A Distance Bounding Protocol for Location-Cloaked Applications
Abstract
:1. Introduction
2. System Overview
2.1. A Distance Bounding Attack
2.2. Thwarting a DBA
3. Protocol Proposal
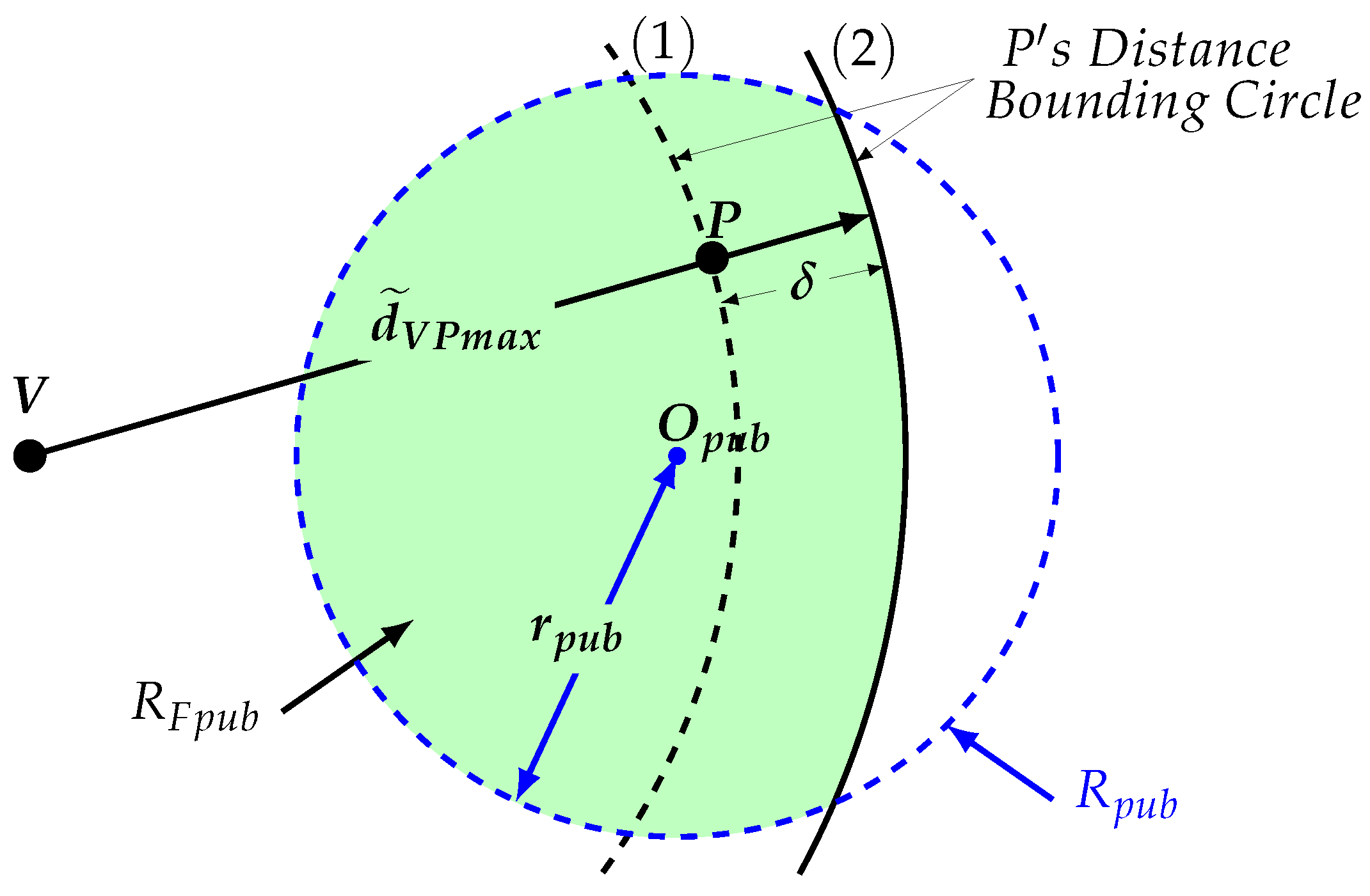
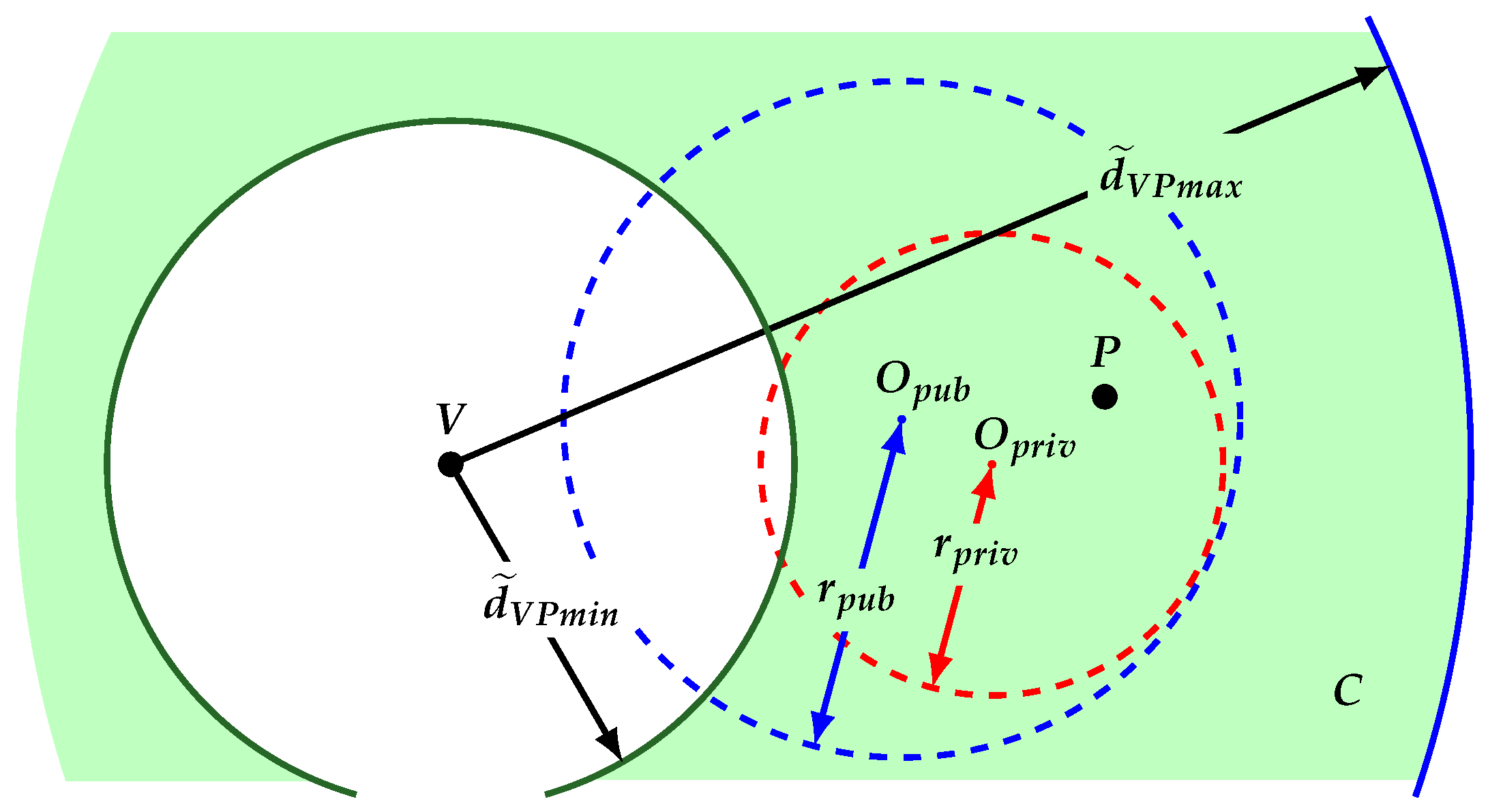
3.1. Metrics
3.2. Protocol
- User P determines the privacy and security criteria for the cloaking regions and . With those, it asks the AS entity to create both regions.
- The AS answers P with the regions and .
- User P determines the refinement level .
- With the information of regions y , user P randomly selects the distance which defines the delay on the interval .
- For the case of maximum possible refinement, user P decides to continue participating with V if condition is satisfied.
- If the protocol is continued, P sends region to V.
- V determines if region satisfies a practical minimum precision, and decides if it will continue with the protocol.
