The Physical Layer Security Experiments of Cooperative Communication System with Different Relay Behaviors
Abstract
:1. Introduction
2. System Description
2.1. System Model
2.2. Different Behaviors of Relay
- Cooperative Behavior: The relay decodes the received signal and forwards it to the destination.
- Selfish Behavior: The relay refuses to cooperate with probability [14], while selecting to cooperate with probability .
- Malicious Behavior: The relay forwards random noise instead of the received signals of the source.
2.3. The Probability of Non-Zero Secrecy Capacity with Different Behavior
- (1)
- under cooperative behavior: The relay cooperatively decodes and forwards the received signal to D (or E). The destination combines the received signals from S and R by maximum ratio combining (MRC). The main channel consists of the S-R-D path and S-D path, and the wiretap channel includes the S-E and S-R-E path. is the SNR of the main channel, and is the SNR of the eavesdropper channel. Therefore, according to (10), the is given by:where is the average SNR of S to D channel, is the average SNR of the main channel which consists of S to R, and R to D path. The average SNR of the S to E path is denoted as , and is the average SNR of the wiretap channel which consists of S to R, and R to E path.
- (2)
- under selfish behavior: If the relay is selfish with the probability , then, and , while the relay uses cooperative behavior with the probability (). Then, is given by:
- (3)
- under malicious behavior: The received signal from the malicious relay at D and E is considered as a noise. and , P(Cs > 0) is given by:
2.4. Equivalent Signal-To-Noise Ratio from Source to the Destination
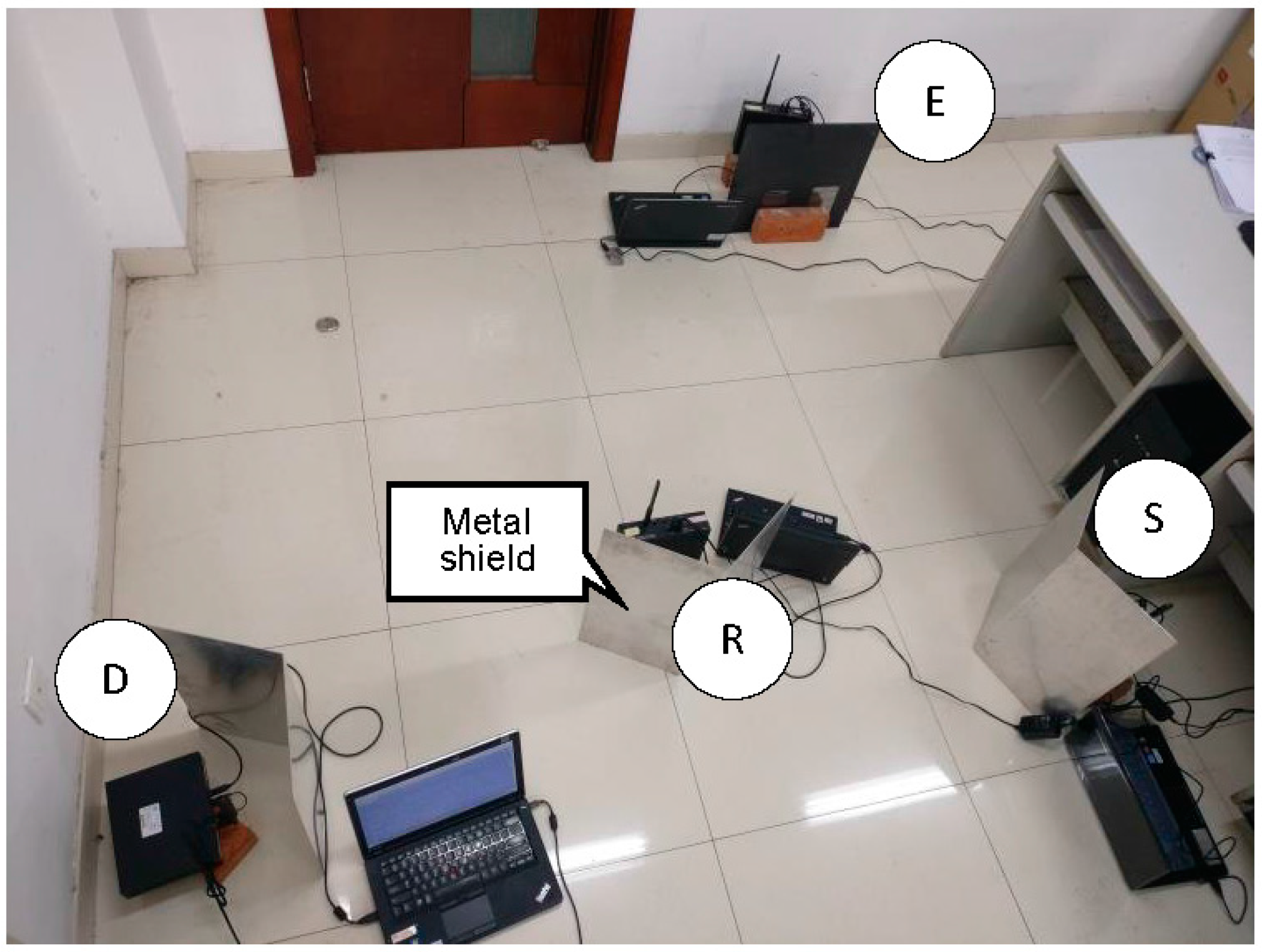
3. Experimental Setup
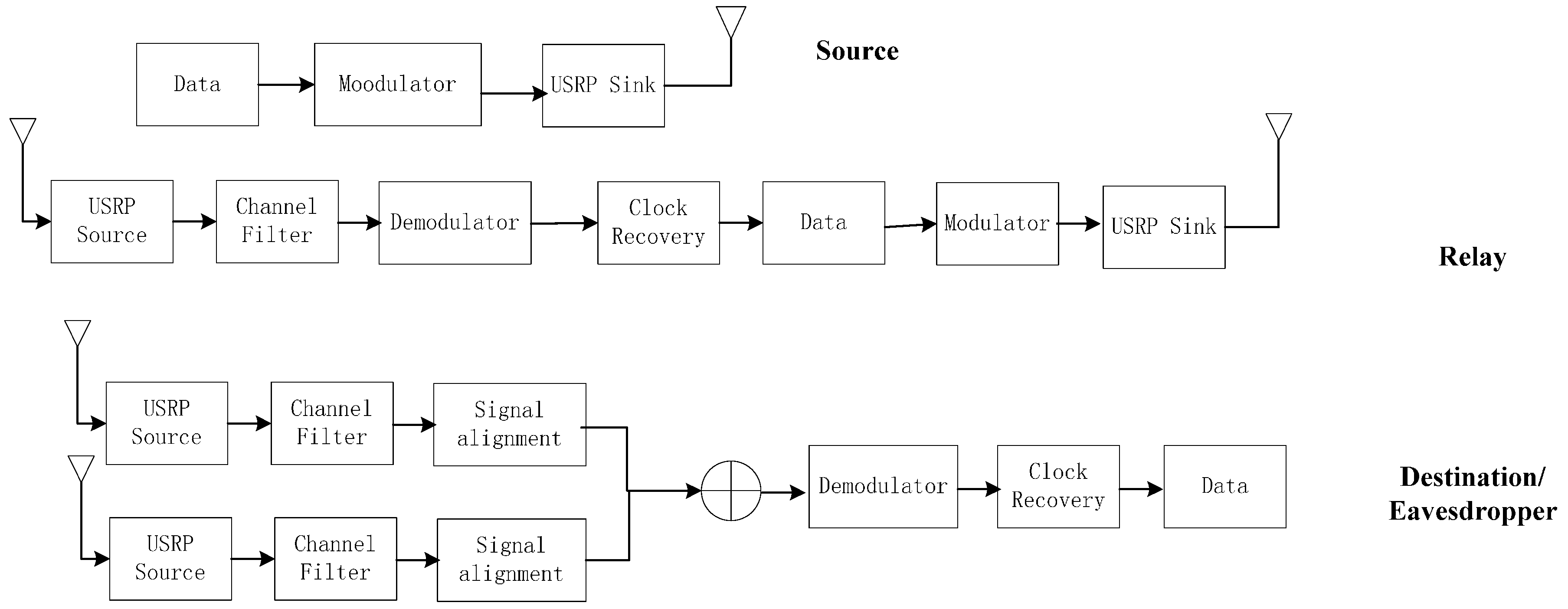
3.1. Source Operations
3.2. Relay Operations
3.3. Data Receiving and Processing
4. The Physical Layer Security Performance of the Relay Transmission Model
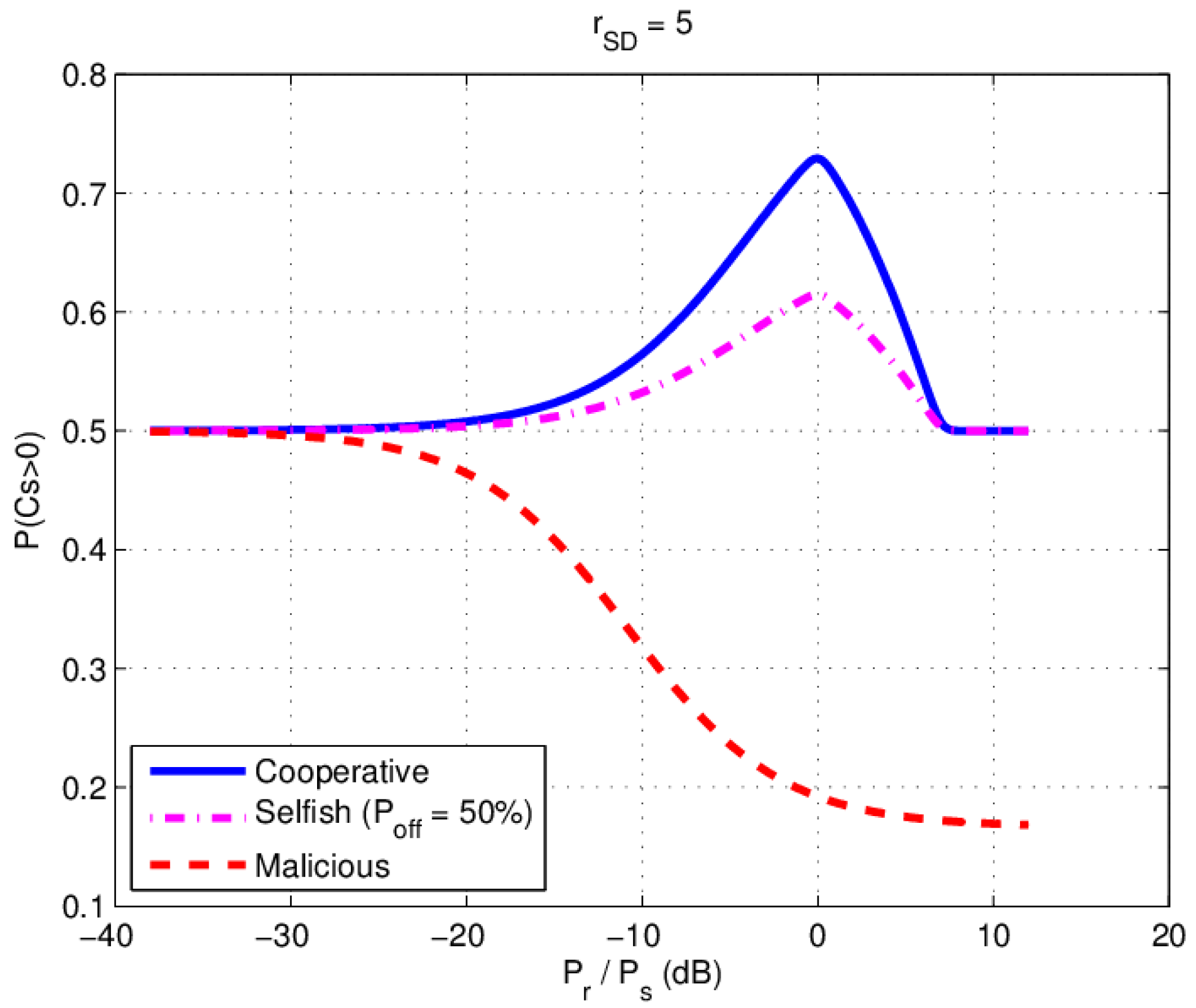
4.1. The Influence of the Relay Power for P(Cs > 0)
4.1.1. Simulation Results with Various Relay Power
4.1.2. Experimental Results with Various Relay Power
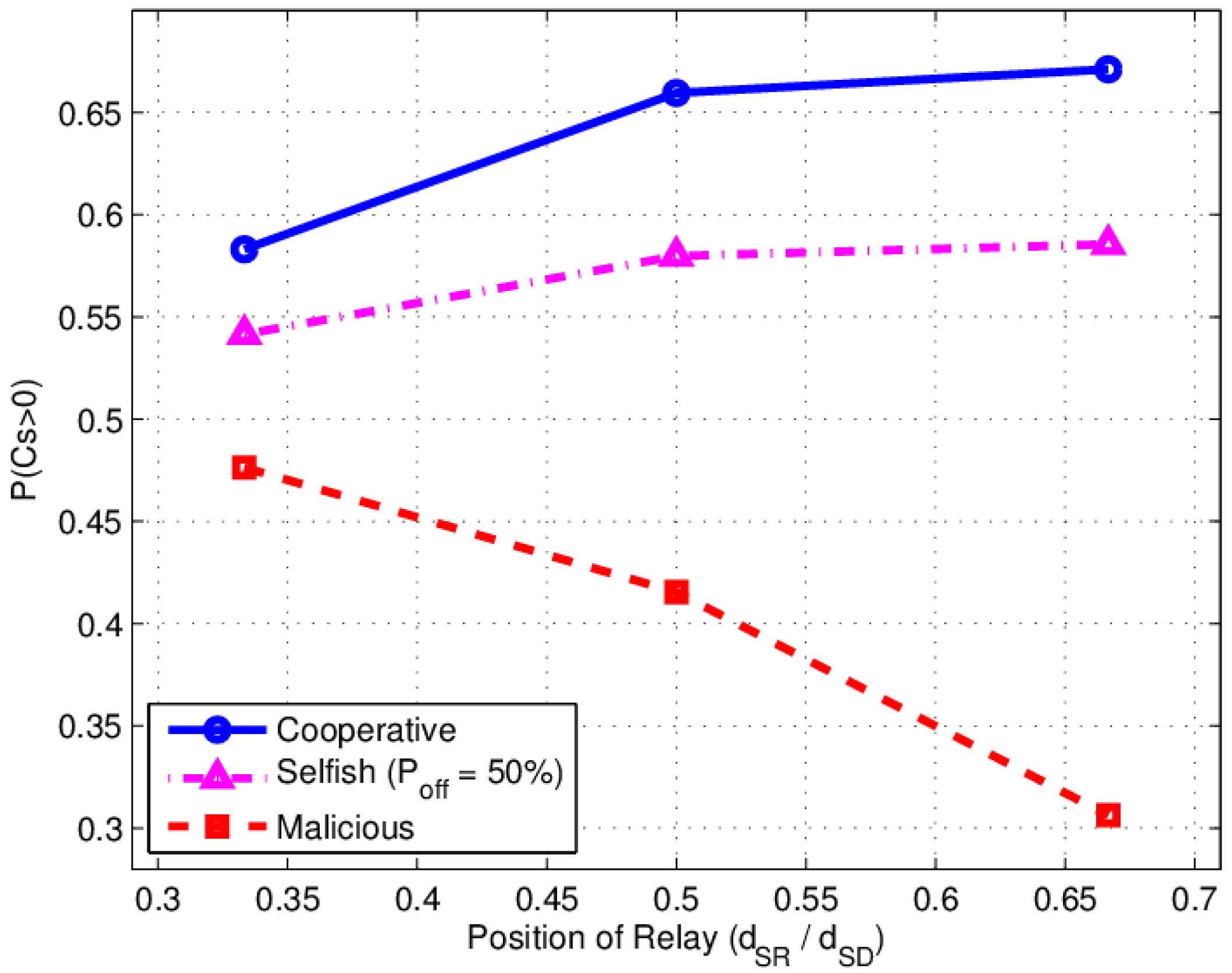
4.2. Influence of Relay Location for P(CS > 0)
4.2.1. Simulation Results with Various Relay Location
4.2.2. Experimental Results with Various Relay Location
5. Conclusions
- (1)
- The relays need more power to achieve the maximum-security performance in a real environment. In the experiment, the optimal relay power is larger than the source power in both cooperative and selfish behavior relay scenarios because of the non-ideal source to destination (S-D) channel;
- (2)
- In the malicious behavior relay case, the experimental value of is different from the ideal theoretical simulation result when the relay power is larger than the critical power (), which indicates that when s malicious relay forwards high enough noise power, the eavesdropper channel is deteriorated more seriously than the main channel;
