La-CTP: Loop-Aware Routing for Energy-Harvesting Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Work
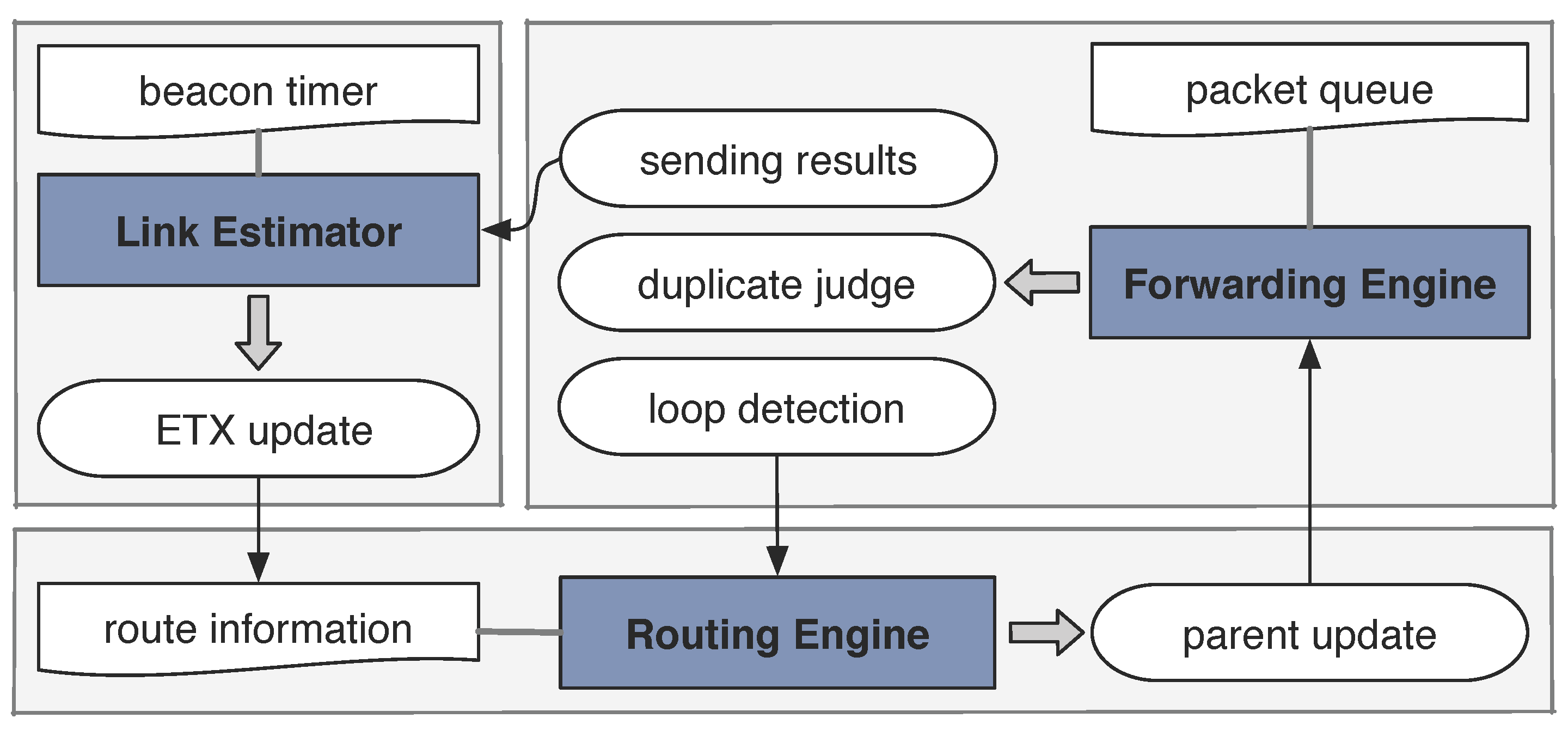
3. Overview of CTP
- Agile Link Estimation: to estimate the radio link quality, CTP uses the four-bit link estimator which profiles the dynamics of the physical, the data-link, and the routing layers. Especially, CTP updates such estimations as quickly as every five packet receptions in order to ensure the accuracy.
- Datapath Validation: topology changes often lead to transient loops in network, which in turn cause significant packet drops, wasting the precious network resources. In detail, CTP uses ETX as the metric for measuring both the single link and the path to the sink. The ETX value of a path is the sum of the ETX values of all the links along this path. Before a node forwards a packet, it will examine whether the ETX value of the passing-by packet is smaller than its local ETX; if true, CTP thinks that routing loops have happened to the previous-hop node.
