Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation
Abstract
:1. Introduction
2. Related Works
2.1. Encryption Algorithms
2.2. IoT System Architecture
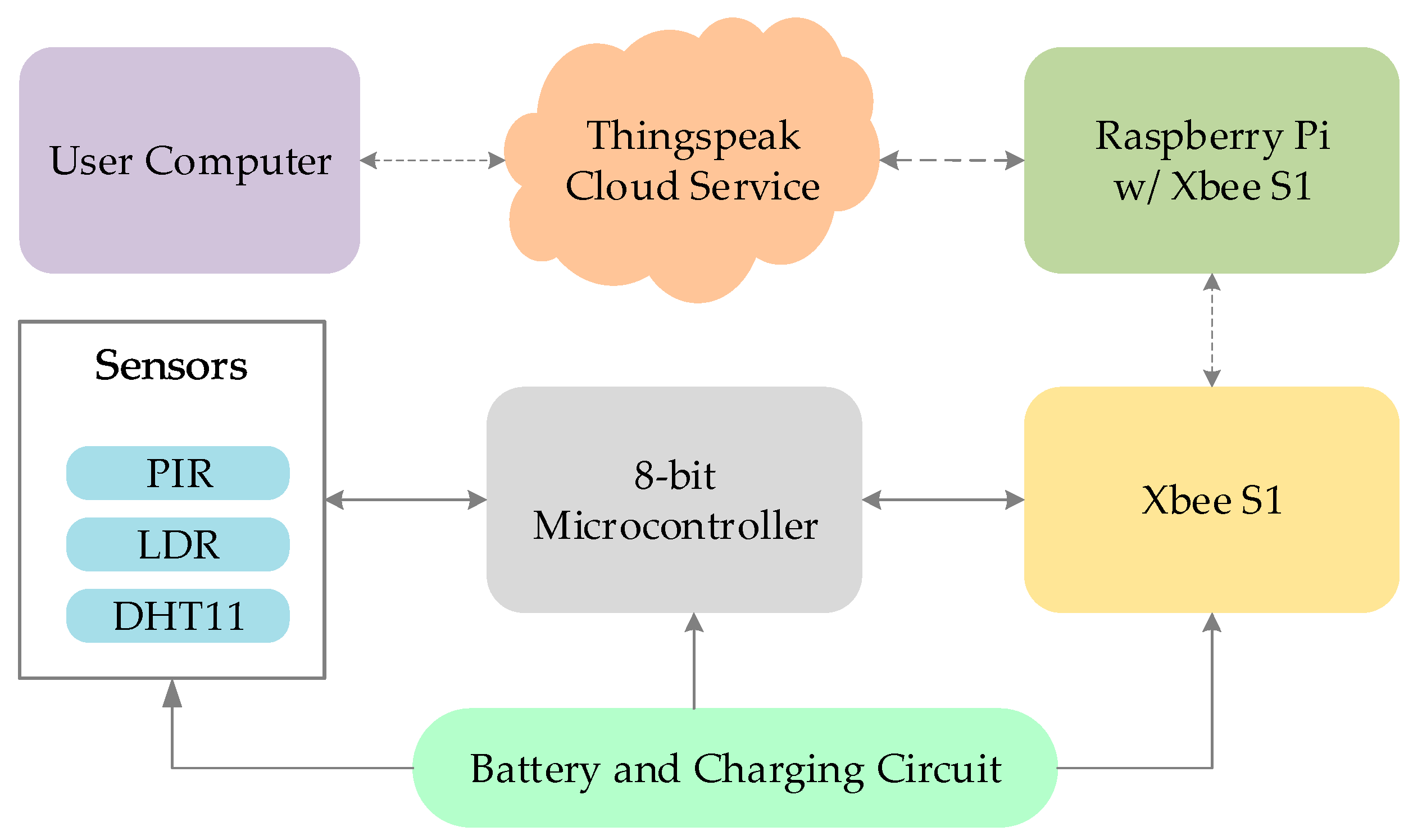
3. Lab-in-a-Box (LiB) Architecture
3.1. Modular System Architecture
3.1.1. Power Supply
3.1.2. Sensors
3.1.3. Microcontroller
3.1.4. Wireless Technologies
3.1.5. Internet Gateway
3.1.6. Cloud Server
3.2. Encryption Algorithms
3.2.1. AES Implementation
3.2.2. XTEA Implementation
4. Application Implementation
4.1. Testbed Setup
4.2. Occupancy Monitoring
4.3. Indoor Environmental Monitoring
4.4. Fall Detection for Elderly
5. Results and Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Mahmud, M.A.; Bates, K.; Wood, T.; Abdelgawad, A.; Yelamarthi, K. A complete Internet of Things (IoT) platform for Structural Health Monitoring (SHM). In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 275–279. [Google Scholar]
- Yelamarthi, K.; Abdelgawad, A.; Khattab, A. IoT-Based Health Monitoring System for Active and Assisted Living. In Proceedings of the Smart Objects and Technologies for Social Good: Second International Conference (GOODTECHS 2016), Venice, Italy, 30 November–1 December 2016; pp. 11–20. [Google Scholar]
- Fortino, G.; Russo, W.; Savaglio, C.; Viroli, M.; Zhou, M. Modeling opportunistic IoT services in open IoT ecosystems. In Proceedings of the 17th Workshop from Objects to Agents WOA, Catania, Italy, 29–30 July 2017; pp. 90–95. [Google Scholar]
- Zhang, Z.; Cho, M.C.Y.; Wang, C.; Hsu, C.; Chen, C.; Shieh, S. IoT Security: Ongoing Challenges and Research Opportunities. In Proceedings of the IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 230–234. [Google Scholar]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Botta, M.; Simek, M.; Mitton, N. Comparison of hardware and software-based encryption for secure communication in wireless sensor networks. In Proceedings of the 2013 36th International Conference on Telecommunications and Signal Processing (TSP), Rome, Italy, 2–4 July 2013; pp. 6–10. [Google Scholar]
