Decision Tree-Based Preventive Control Applications to Enhance Fault Ride Through Capability of Doubly-Fed Induction Generator in Power Systems
Abstract
:1. Introduction
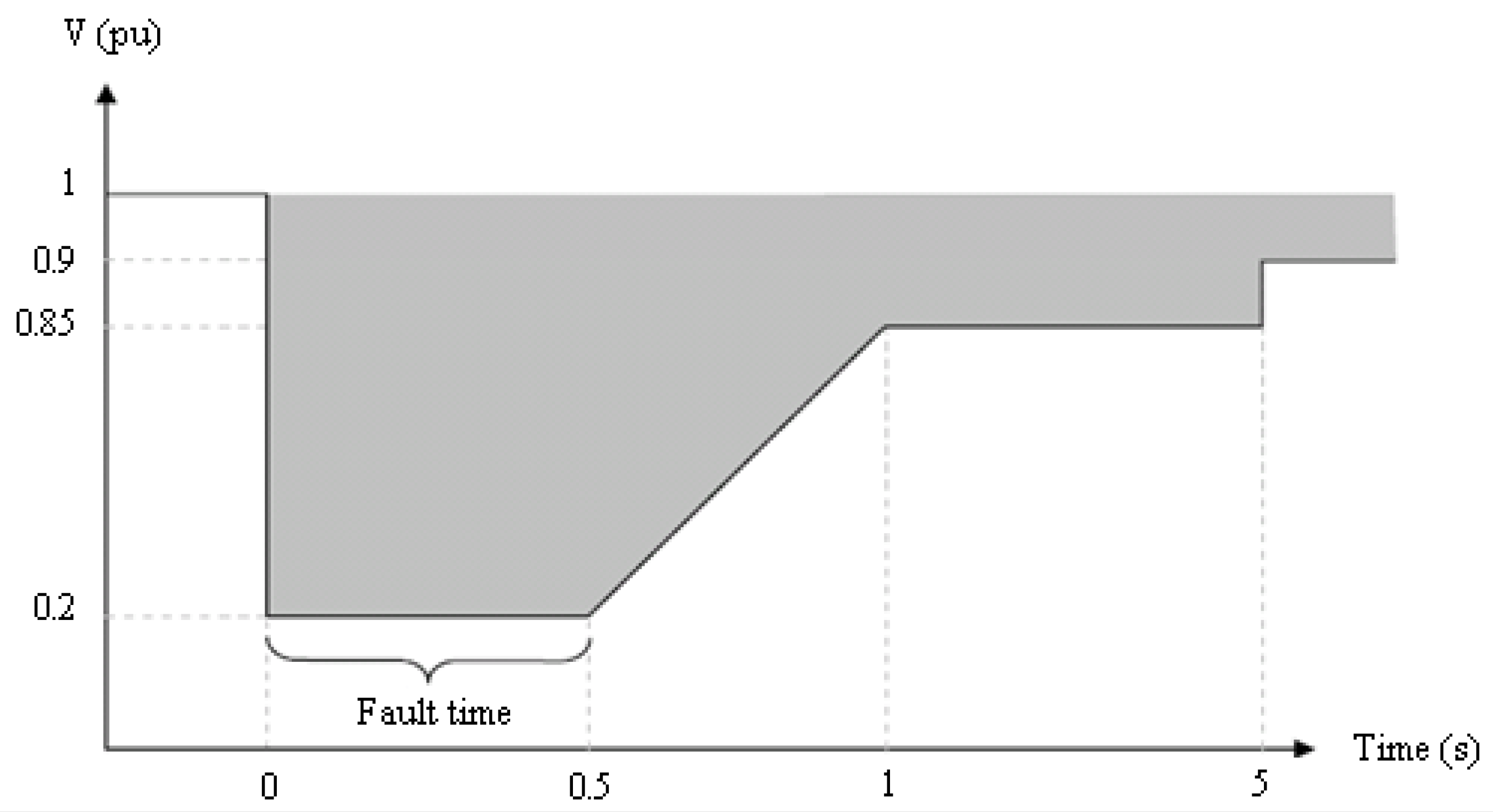
2. Methods and Materials
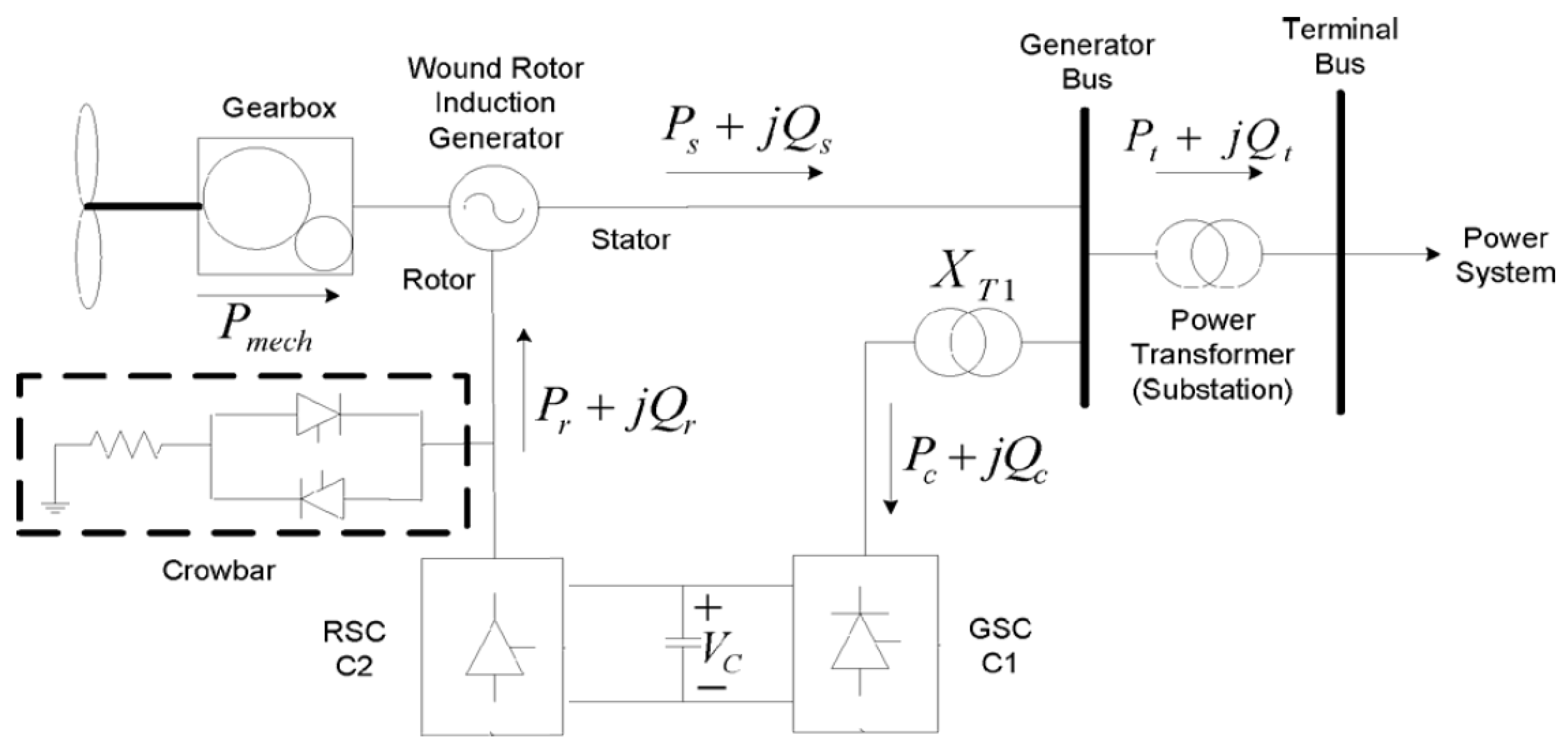
2.1. Doubly-Fed Inductcion Generator (DFIG)
2.2. Decision Tree (DT)
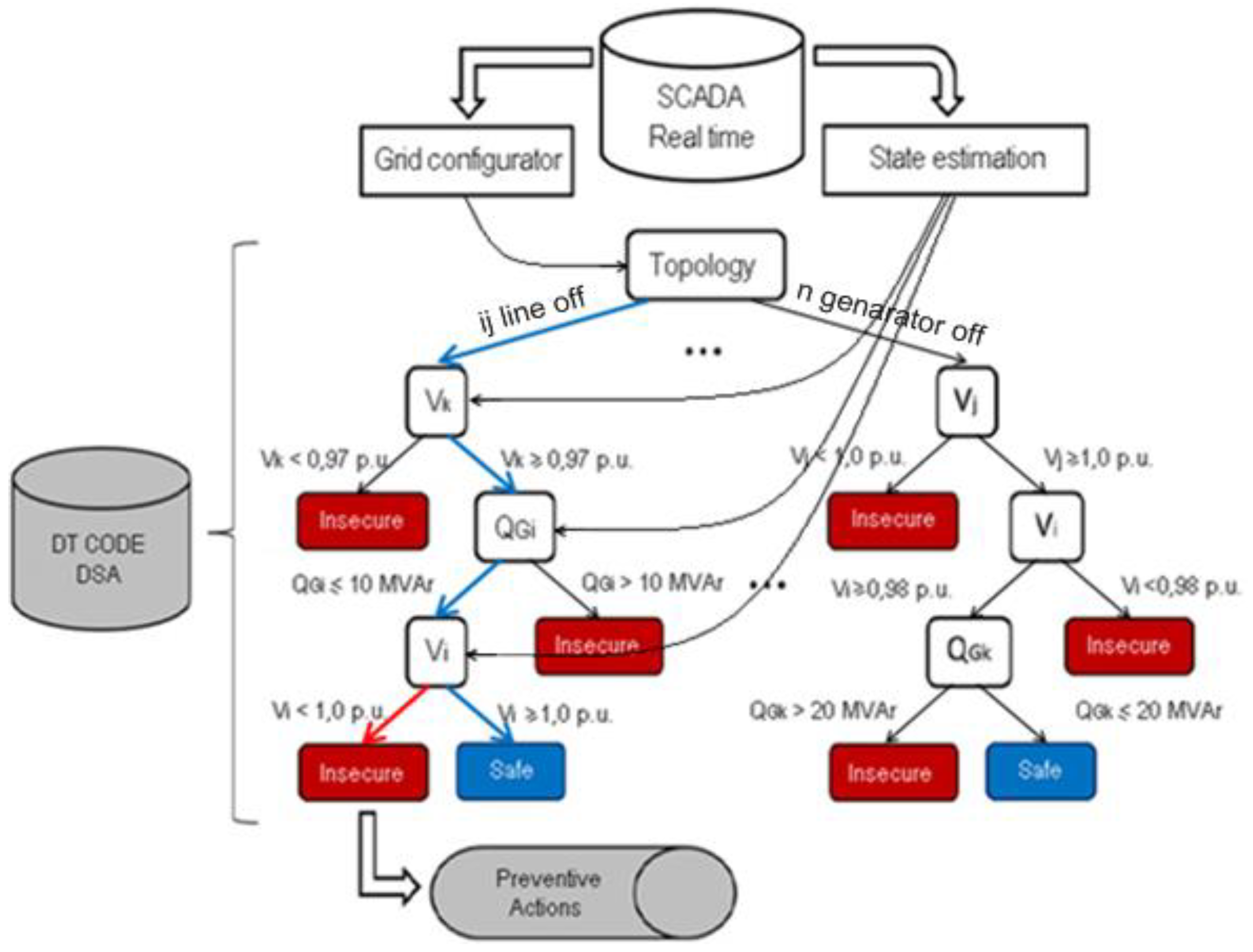
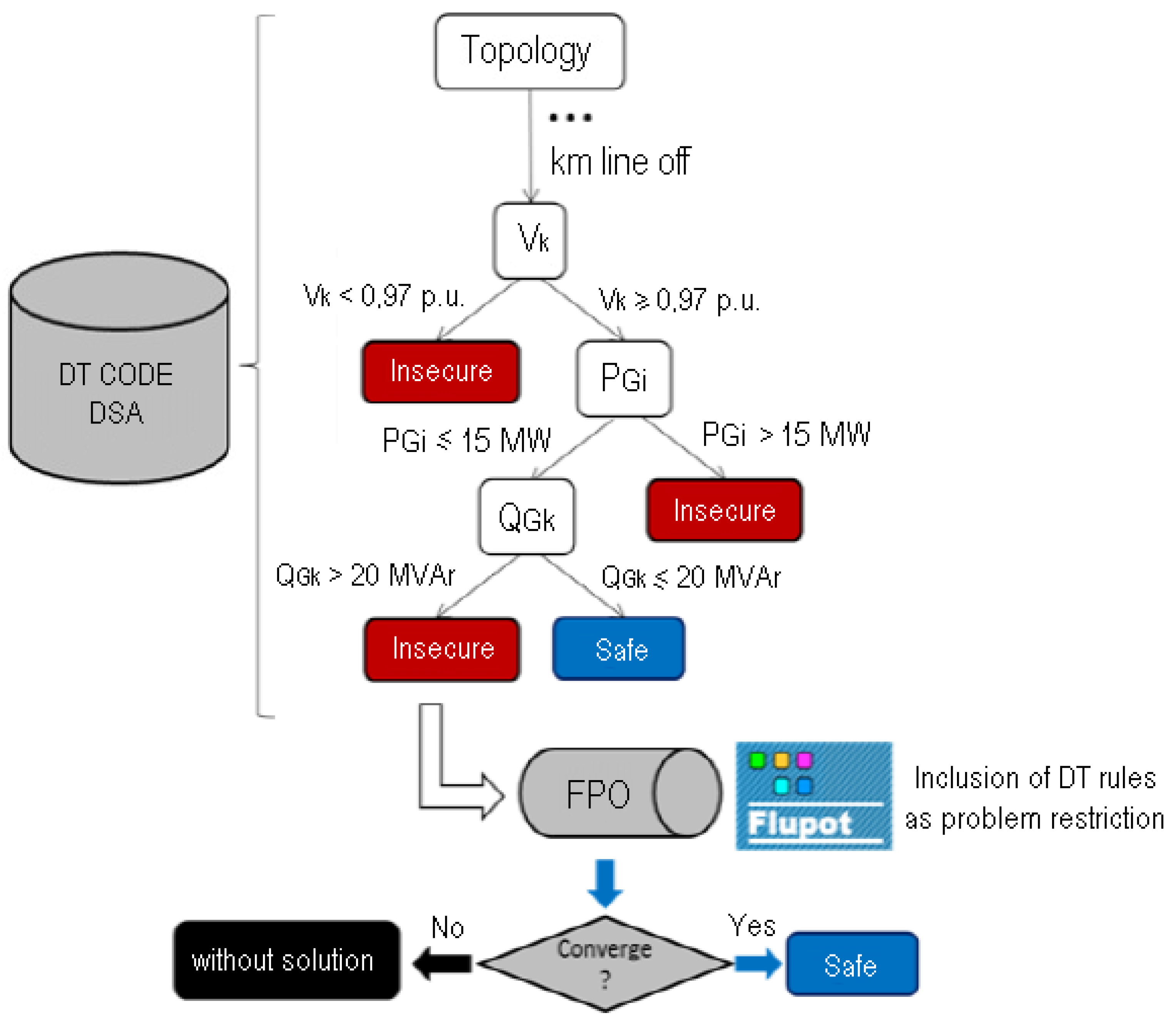
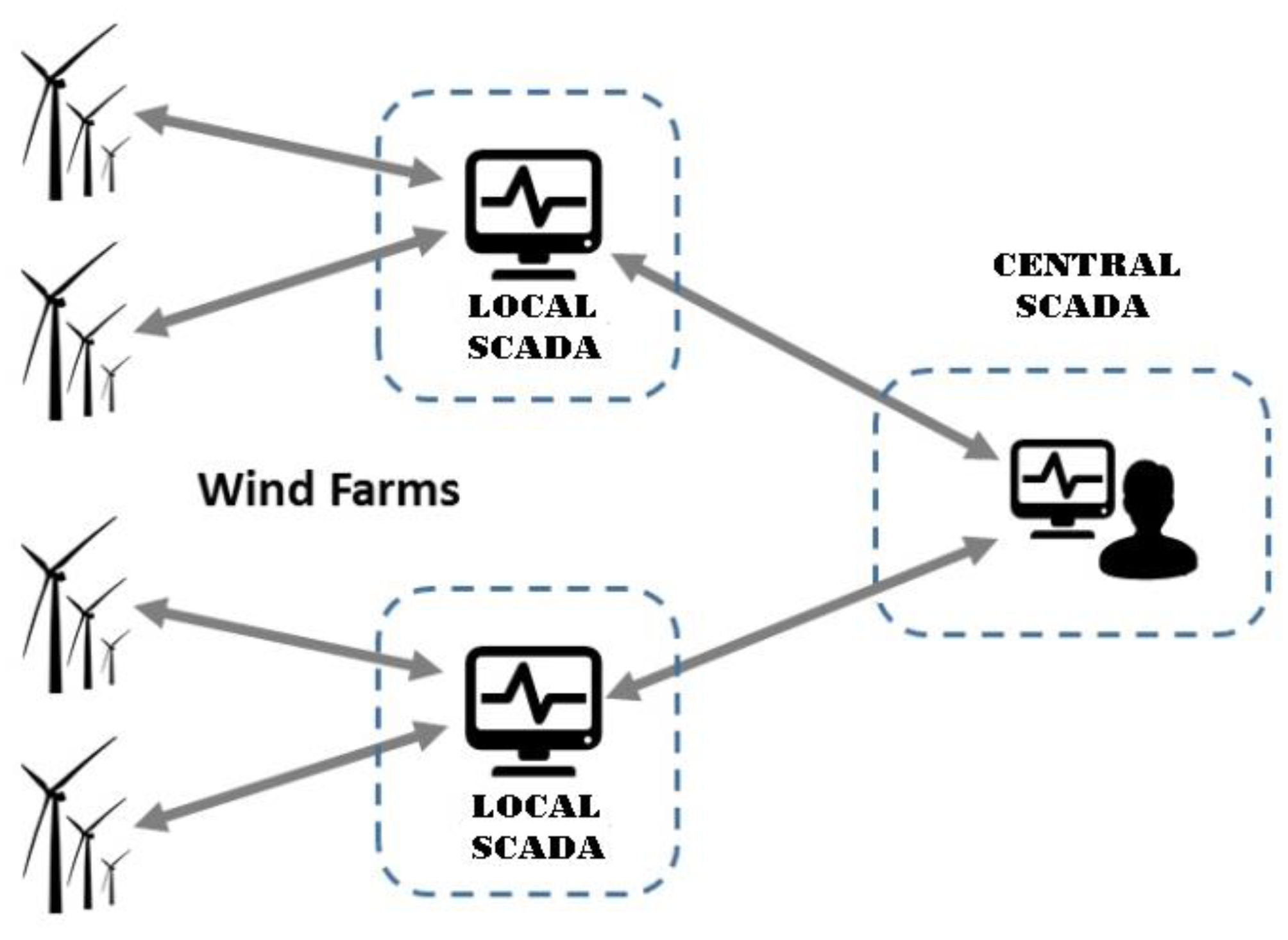
3. Methodology
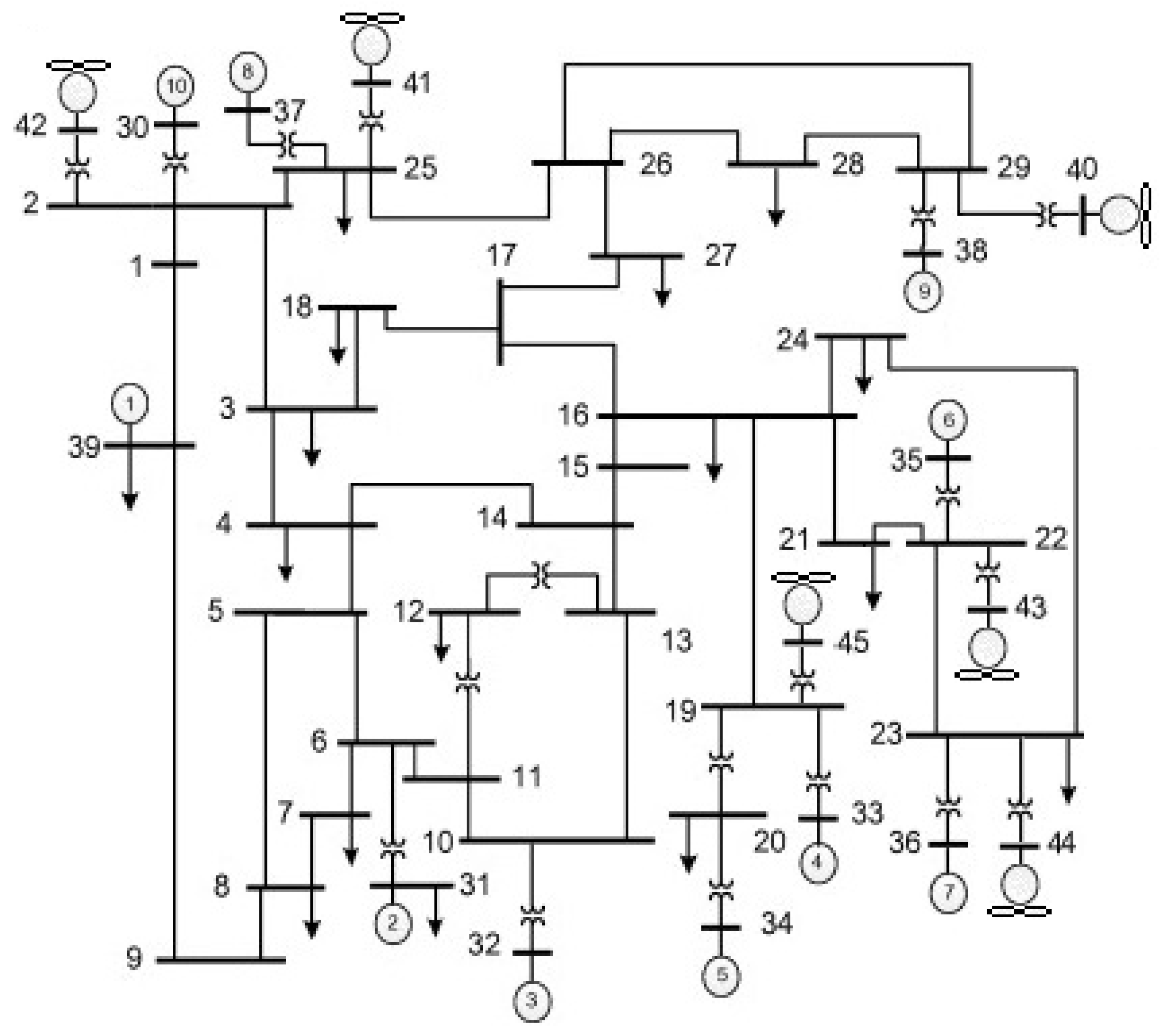
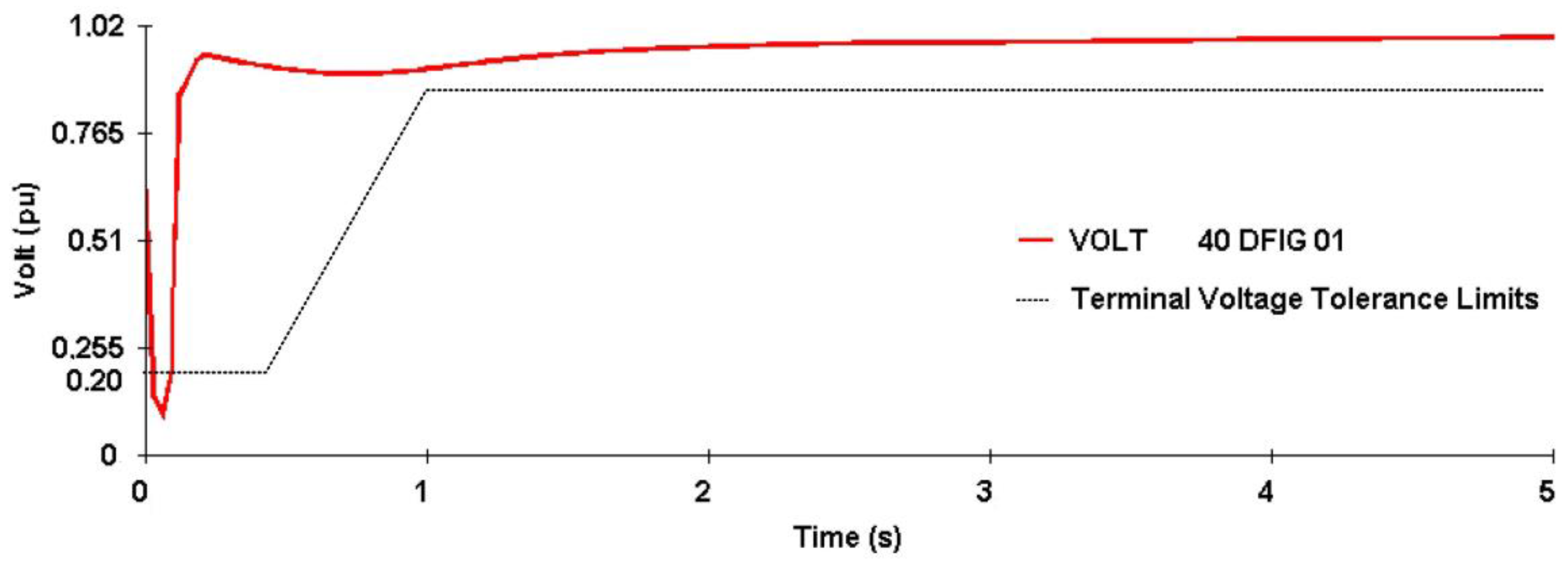
4. Results
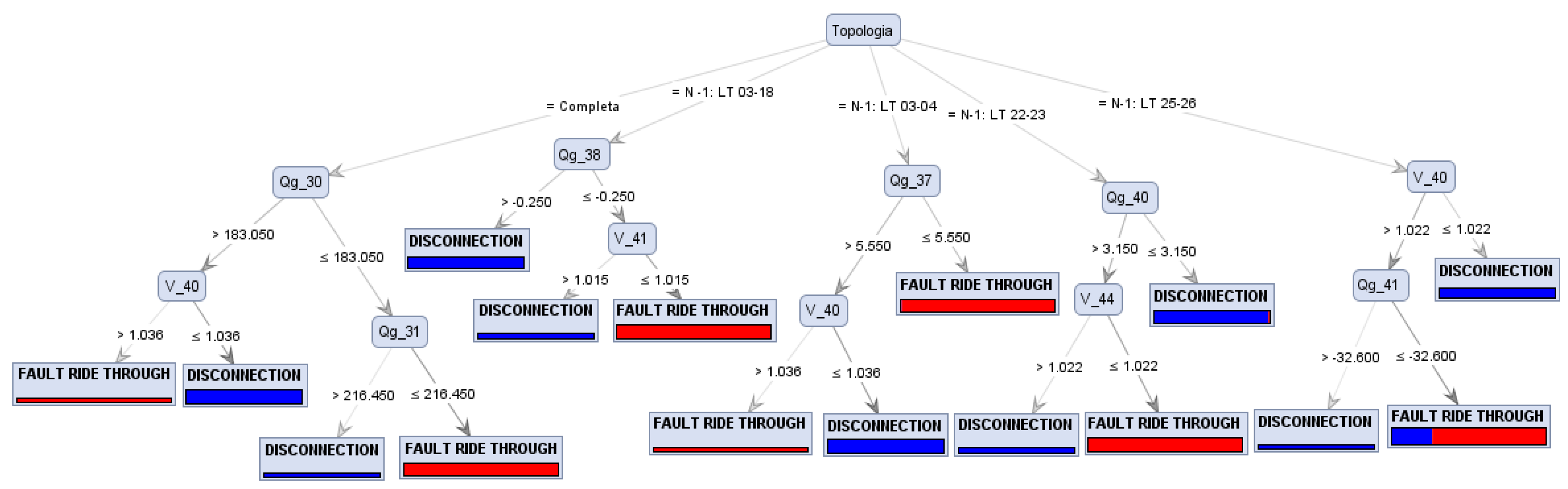
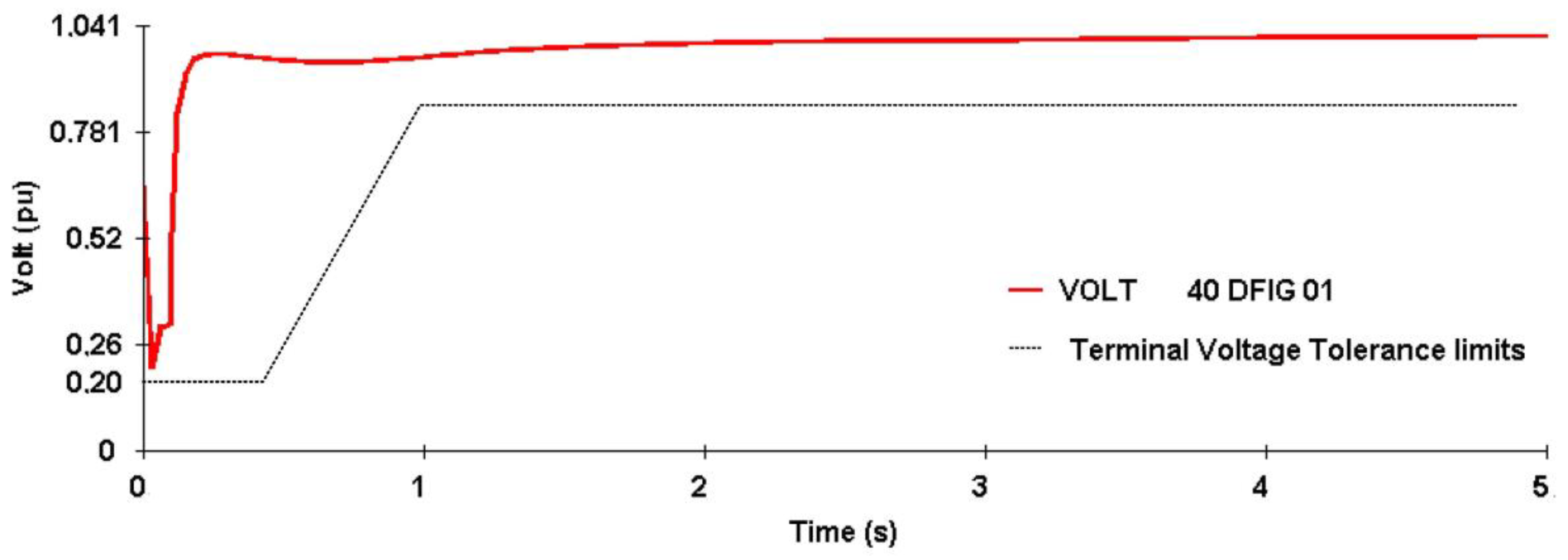
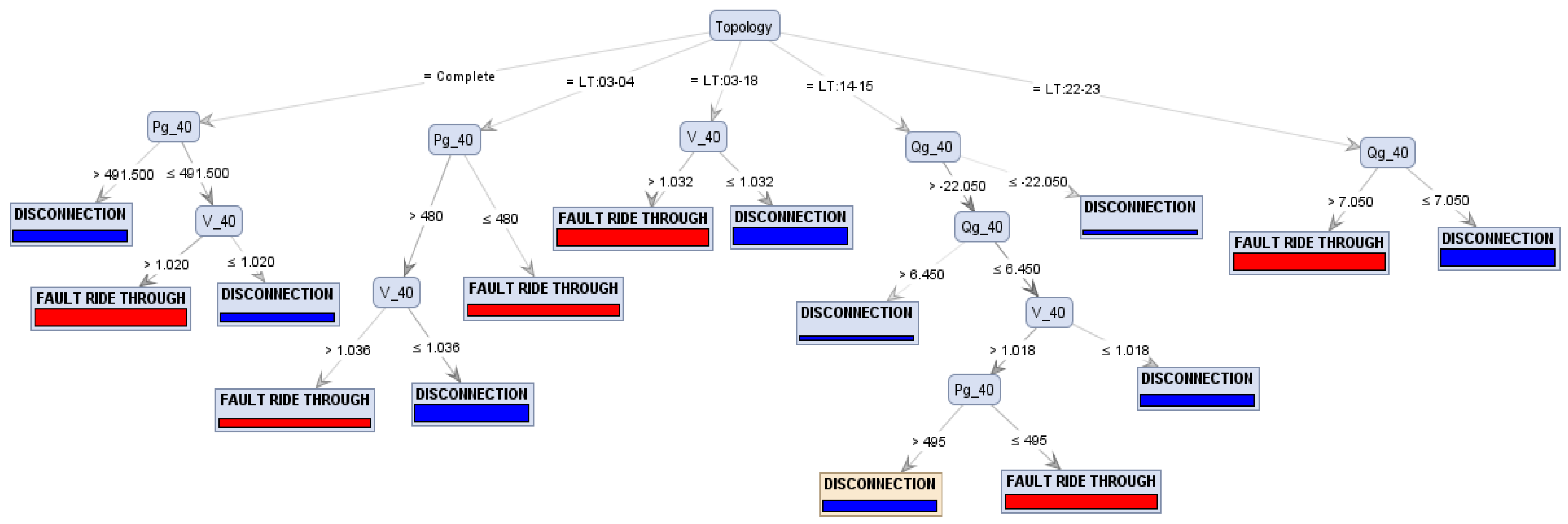
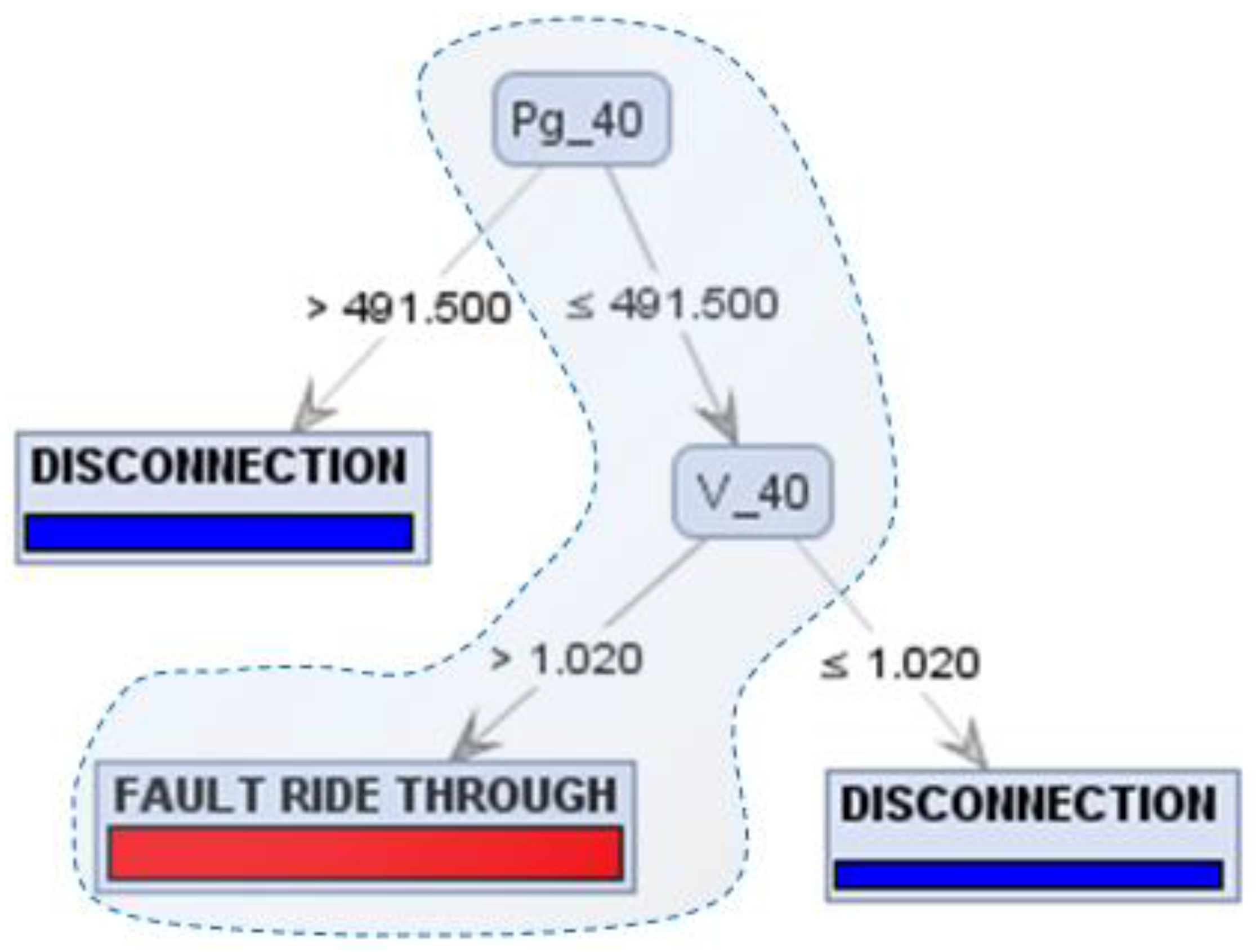
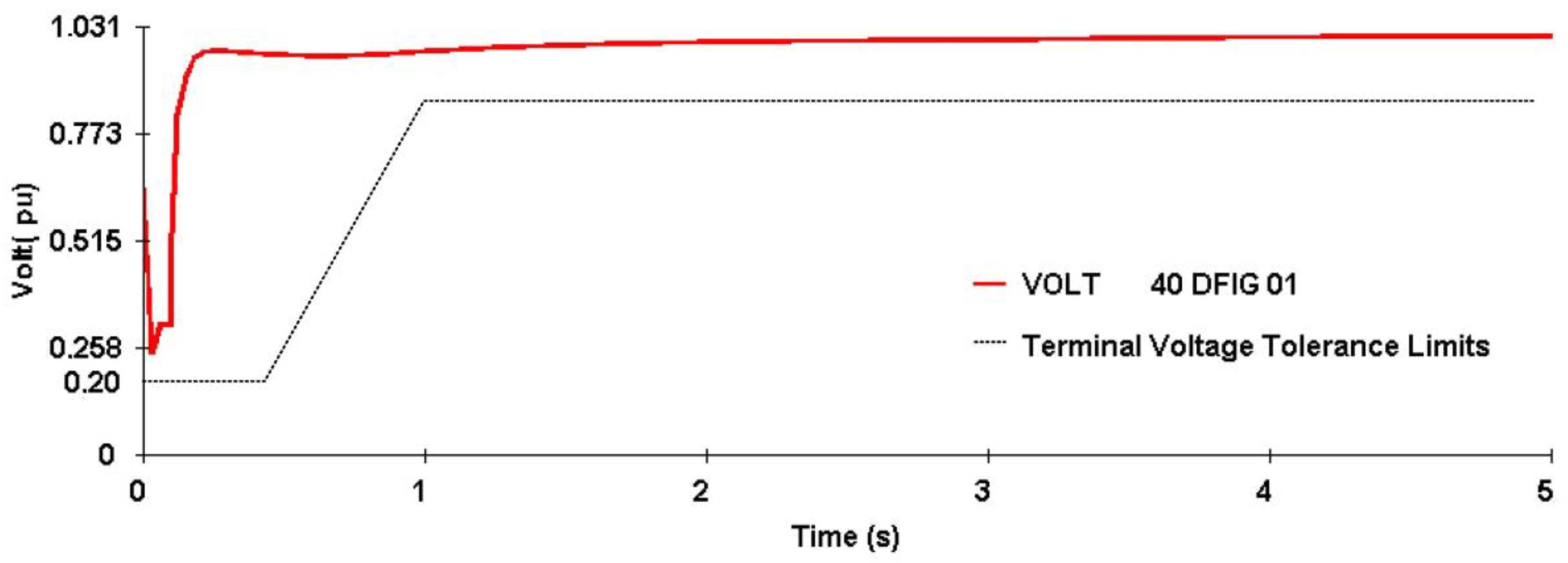
4.1. Case Study of the Preventive Control Application Focusing on the DFIG FRTC—Training and Testing the Systemic Analysis Method
4.2. Case Study of the Preventive Control Application Focusing on the DFIG FRTC—Training and Testing of the Local Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Yang, L.; Yang, G.Y.; Xu, Z.; Dong, Z.Y.; Wong, K.P.; Ma, X. Optimal controller design of a doubly-fed induction generator wind turbine system for small signal stability enhancement. IET Gener. Transm. Distrib. 2010, 4, 579–597. [Google Scholar] [CrossRef]