- Adaptive Beaconing: by exchanging control beacons in a series of time intervals, CTP updates stale routing structure. The adaptive beaconing scheme, improved on the basis of Trickle [21], breaks through the traditional trade-off between the fast recovery of connection and the low cost, and it can control when to reset the timer interval of sending beacons, according to the routing cost gradient that is maintained locally by each node.
4. Dissection of CTP in EH-WSN
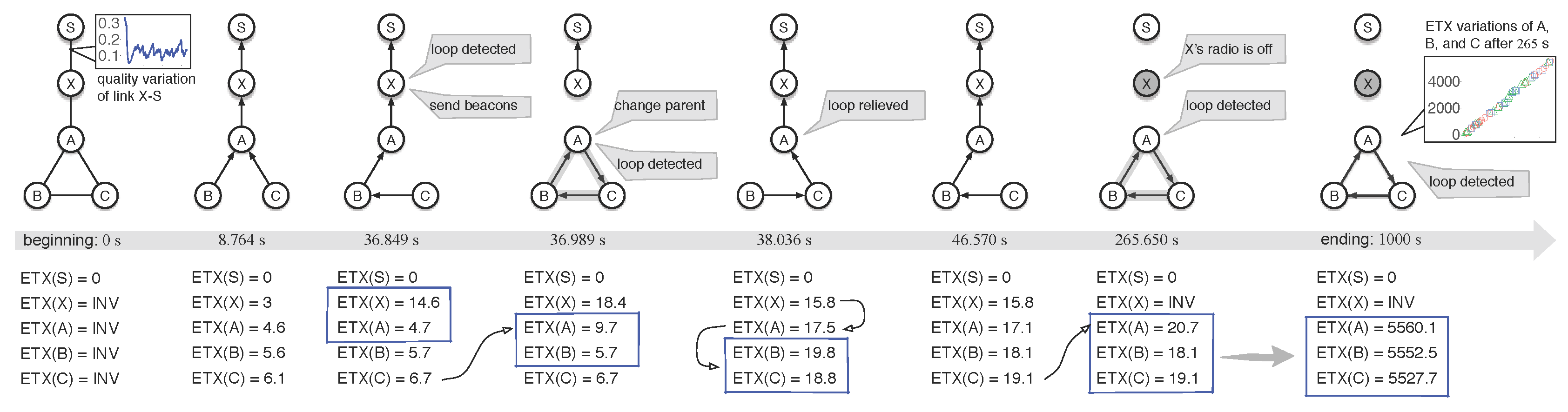
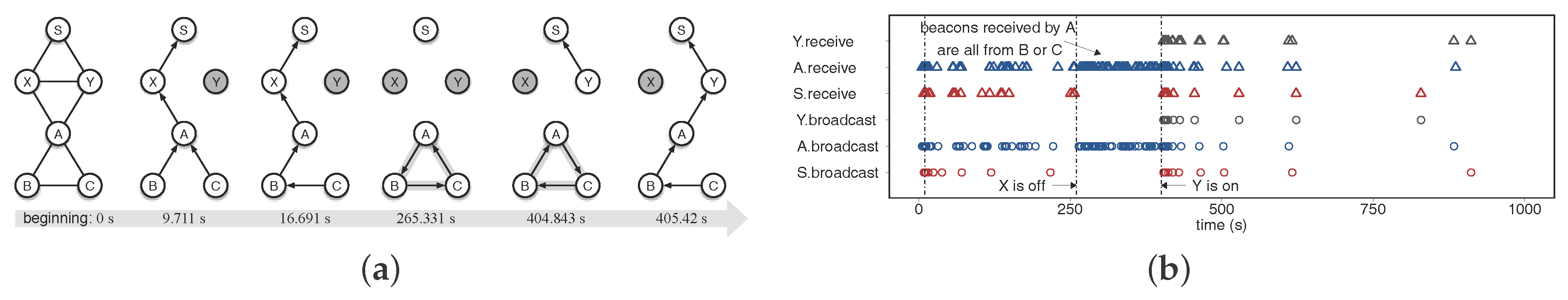
4.1. Experiment T-I
4.2. Experiment T-II
4.3. Experiment T-III
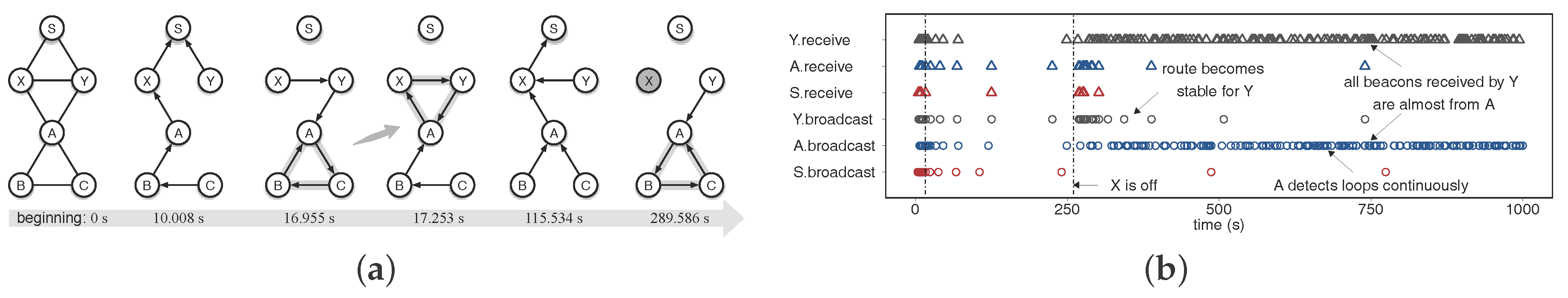
5. Design of La-CTP
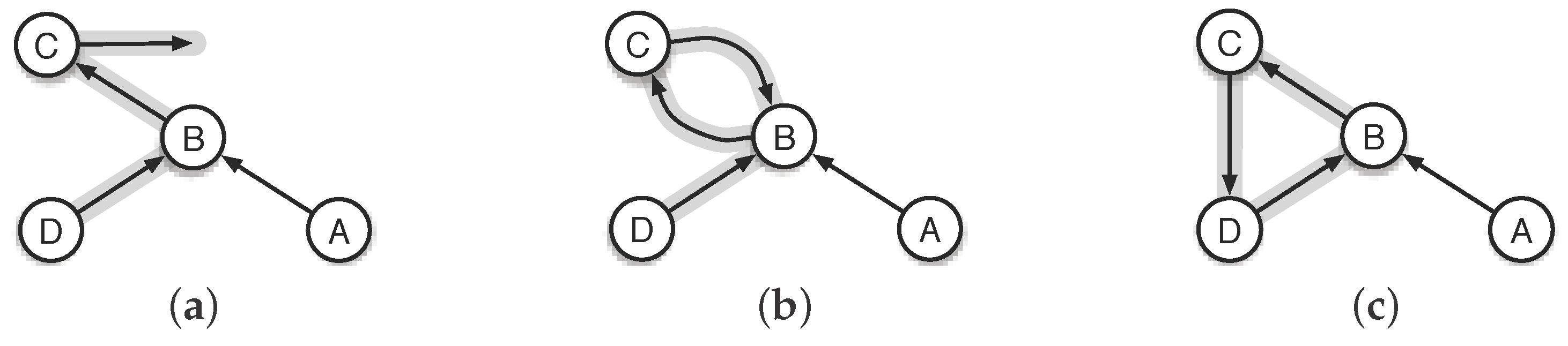
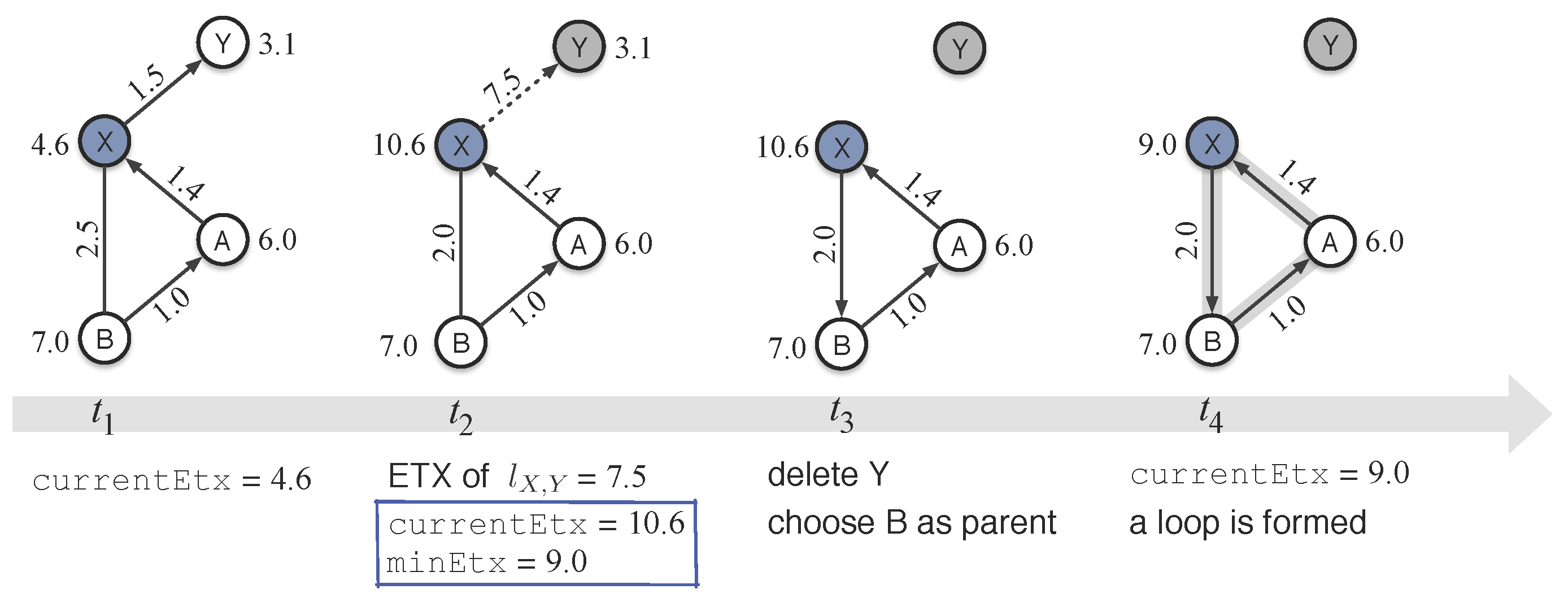
5.1. Depressing Loops
| Algorithm 1 Determination of parent update in CTP |
|
5.2. Handling Loops and Invalid Routes
| Algorithm 2 Beacon timer adjustment of La-CTP |
