Dynamic Resource Allocation and Access Class Barring Scheme for Delay-Sensitive Devices in Machine to Machine (M2M) Communications
Abstract
:1. Introduction
2. Preliminaries
2.1. Related Works
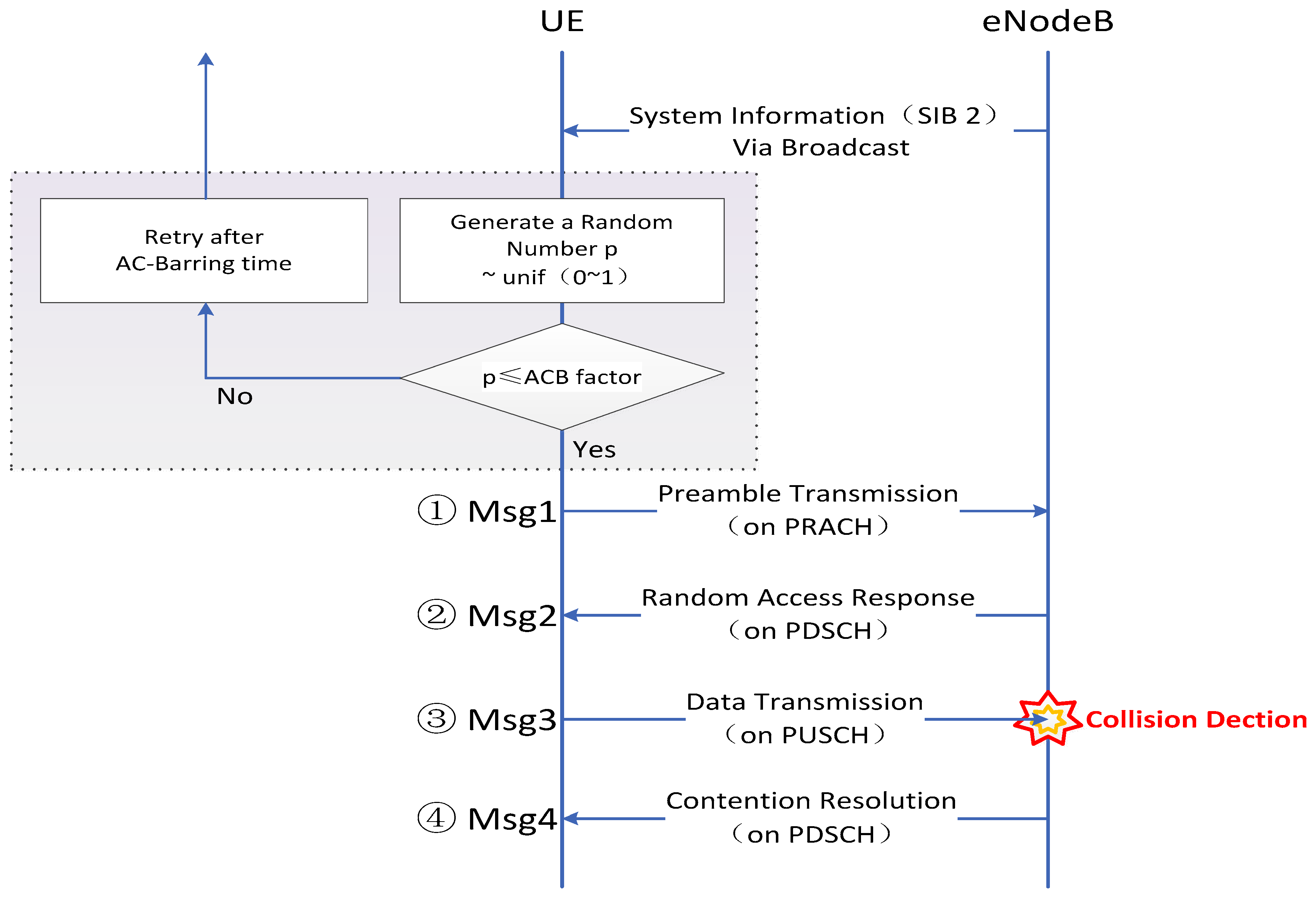
2.2. Random Access Procedure in LTE-A System
- Msg1: preamble transmission. Once an MTC device launches an access request to the RACH, it randomly selects a preamble with equal probability and transmits the selected preamble to the eNodeB via PRACH (i.e., the same uplink time-frequency resources). When two or more nodes select identical preambles and send them at the same time, there could be a collision.
- Msg2: random access response. If a preamble has been received correctly, the eNodeB computes an identifier and then transmits a random access response (RAR) to the UE devices. The RAR includes a RA preamble identifier (ID), an uplink grant for MSG3, timing alignment (TA) command for corresponding UEs, and assignment of a temporary identifier (the cell radio network temporary identifier, CRNTI). UE is expected to receive RAR within a timing window.
- Msg3: data transmission. A UE first finds its random access response by looking up the index of the preamble it has used in its random access request, and then uses the dedicated resource block (RB) on PUSCH to transmit a Connection Request message with a UE identifier to the eNodeB. If two or more UEs select an identical preamble in Step 1, they will implement uplink scheduling in the same RBs, thus scheduled message will not be correctly decoded by eNB due to the co-channel interference. This section is the main reason of random access conflict.
- Msg4: contention resolution. Upon reception of a Connection Request in Step 3, the eNodeB transmits a Connection Resolution message as an response to Step 3. Therefore, if a device does not receive Step 4, it will indicate a failure in the Contention Completion and launch a new access request after a random backoff.
