An Outlier Detection Method Based on Mahalanobis Distance for Source Localization
Abstract
:1. Introduction
- The division and greedy replacement (DIG) method is developed to estimate the target positions.
- The Mahalanobis distance based on robust estimation of mean and covariance matrix is proposed to detect the outliers from estimated source positions.
- An improved WLS localization method based on reliable probabilities and distances is introduced.
- Outdoor experiments are conducted to verify the proposed method.
2. AOA-Based Localization Method and Problem Statement
2.1. The Pseudolinear Estimator (PLE)
2.2. Problem Formulation
3. The DIG_MD Method
3.1. The Division and Greedy Replacement (DIG) Method
| Algorithm 1. Selection method of reference nodes. |
|
| Algorithm 2. Greedy Replacement Method. |
| For k = 1:m |
| For j = m + 1:N |
| end |
| end |
3.2. Outlier Detection Method for Estimated Target Position Sets
| Algorithm 3. Outlier detection method from . |
|
3.3. WLS Based on Reliable Probability and Distance
| Algorithm 4. The procedure of the proposed method based on DIG and MD: DIG_MD. |
|
4. Simulations
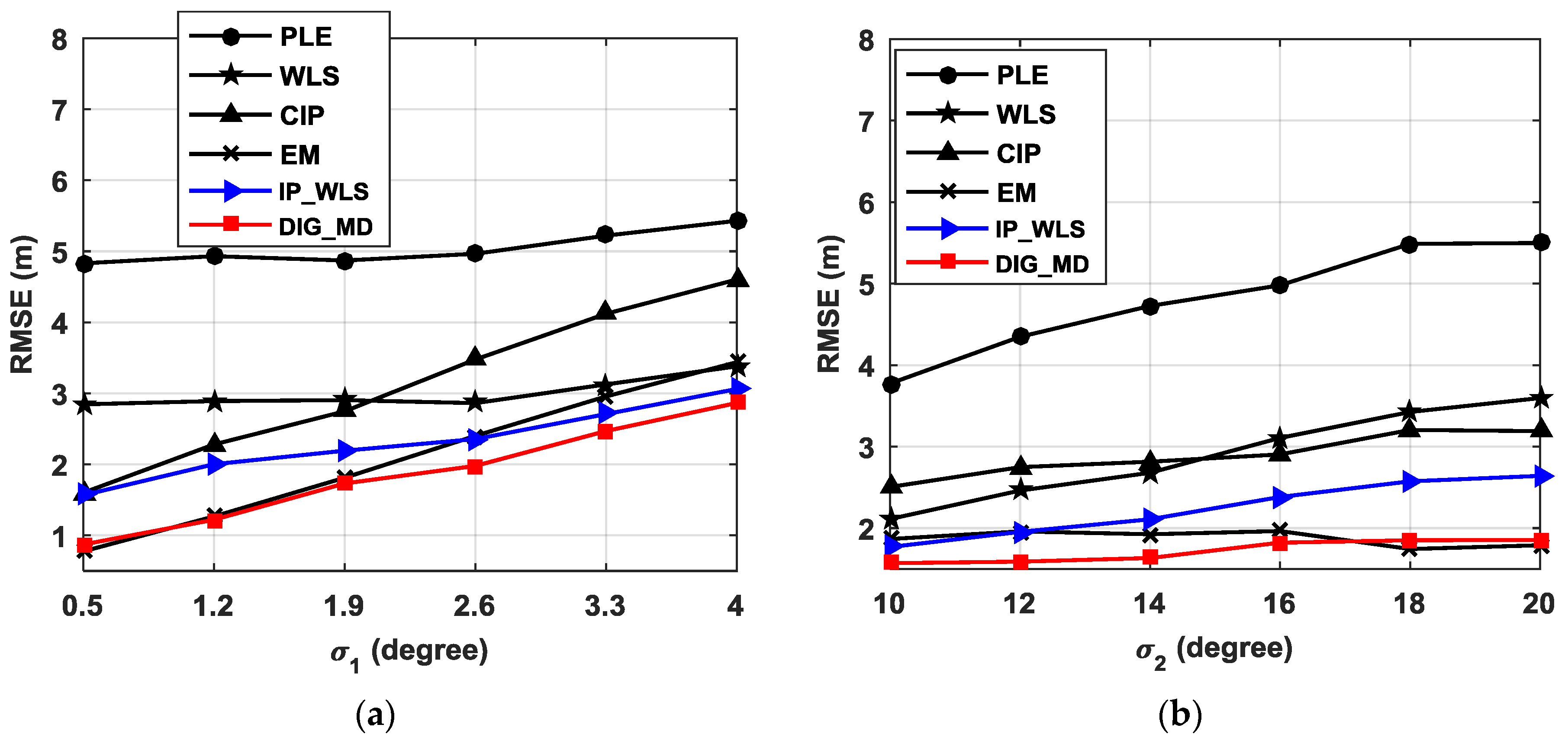
4.1. The RMSEs for Different and
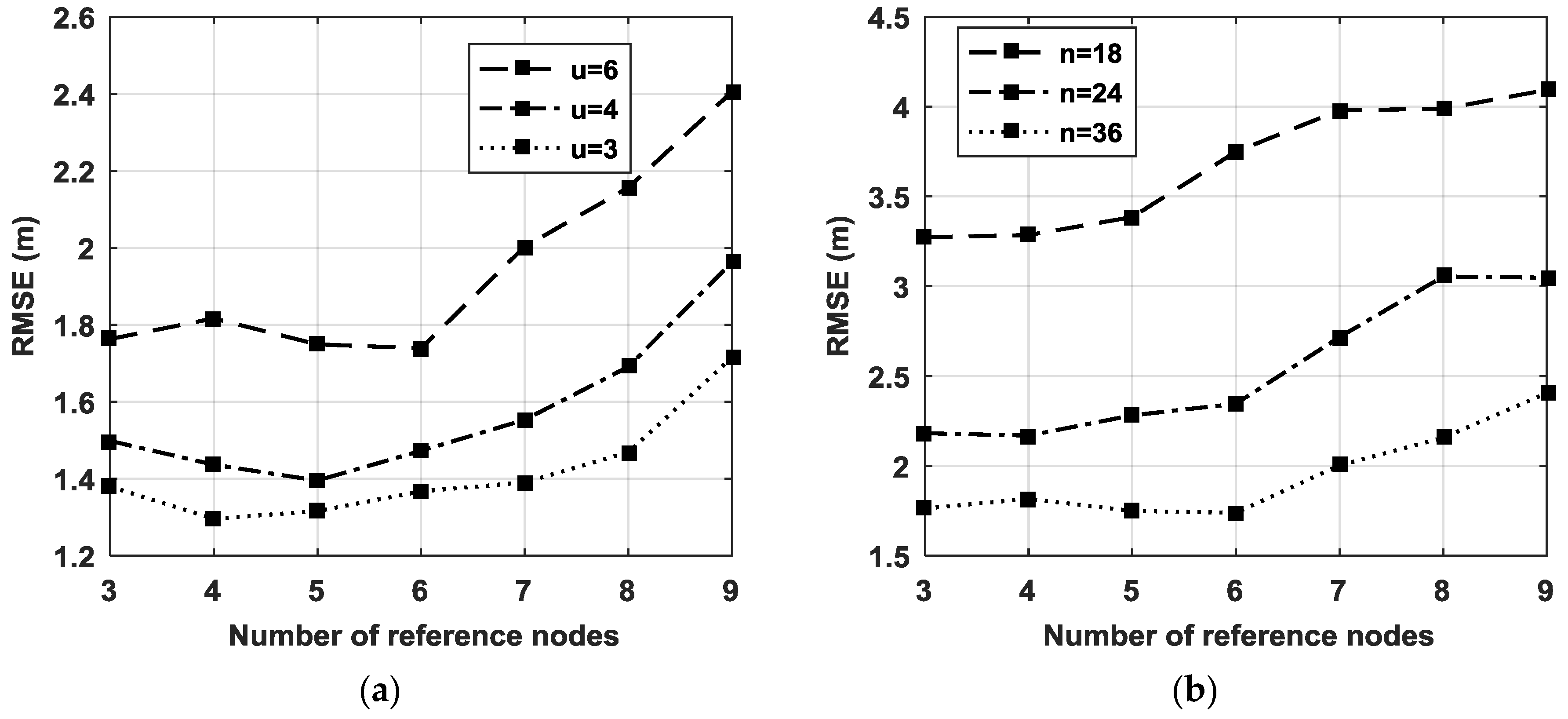
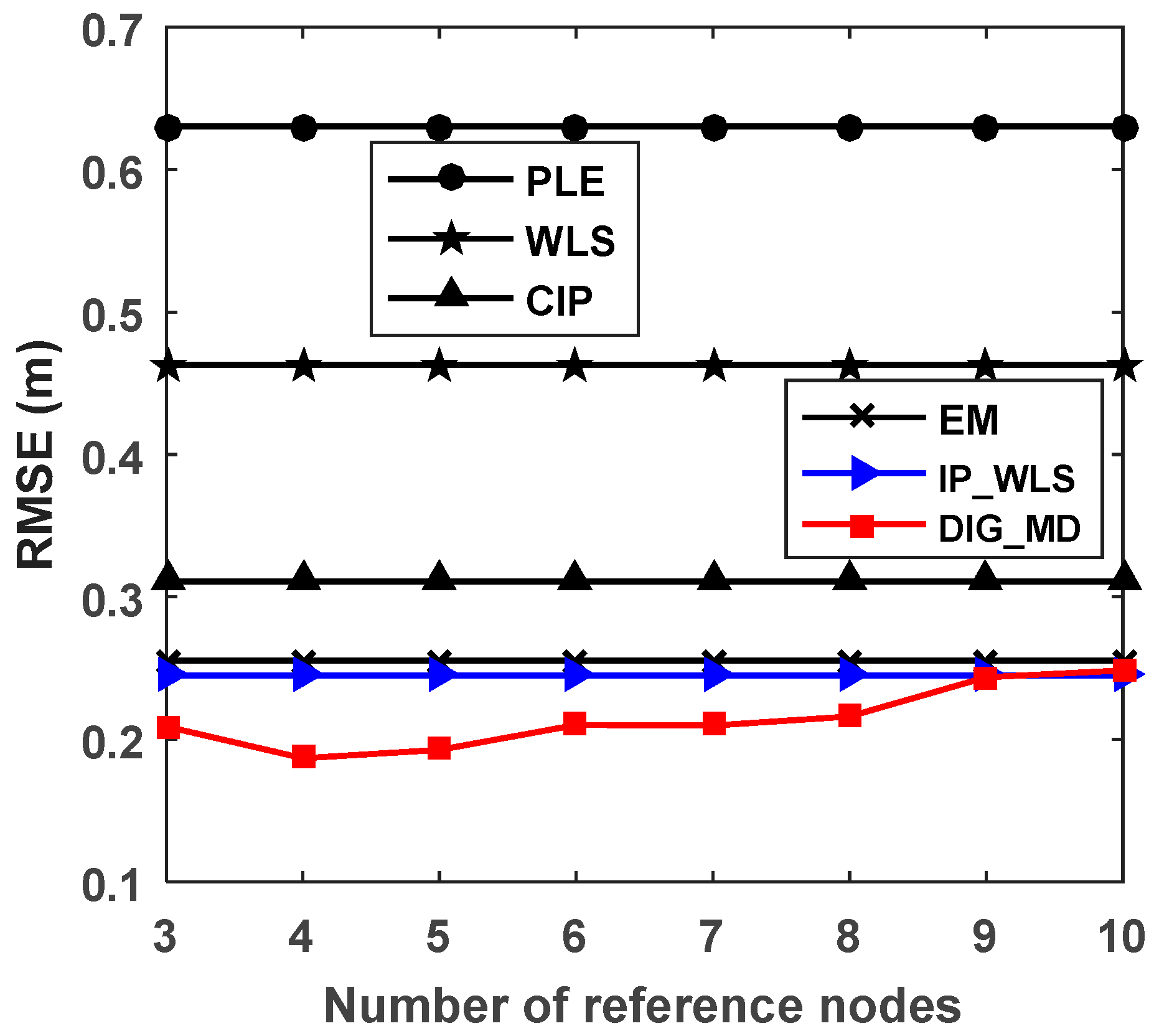
4.2. The Influence of the Number of Reference Nodes
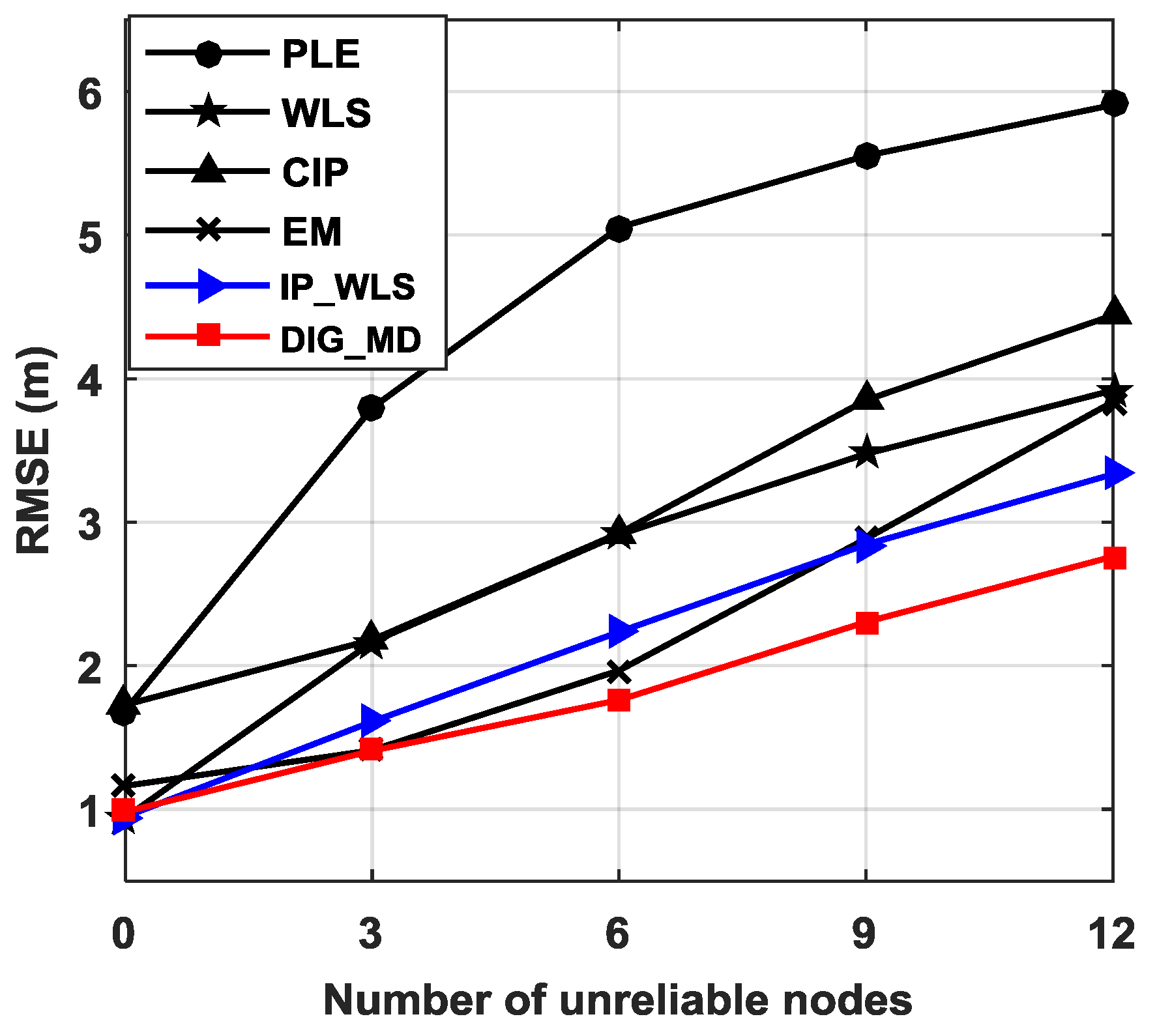
4.3. The Localization Performance for Different Numbers of Unreliable Nodes
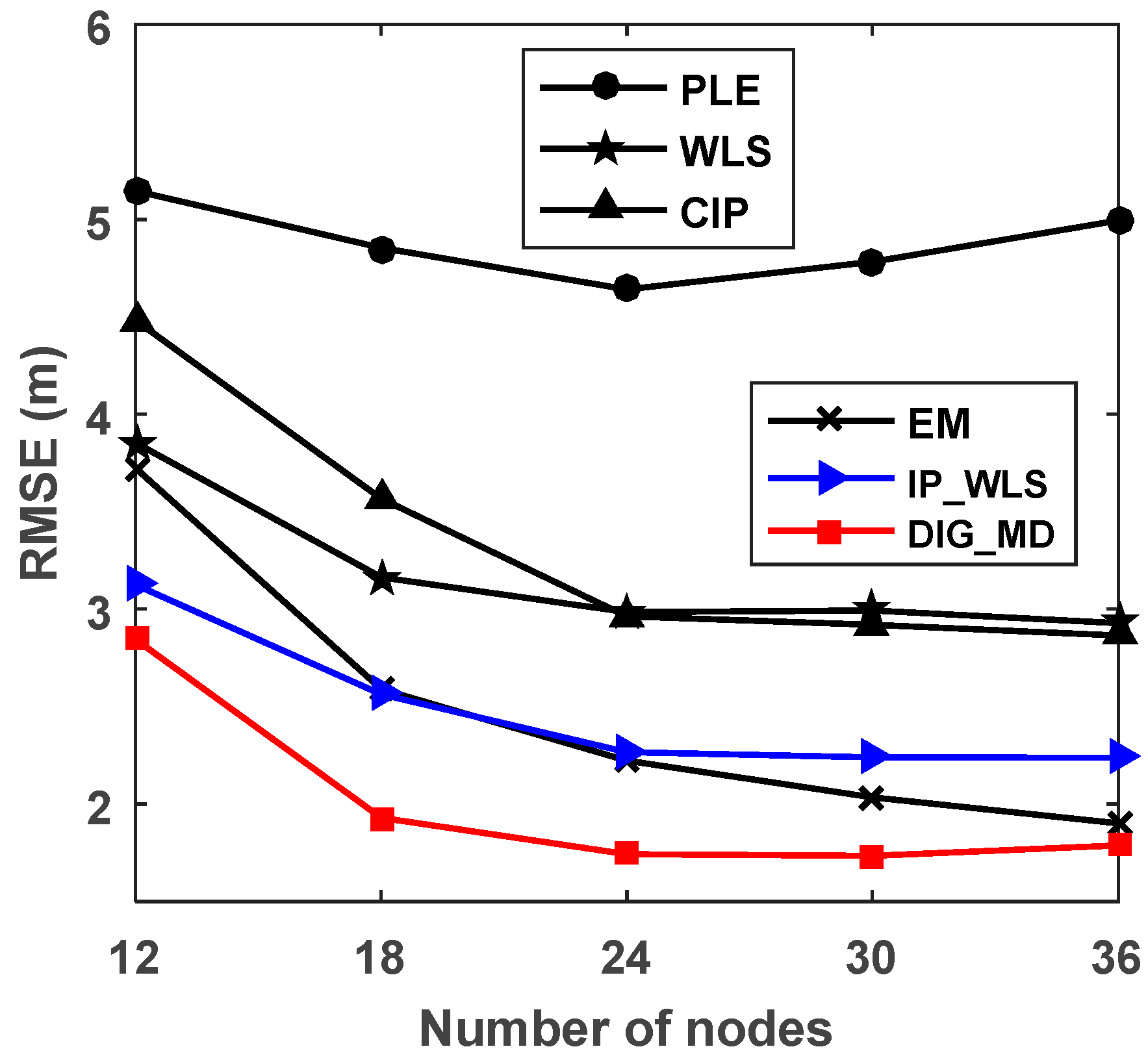
4.4. The Localization Performance for Different Numbers of Nodes and for Different Source Positions
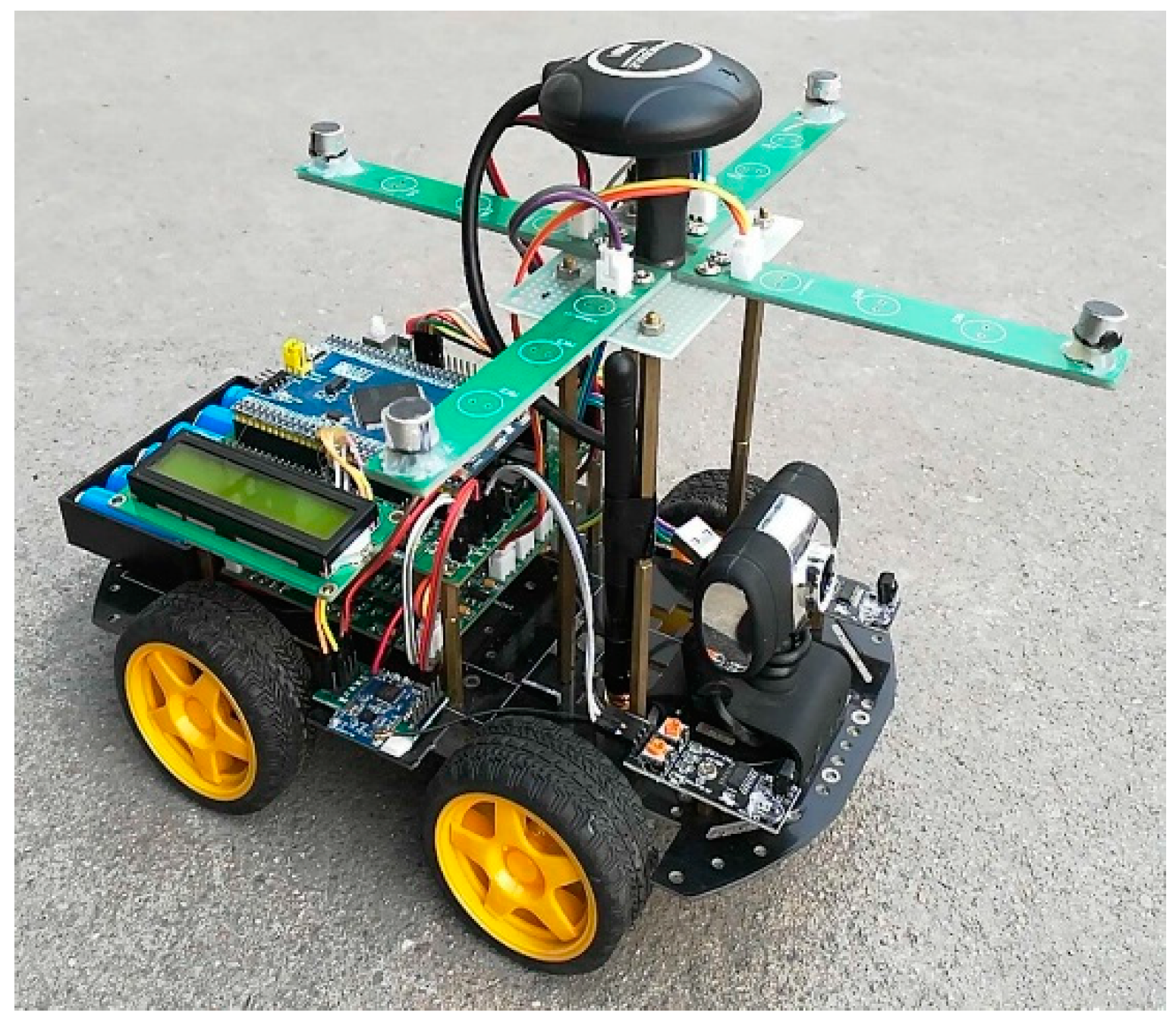
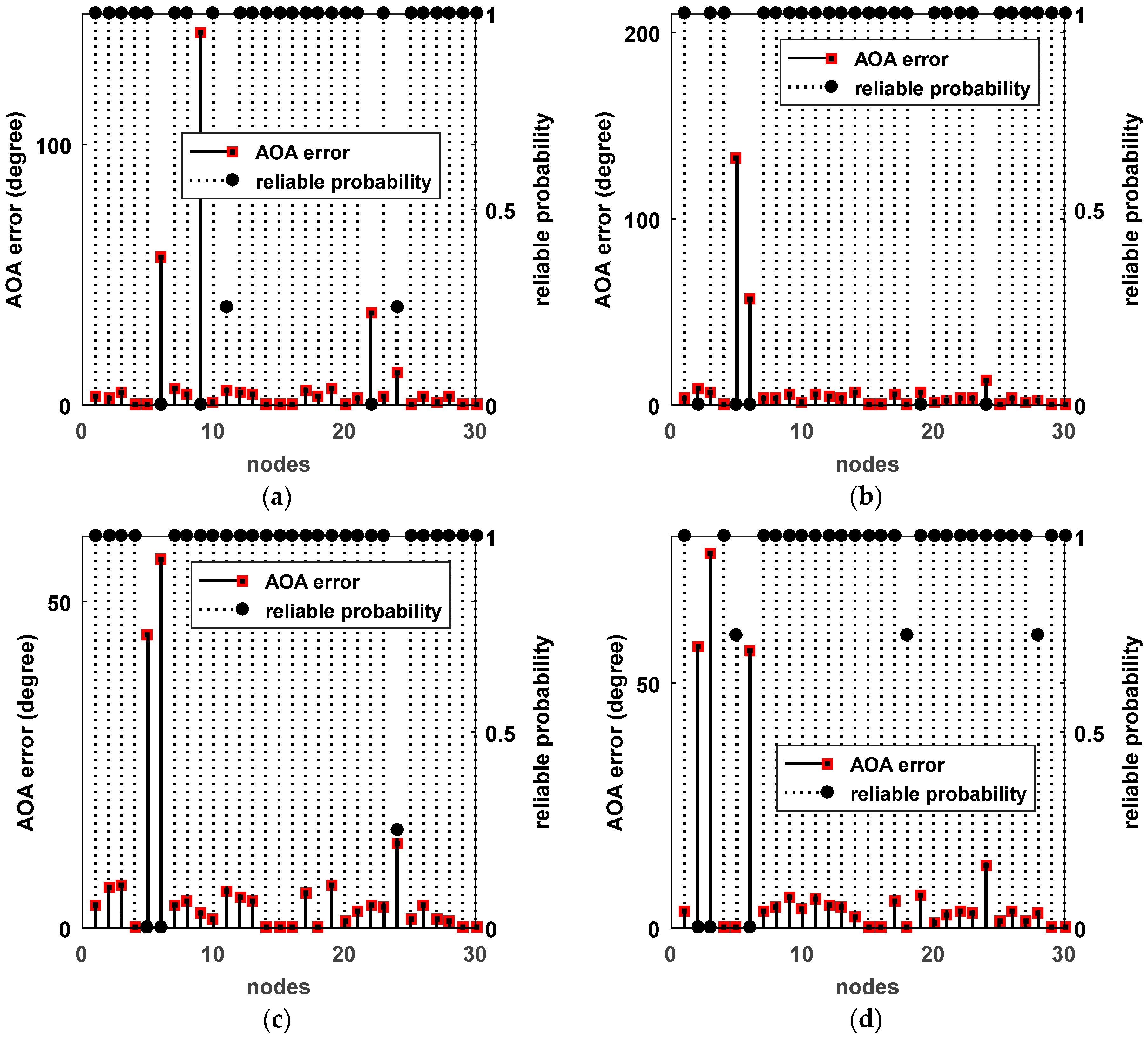
5. Outdoor Experiment Results and Analysis
- Multipath signal: because the distance between the microphone array and the ground is only 20 cm, unreliable AOAs may be introduced by a multipath signal.
- Interferences: the movements of people and cars during the experiment are also causes of unreliable measurements.
