Formal Security-Proved Mobile Anonymous Authentication Protocols with Credit-Based Chargeability and Controllable Privacy †
Abstract
:1. Introduction
2. Some Requirements for Anonymous Authentication
- Dynamic anonymous identity: When an anonymous user uses the same anonymous identity to roam over the mobile network for all sessions, her/his identity may be exposed by analyzing her/his behavior. We think that an anonymous user should use different anonymous identities for different sessions when she/he roams over the mobile network.
- No relation between any two aliases: The privacy of a mobile user will be broken if the relations between any two aliases of the user are disclosed.
- No mapping table, which contains the mapping between each real identity and its corresponding anonymous identity, stored in the system operator: The system operator authenticates an anonymous user directly without maintaining a database to record a mapping between all of the user’s anonymous identities and the user’s real identity. This will make it possible for the user to gain her/his privacy against the system, and the system can save its storage space.
- Authenticated key agreement: After anonymous authentication between the system and an anonymous user, a shared session key will be established. If the user shares a long-term key with the system in advance and derives the session key via the shared long-term key, the system can trace her/him by recognizing the long-term key embedded in the session key. Hence, in order to preserve user anonymity, the system and the user have to establish their session key without sharing any key or information in advance. Besides, all session keys should be mutually independent from each other.
- Traceability in some situations: If there exist malicious users, a trusted third party must be able to revoke their privacy. An anonymous authentication protocol should own the feature of revokable anonymity in order to deal with the above situation.
- Credit-based chargeability: When a user conceals her/his identity from the system operator, it will be hard for the system to charge the anonymous user after she/he utilizes the network services. An anonymous authentication scheme for mobile communications should allow the system operator to charge anonymous mobile users via the popularized credit-based way without revealing their identities. The credit-based chargeability in the proposed system means that any user does not need to pay, even pay with a credit card, before she/he uses the services of the system. Every consumption of the user will be accumulated in her/his ticket. The ticket has a life cycle and the user should return the ticket to the system at the end of the cycle, say the end of each month. Finally, the system will send the user a bill which includes the total amount of the consumption retrieved from the ticket.
3. The Proposed Protocols
- , H, V: These are three participants in our protocols. is a mobile user, H is the server of the home network, and V is the server of a visiting network.
- : the real identity of .
- : is a semantic secure encryption function [15] and is the decryption function corresponding to where x can be an input symmetric key or public/private key.
- : The shared session keys between and H, and V, and V and H, respectively.
- and : is the public/private key pair of the judge and is the public/private key pair of V.
- : a security parameter.
- , , and : three one-way hash functions.
- A judge device: The judge issues a tamper-resistant device which contains {a random-number generator, a symmetric-key cryptosystem, a public-key cryptosystem, a public-private key pair of the judge, , }. This device will be integrated into the system of H. It is impossible to steal or modify any information embedded in the device. In our scheme, the judge is an off-line party, i.e., the judge does not need to keep connection with H in our protocols, but the judge device does. In practice, the judge device can be implemented by the technique of TPM (Trusted Platform Module) [16] which is maintained by the Trusted Computing Group [17]. Nowadays, TPMs are also embedded in mobile phones and notebook computers [18].
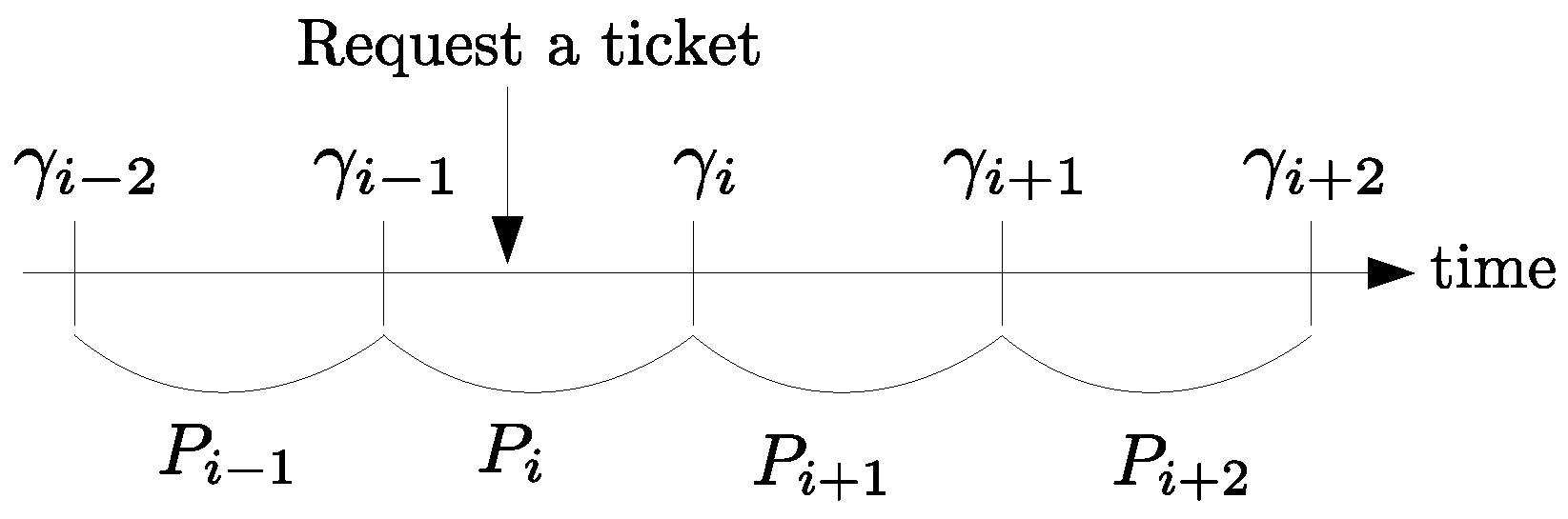
- γ: This is a due date. As shown in Figure 1, if a mobile user requests a ticket for communication in time slot , H will assign her/him the due date where is the last day of next time slot . H assigns the same γ to each mobile user who requests a ticket in the same time slot. All time slots are equally long.
3.1. Overview of Our Proposed Scheme
3.2. Key Generation
3.3. The Protocol for Requesting an Initial Anonymous Ticket
- .First, randomly generates two -bit strings , and an integer . Then computesand . Finally, submits to H.
- The judge device , γ, .In this step, H knows that , whose real identity is , wants to request a ticket. Let and γ be the last day of next time slot. Then H inputs , γ, into the judge device. H also records that has bought a ticket in the current time slot and she/he will have to return an unused ticket on the due date γ for billing.
- The judge device , ρ, .First, the judge device decrypts θ by computing and parses the result as . Then it checks if . If true, it randomly generates two -bit strings and an integer . Then it sets and computes , , andFinally, it computes , b, and and returns to H.
- .After receiving , H records and computes . Then it sends to .
- Unblinding.After receiving , checks if γ is the last day of next time slot. Then she/he decrypts ρ by computing and parses the result as . She/He also computesThen she/he obtains a ticket , δ, σ, γ, and can verify it by examining if the following formula is true:Finally, sets and and then goes to the protocol of Section 3.4 when she/he decides to use the ticket to roam the mobile networks.
