Asymmetric Propagation Delay-Aware TDMA MAC Protocol for Mobile Underwater Acoustic Sensor Networks
Abstract
:1. Introduction
2. The APD-TDMA
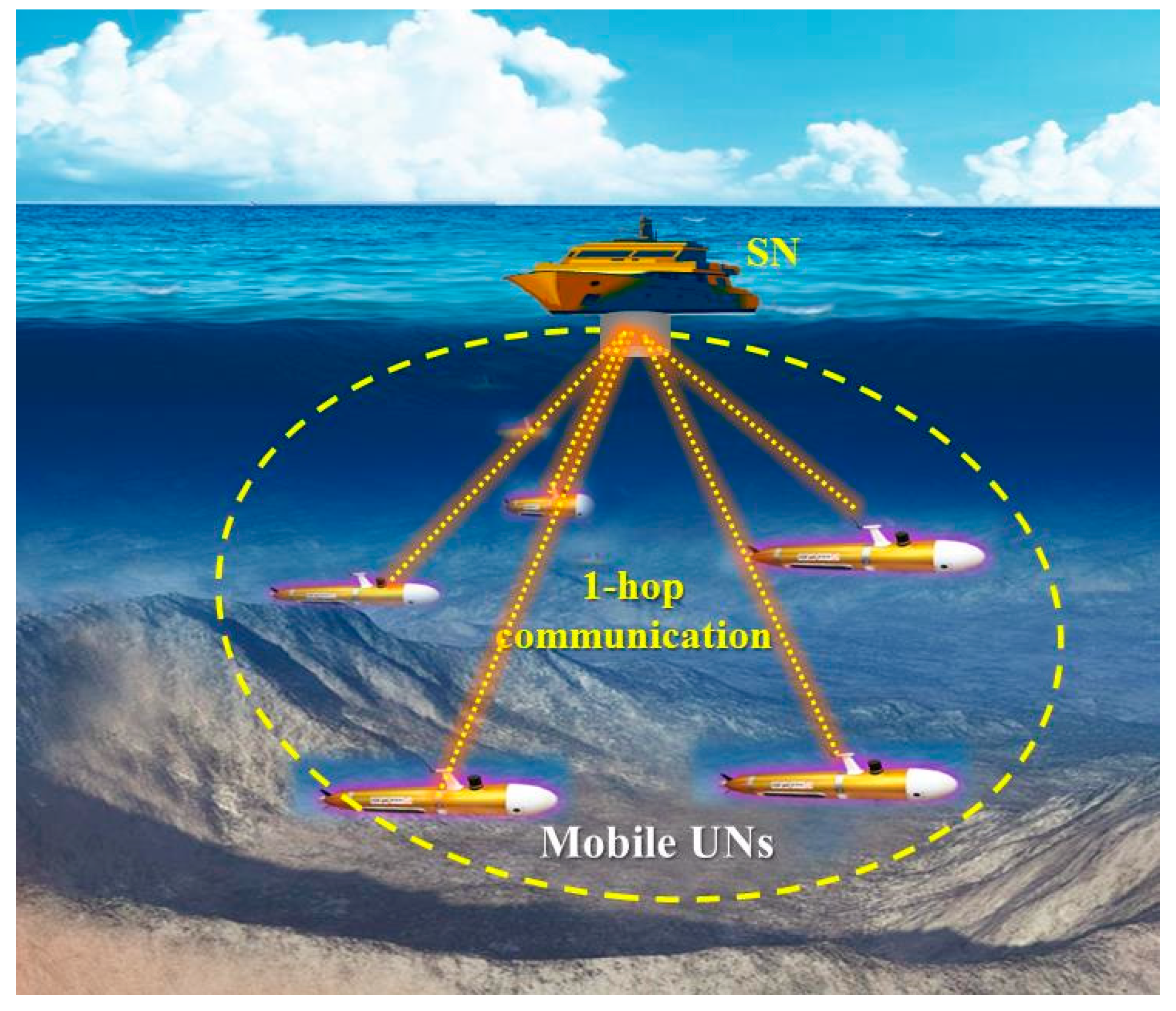
2.1. Network Model
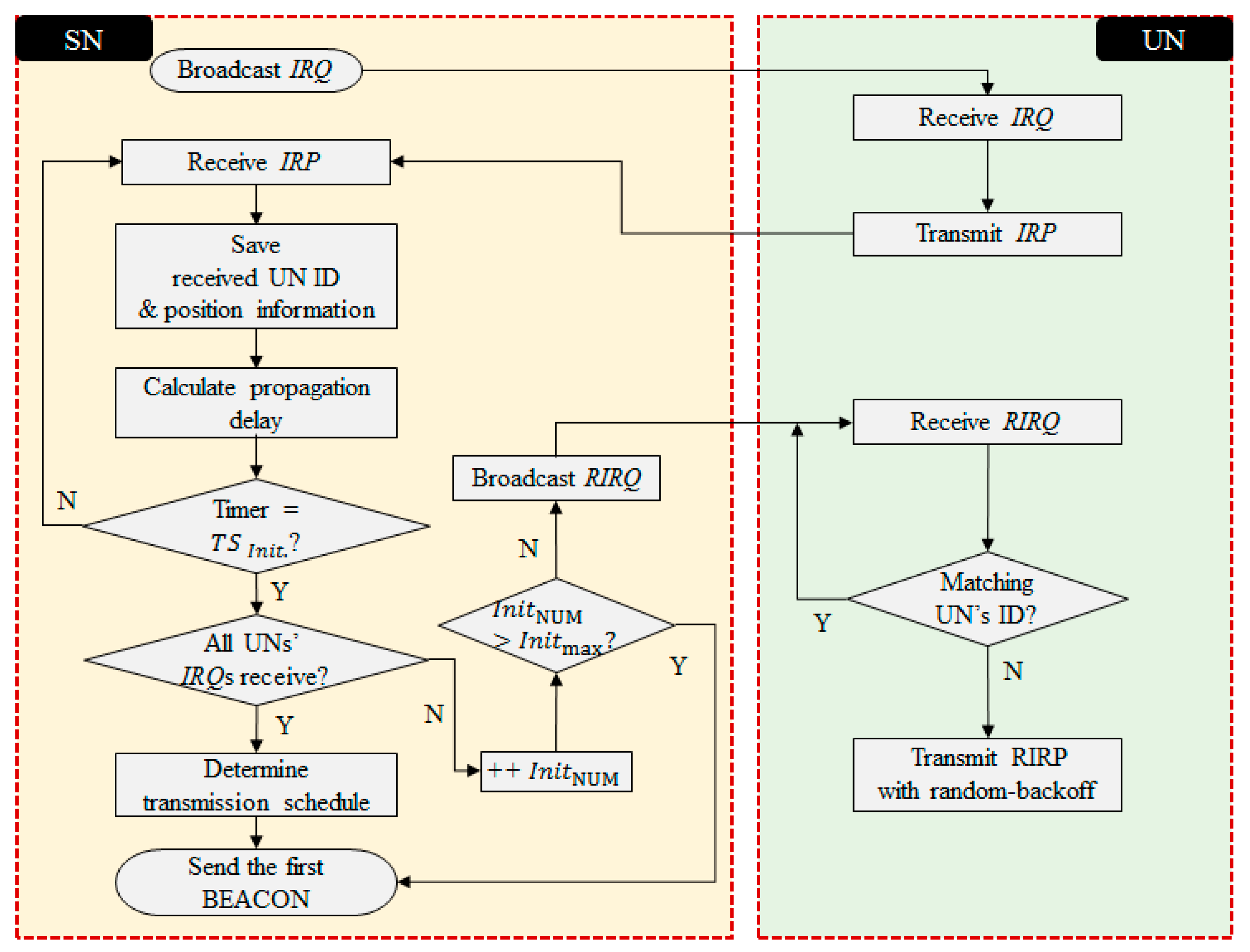
2.2. Initialization Phase
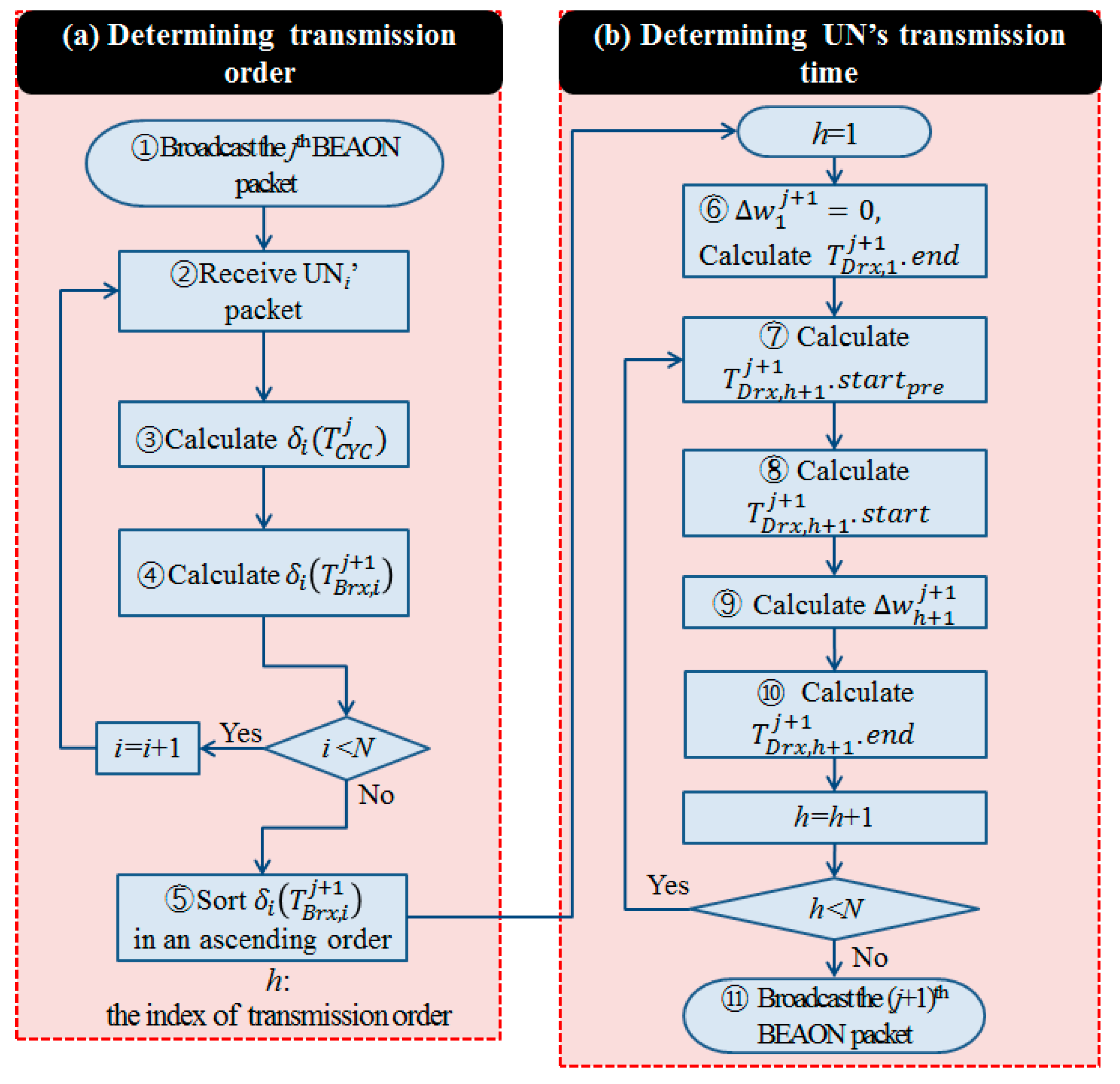
2.3. Transmission Phase
2.3.1. Scheduling to Avoid Collisions at the SN
3. Simulation Results and Analysis
- (1)
- All UNs transmit their data packets in every cycle.
- (2)
- We ignore the collisions caused by other network conditions or communication failures to clearly show the effects of asymmetric propagation delay on the network performances.
- (3)
- UNs are deployed uniformly in a three-dimensional space.
- (4)
- The velocity of UN is randomly chosen such that the speed is less than the pre-defined maximum value Vmax.
- (5)
- The data rate for the acoustic modem is set to 8 kbps, and the packet length is 500 bytes, implying that the data packet duration is 0.5 s.
- (6)
- The number of cycles is set to 10,000, and 10-indepent runs are averaged. Therefore, the CD and the CU are averaged over 100,000 cycles.
- (7)
- Simulation results are drawn by varying the number of UNs N, the network range R, and the UN’s maximum speed Vmax.
