Smart Cybersecurity Framework for IoT-Empowered Drones: Machine Learning Perspective
Abstract
:1. Introduction
1.1. Research Domain
1.2. Research Motivation
Problem Definition
1.3. Major Contribution
- 1.
- A comprehensive modular framework is proposed to ensure privacy and security in the drone network.
- 2.
- The proposed framework highlights vital details, analysis, hardware modules, and security techniques using machine learning (ML) models.
- 3.
- To manage security attacks, the proposed framework uses IoT sensors, drone data, and networking data.
- 4
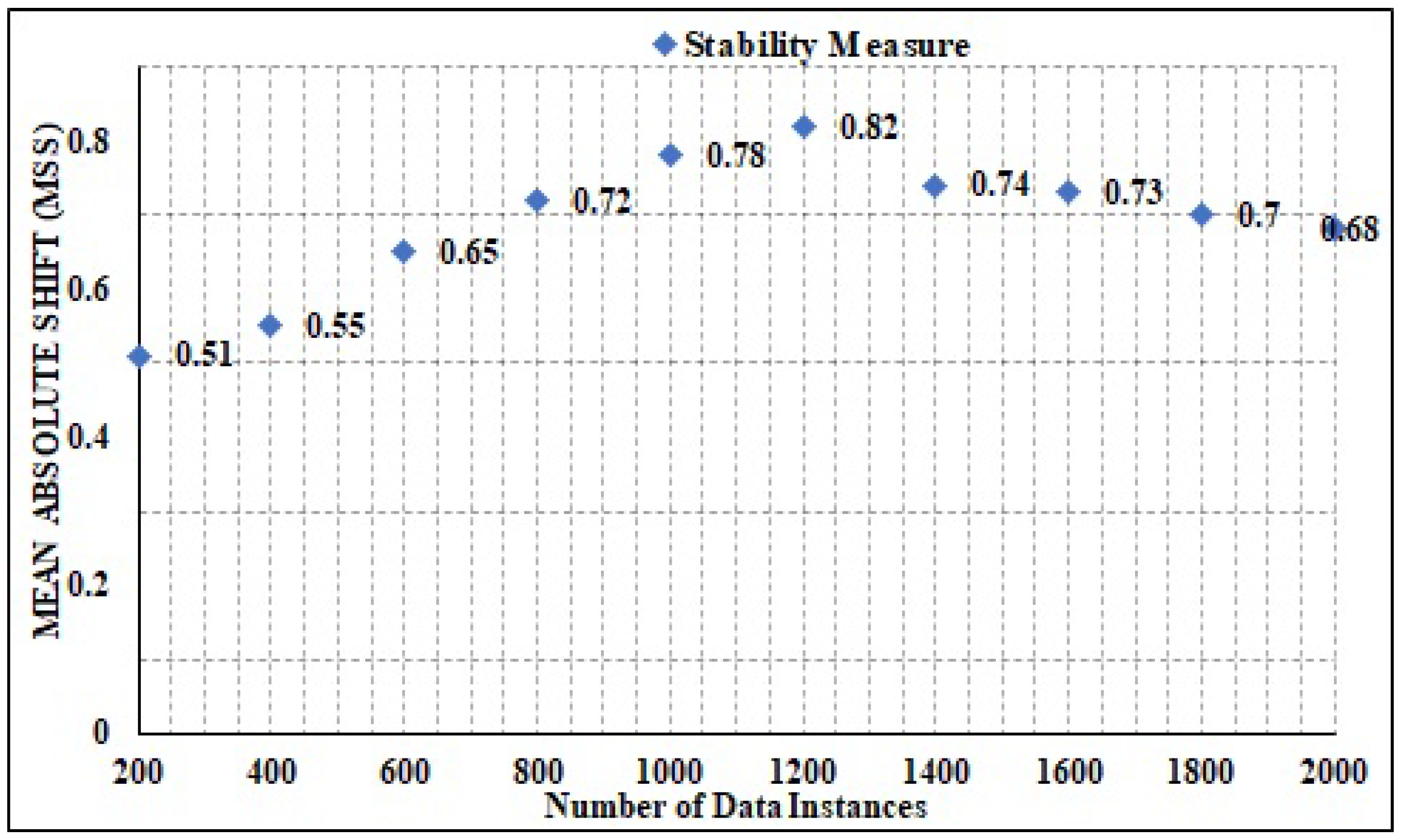
- The proposed model is evaluated on two challenging datasets in which enhanced temporal efficacy (34.56 s), statistical measures (precision (97.68%), accuracy (98.58%), recall (98.59%), F-measure (99.01%), reliability (94.69%), and stability (0.73) are registered.
- 5
- The experimental findings show that the proposed model is generalizable and resilient.