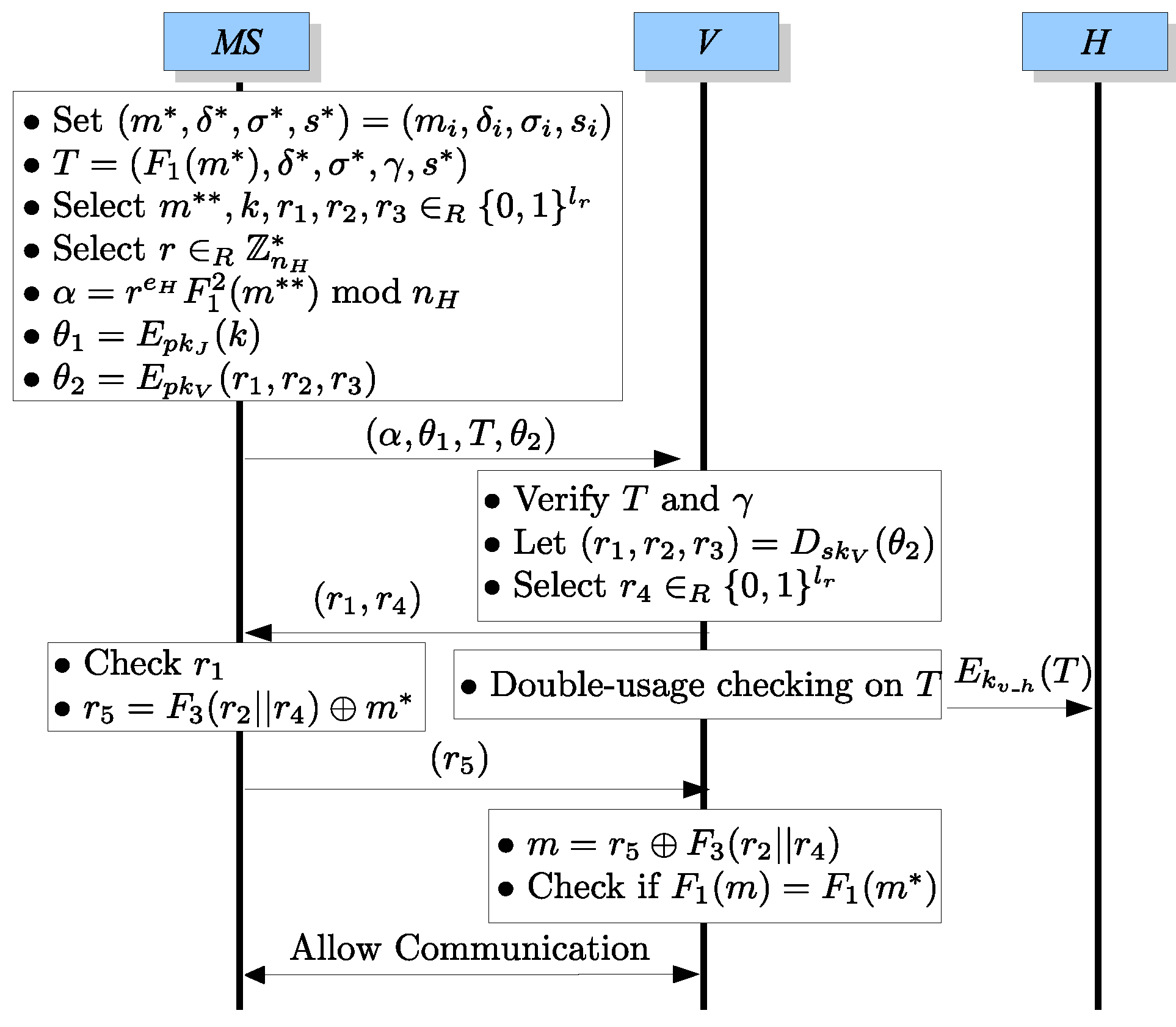
3.4. The Protocol for Using an Anonymous Ticket in the ith Round before the Due Date
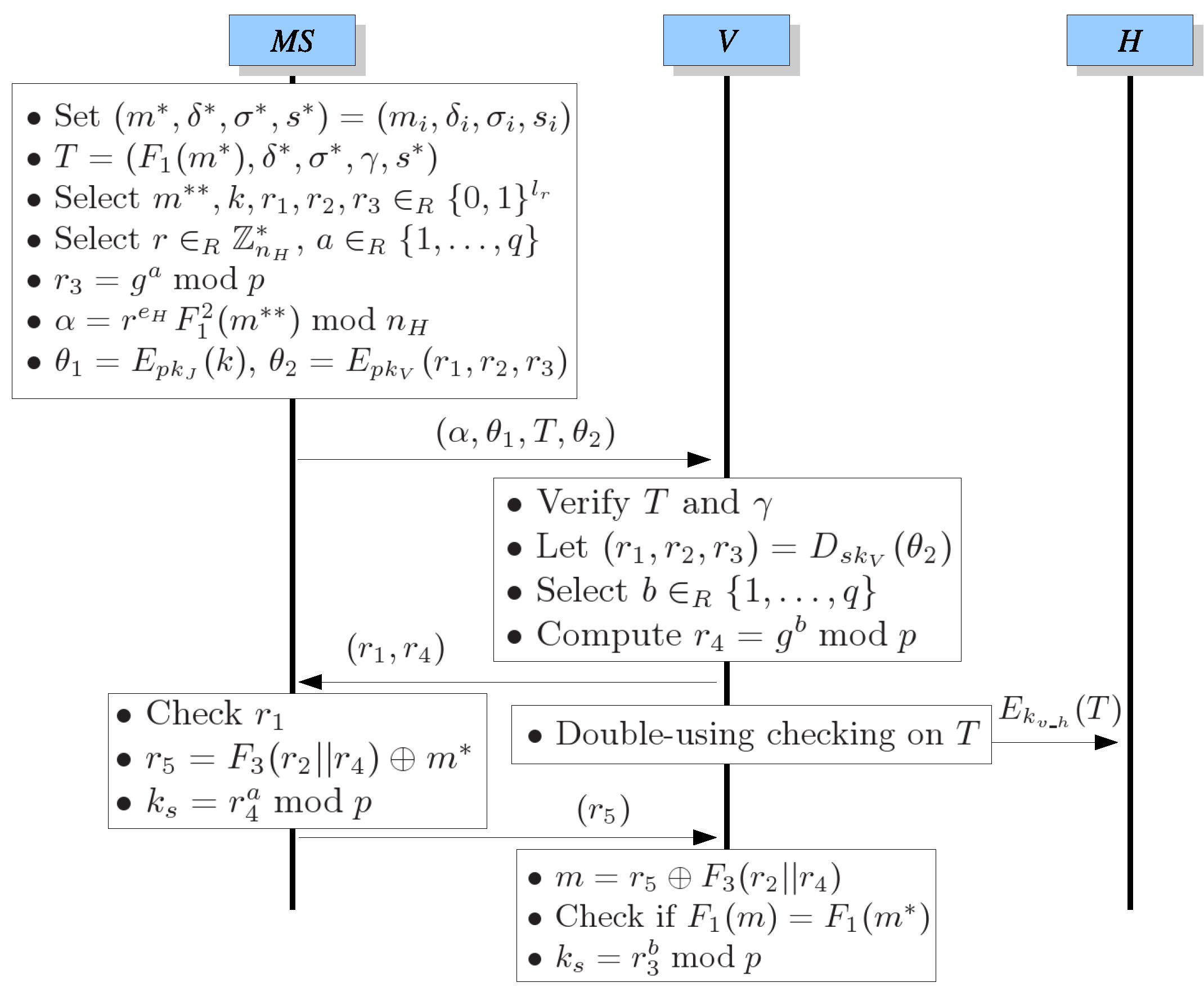
- .First, sets , , , , , , and then prepares , , γ, and randomly generates 5 -bit strings , k, , , and an integer . Furthermore, computes , , and . Finally, submits to V.
- .After receiving , V first verifies T by examining ifand γ is not expired. If true, V decrypts to get and randomly generates an -bit string . Then V sends to .
- .After V sends to , it also immediately submits to H in order to perform the double-using checking on T. If T is doubly used, the connection will be terminated.
- .After receiving , checks if is the same as the one which was chosen by herself/himself. Then computes and sends to V.
- Allowing Communication:After receiving , V computes and checks if where is retrieved from T. If true, V ensures that is the real owner of T. Therefore, V allows to communicate with it. During the communication, they can encrypt/decrypt their messages via the session key .