- Rashid, G.; Ali, M.H. Transient stability enhancement of doubly fed induction machine-based wind generator by bridge-type fault current limiter. IEEE Trans. Energy Convers. 2015, 30, 939–947. [Google Scholar] [CrossRef]
- Tsili, M.; Papathanassiou, S. A review of grid code technical requirements for wind farms. IET Renew. Power Gener. 2009, 3, 308–332. [Google Scholar] [CrossRef]
- Xiang, D.; Ran, L.; Tavner, P.J.; Yang, S. Control of a doubly fed induction generator in a wind turbine during grid fault ride-through. IEEE Trans. Energy Convers. 2006, 21, 652–662. [Google Scholar] [CrossRef]
- Lopez, J.; Sanchis, P.; Gubia, E.; Ursúa, A.; Marroyo, L.; Roboam, X. Control of doubly fed induction generator under symmetrical voltage dips. In Proceedings of the 2008 IEEE International Symposium on Industrial Electronics, Cambridge, UK, 30 June–2 July 2008; pp. 2456–2462. [Google Scholar] [CrossRef]
- Marques, G.D. Active stabilization method for the doubly-fed induction generator using a quadrature inner control loop. In Proceedings of the International Conference on Power Engineering, Energy and Electrical Drives, Setubal, Portugal, 12–14 April 2007; pp. 765–768. [Google Scholar] [CrossRef]
