1. Introduction
A recent advancement in communication technology, Wireless Sensor Networks (WSNs) are widely used in several applications [
1]. The science community has focused on the security of WSNs. Because of the resource-constrained environment of the WSNs, classic security mechanisms are not practical since they consume too much energy; hence researchers are proposing new lightweight security mechanisms for every possible security aspect of WSNs. WSNs consist of many small, low-cost, self-governing ends called sensor nodes with little ability to manipulate data [
2] and with constrained computing, energy, and memory. MICA2 Motes use 8 bit, 16 MHz processors with 4 K bytes of electronically erasable programmable read only memory (EEPROM) and 128 K bytes of programmable memory [
3]. With the passage of time, the sizes of WSN are growing in clusters [
4]. Traditional security mechanisms using public key cryptography cause significant overhead regarding computation and communication. Key management is mandatory and more challenging with limited resources in WSNs [
5]. Many researchers have been recognized that grouped or dispersed heterogeneous sensor systems can sensibly perform with system effectiveness, operational execution, and enduring system lifetimes.
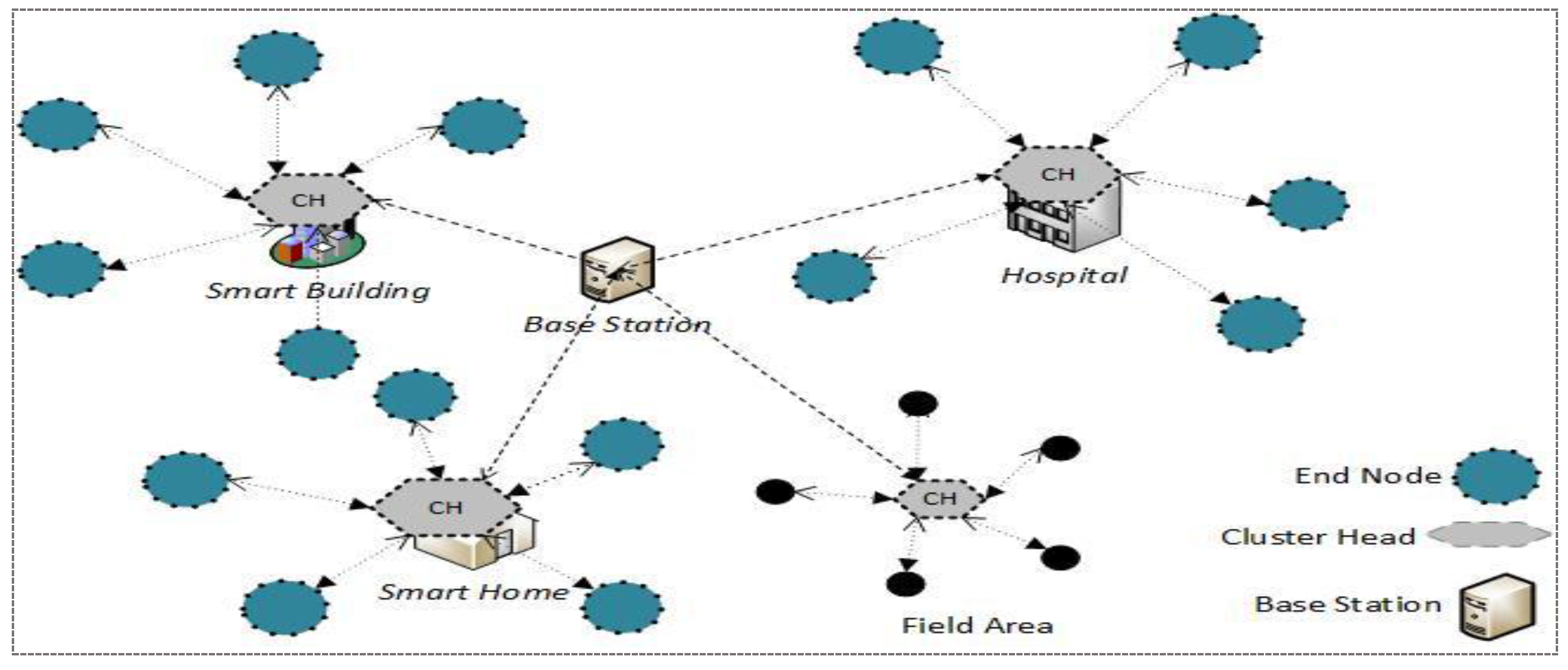
In a heterogeneously grouped approach, as described in
Figure 1, the low end sensor (
L-sensors) are resource-constrained devices with low power, short communication range, limited memory, and less computation power. On the other hand,
H-sensors are equipped with tamper resistance and have enough resources, like high battery power, broad communication ranges, sufficient memory, and high computational capabilities.
