LoRaWAN-Based Energy-Efficient Surveillance by Drones for Intelligent Transportation Systems
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Our Contribution
- Incorporation of drones in ITS by using them as LoRaWAN gateways.
- Drone modeling and traffic estimation in ITS.
- Intelligent solution for location identification and coverage by drones.
- Energy efficient surveillance and LoRaWAN-based drone communication.
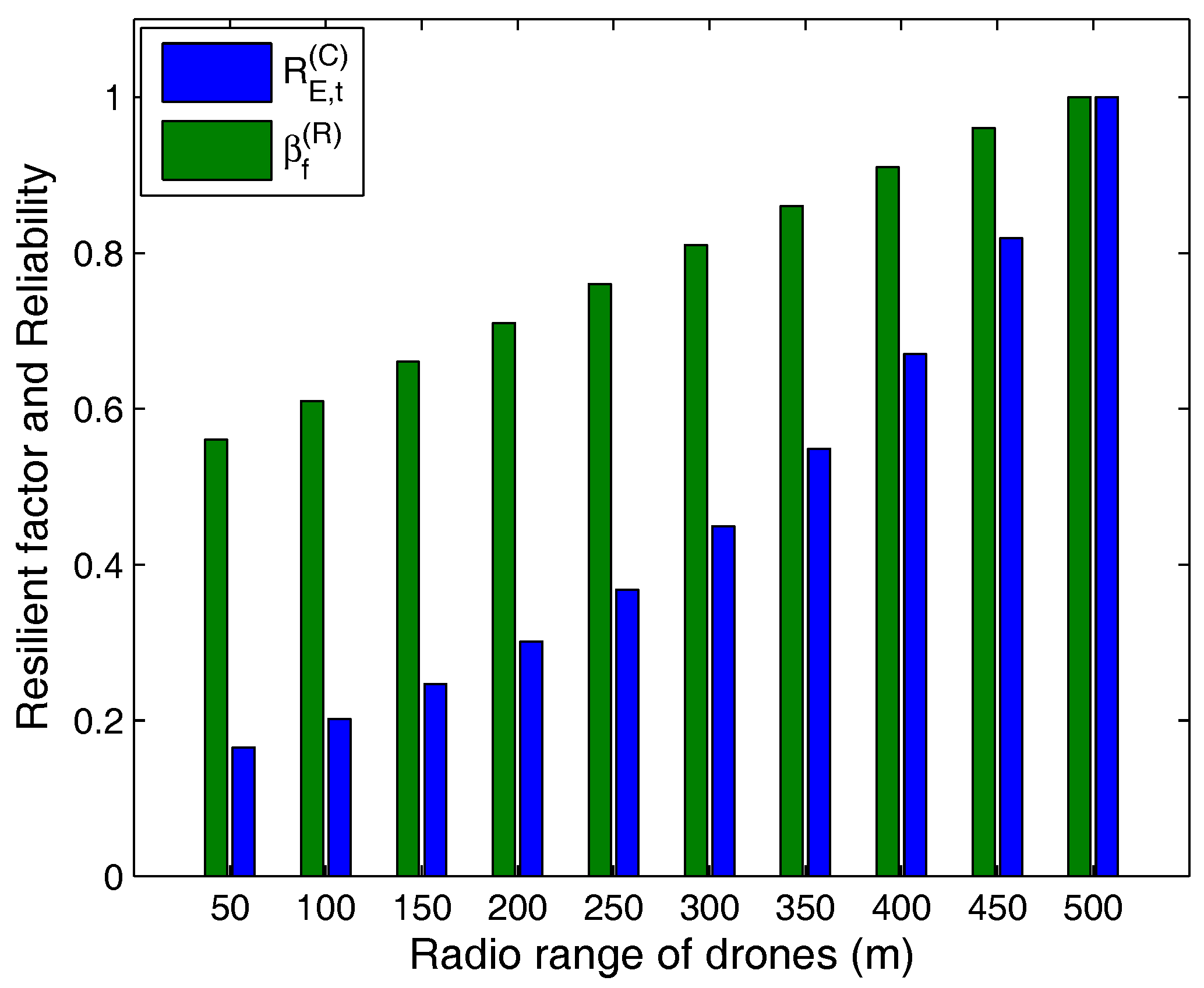
- Resilient factor and fail-safe conditions for drone-based transmissions.
- Numerical case study for performance analysis of the proposed approach.
2. Related Works
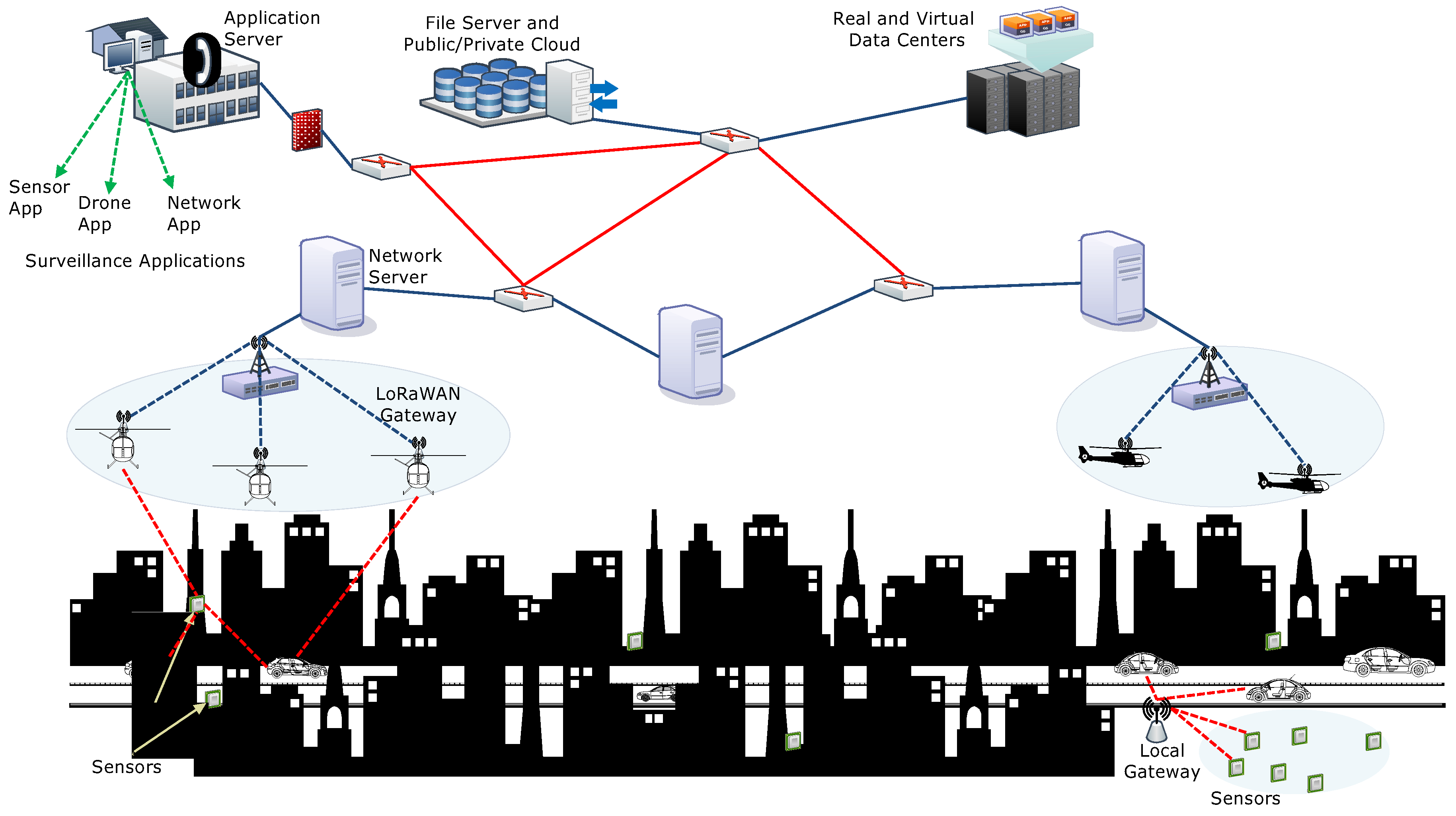
3. Network Model
- Application Server: The application server plays the role of central authority and regulates the data flow in the general LoRaWAN. However, in the proposed model, it is used for delivering applications related to surveillance to the end-users. It supports downloading by an interface, which is classified into sensor App, drones App or network App. Every end-user in the network is assumed to possess all the three Apps that help to communicate with each other.