| Require: : the period of the current beacon timer; : the interval between the current time and the time of receiving last packet |
|
6. Evaluation
6.1. Experimental Settings and Methodologies
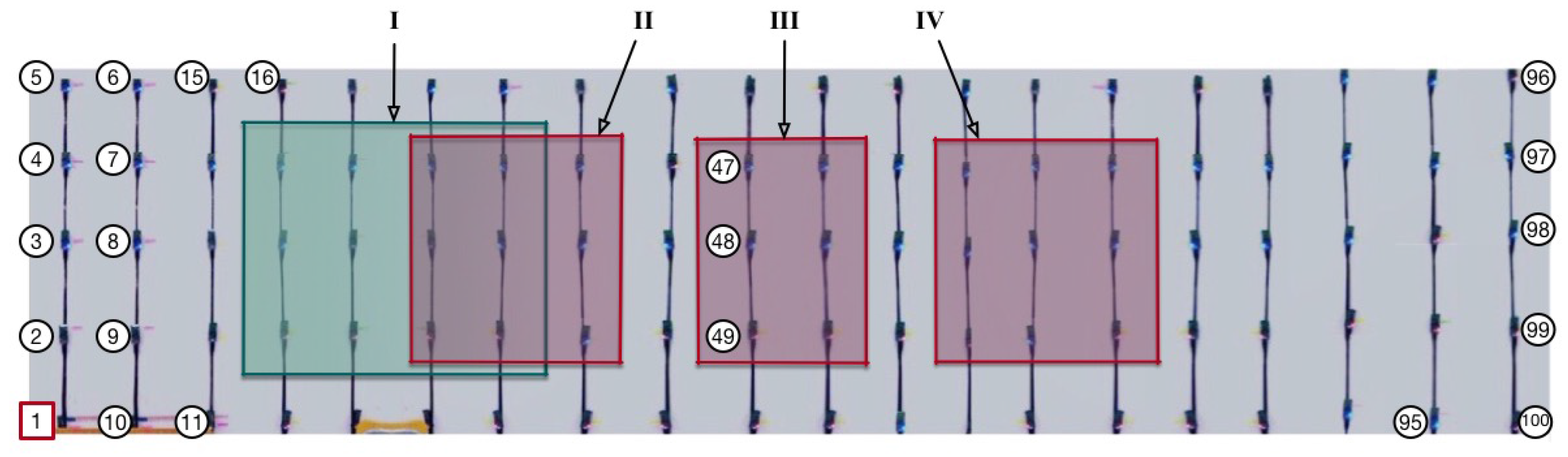
- noEH: this experiment included 50 nodes with numbers from 1, 2, and up to 50, and all the nodes in use were normal nodes, i.e., without any EH-nodes involved. All noEH nodes were powered by the USB wire.
