Review of Intentional Electromagnetic Interference on UAV Sensor Modules and Experimental Study
Abstract
:1. Introduction
2. Review of Intentional Electromagnetic Interference
- High power IEMI: High power IEMI uses an electromagnetic signal with sufficiently high power to destroy an electronic device or cause its serious degradation. Conventionally, the name high-power electromagnetic (HPEM) environment, which includes all naturally occurring electromagnetic phenomena, is mainly used. There is no exact criterion of power to be classified as HPEM; however, it is generally classified as HPEM if it has a field intensity above 100 V/m around the target [32]. In this study, to deal with the areas directly applicable to drones, all the methods of inducing destruction or degradation using high-power signals, without considering the operating mechanism of the target, are included by expanding the criteria.
- Low power IEMI: Low power IEMI uses an electromagnetic signal with relatively low power to cause malfunctioning of the target. The main difference from high-power IEMI is that low-power IEMI sets the applied signal in consideration of the target’s operating mechanism to lower the required power. Specifically, research has been conducted to couple an external interference signal into the sensor to manipulate the sensor’s data signal in a desired manner or to cause a malfunction. The targets of low-power IEMI can be classified as analog sensors, digital sensors, and communication modules. In general, analog sensors use low-voltage signals of a few millivolts. Thus, the data inside the sensor may be changed even when using a small number of coupled signals. To achieve this, an antenna or coil can be used as an attack method, and finding appropriate resonant frequencies to effectively couple the energy is important [33,34]. On the other hand, digital sensors use digital data with relatively high voltage levels of a few volts. Because a large amount of energy must be coupled to cause a significant change in the digital signal, a bulk current injection(BCI) method or direct power injection method (DPI) using an injection probe is commonly used rather than antennas [35,36]. For the communication modules using RF channels, if prior knowledge about the module’s channel information is available, in-band jamming may be an effective interference method, and it requires relatively low power.
- Non-RF: For electromagnetic interference, not only radio-frequency signals but also acoustic [37] and light signals [38] can be candidates for interfering signals. Because these methods operate by targeting the mechanical structure or operating mechanism of particular sensors, their versatility is low; however, they have a significant effect if the required conditions are met.
2.1. High Power Intentional Electromagnetic Interference (High Power IEMI)
2.2. Low Power Intentional Electromagnetic Interference (Low Power IEMI)
2.3. Non-RF Interference
3. Drone Sensor Modules