3.1. Performance Degradation due to Transmission Order
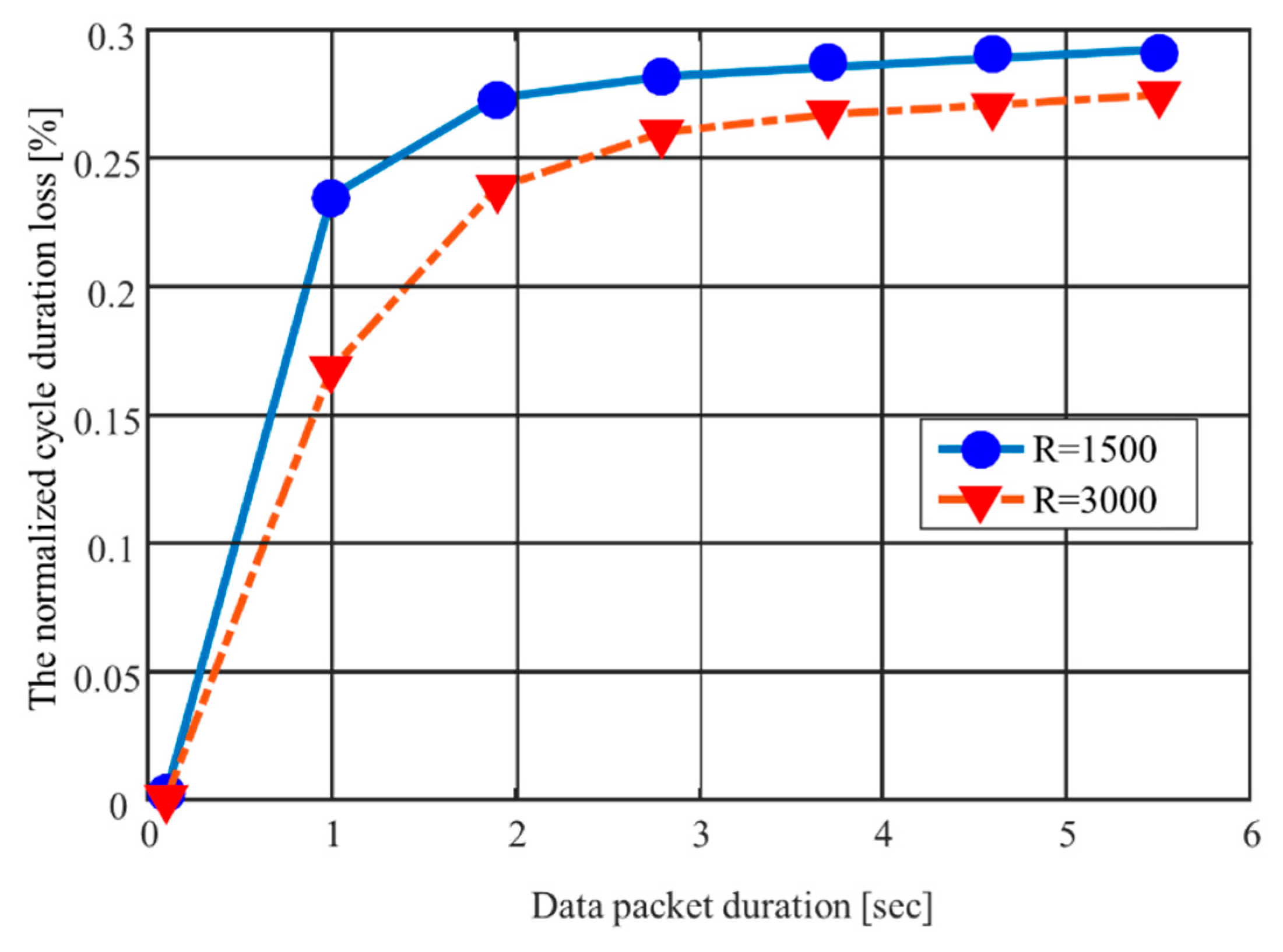
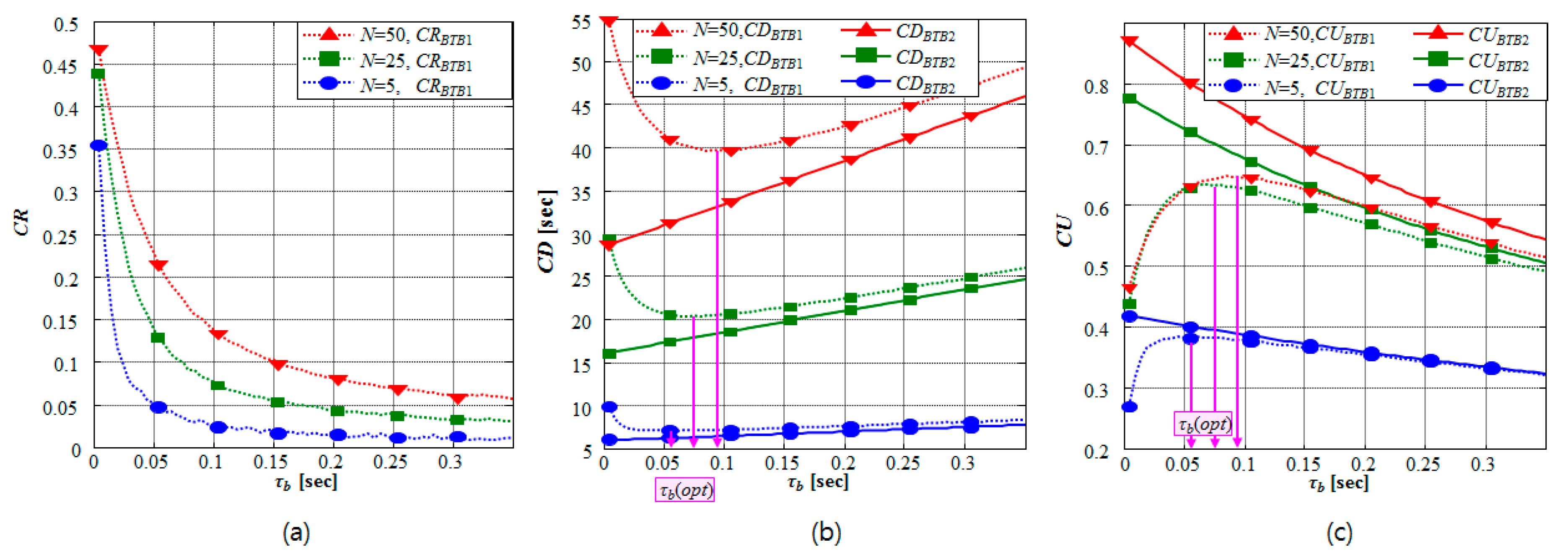
3.2. Optimal Length of a Time Block in the BTB-TDMA
- (1)
- The asymmetric propagation delay is considered in the BTB-TDMA1.
- (2)
- The BTB-TDMA2 is the original BTB-TDMA that assumes symmetric propagation delay.
3.3. Performance Versus the Number of UN
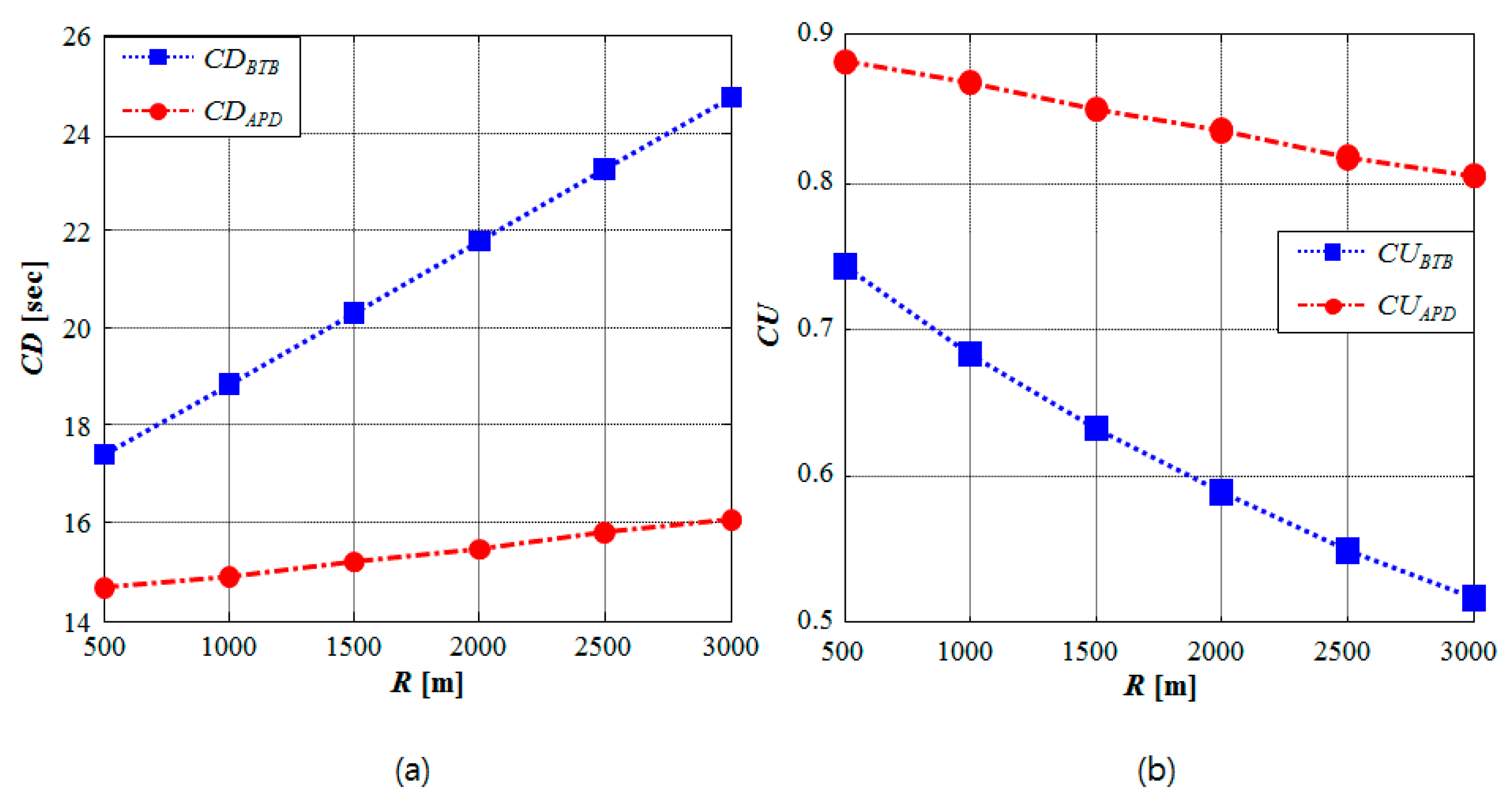
3.4. Performance Versus the Network Range
3.5. Performance Versus the Mobility of UN
4. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Heidemann, J.; Ye, W.; Wills, J.; Syed, A.; Li, Y. Research challenges and applications for underwater sensor networking. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC 2006), Las Vegas, NV, USA, 3–6 April 2006; Volume 1, pp. 228–235. [Google Scholar]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Manjula, R.B.; Sunilkumar, S.M. Issues in underwater acoustic sensor networks. Int. J. Comput. Electr. Eng. 2011, 3, 101–110. [Google Scholar]
- Cui, J.H.; Kong, J.; Gerla, M.; Zhou, S. Challenges: Building scalable mobile underwater wireless sensor networks for aquatic applications. IEEE Netw. 2006, 20, 12–18. [Google Scholar]
- Climent, S.; Sanchez, A.; Capella, J.V.; Meratnia, N.; Serrano, J.J. Underwater acoustic wireless sensor networks: Advances and future trends in physical, MAC and routing layers. Sensors 2014, 14, 795–833. [Google Scholar] [CrossRef] [PubMed]
- Felemban, E.; Shaikh, F.K.; Qureshi, U.M.; Sheikh, A.A.; Qaisar, S.B. Underwater sensor network applications: A comprehensive survey. Int. J. Distrib. Sens. Netw. 2015, 11, 896832. [Google Scholar] [CrossRef]
- Du, X.; Li, K.; Liu, X.; Su, Y. RLT Code Based Handshake-Free Reliable MAC Protocol for underwater Sensor Networks. J. Sens. 2016, 2016, 3184642. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, Y.; Gibson, J.H.; Xie, G.G.; Chen, H. Performance analysis of ALOHA and p-persistent ALOHA for multi-hop underwater acoustic sensor networks. Clust. Comput. 2011, 14, 65–80. [Google Scholar] [CrossRef]