- Abad, G.; López, J.; Rodríguez, M.; Marroyo, L.; Iwanski, G. Doubly Fed Induction Machine: Modeling and Control for Wind Energy Generation; Wiley-IEEE Press: Hoboken, NJ, USA, 2011; ISBN 978-0-470-76865-5. [Google Scholar]
- Gounder, K.; Nanjundappan, D.; Boominathan, V. Enhancement of transient stability of distribution system with SCIG and DFIG based wind farms using STATCOM. IET Renew. Power Gener. 2016, 10, 1171–1180. [Google Scholar] [CrossRef]
- Hossain, M.; Ali, H. Transient stability improvement of doubly fed induction generator based variable speed wind generator using DC resistive fault current limiter. IET Renew. Power Gener. 2016, 10, 150–157. [Google Scholar] [CrossRef]
- Ramirez, D.; Martinez, S.; Platero, A.; Blazquez, F.; De Castro, R.M. Low-voltage ride-through capability for wind generators based on dynamic voltage restorers. IEEE Trans. Energy Convers. 2011, 26, 195–203. [Google Scholar] [CrossRef]
- Okedu, E. Enhancing DFIG wind turbine during three-phase fault using parallel interleaved converters and dynamic resistor. IET Renew. Power Gener. 2016, 10, 1211–1219. [Google Scholar] [CrossRef]
- Rashid, G.; Ali, H. Nonlinear control-based modified BFCL for LVRT capacity enhancement of DFIG based wind farm. IEEE Trans. Energy Convers. 2017, 32, 284–295. [Google Scholar] [CrossRef]