- Network Server: The network server is the connecting entity between the application servers and the LoRaWAN gateways. A series of network servers helps to expand the network and manages connectivity with the public/private cloud infrastructures. It is capable of managing transmissions with the data centers via real or virtual nodes. Network servers are connected through series of routers with information flow management only at the application server. In the proposed setup, the network servers are used as assigning entity that also checks the performance of the end-user devices, sensors, and actuators.
- LoRaWAN Gateways: The LoRaWAN gateway operates just like any other gateway and provides a bridge between the network servers and the end-users, sensors or locators. Unlike the traditional LoRaWAN gateways with fixed roles, the proposed model uses on-demand drones as LoRaWAN gateways that provide direct connectivity to the end-users. At the moment, the LoRaWAN gateway is divided into two components, which include a set of drones and a switch. The switch helps to localize the drones in the network and checks for incoming connections from other drones. Generally, a network may have switches for different service providers and all the drones respond to their particular switch. Information broadcasting and sharing between the sensors and the end-users via drones is independent of the service provider and depends on the accessibility roles and conditions between them.
- Sensors or Locators: Sensors or locators are the fixed devices in ITS which helps in gathering information across its transmission range and share with the nearest requesting end-user. Sensors or locators also communicate with the drones for long-distance surveillance. This helps in gathering information from any isolated areas. In case, there is no sensor or locator information available, surveillance drones can directly be used for transmissions and accessing geographical information.
- End devices: These are the users which take services from the entire setup and use the information to know the current state of the transportation system. The usability of information by end-users depends on the type of Apps which are used for evaluation as well as the type of services being provided by the service providers. End-users have pre-installed applications that are provided by the centralized application server. It is to be noted that in the proposed approach, the centralized procedures between the end-users and the application servers are only carried during the network initialization. Once a device is registered, there is a limited role of the application server for information accessibility. This makes LoRaWAN on-demand and scalable.
3.1. Drone Modeling
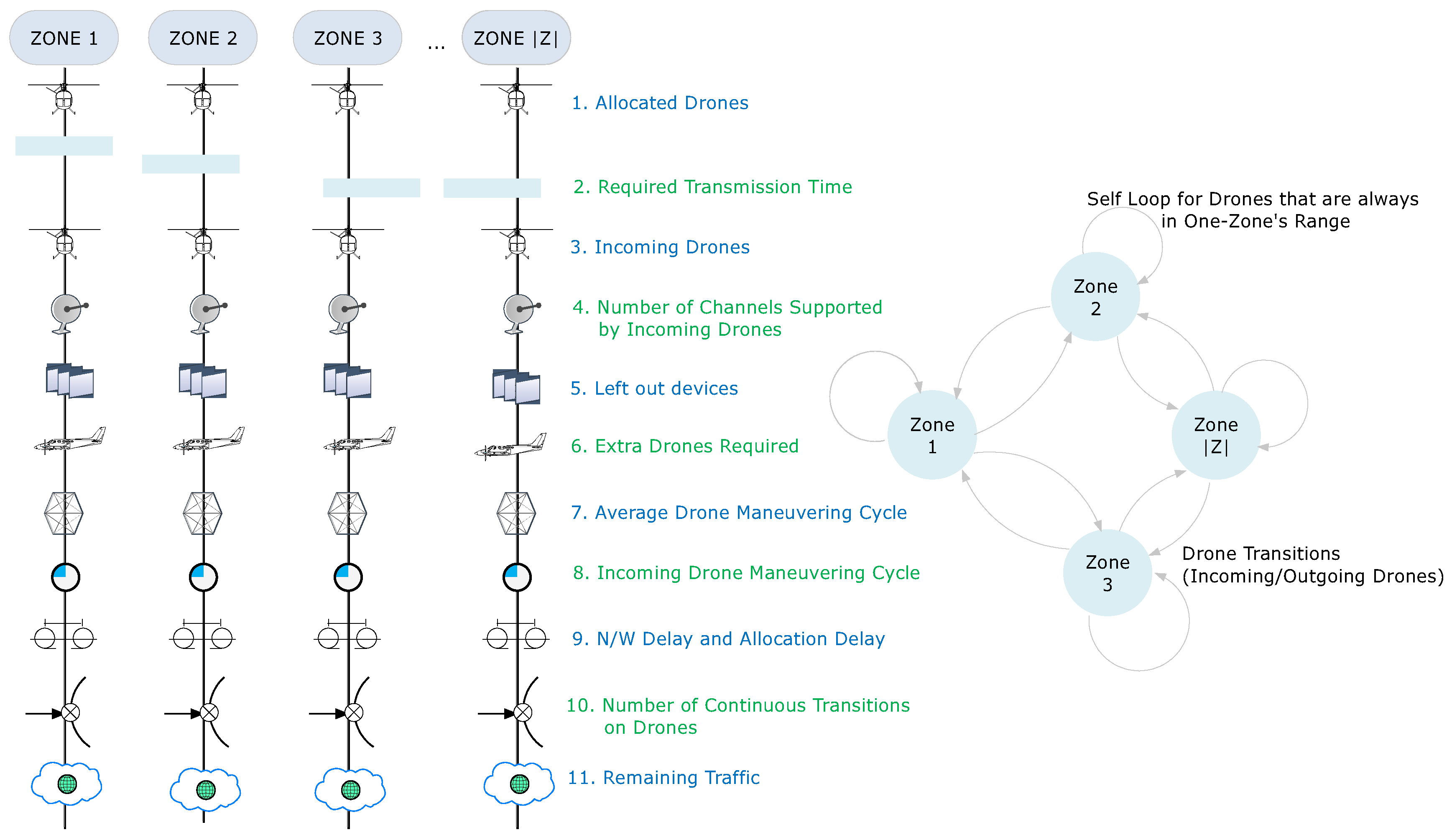
3.2. Traffic and State Estimation
- (i)
- At first, the network is accounted for the number of allocated drones. These are checked for all the zones with communicating entity. The communicating entity can be a sensor, end-user, or another drone.
- (ii)
- Next, the evaluations are conducted for required transmission time by using the above-given formulations. This helps to understand the exact duration for which each drone must be active over all the given zones.
- (iii)
- Next, the details of incoming drones are marked. This is done by understanding the directional maneuvering of each drone and its present location.
- (iv)
- The incoming drones are useful only if they possess a certain number of free channels to support extra sensors from the zones they are entering.
