Communication Channel Reconstruction for Transmission Line Differential Protection: System Arrangement and Routing Protocol
Abstract
:1. Introduction
- (1)
- Complicated environment factors may influence the connectivity of network. When the route reply is missing due to poor link quality or node damage, the routing processes will initialize in succession, which is time-consuming and unfavorable for delay constraint.
- (2)
- Conventional routing protocols consider routes on a two-dimensional plane, while the protective data only needs directional propagation in one dimension.
- (3)
- The WSN nodes of RCCs are deployed fixedly and almost lined up straight; but the WSN routing protocol has considered mobile ad hoc situations, which need requirement-based improvement.
2. System Arrangement
2.1. Application Scope
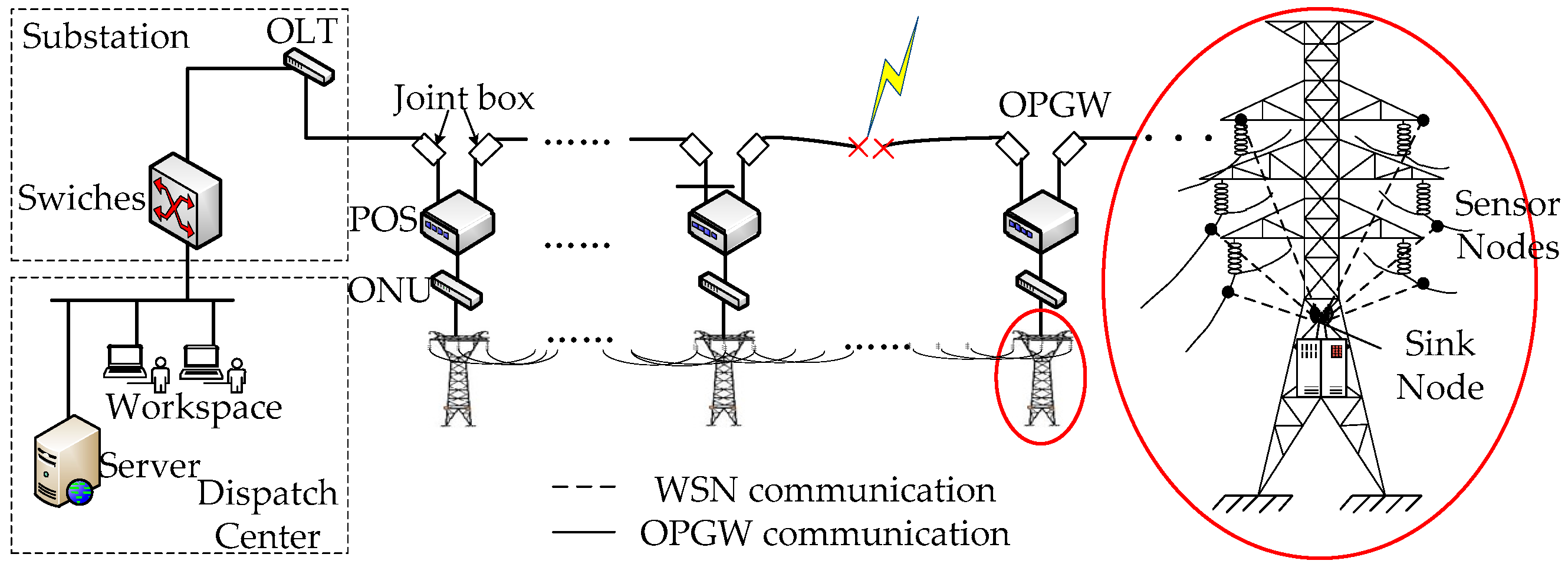
2.2. Structure of a Wireless Sensor Network-Based Monitoring System
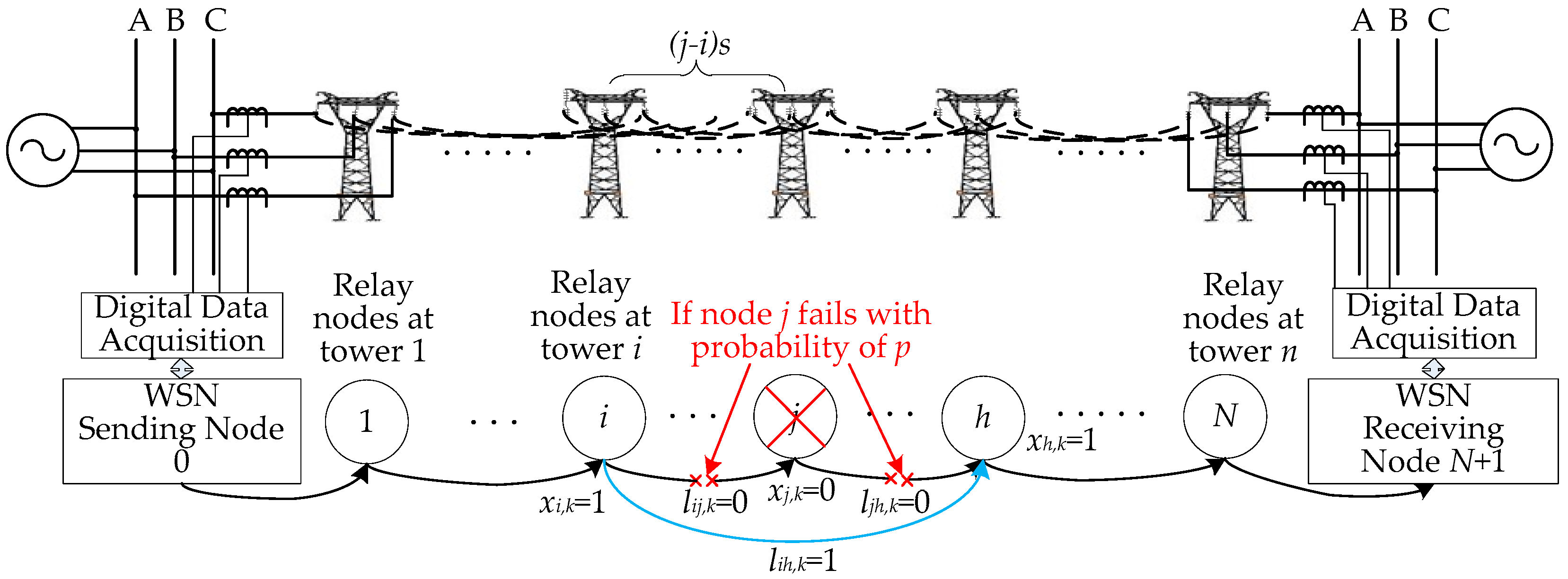
2.3. Description of Reconstructed Communication Channel Model
- (1)
- Since the communication range of radio frequency (RF) modules with the state-of-the-art is around 1 km [24], the relay can skip some adjacent nodes, e.g., from tower 1 to tower 4.