- Shen, W.; Ke, P.; Sun, Z.; Kirschen, D.S.; Qiao, W.; Deng, X.T. Advanced auxiliary control of an energy storage device for transient voltage support of a doubly Fed induction generator. IEEE Trans. Sustain. Energy 2016, 7, 63–76. [Google Scholar] [CrossRef]
- Yunus, A.S.; Abu-Siada, A.; Masoum, M.A. Application of SMES unit to improve DFIG power dispatch and dynamic performance during intermittent misfire and fire-through faults. IEEE Trans. Appl. Supercond. 2013, 23, 5701712. [Google Scholar] [CrossRef]
- Ngamroo, I. Optimization of SMES-FCL for augmenting FRT performance and smoothing output power of grid-connected DFIG wind turbine. IEEE Trans. Appl. Supercond. 2016, 26, 1–5. [Google Scholar] [CrossRef]
- Xiao, X.Y.; Yang, R.H.; Chen, X.Y.; Zheng, Z.X.; Li, C.S. Enhancing fault ride-through capability of DFIG with modified SMES-FCL and RSC control. IET Gener. Transm. Distrib. 2018, 12, 258–266. [Google Scholar] [CrossRef]
- Diao, R.; Vittal, V.; Logic, N. Design of a Real-Time Security Assessment Tool for Situational Awareness Enhancement in Modern Power Systems. IEEE Trans. Power Syst. 2010, 25, 957–965. [Google Scholar] [CrossRef]