- The low SNR: because of the possible nonstationary background, the SNR of the received signal of each node may vary in a large range, possibly resulting in unreliable measurements.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Han, G.; Xu, H.; Duong, T.Q.; Jiang, J.; Hara, T. Localization algorithms of wireless sensor networks: A survey. Telecommun. Syst. 2013, 52, 2419–2436. [Google Scholar] [CrossRef]
- Fresno, J.M.; Robles, G.; Martínez-Tarifa, J.M.; Stewart, B.G. Survey on the performance of source localization algorithms. Sensors 2017, 17, 2666. [Google Scholar] [CrossRef] [PubMed]
- Cobos, M.; Antonacci, F.; Alexandridis, A.; Mouchtaris, A.; Lee, B. A survey of sound source localization methods in wireless acoustic sensor networks. Wirel. Commun. Mob. Comput. 2017. [Google Scholar] [CrossRef]
- Koks, D. Passive Geolocation for Multiple Receivers with No Initial State Estimate; No. DSTO RR-0222; Defence Science & Technology Organization: Edinburgh, SA, Australia, 2001. [Google Scholar]
- Sayed, A.H.; Tarighat, A.; Khajehnouri, N. Network-Based wireless location: Challenges faced in developing techniques for accurate wireless location information. IEEE Signal Process. Mag. 2005, 22, 24–40. [Google Scholar] [CrossRef]
- Lee, W.C. Uncertainty in Wireless Sensor Networks; Workshop on AFRL: Wright-Patterson Air Force Base, OH, USA, 2010. [Google Scholar]
- Yan, Q.; Chen, J.; Ottoy, G.; Cox, B.; De Strycker, L. An accurate AOA localization method based on unreliable sensor detection. In Proceedings of the 2018 IEEE Sensors Applications Symposium (SAS), Seoul, Korea, 12–14 March 2018; pp. 1–6. [Google Scholar]
- Yan, Q.; Chen, J.; Ottoy, G.; De Strycker, L. Robust AOA based acoustic source localization method with unreliable measurements. Signal Process. 2018, 152, 13–21. [Google Scholar] [CrossRef]
- Yu, K.; Guo, Y.J. Statistical NLOS identification based on AOA, TOA, and signal strength. IEEE Trans. Veh. Technol. 2009, 58, 274–286. [Google Scholar] [CrossRef]
