci. Eng. 2021, 8, 2732–2741. [Google Scholar] [CrossRef]
- Gao, Y.; Tao, J.; Xu, Y.; Wang, Z.; Sun, W.; Cheng, G. Cebd: Contact-evidence-driven blackhole detection based on machine learning in oppnets. IEEE Trans. Comput. Soc. Syst. 2021, 8, 1344–1356. [Google Scholar] [CrossRef]
- Ioulianou, P.P.; Vassilakis, V.G.; Shahandashti, S.F. ML-based Detection of Rank and Blackhole Attacks in RPL Networks. In Proceedings of the 13th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20 July 2022; pp. 338–343. [Google Scholar]
- Pundir, S.; Wazid, M.; Singh, D.P.; Das, A.K.; Rodrigues, J.J.; Park, Y. Designing efficient sinkhole attack detection mechanism in edge-based IoT deployment. Sensors 2020, 20, 1300. [Google Scholar] [CrossRef]
- Nadeem, A.; Alghamdi, T.G. Detection Algorithm for Sinkhole Attack in Body Area Sensor Networks Using Local Information. Int. J. Netw. Secur. 2019, 21, 670–679. [Google Scholar]
- Remya Krishnan, P.; Arun Raj Kumar, P. Detection and Mitigation of Smart Blackhole and Gray Hole Attacks in VANET Using Dynamic Time Warping. Wirel. Pers. Commun. 2022, 124, 931–966. [Google Scholar] [CrossRef]
- Shangguan, D.; Chen, L.; Ding, J. A digital twin-based approach for the fault diagnosis and health monitoring of a complex satellite system. Symmetry 2020, 12, 1307. [Google Scholar] [CrossRef]
- Zhao, L.; Wang, C.; Zhao, K.; Tarchi, D.; Wan, S.; Kumar, N. INTERLINK: A digital twin-assisted storage strategy for satellite-terrestrial networks. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3746–3759. [Google Scholar] [CrossRef]
- Liu, J.; Zhao, B.; Xin, Q.; Su, J.; Ou, W. Drl-er: An intelligent energy-aware routing protocol with guaranteed delay bounds in satellite megaconstellations. IEEE Trans. Netw. Sci. Eng. 2020, 8, 2872–2884. [Google Scholar] [CrossRef]