- (v)
- Once the evaluations are done for the number of channels supported by incoming drones, the number of left out devices can be identified on the basis of no connections. Note that failed communications and no-connectivity also refers to a state of being left out.
- (vi)
- This helps to calculate excessive drones required to maintain the connectivity to all and that too at all the instances.
- (vii)
- Now, the excessive requirements for channels can either be resolved by deploying more drones or by understanding the maneuvering cycles of already deployed drones.
- (viii)
- The maneuvering cycles of incoming drones are also identified as this identification helps to understand the state of drones which will leave the current zone during one set of communication (uplink or downlink).
- (ix)
- These cycles help to identify the network delay as well as the allocation delay, which tells about the time required by a drone to reach a particular zone for connectivity.
- (x)
- Next, the number of current transitions on each drone is logged and the current traffic is marked.
- (xi)
- Finally, the remaining traffic is calculated with a stipulated delay after a given number of states. This helps to decide the performance as well as the state of the network by considering new deployment or by improving the maneuvering cycle of each drone.
4. Proposed Approach
4.1. Location Identification and Coverage
| Algorithm 1 Location Identification and Coverage Analysis | |
| 1: | Input: Network components, operational time |
| 2: | Output: Drone allocation |
| 3: | Initialize network and beacon messages |
| 4: | while (Transmission !=Halt) do |
| 5: | Input sensor location () and Drone altitude matrix () |
| 6: | Find drone coordinates w.r.t. sensor field through distance formula and its antenna’s angle of elevation. |
| 7: | Build incidence matrix and share it with other drones |
| 8: | Build adjacency matrix and discard others |
| 9: | Check for overlapping conflicts of coordinates for adjacent drones |
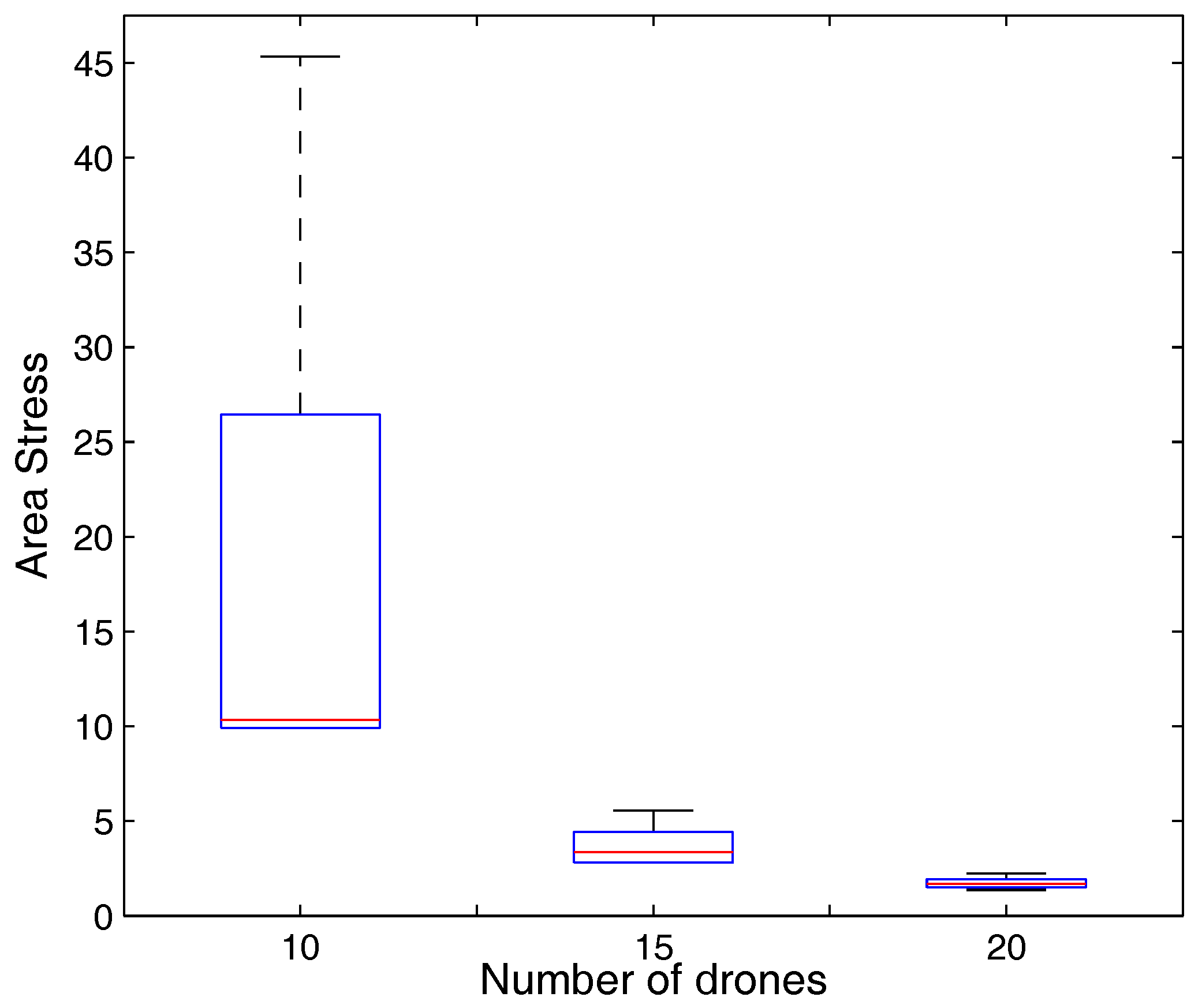
| 10: | Calculate area stress and coverage area using model in Equations (12)–(16) |
| 11: | if (() or ()) then |
| 12: | Reshuffle and re-allocate drones |
| 13: | if (Reshuffle== True && () && ()) then |
| 14: | Continue operations, mark locations, update logs |
| 15: | else |
| 16: | Involve more drones and optimize via energy modeling |
| 17: | end if |
| 18: | else |
| 19: | Exit (−1) or reset |
| 20: | end if |
| 21: | Maintain logs |
| 22: | end while |
4.2. Decision Modeling for Energy Efficient Surveillance
| Algorithm 2 Energy efficient surveillance | |
| 1: | Input: Network components, operational time |
| 2: | Output: Energy efficient surveillance and drone maneuvering |
| 3: | Initialize network and beacon messages |
| 4: | while (Transmission !=Halt) do |
| 5: | Calculate from Equation (19) |
| 6: | Calyculate from Equation (20) |
| 7: | if () && () then |
| 8: | Calculate |
| 9: | if () && (== True) then |
| 10: | Continue with current deployment |
| 11: | else |
| 12: | Mark zones with high energy and |
| 13: | Re-initiate allocation procedures and continue until step 9 holds |