- (3)
- Optimal relay location in both cooperative and selfish behavior of relay is in the middle of source and destination () in the ideal theoretical simulation. However, in the experiment, the optimal relay location is nearer to the destination because of the non-ideal source to relay and to destination (S-R-D) channel.
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Schneier, B. Description of a new variable-length key, 64-bit block cipher (Blowfish). In Proceedings of the Fast Software Encryption: 7th International Workshop, FSE 2000, New York, NY, USA, 10–12 April 2000; pp. 191–204. [Google Scholar]
- Bruce, S. Applied Cryptography: Protocols, Algorithms, and Source Code in C; John Wiley & Sons, Inc.: New York, NY, USA, 1996. [Google Scholar]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Wang, H.M.; Zheng, T.X. Physical Layer Security in Heterogeneous Cellular Network. In Physical Layer Security in Random Cellular Networks; Springer: Singapore, 2016; pp. 61–84. [Google Scholar]
- Wyner, A.D. The Wire-Tap Channel. Bell Labs Techn. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Labs Techn. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Lai, L.; El Gamal, H. The relay–eavesdropper channel: Cooperation for secrecy. IEEE Trans. Inf. Theory 2008, 54, 4005–4019. [Google Scholar] [CrossRef]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving wireless physical layer security via cooperating relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Bassily, R.; Ulukus, S. Deaf cooperation and relay selection strategies for secure communication in multiple relay networks. IEEE Trans. Signal Process. 2013, 61, 1544–1554. [Google Scholar] [CrossRef]
- Bassily, R.; Ulukus, S. Deaf cooperation for secrecy with multiple antennas at the helper. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1855–1864. [Google Scholar] [CrossRef]
- Bassily, R.; Ulukus, S. Secure communication in multiple relay networks through decode-and-forward strategies. J. Commun. Netw. 2012, 14, 352–363. [Google Scholar] [CrossRef]
- Chen, X.; Lei, L.; Zhang, H.; Yuen, C. Large-scale MIMO relaying techniques for physical layer security: AF or DF? IEEE Trans. Wirel. Commun. 2015, 14, 5135–5146. [Google Scholar] [CrossRef]
- Chen, X.; Zhong, C.; Yuen, C.; Chen, H.H. Multi-antenna relay aided wireless physical layer security. IEEE Commun. Mag. 2015, 53, 40–46. [Google Scholar] [CrossRef]
- Li, Q.; Yang, Y.; Ma, W.K.; Lin, M.; Ge, J.; Lin, J. Robust cooperative beamforming and artificial noise design for physical-layer secrecy in AF multi-antenna multi-relay networks. IEEE Trans. Signal Process. 2015, 63, 206–220. [Google Scholar] [CrossRef]
