Optimizing the MAC Protocol in Localization Systems Based on IEEE 802.15.4 Networks
Abstract
:1. Introduction
2. IEEE 802.15.4 MAC Analysis
- NB: number of times a mote has tried to access the channel.
- BE: The backoff exponent represents the number of backoff periods the mote must wait before accessing the channel. The minimum (aMinBE) and maximum values (aMaxBE) in the standard are 3 and 5, respectively.
- macMaxCSMABackoffs: Maximum number of channel access tries. This value is 4 by default.
2.1. Transmission Delay
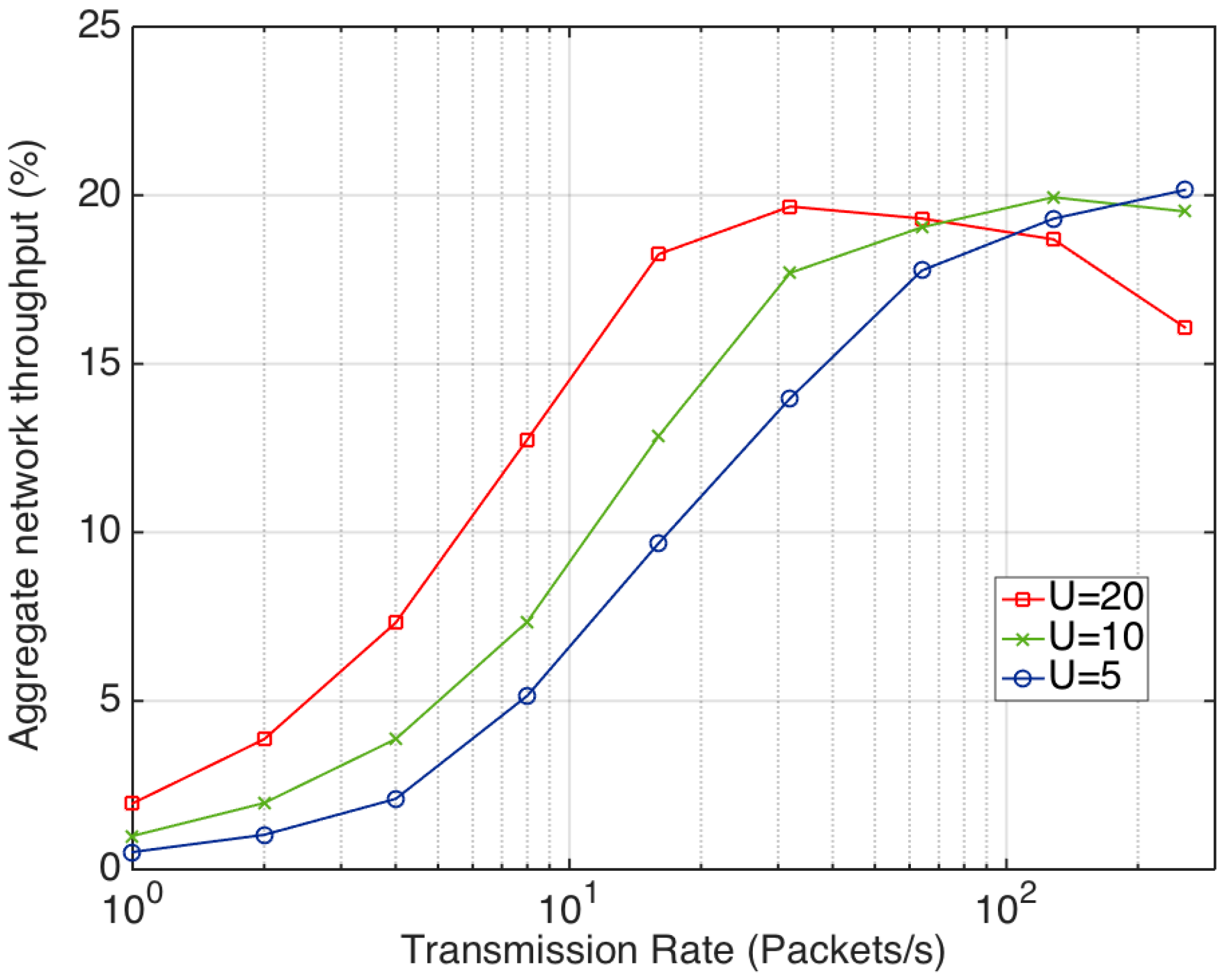
2.2. Performance Simulation
3. New MAC protocol
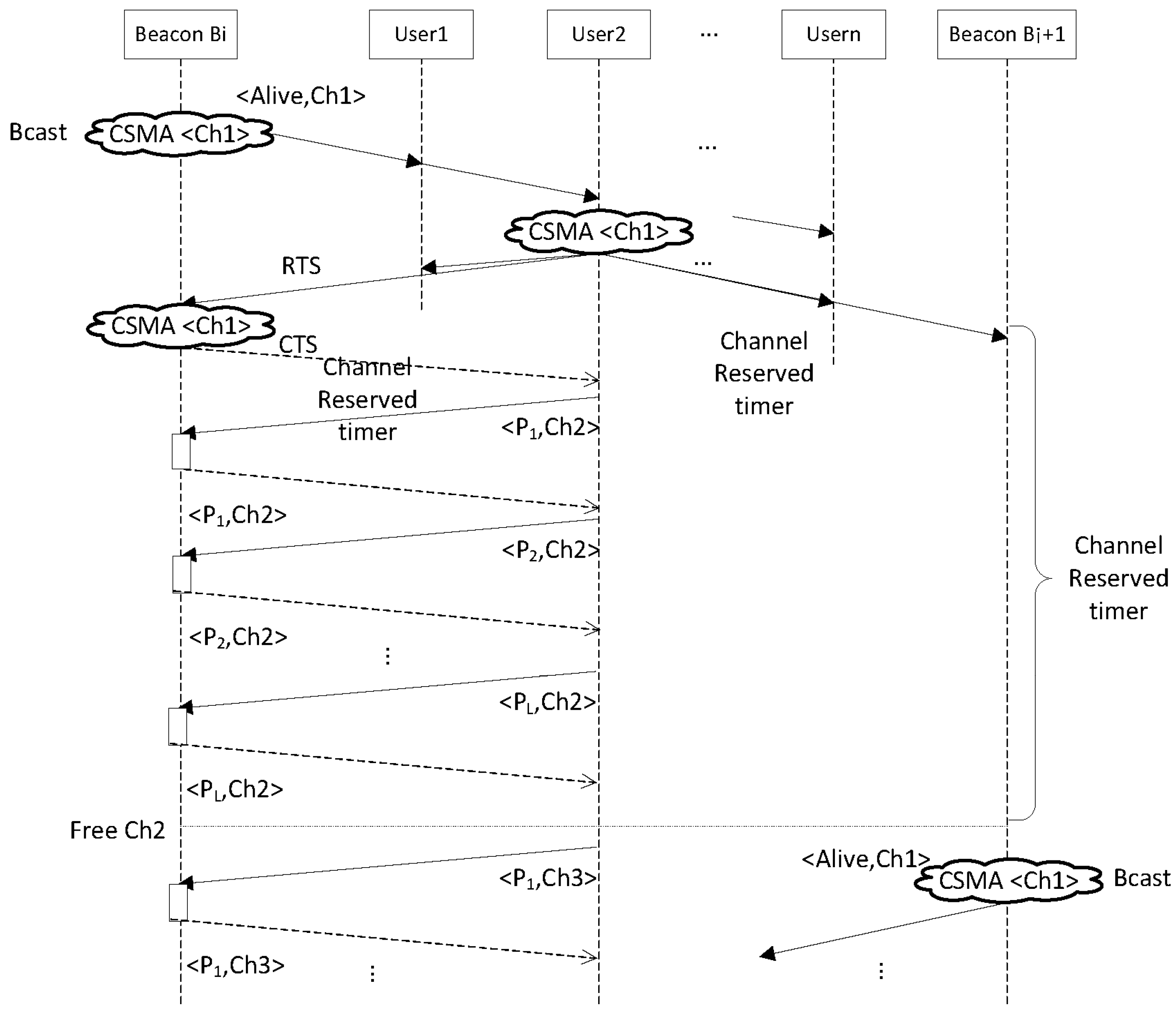
3.1. Initial Assumptions