Paper Organization
2. Literature Review
2.1. Drone Security Threats
2.2. Drone Security Using Machine Learning
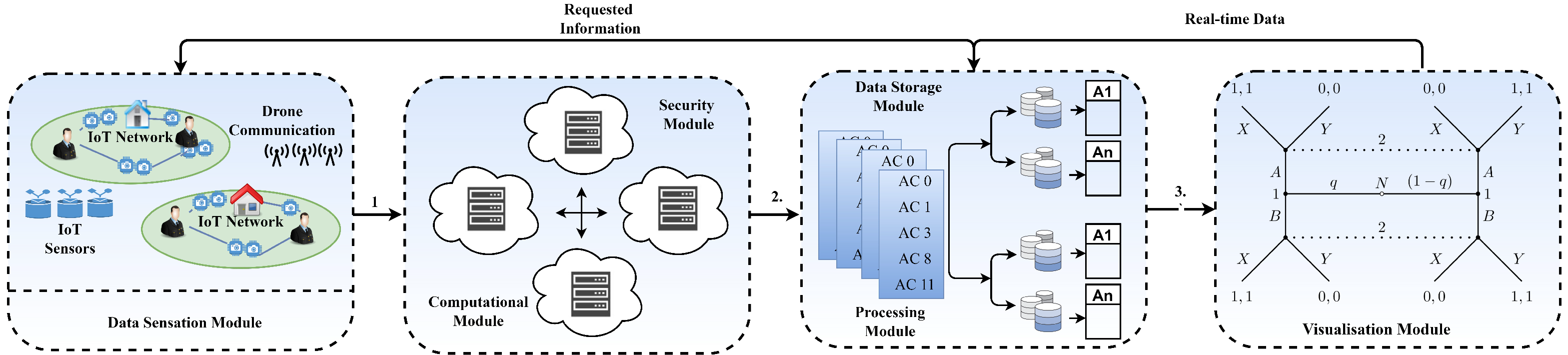
3. Proposed Framework
3.1. Procedural Steps
- 1
- In the initial step, the drone module acquires the ubiquitous information using numerous embedded IoT sensors and camcorders.
- 2
- The acquired data is forwarded to the edge computational module for local analysis.
- 3
- Based on anomaly elimination using quantile regression [42], level-1 of physical data security is ensured.
- 4
- Once security is ensured, the data are forwarded to the regional data hub for storage and application purposes.
- 5
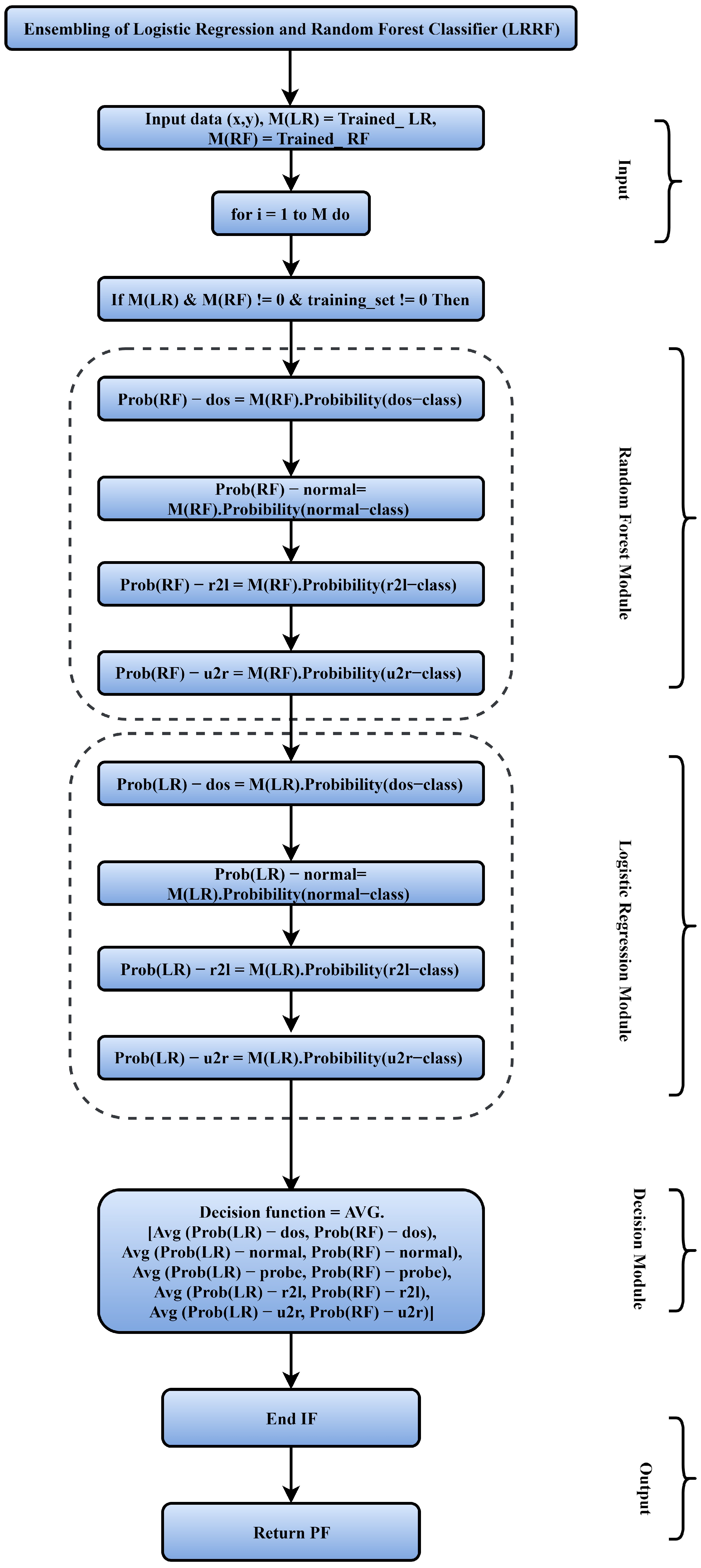
- Before deployment of the application, the acquired data are processed for level-2 security using the hybrid ML technique of logistic regression and random forest. The acquired data segments are generated by the sensors equipped over drones in heterogeneous format, which is classified as normal or attacked data segment using ML technique.