- Through a DBA, V determines region C. During that process, P delays its answer by a given time .
- V determines the region were P must be by intersecting regions and C.
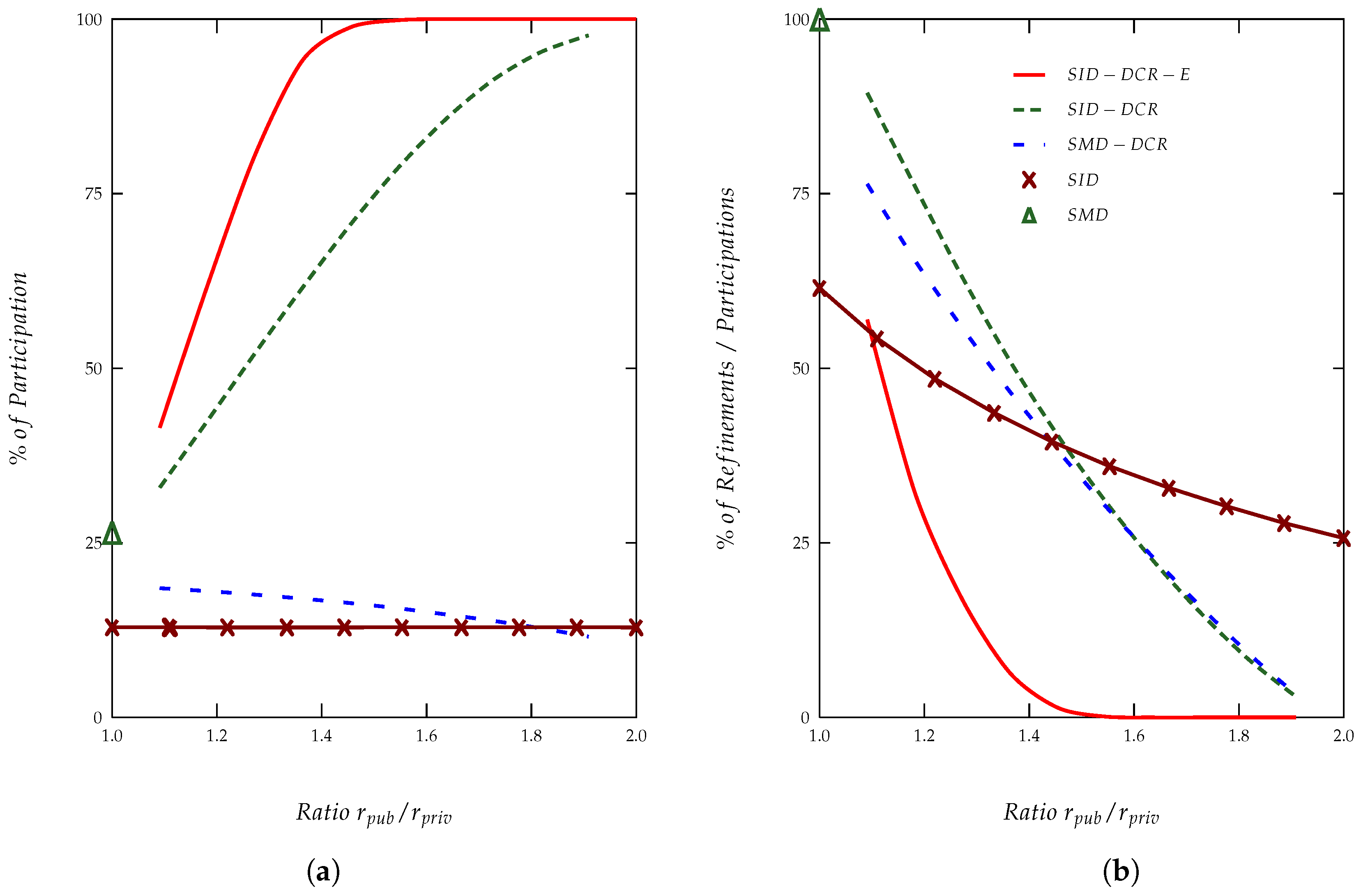
4. Results and Discussion
- Solution with a delay equal to maximal distance (SMD), which is implemented with a cloaking region and a delay based on the maximum distance within the cloaking region.
