Architecture and Design for Virtual Conferences: A Case Study
Abstract
: This paper presents a case study of the design issues facing a large multi-format virtual conference. The conference took place twice in two different years, each time using an avatar-based 3D world with spatialized audio including keynote, poster and social sessions. Between year 1 and 2, major adjustments were made to the architecture and design of the space, leading to improvement in the nature of interaction between the participants. While virtual meetings will likely never supplant the effectiveness of face-to-face meetings, this paper seeks to outline a few design principles learned from this experience, which can be applied generally to make computer mediated collaboration more effective.1. Introduction
In response to the economic downturn in 2008, IBM challenged its employees to find an alternative to face-to-face meetings. While the response from the employees was understandably ambivalent, effort was made to enable a “replacement” to the annual Academy General Meeting (AGM) event which included approximately 500 attendees each year. The conference, previously held face-to-face, was held online in an avatar-based virtual world in the fall of 2008 and 2009. This paper focuses on the architecture and design decisions that went into the layout and construction of the conference space. For more information on the event itself and its effectiveness, please see Erickson et al.: Synchronous Interaction among Hundreds: An Evaluation of a Conference in an Avatar-based Virtual Environment published in the proceedings of CHI 2011 [1].
2. The First Conference: Fall 2008
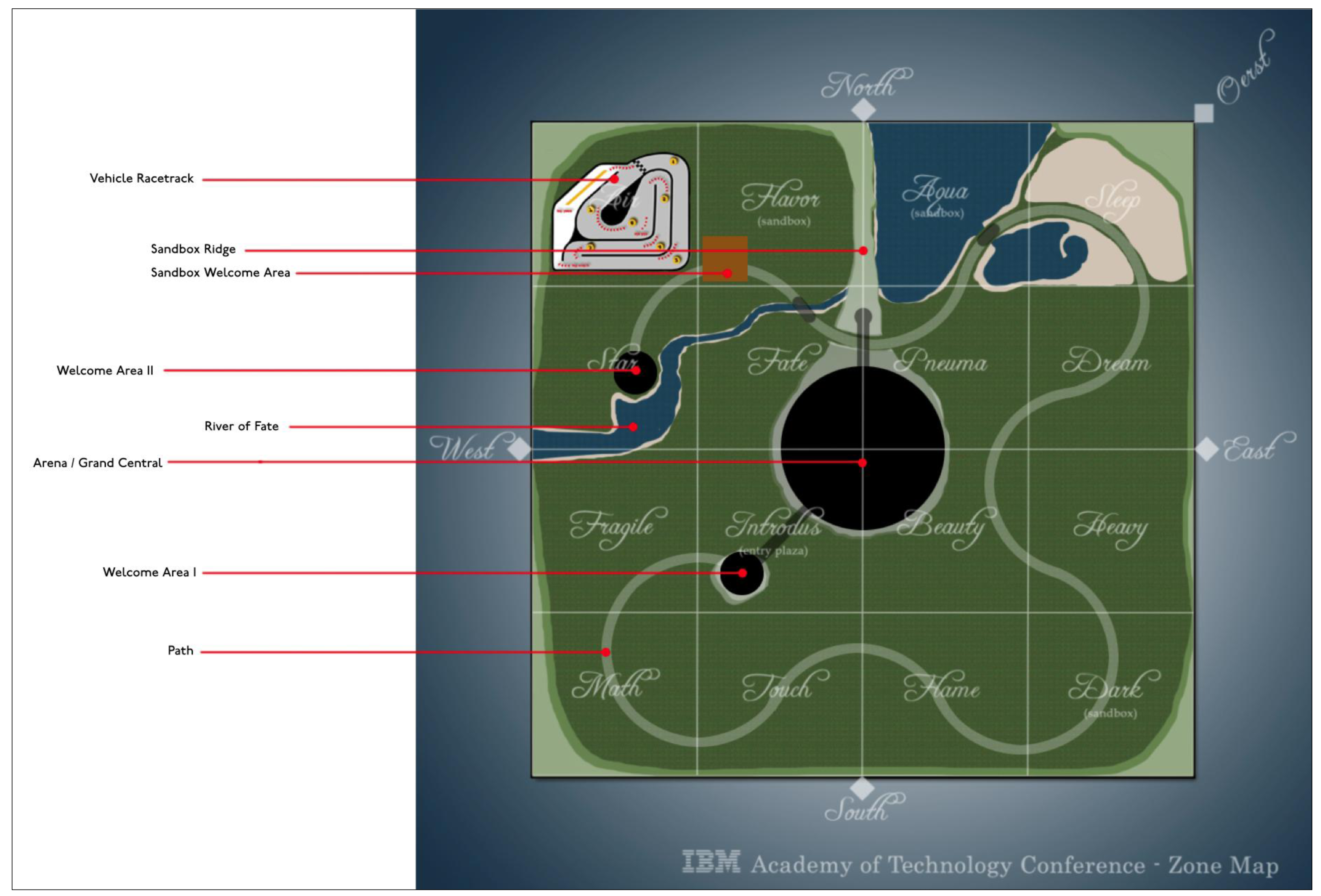
The first AGM virtual conference was held in the fall of 2008. By special arrangement with Linden Lab, the parent company of Second Life (SL), the conference was held in a special “shard” of SL. While avatars could travel freely between the publicly accessible Second Life servers and the AGM servers, the machines for the conference were physically located on IBM property and connected via the IBM network. As a result, individuals not securely connected to the IBM network found the conference servers unreachable. In this way, the conference was held “behind the firewall,” an action considered necessary in order to allow for confidential internal conversations. This conference was certainly not the first time an organization had attempted to conduct a business meeting in virtual worlds [2–4], nor was it the first time that IBM explored the use avatars in a meeting context [5,6], however it did represent the first large-scale use of avatar-mediated interaction in Second Life for IBM business.
