An Investigation into Healthcare-Data Patterns
Abstract
:1. Introduction
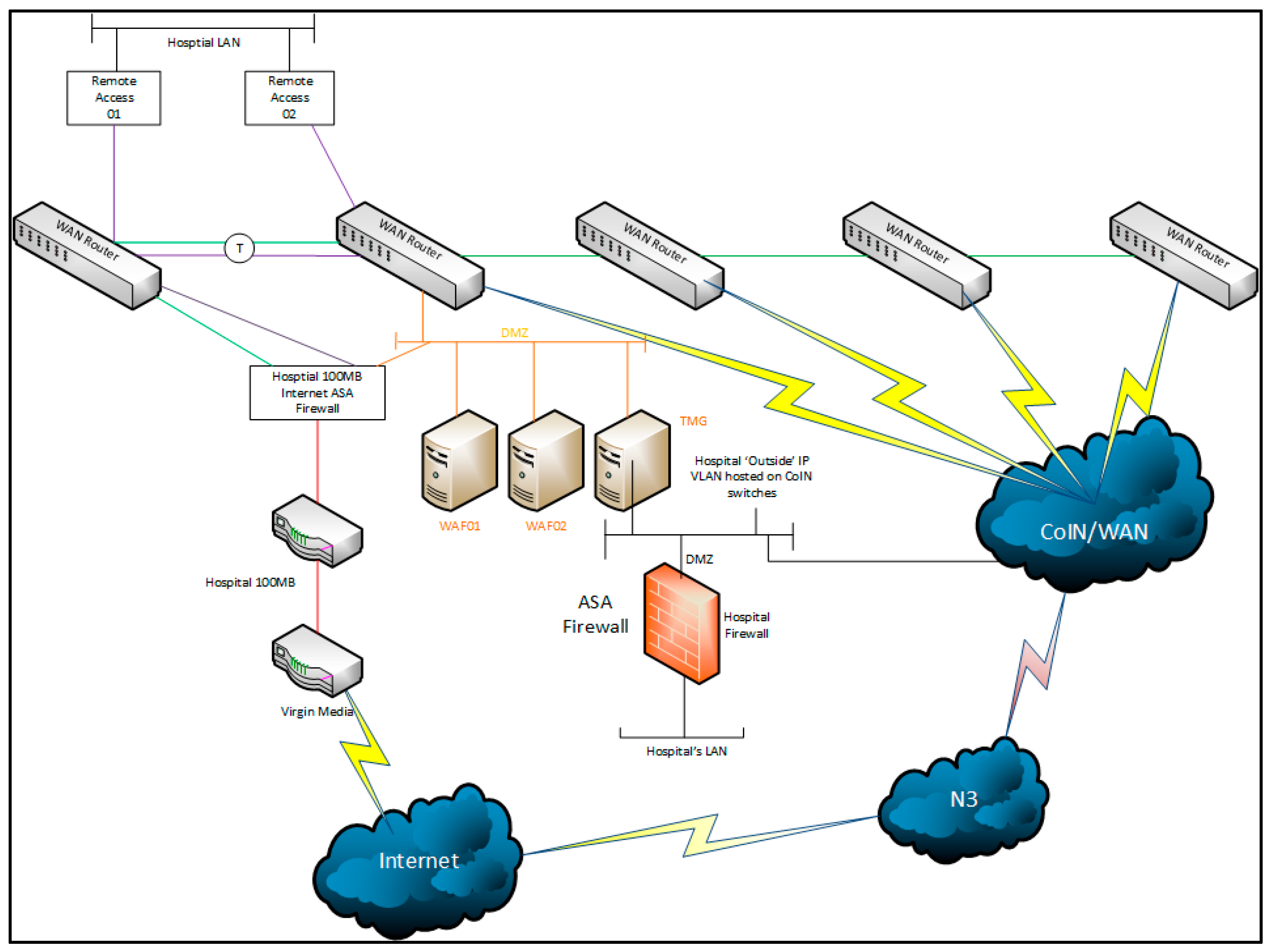
1.1. Motivating Scenario
1.2. Problem Statement and Contributions
1.3. Structure
2. Background Research
2.1. Structure
2.2. Security Challenges