- 6
- Moreover, the data are stored in the NoSQL data format repository for effective application-specific computation.
- 7
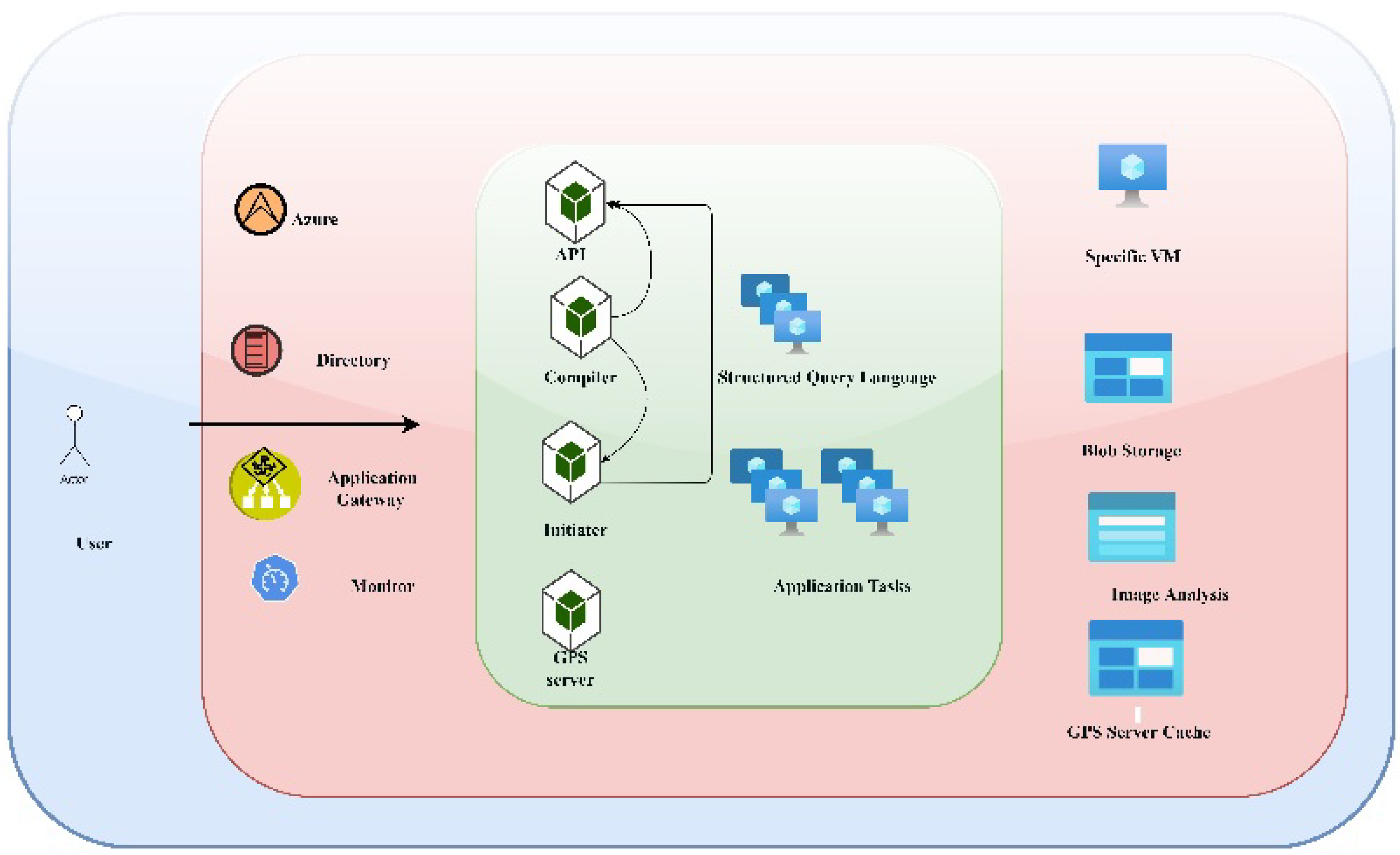
- Finally, the visualization of the drone attack is performed over the Microsoft Azure framework.
3.2. Modules
3.2.1. Drone Module (DM)
3.2.2. Edge Computational Module
3.2.3. Security Module
- 1
- Danger to physical privacy.
- 2
- Threat to behavior privacy.
- 3
- Threat to location privacy.
3.2.4. Transmission Module
3.2.5. Processing Module
3.2.6. Probabilistic Ranking Strategy
- 1.
- Jamming.
- 2.
- Denial of service (DoS) attacks.
- 3.
- Exposure to cybersecurity threats from drones.
- 4.
- Malicious attacks.
- 5.
- Spoofing.
Stepwise Procedure
3.2.7. Storage Module
3.2.8. Visualization Module
3.3. Hardware Components
3.3.1. DJI Phantom 4 Pro Drone
3.3.2. Sensor GPS
3.3.3. Radar Sensor
3.3.4. Wireless ZigBee Transmission
3.3.5. BMP180 Pressure Sensor
4. Experimental Assessment
4.1. Dataset
4.2. Incorporated Machine Learning Technique
- 1.