- There is a channel, denoted Ch1, which is used for signaling purposes.
- Beacons announce their availability using broadcast packets.
- Users receiving these packets can reserve the beacon for subsequent transmissions using the request to send and clear to send (RTS/CTS) mechanism.
- The sequence of transmissions, including the list of channels and power levels that are used during the packet exchange with a beacon, is predefined and fixed beforehand, and all users follow the same sequence.
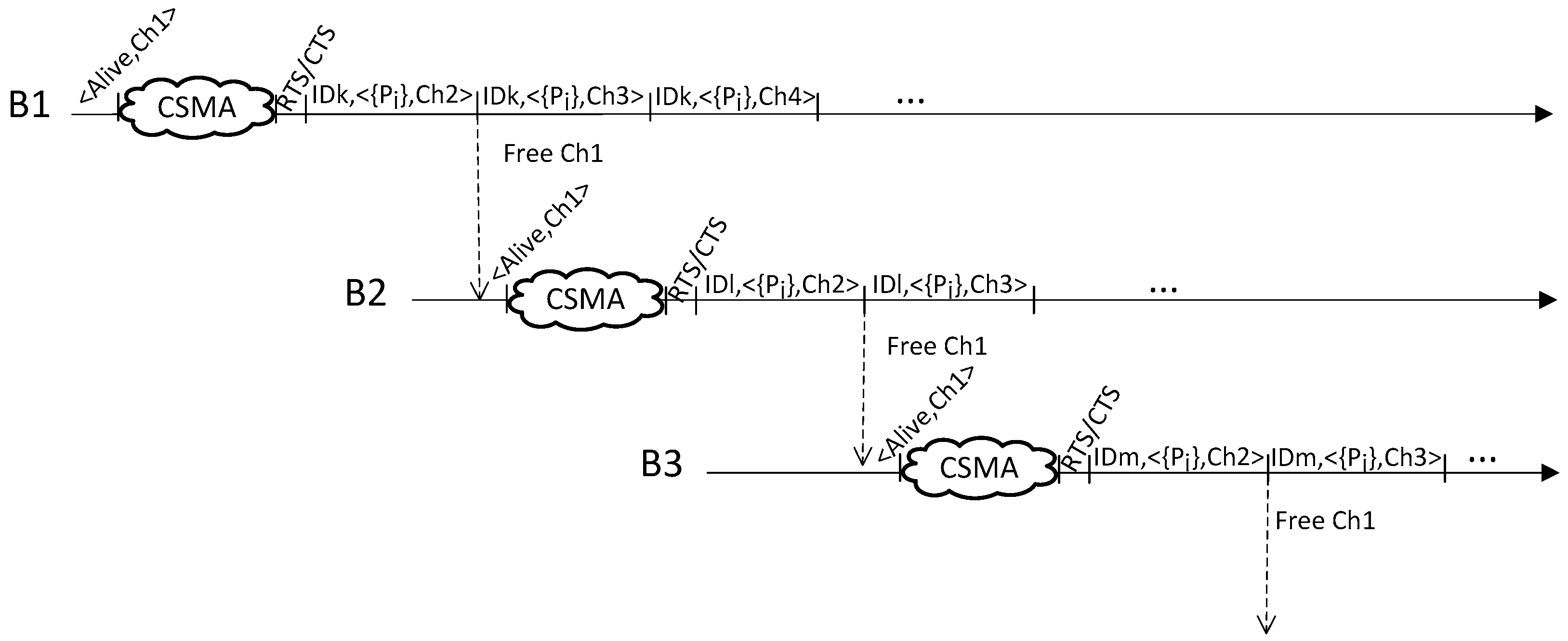
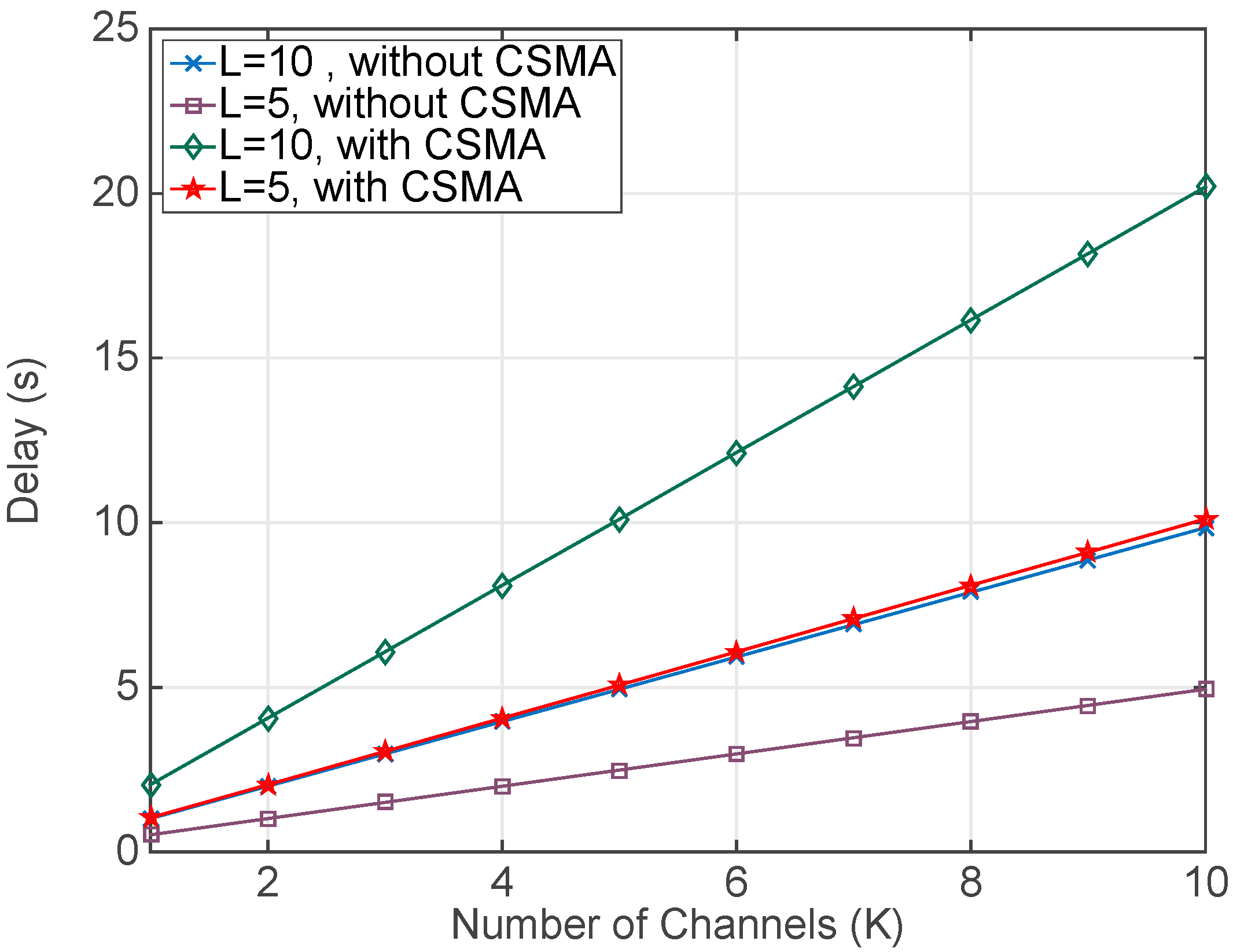
- The total number of packets exchanged to collect the RSSI values depends on three factors: (a) number of frequency channels tested (denoted as K), (b) number of different power levels considered (L), and (c) retransmissions for a fixed combination of a channel and a power level (N). Thus, the total number of packets exchanged is: 2·N·L·K.
- After receiving a RTS or CTS packet, other beacons and users stop using the radio during a certain time. This period of time is long enough to allow the user that has reserved the beacon to exchange all the packets at the first channel.
- A user and a beacon have a fixed period to complete the packet exchanging process at every different channel. When this period ends, they have to change from the current channel to the next.