3. Dynamic Resource Allocation and ACB Scheme for Delay-Sensitive Devices
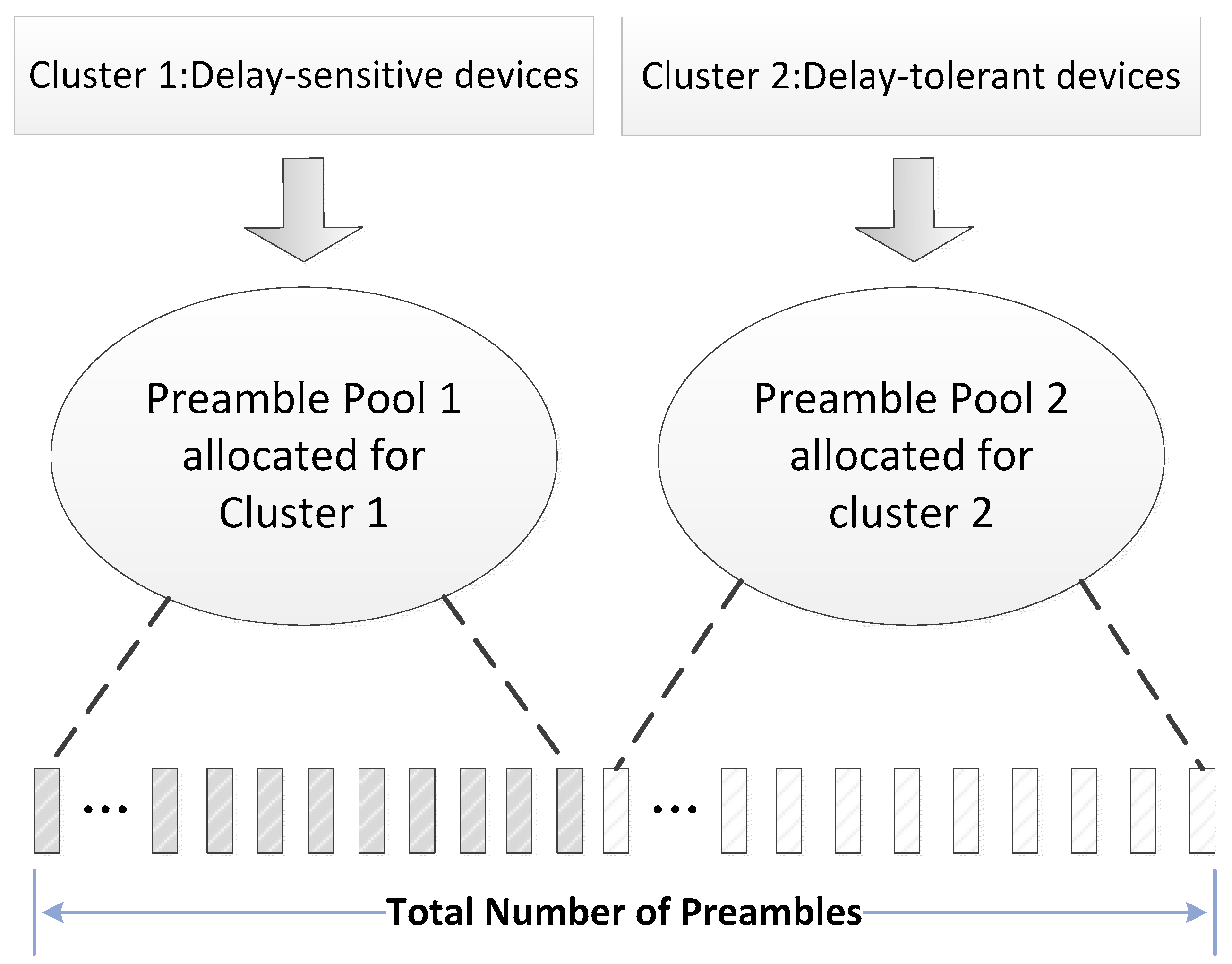
3.1. Clustured Structure
3.2. Proposed Optimization Scheme
- Average access delay of delay-sensitive devices.
- Preamble utilization rate for delay-sensitive devices.
| Algorithm 1 Proposed dynamic resource allocation and ACB scheme in a slot |
| 1: : number of DS devices attempt to access |
| 2: : ACB factor |
| 3: : optimal number of preambles allocated to DS devices |
| 4: : optimal value of ACB factor for DS devices |
| 5: : number of available preambles |
| 6: if then |
| 7: Set ; |
| 8: Compute through Equation (9); |