L-sensors are deliberately conveyed in a group, and every group is controlled by a group head (
H-sensor). The
L-sensors essentially sense environmental statistics and forward it to the
H-sensors and the other way around.
H-sensors can perform complex operations on the sensor information, and utilize longer radio and straightforwardly transfer it to the base-station. The base-station (BS) is a powerful hub, and it has abundant sources. The BS might be a remote server, and it might be connected with the external world utilizing the accelerated Internet.
Various anonymous security protocols have been recommended for heterogeneous WSNs in recent past, and they display diverse sorts as well as levels of security protection at various cost. In this section, we discuss the existing cryptography techniques that addressed the issue of authentication in heterogeneous WSNs. Due to the limited resources of WSNs, a sound balance between security level and the associated energy utilization overhead is needed to mitigate the security threats. Symmetric parameters such as node ID, message authentication code, nonce number, and time stamps are the significant parameters for grouped key management techniques which are energy efficient and avoid the different type of attacks from malicious nodes and avoid node compromising attacks. Most security protocols developed for WSNs use symmetric encryption, due to ease of its implementation [
6]. Besides this, single node authentication has become unable to meet the increasing communication demand, as the service demand increases with the passage time, multiparty computing is necessary for node authentication simultaneously and securely inter-cluster and intra-cluster where [