- Random forest (RF) is an ensemble learning technique that uses decision trees (DT), which are also known as estimators, to classify data. The probabilistic ranking is used to combine the results of various trees to produce better results. The bagging technique is used to train trees using bootstrap samples. To evaluate the model’s performance on test data, all trees are created in the same way. The decision tree with the lowest error rate is given a larger weight, resulting in a lower likelihood of making an inaccurate estimation.
- 2.
- Decision tree (DT) is a multi-variable ML technique for text categorization that is widely used. It is used to forecast certain data values. It divides data into branching segments, which are utilized to construct an inverted tree with internal nodes, the root node, and leave nodes. The method is nonparametric, which means it can effectively assess complex data without imposing a sophisticated framework.
- 3.
- Logistic regression is a mathematical strategy to predict outcomes; it examines data and works on numerous factors. It is a low-variance, basic but efficient approach that is commonly used in classification. This model may also be used to extract features. Stochastic gradient descent makes it simple to update with fresh data.
- 4.
- The naive Bayesian classifier, which makes independent assumptions among predictors, is based on Bayes’ theorem. It is simple to put together, with simple iterative parameter estimation. As a result, it is thought to be ideal for huge datasets. Despite its simplicity, it produces excellent results and outperforms other, more advanced classifiers.
- 5.
- In text categorization, the support vector machine (SVM) is widely used. By maximizing the marginal distance, it draws hyperplanes that split classes. In binary classification, the SVM hyperplane separates the text into two separate groups. It is simpler and less complicated than deep learning approaches, and it is easy to understand. SVM is also commonly used to detect intrusions.
- 6.
- The multilayer perceptron (MLP) is a basic deep learning model that can classify data rather well. It is a layered model, with neurons representing features in the initial layer and hidden layers processing incoming data and feeding them to the output layer represented by neurons. The numbers of hidden layers and neurons are chosen optimally to obtain the best outcomes. The model is trained using the hyperparameter values to increase classification training efficiency. Backpropagation, which is based on gradient descent, is commonly employed to assess MLP weights. The rectified linear unit (ReLU) is employed in hidden layers, while the sigmoid is utilized as an activation function. Sigmoid (G(x))= .
4.3. Experimental Results
4.4. Temporal Efficacy
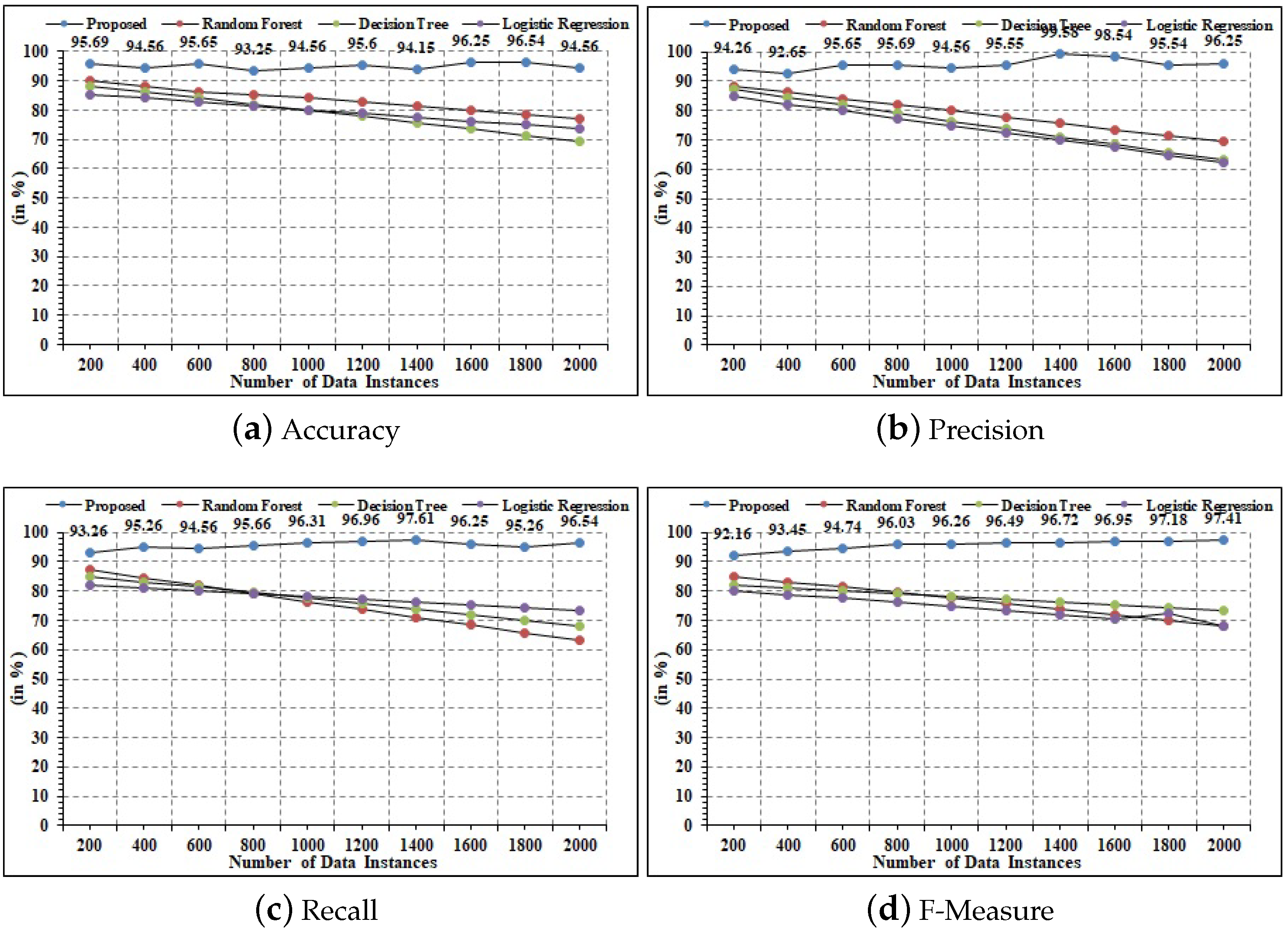
4.5. Statistical Analysis
4.6. Reliability
4.7. Stability
4.8. Scalability Analysis
4.9. Cost Analysis
5. Limitations and Future Works
- 1.