| 9: if then |
| 10: ; |
| 11: else |
| 12: Compute through Equation (10); |
| 13: end if |
| 14: else if then |
| 15: Set |
| 16: Compute through Equation (12); |
| 17: if then |
| 18: ; |
| 19: else |
| 20: Compute through Equation (13); |
| 21: end if |
| 22: end if |
4. Analysis Model
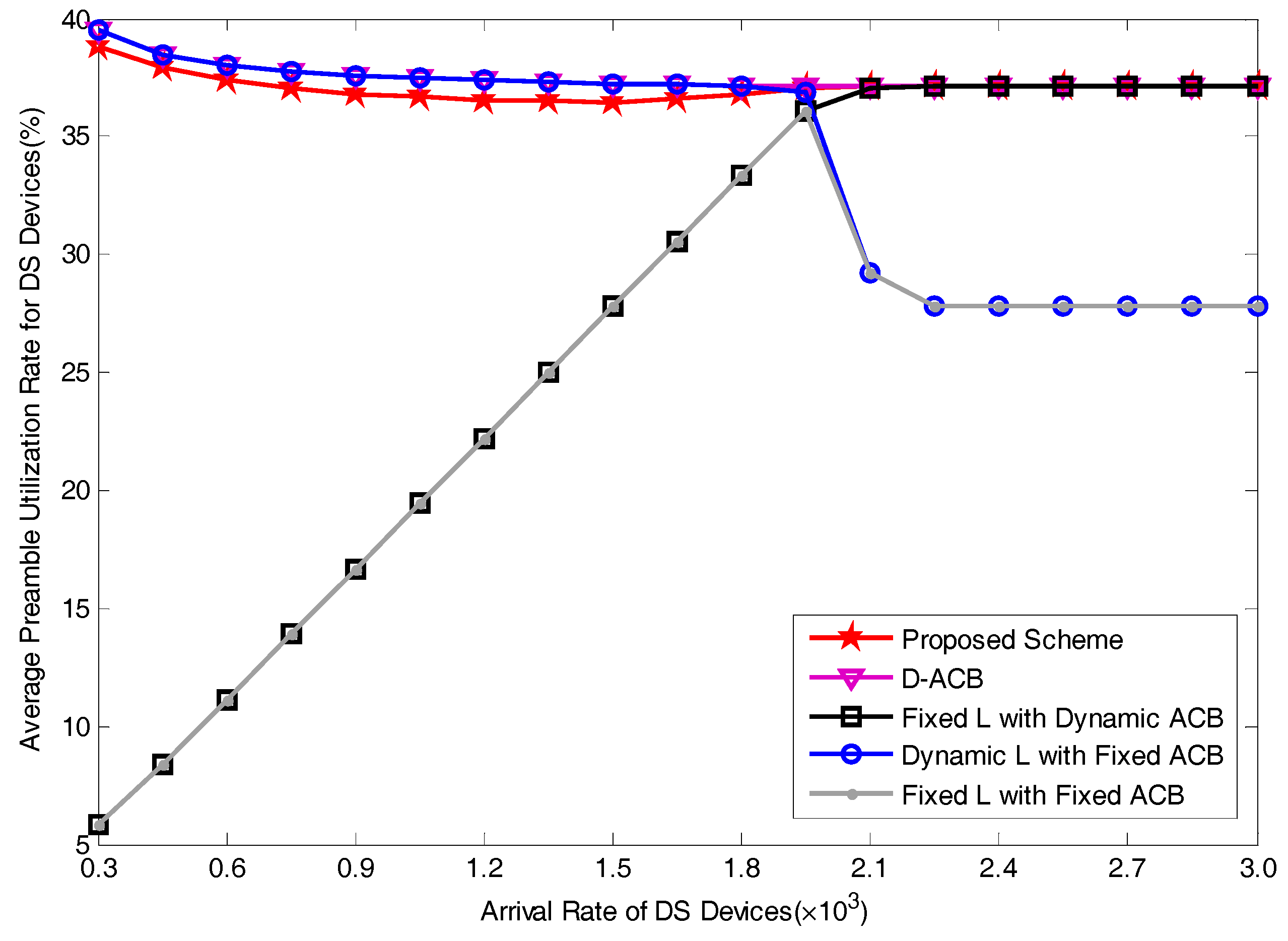
5. Performance Evaluation
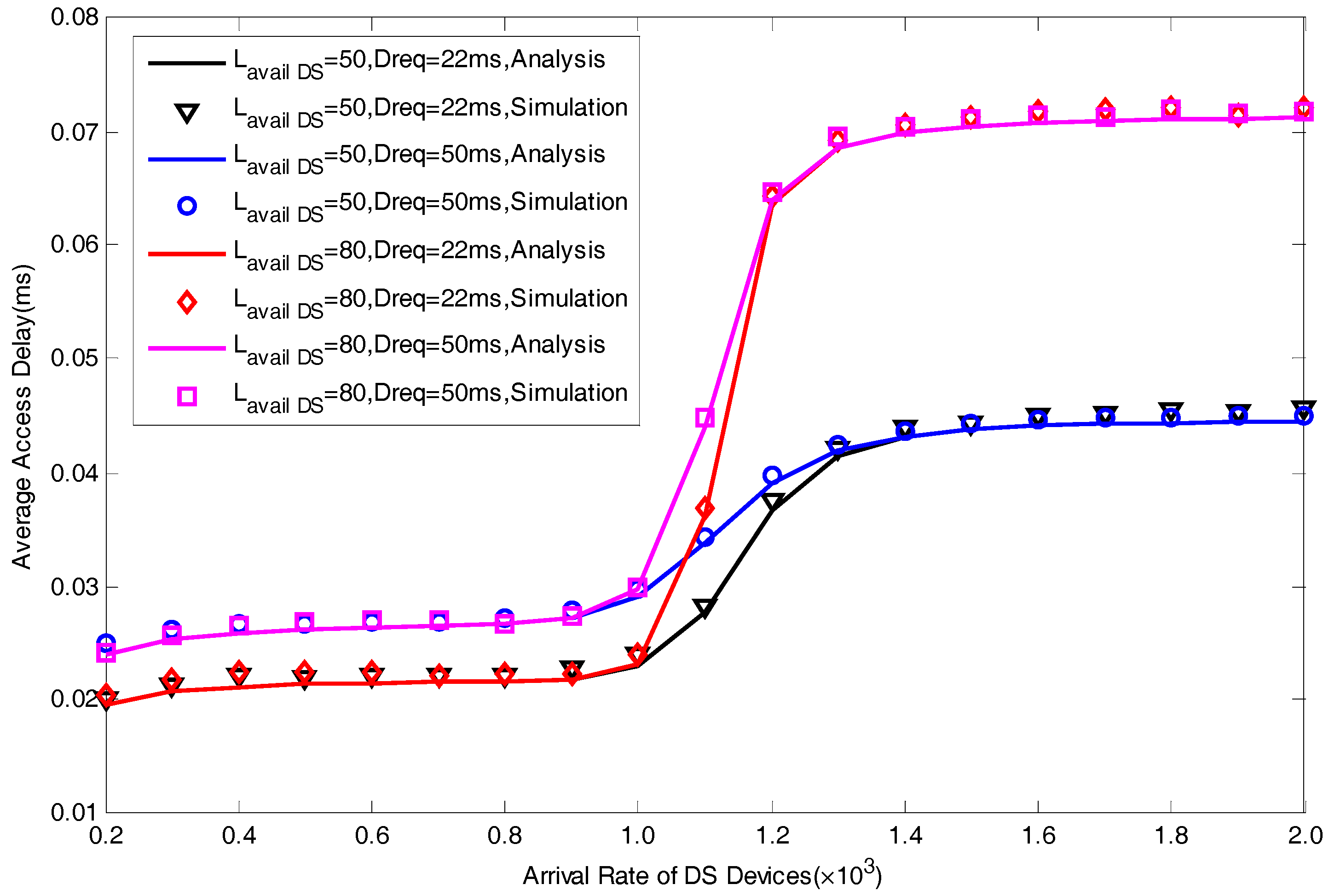
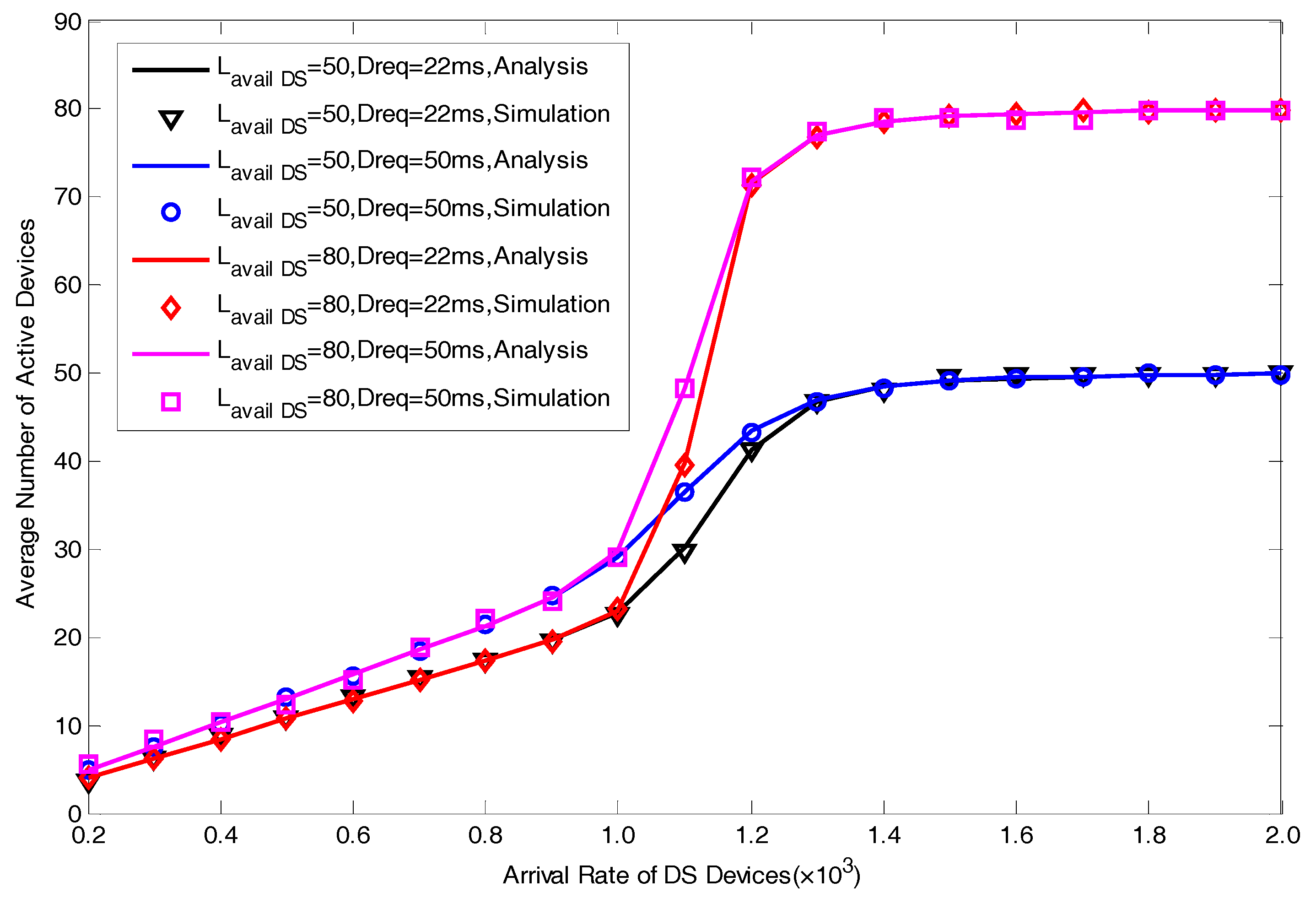
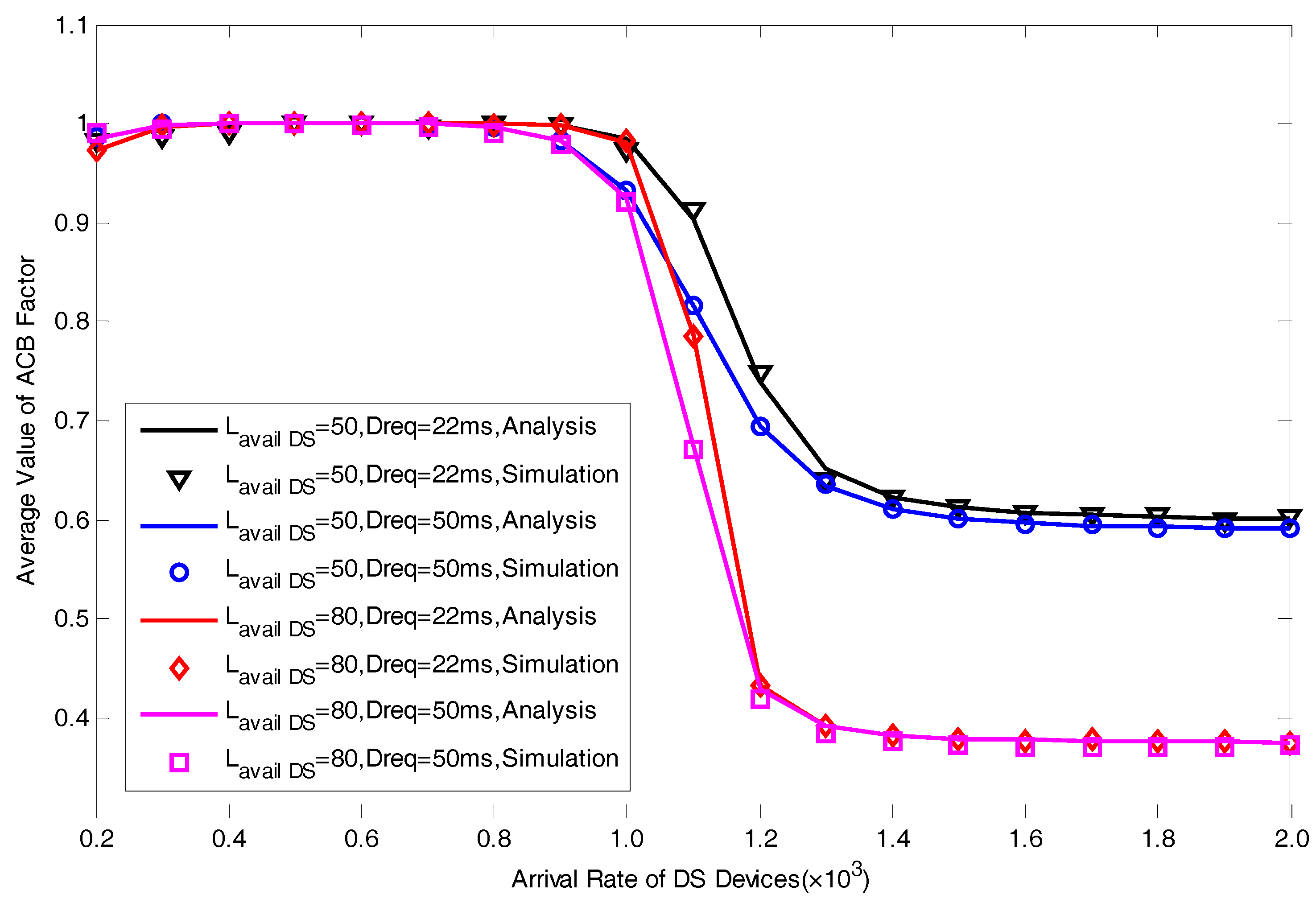
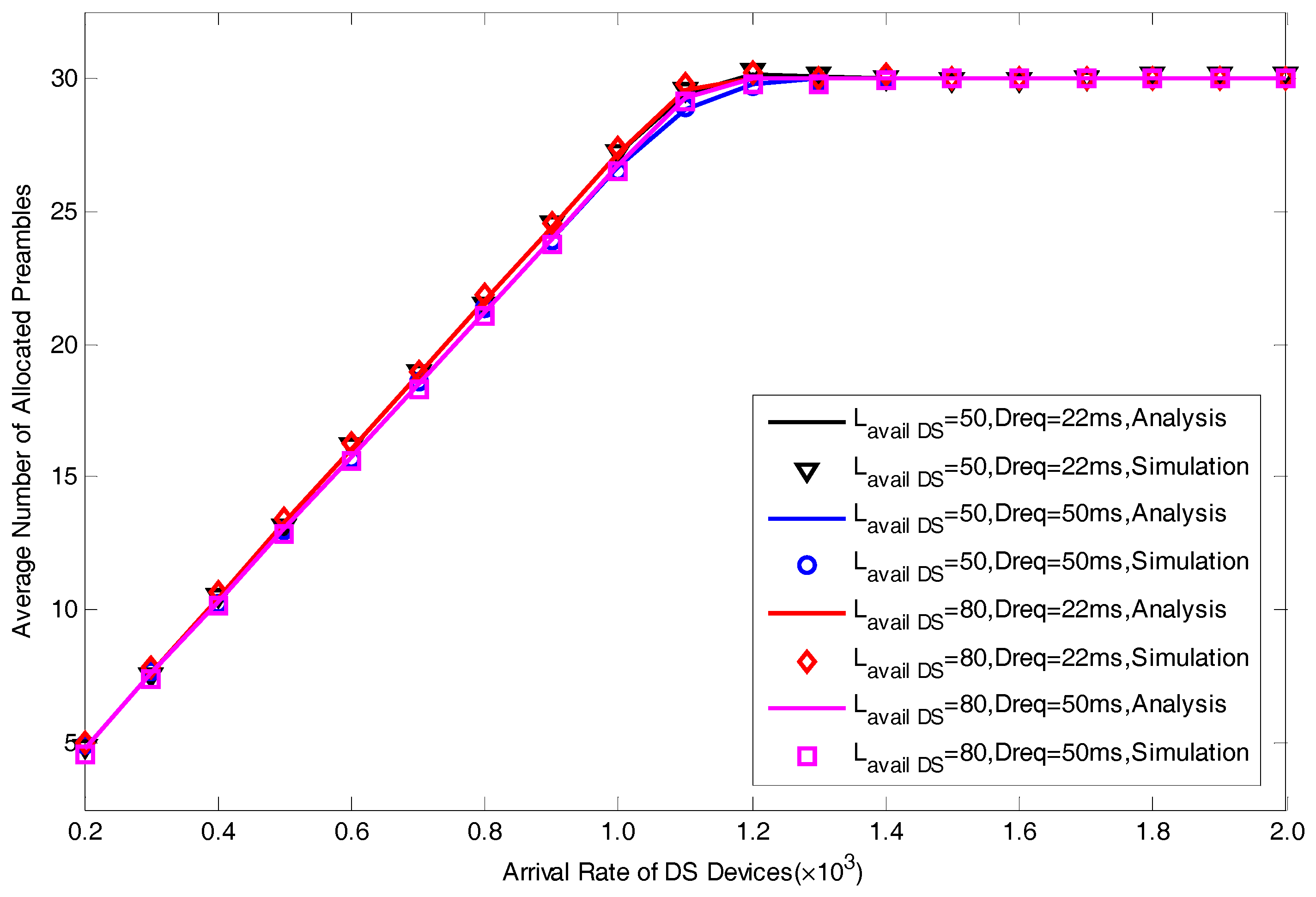
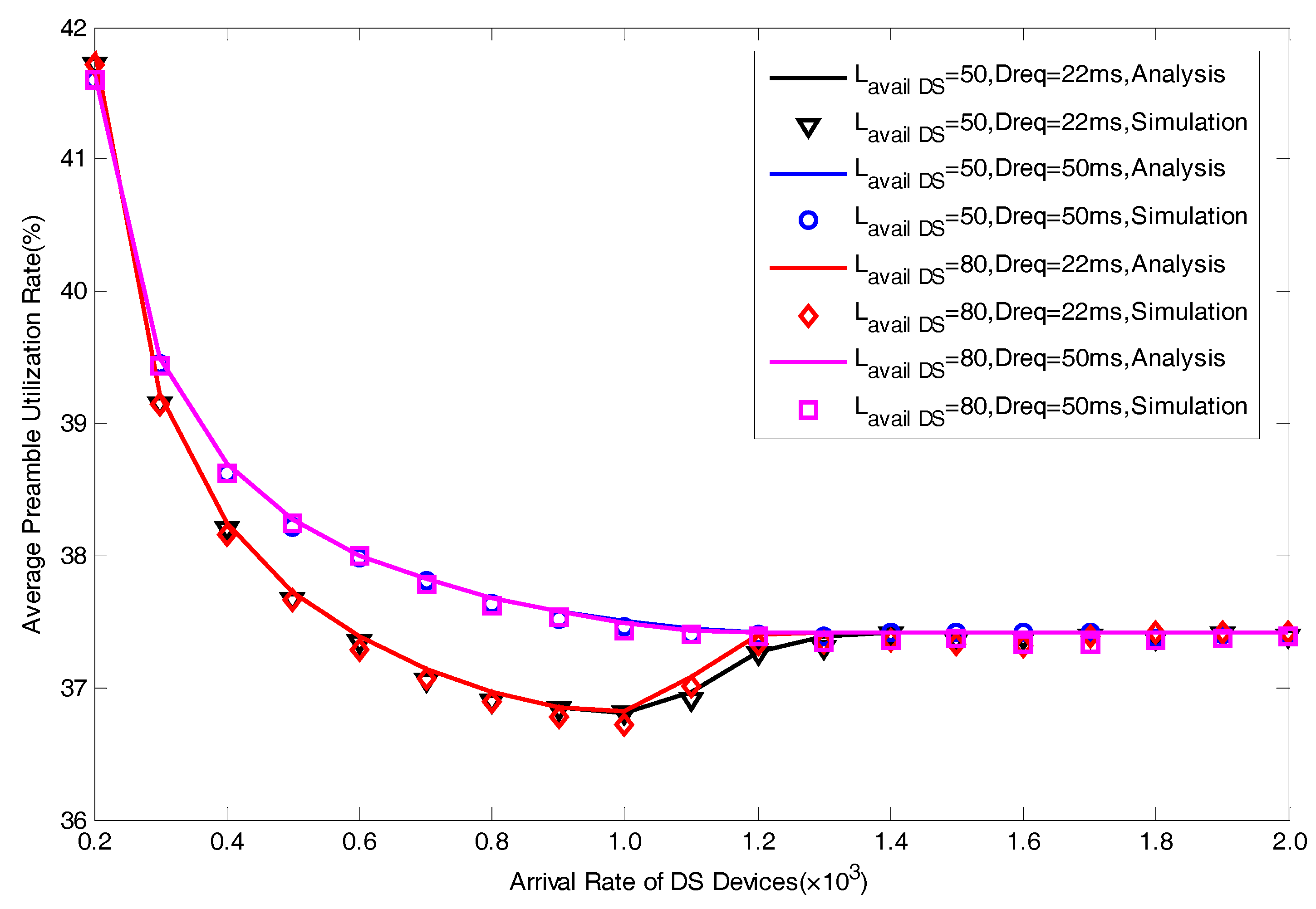
5.1. Model Verification
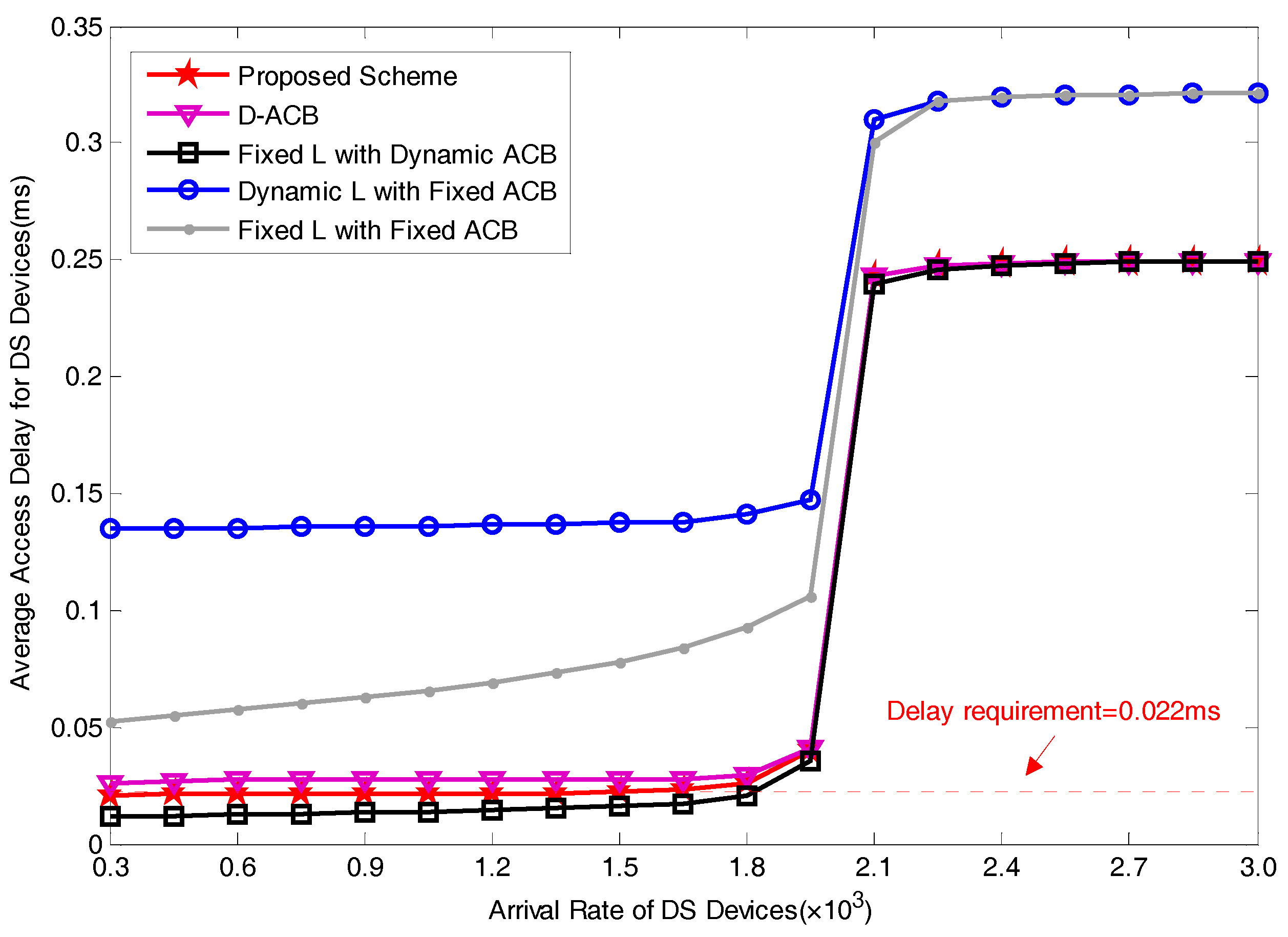