7] participants collectively to set up a mutual session key to enable the multi-party computing and secure exchange of messages.
Multi-party computing for security credential calculations has been adopted using many-to-many nodes communication scenarios. Conventional node authentication involves computation at single sensor node for the entire security credential calculation, which is less secure as compared to trustworthy multi-party involvement. These days, a new form of authentication, known as group authentication [
8] is proposed which may be used to decide whether or not all users belong to the same group or now not. The group authentication is very green for the reason that it can authenticate all members at one time. It can be used for pre-processing of node authentication to identify trustworthy contributors and non-contributors as well.
To communicate securely with the same group and among different groups, we employed a polynomial
to achieve efficient intra-group key refreshment and generated a polynomial to create an inter-group key. For this reason, our proposed protocol could be highly effective in each authentication and key establishment because it may provide the most effective broadcast transmission. Moreover, for computations every sensor needs a polynomial assessment and key-hash feature and it is easier for performing encryption and decryption. In [
9] a technique to optimize the energy consumption for computing polynomial expressions was proposed. In this context, it is, therefore, crucial to have efficient key revocation and renewal mechanisms in WSNs. The goal of this work is to propose secure and efficient protocols for key revocation and renewal.
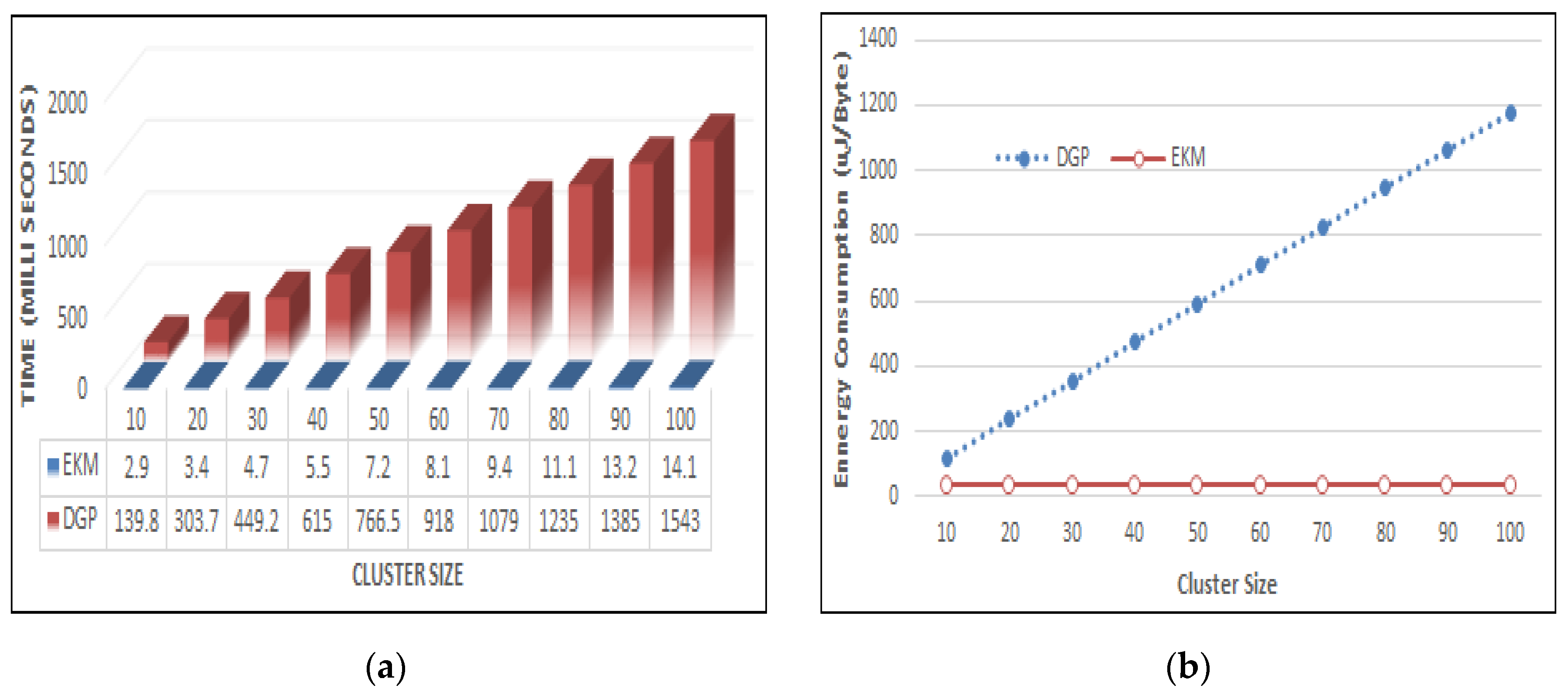
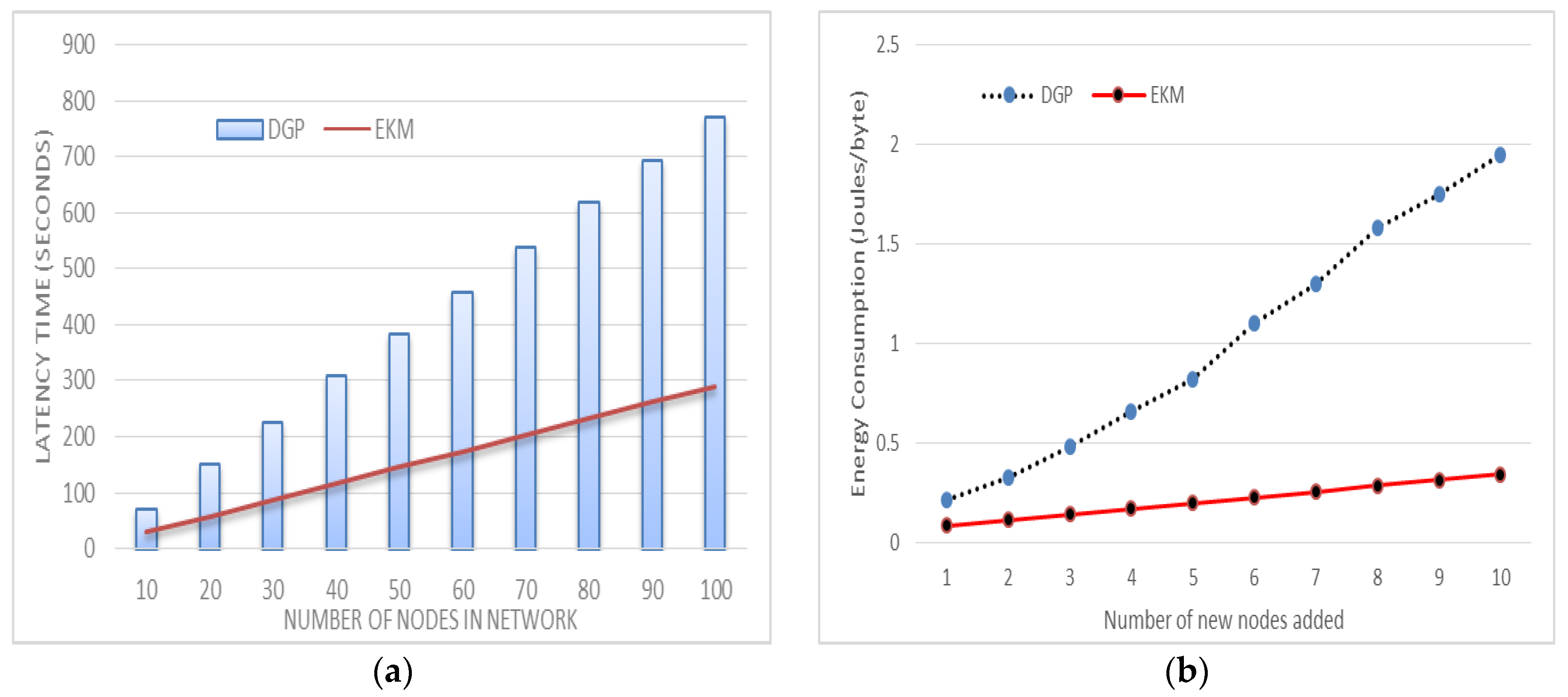
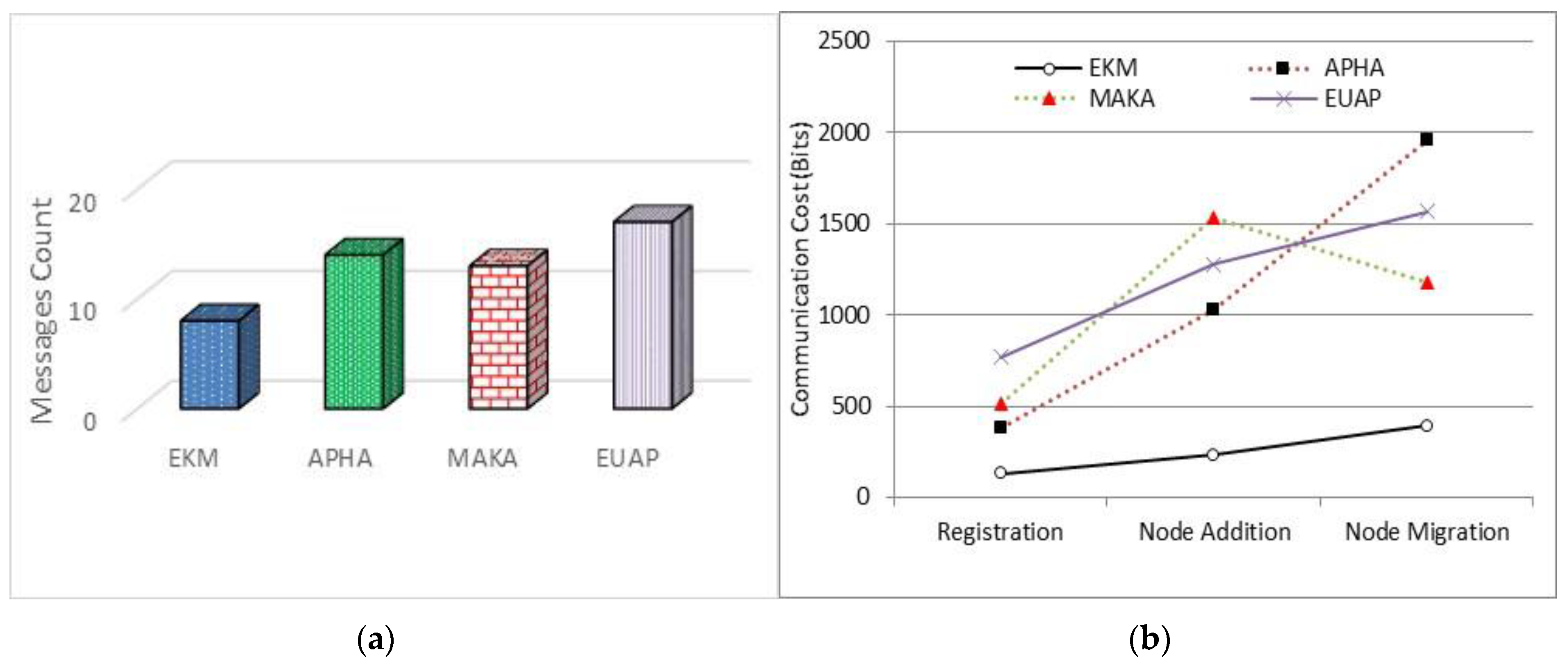
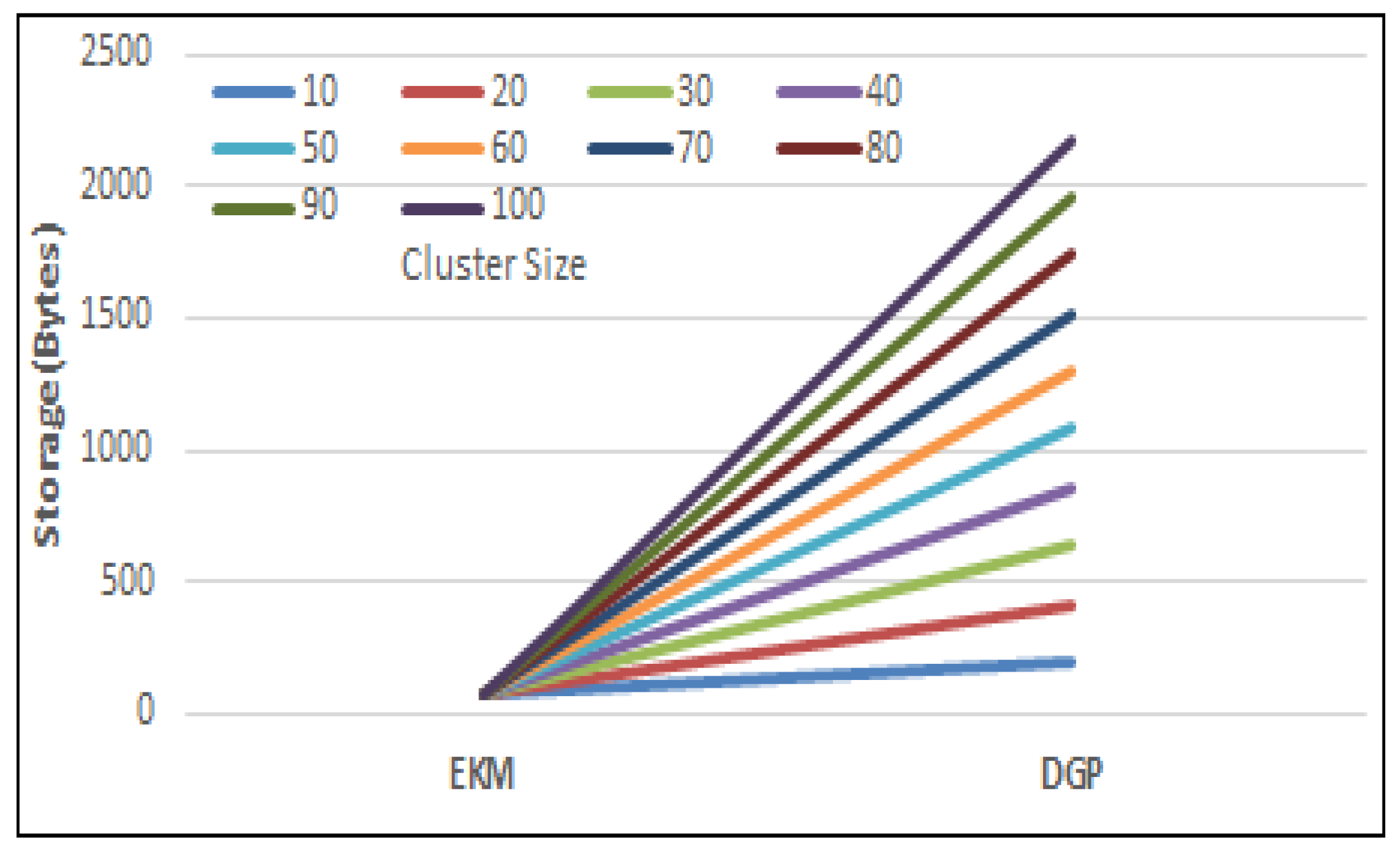
This research proposes an Efficient Keying for Multi-party (EKM) scheme to calculate the polynomial values using lightweight XOR operations. It also includes pre-deployment, node joining, and key establishment protocols. Before the nodes’ deployment in WSNs, each sensor node is pre-configured with a set of symmetric keys shared with all the other sensor nodes of the network to transmit IDs securely. After the network deployment, every sensor node identifies the specified symmetric keys used to communicate with the cluster head (CH). The cluster-head maintains all the symmetric keys shared with the sensor nodes belonging to its cluster. The main reason the use of these symmetric keys is to facilitate the multi-hop communication while transmitting secret data, particularly, the personal-proportion distribution and the exchanged facts among the cluster-heads and the base station (BS). The implementation of the polynomial that is applied for deriving an intra-group key can reduce the session key storage overhead at the member nodes and their CH. After the intra-group key is acquired, the member nodes self-generate the polynomial functions, which are necessary for growing an inter-organization key. This facilitates the reduction of the communication overhead on the CH. We have proposed a key generation and update mechanism for secure data sharing in identical clusters and among different cluster. In the session key generation mechanism for intra-clusters, the proposed technique significantly decreases