3.1. Sensor Modules in Drone
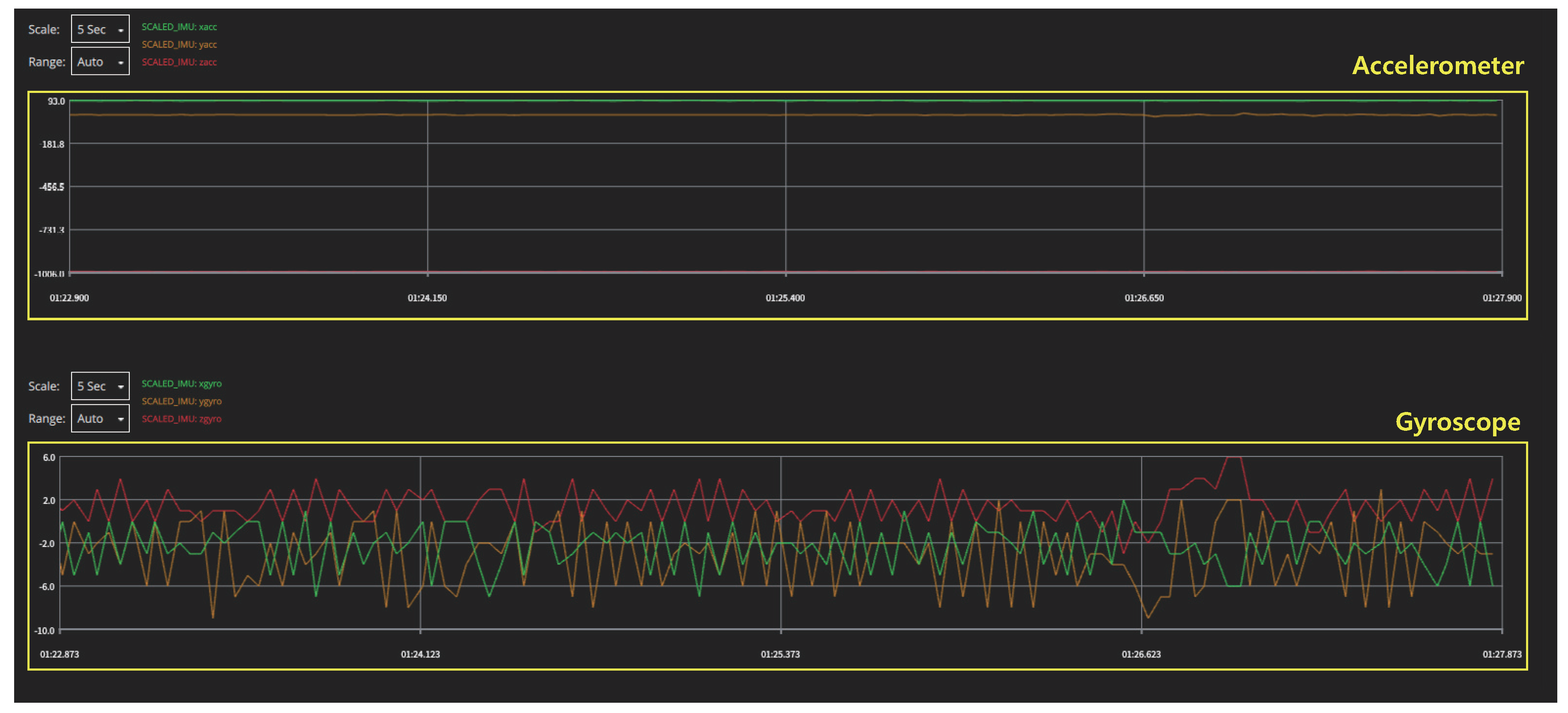
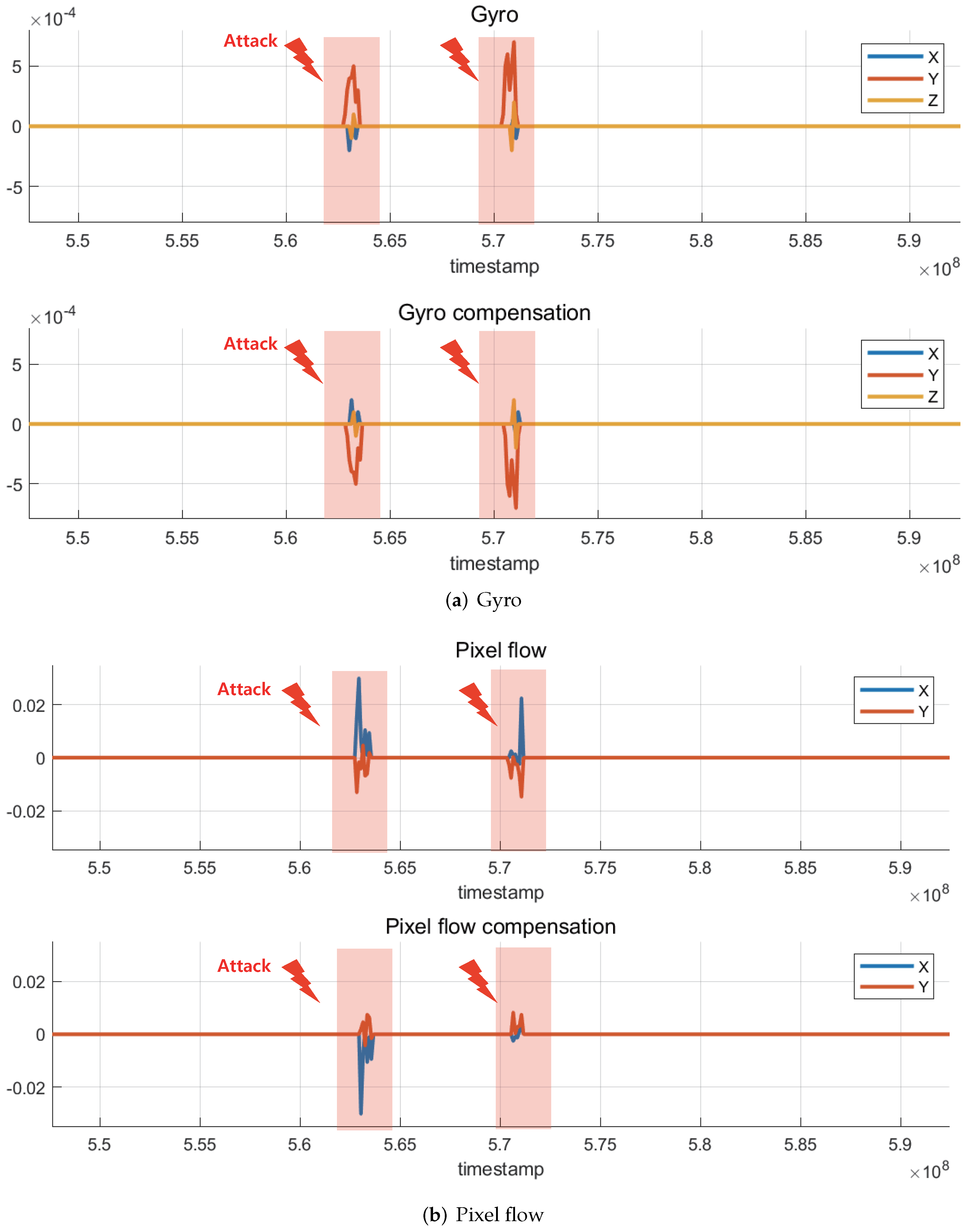
- Inertial Measurement Unit (IMU): IMU is an essential sensor module for navigation devices; it is a combination of a three-axis gyroscope and a three-axis accelerometer, and in some cases, a three-axis magnetometer is added to improve its performance. The acceleration measured by the accelerometer and the angular velocity measured by the gyroscope are combined to precisely estimate the attitude of the drone. The resulting data from this sensor fusion are transmitted to the main processor of the flight controller in the form of a digital signal. Because the IMU plays a critical role in estimating the attitude of the drone, stable flight is not achievable if these signals are affected by external interference. To interfere with IMU-data signals, a high-power interference signal is needed because the digital data signals have a relatively high amplitude, i.e., in the range of few volts. The effects of high-power electromagnetic interference on the IMU data signals are presented in Section 4.1.
- Camera: Cameras are the most widely used modules for drone use. A wide variety of camera modules are applicable to drones and can be divided into two types based on the communication scheme: analog and digital. Many custom drones are equipped with camera modules that use analog communication owing to their low price and high accessibility. Most commercial photography drones use a digital-communication camera module for stable communication with a large amount of data. The most effective way to interfere with the camera module through radio-frequency signals is to apply an in-band interference signal. The effects of the in-band interference signal on the camera module using analog and digital communication schemes are described in Section 4.2.
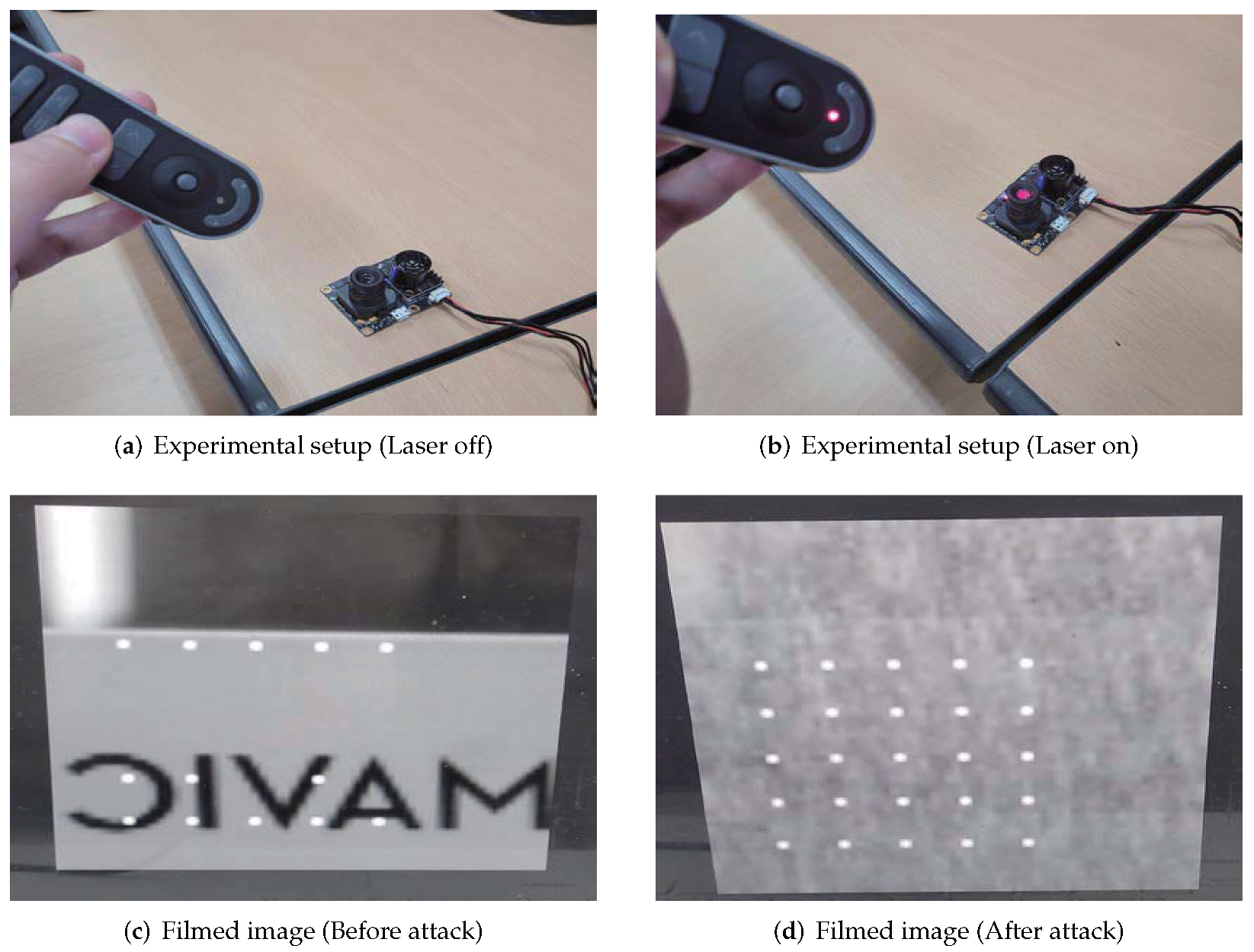
- Optical flow: The optical flow consists of a camera, various sensors, and a CPU. It films the video using an onboard downward camera and compares the subsequent frames to estimate the attitude and velocity of the drone. In this process, various sensors, such as sonar and gyroscope, are also used, and these data are processed by the on-board CPU. The resulting data are digital signals, which is the same as the IMU data. However, because the optical flow uses filmed data as the sensor input, an external light source may operate as an interference source by distorting the filmed image. Therefore, the effects of a laser attack on an optical flow sensor were examined and are described in Section 4.3
- GPS: The GPS module receives signals from satellites orbiting around the earth and calculates the actual position of the drone. To calculate the position accurately, more than four signals from separate satellites are necessary. Jamming and spoofing are well-known interference methods for GPS modules, and the relevant studies and experimental results are well known [56].