2.1. Identification: To Whom Am I Speaking?
By placing the servers behind a firewall, attendees could be reasonably certain that anyone they encountered was an IBM employee, meeting the minimum requirements for confidential exchange. However, the exact identity of the individual remained in question. The registration system for Second Life at the time forced users to select a “last name” from a predefined set of names. In addition, the system provided no facility for displaying “real names,” insuring that everyone attending the event did so under a pseudonym.
In addition, while the interconnection between the public Second Life “grid” and the conference space provided an extremely powerful way of maintaining social ties before and after the conference, it created another identity-related problem: a high level of avatar customizability. Customizability allows a user to create (painstakingly) a replica of their real-life body, facilitating the type of easy recognizance that makes face-to-face meetings ideal. However this same customizability enables users to create bodies that not only do not resemble their real-life self, but might not even resemble their genders or even species. If trust is key to business and one uses personal recognition as a first-order of trust, this lack of easy identification presents a severe obstacle.
How to Solve the Identity Problem
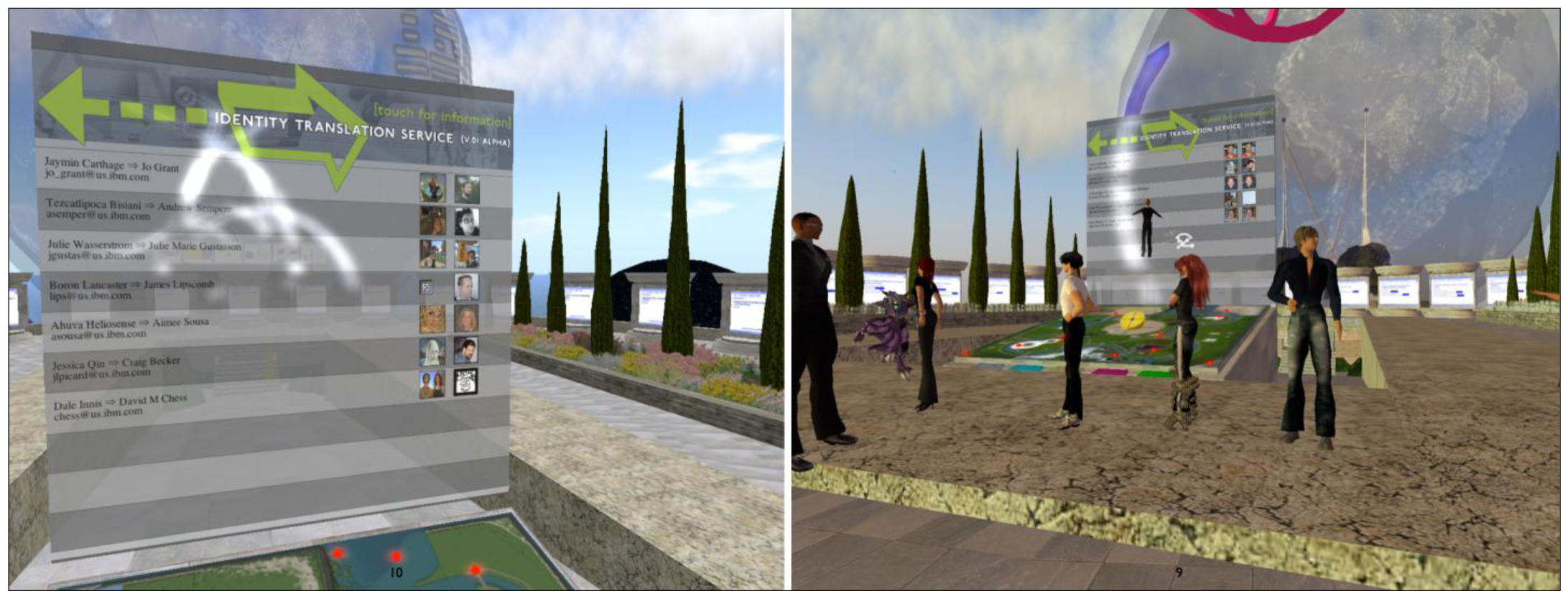
Changes to the underlying platform were not possible. Various proposals were therefore made in order to cope with the identity “translation” issue, but all required the installation of special software or an independent lookup action on behalf of the user. In an effort to ameliorate this, an automatic identity translation “big board” was created. This board was a shared artifact in virtual space that constantly and automatically updated the virtual and personal credentials of avatars occupying a given space (Figure 1). Information displayed included an avatar headshot from the Second Life system paired with one from the IBM internal employee database (called Blue Pages) resulting in an easy connection between avatar and individual. In addition, this board provided a basic secondary security function: in a mixed-server environment (i.e., on a virtual server not behind the corporate firewall) the identity service is unable to resolve the identity of the avatar in question. This inability to resolve is manifest in a clear error message on the board, conveying at a glance which avatars belong to IBM employees and which do not. This allows people to interact online in a “mixed” environment while remaining passively aware of when it is and is not appropriate to discuss internal business.
2.3. Conversation Scope: How Can I Chat with My Colleague Privately?