- Wang, Y.; Feng, J.; Liu, J.; Liu, X.; Wang, J. Case Study of Digital Twin-based Human-robot Collaborative Work-cell for Satellite Assembly. In Proceedings of the 2021 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Xi’an, China, 8 December 2021; pp. 698–702. [Google Scholar]
- Li, Y.; Tao, Z.; Wang, L.; Du, B.; Guo, J.; Pang, S. Digital twin-based job shop anomaly detection and dynamic scheduling. Robot. Comput.-Integr. Manuf. 2023, 79, 102443. [Google Scholar] [CrossRef]
- Azangoo, M.; Sorsamäki, L.; Sierla, S.A.; Mätäsniemi, T.; Rantala, M.; Rainio, K.; Vyatkin, V. A methodology for generating a digital twin for process industry: A case study of a fiber processing pilot plant. IEEE Access 2022, 10, 58787–58810. [Google Scholar] [CrossRef]
- Prathapchandran, K.; Janani, T. A trust aware security mechanism to detect sinkhole attack in RPL-based IoT environment using random forest–RFTRUST. Comput. Netw. 2021, 198, 108413. [Google Scholar] [CrossRef]
- Zaminkar, M.; Fotohi, R. SoS-RPL: Securing internet of things against sinkhole attack using RPL protocol-based node rating and ranking mechanism. Wirel. Pers. Commun. 2020, 114, 1287–1312. [Google Scholar] [CrossRef]
- Pan, T.; Huang, T.; Li, X.; Chen, Y.; Xue, W.; Liu, Y. OPSPF: Orbit prediction shortest path first routing for resilient LEO satellite networks. In Proceedings of the ICC 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20 May 2019; pp. 1–6. [Google Scholar]
- Pramitarini, Y.; Perdana, R.H.Y.; Tran, T.N.; Shim, K.; An, B. A hybrid price auction-based secure routing protocol using advanced speed and cosine similarity-based clustering against sinkhole attack in VANETs. Sensors 2022, 22, 5811. [Google Scholar] [CrossRef]