- Solution with an interval of possible delays (SID), which is considered a cloaking region and a delay chosen at random from ().
- Solution with a delay equal to maximal distance with double cloaking regions (SMD-DCR), where two cloaking regions are considered and a delay based on the maximum distance within .
- Solution with an interval of possible delays with double cloaking regions (SID-DCR), where two cloaking regions are considered and a selected delay chosen at random from ().
- Solution with an interval of possible delays with double cloaking regions and entropy usage (SID-DCR-E); it considers a location privacy leakage only if the entropy of the refined regions is smaller than the entropy of .
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Ford. Safe and Secure SecuriCode™ Keyless Entry. Available online: https://www.ford.com.pr/en/ technology/securicode-keyless-entry-keypad/ (accessed on 12 March 2018).
- Ko, Y.; Vaidya, N.H. Location-Aided Routing (LAR) Mobile Ad Hoc Networks. In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Dallas, TX, USA, 25–30 October 1998; pp. 66–75. [Google Scholar]
- Royer, E.; Perkins, C.E. Multicast Operation of the Ad-hoc On-Demand Distance Vector Routing Protocol. In Proceedings of the 5th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Seattle, WA, USA, 15–19 August 1999; pp. 207–218. [Google Scholar]
- Karp, B.; Kung, H.T. GPSR: Greedy Perimeters Stateless Routing for Wireless Network. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 243–254. [Google Scholar]
- Placecast. Location Verification. 2017. Available online: http://placecast.net/location-verification.html (accessed on 3 April 2018).
- Ghinita, G.; Kalnis, P.; Skiadopoulos, S. PRIVE: Anonymous location-based queries in distributed mobile systems. In Proceedings of the 16th International Conference on World Wide Web, Banff, AB, Canada, 8–12 May 2007; pp. 371–380. [Google Scholar]
- Xu, T.; Cai, Y. Location Anonymity in Continuous Location-based Services. In Proceedings of the 15th Annual ACM International Symposium on Advances in Geographic Information Systems, Seattle, WA, USA, 7–9 November 2007; pp. 300–307. [Google Scholar]
- Hu, H.; Xu, J. Non-Exposure Location Anonymity. In Proceedings of the IEEE 25th International Conference on Data Engineering, Shanghai, China, 29 March–2 April 2009; pp. 1120–1131. [Google Scholar]
- Xu, T.; Cai, Y. Exploring Historical Location Data for Anonymity Preservation in Location-based Services. In Proceedings of the IEEE 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; pp. 547–555. [Google Scholar]
- Xu, T.; Cai, Y. Feeling-based Location Privacy Protection for Location-based Services. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 348–357. [Google Scholar]
- Xu, T.; Cai, Y. Location Cloaking for Safety Protection of Ad Hoc Networks. In Proceedings of the IEEE International Conference on Computer Communications, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1944–1952. [Google Scholar]
- Xu, T.; Cai, Y. Location safety protection in ad hoc networks. Ad Hoc Netw. 2009, 7, 1551–1562. [Google Scholar] [CrossRef]
- Niu, B.; Li, Q.; Zhu, X.; Cao, G.; Li, H. Achieving k-anonymity in Privacy-Aware Location-Based Services. In Proceedings of the 33rd Conference on Computer Communications (INFOCOM’14), Toronto, ON, Canada, 27 April–2 May 2014. [Google Scholar]
- Niu, B.; Gao, S.; Li, F.; Li, H.; Lu, Z. Protection of location privacy in continuous LBSs against adversaries with background information. In Proceedings of the International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016; pp. 1–6. [Google Scholar]
- Brands, S.; Chaum, D. Distance-Bounding Protocols (Extended Abstract). In Workshop on the Theory and Application of Cryptographic Techniques (EUROCRYPT’93); Springer: Berlin/Heidelberg, Germany, 1993; pp. 344–359. [Google Scholar]
- Hancke, G.P.; Kuhn, M.G. An RFID Distance Bounding Protocol. In Proceedings of the 1st International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM’05), Athens, Greece, 5–9 September 2005; pp. 67–73. [Google Scholar]