| 14: | if (steps 12 && 13== Success) then |
| 15: | continue and maintain updated logs with fresh incidence and adjacency matrices |
| 16: | else |
| 17: | exit(−1) or reset |
| 18: | end if |
| 19: | end if |
| 20: | else |
| 21: | Perform steps from Algorithm 1 |
| 22: | end if |
| 23: | Maintain logs |
| 24: | end while |
4.3. LoRaWAN-based Drone Model for End to End Communication
| Algorithm 3 LoRaWAN-based Drone Communications for urban-Surveillance | |
| 1: | Input: Network components, system model |
| 2: | Output: Incidence and Adjacency matrices for communication |
| 3: | Initialize network and beacon messages |
| 4: | Evaluate initial system model |
| 5: | ADJ, INJ=Calculate initial adjacency and incidence matrices through Algorithms 1 and 2 |
| 6: | counter=count of links in INJ or ADJ |
| 7: | while (Transmission !=Halt) do |
| 8: | Fetch current time |
| 9: | while (i ≤ counter) do |
| 10: | Calculate using Equation (26) |
| 11: | Calculate using Equation (27) |
| 12: | Calculate and |
| 13: | if then |
| 14: | Mark link and the nodes connected by it |
| 15: | Proceed with new incidence and adjacency matrices |
| 16: | Check for isolation |
| 17: | if (isolation == True) then |
| 18: | exit(−1) or reset model to remove isolation |
| 19: | else |
| 20: | Continue |
| 21: | end if |
| 22: | else |
| 23: | discard node and continue until all the links are not checked |
| 24: | end if |
| 25: | |
| 26: | end while |
| 27: | Communicate and maintain links until conditions in step 13 holds |
| 28: | end while |
| 29: | Maintain logs and build connectivity graph |
| 30: | Share logs with the Application Server |
| 31: | Update database and generate files for analysis |
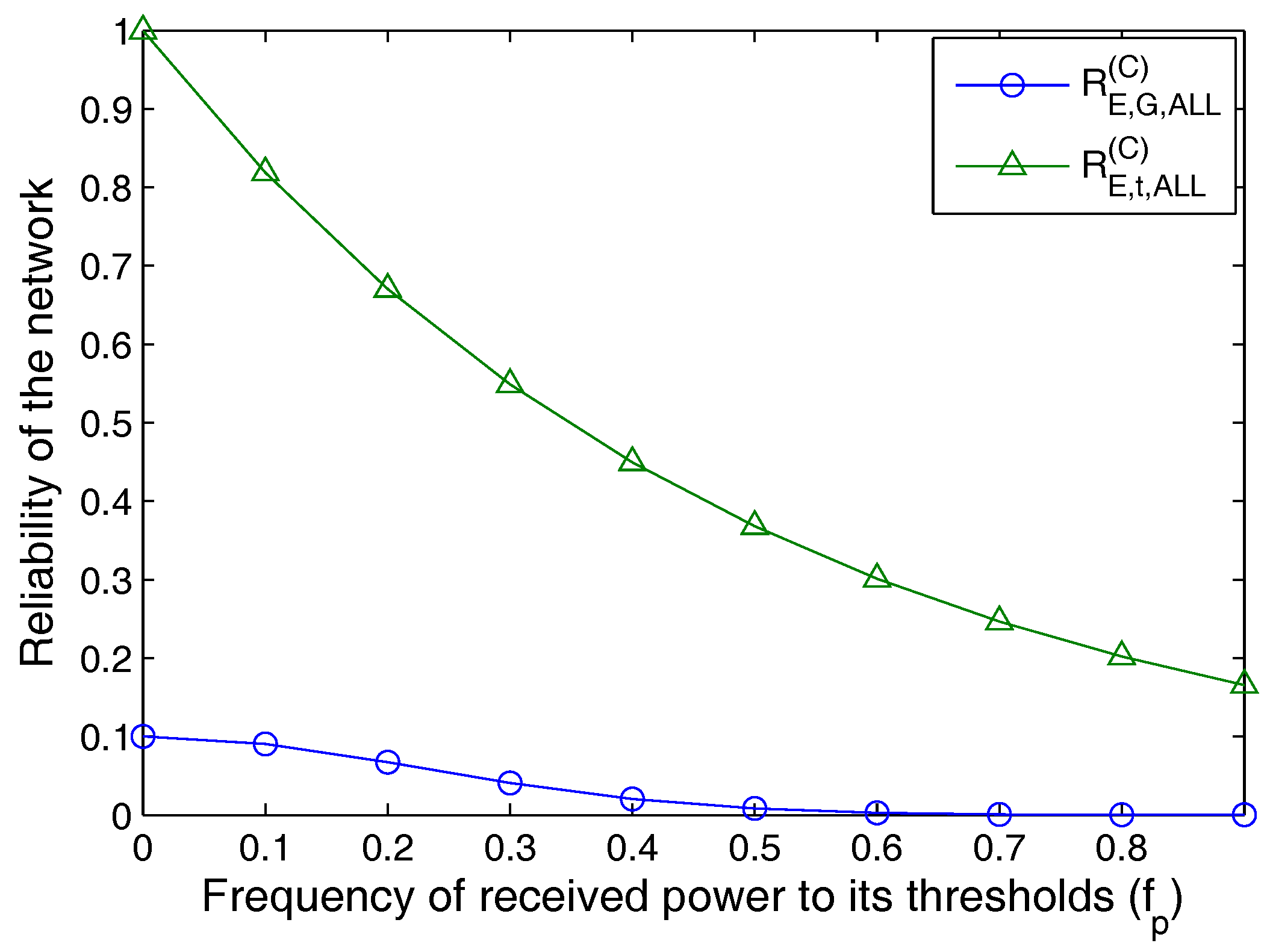
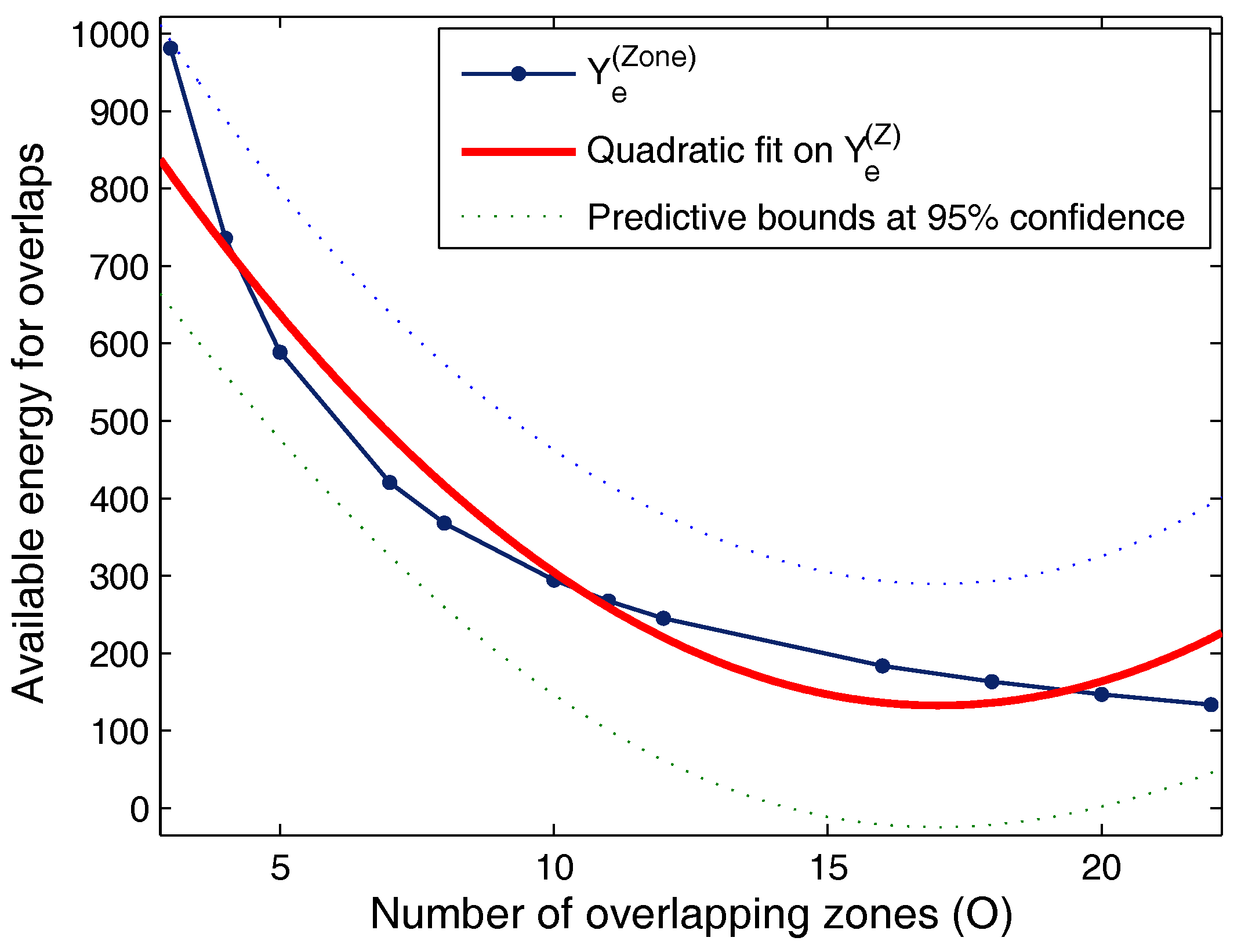
5. Performance Evaluation
6. Comparison with State-of-the-Art Solutions
7. Conclusions and Future Remarks
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zhang, J.; Wang, F.Y.; Wang, K.; Lin, W.H.; Xu, X.; Chen, C. Data-driven intelligent transportation systems: A survey. IEEE Trans. Intell. Transp. Syst. 2011, 12, 1624–1639. [Google Scholar] [CrossRef]
- Lin, Y.; Wang, P.; Ma, M. Intelligent Transportation System (ITS): Concept, Challenge and Opportunity. In Proceedings of the 2017 IEEE 3rd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), Beijing, China, 26–28 May 2017; pp. 167–172. [Google Scholar]
- Saxena, N.; Roy, A.; Sahu, B.J.R.; Kim, H. Efficient IoT Gateway over 5G Wireless: A New Design with Prototype and Implementation Results. IEEE Commun. Mag. 2017, 55, 97–105. [Google Scholar] [CrossRef]
- Arasteh, H.; Hosseinnezhad, V.; Loia, V.; Tommasetti, A.; Troisi, O.; Shafie-khah, M.; Siano, P. Iot-based smart cities: A survey. In Proceedings of the 2016 IEEE 16th International Conference on Environment and Electrical Engineering (EEEIC), Florence, Italy, 7–10 June 2016; pp. 1–6. [Google Scholar]
- Sharma, V.; Song, F.; You, I.; Atiquzzaman, M. Energy efficient device discovery for reliable communication in 5G-based IoT and BSNs using unmanned aerial vehicles. J. Netw. Comput. Appl. 2017, 97, 79–95. [Google Scholar] [CrossRef]