- Singh, S.; Nandan, A.S.; Sikka, G.; Malik, A.; Vidyarthi, A. A secure energy-efficient routing protocol for disease data transmission using IoMT. Comput. Electr. Eng. 2022, 101, 108113. [Google Scholar] [CrossRef]
- Didehban, M.; So, H.; Gali, P.; Shrivastava, A.; Lee, K. Generic Soft Error Data and Control Flow Error Detection by Instruction Duplication. IEEE Trans. Dependable Secur. Comput. 2023, 1, 1–16. [Google Scholar] [CrossRef]
- So, H.; Didehban, M.; Ko, Y.; Shrivastava, A.; Lee, K. EXPERT: Effective and flexible error protection by redundant multithreading. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19 March 2018; pp. 533–538. [Google Scholar]
- So, H.; Didehban, M.; Shrivastava, A.; Lee, K. A software-level redundant multithreading for soft/hard error detection and recovery. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25 March 2019; pp. 1559–1562. [Google Scholar]
- Li, Z.; Menon, H.; Maljovec, D.; Livnat, Y.; Liu, S.; Mohror, K. Spotsdc: Revealing the silent data corruption propagation in high-performance computing systems. IEEE Trans. Vis. Comput. Gr. 2020, 27, 3938–3952. [Google Scholar] [CrossRef] [PubMed]
- Shrivastava, A.; Didehban, M. Software approaches for in-time resilience. In Proceedings of the 56th Annual Design Automation Conference, Las Vegas, NV, USA, 2 June 2019; pp. 1–4. [Google Scholar]
- Wei, J.; Thomas, A.; Li, G.; Pattabiraman, K. Quantifying the accuracy of high-level fault injection techniques for hardware faults. In Proceedings of the 2014 44th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Atlanta, GA, USA, 23 June 2014; pp. 375–382. [Google Scholar]