- Chirdchoo, N.; Soh, W.S.; Chua, K.C. Aloha-based MAC protocols with collision avoidance for underwater acoustic networks. In Proceedings of the 26th IEEE International Conference on Computer Communications (INFOCOM 2007), Barcelona, Spain, 6–12 May 2007; pp. 2271–2275. [Google Scholar]
- Syed, A.A.; Ye, W.; Heidemann, J.; Krishnamachari, B. Understanding spatio-temporal uncertainty in medium access with ALOHA protocols. In Proceedings of the Second Workshop on Underwater Networks, Montreal, QC, Canada, 9–14 September 2007; pp. 41–48. [Google Scholar]
- Syed, A.; Ye, W.; Heidemann, J. T-Lohi: A new class of MAC protocols for underwater acoustic sensor networks. In Proceedings of the 27th IEEE Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 231–235. [Google Scholar]
- Chirdchoo, N.; Soh, W.S.; Chua, K.C. RIPT: A receiver-initiated reservation-based protocol for underwater acoustic networks. IEEE J. Sel. Areas Commun. 2008, 26, 1744–1753. [Google Scholar] [CrossRef]
- Molins, M.; Stojanovic, M. Slotted FAMA: A MAC protocol for underwater acoustic networks. In Proceedings of the OCEANS 2006-Asia Pacific, Singapore, 16–19 May 2007; pp. 1–7. [Google Scholar]
- Chitre, M.; Shahabudeen, S.; Freitag, L.; Stojanovic, M. Recent advances in underwater acoustic communications and networking. In Proceedings of the OCEANS 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 1–10. [Google Scholar]
- Guo, X.; Frater, M.R.; Ryan, M.J. A propagation-delay-tolerant collision avoidance protocol for underwater acoustic sensor networks. In Proceedings of the OCEANS 2006-Asia Pacific, Singapore, 16–19 May 2007; pp. 1–6. [Google Scholar]
- Peleato, B.; Stojanovic, M. Distance aware collision avoidance protocol for ad-hoc underwater acoustic sensor networks. IEEE Commun. Lett. 2007, 11. [Google Scholar] [CrossRef]