- Richards, D.; Abdelgawad, A.; Yelamarthi, K. How Does Encryption Influence Timing in IoT? In Proceedings of the 2018 IEEE Global Conference on Internet of Things, Alexandria, Egypt, 5–7 December 2018; pp. 1–5. [Google Scholar]
- Kotel, S.; Sbiaa, F.; Zeghid, M.; Machhout, M.; Baganne, A.; Tourki, R. Performance evaluation and design considerations of a lightweight block cipher for low-cost embedded devices. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–7. [Google Scholar]
- Yelamarthi, K.; Aman, M.S.; Abdelgawad, A. An application-driven modular IoT architecture. Wirel. Commun. Mob. Comput. 2017, 2017, 1350929. [Google Scholar] [CrossRef]
- Krco, S.; Pokric, B.; Carrez, F. Designing IoT architecture(s): A European perspective. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 79–84. [Google Scholar]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Islamabad, India, 17–19 December 2012; pp. 257–260. [Google Scholar]
- Gazis, V.; Goertz, M.; Huber, M.; Leonardi, A.; Mathioudakis, K.; Wiesmaier, A.; Zeiger, F. Short Paper: IoT: Challenges, projects, architectures. In Proceedings of the 2015 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; pp. 145–147. [Google Scholar] [CrossRef]
- Faisal, M.A.; Bakar, S.; Rudati, P.S. The development of a data acquisition system based on internet of things framework. In Proceedings of the 2014 International Conference on ICT For Smart Society (ICISS), Bandung, Indonesia, 24–25 September 2014; pp. 211–216. [Google Scholar]
- Eisenbarth, T.; Kumar, S.; Paar, C.; Poschmann, A.; Uhsadel, L. A survey of lightweight-cryptography implementations. IEEE Des. Test 2007, 24, 522–533. [Google Scholar] [CrossRef]
- Agrawal, M.; Mishra, P. A comparative survey on symmetric key encryption techniques. Int. J. Comput. Sci. Eng. 2012, 4, 877–882. [Google Scholar]
- Thambiraja, E.; Ramesh, G.; Umarani, R. A survey on various most common encryption techniques. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2012, 2, 226–233. [Google Scholar]
- Mahajan, P.; Sachdeva, A. A study of Encryption algorithms AES, DES and RSA for security. Glob. J. Comput. Sci. Technol. 2013, 13. Available online: https://computerresearch.org/index.php/computer/article/view/272 (accessed on 27 May 2019).