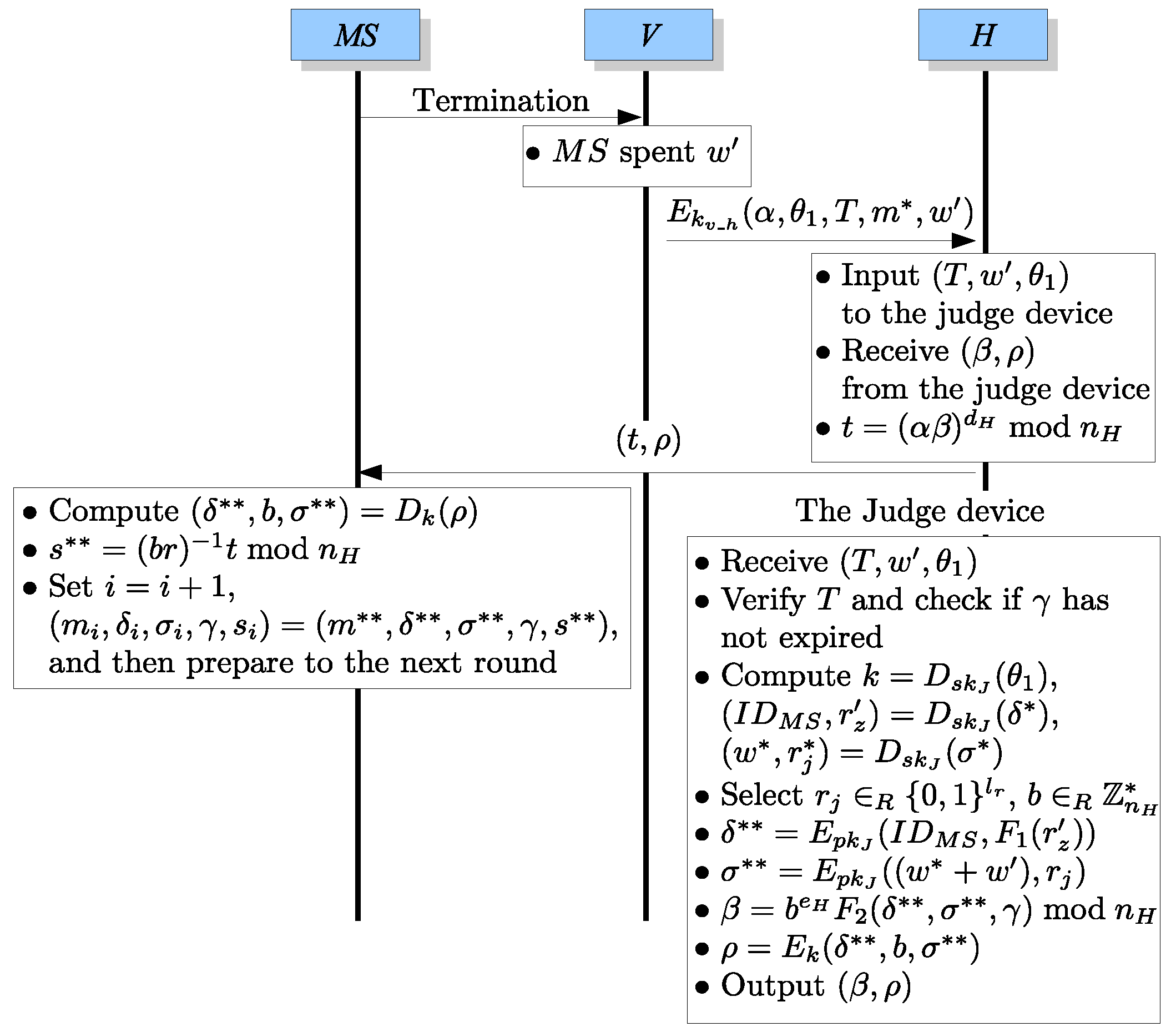
- (Termination).notifies V that she/he wants to terminate her/his communication.
- .After receiving the termination request from , V computes the spending value of according to the communication time or services utilized by . Then V sends to H.
- The judge device: , , .H decrypts the message received from V and stores into its database. Then H inputs , , into the judge device.
- The judge device , .When receiving , , , the judge device will verify T by (5) first and verify whether the due date γ embedded in T has expired or not. If one of the above verifications fails, the judge device will return an aborting signal. Otherwise, the judge device computes , , and where and are retrieved from T. Furthermore, it randomly selects a string and an integer and prepares , , and . Finally, it computes , b, and outputs , to H.
- .After receiving , , H computes and returns to .
- UnblindingAfter receiving , computes , b, and . obtains a new ticket as which can be verified by checking whether is true or not. If true, sets and , , , γ, , , , γ, , which is the new unused (fresh) ticket of the user. Thus, she/he can use the fresh ticket for the next round of communication before the due date, γ.
3.5. The Protocol for Charging Mobile Users
- returns her/his real identity and unused ticket, , to H before the due date.
- H checks that the ticket does not exist in its database and sends the ticket to the judge device.
- The judge device verifies if the ticket is valid via (4) and checks if the γ has expired. If true, it computes and returns the spending value w to H.
- H adds w to the bill of and deletes the record which indicates that has ever requested a ticket.
- Send the bill to .
- Adaptability. In current GSM services, almost all of the systems adopt credit-based ways to charge users.
- Reducing the relations between any two rounds of communication with one token only. There are two possible ways to charge a mobile user in advance (debit-based ways), which are described as follows:
- (a)
- The mobile user purchases a set of payment tokens from the system previously where each of the tokens is with a unit of value. In each round of communication, the mobile user sends a proper number of tokens to the system for payment. In this case, it is difficult for the system to derive the relation between any two rounds of communication since the tokens are independent one another. However, this will consume much storage and communication cost for recording and transmitting these tokens.
- (b)
- The mobile user purchases only one payment token from the system previously where the token is with a specific value w. In the following round of communication, the mobile user sends the token to the system for payment and then the system returns a new token with value if the user consumes value of that token. In this mechanism, the mobile user just needs to store one token. However, this will cause defective privacy. When the system returns one token with value to the user, the system knows that the user will use the token with value in the next round. There exists a relation between these two rounds of communication.
Our scheme allows a user to store one token and greatly reduces the relations between any two rounds of communication from the system’s point of view. All of the users return their unused tickets to the system for charging and thus the system knows the total spending value of every user in the previous time slot. However, it is difficult for the system to trace a specific user by finding out all of her/his spending values from the spending value pool which contains all spending values of all users in the previous time slot. This is the subset sum problem, shown below, which is NP-Hard [19]. The proposed system makes it computationally infeasible to link any two rounds of communication with the assumption of large subset sizes.Definition 1. Given a vector over integers and a positive integer s, called the sum, compute a solution vector where such that .The integer s can be regarded as the total spending value of a mobile user and the vector A contains all spending values in the spending value pool. - Free from the problem of overspending. In debit-based charging methods (both of the above two ways (a) and (b)), when a mobile user shows her/his token(s) to the system for communicating, her/his communication will be terminated if the tokens or the token’s value are used up. It will cause inconvenience for the mobile user. If the system does not terminate the communication, the mobile user will overspend the token(s) and the system must perform extra procedures to deal with the situation. In our scheme, based on a credit-based method, the above problem can be avoided.
3.6. The Protocol for Privacy Revoking
- Tracing the mobile user by a designated ticket: Once an anonymous user imposes on anonymity to commit a crime, her/his ticket will be reported to the judge. Assume that the ticket is . The judge will extract from the ticket and parse to get .
- Tracing the tickets by a designated mobile user: If the police want to trace a criminal (whose real identity is ) in the time slot , the police can send to H and ask H and the judge to disclose the privacy of the criminal. In this case, H will retrieve ξ from its stored records according to and send ξ to the judge. After decrypting ξ and obtaining , the judge computesThen, it sends to H, and H can help the police to trace the mobile user in time slot via the above set. In our scheme, the mobile user takes the anonymous ticket containing for her/his first round of communication, the ticket containing for the second round, and so forth. According to this order, H can trace the communication activities of the criminal from the first round to the ith round via {}.
3.7. Exceptions
- The mobile user denies returning her/his ticket for billing on the due date: After the due date γ, if there is any mobile user who has not returned her/his unused ticket yet, H will send a list to the judge where contains the identities of the mobile users who did not return their unused tickets. According to , the judge sends a payment notification to each mobile user on and announces another due date . If a mobile user, say , has not returned her/his unused ticket on the new due date , the judge will compute the set , , , according to via Equation (6) and then sends it to H. Let denote the ith ticket, i.e., the ticket containing . Assume that the mobile user denied returning . H can find from its database via . When H finds , the judge can help H with extracting the spending value from , and then H computes and adds to the bill of the mobile user .
- The mobile user lost her/his ticket: When a mobile user, say , lost her/his unused ticket , she/he must ask H to freeze her/his unused ticket or it may be used by a malicious user. After an authorization process, for example, the mobile user signs a document to show that she/he agrees H to ask the judge to compute where the mobile user authorizes H to reveal her/his privacy, H sends to the judge to compute by Equation (6). Assume that the mobile user lost . H must deny the services for by , respectively, where . Besides, H finds from its database via and sends to the judge to extract the accumulated spending value from . After the judge returns to H, H adds to the bill of the mobile user.In order to handle this exception, the privacy of of the mobile user will be revealed. However, if the mobile user remembered how many tickets she/he has used, she/he can still preserve her/his privacy. For example, a mobile user lost her/his unused ticket, and she/he remembers that she/he has consumed 4 tickets. Then the judge just needs to compute for H, and { are still kept secret for the mobile user. H will check if exists in its database where . If exists in its database and does not, H will retrieve , which will be used for charging the mobile user, from the database via . After the mobile user freezes her/his lost ticket, she/he can perform the protocol in Section 3.3 again to request a new ticket.
- The communication is terminated abnormally: Consider the case that the communication of Step 5 in Section 3.4 is abnormally terminated, i.e., the mobile user does not receive a renewed ticket. We assume that each time when the mobile user receives successfully, she/he will return an to H. Once H does not receive , it will store and into an unsuccessful communication record. Thus, the mobile user can retransmit to H, and H can re-send to the mobile user.Even though the mobile user lost all information in the abnormal termination, i.e., the mobile user cannot unblind t and decrypt ρ when H retransmits them to her/him, she/he can notify H that she/he lost her/his ticket and then go back to the protocol of requesting an anonymous ticket (Section 3.3) to request a new one. In such a case, H can still correctly charge the mobile user and the mobile user can still use the new ticket for the following communications.