- EH1: this experiment included 50 nodes with numbers from 1, 2, and up to 50, and only the nodes within region I of Figure 7 were EH-nodes. All EH1 nodes were powered by the USB wire.
- EH2: this experiment included all the 100 nodes and the nodes within regions II, III, and IV of Figure 7 were all EH-nodes. All EH2 nodes were powered by the USB wire.
- AllEH: this experiment included all the 100 nodes and node 1 still served as the sink. Specially, each of the nodes except node 1 was powered by two AA batteries.
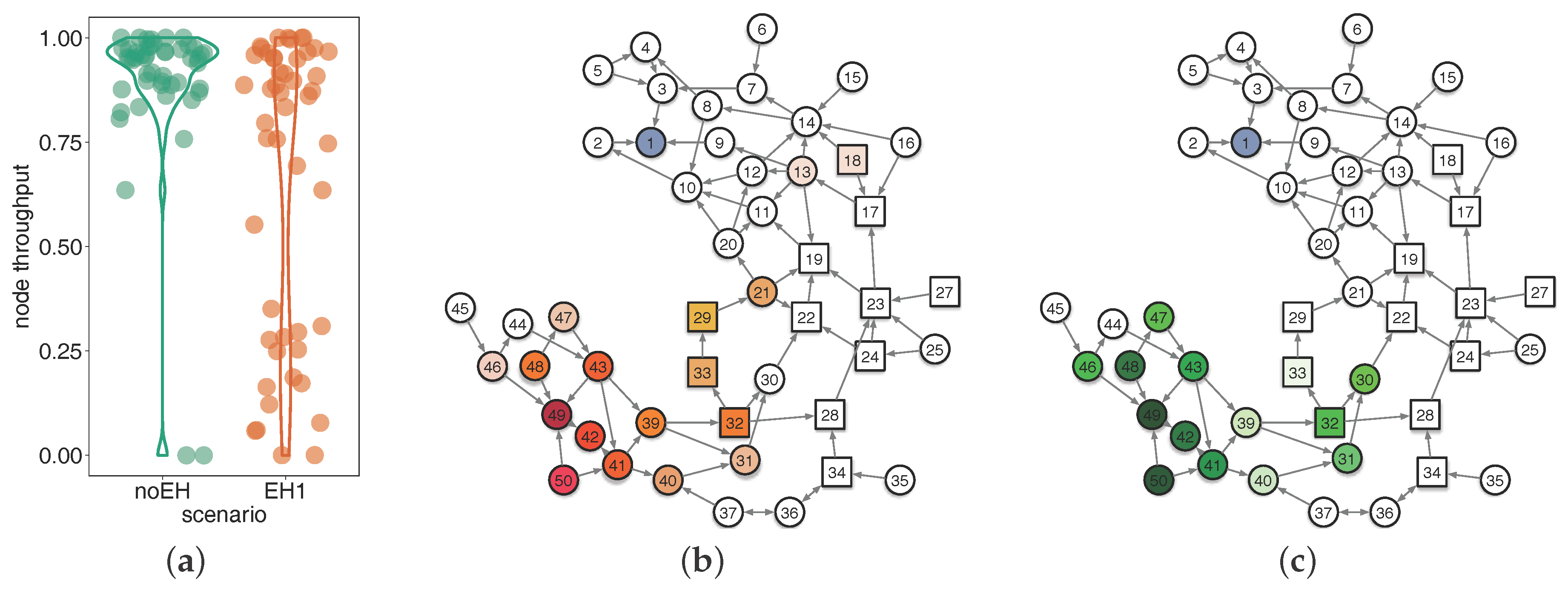
- Network throughput: the ratio between the number of packets received by the sink and the number of packets generated during experiment.
- Number of parent updates: the total number of parent updates that all the nodes perform during experiment. This metric can reflect the dynamics of the network topology.
- Number of detected loops: the total number of loops that occurred during experiment. This metric is used to weigh the performance that the protocol handles the loops.
- Average time of loop removement: if parent node u determines a loop-detection event just upon receiving a packet from child v at time and in the following time , u receives another packet from v, yet without reporting loop detection, then this loop through u and v is reckoned to have been removed and the removement time of this loop is calculated by . We use the average time of loop removements in the routing performance evaluation.