5.2. Performance Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Atzori, L.; Lera, A.; Morabito, G. The Internet of Things: A survey. Computer Networks the International. J. Comput. Telecommun. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Wu, H.; Zhu, C.; La, R.; Liu, X.; Zhang, Y. FASA: Accelerated S-ALOHA Using Access History for Event-Driven M2M Communications. IEEE/ACM Trans. Netw. 2013, 21, 1904–1917. [Google Scholar] [CrossRef]
- Laya, A.; Alonso, L.; Alonso-Zarate, J. Is the Random Access Channel of LTE and LTE-A Suitable for M2M Communications? A Survey of Alternatives. IEEE Commun. Surv. Tutor. 2014, 16, 4–16. [Google Scholar] [CrossRef]
- Lawton, G. Machine-to-machine technology gears up for growth. Computer 2014, 37, 12–15. [Google Scholar] [CrossRef]
- Islam, M.; Taha, A.E.; Akl, S. A Survey of Access Management Techniques in Machine Type Communications. IEEE Commun. Mag. 2014, 52, 74–81. [Google Scholar] [CrossRef]
- Digital Cellular Telecommunications System (Phase 2+) (GSM); Universal Mobile Telecommunications System (UMTS); LTE; Service Requirements for Machine-Type Communications (MTC); Stage 1 (3GPP TS 22.368 Version 13.1.0 Release 13). Available online: http://www.etsi.org/deliver/etsi_ts/122300_122399/122368/13.01.00_60/ts_122368v130100p.pdf (accessed on 28 March 2016).