- The proposed model is suitable for four categories of attacks only. This aspect can be explored for other types of UAV attacks, including DDoS and man-in-middle.
- 2.
- The application domain of the proposed model can be explored for deployment in different sectors for performance assessment.
- 3.
- The computation cost of the proposed model increases with a large number of data segments. It can be further improved using effective techniques.
- 4.
- Finally, the security-based network topology of drones is another aspect for future exploration.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Diaz Linares, I.; Pardo, A.; Patch, E.; Dehghantanha, A.; Choo, K.K.R. IoT Privacy, Security and Forensics Challenges: An Unmanned Aerial Vehicle (UAV) Case Study. In Handbook of Big Data Analytics and Forensics; Springer: Berlin, Germany, 2022; pp. 7–39. [Google Scholar]
- Aloqaily, M.; Bouachir, O.; Boukerche, A.; Al Ridhawi, I. Design guidelines for blockchain-assisted 5G-UAV networks. IEEE Netw. 2021, 35, 64–71. [Google Scholar] [CrossRef]
- Aldhyani, T.H.; Alkahtani, H. Attacks to automatous vehicles: A deep learning algorithm for cybersecurity. Sensors 2022, 22, 360. [Google Scholar] [CrossRef]
- Aloqaily, M.; Hussain, R.; Khalaf, D.; Hani, D.; Oracevic, A. On the Role of Futuristic Technologies in Securing UAV-Supported Autonomous Vehicles. IEEE Consum. Electron. Mag. 2022. [Google Scholar] [CrossRef]
- Abdani, S.R.; Zulkifley, M.A.; Zulkifley, N.H. A lightweight deep learning model for covid-19 detection. In Proceedings of the 2020 IEEE Symposium on Industrial Electronics & Applications (ISIEA), Kuala Lumpur, Malaysia, 17–18 July 2020; pp. 1–5. [Google Scholar]
- Angurala, M.; Singh, H.; Anupriya; Grover, A.; Singh, M. Testing Solar-MAODV energy efficient model on various modulation techniques in wireless sensor and optical networks. Wirel. Netw. 2022, 28, 413–425. [Google Scholar] [CrossRef]
- Cabassi, J.; Lazzaroni, M.; Giannini, L.; Mariottini, D.; Nisi, B.; Rappuoli, D.; Vaselli, O. Continuous and near real-time measurements of gaseous elemental mercury (GEM) from an Unmanned Aerial Vehicle: A new approach to investigate the 3D distribution of GEM in the lower atmosphere. Chemosphere 2022, 288, 132547. [Google Scholar] [CrossRef]
- Grieco, L.A.; Boggia, G.; Piro, G.; Jararweh, Y.; Campolo, C. Ad-Hoc, Mobile, and Wireless Networks. In Proceedings of the 19th International Conference on Ad-Hoc Networks and Wireless, ADHOC-NOW 2020, Bari, Italy, 19–21 October 2020; Springer Nature: Berlin, Germany, 2020; Volume 12338. [Google Scholar]
- Supramongkonset, J.; Duangsuwan, S.; Promwong, S. A WiFi Link Budget Analysis of Drone-based Communication and IoT Ground Sensors. In Proceedings of the 2021 7th International Conference on Engineering, Applied Sciences and Technology (ICEAST), Pattaya, Thailand, 1–3 April 2021; pp. 234–237. [Google Scholar]
- Yin, Z.; Song, Q.; Han, G.; Zhu, M. Unmanned optical warning system for drones. In Global Intelligence Industry Conference (GIIC 2018); International Society for Optics and Photonics: Bellingham, DC, USA, 2018; Volume 10835, p. 108350Q. [Google Scholar]
- Koslowski, R.; Schulzke, M. Drones along borders: Border security UAVs in the United States and the European Union. Int. Stud. Perspect. 2018, 19, 305–324. [Google Scholar] [CrossRef]
- Ozmen, M.O.; Yavuz, A.A. Dronecrypt-an efficient cryptographic framework for small aerial drones. In Proceedings of the MILCOM 2018–2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Khan, M.A.; Ullah, I.; Alsharif, M.H.; Alghtani, A.H.; Aly, A.A.; Chen, C.M. An Efficient Certificate-Based Aggregate Signature Scheme for Internet of Drones. Secur. Commun. Netw. 2022, 2022, 9718580. [Google Scholar] [CrossRef]
- Ranjitha, K.; Pathak, D.; Tammana, P.; Antony, F.A.; Alladi, T. Accelerating PUF-based UAV Authentication Protocols Using Programmable Switch. In Proceedings of the 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 4–8 January 2022; pp. 309–313. [Google Scholar]
- Li, S.; Bai, Y. Deep Learning and Improved HMM Training Algorithm and Its Analysis in Facial Expression Recognition of Sports Athletes. Comput. Intell. Neurosci. 2022, 2022, 1027735. [Google Scholar] [CrossRef]