- Singelée, D.; Preneel, B. Distance bounding in noisy environments. In Security and Privacy in Ad-Hoc and Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4572, pp. 101–1115. [Google Scholar]
- Hoda, J.; Abolfazl, F. Achieving an appropriate security level for distance bounding protocols over a noisy channel. Telecommun. Syst. 2015, 58, 219–231. [Google Scholar]
- Čapkun, S.; Rasmussen, K.; Kasper, M.; Čagalj, M.; Srivastava, M. Secure Location Verification with Hidden and Mobile Base Stations. IEEE Trans. Mob. Comput. 2008, 7, 470–483. [Google Scholar] [CrossRef]
- Sastry, N.; Shankar, U.; Wagner, D. Secure verification of location claims. In Proceedings of the 2nd ACM Workshop on Wireless Security (WiSe’03), San Diego, CA, USA, 19 September 2003; pp. 1–10. [Google Scholar]
- Rasmussen, K.; Čapkun, S. Location privacy of distance bounding protocols. In Proceedings of the 15th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 149–160. [Google Scholar]
- Mitrokotsa, A.; Onete, C.; Vaudenay, S. Location leakage in distance bounding: Why location privacy does not work. Comput. Secur. 2014, 45, 199–209. [Google Scholar] [CrossRef]
- Avoine, G.; Trujillo-Rasua, R. Comparing distance bounding protocols: A critical mission supported by decision theory. Comput. Commun. 2015, 67, 92–102. [Google Scholar] [CrossRef]
- Entezari, R.; Tajamolian, M. RFID unilateral distance bounding protocols: A trade-off between mafia and distance fraud. Comput. Commun. 2017, 98, 97–105. [Google Scholar] [CrossRef]
- Zhuang, Y.; Yang, A.; Hancke, G.; Wong, D.; Yang, G. Energy-Efficient Distance-Bounding with Residual Charge Computation. IEEE Trans. Emerg. Top. Comput. 2017, PP, 1. [Google Scholar] [CrossRef]
- Pagnin, E.; Yang, A.; Hub, Q.; Hancke, G.; Mitrokotsa, A. Distance bounding meets human based authentication. Future Gener. Comput. Syst. 2018, 80, 627–639. [Google Scholar] [CrossRef]
- Gruteser, M.; Grunwald, D. Anonymous Usage of Location-based Services through Spatial and Temporal Cloaking. In Proceedings of the 1st International Conference on Mobile Systems, Applications and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 31–42. [Google Scholar]
- Chow, C.Y.; Mokbel, M.; Liu, X. A peer-to-peer spatial cloaking algorithm for anonymous location-based service. In Proceedings of the 14th Annual ACM International Symposium on Advances in Geographic Information Systems, Arlington, VA, USA, 10–11 November 2006; pp. 171–178. [Google Scholar]
- Rasmussen, K.; Čapkun, S. Realization of RF distance bounding. In Proceedings of the 19th USENIX Conference on Security, Washington, DC, USA, 11–13 August 2010; pp. 389–402. [Google Scholar]
- Ranganathan, A.; Danev, B.; Capkun, S. Low-power Distance Bounding. arXiv, 2014; arXiv:1404.4435. [Google Scholar]
- Riahi-Manesh, M.; Kaabouch, N. Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system. Int. J. Crit. Infrastruct. Prot. 2017, 19, 16–31. [Google Scholar] [CrossRef]
- Galdames, P. Novel Techniques for Location-Cloaked Applications. Ph.D. Thesis, Iowa State University, Ames, IA, USA, 2012. [Google Scholar]

© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Molina-Martínez, C.; Galdames, P.; Duran-Faundez, C. A Distance Bounding Protocol for Location-Cloaked Applications. Sensors 2018, 18, 1337. https://doi.org/10.3390/s18051337
Molina-Martínez C, Galdames P, Duran-Faundez C. A Distance Bounding Protocol for Location-Cloaked Applications. Sensors. 2018; 18(5):1337. https://doi.org/10.3390/s18051337
Chicago/Turabian StyleMolina-Martínez, Cristián, Patricio Galdames, and Cristian Duran-Faundez. 2018. "A Distance Bounding Protocol for Location-Cloaked Applications" Sensors 18, no. 5: 1337. https://doi.org/10.3390/s18051337
APA StyleMolina-Martínez, C., Galdames, P., & Duran-Faundez, C. (2018). A Distance Bounding Protocol for Location-Cloaked Applications. Sensors, 18(5), 1337. https://doi.org/10.3390/s18051337