Assuming that participants managed to find their way around the conference and successfully identify the people they wanted to speak with, there was always the question of conversation scope. By default, conversation (typewritten and spoken “voice chat”) is scoped globally with a general notion of “falloff.” Thus avatars within a 20 meter radius of your avatar will, by default, hear every word of your conversation, and avatars past this point will hear nothing (various techniques were used to overcome this limitation for large events, such as keynotes, but this is the default behavior for regular conversation).
In practice this works much the same way that the real world works: One must make an effort to find a quiet space, close the office door or move to another to avoid being overheard or simply to avoid the noise of a crowd. In virtual spaces, however, the ability to monitor and trust that a channel is “secure” is a much more difficult proposition. At the same time, there is much research that suggests that the “hallway effect” of conferences is the primary utility of face to face meetings. While keynotes and organized events are useful, catching up with colleagues is even more so.
To be fair the Second Life platform does allow “person to person” calls and private chats, but the user interface is overly complicated. At this event many users resorted to traditional phone calls or, worse, avoided this kind of interaction entirely, treating the virtual environment as a very expensive and awkward slide-sharing tool for one-way presentations.
3. The Second Conference: Fall 2009
In 2009 the AGM again held a virtual conference with several major changes. First, the servers used were disconnected entirely from the main public Second Life product. This had the effect of not only guaranteeing that the content of the event was secure but also allowed the AGM to use real, authenticated names for login. As a result, avatars were no longer anonymous, largely eliminating the first-order problem with respect to identity.
However, the choice to cut off these servers from the main Second Life product made the already difficult task of avatar customization even more challenging. Not only could users not re-use the avatars they had created in the past, but they were no longer able to access the vast library of user-created content supplied by the Second Life community. As a result, while the intention was to make avatars more easily identifiable, they were visually LESS recognizable visually by virtue of the fact that opportunity cost for customization was simply too high. Most users chose to use unmodified, default avatars.
While beyond the scope of this paper, it is interesting to note that users also devised various techniques to overcome the identification problem without the opportunity costs associated with avatar customization, including attaching a photographic “mask” to their avatar's head in order to inform people who they were talking to (Figure 3).