- Zhang, J.; Yuen, C.; Wen, C.K.; Jin, S.; Wong, K.K.; Zhu, H. Large system secrecy rate analysis for SWIPT MIMO wiretap channels. IEEE Trans. Inf. Forensics Secur. 2016, 11, 74–85. [Google Scholar] [CrossRef]
- Salem, A.; Hamdi, K.A.; Rabie, K.M. Physical layer security with RF energy harvesting in AF multi-antenna relaying networks. IEEE Trans. Commun. 2016, 64, 3025–3038. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, H.H.; Wang, L. Physical layer security for next generation wireless networks: Theories, Technologies, and Challenges. IEEE Commun. Surv. Tutor. 2016, 19, 347–376. [Google Scholar] [CrossRef]
- Xiang, H.; Yener, A. Secrecy and reliable Byzantine detection in a Gaussian untrusted two-hop link. In Proceedings of the 2010 IEEE Information Theory Workshop on Information Theory (ITW 2010), Cairo, Egypt, 6–8 January 2010; pp. 1–5. [Google Scholar]
- He, X.; Yener, A. Cooperation with an untrusted relay: A secrecy perspective. IEEE Trans. Inf. Theory 2010, 56, 3807–3827. [Google Scholar] [CrossRef]
- Hou, L.; Fu, X. Physical layer security with dynamic behaviour cooperator based on coalitional game. IET Commun. 2014, 8, 1258–1264. [Google Scholar] [CrossRef]
- Fu, X.; Li, L.; Zong, Q. Bayesian Coalitional Game in Physical Layer Security. Wirel. Pers. Commun. 2015, 85, 1237–1250. [Google Scholar] [CrossRef]
- Chrysikos, T.; Dagiuklas, T.; Kotsopoulos, S. Wireless information-theoretic security in an outdoor topology with obstacles: Theoretical analysis and experimental measurements. EURASIP J. Wirel. Commun. Netw. 2011, 2011. [Google Scholar] [CrossRef]