- (2)
- To simplify installation, sensors are placed near the tower. Then, the distance between these sensors are less than 20 m, which is far less than span distance, so nodes at a tower can be regarded as an equivalent node.
- (3)
- During natural disasters, the OPGW is likely to be damaged, while the WSN nodes have redundancy and most of them can survive under natural disasters. In addition, taking the self-organized characteristic of WSNs into account, they can undertake the task of transmitting protection data.
2.4. Formulation of System Arrangement
2.4.1. Symbol Statement
2.4.2. Optimal Arrangement Formulation
2.4.3. Monte Carlo Solution
3. Overall Design of the Communication Channel Reconstruction
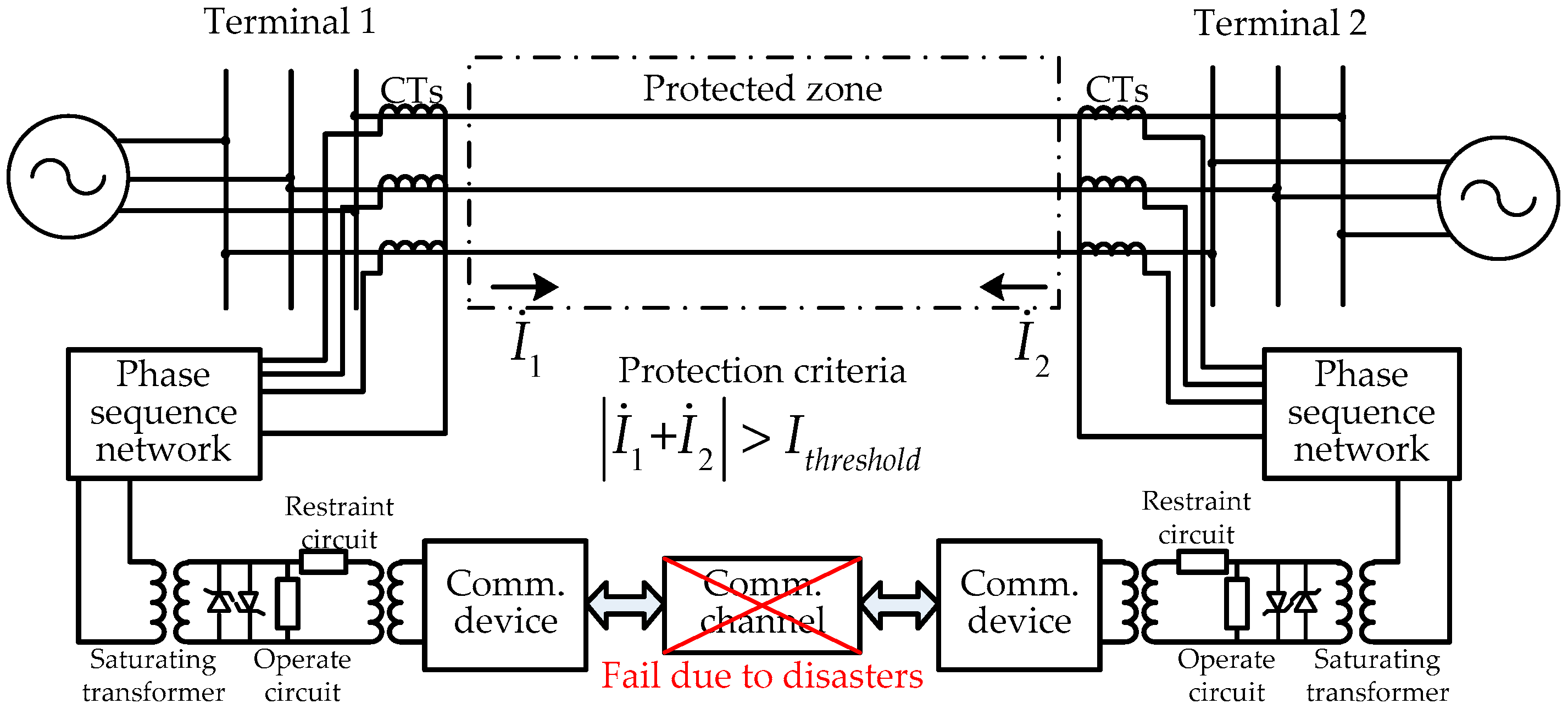
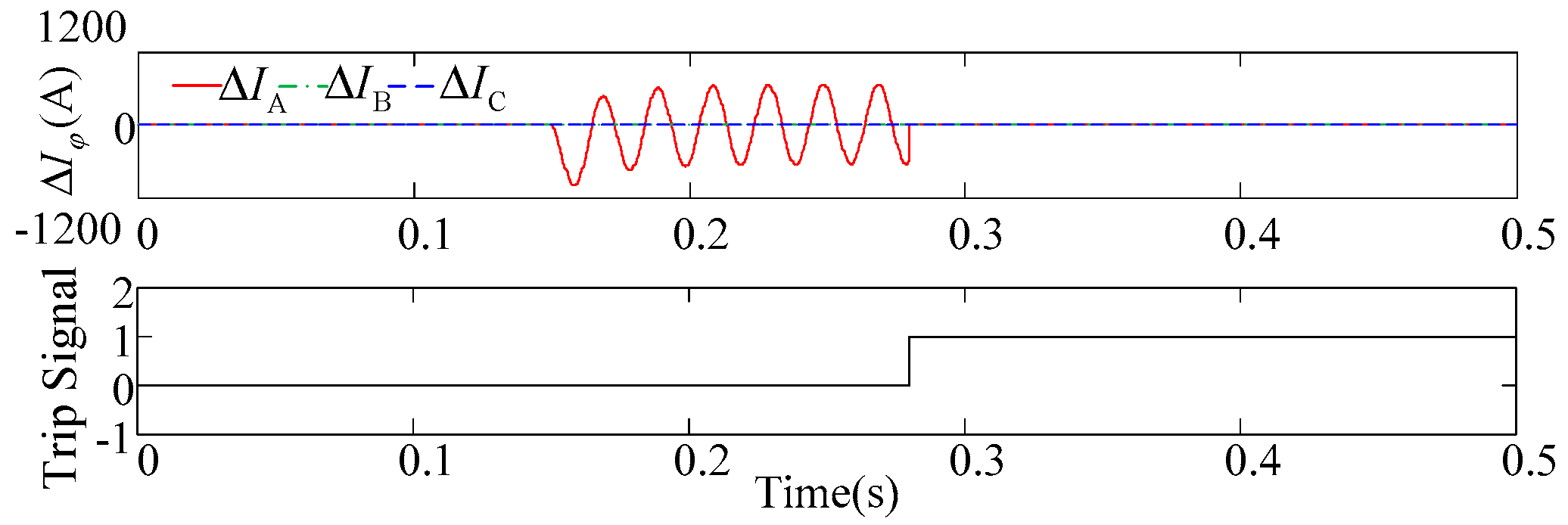
3.1. Protection Principle