3.2. Sensor Data Monitoring
4. Experimental Section
4.1. IMU Sensors Interfered by High Power IEMI Source
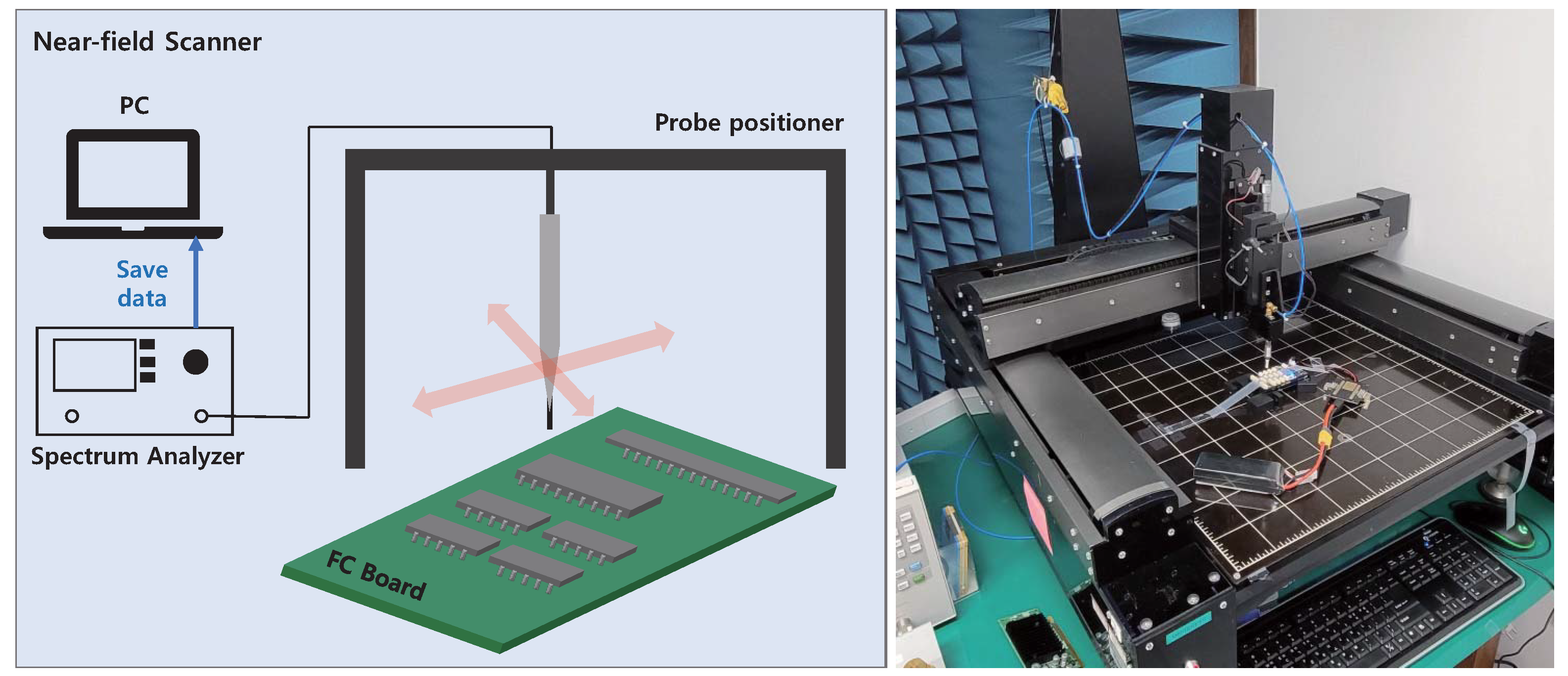
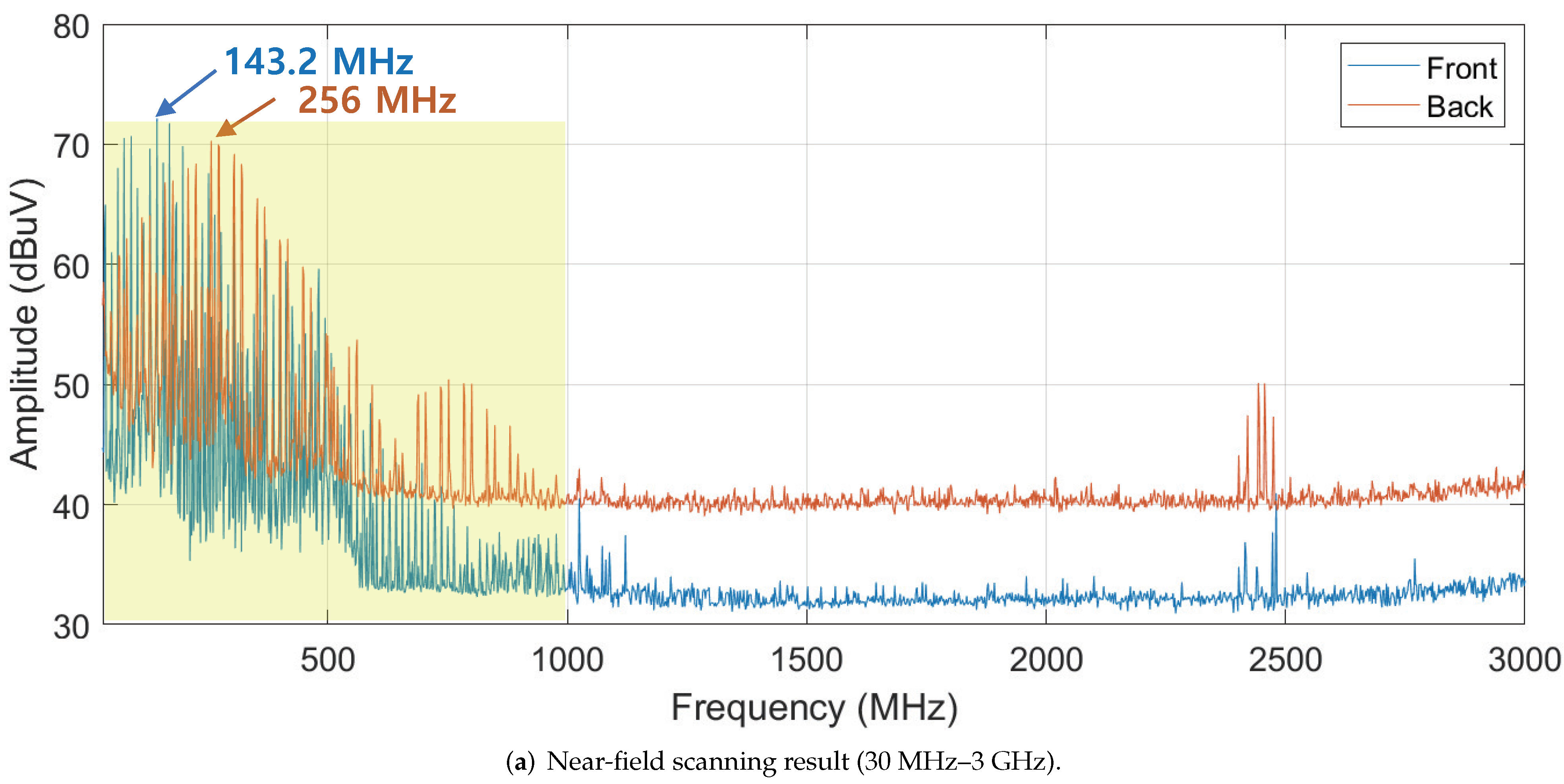
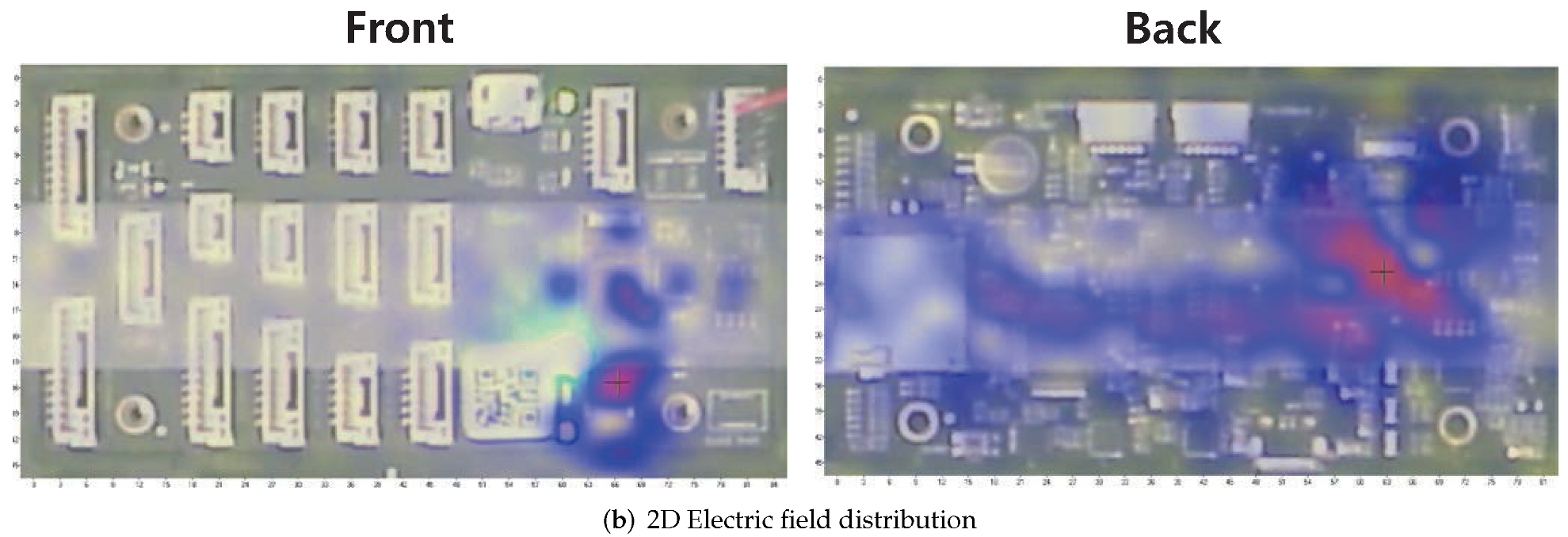
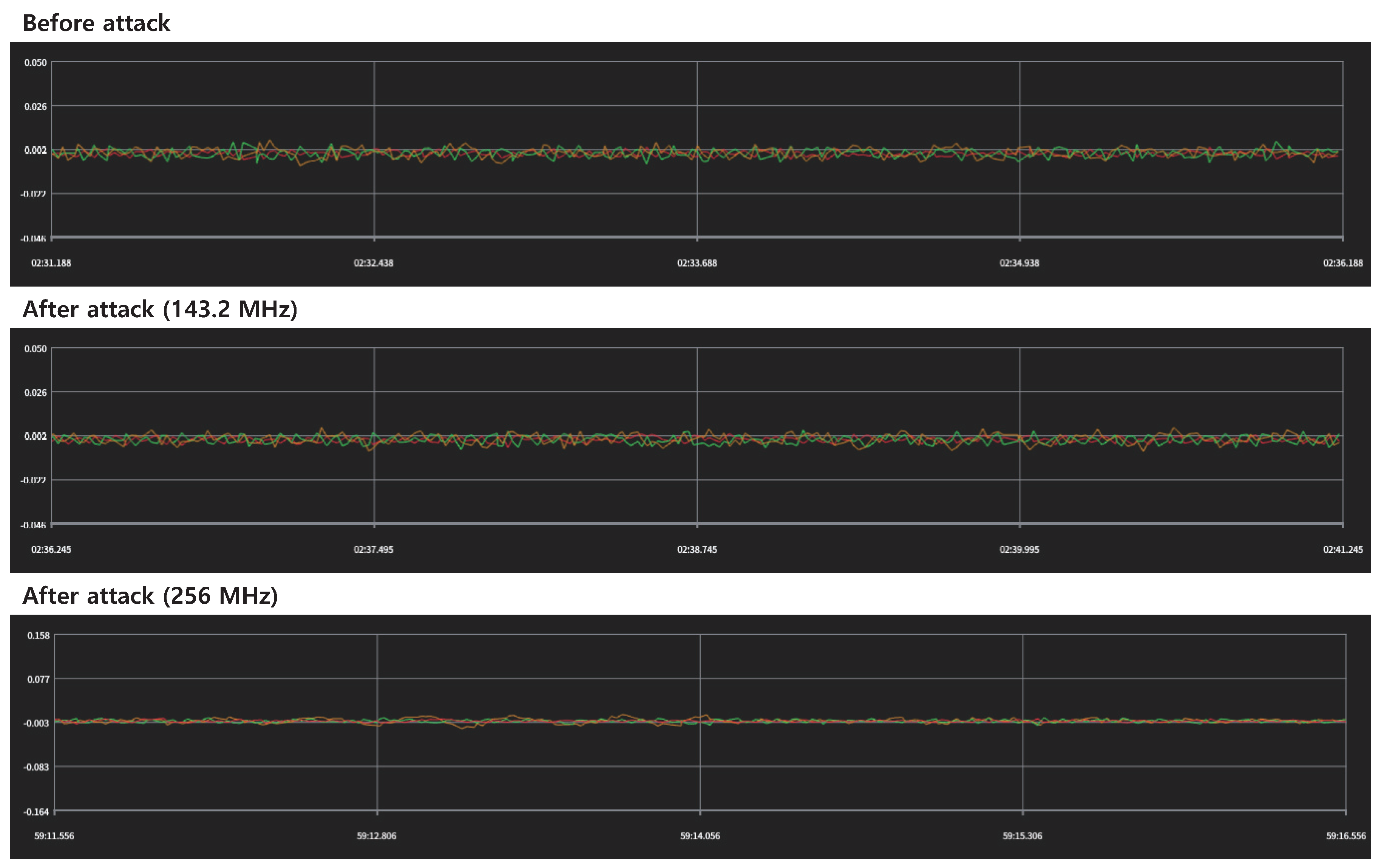
4.1.1. Near-Field Measurement
4.1.2. Interference Experiment
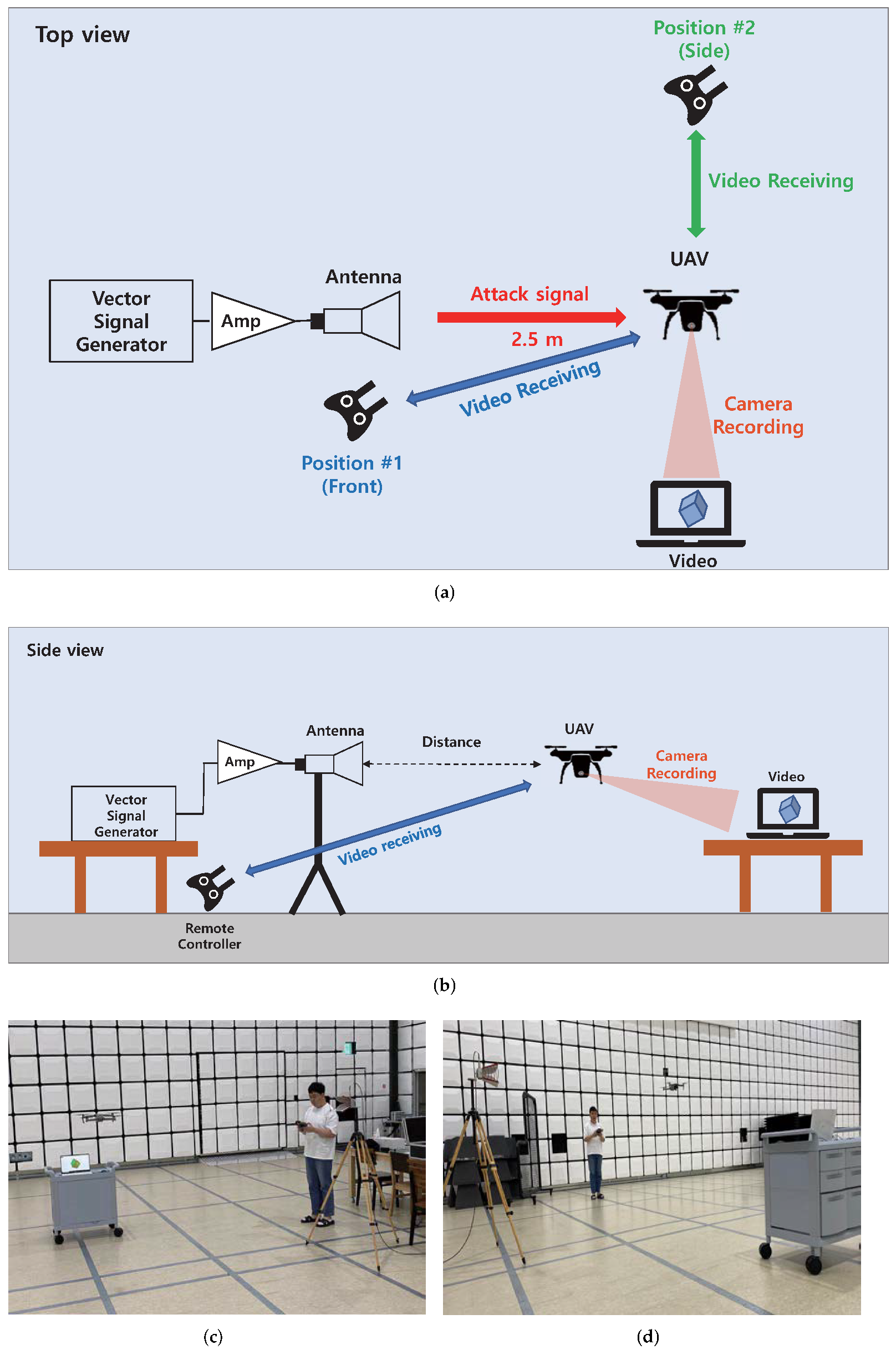
4.2. Camera Module Interfered by Low Power IEMI Source
4.2.1. Custom Drone
4.2.2. Commercial Drone (DJI Mavic Air2)
4.3. Optical Flow Sensor Interfered by Non-RF Source
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhilenkov, A.A.; Epifantsev, I.R. System of autonomous navigation of the drone in difficult conditions of the forest trails. In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow, Russia, 29 January–1 February 2018; pp. 1036–1039. [Google Scholar] [CrossRef]
- Hodge, V.J.; Hawkins, R.; Alexander, R. Deep reinforcement learning for drone navigation using sensor data. Neural Comput. Appl. 2021, 33, 2015–2033. [Google Scholar] [CrossRef]
- Zhang, C.; Zhang, W. Spectrum Sharing for Drone Networks. IEEE J. Sel. Areas Commun. 2017, 35, 136–144. [Google Scholar] [CrossRef]
- Shrit, O.; Martin, S.; Alagha, K.; Pujolle, G. A new approach to realize drone swarm using ad hoc network. In Proceedings of the 2017 16th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Budva, Montenegro, 28–30 June 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Dijkshoorn, N.; Visser, A. Integrating Sensor and Motion Models to Localize an Autonomous AR.Drone. Int. J. Micro Air Veh. 2011, 3, 183–200. [Google Scholar] [CrossRef] [Green Version]