- Luo, Y.; Xiang, Y.; Cao, K.; Li, K. A dynamic automated lane change maneuver based on vehicle-to-vehicle communication. Transp. Res. C Emerg. Technol. 2016, 62, 87–102. [Google Scholar] [CrossRef]
- Liu, X.; Liu, W.; Ma, H.; Fu, H. Large-scale vehicle re-identification in urban surveillance videos. In Proceedings of the 2016 IEEE International Conference on Multimedia and Expo (ICME), Seattle, WA, USA, 11–15 July 2016; pp. 1–6. [Google Scholar]
- Chen, N.; Chen, Y.; You, Y.; Ling, H.; Liang, P.; Zimmermann, R. Dynamic urban surveillance video stream processing using fog computing. In Proceedings of the 2016 IEEE Second International Conference on Multimedia Big Data (BigMM), Taipei, Taiwan, 20–22 April 2016; pp. 105–112. [Google Scholar]
- Jensen, O.B. Drone city-power, design and aerial mobility in the age of “smart cities”. Geogr. Helv. 2016, 71, 67–75. [Google Scholar] [CrossRef]
- Jensen, O.B. New ‘Foucauldian Boomerangs’: Drones and Urban Surveillance. Surveill. Soc. 2016, 14, 20–33. [Google Scholar]
- Ramon, P.; Arrue, B.C.; Acevedo, J.J.; Ollero, A. Visual Surveillance System with Multi-UAVs Under Communication Constrains. In Proceedings of the Robot 2015: Second Iberian Robotics Conference, Lisbon, Portugal, 19–21 November 2016; pp. 705–713. [Google Scholar]
- McNeal, G.S. Drones and the future of aerial surveillance. George Wash. Law Rev. 2016, 84, 354. [Google Scholar]
- Bor-Yaliniz, I.; Yanikomeroglu, H. The new frontier in RAN heterogeneity: Multi-tier drone-cells. IEEE Commun. Mag. 2016, 54, 48–55. [Google Scholar] [CrossRef]
- Zema, N.R.; Mitton, N.; Ruggeri, G. Using location services to autonomously drive flying mobile sinks in wireless sensor networks. In Proceedings of the International Conference on Ad Hoc Networks, Benidorm, Spain, 22–27 June 2014; pp. 180–191. [Google Scholar]
- Erdelj, M.; Król, M.; Natalizio, E. Wireless sensor networks and multi-UAV systems for natural disaster management. Comput. Netw. 2017, 124, 72–86. [Google Scholar] [CrossRef]
- Sharma, V.; You, I.; Leu, F.; Atiquzzaman, M. Secure and efficient protocol for fast handover in 5G mobile Xhaul networks. J. Netw. Comput. Appl. 2018, 102, 38–57. [Google Scholar] [CrossRef]
- Desnitsky, V.; Levshun, D.; Chechulin, A.; Kotenko, I.V. Design Technique for Secure Embedded Devices: Application for Creation of Integrated Cyber-Physical Security System. JoWUA 2016, 7, 60–80. [Google Scholar]
- Carniani, E.; Costantino, G.; Marino, F.; Martinelli, F.; Mori, P. Enhancing Video Surveillance with Usage Control and Privacy-Preserving Solutions. JoWUA 2016, 7, 20–40. [Google Scholar]
- Baiardi, F.; Tonelli, F.; Isoni, L. Application Vulnerabilities in Risk Assessment and Management. JoWUA 2016, 7, 41–59. [Google Scholar]
- Sharma, V.; Bennis, M.; Kumar, R. UAV-assisted heterogeneous networks for capacity enhancement. IEEE Commun. Lett. 2016, 20, 1207–1210. [Google Scholar] [CrossRef]
- Sharma, V.; Sabatini, R.; Ramasamy, S. UAVs assisted delay optimization in heterogeneous wireless networks. IEEE Commun. Lett. 2016, 20, 2526–2529. [Google Scholar] [CrossRef]