2.3. Data
3. Investigation Methodology
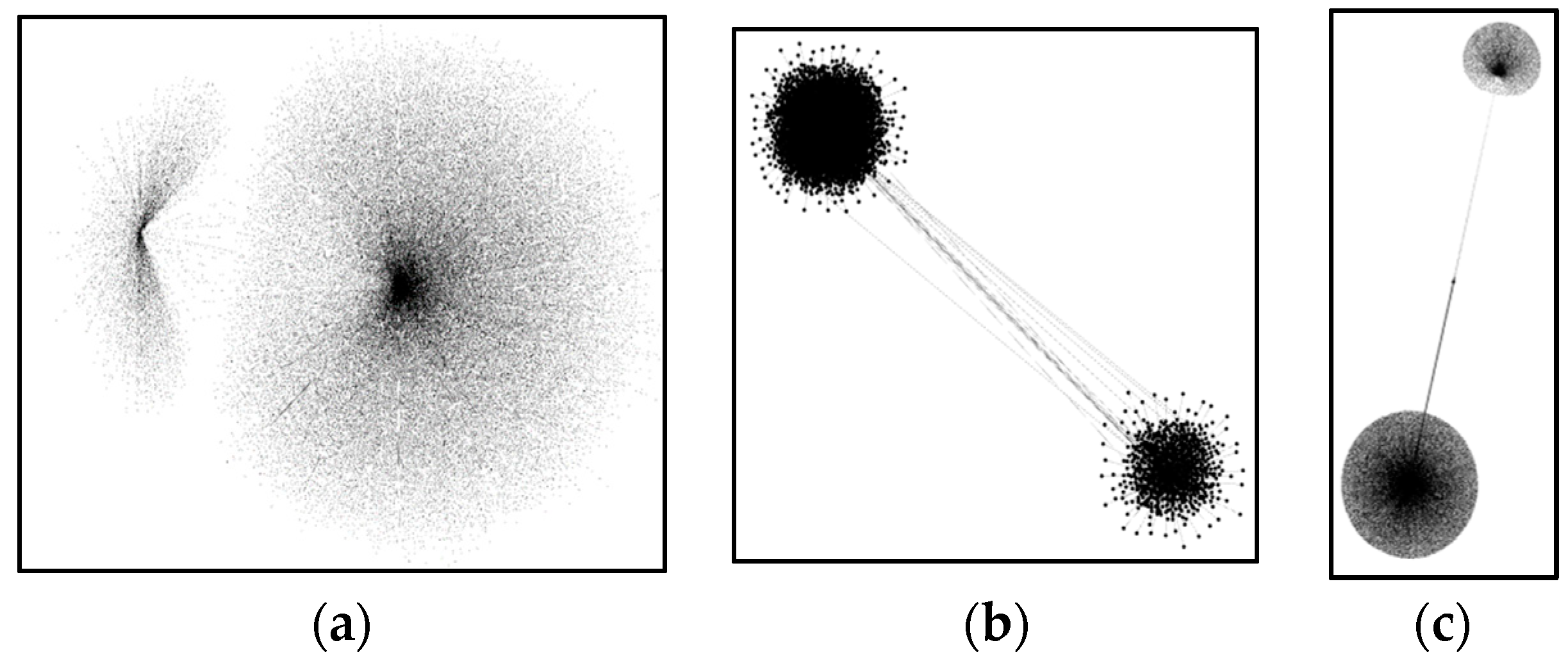
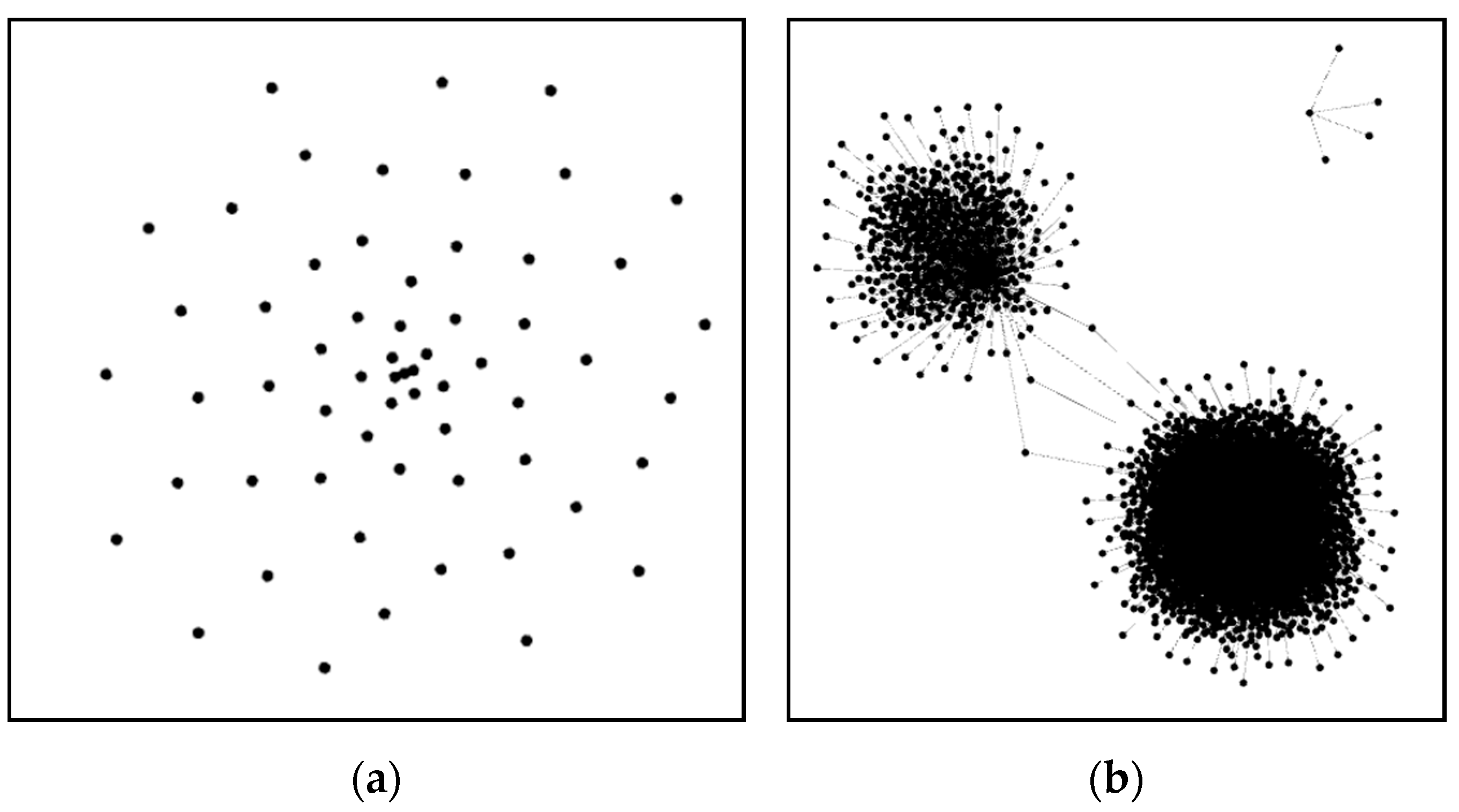
3.1. Force Directed Visualisation Algorithm
| Algorithm 1 Yifan Hu Multilevel algorithm |