- Mitola, J. The software radio architecture. IEEE Commun. Mag. 1995, 33, 26–38. [Google Scholar] [CrossRef]
- Zhang, R.; Comaniciu, C.; Poor, H.V. Outage capacity and partial secrecy for energy efficient physical layer security in Gaussian fading channels. In Proceedings of the 2013 16th International Symposium on Wireless Personal Multimedia Communications (WPMC), Atlantic City, NJ, USA, 24–27 June 2013; pp. 1–5. [Google Scholar]
- Barros, J.; Rodrigues, M.R. Secrecy capacity of wireless channels. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Honolulu, HI, USA, 9–14 July 2006; pp. 356–360. [Google Scholar]
- Wang, T.; Cano, A.; Giannakis, G.B.; Laneman, J.N. High-performance cooperative demodulation with decode-and-forward relays. IEEE Trans. Commun. 2007, 55, 1427–1438. [Google Scholar] [CrossRef]
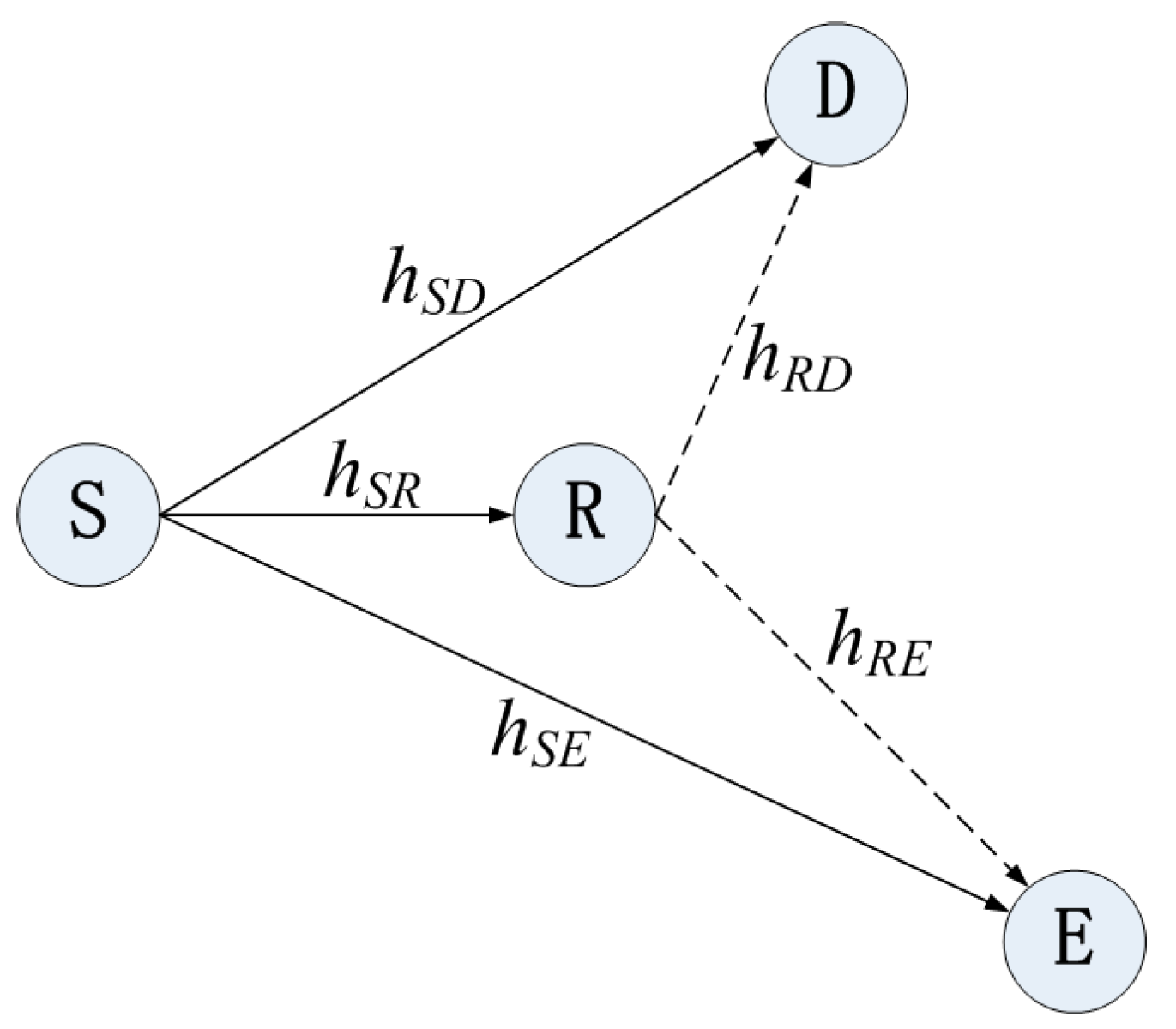




| the channel fading coefficients from S to D (source to destination) | |
| the channel fading coefficients from S to R (source to relay) | |
| the channel fading coefficients from R to D (relay to destination) | |
| the probability in the Off-State | |
| the probability of Non-zero secrecy capacity | |
| the average SNR of the main channel | |
| the average SNR of the wiretap channel | |
| the average SNR of the S to D channel (source to destination) | |
| the average SNR of the main channel which consists of channel from S to R and R to D | |