- Sharma, V.; Kumar, R. A cooperative network framework for multi-UAV guided ground ad hoc networks. J. Intell. Robot. Syst. 2015, 77, 629–652. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Huang, X.; Tang, S.; Xiang, Y.; Hassan, M.M.; Alelaiwi, A. Secure distributed deduplication systems with improved reliability. IEEE Trans. Comput. 2015, 64, 3569–3579. [Google Scholar] [CrossRef]
- Chen, X.; Li, J.; Weng, J.; Ma, J.; Lou, W. Verifiable computation over large database with incremental updates. IEEE Trans. Comput. 2016, 65, 3184–3195. [Google Scholar] [CrossRef]
- Cai, J.; Wang, Y.; Liu, Y.; Luo, J.Z.; Wei, W.; Xu, X. Enhancing network capacity by weakening community structure in scale-free network. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Li, M.; Li, J.; Lee, P.; Lou, W. Secure Deduplication with Efficient and Reliable Convergent Key Management. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1615–1625. [Google Scholar] [CrossRef]
- Hakiri, A.; Berthou, P.; Gokhale, A.; Abdellatif, S. Publish/subscribe-enabled software defined networking for efficient and scalable IoT communications. IEEE Commun. Mag. 2015, 53, 48–54. [Google Scholar] [CrossRef]
- Shin, D.; Sharma, V.; Kim, J.; Kwon, S.; You, I. Secure and Efficient Protocol for Route Optimization in PMIPv6-Based Smart Home IoT Networks. IEEE Access 2017, 5, 11100–11117. [Google Scholar] [CrossRef]
- Wei, Z.; Zhao, B. A Space Information Service Forwarding Mechnism Based on Software Defined Network. J. Internet Serv. Inf. Secur. 2017, 7, 48–60. [Google Scholar]
- Li, G.; Zhou, H.; Li, G.; Feng, B. Application-aware and Dynamic Security Function Chaining for Mobile Networks. J. Internet Serv. Inf. Secur. 2017, 7, 21–34. [Google Scholar]
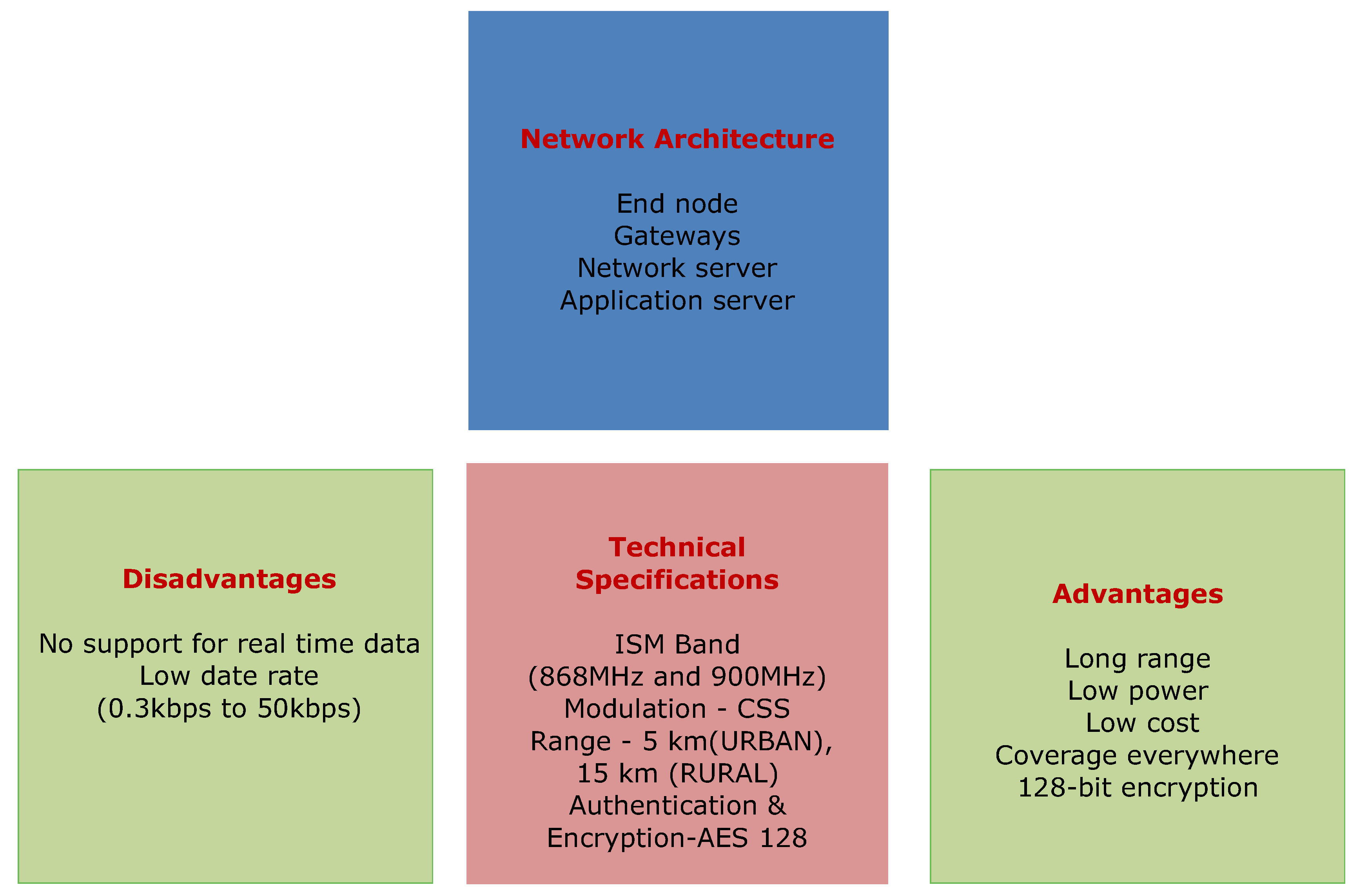
- Neumann, P.; Montavont, J.; Noël, T. Indoor deployment of low-power wide area networks (LPWAN): A LoRaWAN case study. In Proceedings of the 2016 IEEE 12th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), New York, NY, USA, 17–19 October 2016; pp. 1–8. [Google Scholar]
- Bardyn, J.P.; Melly, T.; Seller, O.; Sornin, N. IoT: The era of LPWAN is starting now. In Proceedings of the 42nd European Solid-State Circuits Conference (ESSCIRC Conference 2016), Lausanne, Switzerland, 12–15 September 2016; pp. 25–30. [Google Scholar]
- Sanchez-Iborra, R.; Gamez, J.S.; Santa, J.; Fernandez, P.J.; Skarmeta, A.F. Integrating LP-WAN Communications within the Vehicular Ecosystem. J. Internet Serv. Inf. Secur. 2017, 7, 45–56. [Google Scholar]
- Garcia, D.; Marin, R.; Kandasamy, A.; Pelov, A. LoRaWAN Authentication in RADIUS Draft-Garcia-Radext-Radius-Lorawan-03. 2 May 2017. Available online: https://www.ietf.org/archive/id/draft-garcia-radext-radius-lorawan-03.txt (accessed on 26 December 2017).
- Garcia, D.; Marin, R.; Kandasamy, A.; Pelov, A. LoRaWAN Authentication in Diameter Draft-Garcia-Dime-Diameter-Lorawan-00. 30 May 2016. Available online: https://tools.ietf.org/html/draft-garcia-dime-diameter-lorawan-00 (accessed on 26 December 2017).
- LoRa Alliance Technology. Available online: https://www.lora-alliance.org/technology (accessed on 25 January 2018).