| 1) Coarsest Graph Layout, which is as modelled as follows: |
| 2) The Coarsening Phase, calculated as outlined: |
| and 3) the Prolongation and Refinement Phase, where prolongation is employed to acquire initial layout: |
3.2. Logarithmic Heatmaps
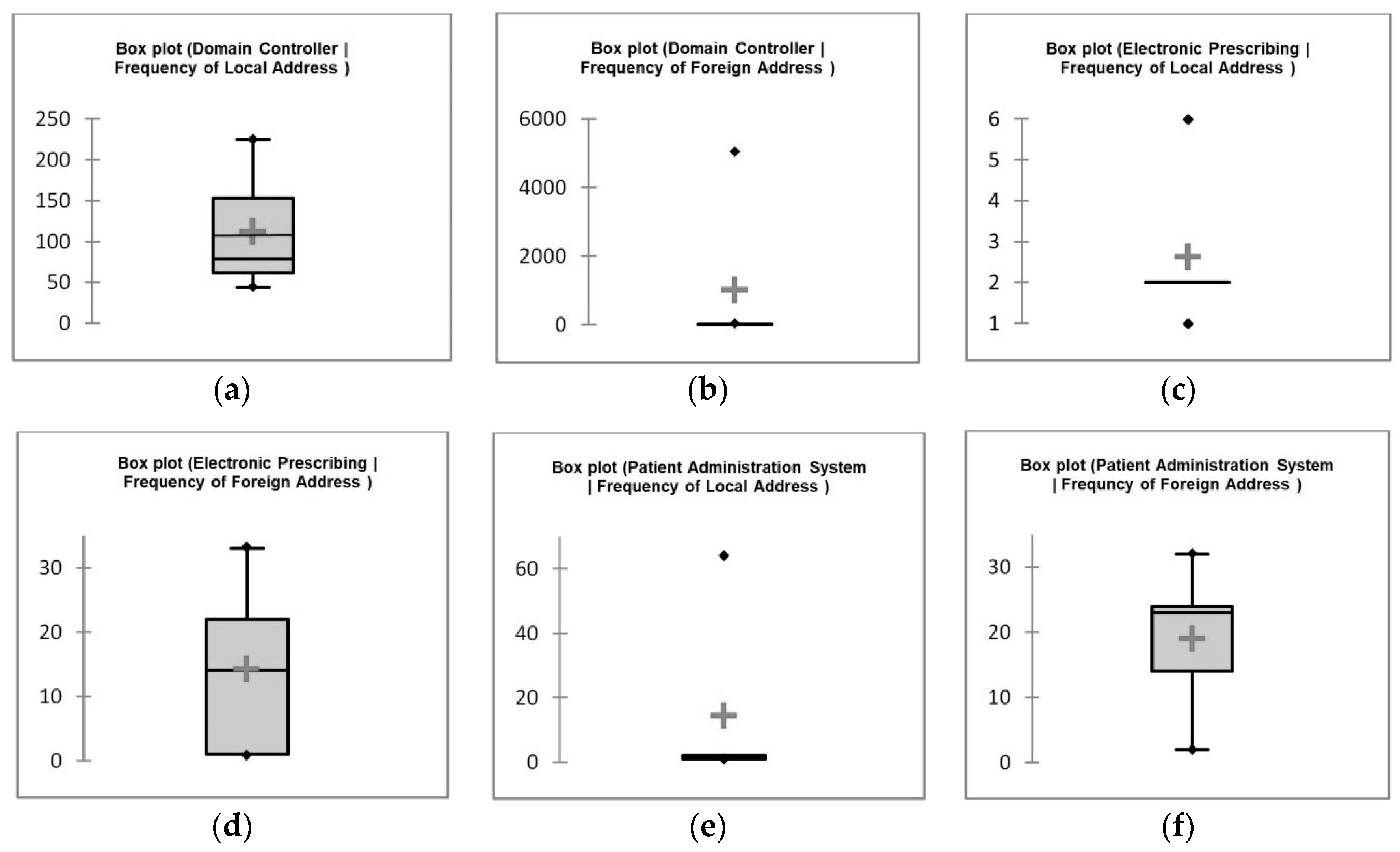