the number of broadcast messages in the inter-cluster communication. The extra number of re-keying messages and communication overheads due to the proposed scheme has been conscientiously justified. Through the usage of the proposed mechanism, we have enhanced the WSN efficiency and network lifetime by reducing the number of exchanged messages to enhance the network lifetime during node mobility while reducing the coverage area of cluster heads and the need to migrate nodes to join the powerful coverage area of the CH. This research proposes a secure node migration protocol in which reliable handoff occurs and new connections are established between CHs and member nodes.
The organization of the rest of the paper is as follows: the system and security model for proposed protocol established in
Section 2.
Section 3 elaborates the related work to develop existing key establishment schemes.
Section 4 provides a detailed discussion on a proposed EKM system for key distribution, node joining, and key establishment scenarios. The formal specification and security analysis of proposed technique is discussed in
Section 5.
Section 6 are about simulation parameters and scenarios to present results and illustrate the analytical discussion. Finally,
Section 7 provides conclusions and future work.
2. System and Security Model
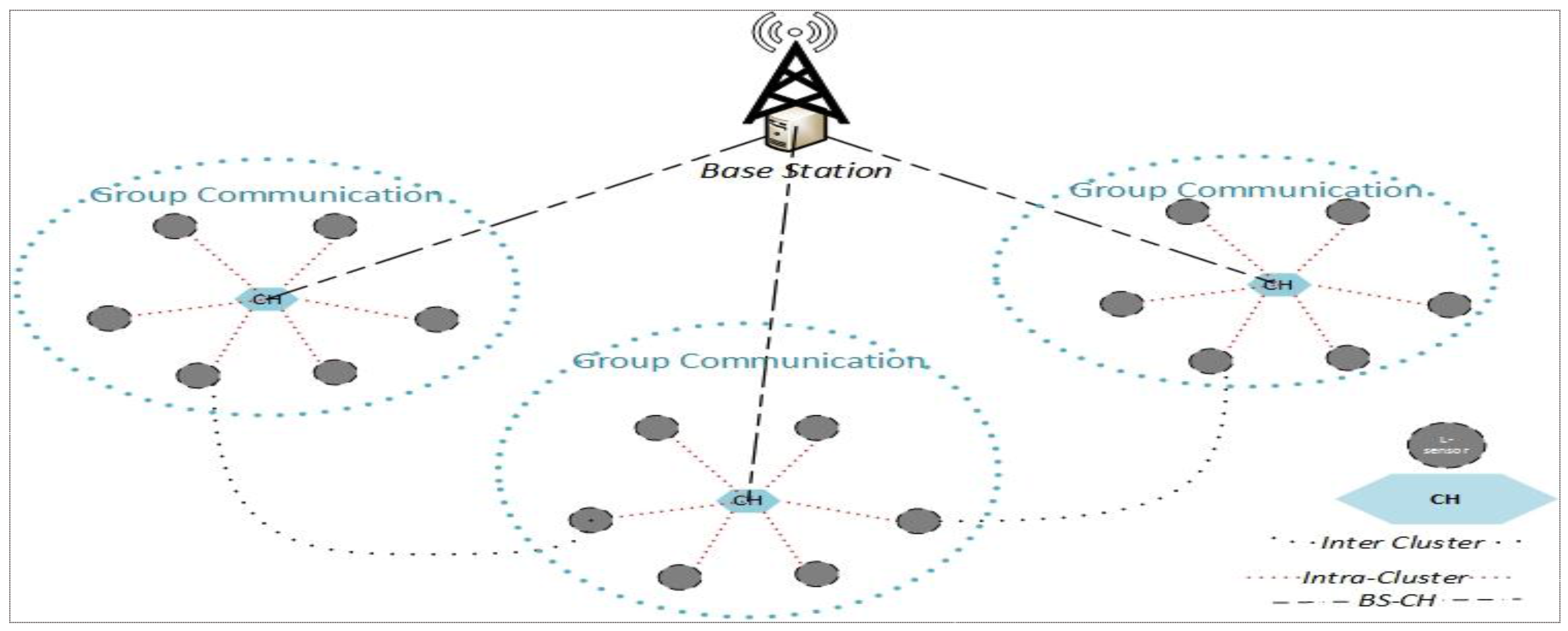
In this section, the network model, adversarial model, and security model are described, respectively. For multicast communications in WSNs, the network model used here is the heterogeneous and hierarchical topology depicted in