- Casals, L.; Mir, B.; Vidal, R.; Gomez, C. Modeling the Energy Performance of LoRaWAN. Sensors 2017, 17, 2364. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016; pp. 1–7. [Google Scholar]
- Sornin, N.; Luis, M.; Eirich, T.; Kramp, T.; Hersent, O. LoRaWAN Specification V1.0.2; Technical Report; LoRa Alliance: Beaverton, OR, USA, 2016. [Google Scholar]
- Motlagh, N.H.; Bagaa, M.; Taleb, T. UAV-Based IoT Platform: A Crowd Surveillance Use Case. IEEE Commun. Mag. 2017, 55, 128–134. [Google Scholar] [CrossRef]
- Wu, D.; Arkhipov, D.I.; Kim, M.; Talcott, C.L.; Regan, A.C.; McCann, J.A.; Venkatasubramanian, N. ADDSEN: Adaptive data processing and dissemination for drone swarms in urban sensing. IEEE Trans. Comput. 2017, 66, 183–198. [Google Scholar] [CrossRef]
- Naqvi, S.A.R.; Hassan, S.A.; Pervaiz, H.; Ni, Q. Drone-Aided Communication as a Key Enabler for 5G and Resilient Public Safety Networks. IEEE Commun. Mag. 2018, 56, 36–42. [Google Scholar] [CrossRef]
- Menouar, H.; Guvenc, I.; Akkaya, K.; Uluagac, A.S.; Kadri, A.; Tuncer, A. UAV-Enabled Intelligent Transportation Systems for the Smart City: Applications and Challenges. IEEE Commun. Mag. 2017, 55, 22–28. [Google Scholar]
- Zeng, Y.; Zhang, R. Energy-efficient UAV communication with trajectory optimization. IEEE Trans. Wirel. Commun. 2017, 16, 3747–3760. [Google Scholar] [CrossRef]
- Sharma, V.; You, I.; Kumar, R. Energy efficient data dissemination in multi-UAV coordinated wireless sensor networks. Mob. Inf. Syst. 2016, 2016, 8475820. [Google Scholar] [CrossRef]
- Trotta, A.; D’Andreagiovanni, F.; Di Felice, M.; Natalizio, E.; Chowdhury, K.R. When UAVs Ride A Bus: Towards Energy-efficient City-scale Video Surveillance. In Proceedings of the 2018 IEEE International Conference on Computer Communications (INFOCOM), Honolulu, HI, USA, 16–19 April 2018. [Google Scholar]
- Mathur, S.; Sankar, A.; Prasan, P.; Iannucci, B. Energy Analysis of LoRaWAN Technology for Traffic Sensing Applications. In Proceedings of the Intelligent Transportation Society of America (ITS) World Congress, Montréal, QC, Canada, 29 October–2 November 2017; Available online: https://works.bepress.com/bob/34/ (accessed on 25 January 2018).
- Adame Vázquez, T.; Barrachina-Muñoz, S.; Bellalta, B.; Bel, A. HARE: Supporting Efficient Uplink Multi-Hop Communications in Self-Organizing LPWANs. Sensors 2018, 18, 115. [Google Scholar] [CrossRef] [PubMed]
- Kennington, J.; Olinick, E.; Rajan, D. Wireless Network Design: Optimization Models and Solution Procedures; Springer: New York, NY, USA, 2010; ISBN 978-1-4419-6111-2. [Google Scholar]
- Bauschert, T.; Busing, C.; D’Andreagiovanni, F.; Koster, A.C.; Kutschka, M.; Steglich, U. Network planning under demand uncertainty with robust optimization. IEEE Commun. Mag. 2014, 52, 178–185. [Google Scholar] [CrossRef]
- Chiaraviglio, L.; Amorosi, L.; Cartolano, S.; Blefari-Melazzi, N.; Dell’Olmo, P.; Shojafar, M.; Salsano, S. Optimal superfluid management of 5G networks. In Proceedings of the 2017 IEEE Conference on Network Softwarization (NetSoft), Bologna, Italy, 3–7 July 2017; pp. 1–9. [Google Scholar]
- Shojafar, M.; Chiaraviglio, L.; Blefari-Melazzi, N.; Salsano, S. P5G: A bio-inspired algorithm for the superfluid management of 5G Networks. In Proceedings of the 18th IEEE GLOBECOM, Singapore, 4–8 December 2017; pp. 4–8. [Google Scholar]
- D’Andreagiovanni, F.; Mannino, C.; Sassano, A. GUB covers and power-indexed formulations for wireless network design. Manag. Sci. 2013, 59, 142–156. [Google Scholar] [CrossRef]
- D’Andreagiovanni, F.; Mett, F.; Nardin, A.; Pulaj, J. Integrating LP-guided variable fixing with MIP heuristics in the robust design of hybrid wired-wireless FTTx access networks. Appl. Soft Comput. 2017, 61, 1074–1087. [Google Scholar] [CrossRef]
- Garofalaki, Z.; Kallergis, D.; Katsikogiannis, G.; Douligeris, C. A Policy-Aware Model for Intelligent Transportation Systems. arXiv, 2017; arXiv:1706.04803. [Google Scholar]
- Sharma, V.; Chen, H.C.; Kumar, R. Driver behaviour detection and vehicle rating using multi-UAV coordinated vehicular networks. J. Comput. Syst. Sci. 2017, 86, 3–32. [Google Scholar] [CrossRef]
- Portelinha Júnior, F.M.; Carlos Zambroni de Souza, A.; Castilla, M.; Queiroz Oliveira, D.; Ribeiro, P.F. Control Strategies for Improving Energy Efficiency and Reliability in Autonomous Microgrids with Communication Constraints. Energies 2017, 10, 1443. [Google Scholar] [CrossRef]
- Afzal, B.; Alvi, S.A.; Shah, G.A.; Mahmood, W. Energy efficient context aware traffic scheduling for IoT applications. Ad Hoc Netw. 2017, 62, 101–115. [Google Scholar] [CrossRef]
- Memos, V.A.; Psannis, K.E.; Ishibashi, Y.; Kim, B.G.; Gupta, B. An Efficient Algorithm for Media-based Surveillance System (EAMSuS) in IoT Smart City Framework. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Zhang, B.; Liu, C.H.; Tang, J.; Xu, Z.; Ma, J.; Wang, W. Learning-based Energy-Efficient Data Collection by Unmanned Vehicles in Smart Cities. IEEE Trans. Ind. Inform. 2017. [Google Scholar] [CrossRef]
- Magrin, D.; Centenaro, M.; Vangelista, L. Performance evaluation of LoRa networks in a smart city scenario. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar]
- Cuomo, F.; Campo, M.; Caponi, A.; Bianchi, G.; Rossini, G.; Pisani, P. EXPLoRa: Extending the performance of LoRa by suitable spreading factor allocations. In Proceedings of the 2017 IEEE 13th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Rome, Italy, 9–11 October 2017; pp. 1–8. [Google Scholar]
- Chen, M.; Mozaffari, M.; Saad, W.; Yin, C.; Debbah, M.; Hong, C.S. Caching in the sky: Proactive deployment of cache-enabled unmanned aerial vehicles for optimized quality-of-experience. IEEE J. Sel. Areas Commun. 2017, 35, 1046–1061. [Google Scholar] [CrossRef]
- Weibull Reliability. Available online: http://www.weibull.com/hotwire/issue151/hottopics151.htm (accessed on 18 January 2018).