- Numbers of beacons: the number of beacons sent by nodes and the number of beacons received by nodes in the routing establishment and maintenance. We use this metric to approximately measure the energy overhead needed by the routing protocol, because the exact energy consumption cannot be measured at the nodes powered by USB lines.
6.2. Analyses of Experimental Results
6.2.1. Examination of CTP under noEH and EH1
6.2.2. Comparison of CTP and La-CTP
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor Network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2015, 60, 192–219. [Google Scholar] [CrossRef]
- Shaikha, F.; Zeadally, S. Energy harvesting in wireless sensor networks: A comprehensive review. Renew. Sustain. Energy Rev. 2016, 55, 1041–1054. [Google Scholar] [CrossRef]
- Zou, T.; Lin, S.; Feng, Q.; Chen, Y. Energy-Efficient Control with Harvesting Predictions for Solar-Powered Wireless Sensor Networks. Sensors 2016, 16, 53. [Google Scholar] [CrossRef] [PubMed]
- Aslam, S.; Hasan, N.; Jang, J.; Lee, K. Optimized Energy Harvesting, Cluster-Head Selection and Channel Allocation for IoTs in Smart Cities. Sensors 2016, 16, 2046. [Google Scholar] [CrossRef] [PubMed]
- Hao, Y.; Peng, L.; Lu, H.; Hassan, M.; Alamri, A. Energy Harvesting Based Body Area Networks for Smart Health. Sensors 2017, 17, 1602. [Google Scholar] [CrossRef] [PubMed]
- Demori, M.; Ferrari, M.; Bonzanini, A.; Poesio, P.; Ferrari, V. Autonomous Sensors Powered by Energy Harvesting from von Karman Vortices in Airflow. Sensors 2017, 17, 2100. [Google Scholar] [CrossRef] [PubMed]
- Gorlatova, M.; Wallwater, A.; Zussman, G. Networking low-power energy harvesting devices: Measurement and Algorithms. In Proceedings of the INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1602–1610. [Google Scholar]
- Yerva, L.; Campbel, B.; Bansa, A.; Schmid, T.; Dutta, P. Grafting Energy-Harvesting Leaves onto Sensornet Tree. In Proceedings of the 11th International Conference on Information Processing in Sensor Networks (IPSN), Beijing, China, 16–20 April 2012; pp. 197–208. [Google Scholar]
- Basagni, S.; Naderi, M.Y.; Petrioli, C.; Spenza, D. Mobile Ad Hoc Networking: Cutting Edge Directions; Chapter Wireless Sensor Networks with Energy Harvesting; John Wiley and Sons: Hoboken, NJ, USA, 2013; pp. 701–736. [Google Scholar]
- Qiao, G.; Sun, G.; Li, H.; Ou, J. Heterogeneous tiny energy: An appealing opportunity to power wireless sensor motes in a corrosive environment. Appl. Energy 2014, 131, 87–96. [Google Scholar] [CrossRef]
- Faruque, J.; Helmy, A. Gradient-based routing in sensor networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2003, 7, 50–52. [Google Scholar] [CrossRef]
- Pei, D.; Zhao, X.; Massey, D.; Zhang, L. A Study of BGP Path Vector Route Looping Behavior. In Proceedings of the 24th International Conference on Distributed Computing Systems (ICDCS), Tokyo, Japan, 26 March 2004. [Google Scholar]
- Francois, P.; Shand, M.; Bonaventure, O. Disruption-free Topology Reconfiguration in OSPF Networks. In Proceedings of the 26th IEEE International Conference on Computer Communications (INFOCOM 2007), Barcelona, Spain, 6–12 May 2007. [Google Scholar]
- Yoshihiro, T. Reducing Routing Loops under Dynamic Metrics in Wireless Mesh Networks. In Proceedings of the IEEE Globecom, Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Zhu, T.; Dong, W.; He, Y.; Ma, Q.; Mo, L.; Liu, Y. Understanding Routing Dynamics in a Large-scale Wireless Sensor Network. In Proceedings of the 2013 IEEE 10th International Conference on Mobile Ad-Hoc and Sensor Systems, Hangzhou, China, 14–16 October 2013; pp. 574–582. [Google Scholar]