| the average SNR of the S to E path | |
| the average SNR of the wiretap channel which consists of channel from S to R, and R to E | |
| the BER at S-R hop | |
| the BER at R-D hop | |
| the BER of the two-hop S-R-D channel |
| Transmit Power (dBm) | −51 | −49 | −46.5 | −44 | −41.5 | −39 | −36 | −34 | −31 | −28.5 |
|---|---|---|---|---|---|---|---|---|---|---|
| 0.3383 | 0.2472 | 0.1873 | 0.113 | 0.061 | 0.0196 | 0.0026 | 0.0002 | 0.0001 | 0.0000 | |
| 0.0974 | 0.2614 | 0.4415 | 0.825 | 1.3386 | 2.3814 | 4.3727 | 7.1942 | 8.1577 | ∞ | |
| 0.3472 | 0.2639 | 0.2096 | 0.152 | 0.1118 | 0.0692 | 0.0226 | 0.0054 | 0.0005 | 0.0000 | |
| 0.0864 | 0.2231 | 0.3652 | 0.593 | 0.8293 | 1.2289 | 2.2451 | 3.6327 | 6.1224 | ∞ | |
| 0.5299 | 0.5394 | 0.5473 | 0.582 | 0.6175 | 0.6596 | 0.6608 | 0.6645 | 0.5713 | 0.5 |
| Transmit Power (dBm) | −51 | −49 | −46.5 | −44 | −41.5 | −39 | −36 | −34 | −31 | −28.5 |
|---|---|---|---|---|---|---|---|---|---|---|
| 0.3670 | 0.3810 | 0.4017 | 0.4198 | 0.4358 | 0.4459 | 0.4635 | 0.4811 | 0.4878 | 0.4918 | |
| 0.0647 | 0.0513 | 0.0343 | 0.0229 | 0.0146 | 0.0104 | 0.0047 | 0.0013 | 0.0005 | 0.0002 | |
| 0.3609 | 0.3725 | 0.3902 | 0.4104 | 0.4251 | 0.4359 | 0.4530 | 0.4685 | 0.4847 | 0.4918 | |
| 0.0710 | 0.0592 | 0.0416 | 0.0287 | 0.0200 | 0.0146 | 0.0078 | 0.0035 | 0.0010 | 0.0002 | |
| 0.4767 | 0.4624 | 0.4519 | 0.4438 | 0.4231 | 0.4155 | 0.3761 | 0.2652 | 0.3333 | 0.5 |