- Guan, M.; Xu, T.; Gao, F.; Nie, W.; Yang, H. Optimal walker constellation design of LEO-based global navigation and augmentation system. Remote Sens. 2020, 12, 1845. [Google Scholar] [CrossRef]
- Xu, R.; Di, X.; He, X.; Qi, H. Evaluation method of node importance in temporal satellite networks based on time slot correlation. EURASIP J. Wirel. Commun. 2021, 1, 188. [Google Scholar] [CrossRef]
- Yue, H.; Wei, X.; Tan, J.; Jiang, N.; Qiu, M. Eff-ECC: Protecting GPGPUs Register File with a Unified Energy-Efficient ECC Mechanism. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2022, 41, 2080–2093. [Google Scholar] [CrossRef]
- Zhang, X.; Yang, Y.; Xu, M.; Luo, J. ASER: Scalable distributed routing protocol for LEO satellite networks. In Proceedings of the IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4 October 2021; pp. 65–72. [Google Scholar]
- Lu, Q.; Farahani, M.; Wei, J.; Thomas, A.; Pattabiraman, K. Llfi: An intermediate code-level fault injection tool for hardware faults. In Proceedings of the 2015 IEEE International Conference on Software Quality, Reliability and Security (QRS), Vancouver, BC, Canada, 5 August 2015; pp. 11–16. [Google Scholar]
- Muzammal, S.M.; Murugesan, R.K.; Jhanjhi, N.Z.; Jung, L.T. SMTrust: Proposing trust-based secure routing protocol for RPL attacks for IoT applications. In Proceedings of the 2020 International Conference on Computational Intelligence (ICCI), Bandar Seri Iskandar, Malaysia, 8 October 2020; pp. 305–310. [Google Scholar]
- Surendar, M.; Umamakeswari, A. InDReS: An Intrusion Detection and response system for Internet of Things with 6LoWPAN. In Proceedings of the 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23 March 2016; pp. 1903–1908. [Google Scholar]