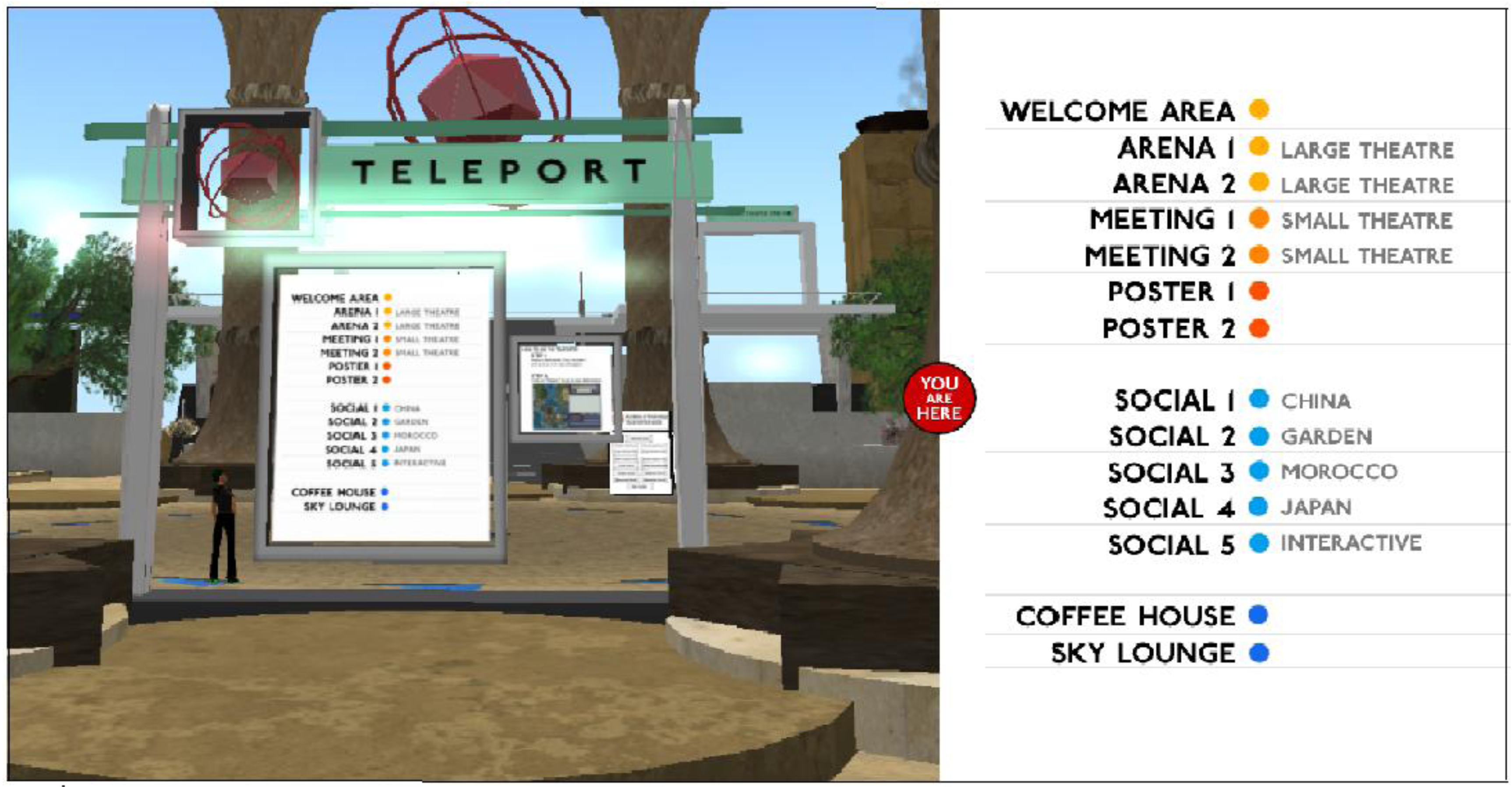
In order to alleviate this problem, a streamlined “personal” version of the earlier identity translation system was recommended. This tool also enabled users to “friend” each other and track who they had “met” for later follow-up. The AGM opted not to implement this, but the design can be seen in Figure 4.
3.2. Ability to Have Smaller Localized Conversations
IBM, like many large corporations, is a distributed organization. Telephone interactions are a familiar and comfortable model, and many of the conference attendees wanted to take advantage of the “voice chat” capabilities of the virtual environment.
The scoping problem, outlined above, meant that it was often difficult for attendees to know to whom they were speaking, and even harder to know who might be listening.
In an effort to facilitate more “hallway” interactions as well as support more informal conversations among attendees, careful attention was paid to the layout of the voice chat areas, in particular with respect to the design of the “poster hall,” deemed one of the most successful areas used in the 2009 conference (Figure 7).
Echoing the linear design principle for the conference itself, the poster hall consists of two wings connected by a central agora. Each wing contains 40 poster presentation areas tiered in stacked rows of 20, for a total of 80 presentation spaces.
The SL platform allowed for multiple independent audio channels to be created, in “squares” of 1 meter minimum. Working with this, the audio space was isolated in such a way that each poster area comprised its own “channel.” This fact was visually reinforced by designing the poster presentation areas as “bays.” The baked-texture “light pool” on the ground indicates the chat area, and the “sidewalk” indicates a transition zone. Moving sideways between zones requires that the avatar either “climb over” a wall or transition into the contiguous hallway that connects the bays.