- Tuli, E.A.; Golam, M.; Kim, D.S.; Lee, J.M. Performance Enhancement of Optimized Link State Routing Protocol by Parameter Configuration for UANET. Drones 2022, 6, 22. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alkhalifah, A.; Rehman, S.U.; Shah, J.A.; Uddin, I.I.; Alsharif, M.H.; Algarni, F. A provable and privacy-preserving authentication scheme for UAV-enabled intelligent transportation systems. IEEE Trans. Ind. Inform. 2021, 18, 3416–3425. [Google Scholar] [CrossRef]
- Maghazei, O.; Netland, T.H.; Frauenberger, D.; Thalmann, T. Automatic drones for factory inspection: The role of virtual simulation. In Proceedings of the IFIP International Conference on Advances in Production Management Systems; Springer: Berlin, Germany, 2021; pp. 457–464. [Google Scholar]
- Kapoutsis, A.C.; Michailidis, I.T.; Boutalis, Y.; Kosmatopoulos, E.B. Building synergetic consensus for dynamic gas-plume tracking applications using UAV platforms. Comput. Electr. Eng. 2021, 91, 107029. [Google Scholar] [CrossRef]
- Nguyen, H.P.D.; Nguyen, D.D. Drone application in smart cities: The general overview of security vulnerabilities and countermeasures for data communication. In Development and Future of Internet of Drones (IoD): Insights, Trends and Road Ahead; Springer: Berlin, Germany, 2021; pp. 185–210. [Google Scholar]
- Kumar, A.; Elsersy, M.; Darwsih, A.; Hassanien, A.E. Drones combat COVID-19 epidemic: Innovating and monitoring approach. In Digital Transformation and Emerging Technologies for Fighting COVID-19 Pandemic: Innovative Approaches; Springer: Berlin, Germany, 2021; pp. 175–188. [Google Scholar]
- Aydin, Y.; Kurt, G.K.; Ozdemir, E.; Yanikomeroglu, H. Group authentication for drone swarms. In Proceedings of the 2021 IEEE International Conference on Wireless for Space and Extreme Environments (WiSEE), Cleveland, OH, USA, 12–14 October 2021; pp. 72–77. [Google Scholar]
- Maddikunta, P.K.R.; Pham, Q.V.; Prabadevi, B.; Deepa, N.; Dev, K.; Gadekallu, T.R.; Ruby, R.; Liyanage, M. Industry 5.0: A survey on enabling technologies and potential applications. J. Ind. Inf. Integr. 2021, 26, 100257. [Google Scholar] [CrossRef]
- Saha, H.N.; Roy, R.; Chakraborty, M.; Sarkar, C. IoT-Enabled Agricultural System Application, Challenges and Security Issues. In Agricultural Informatics: Automation Using the IoT and Machine Learning; Wiley Online Library: Hoboken, NJ, USA, 2021; pp. 223–247. [Google Scholar]
- Lyu, C.; Zhan, R. Global Analysis of Active Defense Technologies for Unmanned Aerial Vehicle. IEEE Aerosp. Electron. Syst. Mag. 2022, 37, 6–31. [Google Scholar] [CrossRef]
- Jares, G.A.; Valasek, J. Flight Demonstration and Validation of Control Acquisition Autopilot Attack. In Proceedings of the AIAA SCITECH 2022 Forum, San Diego, CA, USA, 3–7 January 2022; p. 2341. [Google Scholar]
- Talaei Khoei, T.; Ismail, S.; Kaabouch, N. Dynamic Selection Techniques for Detecting GPS Spoofing Attacks on UAVs. Sensors 2022, 22, 662. [Google Scholar] [CrossRef] [PubMed]
- Nasrollahi, S.; Mirrezaei, S.M. Toward UAV-based communication: Improving throughput by optimum trajectory and power allocation. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 9. [Google Scholar] [CrossRef]
- Rajasekaran, A.S.; Maria, A.; Al-Turjman, F.; Altrjman, C.; Mostarda, L. Anonymous Mutual and Batch Authentication with Location Privacy of UAV in FANET. Drones 2022, 6, 14. [Google Scholar] [CrossRef]
- Zhai, L.; Kanellopoulos, A.; Fotiadis, F.; Vamvoudakis, K.G.; Hugues, J. Towards Intelligent Security for Unmanned Aerial Vehicles: A Taxonomy of Attacks, Faults, and Detection Mechanisms. In Proceedings of the AIAA SCITECH 2022 Forum, San Diego, CA, USA, 3–7 January 2022; p. 0969. [Google Scholar]
- Rugo, A.; Ardagna, C.A.; Ioini, N.E. A Security Review in the UAVNet Era: Threats, Countermeasures, and Gap Analysis. ACM Comput. Surv. (CSUR) 2022, 55, 1–35. [Google Scholar] [CrossRef]
- Norooz Oliaee, J.; Sabourin, N.A.; Festa-Bianchet, S.A.; Gupta, J.A.; Johnson, M.R.; Thomson, K.A.; Smallwood, G.J.; Lobo, P. Development of a Sub-ppb Resolution Methane Sensor Using a GaSb-Based DFB Diode Laser near 3270 nm for Fugitive Emission Measurement. ACS Sens. 2022, 7, 564–572. [Google Scholar] [CrossRef]