- Cho, I.S.; Baek, S.J. Optimal multicast scheduling for millimeter wave networks leveraging directionality and reflections. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10 May 2021; pp. 1–10. [Google Scholar]
- Bai, T.; Heath, R.W. Coverage and rate analysis for millimeter-wave cellular networks. IEEE Trans. Wireless Commun. 2014, 14, 1100–1114. [Google Scholar] [CrossRef]
- Yang, S.; Shao, Q.; Bian, C. Reliability analysis of ensemble fault tolerance for soft error mitigation against complex radiation effect. Reliab. Eng. Syst. Saf. 2022, 217, 108092. [Google Scholar] [CrossRef]




| Methods | Description | Disadvantages | |
|---|---|---|---|
| Traffic- and behavior-based detection and protection method (TBDM) | SAD-EIoT [8] | 1. Nodes perceive network status by exchanging messages. 2. Detect SH nodes in the network through assumptions and assertions. | 1. Working in the forwarding stage, and, therefore, cannot SH or GH nodes caused by SDC (during the routing update stage) in time. 2. Requiring one or more satellites with strong computing power. 3. Increasing computational burden and energy consumption of satellites. |
| RFTrust [17] | 1. Nodes perceive network status by exchanging messages. 2. Random forest and subjective logic are used to detect SHs. | ||
| SoS-RPL [18] | 1. Nodes can exchange information with each other. 2. Child nodes can only detect the malicious parent by using the routing graph information. | ||
| CEBD [6]/ AutoML [7] | 1. Collect and analyze data exchanged between nodes. 2. Construct behavior classifiers to distinguish the blackhole behaviors from rational ones. | ||