- Zahran, S.; Moussa, A.; El-Sheimy, N. Enhanced drone navigation in GNSS denied environment using VDM and hall effect sensor. ISPRS Int. J. Geoinf. 2019, 8, 169. [Google Scholar] [CrossRef] [Green Version]
- Pobkrut, T.; Eamsa-ard, T.; Kerdcharoen, T. Sensor drone for aerial odor mapping for agriculture and security services. In Proceedings of the 2016 13th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Chiang Mai, Thailand, 28 June–1 July 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Saha, A.K.; Saha, J.; Ray, R.; Sircar, S.; Dutta, S.; Chattopadhyay, S.P.; Saha, H.N. IOT-based drone for improvement of crop quality in agricultural field. In Proceedings of the 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2018; pp. 612–615. [Google Scholar] [CrossRef]
- Lee, S.; Har, D.; Kum, D. Drone-Assisted Disaster Management: Finding Victims via Infrared Camera and Lidar Sensor Fusion. In Proceedings of the 2016 3rd Asia-Pacific World Congress on Computer Science and Engineering (APWC on CSE), Nadi, Fiji, 5–6 December 2016; pp. 84–89. [Google Scholar] [CrossRef]
- Restas, A. Drone applications for supporting disaster management. World J. Eng. Technol. 2015, 3, 316. [Google Scholar] [CrossRef] [Green Version]
- Allauddin, M.S.; Kiran, G.S.; Kiran, G.R.; Srinivas, G.; Mouli, G.U.R.; Prasad, P.V. Development of a surveillance system for forest fire detection and monitoring using drones. In Proceedings of the IGARSS 2019—2019 IEEE International Geoscience and Remote Sensing Symposium, Yokohama, Japan, 28 July–2 August 2019; pp. 9361–9363. [Google Scholar] [CrossRef]
- Vergouw, B.; Nagel, H.; Bondt, G.; Custers, B. Drone technology: Types, payloads, applications, frequency spectrum issues and future developments. In The Future of Drone Use; Springer: Berlin/Heidelberg, Germany, 2016; pp. 21–45. [Google Scholar] [CrossRef]