4. Security Proofs
4.1. Security Requirements
- Unlinkability: No one except the judge can trace a user when she/he is using her/his ticket for roaming the mobile networks.
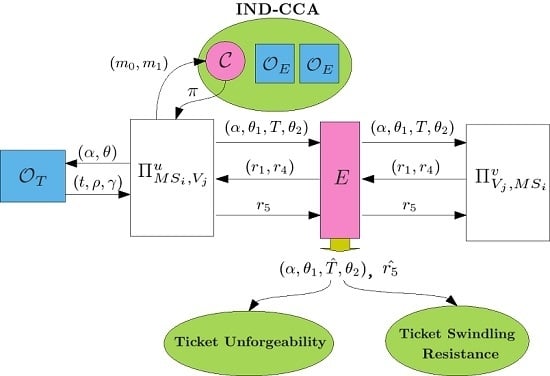
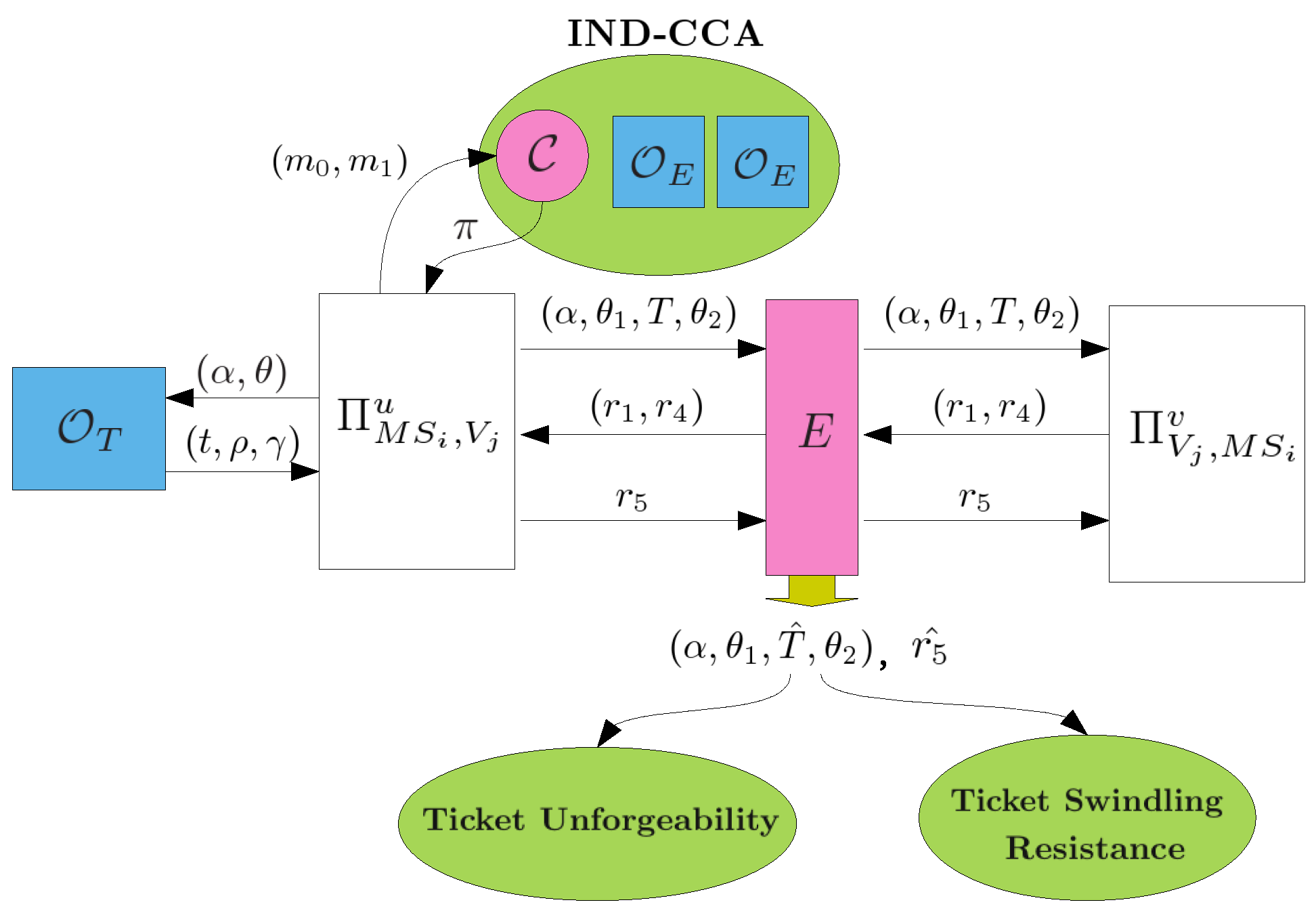
- Ticket Unforgeability: None can forge a ticket without performing the requesting ticket protocol of Section 3.3 with the system.
- Tamper Resistance: The triple in a ticket cannot be modified.
- Ticket Swindling Resistance: Anyone else cannot consume an eavesdropped ticket for communication services where the ticket is owned by some user.
- Mutual Authentication: Neither a mobile user without a valid ticket nor an illegal system can pass the authentication.
- Secure Authenticated Key Exchange: After mutual authentication, a mobile user and V can share a common session key unknown to any eavesdropper.
4.2. Unlinkability
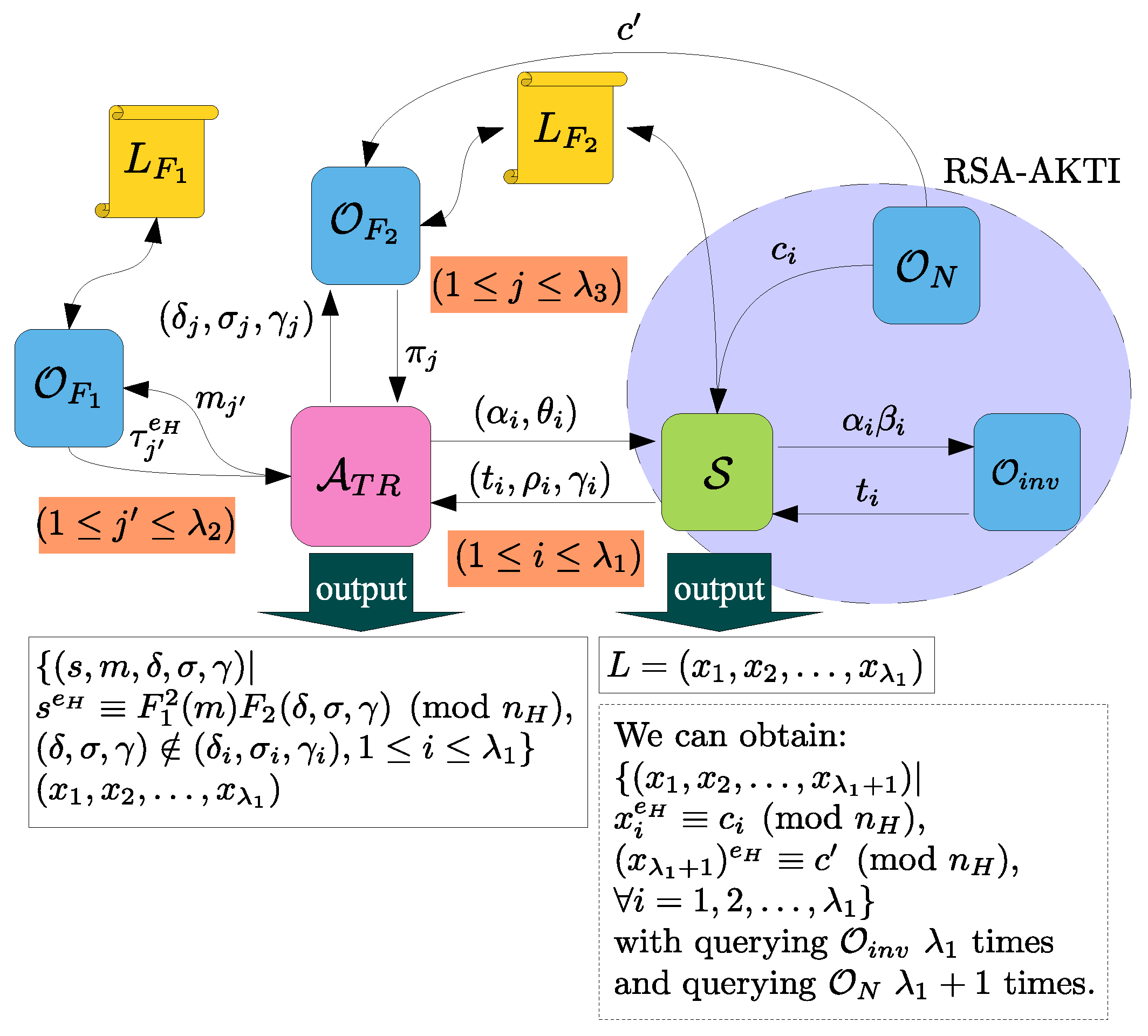
4.3. Ticket Unforgeability
4.4. Tamper Resistance
- Search by m and get entry .