- Genc, I.; Diao, R.; Vittal, V.; Kolluri, S.; Mandal, S. Decision Tree-Based Preventive and Corrective Control Applications for Dynamic Security Enhancement in Power Systems. IEEE Trans. Power Syst. 2010, 25, 1611–1619. [Google Scholar] [CrossRef]
- Liu, C.; Sun, K.; Rather, Z.H.; Chen, Z.; Bak, C.L.; Thøgersen, P.; Lund, P. A Systematic Approach for Dynamic Security Assessment and the Corresponding Preventive Control Scheme Based on Decision Trees. IEEE Trans. Power Syst. 2014, 29, 717–730. [Google Scholar] [CrossRef]
- Wehenkel, L.A. Automatic Learning Techniques in Power Systems; Kluwer: Norwell, MA, USA, 1998. [Google Scholar]
- Ullah, N.R.; Thiringer, T.; Karlsson, D. Voltage and Transient Stability Support by Wind Farms Complying with the E.ON Netz Grid Code. IEEE Trans. Power Syst. 2007, 22, 1647–1656. [Google Scholar] [CrossRef]
- Ullah, N.R.; Bhattacharya, K.; Thiringer, T. Wind Farms as Reactive Power Ancillary Service Providers—Technical and Economic Issues. IEEE Trans. Energy Convers. 2009, 24, 661–672. [Google Scholar] [CrossRef]
- Braun, M. Reactive Power Supplied by Wind Energy Converters Cost-Benefit-Analysis. In Proceedings of the EWEC European Wind Energy Conference, Brussels, Belgium, 31 March–3 April 2008. [Google Scholar]