- Sanchez, A.; McKibben, C. Worst Case Scenario: The Criminal Use of Drones; Council on Hemispheric Affairs: Washington, DC, USA, 2015; Volume 2. [Google Scholar]
- Aker, C.; Kalkan, S. Using deep networks for drone detection. In Proceedings of the 2017 14th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS), Lecce, Italy, 29 August–1 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Bernardini, A.; Mangiatordi, F.; Pallotti, E.; Capodiferro, L. Drone detection by acoustic signature identification. Electron. Imaging 2017, 2017, 60–64. [Google Scholar] [CrossRef]
- Taha, B.; Shoufan, A. Machine learning-based drone detection and classification: State-of-the-art in research. IEEE Access 2019, 7, 138669–138682. [Google Scholar] [CrossRef]
- Al-Sa’d, M.F.; Al-Ali, A.; Mohamed, A.; Khattab, T.; Erbad, A. RF-based drone detection and identification using deep learning approaches: An initiative towards a large open source drone database. Future Gener. Comput. Syst. 2019, 100, 86–97. [Google Scholar] [CrossRef]
- Gumaei, A.; Al-Rakhami, M.; Hassan, M.M.; Pace, P.; Alai, G.; Lin, K.; Fortino, G. Deep learning and blockchain with edge computing for 5G-enabled drone identification and flight mode detection. IEEE Netw. 2021, 35, 94–100. [Google Scholar] [CrossRef]
- Lee, D.; La, W.G.; Kim, H. Drone detection and identification system using artificial intelligence. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 17–19 October 2018; pp. 1131–1133. [Google Scholar] [CrossRef]
- Shi, X.; Yang, C.; Xie, W.; Liang, C.; Shi, Z.; Chen, J. Anti-Drone System with Multiple Surveillance Technologies: Architecture, Implementation, and Challenges. IEEE Commun. Mag. 2018, 56, 68–74. [Google Scholar] [CrossRef]