- Search by and get entry where , i.e., .
- Compute and thus .
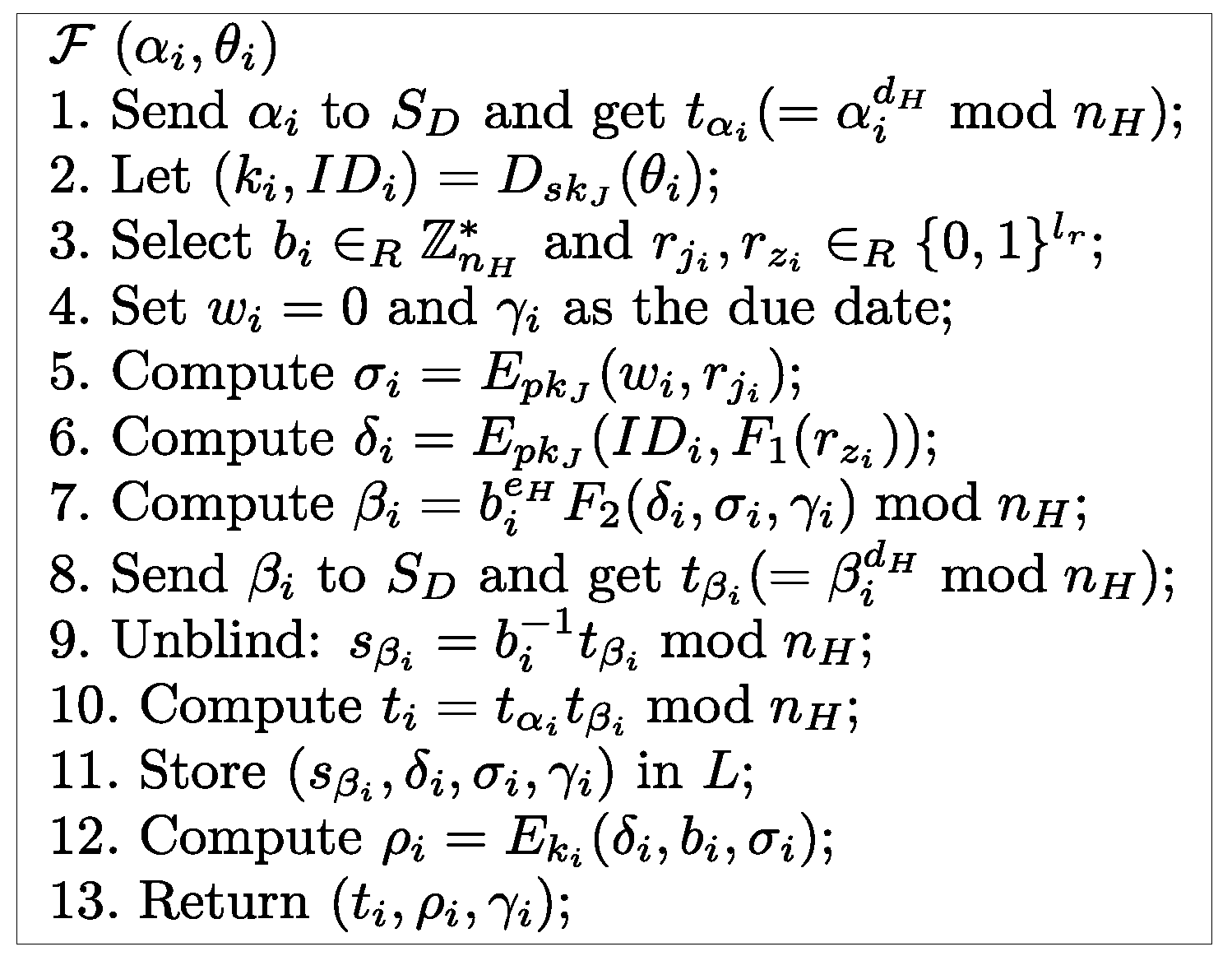
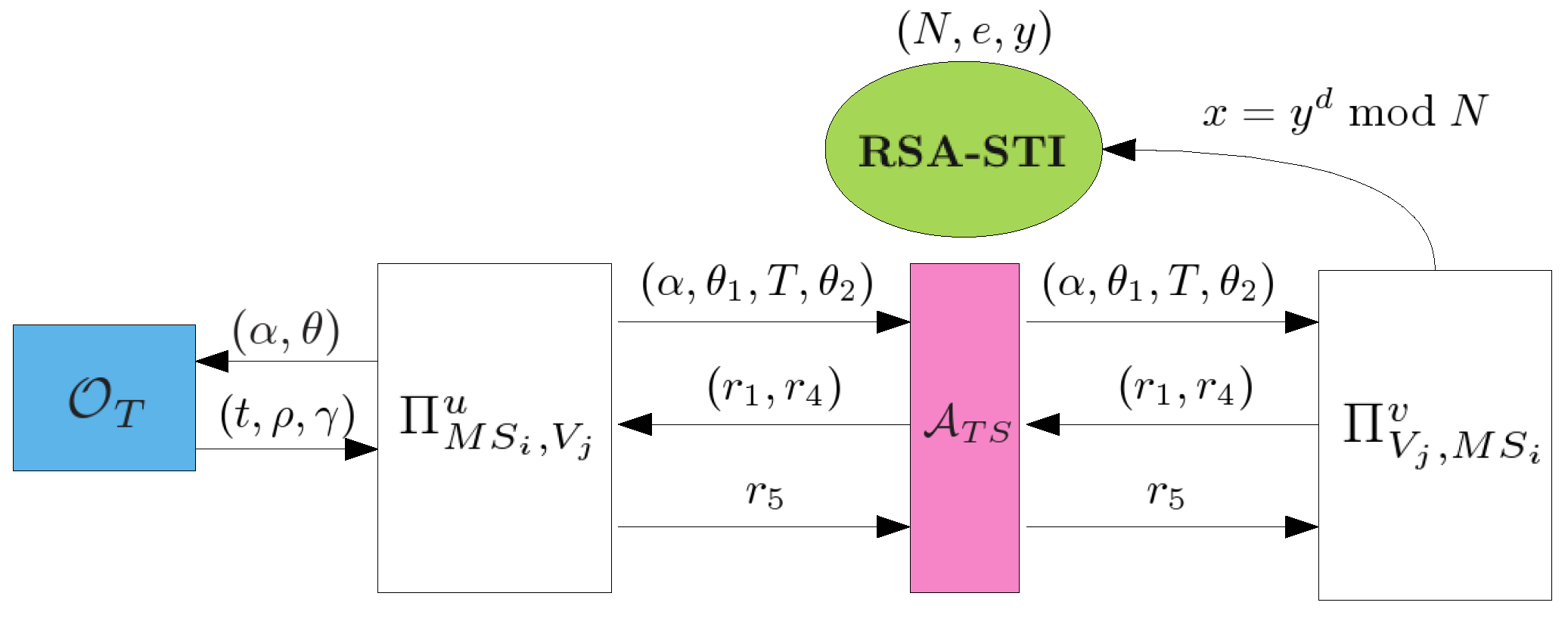
4.5. Ticket Swindling Resistance
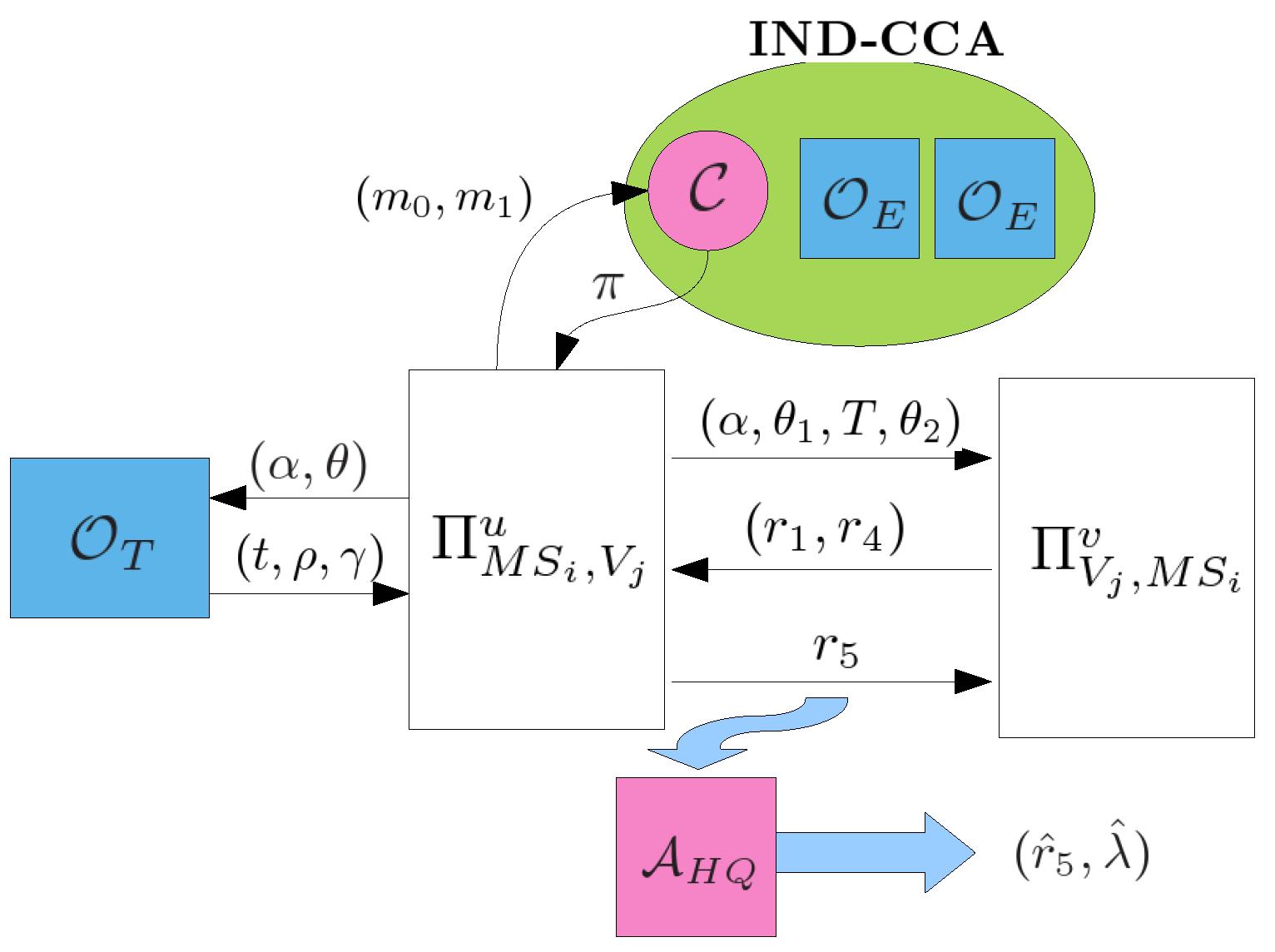
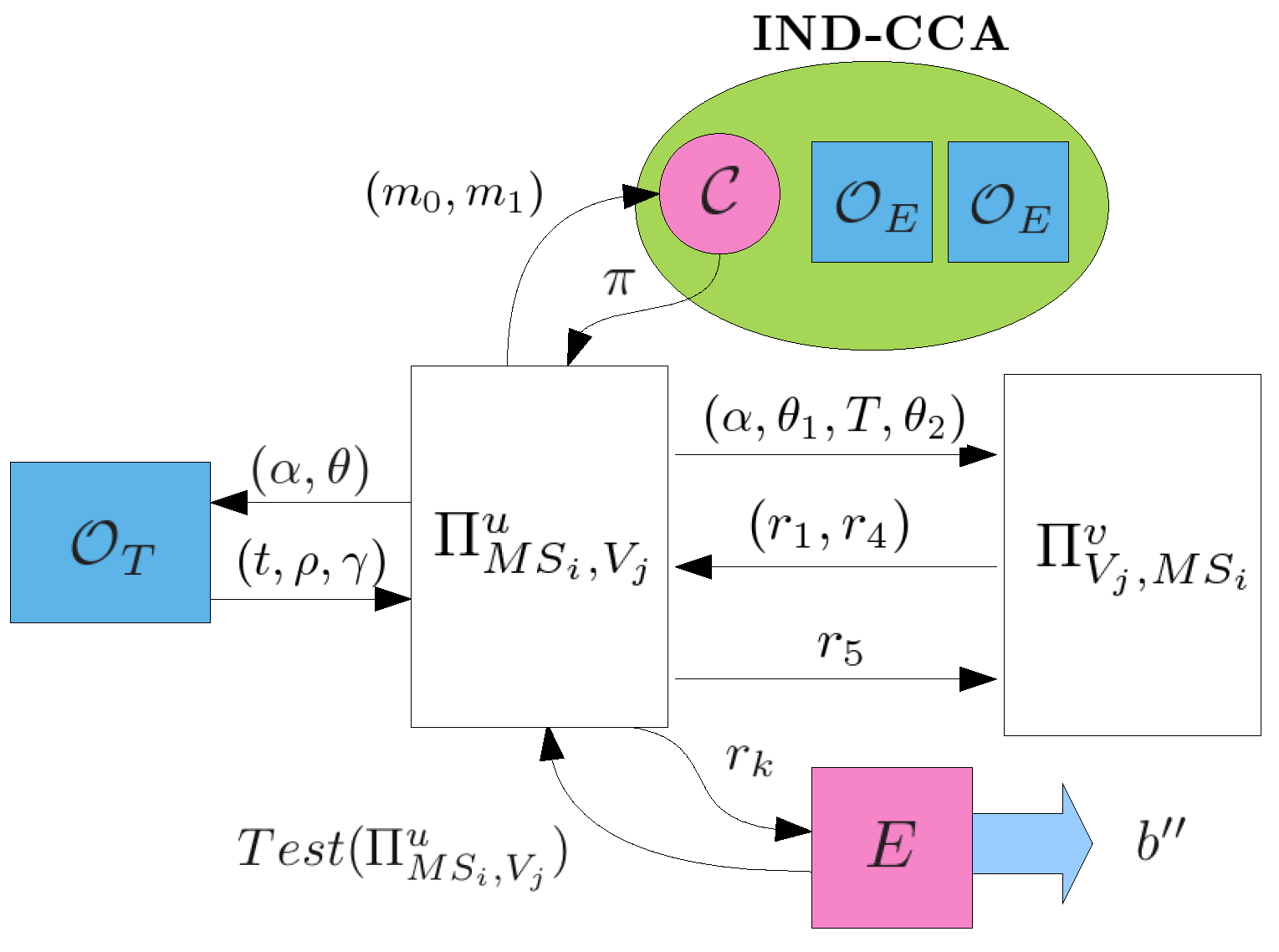
- , : This query models all kinds of passive attacks. and will carry out the protocol of Section 3.4 and the adversary E can eavesdrop all messages transmitted between and .
- , or , : This query models all kinds of active attacks. The adversary E can send any message to or which will give responses to E according to the protocol of Section 3.4. E can make the query , to get a response of the first flow where is an empty string.
- or : This query allows the adversary to get the session key of or after and have successfully finished mutual authentication and established a common session key.
- : This query allows the adversary to obtain the secret value m if T has been successfully consumed for authentication where , δ, σ, γ, .
- : This query reveals ’s long-term key .
4.6. Secure Mutual Authentication
- is a matching conversation to K if there exist such that K is prefixed byand is prefixed by
- K is a matching conversation to if there exist such that is prefixed byand K is prefixed by
- If and have matching conversations, then both oracles accept;
- The probability of No Matching is negligible.
- : Assume that , , , , . Thus, can obtain and forge a ticket . However, we have proved the security of ticket unforgeability in Section 4.3. Hence, the probability of that E is successful in this sub-case is negligible.