| Relay Location | Left (1.2 m, 0) | Middle (1.8 m, 0) | Right (2.4 m, 0) |
|---|---|---|---|
| 327.08 | 237.84 | 383.27 | |
| 2.081 | 2.3814 | 1.9336 | |
| 625.71 | 840.78 | 1174.15 | |
| 1.488 | 1.2289 | 0.9472 | |
| 0.5831 | 0.6596 | 0.6712 |
| Relay Location | Left (1.2 m, 0) | Middle (1.8 m, 0) | Right (2.4 m, 0) |
|---|---|---|---|
| 0.441 | 0.4459 | 0.4535 | |
| 0.0123 | 0.0104 | 0.0076 | |
| 0.4382 | 0.4359 | 0.4302 | |
| 0.0135 | 0.0146 | 0.0173 | |
| 0.4763 | 0.4155 | 0.3063 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Su, Y.; Han, G.; Fu, X.; Xu, N.; Jin, Z. The Physical Layer Security Experiments of Cooperative Communication System with Different Relay Behaviors. Sensors 2017, 17, 781. https://doi.org/10.3390/s17040781
Su Y, Han G, Fu X, Xu N, Jin Z. The Physical Layer Security Experiments of Cooperative Communication System with Different Relay Behaviors. Sensors. 2017; 17(4):781. https://doi.org/10.3390/s17040781
Chicago/Turabian StyleSu, Yishan, Guangyao Han, Xiaomei Fu, Naishen Xu, and Zhigang Jin. 2017. "The Physical Layer Security Experiments of Cooperative Communication System with Different Relay Behaviors" Sensors 17, no. 4: 781. https://doi.org/10.3390/s17040781
APA StyleSu, Y., Han, G., Fu, X., Xu, N., & Jin, Z. (2017). The Physical Layer Security Experiments of Cooperative Communication System with Different Relay Behaviors. Sensors, 17(4), 781. https://doi.org/10.3390/s17040781







