5.1. Testing System Description
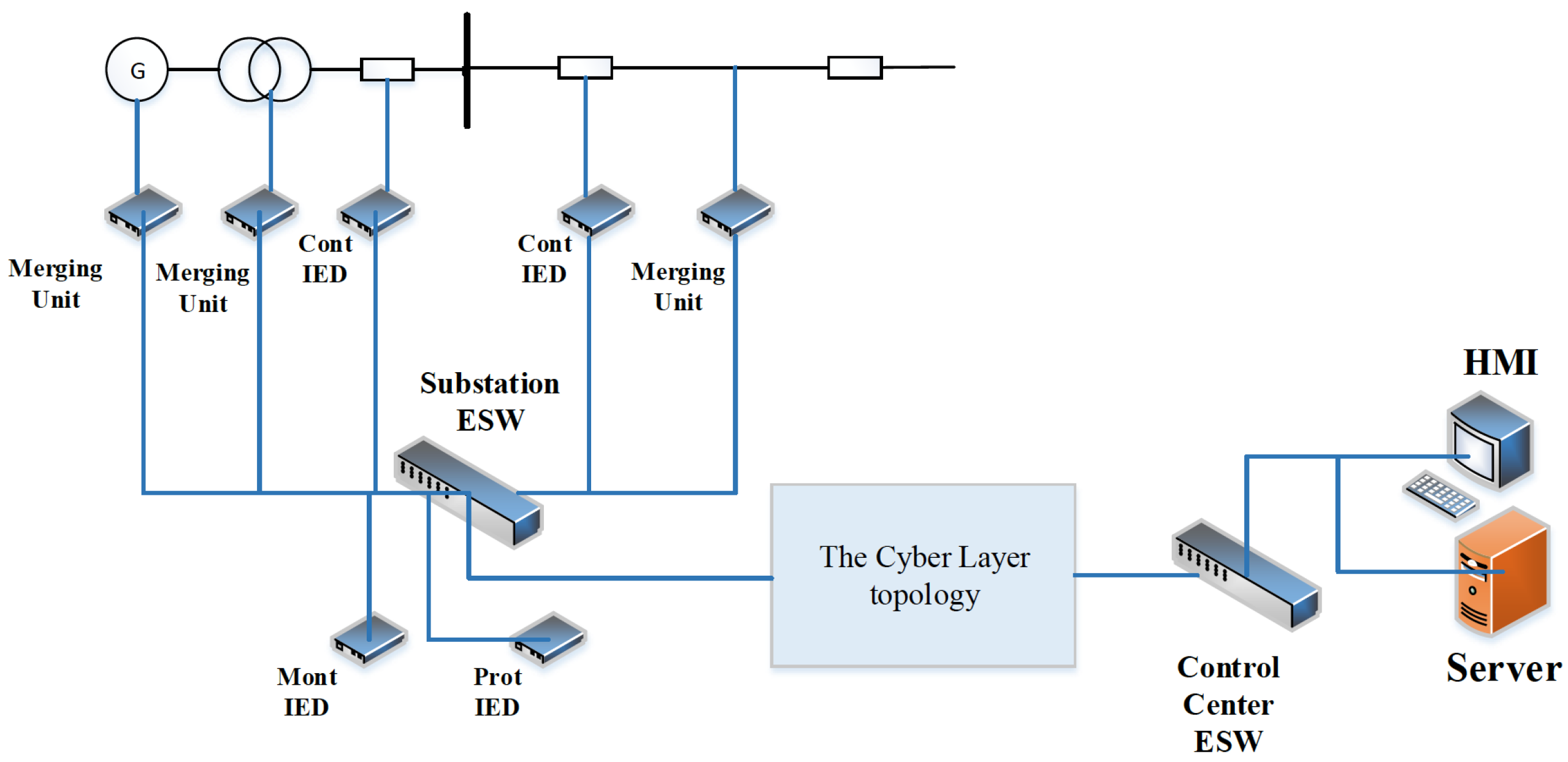
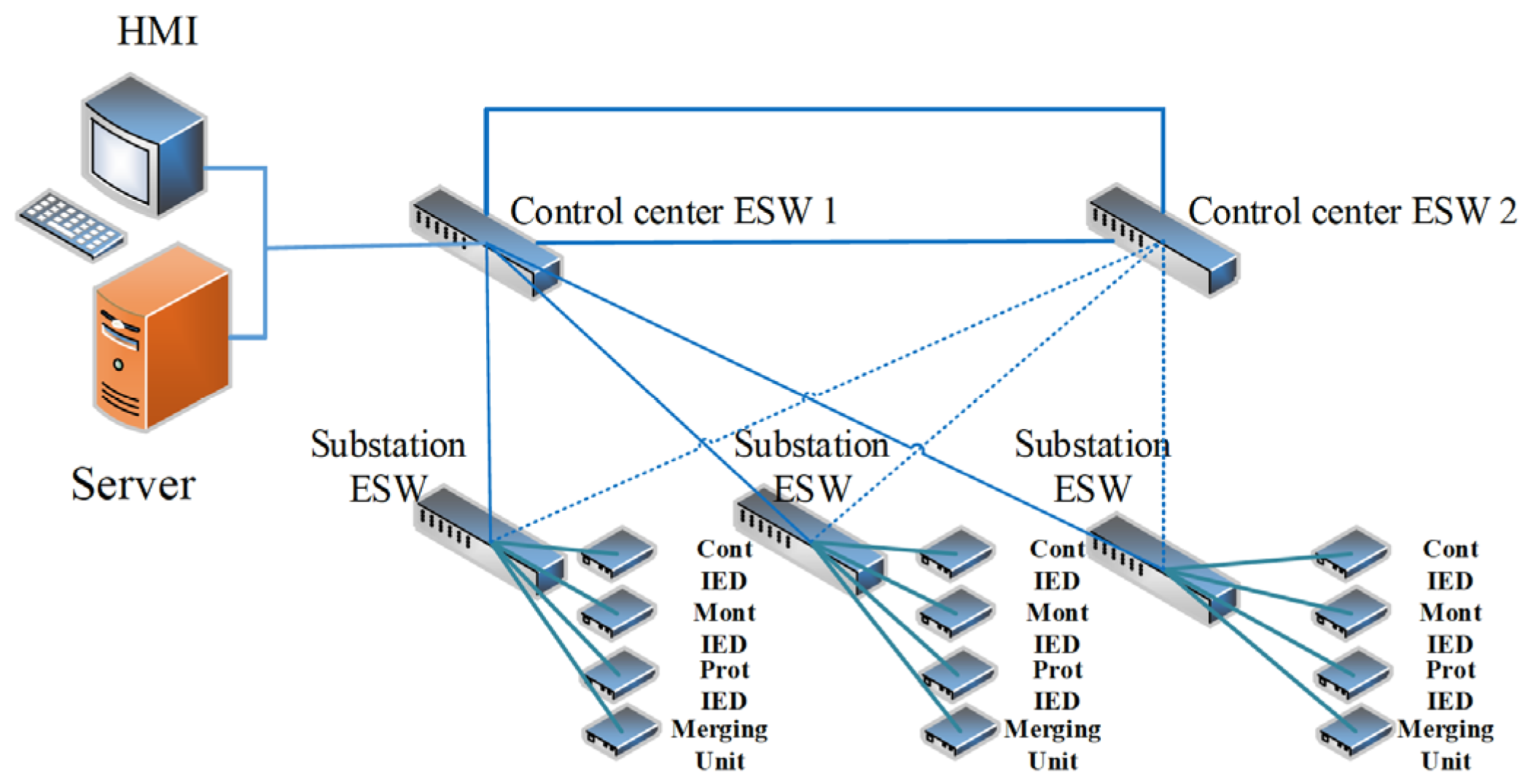
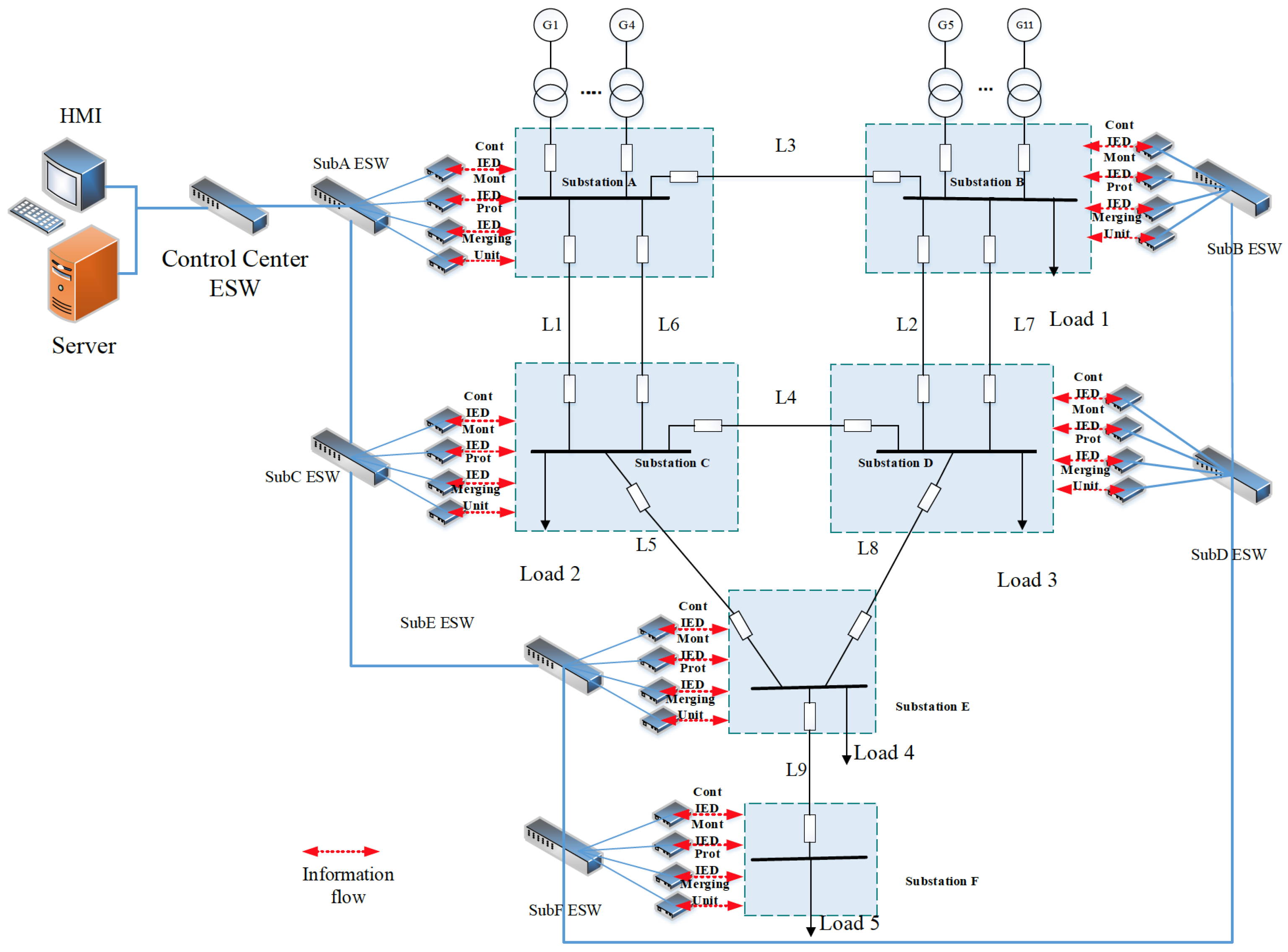
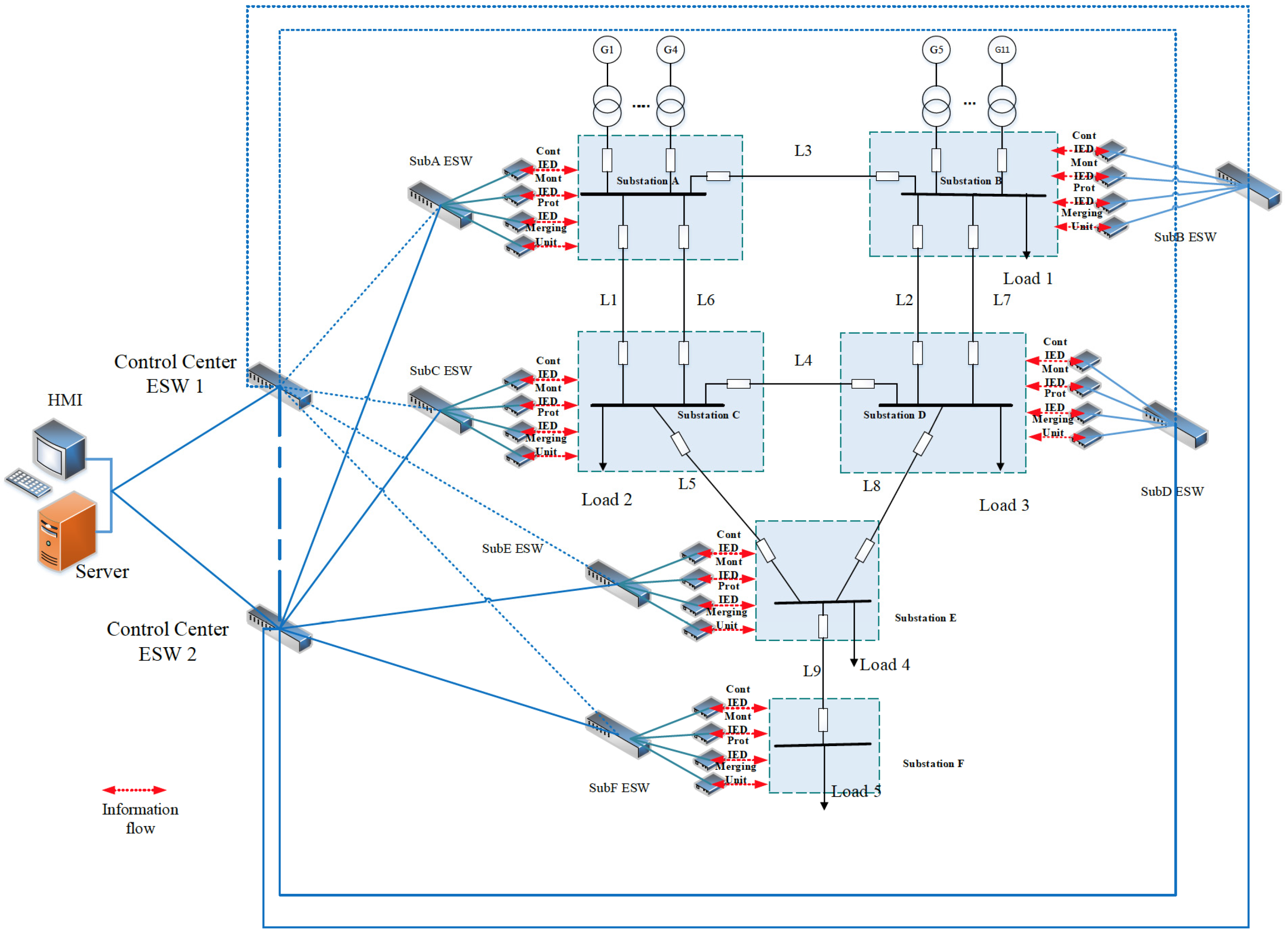
The proposed technique is applied to the 6-substation BRTS. To analyze the impacts of the cyber layer availability and its function failures on the reliability indices of composite power systems, two cyber layer topologies, the cascading topology and the star-ring topology, are illustrated in detail. The CPES models of RBTS with the cyber layer of the cascading topology and the star-ring topology are shown in
Figure 11 and
Figure 12, respectively.
Figure 11.
The CPES model of RBTS with the cyber layer of cascading topology.
Figure 11.
The CPES model of RBTS with the cyber layer of cascading topology.
Figure 12.
The CPES model of RBTS with the cyber layer of star-ring topology.
Figure 12.
The CPES model of RBTS with the cyber layer of star-ring topology.