- Radasky, W.; Baum, C.; Wik, M. Introduction to the special issue on high-power electromagnetics (HPEM) and intentional electromagnetic interference (IEMI). IEEE Trans. Electromagn. Compat. 2004, 46, 314–321. [Google Scholar] [CrossRef]
- Donatti, M.; Frazatto, F.; Manera, L.; Teramoto, T.; Neger, E. Radio frequency spoofing system to take over law-breaking drones. In Proceedings of the 2016 IEEE MTT-S Latin America Microwave Conference (LAMC), Puerto Vallarta, Mexico, 12–14 December 2016; pp. 1–3. [Google Scholar] [CrossRef]
- Adami, C.; Chmel, S.; Jöster, M.; Pusch, T.; Suhrke, M. Definition and test of the electromagnetic immunity of UAS for first responders. Adv. Radio Sci. 2015, 13, 141–147. [Google Scholar] [CrossRef] [Green Version]
- Zhang, D.; Zhou, X.; Cheng, E.; Wan, H.; Chen, Y. Investigation on Effects of HPM Pulse on UAV’s Datalink. IEEE Trans. Electromagn. Compat. 2019, 62, 829–839. [Google Scholar] [CrossRef]
- Hamdalla, M.; Bissen, B.; Hunter, J.D.; Yuanzhuo, L.; Khilkevich, V.; Beetner, D.G.; Caruso, A.N.; M Hassan, A. Prediction of Experimental Electromagnetic Coupling to a UAV Model Using Characteristic Mode Analysis. TechRxiv 2021. [Google Scholar] [CrossRef]
- Sabath, F. What can be learned from documented Intentional Electromagnetic Interference (IEMI) attacks? In Proceedings of the 2011 XXXth URSI General Assembly and Scientific Symposium, Istanbul, Turkey, 13–20 August 2011; pp. 1–4. [Google Scholar] [CrossRef]
- Mora, N.; Vega, F.; Lugrin, G.; Rachidi, F.; Rubinstein, M. Study and classification of potential IEMI sources. Syst. Des. Assess. Notes 2014, 41. Available online: https://infoscience.epfl.ch/record/200164 (accessed on 19 January 2022).