Figure 2. We assume that the network consists of a sink and many groups, and each group has a powerful node which has abundant resources (energy, computing, and storage) and many low ordinary nodes. The powerful node acts as the cluster head (
CH) and is responsible for network security management, such as key issuing, updating, revocation, intrusion detection, etc. As an ordinary member,
L-sensor is responsible for sensing data and authentication for secure communications.
When we consider that WSN may additionally encounter attacks from inside by compromised nodes or external attackers, so its lifetime can be classified into many phases. At the beginning of every session, all types of keys like BS-CH, CH-L-Sensor, and L-Sensor-L-Sensor for security functions will be re-issued. The length of every session could be modified dynamically with the security strength of the safety mechanism used or the regulations of group members like new node addition and migration. Session switching might be launched using cluster heads for group members and by the BS for cluster heads. The self-restoration key control schemes proposed in particular focus on the problems, updating and revocation manner of organization keys and pairwise session keys. Different styles of keys methods may be originated according to the devices for group keys and pairwise keys.
2.1. Threat Model
In this section, we describe the threat model adopted in the proposed scenario. We assume that there aren’t any compromised nodes at network deployment time. Attacks are released a while after the nodes are deployed. With effective computing capability, the adversary can execute advanced fact evaluation to gather the important data. The adversary can be either inner or external and active or passive. Moreover, a single entity or a member of a coordinated group of entities can also perform malicious activities. An adversary can launch a physical attack by compromising a node and reading secret data to use it for future tracking. An insider adversary is a malicious node that may examine/alter all messages encrypted with its keys. Passive adversaries can spy on all communication channels in the community like idea channels, or unintended verbal exchange channels. Energetic adversaries can examine, tamper, and inject fraudulent packets over verbal exchange channels.
2.1.1. Adversarial Model
Moreover, insider attackers and outside attackers can apportion the important thing, captured information, to interrupt the security collusively, in what is referred to as a collusive physical attack. For instance, the revoked nodes and the newly joined nodes can launch deceitful attacks on the session keys no longer belonging to them. We expect that the compromised or insider adversary behaving abnormally could be revoked from the network inside the following session with the assist of the intrusion detection mechanism, which is not addressed in this research.
Moreover, a comprehensive attacker can easily monitor the wireless data of WSNs and capture the wireless packets. The attacker will be able to gather plenty of useful sensor information from the captured packets like node IDs and node location and might adjust packet information even as a packet is in transit. Additionally important, an attacker can intentionally apprehend a node and capture all its cryptographic keys. As a result, node capturing physical attacks are very harmful to the network if excessive numbers of cryptographic keys remain stored on a node.