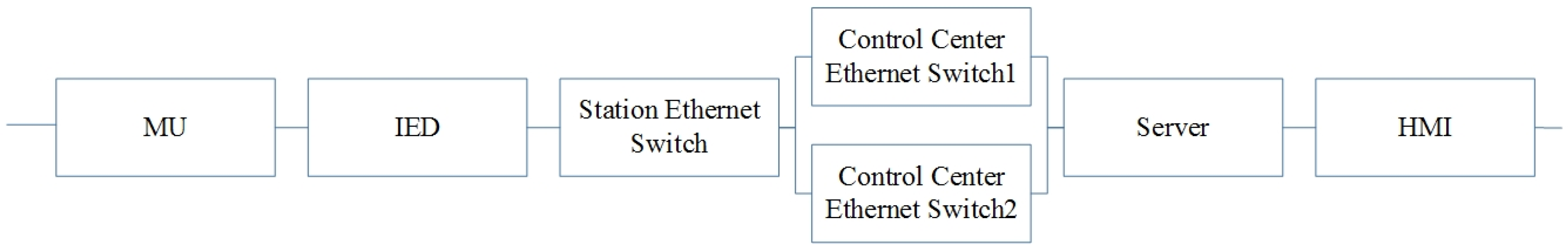
For simplicity, the control center is in charge of those six substations and generating units connected to substations A and B, also the server and the HMI with the highest authority are located in the control center. Within each substation, the connection of the cyber layer is illustrated in a compact form as the above
Figure 11 and
Figure 12, in which the Control IED, Monitoring IED, Protection IED and Merging unit are represented by one of each kind of the cyber layer components in the substation. The detailed connection and location of them within the substation is as the description in
Section 2.2. The optical fiber used as the connection medium is considered fully reliable [
23]. The MTTF and MTTR of the cyber layer components are shown in
Table 1.
Table 1.
The MTTF and MTTR of cyber layer components.
Table 1.
The MTTF and MTTR of cyber layer components.
| Cyber Layer Component | MTTF (h) | MTTR (h) |
|---|
| Substation Ethernet switch | 175200 | 72 |
| Control center Ethernet switch | 175200 | 72 |
| Pro IED | 175200 | 72 |
| Mont IED | 175200 | 72 |
| Cont IED | 175200 | 72 |
| Merging Unit | 175200 | 72 |
| Server | 175200 | 72 |
| HMI | 87600 | 72 |
Based on Equations (1)–(11) in
Section 2, the MTTF and availability of the cyber layer and its functions are calculated and compared in
Table 2.
Table 2.
The MTTF and availability of the cyber layer functions.
Table 2.
The MTTF and availability of the cyber layer functions.
| The Reliability Data of Cyber Layer Function | Cascading Topology | Star-ring Topology |
|---|
| The MTTF of monitoring function | 14600h | 35034h |
| The availability of monitoring function | 0.9951 | 0.9975 |
| The MTTF of protection function | 14600h | 35034h |
| The availability of protection function | 0.9951 | 0.9975 |
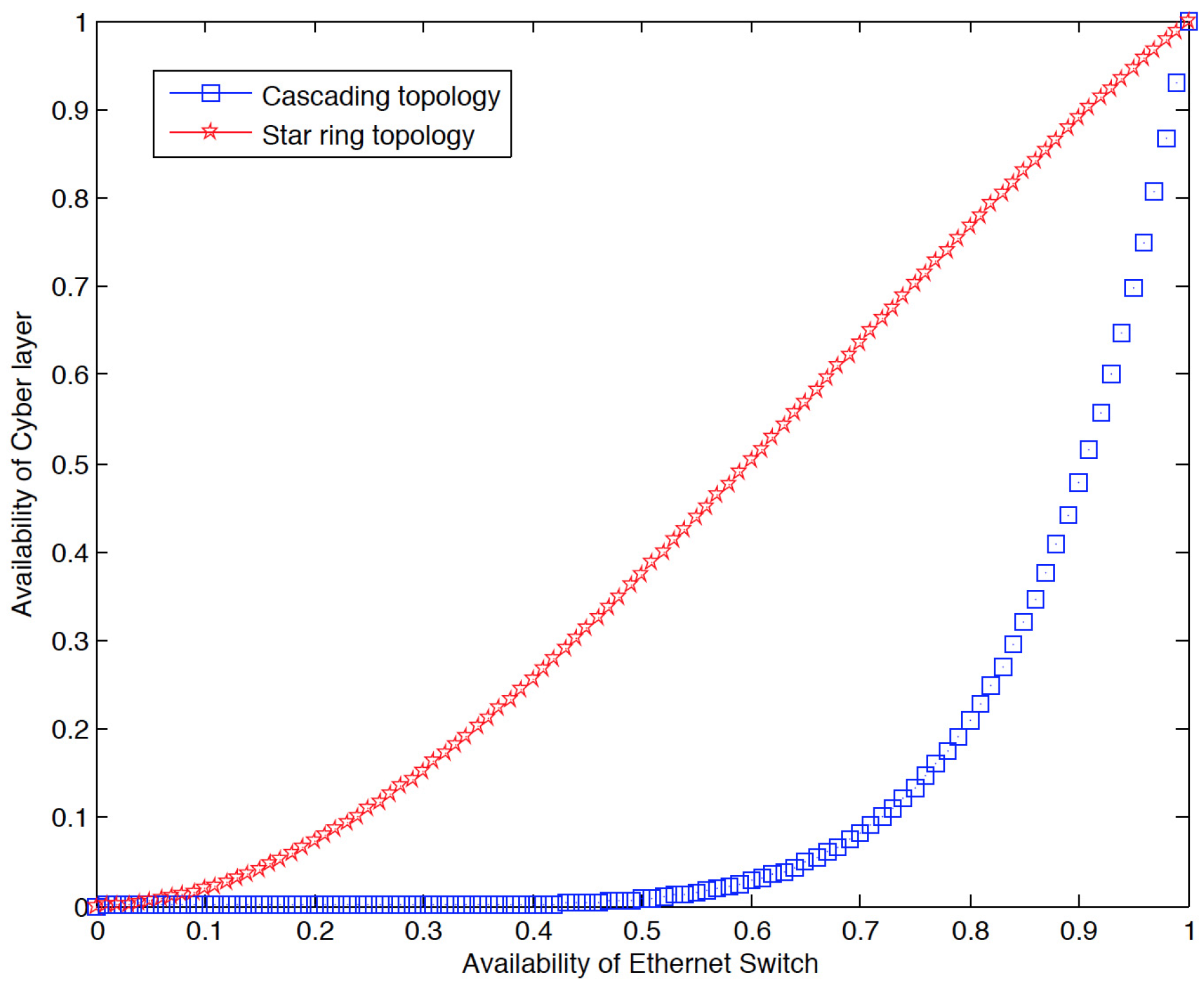