- Engelhardt, S.; Erlich, I.; Feltes, C.; Kretschmann, J.; Shewarega, F. Reactive Power Capability of Wind Turbines Based on Doubly Fed Induction Generators. IEEE Trans. Energy Convers. 2011, 25, 364–372. [Google Scholar] [CrossRef]
- CEPEL. ELETROBRAS: R&D Center in Electrical Energy: ANAREDE-Electrical Networks Analysis Program; User Guide, Version 9.7.2; CEPEL: Rio de Janeiro, Brasil, 2011. [Google Scholar]
- CEPEL. ELETROBRAS: R&D Center in Electrical Energy: ANATEM-Electromagnetic Transient Analysis Program; User Guide, Version 10.4.6; CEPEL: Rio de Janeiro, Brasil, 2012. [Google Scholar]
- ONS. Operador Nacional do Sistema Elétrico. Available online: http://www.ons.org.br (accessed on 20 January 2018).
- Rokach, L.; Maimon, O. Data Mining with Decision Tree: Theory and Applications; World Scientific: River Edge, NJ, USA, 2008. [Google Scholar]
- Hofmann, M.; Klinkenberg, R. RapidMiner: Data Mining Use Cases and Business Analytics Applications; Chapman & Hall/CRC: Boca Raton, FL, USA, 2013. [Google Scholar]





| Topology | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Atribute |
|---|---|---|---|---|---|---|---|---|---|---|
| Complete | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Disconnection |