- : In the sub-case, E successfully swindles which is owned by . We have proved the security of ticket swindling resistance in Section 4.5. Consequently, the probability of that E is successful in this sub-case is also negligible.
4.7. Secure Authenticated Key Exchange
- 1.
- P is a secure mutual authentication protocol;
- 2.
- Both oracles and always accept and hold the same session key if E is a benign adversary; and
- 3.
- For any adversary E, is negligible.
5. The Forward Secrecy Extension
5.1. The Security Proof for the Forward Secrecy Extension
6. Comparisons and Performance Evaluation
6.1. Comparisons
- Hiding identity: Mobile users hide their real identities from the system operator, H and V, and eavesdroppers.
- No relation: It is difficult for the system to derive the relation between any two rounds of the communication of the same mobile user.
- Secure channels: After performing mutual authentication between an anonymous mobile user and the system operator, they must establish a shared session key for the following communication activities.
- Fair privacy: Fair privacy contains traceability and revokeability. If a crime happens, the police can trace the identities of related anonymous mobile users or the judge can revoke their privacy.
- Credit-based chargeability: As mentioned in Section 3.5, the credit-based charging method is better than the debit-based one since the former (1) is the same as the practical situation in current GSM services; (2) can greatly reduce the relations between any two rounds of communication; and (3) is free from the problem of overspending.