- Ouiazzane, S.; Addou, M.; Barramou, F. A Multiagent and Machine Learning Based Denial of Service Intrusion Detection System for Drone Networks. In Geospatial Intelligence; Springer: Berlin, Germany, 2022; pp. 51–65. [Google Scholar]
- Kong, W.; Li, X.; Hou, L.; Yuan, J.; Gao, Y.; Yu, S. A Reliable and Efficient Task Offloading Strategy Based on Multi-feedback Trust Mechanism for IoT Edge Computing. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Pushpa, S.X.; Raja, S.K. Elliptic Curve Cryptography Based Authentication Protocol Enabled with Optimized Neural Network Based DoS Mitigation. Wirel. Pers. Commun. 2022, 1–25. [Google Scholar]
- Sengan, S.; Khalaf, O.I.; Sharma, D.K.; Hamad, A.A. Secured and privacy-based IDS for healthcare systems on E-medical data using machine learning approach. Int. J. Reliab. Qual. Healthc. (IJRQEH) 2022, 11, 1–11. [Google Scholar]
- Vedula, V.; Lama, P.; Boppana, R.V.; Trejo, L.A. On the Detection of Low-Rate Denial of Service Attacks at Transport and Application Layers. Electronics 2021, 10, 2105. [Google Scholar] [CrossRef]
- Hosseinzadeh, M.; Sinopoli, B. Active Attack Detection and Control in Constrained Cyber-Physical Systems Under Prevented Actuation Attack. arXiv 2021, arXiv:2101.09885. [Google Scholar]
- Bera, B.; Saha, S.; Das, A.K.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-envisioned secure data delivery and collection scheme for 5g-based iot-enabled internet of drones environment. IEEE Trans. Veh. Technol. 2020, 69, 9097–9111. [Google Scholar] [CrossRef]
- Yijing, Z.; Zheng, Z.; Xiaoyi, Z.; Yang, L. Q learning algorithm based UAV path learning and obstacle avoidence approach. In Proceedings of the 2017 36th Chinese Control Conference (CCC), Dalian, China, 26–28 July 2017; pp. 3397–3402. [Google Scholar]
- Pandey, A.; Jain, K. An intelligent system for crop identification and classification from UAV images using conjugated dense convolutional neural network. Comput. Electron. Agric. 2022, 192, 106543. [Google Scholar] [CrossRef]
- Zhang, Z.; Khanal, S.; Raudenbush, A.; Tilmon, K.; Stewart, C. Assessing the efficacy of machine learning techniques to characterize soybean defoliation from unmanned aerial vehicles. Comput. Electron. Agric. 2022, 193, 106682. [Google Scholar] [CrossRef]
- Jiang, J.; Johansen, K.; Stanschewski, C.S.; Wellman, G.; Mousa, M.A.; Fiene, G.M.; Asiry, K.A.; Tester, M.; McCabe, M.F. Phenotyping a diversity panel of quinoa using UAV-retrieved leaf area index, SPAD-based chlorophyll and a random forest approach. Precis. Agric. 2022, 1–23. [Google Scholar] [CrossRef]
- Avola, D.; Cinque, L.; Di Mambro, A.; Diko, A.; Fagioli, A.; Foresti, G.L.; Marini, M.R.; Mecca, A.; Pannone, D. Low-Altitude Aerial Video Surveillance via One-Class SVM Anomaly Detection from Textural Features in UAV Images. Information 2022, 13, 2. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Kim, S. 6G enabled unmanned aerial vehicle traffic management: A perspective. IEEE Access 2021, 9, 91119–91136. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE symposium on computational intelligence for security and defense applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Siddique, K.; Akhtar, Z.; Khan, F.A.; Kim, Y. KDD cup 99 data sets: A perspective on the role of data sets in network intrusion detection research. Computer 2019, 52, 41–51. [Google Scholar] [CrossRef]











| Attack | Attributes | Reference |
|---|---|---|
| Protocol-based attacks | Security of communication link | [28] |
| Protocol-based attacks | Data confidentiality | [29] |
| Protocol-based attacks | Replay attack | [30] |
| Protocol-based attacks | Privacy leakage | [1] |
| Sensors-based attacks | GPS spoofing/jamming attack | [31] |
| Sensors-based attacks | Motion sensors spoofing | [27] |
| Sensors-based attacks | UAV spoofing/jamming attack | [31] |
| Compromised component | IoT security threats | [1] |
| Compromised component | Control/data interception | [32] |
| Jammers | Denial of service | [33] |
| Jammers | Stop packet delivery | [6] |
| Attack | Privacy | Conf | Int | Ave | Auth | Security Measures |
|---|---|---|---|---|---|---|
| Malware | 1 | 1 | 1 | 1 | 1 | Hybrid lightweight IDS |