- Peng, Z.; Zhu, Y.; Zhou, Z.; Guo, Z.; Cui, J.H. COPE-MAC: A Contention-based medium access control protocol with Parallel Reservation for underwater acoustic networks. In Proceedings of the OCEANS 2010, Sydney, Australia, 24–27 May 2010; pp. 1–10. [Google Scholar]
- Xie, P.; Cui, J.H. R-MAC: An energy-efficient MAC protocol for underwater sensor networks. In Proceedings of the International Conference on Wireless Algorithms, Systems and Applications 2007 (WASA 2007), Chicago, IL, USA, 1–3 August 2007; pp. 187–198. [Google Scholar]
- Noh, Y.; Wang, P.; Lee, U.; Torres, D.; Gerla, M. DOTS: A propagation Delay-aware Opportunistic MAC protocol for underwater sensor networks. In Proceedings of the 18th IEEE International Conference Network Protocols (ICNP 2010), Kyoto, Japan, 5–8 October 2010; pp. 183–192. [Google Scholar]
- Sozer, E.M.; Stojanovic, M.; Proakis, J. Underwater acoustic networks. IEEE J. Ocean. Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Hwang, H.Y.; Cho, H.S. Throughput and Delay analysis of an underwater CSMA/CA protocol with multi-RTS and multi-DATA receptions. Int. J. Distrib. Sens. Netw. 2016, 2, 2086279. [Google Scholar] [CrossRef]
- Pompili, D.; Melodia, T.; Akyildiz, I.F. A CDMA-based medium access control for underwater acoustic sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1899–1909. [Google Scholar] [CrossRef]
- Watfa, M.; Selman, S.; Denkilkian, H. UW-MAC: An underwater sensor network MAC protocol. Int. J. Commun. Syst. 2010, 23, 485–506. [Google Scholar] [CrossRef]
- Fan, G.; Chen, H.; Xie, L.; Wang, K. A hybrid reservation-based MAC protocol for underwater acoustic sensor networks. Ad Hoc Netw. 2013, 11, 1178–1192. [Google Scholar] [CrossRef]
- Park, M.K.; Rodoplu, V. UWAN-MAC: An energy-efficient MAC protocol for underwater acoustic wireless sensor networks. IEEE J. Ocean. Eng. 2007, 32, 710–720. [Google Scholar] [CrossRef]