6.2. Performance Evaluation
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix

References
- Fragkiadakis, A.G.; Askoxylakis, L.G.; Tragos, E.Z.; Verikoukis, C.V. Ubiquitous Robust Communications for Emergency Response Using Multi-operator Heterogeneous Networks. EURASIP J. Wirel. Commun. Netw. 2011, 13, 1–16. [Google Scholar] [CrossRef]
- Hwang, K.F.; Chang, C.C. A Self-encryption Mechanism for Authentication of Roaming and Teleconference Services. IEEE Trans. Wirel. Commun. 2003, 2, 400–407. [Google Scholar] [CrossRef]
- Samfat, D.; Molva, R.; Asokan, N. Untraceability in Mobile Networks. In Proceedings of the 1st Annual International Conference on Mobile Computing and Networking, Berkeley, CA, USA, 13–15 November 1995; pp. 26–36.
- Asokan, N. Anonymity in a Mobile Computing Environment. In Proceedings of the Workshop on Mobile Computing System and Applications, Santa Cruz, CA, USA, 8–9 December 1994; pp. 200–204.
- Ozturk, C.; Zhang, Y.; Trappe, W.; Ott, M. Source-location Privacy for Networks of Energy-constrained Sensors. In Proceedings of the Second IEEE Workshop on Software Technologies for Future Embedded and Ubiquitous Systems (WSTFEUS’04), Vienna, Austria, 11–12 May 2004; pp. 68–72.
- Karygiannis, A.; Kiayias, A.; Tsiounis, Y. A Solution for Wireless Privacy and Payments Based on E-cash. In Proceedings of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks, Athens, Greece, 5–9 September 2005; pp. 206–218.
- He, Q.; Wu, D.; Khosla, P. The Quest for Personal Control over Mobile Location Privacy. IEEE Commun. Mag. 2004, 42, 130–136. [Google Scholar]
- Park, S.Y.; Han, M.S.; Eom, Y.I. An Efficient Authentication Protocol Supporting Privacy in Mobile Computing Environments. In Proceedings of the 5th IEEE International Conference on High Speed Networks and Multimedia Communications, Jeju Island, Korea, 3–5 July 2002; pp. 332–334.
- Zhu, J.; Ma, J. A New Authentication Scheme with Anonymity for Wireless Environments. IEEE Trans. Consum. Electron. 2004, 50, 231–235. [Google Scholar]
- Kesdogan, D.; Fouletier, X. Secure Location Information Management in Cellular Radio Systems. In Proceedings of the IEEE Wireless Communication System Symposium, Smithtown, NY, USA, 27–28 November 1995; pp. 35–40.
- Lin, W.D.; Jan, J.K. A Wireless-based Authentication and Anonymous Channels for Large Scale Area. In Proceedings of the Sixth IEEE Symposium on Computers and Communications, Hammamet, Tunisia, 3–5 July 2001; pp. 36–41.
- Tracz, R.; Wrona, K. Fair Electronic Cash Withdrawal and Change Return for Wireless Networks. In Proceedings of the 1st International Workshop on Mobile Commerce, Rome, Italy, 21 July 2001; pp. 14–19.
- Chaum, D. Blind Signature Systems. In Advance in Cryptology—CRYPTO ’83; Springer: Berlin/Heidelberg, Germany, 1984; p. 153. [Google Scholar]
- Fan, C.-I.; Huang, V.-S. Anonymous Authentication Protocols with Credit-Based Chargeability and Fair Privacy for Mobile Communications. In International Workshop on Security (IWSEC), LNCS 4752; Springer-Verlag: Berlin/Heidelberg, Germany, 2007; pp. 412–427. [Google Scholar]
- Canetti, R.; Halevi, S.; Katz, J. A Forward-secure Public-key Encryption Scheme. J. Cryptol. 2007, 20, 265–294. [Google Scholar] [CrossRef]
- Pearson, S. Trusted Computing Platforms, the Next Security Solution; Technical Report HPL-2002-221; Hewllet-Packard Laboratories: Bristol, UK, 2002. [Google Scholar]
- Trusted Computing Group Website. Available online: http://www.trustedcomputinggroup.org/ (accessed on 17 January 2016).
- Bajikar, S. Trusted Plateform Module (TPM) Based Security on Notebook PCs-White Paper; Mobile Platform Group, Intel Corporation: Santa Clara, CA, USA, 2002; Volume 1, p. 1. [Google Scholar]
- Horowitz, E.; Sahni, S. Computing Partitions with Applications to the Knapsack Problem. J. ACM 1974, 21, 277–292. [Google Scholar] [CrossRef]
- Bellare, M.; Namprempre, C.; Pointcheval, D.; Semanko, M. The One-more-rsa-inversion Problems and the Security of Chaum’s Blind Signature Scheme. J. Cryptol. 2008, 16, 185–215. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Advances in Cryptology—CRYPTO’ 93; Springer: Berlin/Heidelberg, Germany, 1994; Volume 773, pp. 232–249. [Google Scholar]
- Blake-Wilson, S.; Menezes, A. Entity Authentication and Authenticated Key Transport Protocols Employing Asymmetric Techniques. In Security Protocols; Springer: Berlin/Heidelberg, Germany, 1998; pp. 137–158. [Google Scholar]
- Goldwasser, S.; Micali, S. Probabilistic Encryption. J. Comput. Syst. Sci. 1984, 28, 270–299. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M.E. New Directions in Cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Boneh, D. The Decision Diffie-Hellman Problem. In Proceedings of the Third Algorithmic Number Theory Symposium, Portland, OR, USA, 21–25 June 1998; Volume 1423, pp. 48–63.
- Mu, Y.; Varadharajan, V. A New Scheme of Credit Based Payment for Electronic Commerce. In Proceedings of the 23rd Annual Conference on Local Computer Networks, LowelI, MA, USA, 11–14 October 1998; pp. 278–284.
- Yang, C.C.; Tang, Y.L.; Wang, R.C.; Yang, H.W. A Secure and Efficient Authentication Protocol for Anonymous Channel in Wireless Communications. Appl. Math. Comput. 2005, 169, 1431–1439. [Google Scholar] [CrossRef]
- Yeh, K.H. An Anonymous and Lightweight Authentication Scheme for Mobile Devices. Inf. Technol. Control 2015, 44, 206–215. [Google Scholar] [CrossRef]
- Crypto++. Crypto++ Benchmarks. Available online: http://www.packetstormsecurity.org/crypt/LIBS/cryptolib/benchmarks.html (accessed on 15 March 2009).
- The GSM Phone Reviews Website. Available online: http://www.gsmar-ena.com/ (accessed on 22 May 2008).