- Metnitzer, A. Nokia Siemens Networks Machine2Machine Solution. In Proceedings of the 34th International Convention MIPRO, Opatija, Croatia, 23–27 May 2011. [Google Scholar]
- More than 50 Billion Connected Devices. Available online: http://www.akos-rs.si/files/Telekomunikacije/Digitalna_agenda/Internetni_protokol_Ipv6/More-than-50-billion-connected-devices.pdf (accessed on 12 January 2017).
- Kan, Z.; Fanglong, H.; Wenbo, W.; Wei, X.; Dohler, M. Radio resource allocation in LTE-advanced cellular networks with M2M communications. IEEE Commun. Mag. 2012, 50, 184–192. [Google Scholar]
- Ferdouse, L.; Anpalagan, A.; Misra, S. Congestion and overload control techniques in massive M2M systems: A survey. Trans. Emerg. Tel. Tech. 2015, 28, e2936. [Google Scholar] [CrossRef]
- Hussain, F.; Anpalagan, A.; Vannithamby, R. Medium access control techniques in M2M communication: Survey and critical review. Trans. Emerg. Tel. Tech. 2014, 28, e2869. [Google Scholar] [CrossRef]
- LTE; Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN); Overall Description; Stage 2 (3GPP TS 36.300 Version 10.7.0 Release 10). Available online: http://www.etsi.org/deliver/etsi_ts/136300_136399/136300/10.07.00_60/ts_136300v100700p.pdf (accessed on 18 December 2015).