- Car, G.A.; Adams, A.E. ACMENet: An underwater acoustic sensor network for real-time environmental monitoring in coastal areas. IEE Proc.-Radar Sonar Navig. 2006, 153, 365–380. [Google Scholar]
- Shin, S.Y.; Park, S.H. GT2: Reduced wastes time mechanism for underwater acoustic sensor network. In Proceedings of the International Conference on Embedded and Ubiquitous Computing 2007, Taipei, Taiwan, 17–20 December 2007; pp. 531–537. [Google Scholar]
- Guo, P.; Jiang, T.; Zhu, G.; Chen, H.H. Utilizing acoustic propagation delay to design MAC protocols for underwater wireless sensor networks. Wirel. Commun. Mob. Comput. 2008, 8, 1035–1044. [Google Scholar] [CrossRef]
- Yackoski, J.; Shen, C.C. UW-FLASHR: Achieving high channel utilization in a time-based acoustic MAC protocol. In Proceedings of the Third ACM International Workshop on Underwater Networks, San Francisco, CA, USA, 14–19 September 2008; pp. 59–66. [Google Scholar]
- Kredo, K.; Djukic, P.; Mohapatra, P. STUMP: Exploiting position diversity in the staggered TDMA underwater MAC protocol. In Proceedings of the INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 2961–2965. [Google Scholar]
- Kredo, K.; Mohapatra, P. Distributed scheduling and routing in underwater wireless networks. In Proceedings of the 2010 IEEE Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–6. [Google Scholar]
- Diamant, R.; Lampe, L. A hybrid spatial reuse MAC protocol for ad-hoc underwater acoustic communication networks. In Proceedings of the 2010 IEEE International Conference on Communications Workshops (ICC), Capetown, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Diamant, R.; Shirazi, G.N.; Lampe, L. Robust spatial reuse scheduling in underwater acoustic communication networks. IEEE J. Ocean. Eng. 2014, 39, 32–46. [Google Scholar] [CrossRef]