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK Families of Lightweight Block Ciphers. IACR Cryptol. ePrint Arch. 2013, 2013, 404. [Google Scholar]
- Cannière, C.; Dunkelman, O.; Knežević, M. KATAN and KTANTAN—A family of small and efficient hardware-oriented block ciphers. Lect. Notes Comput. Sci. 2009, 5747, 272–288. [Google Scholar]
- Bogdanov, A.; Knudsen, L.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.; Seurin, Y.; Vikkelsoe, C. PRESENT: An ultra-lightweight block cipher. Lect. Notes Comput. Sci. 2007, 4727, 450–466. [Google Scholar]
- Eisenbarth, T.; Gong, Z.; Guneysu, T.; Heyse, S.; Indesteege, S.; Kerckhof, S.; Koeune, F.; Nad, T.; Plos, T.; Regazzoni, F.; et al. Compact Implementation and Performance Evaluation of Block Ciphers in ATtiny Devices. In Proceedings of the 5th International Conference on Cryptology in Africa, Ifrance, Morocco, 10–12 July 2012; pp. 172–187. [Google Scholar]
- Appel, M.; Bossert, A.; Cooper, S.; Kußmaul, T.; Löffler, J.; Pauer, C.; Wiesmaier, A. Block Ciphers for the IoT–SIMON, SPECK, KATAN, LED, TEA, PRESENT, and SEA Compared. 2016. Available online: https://download.hrz.tu-darmstadt.de/pub/FB20/Dekanat/Publikationen/CDC/2016-09-05_TR_SimonSpeckKatanLedTeaPresentSea.pdf (accessed on 28 May 2019).
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on Internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Zhang, F. On the Security and Energy Consumption Estimation of Wireless Sensor Network Protocols. Ph.D. Thesis, University of Limerick, Limerick, Ireland, 5 November 2012. [Google Scholar]
- Xiao, Y.; Chen, H.; Sun, B.; Wang, R.; Sethi, S. MAC security and security overhead analysis in the IEEE 802.15.4 wireless sensor networks. EURASIP J Wirel Commun Netw. 2006, 2006, 81. [Google Scholar] [CrossRef]
- Barahtian, O.; Cuciuc, M.; Petcana, L.; Leordeanu, C.; Cristea, V. Evaluation of Lightweight Block Ciphers for Embedded Systems. In Innovative Security Solutions for Information Technology and Communications; Bica, I., Naccache, D., Simion, E., Eds.; Springer: Cham, Switzerland, 2015; pp. 49–58. ISBN 978-3-319-27179-8. [Google Scholar]
- Noura, H.; Chehab, A.; Sleem, L.; Noura, M.; Couturier, R.; Mansour, M. One round cipher algorithm for multimedia IoT devices. Multimed. Tools Appl. 2018, 77, 18383–18413. [Google Scholar] [CrossRef]
- Biryukov, A.; Perrin, L. State of the Art in Lightweight Symmetric Cryptography; International Association for Cryptologic Research: Esch-sur-Alzette, Luxembourg, 2017. [Google Scholar]
- Wetzels, J.; Bokslag, W. Simple SIMON: FPGA implementations of the SIMON 64/128 Block Cipher. arXiv 2015, arXiv:1507.06368. [Google Scholar]
- Bui, D.H.; Puschini, D.; Bacles-Min, S.; Beigné, E.; Tran, X.T. AES datapath optimization strategies for low-power low-energy multisecurity-level internet-of-things applications. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 3281–3290. [Google Scholar] [CrossRef]
- Shirai, T.; Shibutani, K.; Akishita, T.; Moriai, S.; Iwata, T. The 128-bit blockcipher CLEFIA. In Proceedings of the 14th International Workshop on Fast Software Encryption—FSE’07, Luxembourg, 26–28 March 2007; pp. 181–195. [Google Scholar]
- Aysu, A.; Gulcan, E.; Schaumont, P. SIMON Says, Break Area Records of Block Ciphers on FPGAs. IEEE Embed. Syst. Lett. 2014, 6, 37–40. [Google Scholar] [CrossRef]
- Singh, A.; Chawla, N.; Ko, J.H.; Kar, M.; Mukhopadhyay, S. Energy efficient and side-channel secure cryptographic hardware for IoT-edge nodes. IEEE Internet Things J. 2019, 6, 421–434. [Google Scholar] [CrossRef]
- Needham, R.M.; Wheeler, D.J. Tea Extensions; Technical Report; Cambridge University: Cambridge, UK, 1997. [Google Scholar]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef] [Green Version]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IOT security and privacy: The case study of a smart home. In Proceedings of the 2nd IEEE Percom Workshop on Security Privacy and Trust in the Internet of Things, Hawaii, HI, USA, 13–17 March 2017. [Google Scholar]
- Weekly, K.; Jin, M.; Zou, H.; Hsu, C.; Soyza, C.; Bayen, A.; Spanos, C. Building-in-Briefcase: A Rapidly-Deployable Environmental Sensor Suite for the Smart Building. Sensors 2018, 18, 1381. [Google Scholar] [CrossRef]