| Error detection and protection method (SEDM) | EXPERT [23] | 1. Duplicate application main thread. 2. Main thread updates memory, while the other loads values from memory and detects errors. | 1. Increasing program execution time, which does not meet the high-efficiency requirements of routing programs. 2. Increasing computational burden and energy consumption of satellites. 3. Overprotection problem, namely introducing false alarms by detecting benign faults (faults that are going to be masked). |
| FISHER [24] | 1. Triplicate application main thread. 2. Main thread updates memory and the redundant threads perform error detection. | ||
| gZDC [22] | 1. Duplicate arithmetic and logical operations. 2. Replicate the execution of critical instructions and check for errors by comparing the values of redundant register operands. | ||
| DT-based detection and protection method | Our method | 1. Virtual satellite network updates according to the actual satellite network. 2. Check the routing update process file to determine if a soft error has occurred and could cause a SH or GH. | 1. Increasing satellite communication overhead. |
| Route Discovery Phase | Route Planning Phase | |
|---|---|---|
| Name | Build_RIB | Dijkstra’s Shortest Path (DSP) |
| Input | LSA (Link-state advertisement) | RIB (Routing information base) |
| Output | RIB | RT (Routing table) |
| Main function | Receive LSA information from other satellite nodes, obtain the overall link state of the satellite network, and generate an RIB. | Read the link-state information in the local RIB, use the Dijkstra algorithm to plan the shortest path to other nodes, and generate an RT. |