- Chitre, M.; Motani, M.; Shahabudeen, S. Throughput of networks with large propagation delays. IEEE J. Ocean. Eng. 2014, 37, 645–658. [Google Scholar] [CrossRef]
- Hsu, C.C.; Lai, K.F.; Chou, C.F.; Lin, K.J. ST-MAC: Spatial-temporal MAC scheduling for underwater sensor networks. In Proceedings of the INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1827–1835. [Google Scholar]
- Yun, C.; Lim, Y. GSR-TDMA: A geometric spatial reuse-time division multiple access MAC protocol for multihop underwater acoustic sensor networks. J. Sens. 2016, 2016, 6024610. [Google Scholar] [CrossRef]
- Cho, A.R.; Yun, C.; Park, J.W.; Lim, Y.K. Design of a block time bounded TDMA (BTB-TDMA) MAC protocol for UANets. Ocean Eng. 2011, 38, 2215–2226. [Google Scholar] [CrossRef]
- Salva-Garau, F.; Stojanovic, M. Multi-cluster protocol for ad hoc mobile underwater acoustic networks. In Proceedings of the OCEANS 2003, San Diego, CA, USA, 22–26 September 2003; pp. 91–98. [Google Scholar]
- Urick, R. Principles of Underwater Sound for Engineers; Tata McGraw-Hill Education: New York, NY, USA, 1967. [Google Scholar]
- Morozs, N.; Mitchell, P.; Zakharov, Y. TDA-MAC: TDMA without clock synchronization in underwater acoustic networks. IEEE Access 2018, 6, 1091–1108. [Google Scholar] [CrossRef]




© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, A.-R.; Yun, C.; Lim, Y.-K.; Choi, Y. Asymmetric Propagation Delay-Aware TDMA MAC Protocol for Mobile Underwater Acoustic Sensor Networks. Appl. Sci. 2018, 8, 962. https://doi.org/10.3390/app8060962
Cho A-R, Yun C, Lim Y-K, Choi Y. Asymmetric Propagation Delay-Aware TDMA MAC Protocol for Mobile Underwater Acoustic Sensor Networks. Applied Sciences. 2018; 8(6):962. https://doi.org/10.3390/app8060962
Chicago/Turabian StyleCho, A-Ra, Changho Yun, Yong-Kon Lim, and Youngchol Choi. 2018. "Asymmetric Propagation Delay-Aware TDMA MAC Protocol for Mobile Underwater Acoustic Sensor Networks" Applied Sciences 8, no. 6: 962. https://doi.org/10.3390/app8060962