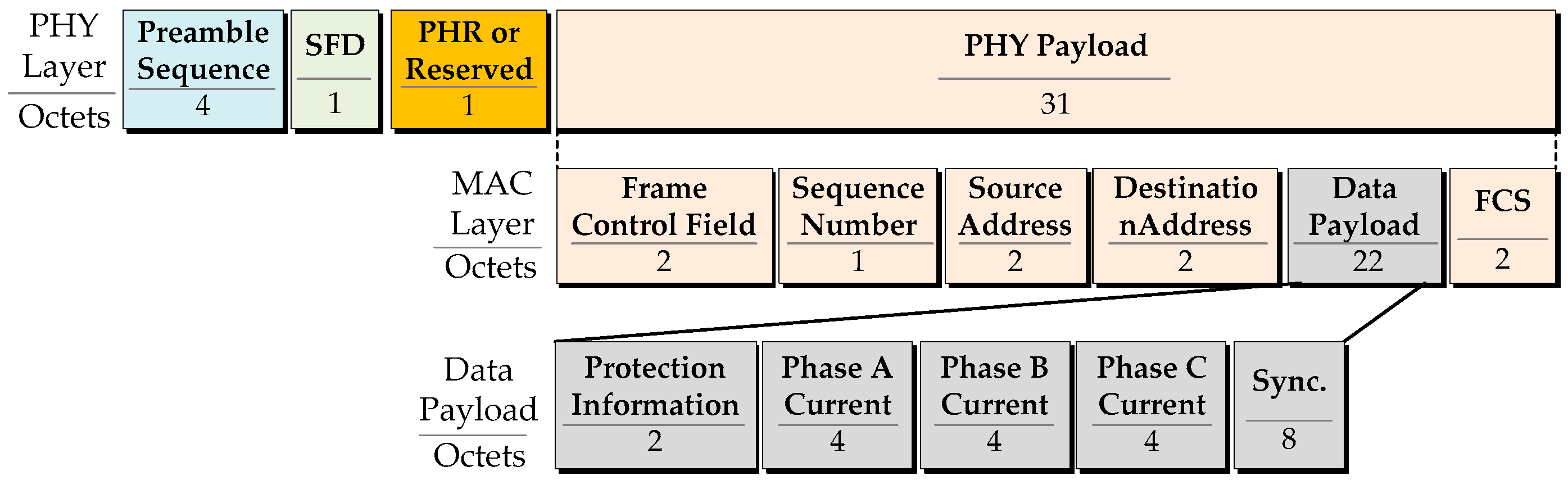
3.2. Data Preparation
3.3. Capacity Analysis
3.4. Synchronization
4. Improved Routing Protocol
4.1. Basic Concept in Route Establishment
4.2. Route Discovery
4.2.1. Route Request
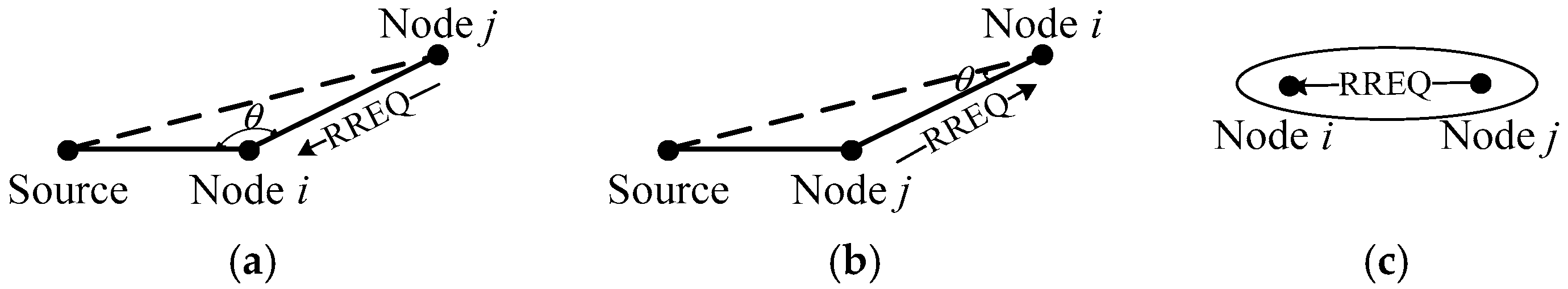
4.2.2. Route Reply
- Case 1
- As shown in Figure 5a, if θ > θth, node j is added to the forward list of node i. Namely, node i is the intermediate node from the source to node j.
- Case 2
- As shown in Figure 5b, if θ < θth, node j is added to the backward list of node i. Namely, node j is the intermediate node from the destination to node i.
- Case 3
- As shown in Figure 5c, if dij < dth, node B will not be added to any list of node A. It indicates that node i and node j will not exist on the forward list or the backward list of each other when they are in the same tower range.