- Wu, F.; Rüdiger, C.; Redouté, J.M.; Yuce, M.R. WE-Safe: A wearable IoT sensor node for safety applications via LoRa. In Proceedings of the IEEE 4th World Forum Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 144–148. [Google Scholar]
- Aman, M.S.; Quint, C.D.; Abdelgawad, A.; Yelamarthi, K. Sensing and classifying indoor environments: An IoT based portable tour guide system. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–6. [Google Scholar]
- Gupta, G.S.; Quan, V.M. Multi-sensor integrated system for wireless monitoring of greenhouse environment. In Proceedings of the 2018 IEEE Sensors Applications Symposium (SAS), Seoul, Korea, 12–14 March 2018; pp. 1–6. [Google Scholar]
- Guan, G.; Fu, K.; Cheng, Z.; Gao, Y.; Dong, W. Rapid development of IoT applications with TinyLink. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 956–957. [Google Scholar]
- Guan, G.; Dong, W.; Gao, Y.; Bu, J. Towards rapid and cost-effective prototyping of IoT platforms. In Proceedings of the 2016 IEEE 24th International Conference on Network Protocols (ICNP), Singapore, 9–11 November 2016; pp. 1–5. [Google Scholar]
- Tabesh, A.; Fréchette, L.G. A Low-Power Stand-Alone Adaptive Circuit for Harvesting Energy from a Piezoelectric Micropower Generator. IEEE Trans. Ind. Electron. 2010, 57, 840–849. [Google Scholar] [CrossRef]
- Toh, W.Y.; Tan, Y.K.; Koh, W.S.; Siek, L. Autonomous Wearable Sensor Nodes with Flexible Energy Harvesting. IEEE Sens. J. 2014, 14, 2299–2306. [Google Scholar] [CrossRef]
- Bandodkar, A.J.; Jia, W.; Wang, J. Tattoo-based wearable electrochemical devices: A review. Electroanalysis 2015, 27, 562–572. [Google Scholar] [CrossRef]
- ZigBee Alliance. Available online: http://www.zigbee.org (accessed on 17 April 2019).
- Baronti, P.; Pillai, P.; Chook, V.; Chessa, S.; Gotta, A.; Fun Hu, Y. Wireless sensor networks: A survey on the state of the art and the 802.15.4 and ZigBee standards. Comput. Commun. 2007, 30, 1655–1695. [Google Scholar] [CrossRef]
- Vivek, G.V.; Sunil, M.P. Enabling IOT services using WIFI-ZigBee gateway for a home automation system. In Proceedings of the 2015 IEEE International Conference on Research in Computational Intelligence and Communication Networks (ICRCICN), Kolkata, India, 20–22 November 2015; pp. 77–80. [Google Scholar]
- Gomez, C.; Oller, J.; Paradells, J. Overview and Evaluation of Bluetooth Low Energy: An Emerging Low-Power Wireless Technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Siekkinen, M.; Hiienkari, M.; Nurminen, J.K.; Nieminen, J. How low energy is Bluetooth low energy? Comparative measurements with ZigBee/802.15.4. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Paris, France, 1 April 2012; pp. 232–237. [Google Scholar]
- Mikhaylov, K.; Petaejaejaervi, J.; Haenninen, T. Analysis of capacity and scalability of the LoRa low power wide area network technology. In Proceedings of the 22nd European Wireless Conference (European Wireless 2016), Oulu, Finland, 18–20 May 2016; pp. 1–6. [Google Scholar]
- Sanchez-Iborra, R.; Sanchez-Gomez, J.; Ballesta-Viñas, J.; Cano, M.D.; Skarmeta, A.F. Performance Evaluation of LoRa Considering Scenario Conditions. Sensors 2018, 18, 772. [Google Scholar] [CrossRef]
- Evrythng. Available online: https://evrythng.com (accessed on 12 May 2019).
- Thingworx. Available online: https://www.ptc.com/en/products/IoT (accessed on 12 May 2019).
- Pintus, A.; Carboni, D.; Piras, A. Paraimpu: A platform for a social web of things. In Proceedings of the 21st International Conference on World Wide Web, Lyon, France, 16–20 April 2012; pp. 401–404. [Google Scholar]
- PIC18(L)F27/47K40. Available online: http://ww1.microchip.com/downloads/en/DeviceDoc/PIC18LF27_47K40-Data-Sheet-40001844E.pdf (accessed on 17 April 2019).
- PIC18(L)F24/25K42. Available online: http://ww1.microchip.com/downloads/en/devicedoc/40001869b.pdf (accessed on 17 April 2019).
- Real-Time Current Monitor with USB. Available online: https://www.ee-quipment.com/products/real-time-current-monitor-with-usb (accessed on 17 April 2019).