- Audeoud, H.J.; Krol, M.; Heusse, M.; Duda, A. Low Overhead Loop-Free Routing in Wireless Sensor Networks. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Abu Dhabi, UAE, 19–21 October 2015. [Google Scholar]
- Sun, Y.; Gurewitz, O.; Du, S.; Tang, L.; Johnson, D.B. ADB: An efficient multihop broadcast protocol based on asynchronous duty-cycling in wireless sensor networks. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems (SenSys), Berkeley, CA, USA, 4–6 November 2009; pp. 43–56. [Google Scholar]
- Guo, S.; Gu, Y.; Jiang, B.; He, T. Opportunistic flooding in low-duty-cycle wireless sensor networks with unreliable links. IEEE Trans. Comput. 2014, 63, 2787–2802. [Google Scholar]
- Mahapatra, C.; Sheng, Z.; Kamalinejad, P.; Leung, V.; Mirabbasi, S. Optimal Power Control in Green Wireless Sensor Networks With Wireless Energy Harvesting, Wake-Up Radio and Transmission Control. IEEE Access 2017, 6, 501–518. [Google Scholar] [CrossRef]
- Gnawali, O.; Fonseca, R.; Jamieson, K.; Moss, D.; Levis, P. Collection Tree Protocol. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems (SenSys), Berkeley, CA, USA, 4–6 November 2009; ACM: New York, NY, USA, 2009; pp. 1–14. [Google Scholar]
- Akkaya, K.; Younis, M. A survey of routing protocols in wireless sensor networks. Ad Hoc Netw. 2005, 3, 325–349. [Google Scholar] [CrossRef]
- Mendes, L.; Rodrigues, J. A survey on cross-layer solutions for wireless sensor networks. J. Netw. Comput. Appl. 2011, 34, 523–534. [Google Scholar] [CrossRef]
- Pantazis, N.; Nikolidakis, S.; Vergados, D. Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 551–591. [Google Scholar] [CrossRef]
- Han, G.; Dong, Y.; Guo, H.; Shu, L.; Wu, D. Cross-layer optimized routing in wireless sensor networks with duty cycle and energy harvesting. Wirel. Commun. Mob. Comput. 2014, 15, 1957–1981. [Google Scholar] [CrossRef]
- Ulukus, S.; Yener, A.; Erkip, E.; Simeone, O.; Zorzi, M.; Grover, P.; Huang, K. Energy harvesting wireless communications: A review of recent advances. IEEE J. Sel. Areas Commun. 2015, 33, 360–381. [Google Scholar] [CrossRef]
- Cao, Q.; Abdelzaher, T.; He, T.; Stankovic, J. Towards optimal sleep scheduling in sensor network for rare-event detection. In Proceedings of the 4th International Symposium on Information Processing in Sensor Networks, Boise, ID, USA, 15 April 2005. [Google Scholar]
- Keshavarzian, A.; Lee, H.; Venkatraman, L. Wakeup scheduling in wireless sensor networks. In Proceedings of the 7th ACM international symposium on Mobile ad hoc networking and computing (MobiHoc), Florence, Italy, 22–25 May 2006; pp. 322–333. [Google Scholar]
- Ku, M.L.; Li, W.; Liu, K.J.R. Advances in Energy Harvesting Communications: Past, Present, and Future Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 1384–1412. [Google Scholar] [CrossRef]
- Kailas, A.; Ingram, M.; Zhang, Y. A novel routing metric for environmentally-powered sensors with hybrid energy storage systems. In Proceedings of the 1st International Conference on Wireless VITAE, Aalborg, Denmark, 17–20 May 2009; pp. 42–47. [Google Scholar]
- Eu, Z.A.; Tan, H.P.; Seah, W. Opportunistic routing in wireless sensor networks powered by ambient energy harvesting. Comput. Netw. 2010, 54, 2943–2966. [Google Scholar] [CrossRef]
- Eu, Z.; Tan, H. Adaptive opportunistic routing protocol for energy harvesting wireless sensor networks. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 318–322. [Google Scholar]
- Liu, R.S.; Fan, K.W.; Zheng, Z.; Sinha, P. Perpetual and fair data collection for environmental energy-harvesting sensor networks. IEEE/ACM Trans. Netw. 2010, 19, 947–960. [Google Scholar] [CrossRef]