- Giri, D.V.; Tesche, F. Classification of Intentional Electromagnetic Environments (IEME). IEEE Trans. Electromagn. Compat. 2004, 46, 322–328. [Google Scholar] [CrossRef]
- Giechaskiel, I.; Rasmussen, K. Taxonomy and challenges of out-of-band signal injection attacks and defenses. IEEE Commun. Surv. Tutor. 2019, 22, 645–670. [Google Scholar] [CrossRef] [Green Version]
- Shin, H.; Kim, D.; Kwon, Y.; Kim, Y. Illusion and Dazzle: Adversarial Optical Channel Exploits Against Lidars for Automotive Applications. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2017, Taipei, Taiwan, 25–28 September 2017; Volume 10529, pp. 445–467. [Google Scholar] [CrossRef]
- Shin, H.; Son, Y.; Park, Y.; Kwon, Y.; Kim, Y. Sampling Race: Bypassing Timing-Based Analog Active Sensor Spoofing Detection on Analog-Digital Systems. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT 16), Austin, TX, USA, 8–9 August 2016. [Google Scholar]
- Giri, D.V.; Hoad, R.; Sabath, F. Implications of high-power electromagnetic (HPEM) environments on electronics. IEEE Electromagn. Compat. Mag. 2020, 9, 37–44. [Google Scholar] [CrossRef]
- Kasmi, C.; Lopes Esteves, J. IEMI Threats for Information Security: Remote Command Injection on Modern Smartphones. IEEE Trans. Electromagn. Compat. 2015, 57, 1752–1755. [Google Scholar] [CrossRef]
- Selvaraj, J.; Dayanıklı, G.Y.; Gaunkar, N.P.; Ware, D.; Gerdes, R.M.; Mina, M. Electromagnetic Induction Attacks Against Embedded Systems. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security, Incheon, Korea, 4–8 June 2018; ACM: New York, NY, USA, 2018; pp. 499–510. [Google Scholar] [CrossRef]
- Maurine, P. Techniques for EM Fault Injection: Equipments and Experimental Results. In Proceedings of the 2012 Workshop on Fault Diagnosis and Tolerance in Cryptography, Leuven, Belgium, 9 September 2012; pp. 3–4. [Google Scholar] [CrossRef] [Green Version]
- Hayashi, Y.i.; Homma, N.; Mizuki, T.; Aoki, T.; Sone, H. Transient IEMI Threats for Cryptographic Devices. IEEE Trans. Electromagn. Compat. 2013, 55, 140–148. [Google Scholar] [CrossRef]
- Trippel, T.; Weisse, O.; Xu, W.; Honeyman, P.; Fu, K. WALNUT: Waging Doubt on the Integrity of MEMS Accelerometers with Acoustic Injection Attacks. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS P), Paris, France, 26–28 April 2017; pp. 3–18. [Google Scholar] [CrossRef]
- Yan, C.; Xu, W.; Liu, J. Can you trust autonomous vehicles: Contactless attacks against sensors of self-driving vehicle. Def Con 2016, 24, 109. [Google Scholar] [CrossRef]
- Backstrom, M.; Lovstrand, K. Susceptibility of electronic systems to high-power microwaves: Summary of test experience. IEEE Trans. Electromagn. Compat. 2004, 46, 396–403. [Google Scholar] [CrossRef]
- Yu Sakharov, K.; Sukhov, A.; Ugolev, V.; Gurevich, Y. Study of UWB Electromagnetic Pulse Impact on Commercial Unmanned Aerial Vehicle. In Proceedings of the 2018 International Symposium on Electromagnetic Compatibility (EMC EUROPE), Amsterdam, The Netherlands, 27–30 August 2018; pp. 40–43. [Google Scholar] [CrossRef]
- Lubkowski, G.; Lanzrath, M.; Lavau, L.C.; Suhrke, M. Response of the UAV Sensor System to HPEM Attacks. In Proceedings of the 2020 International Symposium on Electromagnetic Compatibility-EMC EUROPE, Virtual, 23–25 September 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Delsing, J.; Ekman, J.; Johansson, J.; Sundberg, S.; Backstrom, M.; Nilsson, T. Susceptibility of sensor networks to intentional electromagnetic interference. In Proceedings of the 2006 17th International Zurich Symposium on Electromagnetic Compatibility, Singapore, 27 February–3 March 2006; pp. 172–175. [Google Scholar] [CrossRef] [Green Version]
- Esteves, J.L.; Cottais, E.; Kasmi, C. Unlocking the Access to the Effects Induced by IEMI on a Civilian UAV. In Proceedings of the 2018 International Symposium on Electromagnetic Compatibility (EMC EUROPE), Amsterdam, The Netherlands, 27–30 August 2018; pp. 48–52. [Google Scholar] [CrossRef]
- Kim, S.; Noh, Y.H.; Lee, J.; Lee, J.; Choi, J.S.; Yook, J.G. Electromagnetic Signature of a Quadcopter Drone and Its Relationship With Coupling Mechanisms. IEEE Access 2019, 7, 174764–174773. [Google Scholar] [CrossRef]
- Torrero, L.; Mollo, P.; Molino, A.; Perotti, A. RF immunity testing of an Unmanned Aerial Vehicle platform under strong EM field conditions. In Proceedings of the 2013 7th European Conference on Antennas and Propagation (EuCAP), Gothenburg, Sweden, 8–12 April 2013; pp. 263–267. [Google Scholar]
- Kune, D.F.; Backes, J.; Clark, S.S.; Kramer, D.; Reynolds, M.; Fu, K.; Kim, Y.; Xu, W. Ghost Talk: Mitigating EMI Signal Injection Attacks against Analog Sensors. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–22 May 2013; pp. 145–159. [Google Scholar] [CrossRef]
- Nishiyama, H.; Okamoto, T.; Kim, Y.; Fujimoto, D.; Hayashi, Y.I. Fundamental Study on Influence of Intentional Electromagnetic Interference on IC Communication. In Proceedings of the 2019 12th International Workshop on the Electromagnetic Compatibility of Integrated Circuits (EMC Compo), Hangzhou, China, 21–23 October 2019; pp. 201–203. [Google Scholar] [CrossRef]
- Poucheret, F.; Tobich, K.; Lisarty, M.; Chusseauz, L.; Robissonx, B.; Maurine, P. Local and Direct EM Injection of Power Into CMOS Integrated Circuits. In Proceedings of the 2011 Workshop on Fault Diagnosis and Tolerance in Cryptography, Tokyo, Japan, 29 September 2011; pp. 100–104. [Google Scholar] [CrossRef]
- Noh, J.; Kwon, Y.; Son, Y.; Shin, H.; Kim, D.; Choi, J.; Kim, Y. Tractor Beam: Safe-Hijacking of Consumer Drones with Adaptive GPS Spoofing. ACM Trans. Priv. Secur. 2019, 22, 1–26. [Google Scholar] [CrossRef]
- Rozenbeek, D.J. Evaluation of Drone Neutralization Methods using Radio Jamming and Spoofing Techniques. 2020. Available online: https://www.diva-portal.org/smash/get/diva2:1460807/FULLTEXT01.pdf (accessed on 19 January 2022).