3.2. Protocol Proposal
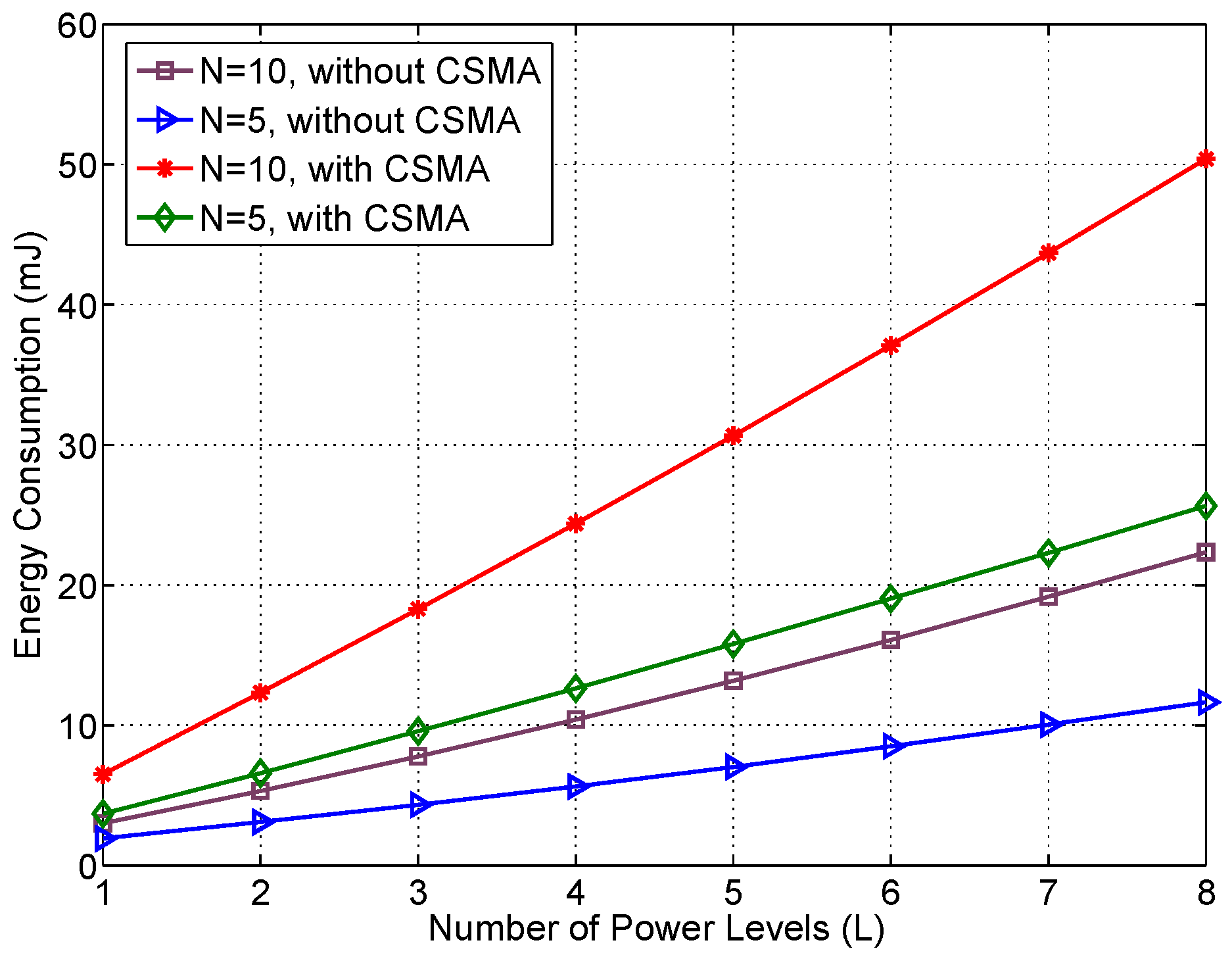
3.3. Energy Consumption Analysis
4. Results
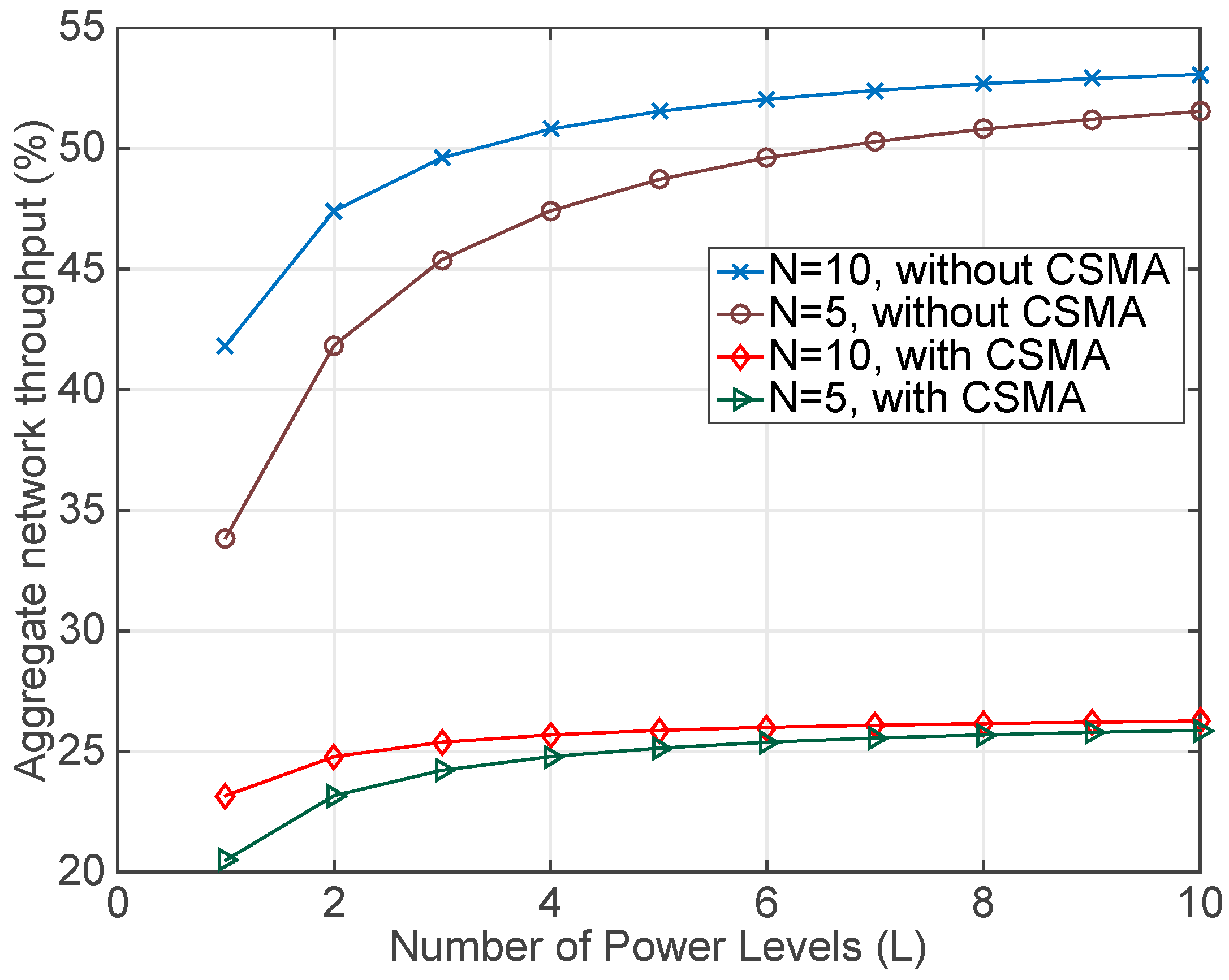
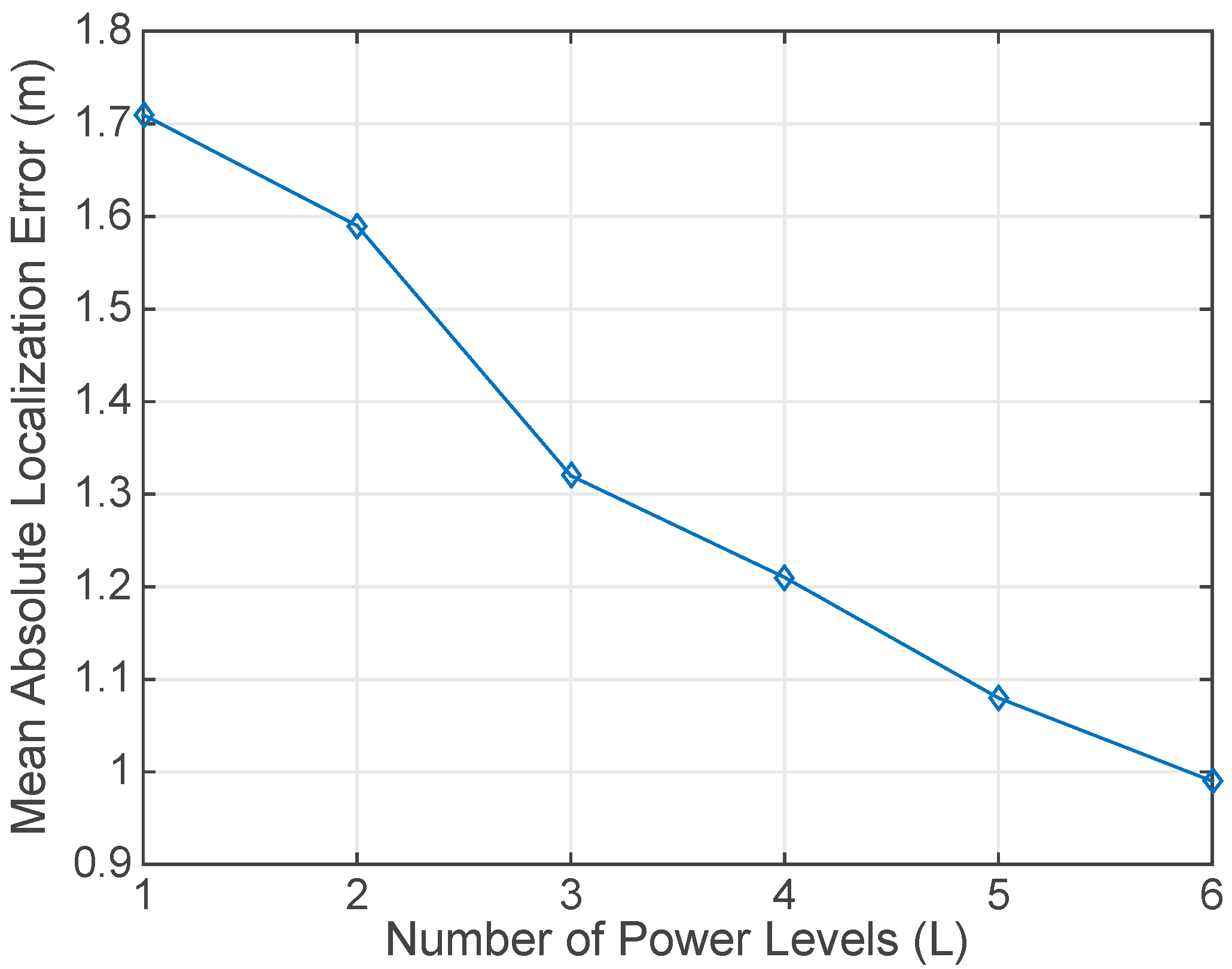
4.1. Simulation Results
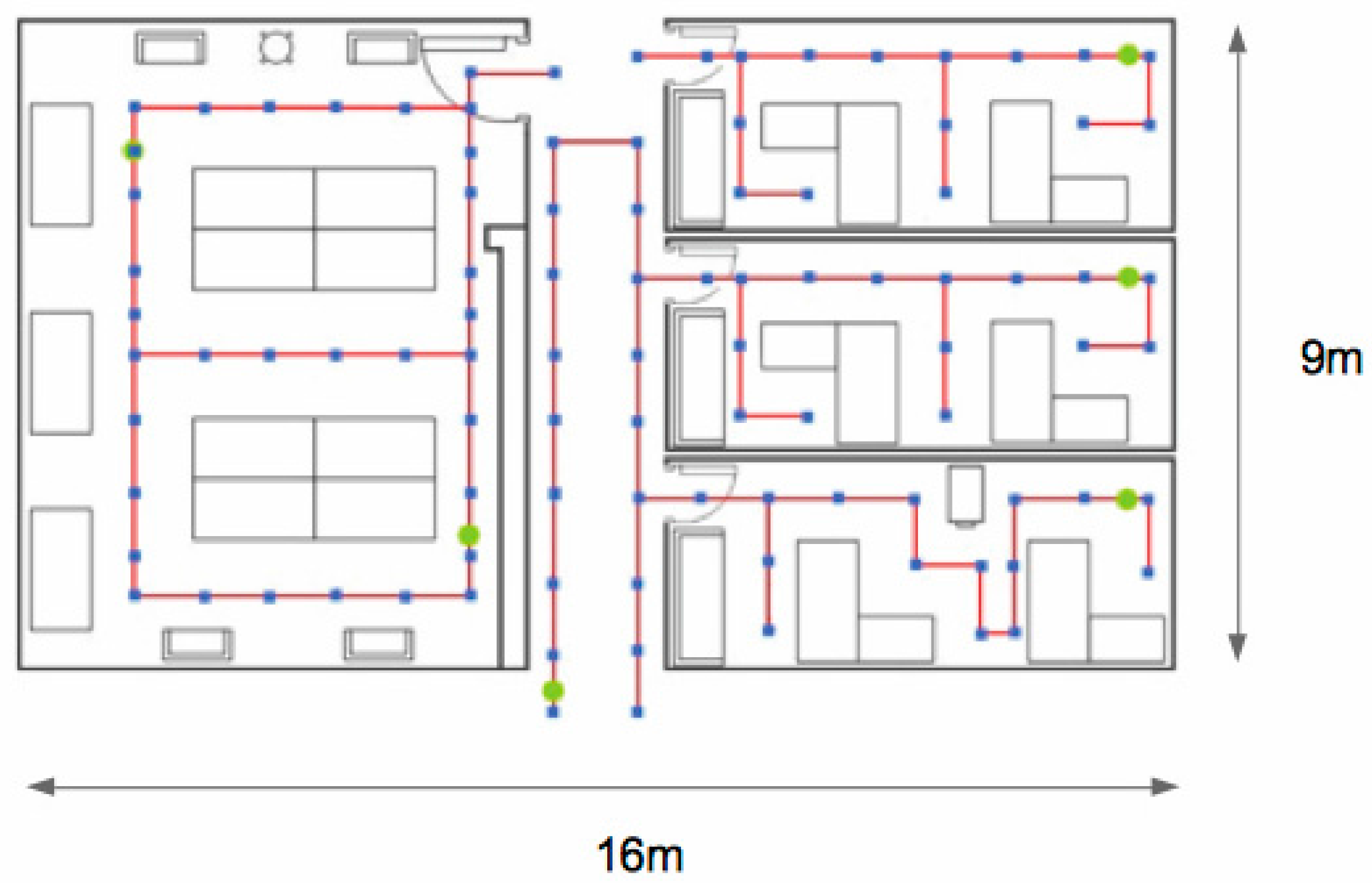
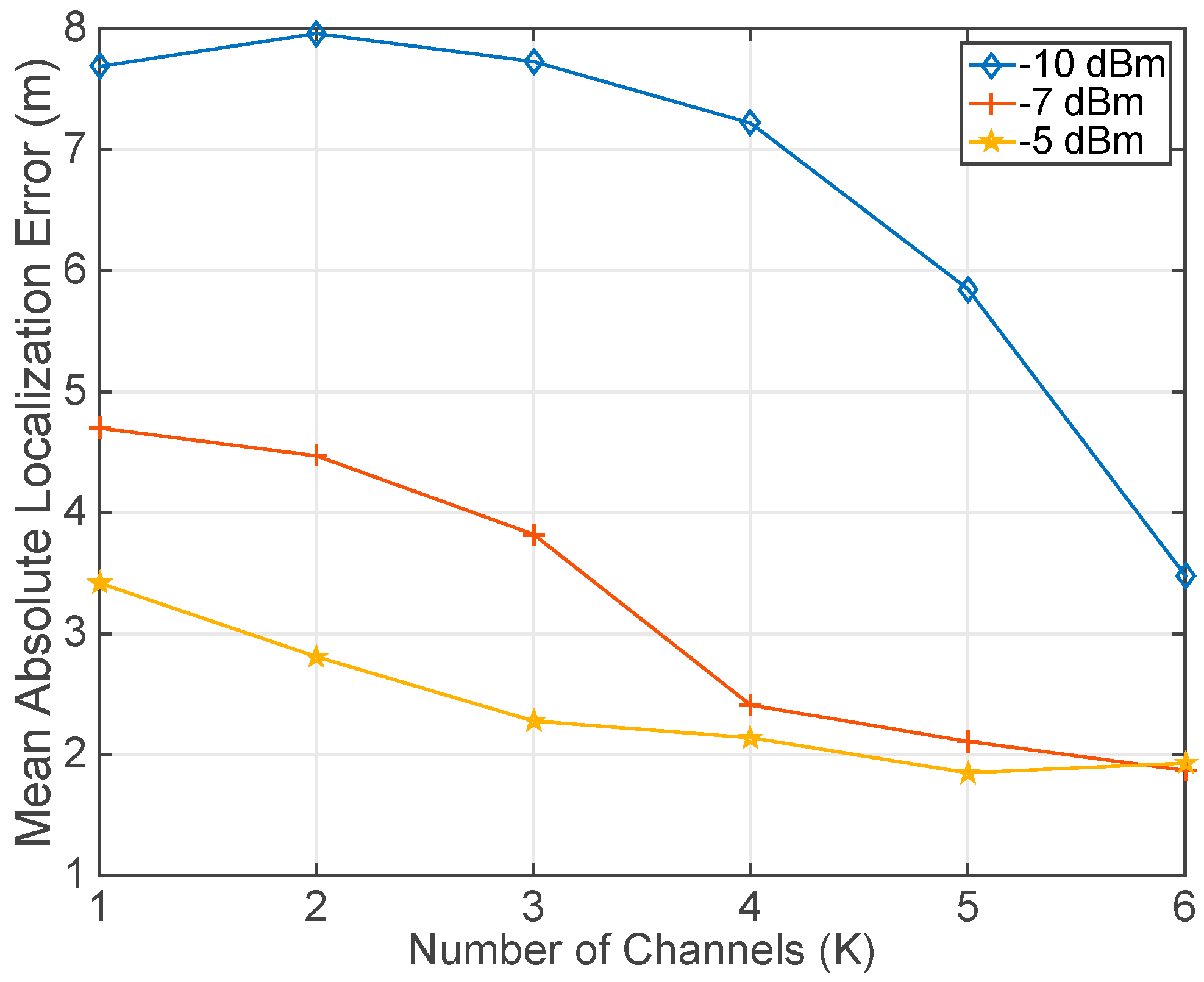
4.2. Experimental Results
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Song, Z.; Jiang, G.; Huang, C. A Survey on Indoor Positioning Technologies. In Theoretical and Mathematical Foundations of Computer Science; Springer: Berlin, Germany, 2011; pp. 198–206. [Google Scholar]