4.2.3. Data Forwarding
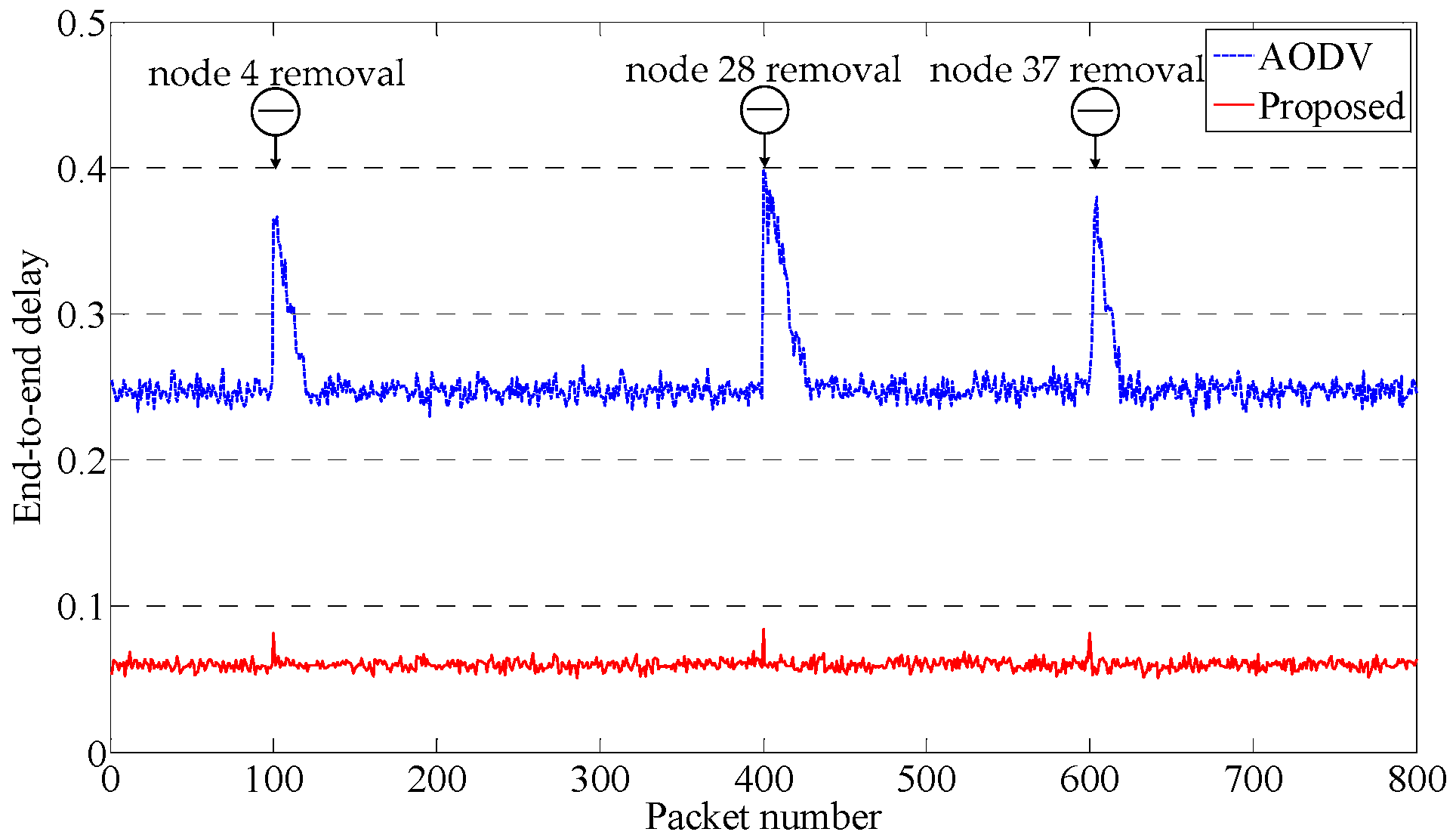
4.3. Route Maintenance
4.4. Comparative Study with Other Novel Solutions
5. Experiments and Performance Evaluation
5.1. Performance of Monte Carlo Simulation
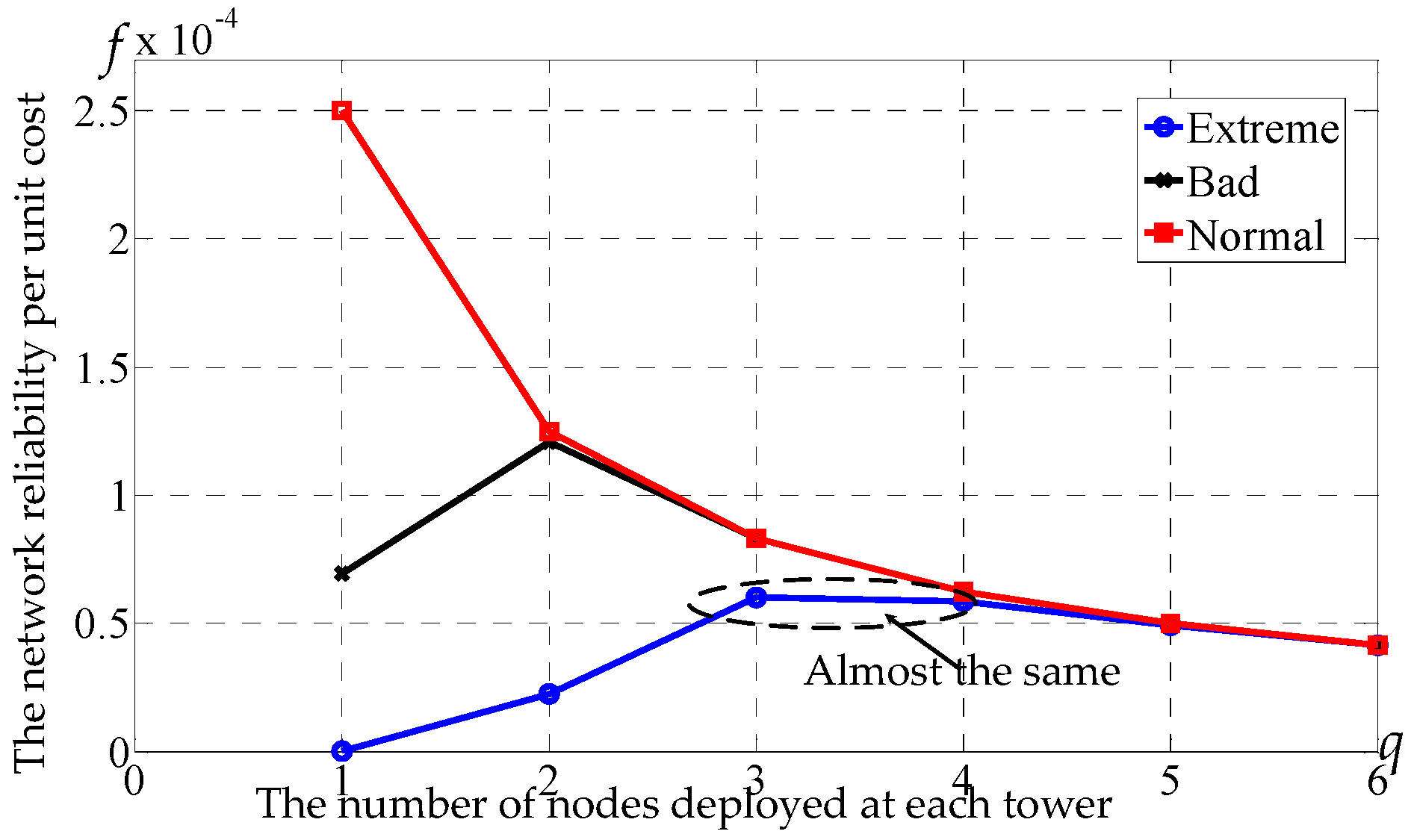
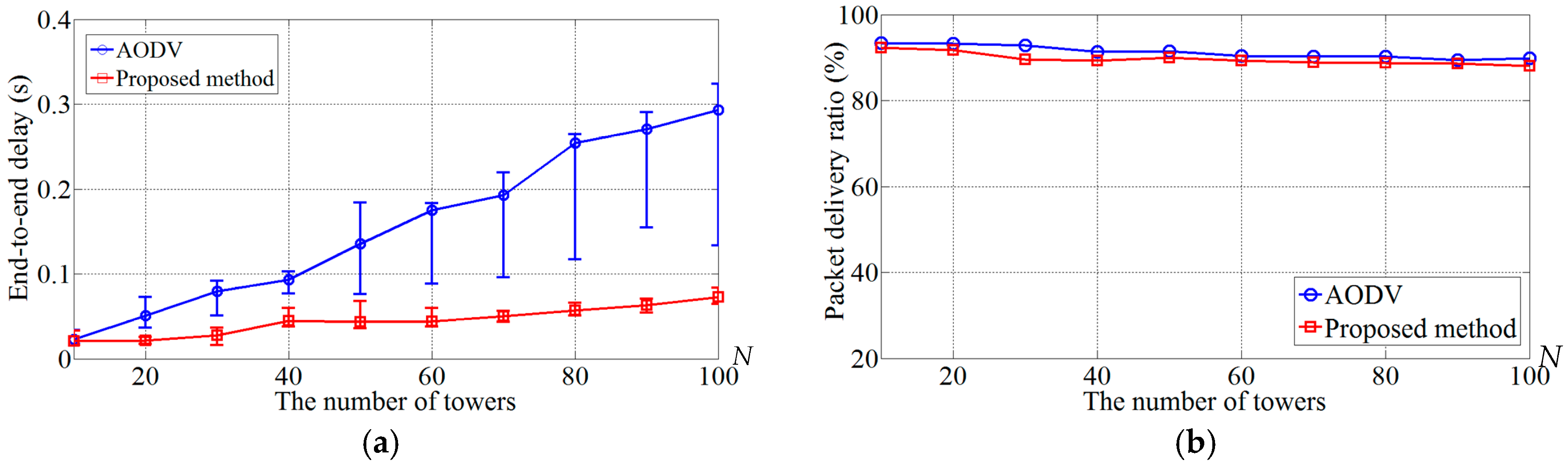
5.2. Effect of the Number of Nodes Deployed at Each Tower
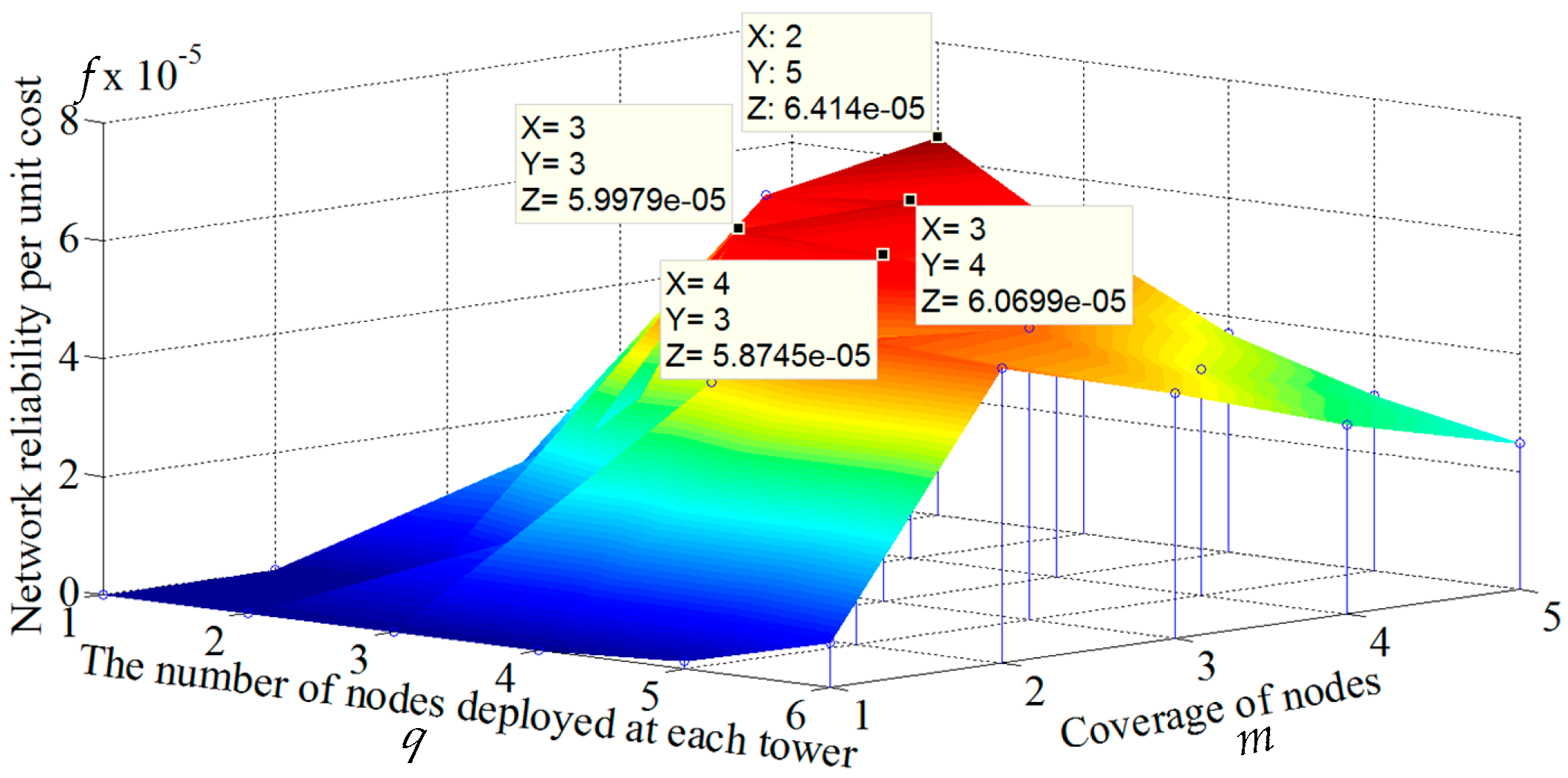
5.3. Effect of Communication Range
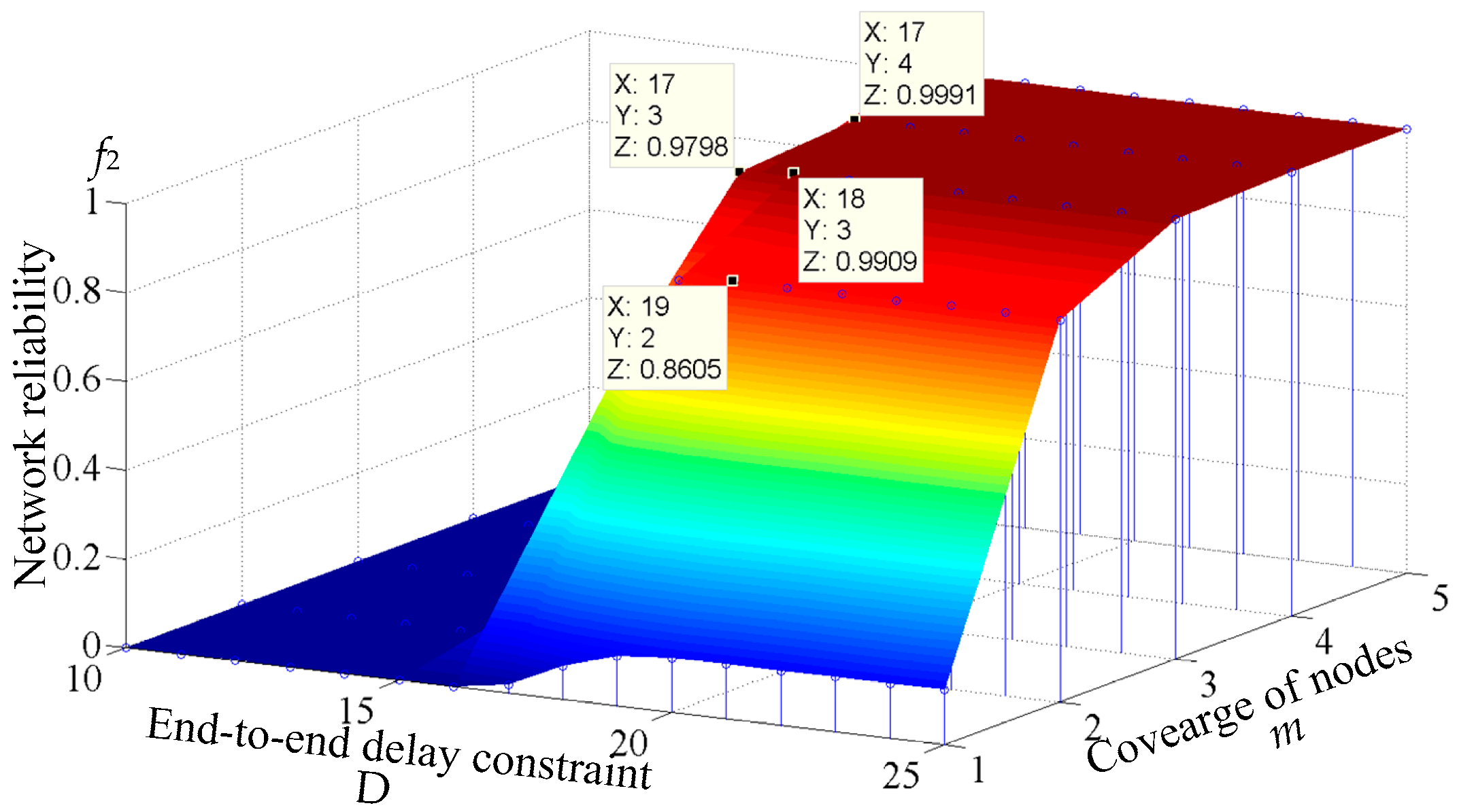
5.4. Effect of End-to-End Delay Constraint
5.5. Performance of the Routing Protocol
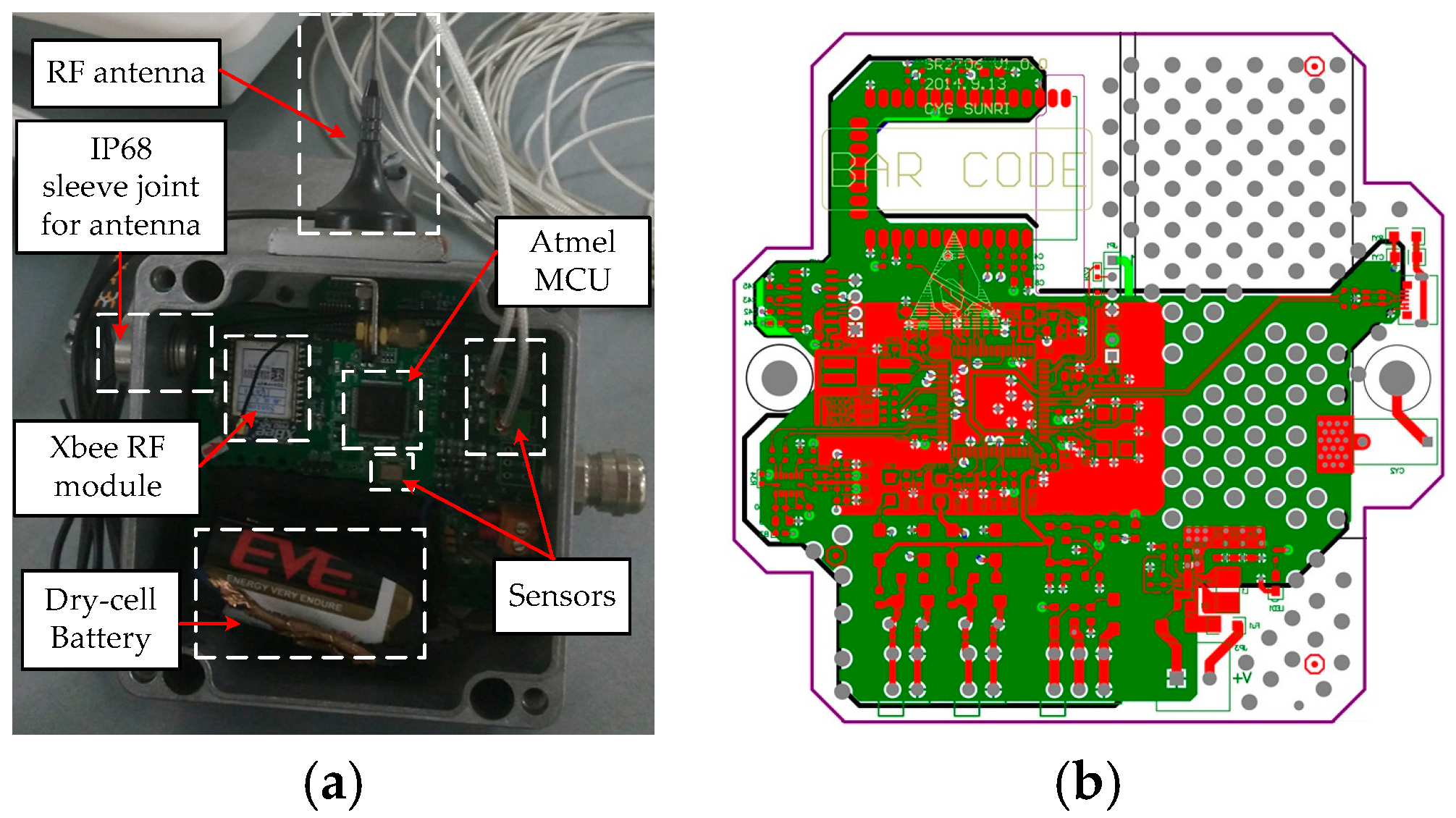
5.6. Experimental Test
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Miao, S.H.; Liu, P.; Lin, X. An adaptive operating characteristic to improve the operation stability of percentage differential protection. IEEE Trans. Power Deliv. 2010, 25, 1410–1417. [Google Scholar] [CrossRef]
- Blackburn, J.L.; Domin, T.J. Protective Relaying: Principles and Applications, 3rd ed.; CRC Press: Boca Raton, FL, USA, 2007. [Google Scholar]