- Ferreira, R.; Gaspar, J.; Souto, N.; Sebastião, P. Effective GPS Jamming Techniques for UAVs Using Low-Cost SDR Platforms. In Proceedings of the 2018 Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018; pp. 27–32. [Google Scholar] [CrossRef]
- Caforio, G.; Scazzoli, D.; Reggiani, L.; Magarini, M.; Moullec, Y.L.; Alam, M.M. A Configurable Radio Jamming Prototype for Physical Layer Attacks Against Malicious Unmanned Aerial Vehicles. In Proceedings of the 2020 17th Biennial Baltic Electronics Conference (BEC), Tallinn, Estonia, 6–8 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Son, Y.; Shin, H.; Kim, D.; Park, Y.; Noh, J.; Choi, K.; Choi, J.; Kim, Y. Rocking Drones with Intentional Sound Noise on Gyroscopic Sensors. In Proceedings of the 24th USENIX Security Symposium (USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 881–896. [Google Scholar]
- Martin, J.E.; Saul, V.; Novick, D.; Allen, D. Assessing the Vulnerability of Unmanned Aircraft Systems to Directed Acoustic Energy; Sandia National Lab.: Albuquerque, NM, USA, 2020. [Google Scholar] [CrossRef]
- Davidson, D.; Wu, H.; Jellinek, R.; Singh, V.; Ristenpart, T. Controlling UAVs with Sensor Input Spoofing Attacks. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT 16), Austin, TX, USA, 8–9 August 2016. [Google Scholar]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Feenstra, B.; Vlahacos, C.; Thanawalla, A.S.; Steinhauer, D.; Dutta, S.; Wellstood, F.; Anlage, S.M. Near-field scanning microwave microscopy: Measuring local microwave properties and electric field distributions. In Proceedings of the 1998 IEEE MTT-S International Microwave Symposium Digest (Cat. No. 98CH36192), Baltimore, MD, USA, 7–12 June 1998; Volume 2, pp. 965–968. [Google Scholar] [CrossRef] [Green Version]
- Weng, H.; Beetner, D.G.; DuBroff, R.E.; Shi, J. Estimation of current from near-field measurement. In Proceedings of the 2005 International Symposium on Electromagnetic Compatibility, Chicago, IL, USA, 8–12 August 2005; Volume 1, pp. 222–227. [Google Scholar] [CrossRef]
- Barreto, A.N.; Furrer, S. Adaptive bit loading for wireless OFDM systems. In Proceedings of the 12th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, PIMRC, (Cat. No. 01TH8598), San Diego, CA, USA, 30 September–3 October 2001; Volume 2. [Google Scholar] [CrossRef]








| Category | Main Target | Method | Specification |
|---|---|---|---|
| High Power IEMI | Electronic circuits | Antenna | - Destruction/degradation of the device using high-power EM wave |
| Low Power IEMI | Analog sensor | Antenna Coil | - Resonant frequency is needed for efficient coupling |
| Digital sensor | BCI DPI | - Injecting the signal to the target at near distance with probes - Antenna is not applicable because of not enough coupling | |
| Comm. module | Antenna | - Prior knowledge of RF communication channel is needed - In-band jamming | |
| Non RF | MEMS sensor | Acoustic | - Mechanical resonance of MEMS-based sensor |
| Optical flow | Laser | - Degrading the received image of optical flow sensor - Degraded image leads to the malfunction |
| Ref. | Target | Radiator | Signal Type/Strength |
|---|---|---|---|
| [39] | Unprotected Electronic System | Cassegrain Antenna Gain: 37–40 dB | Pulse Peak field: few kV/m PRF: 300 Hz–1 kHz |
| [40] | Commercial drone (DJI Phantom 3) | UWB EMP Radiator (4 TEM-horns) | UWB EMP FOM = E (V/m) * R (m) (1.6 kV, 3.5 kV, 49.5 kV) |
| [41] | Commercial quadcopter | Horn antenna | Narrowband pulse 100 MHz–3.4 GHz PRF: 1 kHz |
| [42] | Sensor network (MULLE) | Horn antenna | Continuous wave 2–3 GHz Field peak: 0.24–0.36 kV/m |
| [43] | COTS Quadcopter | - | Continuous wave 100 MHz–2 GHz Field: 75 V/m–95 V/m |
| Ref. | Target | Method | Signal Type/Strength |
|---|---|---|---|
| [45] | Drone (Mikrokopter) | Radiated EMI | Continuous wave 470–862 MHz 1.4–2.7 GHz 10 V/m |
| [46] | Analog sensors (CIEDs, Mic) | Radiated EMI | - Baseband 0.1 Hz–1 kHz High power - Modulated Resonant frequencies Low power |
| [47] | Evaluation board (SASEBO-G) | Bulk Current Injection (BCI) | Injection probe 1–400 MHz 40 dBm |
| [48] | CMOS IC | Direct Power Injection (DPI) | Micro-probe 100–2000 m −40.81∼−1.27 dBm |
| [49] | Drone | GPS Spoofing | GNSS emulator Emulated GLONASS |
| [50] | Drone | GPS, RC, Video Jamming/Spoofing | Various Jamming/Spoofing |
| [51] | Drone | GPS Jamming | 5 types of jamming |
| [52] | Drone | RC Jamming | Sweep jamming |
| Ref. | Target | Method | Signal Type/Strength |
|---|---|---|---|
| [53] | MEMS gyroscope | Acoustic | Bluetooth Speaker Distance: 10 cm SPL: 113 dB |
| [37] | MEMS Accelerometer | Acoustic | Speaker 2–30 kHz |
| [54] | Drone | Acoustic | Explosive C-4 Directed acoustic energy (pressure impulses) 3–40.6 psi |
| [55] | Optical flow | Projector Laser | Projector/Laser Distance: 4 feet/10 feet 138–438 lux |
| [30] | Lidar | Laser | - Saturating 30 mW, 905 nm (weak) 800 mW, 905 nm (strong) - Spoofing by relay Pulsed Laser Diode (PLD) |
| Changes in Video Quality | ||
|---|---|---|
| Level | Description | Status |
| 1 | No effects observed | Normal |
| 2 | Low video quality, but identifiable (Whitening, dot pattern, lagging, etc.) | Degradation |
| 3 | Unable to identify the video | Disable |
| Scenario | Freq (GHz) | Distance | Power (dBm) | Detail |
|---|---|---|---|---|
| 1 | 5.7∼5.8 | 0.3 m | 23 (Max) | - Frequency sweep - Max power of signal generator - Effective frequency range analysis |
| 2 | 5.74 | 0.3 m | −20∼11 | - Power level sweep - Frequency fixed at transmission frequency - Effective signal power analysis |
| 3 | 5.72∼5.75 | 0.3 m | 10 | - Frequency sweep - Power level decided in Scenario 2 |
| Scenario | Status | Frequency Difference (, MHz) | (dBm) |
|---|---|---|---|
| 1 | Normal | >17 | 23 |
| Degradation | 15∼17 | 23 | |
| Disable | ≦14 | 23 | |
| 2 | Normal | - | ∼−4 |
| Degradation | - | −5∼9 | |
| Disable | - | 10∼ | |
| 3 | Normal | >8 | 10 |
| Degradation | 6∼8 | 10 | |
| Disable | ≦5 | 10 |
| Scenario | Freq | Distance (m) | Level (dBm) | Position |
|---|---|---|---|---|
| 1 | : 2.43 GHz BW: 20 MHz | 2.5 | 0∼8 | Front |
| 2 | : 2.33–2.53 GHz BW: 20 MHz | 2.5 | 8 | Front |
| 3 | : 2.43 GHz BW: 20 MHz | 2.5 | 0∼8 | Side |
| 4 | : 2.33–2.53 GHz BW: 20 MHz | 2.5 | 8 | Side |
| Scenario | Status | Description | Cause |
|---|---|---|---|
| 1 | Degradation | - From 6 dBm - No distortion - Lagging | - No bit loss due to gradual decrease of SNR - Data rate reduction by low SNR |
| 2 | Degradation | - Center: 2.44 GHz - Serious distortion for short period - Lagging | - Bit loss due to radical decrease of SNR - Data rate reduction by low SNR |
| 3 | Normal | - No effect observed | - Small path overlap between communication and interference channel |
| 4 | Normal | - No effect observed | - Small path overlap between communication and interference channel |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, S.-G.; Lee, E.; Hong, I.-P.; Yook, J.-G. Review of Intentional Electromagnetic Interference on UAV Sensor Modules and Experimental Study. Sensors 2022, 22, 2384. https://doi.org/10.3390/s22062384
Kim S-G, Lee E, Hong I-P, Yook J-G. Review of Intentional Electromagnetic Interference on UAV Sensor Modules and Experimental Study. Sensors. 2022; 22(6):2384. https://doi.org/10.3390/s22062384
Chicago/Turabian StyleKim, Sung-Geon, Euibum Lee, Ic-Pyo Hong, and Jong-Gwan Yook. 2022. "Review of Intentional Electromagnetic Interference on UAV Sensor Modules and Experimental Study" Sensors 22, no. 6: 2384. https://doi.org/10.3390/s22062384