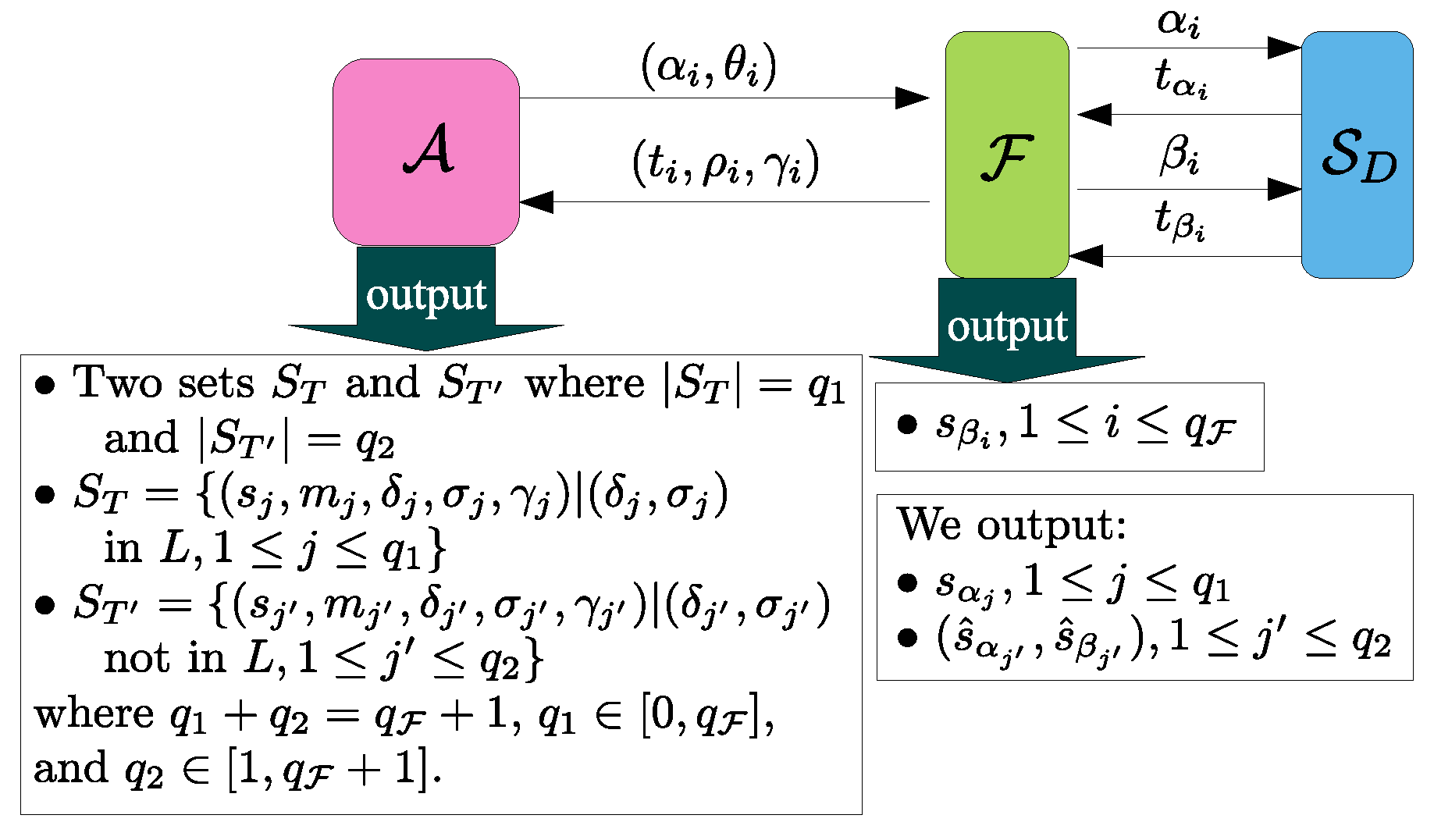
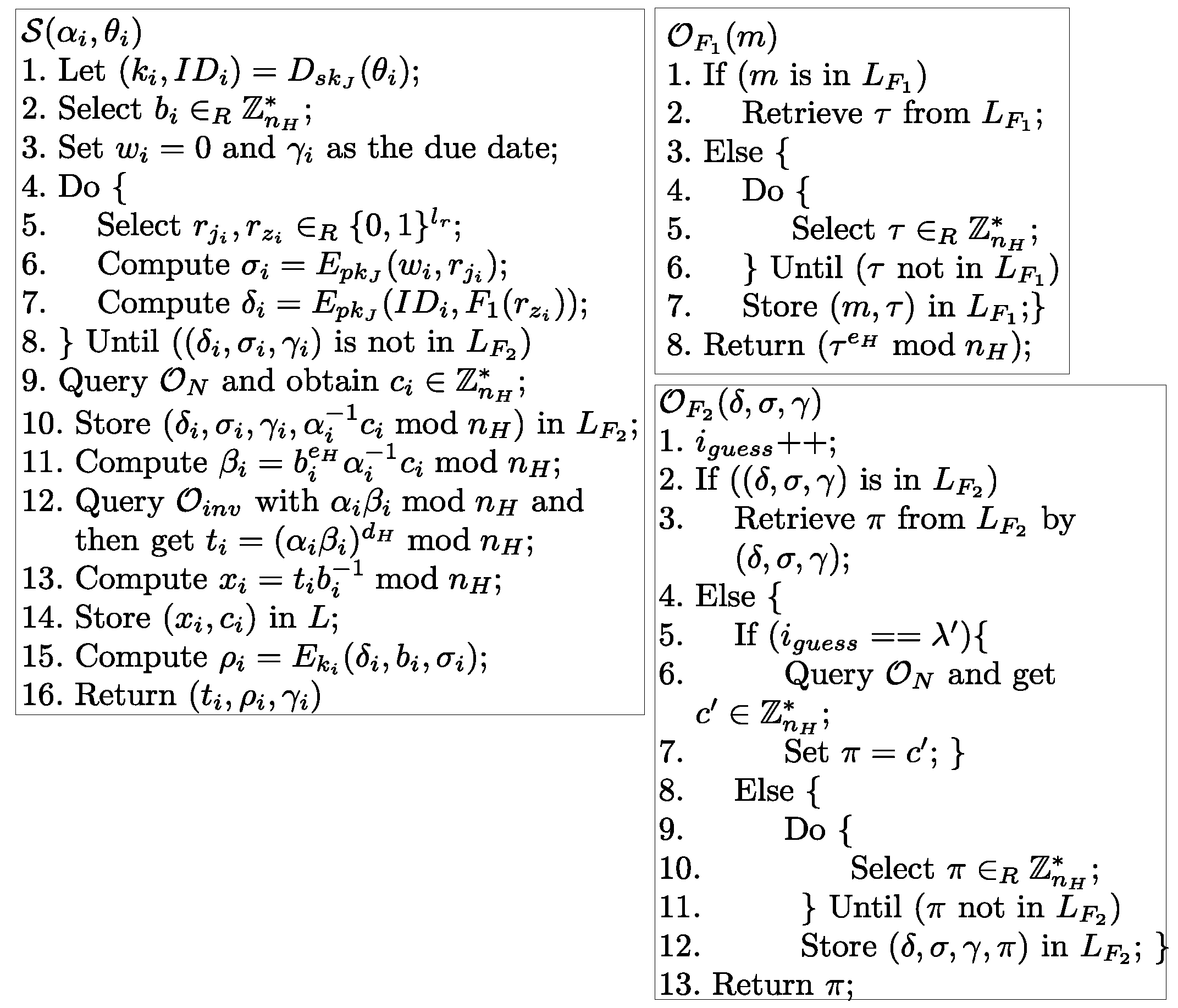





| Privacy | Property | |||||||
|---|---|---|---|---|---|---|---|---|
| Scheme | Hiding ID from: | Credit-Based | ||||||
| H | V | E | NoR | S | T | R | Chargeability | |
| Ours | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ | ◯ |
| [6] | ◯ | ◯ | ◯ | × | ◯ | △ | △ | × |
| [7] | ◯ | ◯ | ◯ | × | × | × | × | × |
| [8] | × | ◯ | ◯ | ◯ | ◯ | × | × | × |
| [9] | × | × | ◯ | ◯ | ◯ | × | × | × |
| [10] | × | ◯ | ◯ | × | ◯ | × | × | ◯ |
| [11] | ◯ | ◯ | ◯ | ◯ | × | × | × | × |
| [12] | ◯ | ◯ | ◯ | × | × | × | × | × |
| [26] | × | ◯ | ◯ | × | × | × | × | × |
| [27] | × | ◯ | ◯ | × | ◯ | × | × | × |
| [28] | × | ◯ | ◯ | × | ◯ | ◯ | ◯ | × |
| Operation | Mobile User () | The System (V+H) |
|---|---|---|
| Requesting a ticket | 4E | 6E |
| Using a ticket | 3E | 2E |
| Termination | 3E | 8E |
| CPU: Intel Celleron 450 MHz, OS: Windows 2000 | |||
|---|---|---|---|
| RSA Operation | Iterations | Total Time | Milliseconds/Operation |
| 1024 Encryption | 41,051 | 30 s | 0.73 |
| 1024 Decryption | 1,084 | 30 s | 27 |
| 2048 Encryption | 13,912 | 30 s | 2 |
| 2048 Decryption | 164 | 30 s | 183 |
| 1024 Signature | 1,086 | 30 s | 27 |
| 1024 Verification | 43,061 | 30 s | 0.69 |
| 2048 Signature | 165 | 30 s | 181 |
| 2048 Verification | 14,187 | 30 s | 2 |
| Mobile Device | CPU | Memory | Execution Time |
|---|---|---|---|
| Mac iphone 3G | Samsung S5L8900 620 MHz | 128 MB | |
| HTC magic | Qualcomm MSM 7201A 528 MHz | 192 MB | E: 3 ms, D: 21 ms |
| Noika N95 | Dual ARM 11 332 MHz | 128 MB | |
| Sony Ericsson X1 | Qualcomm MSM 7200 528 MHz | 256 MB |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, C.-I.; Huang, V.S.-M. Formal Security-Proved Mobile Anonymous Authentication Protocols with Credit-Based Chargeability and Controllable Privacy. Appl. Sci. 2016, 6, 176. https://doi.org/10.3390/app6060176
Fan C-I, Huang VS-M. Formal Security-Proved Mobile Anonymous Authentication Protocols with Credit-Based Chargeability and Controllable Privacy. Applied Sciences. 2016; 6(6):176. https://doi.org/10.3390/app6060176
Chicago/Turabian StyleFan, Chun-I, and Vincent Shi-Ming Huang. 2016. "Formal Security-Proved Mobile Anonymous Authentication Protocols with Credit-Based Chargeability and Controllable Privacy" Applied Sciences 6, no. 6: 176. https://doi.org/10.3390/app6060176