- Liu, H.; Darabi, H.; Banerjee, P.; Liu, J. Survey of Wireless Indoor Positioning Techniques and Systems. IEEE Trans. Syst. Man Cybern. Part C 2007, 37, 1067–1080. [Google Scholar] [CrossRef]
- Sun, G.; Chen, J.; Guo, W.; Liu, K. Signal processing techniques in network-aided positioning: A survey of state-of-the-art positioning designs. IEEE Signal Process. Mag. 2005, 22, 12–23. [Google Scholar] [CrossRef]
- Deak, G.; Curran, K.; Condell, J. A survey of active and passive indoor localisation systems. Comput. Commun. 2012, 35, 1939–1954. [Google Scholar] [CrossRef]
- Bahl, P.; Padmanabhan, V. RADAR: An In-Building RF-Based User Location and Tracking System. INFOCOM 2000. In Proceedings of the IEEE Nineteenth Annual Joint Conference of the IEEE Computer and Communications Societies, Tel Aviv, Israel, 26–30 March 2000; pp. 775–784. [Google Scholar]
- Torres-Sospedra, J.; Montoliu, R.; Trilles, S.; Belmonte, O.; Huerta, J. Comprehensive analysis of distance and similarity measures for Wi-Fi fingerprinting indoor positioning systems. Expert Syst. Appl. 2015, 42, 9263–9278. [Google Scholar] [CrossRef]
- Ezpeleta, S.; Claver, J.M.; Pérez-Solano, J.J.; Martí, J.V. RF-Based Location Using Interpolation Functions to Reduce Fingerprint Mapping. Sensors 2015, 15, 27322–27340. [Google Scholar] [CrossRef] [PubMed]
- Claver, J.M.; Ezpeleta, S.; Martí, J.V.; Pérez-Solano, J.J. Analysis of RF-based Indoor Localization with Multiple Channels and Signal Strengths. In Proceedings of the 8th Wireless Internet International Conference, WICON, Lisbon, Portugal, 13–14 November 2014; pp. 70–77. [Google Scholar]
- IEEE Std 802.15.4-2003. Available online: http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=1237559&isnumber=27762 (accessed on 11 April 2017).