- Giménez Febrer, P.J.; Silva Pereira, S.; López Valcarce, R. Distributed AOA-based source positioning in NLOS with sensor networks. In Proceedings of the 2015 IEEE International Conference on Acoustics, Speech, and Signal Processing (ICASSP), Brisbane, QLD, Australia, 19–24 April 2014; pp. 3197–3201. [Google Scholar]
- Griffin, A.; Mouchtaris, A. Localizing multiple audio sources from DOA estimates in a wireless acoustic sensor network. In Proceedings of the 14th IEEE Workshop on Applications of Signal Processing to Audio and Acoustics (WASPAA), New Paltz, NY, USA, 20–23 October 2013; pp. 1–4. [Google Scholar]
- Do, H.; Silverman, H. A fast microphone array srp-Phat source location implementation using Coarse-To-Fine Region Contraction (CFRC). In Proceedings of the IEEE Workshop on Applications of Signal Processing to Audio and Acoustics (WASPAA), New Paltz, NY, USA, 21–24 October 2007; pp. 295–298. [Google Scholar]
- Lee, D.D.; Kashyap, R.L. Robust maximum likelihood bearing estimation in contaminated Gaussian noise. IEEE Trans. Signal Process. 1992, 40, 1983–1986. [Google Scholar] [CrossRef]
- Yardimci, Y.; Cetin, A.E.; Cadzow, J.A. Robust direction-of-arrival estimation in non-Gaussian noise. IEEE Trans. Signal Process. 1998, 46, 1443–1451. [Google Scholar] [CrossRef] [Green Version]
- Besson, O.; Yuri, A.; Ben, J. Direction-of-arrival estimation in a mixture of K-Distributed and Gaussian noise. Signal Process. 2016, 128, 512–520. [Google Scholar] [CrossRef]
- De Maesschalck, R.; Jouan-Rimbaud, D.; Massart, D.L. The mahalanobis distance. Chemom. Intell. Lab. Syst. 2000, 50, 1–18. [Google Scholar] [CrossRef]
- Bishop, A.N.; Fidan, B.; Anderson, B.D.; Pathirana, P.N.; Dogancay, K. Optimality analysis of sensor node-Target geometries in passive localization: Part 1-Bearing-Only localization. In Proceedings of the 2007 3rd International Conference on Intelligent Sensors Sensor Networks and Information Processing (ISSNIP), Melbourne, VIC, Australia, 3–6 December 2007; pp. 7–12. [Google Scholar]