3.3. Nonparametric Statistical Graphics
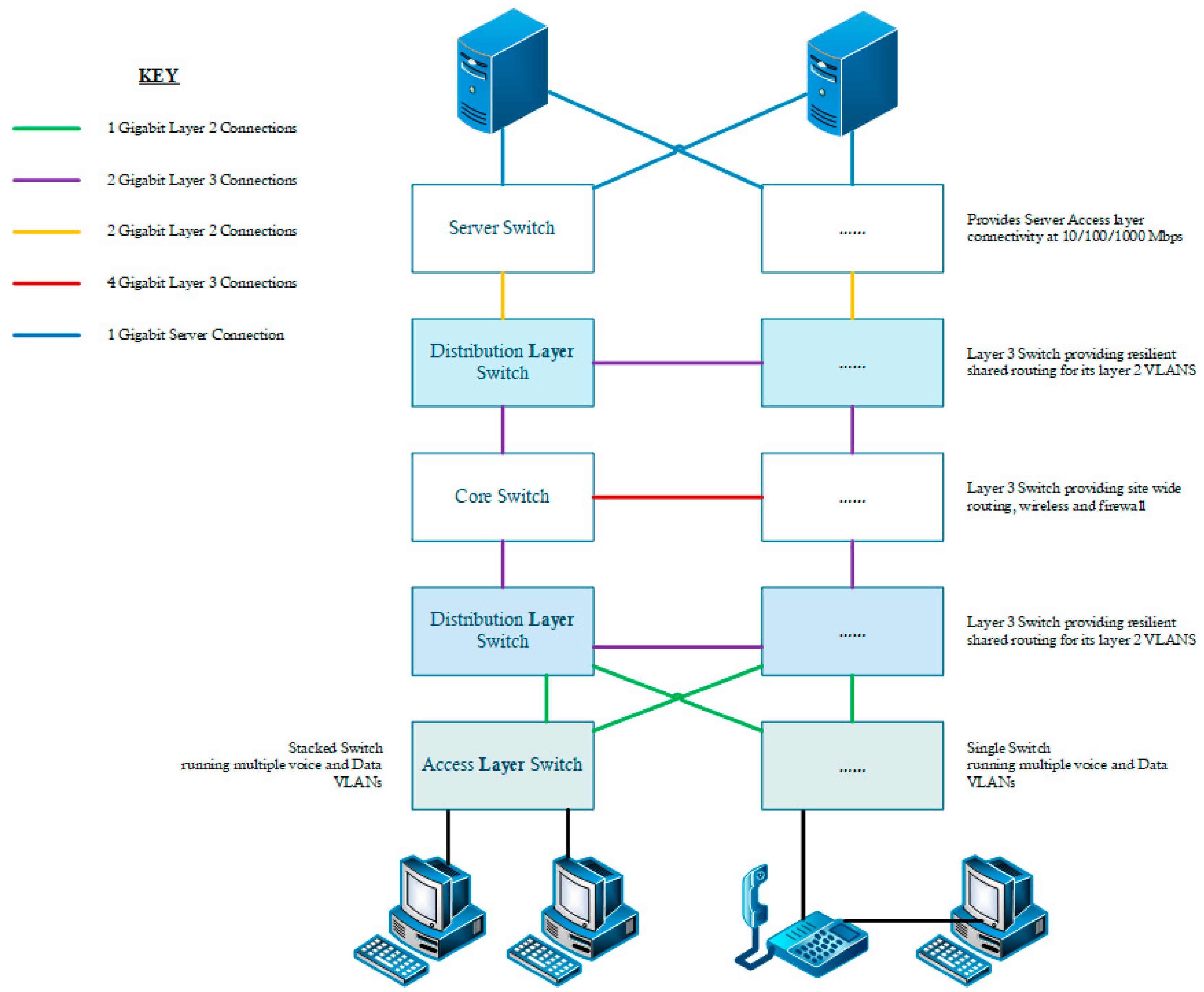
4. Visualisation Case Study
4.1. Force-Directed Layout Algorithms
4.2. Heatmaps
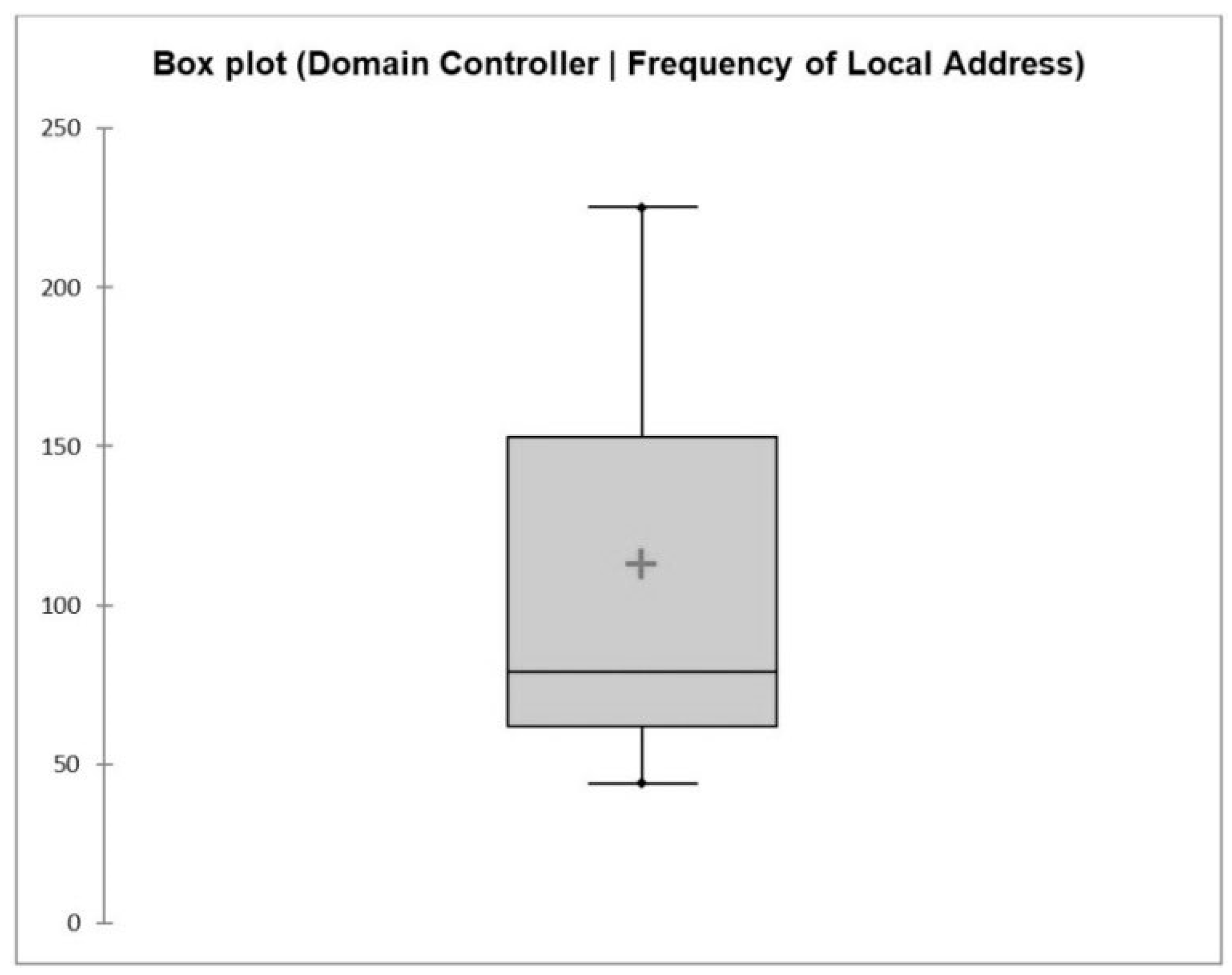
4.3. Boxplots