| SDC Error | Occurrence | Description |
|---|---|---|
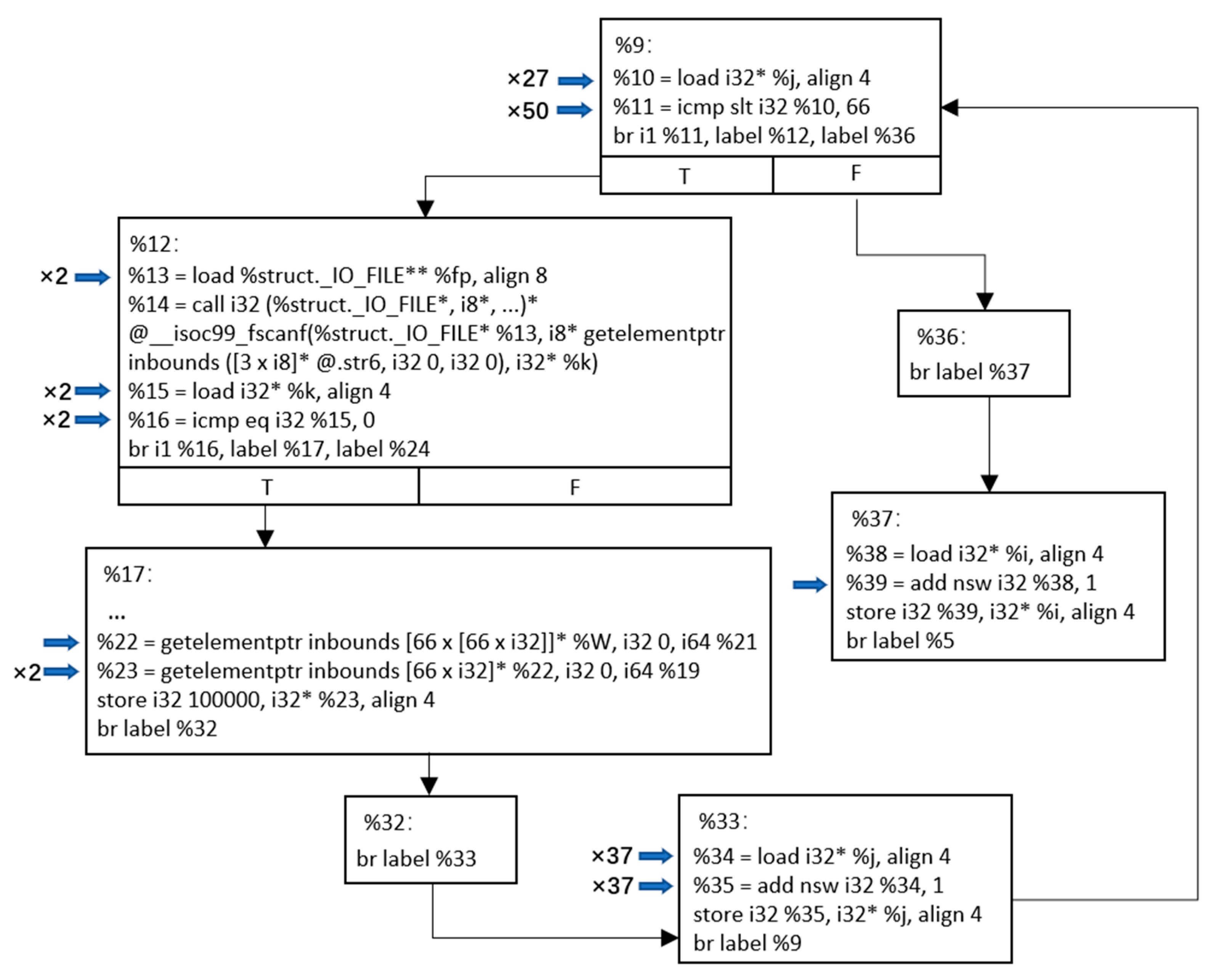
| Format error | 10 | SDC error causes the number of RIB columns to change. |
| Link missing | 124 | SDC error causes the original connected link to be marked as disconnected or missing. |
| Weight change | 121 | SDC error causes the link delay of the original connected path to change. |
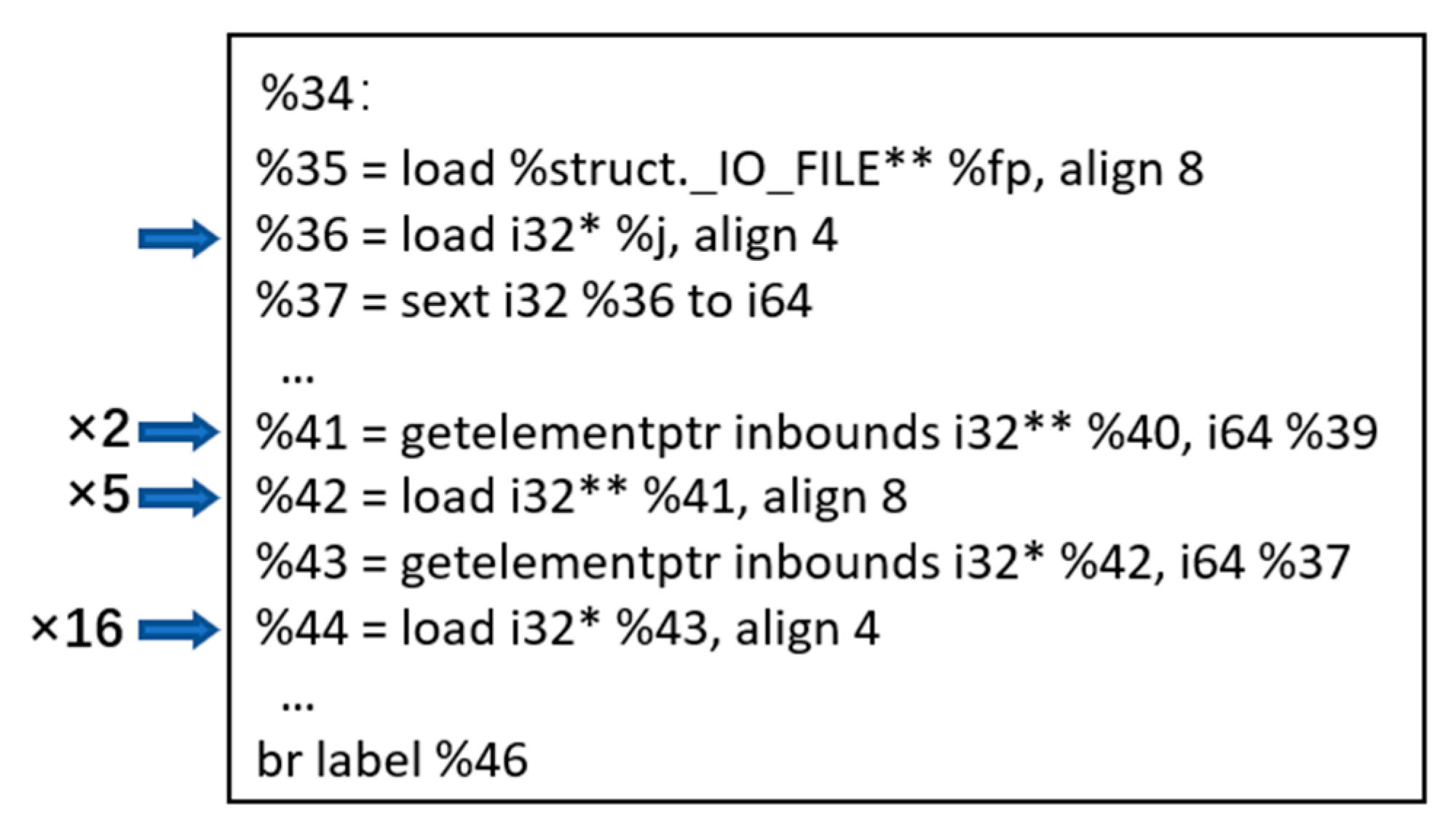
| False link | 173 | SDC error causes an unconnected path to be marked as connected. We find that of these 173 false links, 101 can generate SH nodes. |
| SDC Error | Occurrence | Description |
|---|---|---|
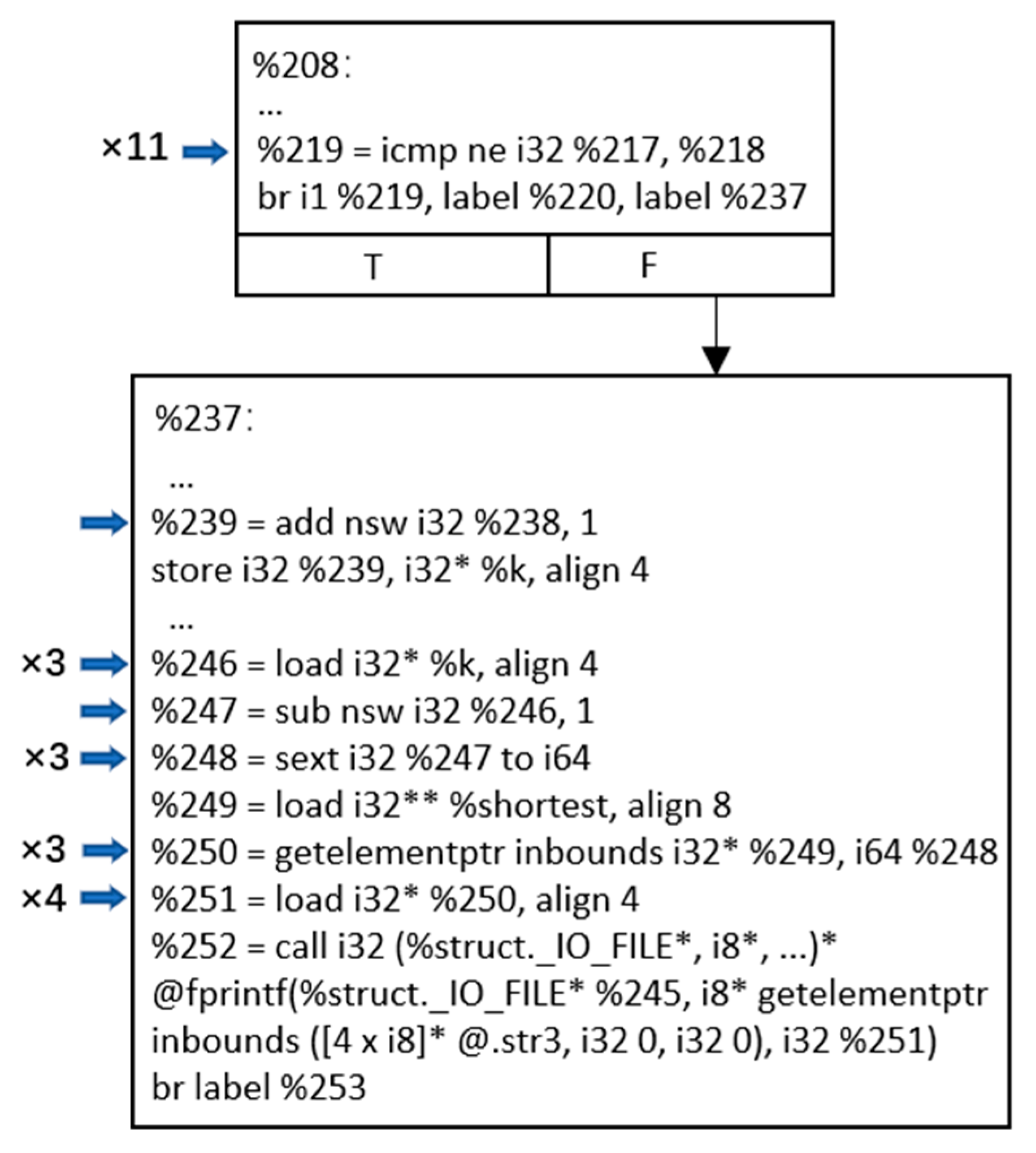
| Data loss | 9 | The route table misses one or more rows. The satellite fails to find the next hop of the corresponding destination node, which can generate a GH. |
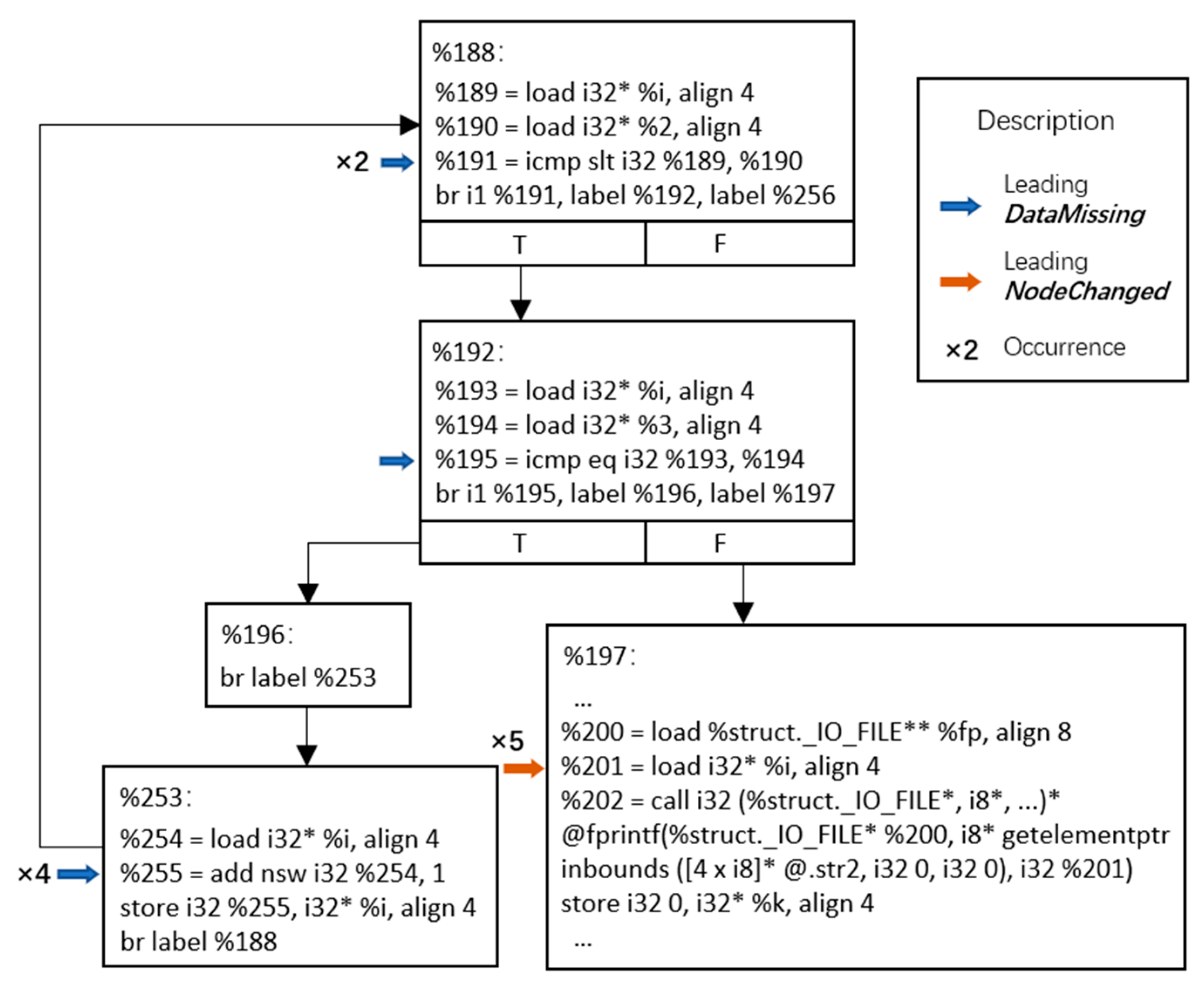
| Destination node change | 5 | The destination node in the routing table changes. The satellite fails to find the next hop of the corresponding destination node, which can generate a GH. |
| Next-hop node change | 1159 | The next hop node in the routing table changes. A GH is generated when the next-hop node changes to a non-neighbor node, which occurs 188 times in total. |
| Parameter Description | Value |
|---|---|
| Number of satellites | 66 |
| Number of orbital planes | 6 |
| Number of satellites per orbit | 11 |
| Orbital altitude (km) | 778 |
| Orbital inclination (°) | 86 |
| Adjacent orbit equatorial longitude difference (°) | 31.6 |
| Adjacent satellite latitude difference (°) | 16.4 |
| The polar region boundary latitude (°) | 70 |
| Number of ISLs for each satellite | ≤4 |