- Gang, L.; Krishnamachari, B.; Raghavendra, C.S. Performance evaluation of the IEEE 802.15.4 MAC for low-rate low-power wireless networks. In Proceedings of the IEEE International Conference on Performance, Computing, and Communications, Phoenix, AZ, USA, 15–17 April 2004; pp. 701–706. [Google Scholar]
- Petrova, M.; Riihijarvi, J.; Mahonen, P.; Labella, S. Performance study of IEEE 802.15.4 using measurements and simulations. In Proceedings of the IEEE Wireless Communications and Networking Conference, Las Vegas, NV, USA, 3–6 April 2006; pp. 487–492. [Google Scholar]
- Latré, B.; De Mil, P.; Moerman, I.; Van Dierdonck, N.; Dhoedt, B.; Demeester, P. Throughput and delay analysis of unslotted IEEE 802.15.4. J. Netw. 2006, 1, 20–28. [Google Scholar] [CrossRef]
- Ergen, S.C.; Varaiya, P. TDMA scheduling algorithms for wireless sensor networks. Wirel. Netw. 2010, 16, 985–997. [Google Scholar] [CrossRef]
- Zhou, G.; Huang, C.; Yan, T.; He, T.; Stankovic, J.A.; Abdelzaher, T.F. MMSN: Multi-frequency media access control for wireless sensor networks. In Proceedings of the 25th IEEE International Conference on Computer Communications, Barcelona, Spain, 23–29 April 2006; pp. 1–13. [Google Scholar]
- Kim, Y.; Shin, H.; Cha, H. Y-MAC: An energy-efficient multi-channel MAC protocol for dense wireless sensor networks. In Proceedings of the 7th International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 53–63. [Google Scholar]
- Jovanovic, M.D.; Djordjevic, G.L. TFMAC: Multi-channel MAC protocol for wireless sensor networks. In Proceedings of the 8th Telecommunications in Modern Satellite, Cable and Broadcasting Services Conference, Nis, Serbia, 26–28 September 2007; pp. 23–26. [Google Scholar]
- Wu, Y.; Stankovic, J.A.; He, T.; Lin, S. Realistic and efficient multi-channel communications in wireless sensor networks. In Proceedings of the 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008. [Google Scholar]
- Van Vinh, P.; Oh, H. Optimized Sharable-Slot Allocation Using Multiple Channels to Reduce Data-Gathering Delay in Wireless Sensor Networks. Sensors 2016, 16, 505. [Google Scholar] [CrossRef] [PubMed]
- Fonseca, J.A.; Bartolomeu, P. A MAC protocol to manage communications in localization systems based on IEEE 802.15.4. In Proceedings of the 2008 34th Annual Conference of IEEE Industrial Electronics, Orlando, FL, USA, 10–13 November 2008; pp. 2717–2723. [Google Scholar]
- Polastre, J.; Szewczyk, R.; Culler, D. Telos: Enabling ultra-low power wireless research. In Proceedings of the 4th International Symposium on Information Processing in Sensor Networks, IPSN, Los Angeles, CA, USA, 25–27 April 2005; pp. 364–369. [Google Scholar]
- Osterlind, F.; Dunkels, A.; Eriksson, J.; Finne, N.; Voigt, T. Cross-Level Sensor Network Simulation with COOJA. In Proceedings of the 31th IEEE Conference on Local Computer Networks, Tampa, FL, USA, 14–17 November 2006; pp. 641–648. [Google Scholar]
- Levis, P.; Gay, D. TinyOS Programming; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar]
- Texas Instruments. CC2420 2.4 GHz IEEE 802.15.4/ZigBee-Ready RF Transceiver Datasheet. Available online: http://www.ti.com/lit/ds/symlink/cc2420.pdf (accessed on 25 June 2017).
- Marti, J.; Sales, J.; Marin, R.; Jimenez-Ruiz, E. Localization of mobile sensors and actuators for intervention in low-visibility conditions: The ZigBee fingerprinting approach. Int. J. Distrib. Sens. Netw. 2012, 2012, 1–10. [Google Scholar] [CrossRef]



| Mode | Current Consumption |
|---|---|
| Reception | 18.8 mA |
| Transmission (L = −25 dBm) | 8.5 mA |
| Transmission (L = −15 dBm) | 9.9 mA |
| Transmission (L = −10 dBm) | 11.2 mA |
| Transmission (L = −7 dBm) | 12.5 mA |
| Transmission (L = −5 dBm) | 13.9 mA |
| Transmission (L = −3 dBm) | 15.2 mA |
| Transmission (L = −1 dBm) | 16.5 mA |
| Transmission (L = 0 dBm) | 17.4 mA |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pérez-Solano, J.J.; Claver, J.M.; Ezpeleta, S. Optimizing the MAC Protocol in Localization Systems Based on IEEE 802.15.4 Networks. Sensors 2017, 17, 1582. https://doi.org/10.3390/s17071582
Pérez-Solano JJ, Claver JM, Ezpeleta S. Optimizing the MAC Protocol in Localization Systems Based on IEEE 802.15.4 Networks. Sensors. 2017; 17(7):1582. https://doi.org/10.3390/s17071582
Chicago/Turabian StylePérez-Solano, Juan J., Jose M. Claver, and Santiago Ezpeleta. 2017. "Optimizing the MAC Protocol in Localization Systems Based on IEEE 802.15.4 Networks" Sensors 17, no. 7: 1582. https://doi.org/10.3390/s17071582
APA StylePérez-Solano, J. J., Claver, J. M., & Ezpeleta, S. (2017). Optimizing the MAC Protocol in Localization Systems Based on IEEE 802.15.4 Networks. Sensors, 17(7), 1582. https://doi.org/10.3390/s17071582