In practice the interaction is natural: Users are able to stand together, scoping their voice conversations with the poster in question and then move fairly freely into the “hallway” to continue a more public conversation. Empty poster bays are available for private chats, allowing users to initiate more interpersonal conversations without worrying who they were talking over or who might overhear.
4. Conclusions
From what we know about the value of conferences, much is gained by casual social encounters and “backchannel” conversations that occur outside of the main event. Virtual worlds force users to re-negotiate these channels in an unfamiliar and sometimes confusing way.
Given the state-of-the-art, it is unlikely that virtual conference systems will ever be able to replicate the nuances of face-to-face communication in a way that is deeply satisfying. However, through careful design of virtual spaces we can make the experience qualitatively better and ultimately more effective. In the case of the IBM experience, three major design issues were found that are worth addressing:
Identification: To whom am I speaking?
Navigation: How do I get around?
Conversation Scope: How can I chat with my colleague privately?
Solving broadly for these three issues provides a solid “base environment” in which to hold a virtual conference. These design principles also apply well to collaboration software in general.
Identification is of critical importance in all human relationships. In particular, in a business environment the ability to ensure the identity of your interlocutor and to trust this information is of paramount importance. Inconstancy in interface undermines the user's trust in a system and, by extension, the degree to which the user is able to build relationships. A strong identification system is not always required (some systems do better with anonymity), but the stance must be completely clear to the user in order to inspire trust.
The navigation solutions presented in this paper are largely unique to 3D environments, but navigation itself is not unique. Attention needs to be paid to the organization of information and functionality in a UI. Ideally designers should provide multiple paths to this information and functionality so that the user can choose the one they are most comfortable with.
Lastly, conversation scope, or audiencing, is of crucial importance to social software in general and specifically to meeting software: It is important always to allow the user control and feedback over who is being addressed and how. Not all systems need to provide all possible scopes, but the ones that they do support should be immediately and clearly visible. No system can completely prevent misunderstandings or deliberate abuse (i.e., eavesdropping or impersonation), but pains should be taken never to obfuscate scope so that at a minimum the user isn't confused about who they conversing with.



References
- Erickson, T.; Shami, N.S.; Kellogg, W.A.; Levine, D.W. Synchronous Interaction among Hundreds: An Evaluation of a Conference in an Avatar-based Virtual Environment. Proceedings of CHI2011 Advance Technical Conference Program, Vancouver, BC, Canada, 7–12 May 2011.
- Lucia, A.D.; Francese, R.; Passero, I.; Tortora, G. SLMeeting: Supporting collaborative work in Second Life. Proceedings of the Working Conference on Advanced Visual Interfaces, Napoli, Italy, 28–30 May 2008.
- Zhang, D.S.; Shrestha, P. Doing business in Second Life: E-commerce in 3D online environment. Int. J. Electron. Bus. 2010, 8, 148–169. [Google Scholar]
- Damer, B.; Gold, S.; de Bruin, J.; de Bruin, D. Conferences and Trade Shows in Inhabited Virtual Worlds: A Case Study of Avatars98 & 99. Lecture Notes Comput. Sci. 2000, 1834, 1–11. [Google Scholar]
- Rohall, S.; Cheng, L.T.; Patterson, J. Bluegrass: Lessons for Deploying Virtual Worlds within the Enterprise. Proceedings of Workshop on Virtual Worlds, Collaboration, and Workplace Productivity, San Diego, CA, USA, 9 November 2008.
- Shami, N.S.; Cheng, L.T.; Rohall, S.; Sempere, A.; Patterson, J. Avatars Meet Meetings: Design Issues in Integrating Avatars in Distributed Corporate Meetings. Proceedings of the Working Conference on Advanced Visual Interfaces, Sanibel Island, FL, USA, 7–10 November 2010.
© 2011 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Sempere, A. Architecture and Design for Virtual Conferences: A Case Study. Future Internet 2011, 3, 175-184. https://doi.org/10.3390/fi3030175
Sempere A. Architecture and Design for Virtual Conferences: A Case Study. Future Internet. 2011; 3(3):175-184. https://doi.org/10.3390/fi3030175
Chicago/Turabian StyleSempere, Andrew. 2011. "Architecture and Design for Virtual Conferences: A Case Study" Future Internet 3, no. 3: 175-184. https://doi.org/10.3390/fi3030175
APA StyleSempere, A. (2011). Architecture and Design for Virtual Conferences: A Case Study. Future Internet, 3(3), 175-184. https://doi.org/10.3390/fi3030175