| Actual Value | |||
|---|---|---|---|
| Positives | Negatives | ||
| Predicted value | Positives | TP:100 | FP:2 |
| Negatives | FN:0 | TN:198 | |
| Actual Value | |||
|---|---|---|---|
| Positives | Negatives | ||
| Predicted value | Positives | 100 | 0 |
| Negatives | 0 | 200 | |
| NS | SN (Extra Overhead) | GN (Extra Overhead) | SGN (Extra Overhead) | |
|---|---|---|---|---|
| PT | K × GR + N × M × GRT | 0 | 0 | 0 |
| DT | K × CR + N × M × CRT | P × (GR + GRT) | q × GRT | p × (GR + GRT) + r × GRT |
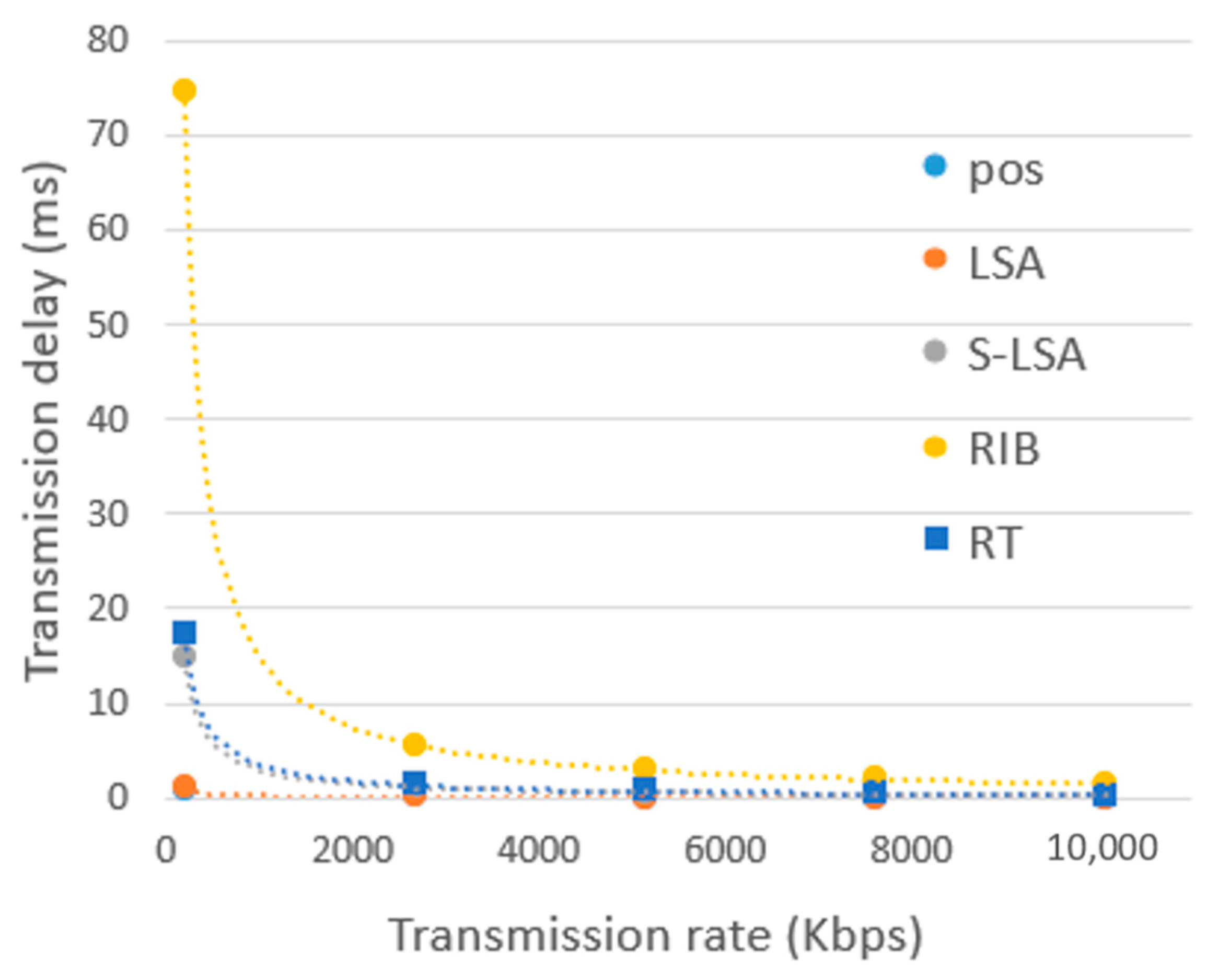
| POS | LSA | S-LSA | RIB | RT | |
|---|---|---|---|---|---|
| Size (B) | 17 | 26 | 368 | 1868 | 432 |
| The number of files in PT | 66 | 66 | 6 | 6 | 66 |
| The inter-satellite link transmission delay (ms) | - | 0.07 | 0.98 | - | 1.16 |
| The uplink transmission delay (ms) | - | - | - | - | 1.73 |
| The downlink transmission delay (ms) | 0.14 | 0.21 | - | 14.94 | 3.46 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qiao, G.; Zhuang, Y.; Ye, T.; Qiao, Y. A Digital-Twin-Based Detection and Protection Framework for SDC-Induced Sinkhole and Grayhole Nodes in Satellite Networks. Aerospace 2023, 10, 788. https://doi.org/10.3390/aerospace10090788
Qiao G, Zhuang Y, Ye T, Qiao Y. A Digital-Twin-Based Detection and Protection Framework for SDC-Induced Sinkhole and Grayhole Nodes in Satellite Networks. Aerospace. 2023; 10(9):788. https://doi.org/10.3390/aerospace10090788
Chicago/Turabian StyleQiao, Gongzhe, Yi Zhuang, Tong Ye, and Yuan Qiao. 2023. "A Digital-Twin-Based Detection and Protection Framework for SDC-Induced Sinkhole and Grayhole Nodes in Satellite Networks" Aerospace 10, no. 9: 788. https://doi.org/10.3390/aerospace10090788