It can be observed that the availability of the cyber layer protection and monitoring functions are the same for each kind of the topology. The availability of the cascading cyber layer functions is slightly less than that of the star-ring cyber layer functions. However, the MTTF of the cascading cyber layer functions is obviously smaller, which means that the failure rates of the cyber layer functions with the cascading topology are nearly twice of those with the star-ring topology.
The availability of transmission lines and generating units incorporating the impacts of the cyber layer function failures can be derived, according to the multi-state Markov chain model illustrated in
Section 3. The initial availability of transmission lines is taken from [
26] and as shown in
Table 3.
Table 3.
The availability of transmission lines incorporating the protection function failures.
Table 3.
The availability of transmission lines incorporating the protection function failures.
| Transmission Line | Availability without the Cyber Layer | Availability Incorporating the Protection Function Failures of the Cascading Cyber Layer | Availability Incorporating the Protection Function Failures of the Star-ring Cyber Layer |
|---|
| L1 | 0.9983 | 0.9946 | 0.9960 |
| L2 | 0.9943 | 0.9897 | 0.9918 |
| L3 | 0.9955 | 0.9909 | 0.9929 |
| L4 | 0.9989 | 0.9953 | 0.9964 |
| L5 | 0.9989 | 0.9955 | 0.9967 |
| L6 | 0.9983 | 0.9946 | 0.9960 |
| L7 | 0.9944 | 0.9897 | 0.9918 |
| L8 | 0.9989 | 0.9954 | 0.9966 |
| L9 | 0.9989 | 0.9959 | 0.9969 |
It can be found that when the cyber layer protection function failures are taken into consideration, the availability of each line decreases. The decrease rate of availability with the cascading cyber layer is about twice of that with the star-ring cyber layer. For lines with the same initial availability, as L1 and L6, the decrease rates are still distinct because the protection of each line acts as the backup protection for different number of adjacent lines and the failure rates of the adjacent lines are different.