| Complete | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Fault Ride Through |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Disconnection |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Disconnection |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Fault Ride Through |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Fault Ride Through |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Disconnection |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Fault Ride Through |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Fault Ride Through |
| N-1 | V1 | V2 | Vi | Pg1 | Pg2 | Pgi | Qg1 | Qg2 | Qgi | Disconnection |
| Topology | Vi | Pgi | Qgi | Atribute |
|---|---|---|---|---|
| Complete | Vi | Pgi | Qgi | Disconnection |
| Complete | Vi | Pgi | Qgi | Fault Ride Through |
| N-1 | Vi | Pgi | Qgi | Disconnection |
| N-1 | Vi | Pgi | Qgi | Disconnection |
| N-1 | Vi | Pgi | Qgi | Fault Ride Through |
| N-1 | Vi | Pgi | Qgi | Fault Ride Through |
| N-1 | Vi | Pgi | Qgi | Disconnection |
| N-1 | Vi | Pgi | Qgi | Fault Ride Through |
| N-1 | Vi | Pgi | Qgi | Fault Ride Through |
| N-1 | Vi | Pgi | Qgi | Disconnection |
| Bus Number | Number of Wind Turbines | Maximum Power (MW) |
|---|---|---|
| 40 | 300 | 500 |
| 41 | 180 | 300 |
| 42 | 90 | 150 |
| 43 | 210 | 350 |
| 44 | 180 | 300 |
| 45 | 156 | 260 |