- Lin, X.; Tian, Q.; Zhao, M. Comparative analysis on current percentage differential protections using a novel reliability evaluation criterion. IEEE Trans. Power Deliv. 2006, 21, 66–72. [Google Scholar] [CrossRef]
- IEEE Guide for Power System Protective Relay Applications over Digital Communication Channels; C37.236–2013; IEEE Std.: New York, NY, USA, 2013.
- Li, H.; Rosenwald, G.W.; Jung, J.; Liu, C. Strategic power infrastructure defense. IEEE J. 2005, 93, 918–933. [Google Scholar]
- Asea Brown Boveri Ltd. Line Differential Protection RED 670 2.0 IEC Application Manual; Asea Brown Boveri Ltd.: Hong Kong, China, 2014. [Google Scholar]
- Ryutaro, K. Architectures for ATM network survivability. IEEE Commun. Surv. 1998, 1, 2–11. [Google Scholar]
- Fodero, K.; Rosselli, G. Applying Digital Current Differential Systems over Leased Digital Service. In Proceedings of the 58th Annual Conference for Protective Relay Engineers, College Station, TX, USA, 5–7 April 2005; pp. 291–298.
- Zhang, P.; Li, F.; Bhatt, N. Next-generation monitoring, analysis, and control for the future smart control center. IEEE Trans. Smart Grid 2010, 1, 186–192. [Google Scholar] [CrossRef]
- Gungor, V.C.; Lambert, F.C. A survey on communication networks for electric system automation. Comput. Netw. 2006, 50, 877–897. [Google Scholar] [CrossRef]
- Bose, A. Smart transmission grid applications and their supporting infrastructure. IEEE Trans. Smart Grid 2010, 1, 11–19. [Google Scholar] [CrossRef]
- Yang, Y.; Divan, D.; Harley, R.G.; Habetler, T.G. Design and Implementation of Power Line Sensornet for Overhead Transmission Lines. In Proceedings of the 2009 IEEE Power and Energy Society General Meeting, Calgary, AB, Canada, 26–30 July 2009.
- Li, F.; Qiao, W.; Sun, H.; Wan, H.; Wang, J.; Xia, Y.; Xu, Z.; Zhang, P. Smart transmission grid: Vision and framework. IEEE Trans. Smart Grid 2010, 1, 168–177. [Google Scholar] [CrossRef]
- Gungor, V.C.; Lu, B.; Hancke, G.P. Opportunities and challenges of wireless sensor networks in smart grid—A case study of link quality assessments in power distribution systems. IEEE Trans. Ind. Electron. 2010, 57, 3557–3564. [Google Scholar] [CrossRef]
- Fateh, B.; Govindarasu, M.; Ajjarapu, V. Wireless network design for transmission line monitoring in smart grid. IEEE Trans. Smart Grid 2013, 4, 1076–1086. [Google Scholar] [CrossRef]
- Wu, Y.; Cheung, L.; Lui, K.; Pong, P. Efficient communication of sensors monitoring overhead transmission lines. IEEE Trans. Smart Grid 2012, 3, 1130–1136. [Google Scholar] [CrossRef] [Green Version]
- Abdel-Latif, K.M.; Eissa, M.M.; Ali, A.S.; Malik, O.P.; Masoud, M.E. Laboratory investigation of using Wi-Fi protocol for transmission line differential protection. IEEE Trans. Power Deliv. 2009, 24, 1087–1094. [Google Scholar] [CrossRef]
- Hung, K.S.; Lee, W.K.; Li, V.O.K.; Lui, K.S.; Pong, P.W.T.; Wong, K.K.Y.; Yang, G.H.; Zhong, J. On wireless sensors communication for overhead transmission line monitoring in power delivery systems. In Proceedings of the 2010 IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 309–314.