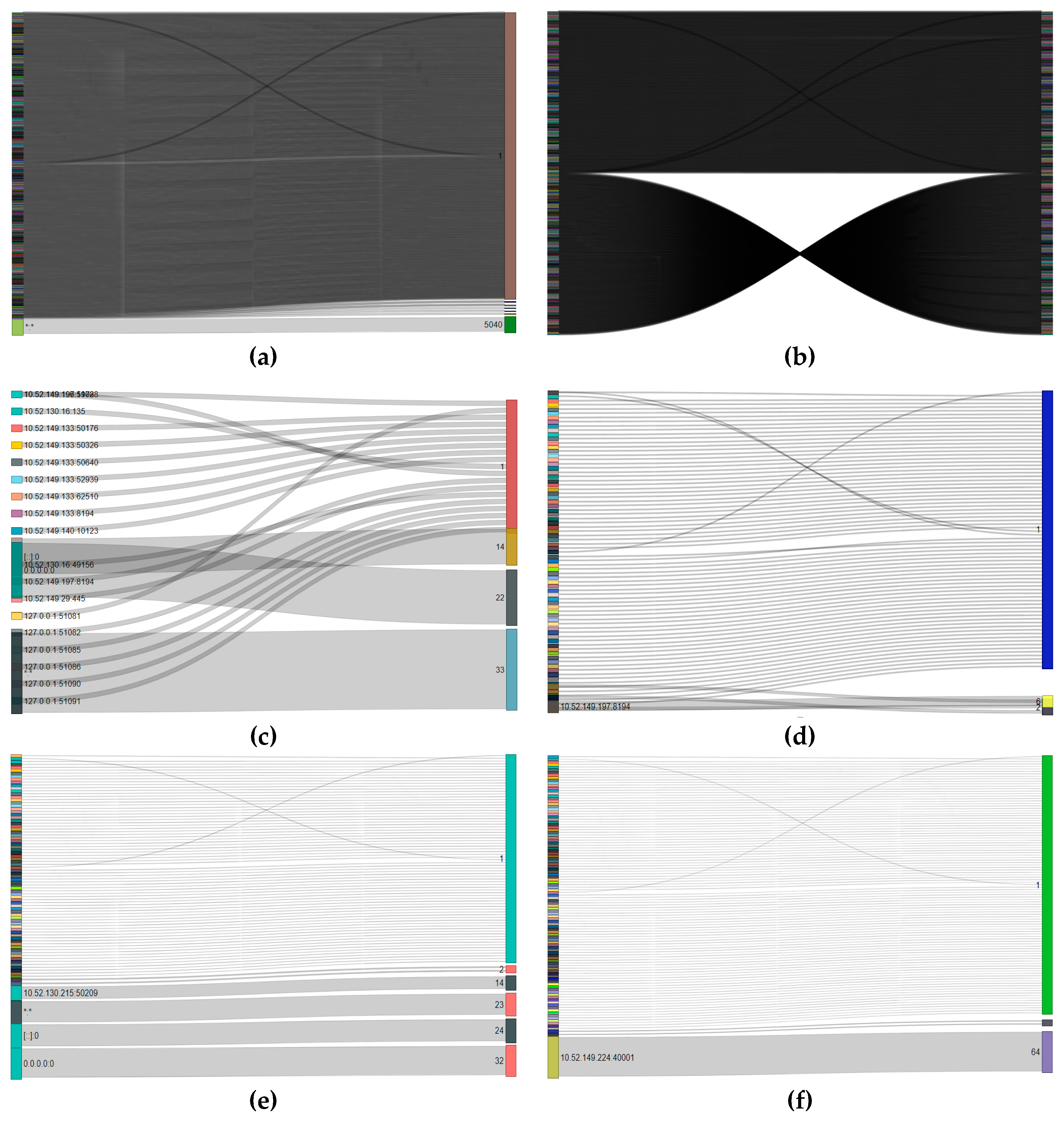
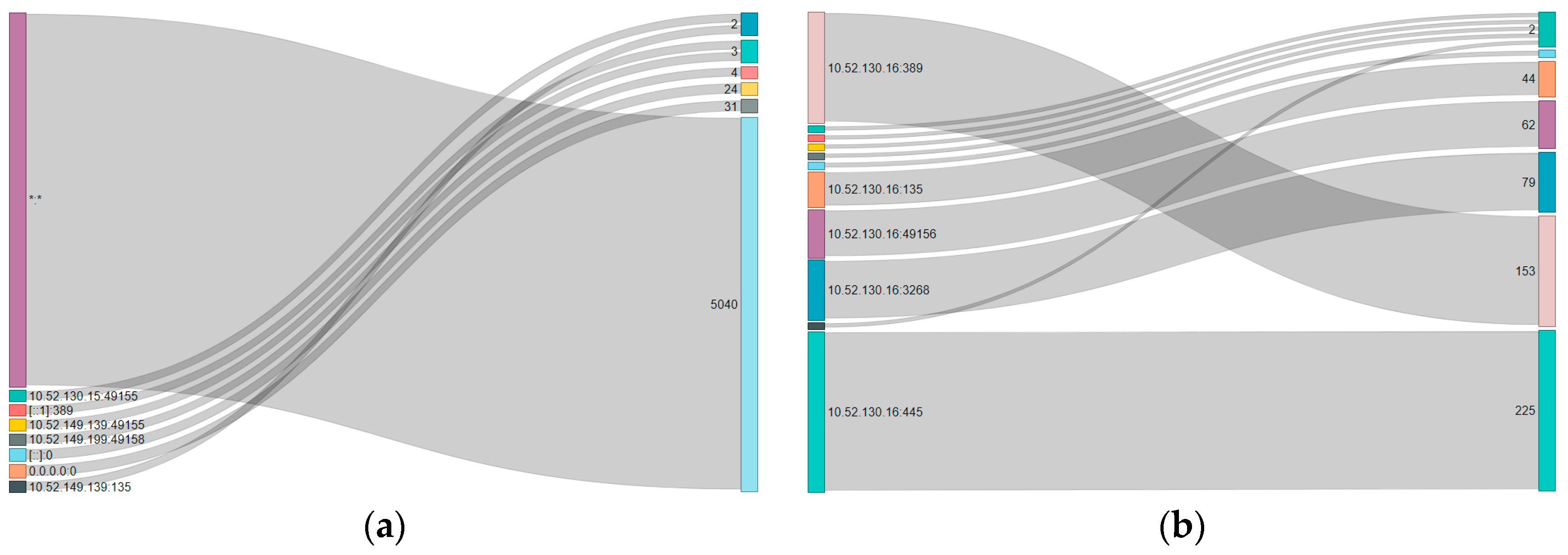
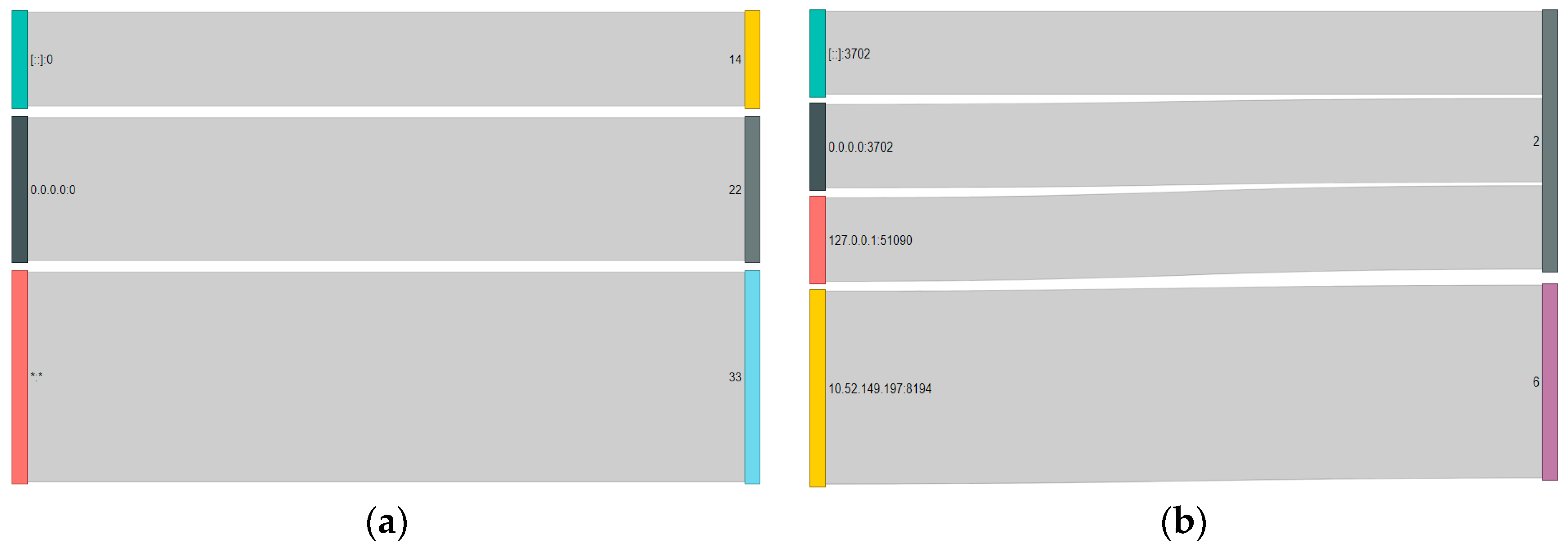
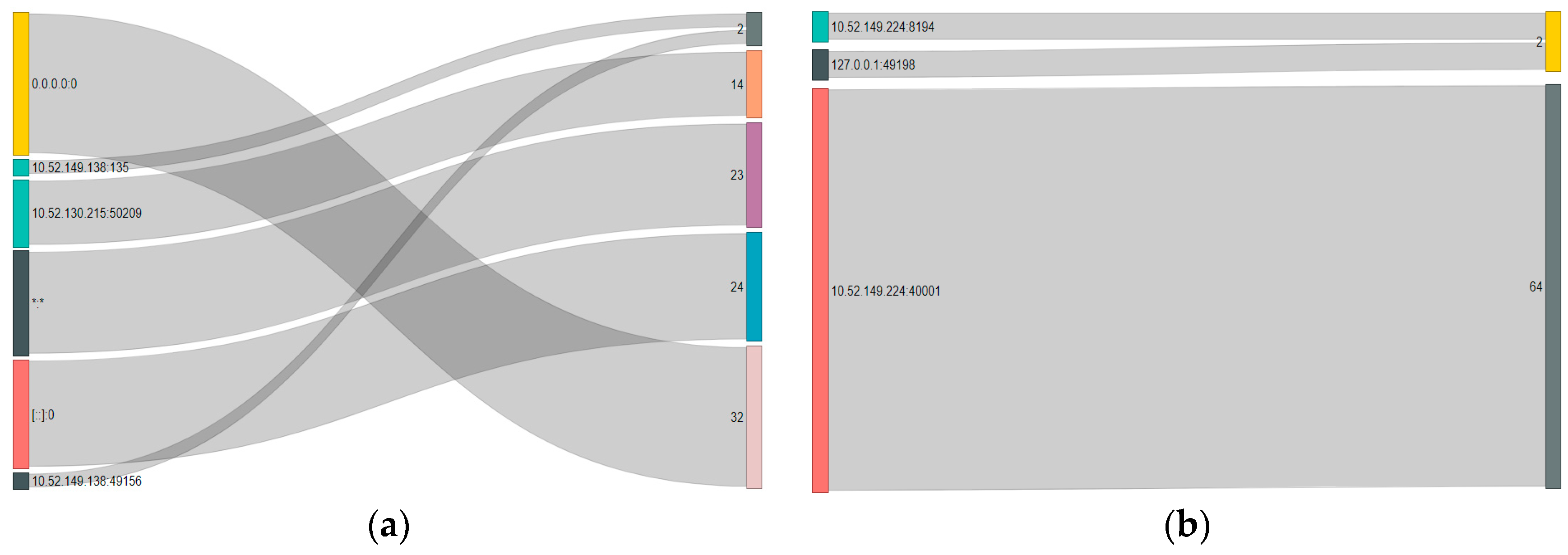
4.4. Sankey Diagrams
5. Discussion and Proposed Algorithm
5.1. Visualisations
- –n—This parameter displays the active TCP connections expressed numerically (in order to quantify the foreign address values for visualisation purposes).
- –a—This parameter displays all the active connections and TCP and UDP ports on which the server is listening.