| Accuracy: 98.67% | Real Class | |||
|---|---|---|---|---|
| - | Disconnection | FRTC | Class Precision | |
| Predicted Class | Disconnection | 143 | 01 | 99.31% |
| FRTC | 03 | 153 | 98.08% | |
| Class Recall | 97.95% | 99.35% | - | |
| Accuracy: 100% | Real Class | |||
|---|---|---|---|---|
| - | Disconnection | FRTC | Class Precision | |
| Predicted Class | Disconnection | 161 | 00 | 100% |
| FRTC | 0 | 139 | 100% | |
| Class Recall | 100% | 100% | - | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vieira, D.; Nunes, M.; Bezerra, U. Decision Tree-Based Preventive Control Applications to Enhance Fault Ride Through Capability of Doubly-Fed Induction Generator in Power Systems. Energies 2018, 11, 1760. https://doi.org/10.3390/en11071760
Vieira D, Nunes M, Bezerra U. Decision Tree-Based Preventive Control Applications to Enhance Fault Ride Through Capability of Doubly-Fed Induction Generator in Power Systems. Energies. 2018; 11(7):1760. https://doi.org/10.3390/en11071760
Chicago/Turabian StyleVieira, Dione, Marcus Nunes, and Ubiratan Bezerra. 2018. "Decision Tree-Based Preventive Control Applications to Enhance Fault Ride Through Capability of Doubly-Fed Induction Generator in Power Systems" Energies 11, no. 7: 1760. https://doi.org/10.3390/en11071760