- Miller, R.G., Jr. Survival Analysis; John Wiley & Sons: Chichester, UK; New York, NY, USA, 2011; Volume 66. [Google Scholar]
- Maunder, E.; Moitinho de Almeida, J.; Ramsay, A. Visualisation of Stress Fields—From Stress Trajectories to Strut & Tie Models. In Proceedings of the 10th Annual Conference of the Association for Computational Mechanics in Engineering, Swansea, WA, USA, 14–17 April 2002; pp. 31–34. [Google Scholar]
- Peterson, R.E.; Peterson, R. Stress Concentration Factors; John Wiley and Sons: Hoboken, NJ, USA, 1967. [Google Scholar]
- Finkelstein, M. Failure Rate Modelling for Reliability and Risk; Springer Science & Business Media: London, UK, 2008. [Google Scholar]
- Mikhaylov, K.; Petaejaejaervi, J.; Haenninen, T. Analysis of capacity and scalability of the LoRa low power wide area network technology. In Proceedings of the 22th European Wireless Conference, Oulu, Finland, 18–20 May 2016; pp. 1–6. [Google Scholar]
- Sharma, V.; Kumar, R. Cooperative frameworks and network models for flying ad hoc networks: A survey. Concurr. Comput. Pract. Exp. 2017, 29, e3931. [Google Scholar] [CrossRef]
- Reda, H.T.; Daely, P.T.; Kharel, J.; Shin, S.Y. On the application of IoT: Meteorological information display system based on LoRa wireless communication. IETE Tech. Rev. 2017. [Google Scholar] [CrossRef]
- Pham, C. Low-cost, low-power and long-range image sensor for visual surveillance. In Proceedings of the 2nd Workshop on Experiences in the Design and Implementation of Smart Objects, New York, NY, USA, 3–7 October 2016; pp. 35–40. [Google Scholar]
- Zhan, W.; Wang, W.; Chen, N.; Wang, C. Efficient UAV path planning with multiconstraints in a 3D large battlefield environment. Math. Prob. Eng. 2014, 2014, 597092. [Google Scholar] [CrossRef]
- Samad, T.; Bay, J.S.; Godbole, D. Network-centric systems for military operations in urban terrain: The role of UAVs. Proc. IEEE 2007, 95, 92–107. [Google Scholar] [CrossRef]
- Xu, B.; Xu, X.; Own, C.M. On the feature detection of nonconforming objects with automated drone surveillance. In Proceedings of the 3rd International Conference on Communication and Information Processing, Tokyo, Japan, 24–26 November 2017; pp. 484–489. [Google Scholar]
- Ding, G.; Wu, Q.; Zhang, L.; Lin, Y.; Tsiftsis, T.A.; Yao, Y.D. An Amateur Drone Surveillance System Based on the Cognitive Internet of Things. IEEE Commun. Mag. 2018, 56, 29–35. [Google Scholar] [CrossRef]
- Scherer, J.; Rinner, B. Short and full horizon motion planning for persistent multi-UAV surveillance with energy and communication constraints. In Proceedings of the 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Vancouver, BC, Canada, 24–28 September 2017; pp. 230–235. [Google Scholar]



| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| Signal to interference plus noise ratio | t | Transmission time | |
| Transmission power | Area under coverage | ||
| Antenna constant | Sensors in a zone | ||
| Transmission range | Set of zones | ||
| Spectral density of the network | Uplink time | ||
| Path loss exponent | Downlink time | ||
| Set of network servers | Mean lifetime | ||
| Set of data centers | Remaining energy of an entity | ||
| Set of cloud servers | Initial energy of an entity | ||
| Set of drones | Wait time for a drone | ||
| Set of users | Velocity of a drone | ||
| Set of switches | Radio range of a drone | ||
| Set of sensors or locators | Minimum active time for a drone | ||
| Path loss exponent for LoS | Area stress | ||
| Path loss exponent for NLoS | Range of a particular entity | ||
| Received power for NLoS | Coverage area | ||
| Received power for LoS | Number of overlaps | ||
| Shadowing component | Distance between centers of overlapping zones | ||
| Path length | Energy requirements of a zone | ||
| Transmission distance | Predicted energy requirements | ||
| Path loss at reference distance | Number of channels for end users | ||
| Path loss for an obstacle | Number of channels for sensors | ||
| Reliability of an entity | Processing energy | ||
| Failure factor | Transmitting energy | ||
| Number of concurrent channels | Energy loss due to interference | ||
| Number of states | Energy consumed in idle phase | ||
| Failure distribution function | Error rate for energy difference | ||
| Probability of failure of an entity | Resilient factor | ||
| Expected future lifetime of an entity | Fail safe metric (Probability of no failure) | ||
| Total connected devices with an entity | Number of entities operating in a given drone zone and number of entities a drone can support |
| Symbol | Value | Symbol | Value |
|---|---|---|---|
| 30 dBm | t | 200 s | |
| −11 dB | 2500 × 2500 sq.m. | ||
| 500 m | 50 | ||
| −174 dBm/Hz | 10 | ||
| 4 | 10 s | ||
| 10 | 5 s | ||
| 5 | 0.3 | ||
| 2 | 2000 J | ||
| 20 | 30 kmph | ||
| 500 | 500 m | ||
| 10 | 20 s | ||
| 500 | b | 1024 bytes | |
| 2 | 100 to 500 m | ||
| 2.4 | 0.00125 W | ||
| 0.1 | 0.0016 W | ||
| 500 | 50, 100 | ||
| 10 | 4 | ||
| 10 dB | 4 | ||
| 2 | 2 | ||
| 10 | 2 | ||
| 0.1 J | 0.25 J | ||
| 0.05 J | 0.32 J | ||
| 30 Kbps | 50 Kbps |
| Approach | Author | Ideology | Drones | Wireless Communication Support | Surveillance | Energy-Efficient Deployment | Resilient | Fail-Safe | LoRaWAN |
|---|---|---|---|---|---|---|---|---|---|
| Meteorological
information display | Reda et al. [71] | LoRa wireless communication | No | Yes | No | - | - | - | Yes |
| Visual surveillance | Pham [72] | Low-cost, low-power
and long-range visualization | No | Yes | Yes | Yes | - | - | Yes |
| UAV path planning | Zhan et al. [73] | Multiconstraints in a 3D environment | Yes | No | Yes | No | - | - | Yes |
| UAV-WSN networks | Sharma et al. [45] | Multi-UAV coordination | Yes | Yes | Yes | Yes | No | No | No |
| Urban Surveillance | Samad et al. [74] | Networm centric systems | Yes | Yes | Yes | - | - | - | No |
| Feature detection of
nonconforming objects | Xu et al. [75] | Key points matching problem | Yes | No | Yes | No | - | - | No |
| Amateur surveillance
System | Ding et al. [76] | Surveillance system based
on the cognitive Internet of Things | Yes | Yes | Yes | No | - | - | No |
| Motion planning | Scherer et al. [77] | Multi-UAV surveillance | Yes | Yes | Yes | Yes | - | - | No |
| Proposed | Sharma et al. | Drones as LoRaWAN gateways | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sharma, V.; You, I.; Pau, G.; Collotta, M.; Lim, J.D.; Kim, J.N. LoRaWAN-Based Energy-Efficient Surveillance by Drones for Intelligent Transportation Systems. Energies 2018, 11, 573. https://doi.org/10.3390/en11030573
Sharma V, You I, Pau G, Collotta M, Lim JD, Kim JN. LoRaWAN-Based Energy-Efficient Surveillance by Drones for Intelligent Transportation Systems. Energies. 2018; 11(3):573. https://doi.org/10.3390/en11030573
Chicago/Turabian StyleSharma, Vishal, Ilsun You, Giovanni Pau, Mario Collotta, Jae Deok Lim, and Jeong Nyeo Kim. 2018. "LoRaWAN-Based Energy-Efficient Surveillance by Drones for Intelligent Transportation Systems" Energies 11, no. 3: 573. https://doi.org/10.3390/en11030573