- Hieu, T.; Dung, L.; Kim, B. Stability-Aware Geographic Routing in Energy Harvesting Wireless Sensor Networks. Sensors 2016, 16, 696. [Google Scholar] [CrossRef] [PubMed]
- Wu, D.; He, J.; Wang, H.; Wang, C.; Wang, R. A Hierarchical Packet Forwarding Mechanism for Energy Harvesting Wireless Sensor Networks. IEEE Commun. Mag. 2015, 53, 92–98. [Google Scholar] [CrossRef]
- Gul, O.; Demirekler, M. Average Throughput Performance of Myopic Policy in Energy Harvesting Wireless Sensor Networks. Sensors 2017, 17, 2206. [Google Scholar] [CrossRef] [PubMed]
- Anisi, M.; Abdul-Salaam, G.; Ahmedy, I. Energy harvesting and battery power based routing in wireless sensor networks. Wirel. Netw. 2017, 23, 249–266. [Google Scholar] [CrossRef]
- Couto, D.D.; Aguayo, D.; Bicket, J.; Morris, R. A High-Throughput Path Metric for Multi-Hop Wireless Routing. Wirel. Netw. 2005, 11, 419–434. [Google Scholar] [CrossRef]
- Corke, P.; Wark, T.; Jurdak, R.; Hu, W.; Valencia, P.; Moore, D. Environmental Wireless Sensor Networks. Proc. IEEE 2010, 98, 1902–1917. [Google Scholar] [CrossRef]
- Dezfouli, B.; Radi, M.; Razak, S.; Hwee-Pink, T.; Bakar, K.A. Modeling low-power wireless communications. J. Netw. Comput. Appl. 2015, 51, 102–126. [Google Scholar] [CrossRef]
- Si, W.; Hashemi, M.; Xin, L.; Starobinsiki, D.; Trachtenberg, A. TeaCP: A Toolkit for Evaluation and Analysis of Collection Protocols in Wireless Sensor Networks. IEEE Trans. Netw. Serv. Manag. 2015, 12, 293–307. [Google Scholar] [CrossRef]
- Basagni, S.; Petrioli, C.; Spenza, D. CTP-WUR: The Collection Tree Protocol in Wake-up Radio WSNs for Critical Applications. In Proceedings of the International Conference on Computing, Networking and Communications (ICNC), Kauai, HI, USA, 15–18 February 2016. [Google Scholar]
- Kafi, M.; Othma, J.; Dadache, N. A Survey on Reliability Protocols in Wireless Sensor Networks. ACM Comput. Surv. 2017, 50, 31. [Google Scholar] [CrossRef]
- Noh, K.-L.; Chaudhari, Q.; Serpedin, E.; Suter, B. Novel Clock Phase Offset and Skew Estimation Using Two-Way Timing Message Exchanges for Wireless Sensor Networks. IEEE Trans. Commun. 2007, 55, 766–777. [Google Scholar] [CrossRef]
- Wu, Y.-C.; Chaudhari, Q.; Serpedin, E. Clock Synchronization of Wireless Sensor Networks. IEEE Signal Process. Mag. 2011, 28, 124–138. [Google Scholar] [CrossRef]

| Metrics | noEH | EH1 | EH2 | AllEH | ||||
|---|---|---|---|---|---|---|---|---|
| CTP | La-CTP | CTP | La-CTP | CTP | La-CTP | CTP | La-CTP | |
| Throughput (%) | 93.7 | 94.2 | 77 | 91.1 | 23 | 84 | 21.4 | 68 |
| #Parent Updates | 85 | 86 | 152 | 83 | 425 | 97 | 174 | 39 |
| #Loops Detected | 58 | 15 | 223 | 8 | 329 | 11 | 283 | 56 |
| Loops Unsolved (%) | 0 | 0 | 36.7 | 0 | 54.1 | 0 | 59.4 | 5.8 |
| Avg. Time of Loop Remv. (ms) | 1102 | 788 | 4217 | 1792 | 6035 | 2811 | 20,486 | 8824 |
| #Beacons Sent | 762 | 449 | 4233 | 2814 | 10,972 | 6756 | 7752 | 5069 |
| #Beacons Recv | 14,566 | 10,980 | 61,095 | 45,332 | 138,643 | 92,754 | 59,040 | 31,483 |
| #Total Beacons | 15,328 | 11,479 | 65,328 | 48,146 | 149,615 | 99,510 | 66,792 | 40,552 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, G.; Shang, X.; Zuo, Y. La-CTP: Loop-Aware Routing for Energy-Harvesting Wireless Sensor Networks. Sensors 2018, 18, 434. https://doi.org/10.3390/s18020434
Sun G, Shang X, Zuo Y. La-CTP: Loop-Aware Routing for Energy-Harvesting Wireless Sensor Networks. Sensors. 2018; 18(2):434. https://doi.org/10.3390/s18020434
Chicago/Turabian StyleSun, Guodong, Xinna Shang, and Yan Zuo. 2018. "La-CTP: Loop-Aware Routing for Energy-Harvesting Wireless Sensor Networks" Sensors 18, no. 2: 434. https://doi.org/10.3390/s18020434