- -–b—This parameter defines the binary (executable) program name involved in creating the connection or listening port.
5.2. Algorithm
| Algorithm 2 Algorithm Pseudocode: Data Filtering |
| Function: Remove Low-Risk Data Points |
| Input: Netstat–nab data for AD, EPMA and PAS |
| Output: Medium/High-Risk Data Points for each Data Type do Selection Control |
| if Data Type = AD/EPMA/PAS then Forward Data |
| else Temp Data Store end |
| Data Pre-Processing |
| if Data Type = AD/EPMA/PAS then Clean Data then Temp Data Store |
| else Temp Data Store Normalisation |
| end |
| Data Analysis for each Data Type Data Optimisation then Data Representation then Data Evaluation then end |
| Visualisation for each Data Type Data Interpretation then Data Consolidation then Visualise Data in User Interface end |
5.3. Results
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Fanucchi, R.Z.; Bessani, M.; Camillo, M.H.M.; London, J.B.A.; Maciel, C.D. Failure rate prediction under adverse weather conditions in an electric Distribution System using Negative Binomial Regression. In Proceedings of the International Conference on Harmonics and Quality of Power, ICHQP, Belo Horizonte, Brazil, 16–19 October 2016; pp. 478–483. [Google Scholar]
- Eusgeld, I.; Nan, C. Creating a simulation environment for critical infrastructure interdependencies study. In Proceedings of the 2009 IEEE International Conference on Industrial Engineering and Engineering Management, Hong Kong, China, 8–11 December 2009; pp. 2104–2108. [Google Scholar]
- Wang, J.-Y.; Ho, H.-Y.; Chen, J.-D.; Chai, S.; Tai, C.-J.; Chen, Y.-F. Attitudes toward inter-hospital electronic patient record exchange: Discrepancies among physicians, medical record staff, and patients. BMC Health Serv. Res. 2015, 15, 264. [Google Scholar] [CrossRef] [PubMed]
- Kruse, C.S.; Frederick, B.; Jacobson, T.; Monticone, D.K. Cybersecurity in healthcare: A systematic review of modern threats and trends. Technol. Health Care 2017, 25, 1–10. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Alazab, M.; Broadhurst, R. An Analysis of the Nature of Spam as Cybercrime. In Cyber-Physical Security; Springer International Publishing: Cham, Switzerland, 2017; pp. 251–266. [Google Scholar]
- De Cauwer, H.; Somville, F.; Sabbe, M.; Mortelmans, L.J. Hospitals: Soft Target for Terrorism? Prehosp. Disaster Med. 2017, 32, 94–100. [Google Scholar] [CrossRef]
- Boddy, A.; Hurst, W.; Mackay, M.; el Rhalibi, A. A Study into Data Analysis and Visualisation to increase the Cyber-Resilience of Healthcare Infrastructures. Internet Things Mach. Learn. 2017. [Google Scholar] [CrossRef]
- Ogie, R. Bring Your Own Device: An overview of risk assessment. IEEE Consum. Electron. Mag. 2016, 5, 114–119. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Stoll, J.; Bengez, R.Z. Visual structures for seeing cyber policy strategies. In Proceedings of the 2015 7th International Conference on Cyber Conflict: Architectures in Cyberspace, Tallinn, Estonia, 26–29 May 2015; pp. 135–152. [Google Scholar]
- Chen, A.S.; Khoury, M.; Savic, D.A.; Vamvakeridou-Lyroudia, L.S.; Djordjevic, S. Interactive 3D visualisation of flood impact to critical infrastructure. Procedia Eng. 2017, 212, 1631–1633. [Google Scholar]
- Schukat, M. Securing critical infrastructure. In Proceedings of the DT 2014—10th International Conference on Digital Technologies 2014, Zilina, Slovakia, 9–11 July 2014; pp. 298–304. [Google Scholar]
- Boddy, A.; Hurst, W.; MacKay, M.; el Rhalibi, A. A Study into Detecting Anomalous Behaviours within HealthCare Infrastructures. In Proceedings of the 2016 9th International Conference on Developments in eSystems Engineering (DeSE), Liverpool, UK, 31 August–2 September 2016. [Google Scholar]
- Kocabas, O.; Soyata, T.; Aktas, M.K. Emerging Security Mechanisms for Medical Cyber Physical Systems. IEEE/ACM Trans. Comput. Biol. Bioinform. 2016, 13, 401–416. [Google Scholar] [CrossRef]
- Camara, C.; Peris-Lopez, P.; Tapiador, J.E. Security and privacy issues in implantable medical devices: A comprehensive survey. J. Biomed. Inform. 2015, 55, 272–289. [Google Scholar] [CrossRef] [Green Version]
- Vargheese, R. Dynamic Protection for Critical Health Care Systems Using Cisco CWS: Unleashing the Power of Big Data Analytics. In Proceedings of the 2014 Fifth International Conference on Computing for Geospatial Research and Application, Washington, DC, USA, 4–6 August 2014; pp. 77–81. [Google Scholar]
- Chui, K.T.; Alhalabi, W.; Pang, S.S.H.; Pablos, P.O.; Liu, R.W.; Zhao, M. Disease Diagnosis in Smart Healthcare: Innovation, Technologies and Applications. Sustainability 2017, 9, 2309. [Google Scholar] [CrossRef]
- Chen, Q.; Lambright, J. Towards Realizing a Self-Protecting Healthcare Information System. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; pp. 687–690. [Google Scholar]
- Thamilarasu, G. iDetect: An intelligent intrusion detection system for wireless body area networks. Int. J. Secur. Netw. 2016, 11, 82. [Google Scholar] [CrossRef]