| Social engineering | 1 | 1 | 0 | 0 | 1 | Raising awareness, training operators |
| Backdoor access | 1 | 1 | 1 | 1 | 1 | Hybrid lightweight IDS |
| Baiting | 1 | 1 | 1 | 0 | 1 | Raising awareness |
| Fabrication | 1 | 0 | 1 | 0 | 1 | Assigning privilege |
| Eavesdropping | 1 | 1 | 0 | 0 | 0 | N/A |
| Man-in-the-middle | 1 | 1 | 1 | 0 | 0 | Lightweight hybrid IDS |
| Wi-Fi aircrack | 0 | 0 | 0 | 0 | 1 | Lightweight IDS |
| Wi-Fi jamming | 0 | 0 | 0 | 0 | 1 | Frequency hopping, frequency range variation |
| Replay | 0 | 0 | 0 | 0 | 1 | Frequency hopping, time stamps |
| Ping-of-death | 0 | 0 | 0 | 0 | 1 | Frequency range variation |
| GPS spoofing | 0 | 0 | 0 | 0 | 1 | Return-to-base |
| Attacks | Security Technique | Machine Learning Solution | Reference |
|---|---|---|---|
| Jamming | Secure offloading | Q-learning, DQN | [40] |
| Denial of service | Secure offloading | Neural network, multivariate correlation analysis | [41] |
| Intrusion | Access control | Naive Bayes | [42] |
| Malware | Access control | Random forest | [43] |
| Spoofing | Authentication | SVM | [44] |
| Traffic blockage | Authentication | Q-learning | [40] |
| Comparative Works | UAV | ML Technique | M2M Communication | Cognitive Decision | Security | Real-Time | Performance Analysis | Numerical Quantification | Packet Evaluation | Statistical Analysis | Temporal Delay |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [40] | YY | YY | YY | NA | NA | YY | YY | YY | NA | NA | NA |
| [43] | YY | YY | YY | YY | YY | NA | YY | NA | NA | NA | YY |
| [44] | YY | YY | NA | NA | YY | NA | YY | NA | YY | NA | NA |
| [41] | YY | YY | NA | NA | YY | YY | YY | YY | NA | NA | NA |
| [42] | YY | YY | YY | NA | YY | YY | YY | NA | YY | NA | NA |
| [27] | YY | YY | NA | YY | NA | NA | NA | YY | NA | NA | NA |
| [23] | YY | NA | YY | YY | NA | NA | YY | NA | NA | YY | NA |
| [24] | YY | NA | YY | NA | NA | YY | YY | NA | YY | NA | NA |
| [2] | YY | YY | YY | NA | YY | NA | NA | NA | NA | NA | NA |
| Proposed | YY | YY | YY | YY | YY | YY | YY | YY | YY | YY | YY |
| Attack Class | Type |
|---|---|
| DOS | land, back, pod, smurf |
| R2L | ftp_write, imap, multihop, phf, spy |
| U2R | buffer-overflow, perl |
| Probe | ipsweep, portsweep |
| Category | Detail |
|---|---|
| Normal | Connections are generated by simulating user behavior. |
| DoS attacks | Use of resources or services are denied to authorized users. |
| Probe attack | Information about the system is exposed to unauthorized entities. |
| User to remote attacks | Access to account types of administrator is gained by unauthorized entities. |
| Remote to local attacks | Access to hosts is gained by unauthorized entities. |
| Models | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| Random forest | 92.36 | 92.36 | 93.15 | 94.56 |
| Decision tree | 93.25 | 91.26 | 93.25 | 95.62 |
| Logistic regression | 92.23 | 96.25 | 94.15 | 96.32 |
| Naïve Bayes | 89.65 | 90.47 | 91.25 | 92.25 |
| Support vector machine | 92.36 | 94.26 | 93.25 | 92.25 |
| MLP | 89.65 | 88.14 | 89.25 | 92.15 |
| Proposed | 98.58 | 97.68 | 98.59 | 99.01 |
| Methods | Dataset | Accuracy (in %) |
|---|---|---|
| Proposed | Drone dataset | 98.58 |
| Proposed | NSL-KDD | 98.69 |
| Proposed | KDD CUP 99 | 99.01 |
| PCA + MCA | Drone dataset | 92.25 |
| Deep neural network | KDD CUP 99 | 91.25 |
| DT–RF | NSL-KDD | 89.69 |
| PCA + MCA | Drone dataset | 92.58 |
| Deep neural network | KDD CUP 99 | 93.25 |
| DT–RF | NSL-KDD | 91.25 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aldaej, A.; Ahanger, T.A.; Atiquzzaman, M.; Ullah, I.; Yousufudin, M. Smart Cybersecurity Framework for IoT-Empowered Drones: Machine Learning Perspective. Sensors 2022, 22, 2630. https://doi.org/10.3390/s22072630
Aldaej A, Ahanger TA, Atiquzzaman M, Ullah I, Yousufudin M. Smart Cybersecurity Framework for IoT-Empowered Drones: Machine Learning Perspective. Sensors. 2022; 22(7):2630. https://doi.org/10.3390/s22072630
Chicago/Turabian StyleAldaej, Abdulaziz, Tariq Ahamed Ahanger, Mohammed Atiquzzaman, Imdad Ullah, and Muhammad Yousufudin. 2022. "Smart Cybersecurity Framework for IoT-Empowered Drones: Machine Learning Perspective" Sensors 22, no. 7: 2630. https://doi.org/10.3390/s22072630