- North American Electric Reliability Council. 2000 System Disturbances Review of Selected Electric System Disturbances in North America; North American Electric Reliability Council: Atlanta, GA, USA, 2000. [Google Scholar]
- Italian Government Working Group on Critical Information Infrastructure Protection (PIC). La Protezione delle Infrastrutture Critiche Informatizzate—La Realtá Italiana; Italian Government: Rome, Italy, 2004. (In Italian)
- Chen, Q.; Yin, X.; You, D.; Hou, H.; Tong, G.; Wang, B.; Liu, H. Review on Blackout Process in China Southern Area Main Power Grid in 2008 Snow Disaster. In Proceedings of the 2009 IEEE Power & Energy Society General Meeting, Calgary, AB, Canada, 26–30 July 2009.
- Hou, H.; Yin, X.; Chen, Q.; Tong, G.; You, D.; Wang, B.; He, X.; Liu, H. Analysis of Vulnerabilities in China’s Southern Power System Using Data from the 2008 Snow Disaster. In Proceedings of the 2009 IEEE Power & Energy Society General Meeting, Calgary, AB, Canada, 26–30 July 2009.
- Chen, X.; Du, Z.; Yin, X.G.; Pan, W.; Xu, L.Q. A Design of WSN and EPON applied in online monitoring for transmission line. Adv. Mater. Res. 2014, 950, 125–132. [Google Scholar] [CrossRef]
- Digi International Inc. Xbee-pro 2009. Available online: http://www.digi.com (accessed on 26 September 2016).
- Binder, K.; Heermann, D.W. Monte Carlo Simulation in Statistical Physics; Springer: New York, NY, USA, 1997; pp. 5–7. [Google Scholar]
- IEEE Standard for Information Technology—Part 15.4: Wireless Medium Access Control and Physical Layer Specifications for Low Rate Wireless Personal Area Networks; IEEE 802.15.4–2006; IEEE: New York, NY, USA, 2006.
- Perkins, C.E.; Royer, E.M. Ad-hoc On-Demand Distance Vector Routing. In Proceedings of the Workshop Mobile Computing Systems and Applications, New Orleans, LA, USA, 25–26 February 1999.
- Shu, J.; Liu, L.; Zhang, R. An Energy-Effective Link Quality Monitoring Mechanism for Event-Driven Wireless Sensor Network. In Proceedings of the WRI International Conference Communications and Mobile Computing, Yunnan, China, 6–8 January 2009; pp. 111–115.
- King, C. Virtual Instrumentation-Based System in a Real-Time Applications of GPS/GIS. In Proceedings of the International Conference on Recent Advances in Space Technologies, Istanbul, Turkey, 20–22 November 2003; pp. 403–408.
- Makwana, N.D.; Kumar, A. Virtual Cluster Head-Set Based Avalanche Predication in Himalayan Region. In Proceedings of the 2014 International Conference on Advanced Communication Control and Computing Technologies, Ramanathapuram, India, 8–10 May 2014.
- Deb, B.; Bhatnagar, S.; Nath, B. A Topology Discovery Algorithm for Sensor Networks with Applications to Network Management; DCS Technical Report DCS-TR-411; Rutgers University: New Brunswick, NJ, USA, 2001. [Google Scholar]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Al-Nabhan, N.; Al-Rodhaan, M.; Al-Dhelaan, A. Cooperative approaches to construction and maintenance of networks’ virtual backbones for extreme wireless sensor applications. IEEE Sens. J. 2014, 14, 3782–3790. [Google Scholar] [CrossRef]
- Liu, J.; Ping, Z. Fault Tolerant and Storage Efficient Directed-Diffusion for Wireless Sensor Networks. In Proceedings of the 2010 IEEE International Conference on Information Theory and Information Security, Beijing, China, 17–19 December 2010; pp. 884–887.
- Zonouz, A.E.; Sun, Y.; Xing, L.; Vokkarane, V.M. Hybrid wireless sensor networks: A reliability, cost and energy-aware approach. IET Wirel. Sens. Syst. 2016, 6, 42–48. [Google Scholar] [CrossRef]
| Address of Nodes | Distance | Link Quality Indicator (LQI) | Link Status |
|---|---|---|---|
| Address 1 | d1 | LQI1 | Valid/invalid |
| … | … | … | … |
| Address n | dn | LQIn | Valid/invalid |
| N | Monte Carlo Experiments | Exhaustive Simulations | ||||
|---|---|---|---|---|---|---|
| ε = 1% | ε = 0.1% | Network Reliability | Time (s) | |||
| Number of Inputs | Time (s) | Number of Inputs | Time (s) | |||
| 10 | 1.3 × 103 | 0.23096 | 9.3 × 103 | 1.29338 | 0.83373 | 0.09567 |
| 15 | 5.8 × 103 | 0.80595 | 2.1 × 104 | 2.93454 | 0.74736 | 2.35184 |
| 20 | 5.2 × 103 | 0.76325 | 1.8 × 104 | 2.75917 | 0.66994 | 76.6096 |
| 25 | 6.2 × 103 | 1.75463 | 2.9 × 104 | 4.31000 | 0.60054 | 2569.68 |
| 30 | 7.5 × 103 | 2.22855 | 3.1 × 104 | 4.59022 | 0.53833 | 85,312.1 |
| Types 1 | DTK DRF1601 | ATZGB-780F1 | Xbee-ZB SMT | Xbee-PRO | DTK DRF1605H |
|---|---|---|---|---|---|
| RF Range | <400 m | <750 m | <1200 m | <1500 m | ≥1600 m |
| Coverage of nodes 2 | 1 | 2 | 3 | 4 | 5 |
| Price 3 | $25 | $39 | $50 | $65 | $84 |
| Producer | DTK Electronics (Shenzhen, China) | Atmel (San Jose, CA, USA) | Digi (Minnetonka, MN, USA) | Digi (Minnetonka, MN, USA) | DTK Electronics (Shenzhen, China) |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, X.; Yin, X.; Yu, B.; Zhang, Z. Communication Channel Reconstruction for Transmission Line Differential Protection: System Arrangement and Routing Protocol. Energies 2016, 9, 893. https://doi.org/10.3390/en9110893
Chen X, Yin X, Yu B, Zhang Z. Communication Channel Reconstruction for Transmission Line Differential Protection: System Arrangement and Routing Protocol. Energies. 2016; 9(11):893. https://doi.org/10.3390/en9110893
Chicago/Turabian StyleChen, Xu, Xianggen Yin, Bin Yu, and Zhe Zhang. 2016. "Communication Channel Reconstruction for Transmission Line Differential Protection: System Arrangement and Routing Protocol" Energies 9, no. 11: 893. https://doi.org/10.3390/en9110893