- DIGI XBEE® S1 802.15.4 RF MODULES. Available online: https://www.digi.com/pdf/ds_xbeemultipointmodules.pdf (accessed on 17 April 2019).
- DHT11 Humidity & Temperature Sensor. Available online: https://www.mouser.com/ds/2/758/DHT11-Technical-Data-Sheet-Translated-Version-1143054.pdf (accessed on 17 April 2019).
- ATmega8/ATmega8L. Available online: https://ww1.microchip.com/downloads/en/DeviceDoc/Atmel-2486-8-bit-AVR-microcontroller-ATmega8_L_datasheet.pdf (accessed on 17 April 2019).
- BME680. Available online: https://cdn-shop.adafruit.com/product-files/3660/BME680.pdf (accessed on 17 April 2019).
- 4-GHz Bluetooth® Low Energy System-On-Chip. Available online: http://www.ti.com/lit/ds/symlink/cc2540.pdf (accessed on 17 April 2019).
- MSP432P401R, MSP432P401M SimpleLink™ Mixed-Signal Microcontrollers. Available online: http://www.ti.com/lit/ds/symlink/msp432p401r.pdf (accessed on 17 April 2019).
- RFM95/96/97/98 (W). Available online: https://cdn.sparkfun.com/assets/learn_tutorials/8/0/4/RFM95_96_97_98W.pdf (accessed on 17 April 2019).
- PubNub. Available online: https://www.pubnub.com/ (accessed on 12 May 2019).
- Fortino, G.; Russo, W.; Savaglio, C. Agent-oriented modeling and simulation of IoT networks. In Proceedings of the Federated Conference on Computer Science and Information Systems (FedCSIS), Gdansk, Poland, 11–14 September 2016; pp. 1449–1452. [Google Scholar]













| Component | Active Current (mA) | Sleep Current (mA) |
|---|---|---|
| 8-bit MCU | 5 | 1 |
| XBee S1 | 50 | 0.03 |
| PIR | 10 | 10 |
| LDR | 0.4 | 0.4 |
| DHT11 | 1 | 0.1 |
| Total | 66.4 | 11.5 |
| Component | Active Current (mA) | Sleep Current (mA) |
|---|---|---|
| 8-bit MCU | 0.2 | 0.06 |
| CC2540 BLE | 30 | 0.3 |
| BME680 | 0.1 | 0.01 |
| LDR | 0.4 | 0.4 |
| Total | 30.7 | 0.77 |
| Component | Active Current (mA) | Sleep Current (mA) |
|---|---|---|
| 32-bit MCU | 4 | 0.8 |
| RFM95W | 50 | 0.8 |
| ADXL345 | 0.2 | 0.01 |
| Total | 54.2 | 1.6 |
| AES-128 | AES-256 | XTEA | SEA | ||
|---|---|---|---|---|---|
| SW | HW | ||||
| Size (bytes) | 13609 | 16251 | 1258 | 1946 | 3765 |
| RAM (bytes) | 2956 | 3508 | 576 | 556 | 983 |
| Time (ms) | 237.3 | 281.5 | 0.5 | 1.196 | 1.23 |
| Energy (mJ) | 5.2 | 6.1 | 0.0109 | 0.026 | 0.03 |
| AES-128 | AES-256 | XTEA | SEA | |
|---|---|---|---|---|
| Size (bytes) | 6368 | 7538 | 1184 | 2296 |
| RAM (bytes) | 986 | 1105 | 99 | 126 |
| Time (ms) | 62.3 | 75.62 | 1.25 | 2.3 |
| Energy (mJ) | 1.27 | 1.45 | 0.024 | 0.03 |
| Application | Without Encryption | With Encryption | |
|---|---|---|---|
| AES-256 | XTEA | ||
| Occupancy Monitoring System | 357.46 | 382.89 | 378.76 |
| Indoor Environmental Monitoring | 167.13 | 183.53 | 176.39 |
| Fall Detection for Elderly | 182.02 | 186.43 | 203.41 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maitra, S.; Yelamarthi, K. Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation. Sensors 2019, 19, 2484. https://doi.org/10.3390/s19112484
Maitra S, Yelamarthi K. Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation. Sensors. 2019; 19(11):2484. https://doi.org/10.3390/s19112484
Chicago/Turabian StyleMaitra, Sudip, and Kumar Yelamarthi. 2019. "Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation" Sensors 19, no. 11: 2484. https://doi.org/10.3390/s19112484