- Skowyra, R.; Bahargam, S.; Bestavros, A. Software-Defined IDS for securing embedded mobile devices. In Proceedings of the 2013 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 10–12 September 2013; pp. 1–7. [Google Scholar]
- Ullah, F.; Habib, M.A.; Farhan, M.; Khalid, S.; Durrani, M.Y.; Jabbar, S. Semantic interoperability for big-data in heterogeneous IoT infrastructure for healthcare. Sustain. Cities Soc. 2017, 34, 90–96. [Google Scholar] [CrossRef]
- Elder, J.; Ong, E.-J.; Bowden, R. IVACS—Interactive Visual Analytics for Cyber Security. In Proceedings of the Institute of Electrical and Electronics Engineers Vision Conference (IEEE VIS), Chicago, IL, USA, 25–30 October 2015; pp. 4–5. [Google Scholar]
- Veeramachaneni, K.; Arnaldo, I.; Korrapati, V.; Bassias, C.; Li, K. AI2: Training a Big Data Machine to Defend. In Proceedings of the 2nd IEEE International Conference on Big Data Security on Cloud, IEEE BigDataSecurity 2016, 2nd IEEE International Conference on High Performance and Smart Computing, IEEE HPSC 2016 and IEEE International Conference on Intelligent Data and S, New York, NY, USA, 9–10 April 2016; pp. 49–54. [Google Scholar]
- Jacomy, M.; Venturini, T.; Heymann, S.; Bastian, M. ForceAtlas2, a Continuous Graph Layout Algorithm for Handy Network Visualization Designed for the Gephi Software. PLoS ONE 2014, 9, e98679. [Google Scholar] [CrossRef] [PubMed]
- Hu, Y. Efficient, High-Quality Force-Directed Graph Drawing. Math. J. 2005, 10, 37–71. [Google Scholar]
- Fruchterman, T.M.J.; Reingold, E.M. Graph drawing by force-directed placement. Softw. Pract. Exp. 1991, 21, 1129–1164. [Google Scholar] [CrossRef] [Green Version]
- Kobourov, S.G. Force-directed drawing algorithms. In Handbook of Graph Drawing and Visualization (Discrete Mathematics and Its Applications); CRC Press: Abingdon, UK, 2013; pp. 383–408. [Google Scholar]
- Martin, S.; Brown, W.M.; Klavans, R.; Boyack, K.W. OpenOrd: An open-source toolbox for large graph layout. Proc. SPIE 2011, 7868, 786806. [Google Scholar]
- Barnes, J.; Hut, P. A hierarchical O(N log N) force-calculation algorithm. Nature 1986, 324, 446–449. [Google Scholar] [CrossRef]
- Promrit, N.; Merabti, M.; Mingkhwan, A.; Hurst, W. Advanced Feature Extraction for Evaluating Host Behaviour in a Network. In Proceedings of the 15th Annual Conference Convergence Telecommunication Networks Broadcast, Liverpool, UK, June 2014; Available online: https://www.researchgate.net/profile/William_Hurst5/publication/267391862_Advanced_Feature_Extraction_for_Evaluating_Host_Behaviour_in_a_Network/links/546c9aff0cf2c4819f229dab.pdf (accessed on 29 January 2019).
- Kramer, D.B.; Baker, M.; Ransford, B.; Molina-Markham, A.; Stewart, Q.; Fu, K.; Reynolds, M.R. Security and privacy qualities of medical devices: An analysis of FDA postmarket surveillance. PLoS ONE 2012, 7, e40200. [Google Scholar] [CrossRef] [PubMed]
- FDA. Merge Healthcare Merge Hemo Programmable Diagnostic Computer. MAUDE Adverse Event Report. 2016. Available online: https://www.accessdata.fda.gov/scripts/cdrh/cfdocs/cfmaude/detail.cfm?mdrfoi__id=5487204 (accessed on 8 December 2016).



| Active Directory Domain Controller | Electronic Prescribing System | ||||||
|---|---|---|---|---|---|---|---|
| Proto | Local address | Foreign address | State | Proto | Local address | Foreign address | State |
| TCP | 0.0.0.0:***** | 0.0.0.0:0 | LISTENING | TCP | 0.0.0.0:***** | 0.0.0.0:0 | LISTENING |
| TCP | **.**.***.16:53 | 0.0.0.0:0 | LISTENING | TCP | **.**.***.197:139 | 0.0.0.0:0 | LISTENING |
| TCP | **.**.***.16:135 | **.**.**.148:53173 | ESTABLISHED | TCP | **.**.***.197:8194 | **.**.***.133:50176 | ESTABLISHED |
| TCP | **.**.***.16:135 | **.**.***.51:63068 | ESTABLISHED | TCP | **.**.***.197:8194 | **.**.***.133:50326 | ESTABLISHED |
| TCP | **.**.***.16:135 | **.**.***.92:29550 | ESTABLISHED | TCP | **.**.***.197:8194 | **.**.***.133:50640 | ESTABLISHED |
| IP Address | Sankey Diagram Counts | |||||||
|---|---|---|---|---|---|---|---|---|
| Domain Controller local | 5040 | 31 | 24 | 4 | 3 | 2 | 1 | |
| Domain Controller foreign | 225 | 153 | 79 | 62 | 44 | 3 | 2 | 1 |
| Electronic Patients and Medicines Administration local | 33 | 22 | 13 | 1 | ||||
| Electronic Patients and Medicines Administration foreign | 6 | 2 | 1 | |||||
| Patient Administration System local | 32 | 24 | 23 | 14 | 2 | 1 | ||
| Patient Administration System foreign | 64 | 2 | 1 | |||||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boddy, A.; Hurst, W.; Mackay, M.; El Rhalibi, A.; Baker, T.; Montañez, C.A.C. An Investigation into Healthcare-Data Patterns. Future Internet 2019, 11, 30. https://doi.org/10.3390/fi11020030
Boddy A, Hurst W, Mackay M, El Rhalibi A, Baker T, Montañez CAC. An Investigation into Healthcare-Data Patterns. Future Internet. 2019; 11(2):30. https://doi.org/10.3390/fi11020030
Chicago/Turabian StyleBoddy, Aaron, William Hurst, Michael Mackay, Abdennour El Rhalibi, Thar Baker, and Casimiro A. Curbelo Montañez. 2019. "An Investigation into Healthcare-Data Patterns" Future Internet 11, no. 2: 30. https://doi.org/10.3390/fi11020030