- Gnanadesikan, R.; Kettenring, J.R. Robust estimates, residuals, and outlier detection with multiresponse data. Biometrics 1972, 28, 81–124. [Google Scholar] [CrossRef]
- Maronna, R.A.; Ruben, H.Z. Robust estimates of location and dispersion for high-dimensional datasets. Technometrics 2002, 44, 307–317. [Google Scholar] [CrossRef]
- Rousseeuw, P.J.; Molenberghs, G. Transformation of nonpositive semidefinite correlation matrices. Commun. Stat. Theory Methods 1993, 22, 965–984. [Google Scholar] [CrossRef]
- Marcus, M.; Minc, H. A Survey of Matrix Theory and Matrix Inequalities; Courier Corporation: Chelmsford, MA, USA, 1992. [Google Scholar]
- Rousseeuw, P.J.; Hubert, M. Robust statistics for outlier detection. In Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery; John Wiley & Sons: Hoboken, NJ, USA, 2011; pp. 73–79. [Google Scholar]
- Rousseeuw, P.J.; Driessen, K.V. A fast algorithm for the minimum covariance determinant estimator. Technometrics 1999, 41, 212–223. [Google Scholar] [CrossRef]
- Knapp, C.; Carter, G. The generalized correlation method for estimation of time delay. IEEE Trans. Acoust. Speech Signal Process. 1976, 24, 320–327. [Google Scholar] [CrossRef]








| Unreliable Node | s1 | s2 | s3 | s4 |
|---|---|---|---|---|
| RMSE (m): N = 4 | 1.2201 | 0.3168 | 0.3146 | 0.8060 |
| RMSE (m): N = 3 | 0.2155 | 0.1642 | 0.1695 | 0.1780 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yan, Q.; Chen, J.; De Strycker, L. An Outlier Detection Method Based on Mahalanobis Distance for Source Localization. Sensors 2018, 18, 2186. https://doi.org/10.3390/s18072186
Yan Q, Chen J, De Strycker L. An Outlier Detection Method Based on Mahalanobis Distance for Source Localization. Sensors. 2018; 18(7):2186. https://doi.org/10.3390/s18072186
Chicago/Turabian StyleYan, Qingli, Jianfeng Chen, and Lieven De Strycker. 2018. "An Outlier Detection Method Based on Mahalanobis Distance for Source Localization" Sensors 18, no. 7: 2186. https://doi.org/10.3390/s18072186