The cyber layer monitoring function is mainly applied to circuit breakers and transformers. The initial availability of circuit breakers and transformers is taken according to [
20,
26].
Table 4 shows the availability of circuit breakers and transformers with fully available cyber layer monitoring function and monitoring function with failures, respectively.
Table 4.
The availability of circuit breakers and transformers incorporating the monitoring function.
Table 4.
The availability of circuit breakers and transformers incorporating the monitoring function.
| Cascading Cyber Layer | Availability without the Cyber Layer | Availability with Fully Available Monitoring Function | Availability with the Monitoring Function with Failures |
|---|
| Circuit breaker | 0.9993 | 0.9998 | 0.9993 |
| Transformer | 0.9982 | 0.9994 | 0.9982 |
| Star-ring cyber layer | Availability without the cyber layer | Availability with fully available monitoring function | Availability with the monitoring function with failures |
| Circuit breaker | 0.9993 | 0.9998 | 0.9994 |
| Transformer | 0.9982 | 0.9994 | 0.9983 |
It can be observed that when the monitoring function is applied, the availability of each monitored device increases, especially that of transformers. If the monitoring function is not fully available, the increase rate will be less, which is relevant to the availability of the cyber layer monitoring function. After the modified availability of circuit breakers and transformers is obtained and the initial availability of generators is taken according to [
26], the availability of generating units with the cyber layer function failures is shown in
Table 5 and
Table 6, respectively.
Table 5.
The availability of generating units incorporating the cascading cyber layer function failures.
Table 5.
The availability of generating units incorporating the cascading cyber layer function failures.
| Generating Unit | Availability without the Cyber Layer | Availability with the Cyber Layer Function Failures |
|---|
| Generating Unit 1 | 0.9683 | 0.9667 |
| Generating Unit 2 | 0.9683 | 0.9667 |
| Generating Unit 3 | 0.9783 | 0.9767 |
| Generating Unit 4 | 0.9733 | 0.9718 |
| Generating Unit 5 | 0.9883 | 0.9869 |
| Generating Unit 6 | 0.9883 | 0.9868 |
| Generating Unit 7 | 0.9783 | 0.9776 |
| Generating Unit 8 | 0.9833 | 0.9824 |
| Generating Unit 9 | 0.9833 | 0.9824 |
| Generating Unit 10 | 0.9833 | 0.9824 |
| Generating Unit 11 | 0.9833 | 0.9824 |
Table 6.
The availability of generating units incorporating the star-ring cyber layer function failures.
Table 6.
The availability of generating units incorporating the star-ring cyber layer function failures.
| Generating Unit | Availability without the Cyber Layer | Availability with the Cyber Layer Function Failures |
|---|
| Generating Unit 1 | 0.9683 | 0.9673 |
| Generating Unit 2 | 0.9683 | 0.9673 |
| Generating Unit 3 | 0.9783 | 0.9773 |
| Generating Unit 4 | 0.9733 | 0.9723 |
| Generating Unit 5 | 0.9883 | 0.9872 |
| Generating Unit 6 | 0.9883 | 0.9872 |
| Generating Unit 7 | 0.9783 | 0.9776 |
| Generating Unit 8 | 0.9833 | 0.9825 |
| Generating Unit 9 | 0.9833 | 0.9825 |
| Generating Unit 10 | 0.9833 | 0.9825 |
| Generating Unit 11 | 0.9833 | 0.9825 |
The availability of the generating unit with the cyber layer protection and monitoring function failures becomes less when the failures of the cyber layer function is considered, and the availability of each generating unit with the cascading cyber layer is less than that with the star-ring cyber layer. Therefore the cyber layer topology, the availability of the cyber layer functions and the initial reliability of each generator and transformer are the three main factors influencing the availability of generating units in the CPES.