- Hasan, M.; Hossain, E.; Niyato, D. Random access for machine-to-machine communication in LTE-advanced networks: Issues and approaches. IEEE Commun. Mag. 2013, 51, 86–93. [Google Scholar] [CrossRef]
- Zhao, X.; Zhai, J.; Fang, G. An Access Priority Level Based Random Access Scheme for QoS Guarantee in TD-LTE-A Systems. In Proceedings of the 2014 IEEE 80th Vehicular Technology Conference (VTC Fall), Vancouver, BC, Canada, 14–17 September 2014. [Google Scholar]
- Fabini, J.; Zseby, T. M2M communication delay challenges: Application and measurement perspectives. In Proceedings of the 2015 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Pisa, Italy, 11–14 May 2015. [Google Scholar]
- Ksentini, A.; Hadjadj-Aoul, Y.; Taleb, T. Cellular-based machine-to-machine: Overload control. IEEE Netw. 2012, 26, 54–60. [Google Scholar] [CrossRef]
- He, H.; Du, Q.; Song, H. Traffic-Aware ACB Scheme for Massive Access in Machine-to-Machine Networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015. [Google Scholar]
- Duan, S.; Shah-Mansouri, V.; Wang, Z. D-ACB: Adaptive Congestion Control Algorithm for Bursty M2M Traffic in LTE Networks. IEEE Trans. Veh. Technol. 2016, 65, 9847–9861. [Google Scholar] [CrossRef]
- Hwang, H.Y.; Oh, S.M.; Lee, C. Dynamic RACH Preamble Allocation Scheme. In Proceedings of the 2015 IEEE International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 28–30 October 2015. [Google Scholar]
- Morvari, F.; Ghasemi, A. Two-Stage Resource Allocation for Random Access M2M Communications in LTE Network. IEEE Commun. Lett. 2016, 20, 982–985. [Google Scholar] [CrossRef]
- Niyato, D.; Wang, P.; Dong, I.K. Performance modeling and analysis of heterogeneous machine type communications. IEEE Trans. Wirel. Commun. 2014, 13, 2836–2849. [Google Scholar]
- Zangar, N.; Gharbi, S.; Abdennebi, M. Service differentiation strategy based on MACB factor for M2M Communications in LTE-A Networks. In Proceedings of the 2016 13th IEEE Consumer Communications & Networking Conference, Las Vegas, NV, USA, 9–12 January 2016. [Google Scholar]
- Phuyal, U.; Koc, A.; Fong, M.H. Controlling access overload and signaling congestion in M2M networks. In Proceedings of the 2012 Conference Record of the Forty Sixth Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Pacific Grove, CA, USA, 4–7 November 2012. [Google Scholar]
- 3nd Generation Partnership Project; Technical Specification Group Radio Access Network; Study on RAN Improvements for Machine-Type Communications (3GPP TR 37.868 V11.0). Available online: http://www.qtc.jp/3GPP/Specs/37868-b00.pdf (accessed on 27 May 2016).
- LET; Evolved Universal Terrestrial Radio Access (E-UTRA); Medium Access Control (MAC) Protocol Specification (3GPP TS 36.321 Version 12.2.1 Release 12). Available online: http://www.etsi.org/deliver/etsi_ts/136300_136399/136321/12.02.01_60/ts_136321v120201p.pdf (accessed on 3 March 2017).
- Kim, D.; Kim, W.; An, S. Adaptive random access preamble split in LTE. In Proceedings of the 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013. [Google Scholar]
- Kurose, J.F.; Ross, K.W. Computer Networking: A Top-Down Approach. Available online: http://www.bau.edu.jo/UserPortal/UserProfile/PostsAttach/10617_1870_1.pdf (accessed on 2 October 2016).
- Choi, J. On the Adaptive Determination of the Number of Preambles in RACH for MTC. IEEE Commun. Lett. 2016, 20, 1385–1388. [Google Scholar] [CrossRef]
- Moon, J.; Lim, Y. Adaptive Access Class Barring for Machine-Type Communications in LTE-A. In Proceedings of the 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, 5–8 July 2016. [Google Scholar]
- MTC Simulation Results with Specific Solutions. Available online: http://www.3gpp.org/ftp/tsg_ran/WG2_RL2/TSGR2_71/Docs/R2-104662.zip (accessed on 19 September 2016).
- Khandelwal, G.; Yener, A.; Lee, K. ASAP: A MAC Protocol for Dense and Time Constrained RFID Systems. EURASIP J. Wirel. Comm. 2006, 2007, 4028–4033. [Google Scholar]
- Choi, Y.J.; Park, S.; Bahk, S. Multichannel random access in OFDMA wireless networks. IEEE J. Sel. Areas Commun. 2006, 24, 603–613. [Google Scholar] [CrossRef]
- Duan, S.; Shah-Mansouri, V.; Wong, V.W.S. Dynamic access class barring for M2M communications in LTE networks. In Proceedings of the 2013 IEEE Globecom Workshops (GC Wkshps), Atlanta, GA, USA, 9–13 December 2013. [Google Scholar]


| Parameter | Value |
|---|---|
| 30 | |
| 50, 80 | |
| 10 ms | |
| 22 ms, 50 ms | |
| 200~2000 arrivals/s |
| Descriptions | Notation | Value |
|---|---|---|
| Maximum number of active devices to be handled in a slot | 500 | |
| Arrival rate of DS devices | 300~3000 arrivals/s | |
| Total number of available preambles in an RA slot | 64 | |
| Maximum number of available preambles for DS Devices in an RA slot | 54 | |
| Length of a random access slot | 10 ms | |
| Delay requirement of DS devices | 22 ms |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, N.; Cao, C.; Wang, C. Dynamic Resource Allocation and Access Class Barring Scheme for Delay-Sensitive Devices in Machine to Machine (M2M) Communications. Sensors 2017, 17, 1407. https://doi.org/10.3390/s17061407
Li N, Cao C, Wang C. Dynamic Resource Allocation and Access Class Barring Scheme for Delay-Sensitive Devices in Machine to Machine (M2M) Communications. Sensors. 2017; 17(6):1407. https://doi.org/10.3390/s17061407
Chicago/Turabian StyleLi, Ning, Chao Cao, and Cong Wang. 2017. "Dynamic Resource Allocation and Access Class Barring Scheme for Delay-Sensitive Devices in Machine to Machine (M2M) Communications" Sensors 17, no. 6: 1407. https://doi.org/10.3390/s17061407