2.1.2. Potential Attacks
In general, attacks affecting secure key establishment are eavesdropping and node capture [
10], referred to as passive adversaries and active adversaries. Passive adversaries gather some statistics via eavesdropping without any physical access to a network entry, and active adversaries encrypt information that is leaked during physical access to the node. The proposed key management technique is secure against eavesdropping and node capture, and we will explain the cause for this below. During cluster key derivation, the cluster head sends an expanded polynomial without any encryption. It is not easy to guess the intra-group key management from the polynomial, considering that it is hard to do polynomial factorization due to the fact there may be certainly a
) options to the polynomial enlargement problem [
11,
12] and the problem for polynomial factorization is NP-hard [
13]. For example,
is not easy to factorize as
for the purpose, it’s tough to guess 3. Even though the accelerated polynomial
is sent without any encryption, cluster head key credentials will no longer leak out. For this reason, it’s far tougher to generate the coefficient of polynomial
with the aid of an attacker due to the safety of these keys in clusters.
2.2. System Model
Based on the system and attack model, we particularly grasp the subsequent security goals: for the reason that
L-sensors aren’t truthful, initializing essential keys allows powerful security. To preserve the mutual authentication among the network devices (sensors, cluster-heads, and base-stations), devices have to perform mutual authentication and establish a dynamic session key before establishing the consultation, so that each the nodes/gadgets can confirm their legitimacy. In vital applications (place of birth security, healthcare, smart grids), nodes’ identities are very critical, as a consequence, nodes’ identities should be stored securely and privately [
14,
15,
16]. To protect the Wi-Fi communication from unlawful eavesdropping and interception all the wireless messages should be secured (i.e., personal), so that a global adversary can’t examine, reveal, intercept, or modify the Wi-Fi messages. During an adversary monitoring, the
L-sensors are easily compromised, so then a key revocation mechanism can play a vital function to protect from any future misleading moves from a compromised node. Moreover, a node addition feature confers scalability to the network.
The proposed model for our key distribution scheme is designed for heterogeneous sensor networks. We assume a heterogeneous sensor network consists of high resource node (
H-sensors) and their member nodes having fewer resources called
L-sensors.
H-sensors are nodes that are more powerful and have more computation, communication, energy supply and storage capability’s sensors are ordinary sensor nodes with limited computation, communication, and energy supply and storage capability. We consider the hierarchical structure of the heterogeneous sensor network proposed in [
17] in which high power sensor nodes work as cluster heads and low power sensor nodes work as their member nodes. This sensor clustering scheme enables local data processing, which reduces the communication load in the network to provide scalable solutions. To increase the lifetime of the deployed network the nodes are divided according to their workload. Initially, when a sensor network is deployed, there are large number of low power sensor nodes and a limited quantity of cluster heads. It is assumed that the
H-sensor and
L-sensors are deployed uniformly and randomly. It has been assumed that the
CH is tamper resistant and cannot be compromised. The major issue with the polynomial calculation is that resulting multiplicative values become very large and slow for larger values of polynomial factors. Due to constrained resources, when the number of
L-sensors increases then the computation and communication cost to the cluster head also increases. The more
L-sensors there are, the more memory required on the cluster head for restoring their IDs and multiplicative values, which causes memory overhead.
3. Related Work
Different issues with existing key management techniques are discussed in conjunction with the availability of limited recourses of WSNs. Minimizing the resource consumption and maximizing security levels are two different points. The probabilistic scheme described in [
18], where each node receives a group of keys smaller than the network size provides better connectivity and little memory overhead. It has key pre-distribution, path-key establishment, and shared key discovery phases that cause scalability problems. The larger network size for a given stage increases the computation and communication overheads. The secret key sharing is limited by the memory existing on the sensor nodes, since the chance that next node shares k/n give a
key, for example, the memory overhead is
O(
n)
. For fixed key chain size, the key connectivity achieved is lower than previously.
In [
19] a dynamic generation of the polynomial (DGP) is proposed for heterogeneous WSNs scheme where nodes are pre-loaded with a master key
K for secure communication during cluster key establishment. During the key management process, each node calculates
MAC(
ID) and then encrypts the concatenated message with the master key. Each
L-sensor node (
Li) generates ciphertext
C_Li = EMK(
ID||MAC(
ID)) and transmits it towards a
H-sensor as depicted in
Figure 3. The
H-sensor calculates the hash of
L-sensor
IDs and saves these values.
H-Sensor generates a polynomial using Equation (1) where
h(
Li) is hashed function for
L-sensor
Li and
i = 1, …,
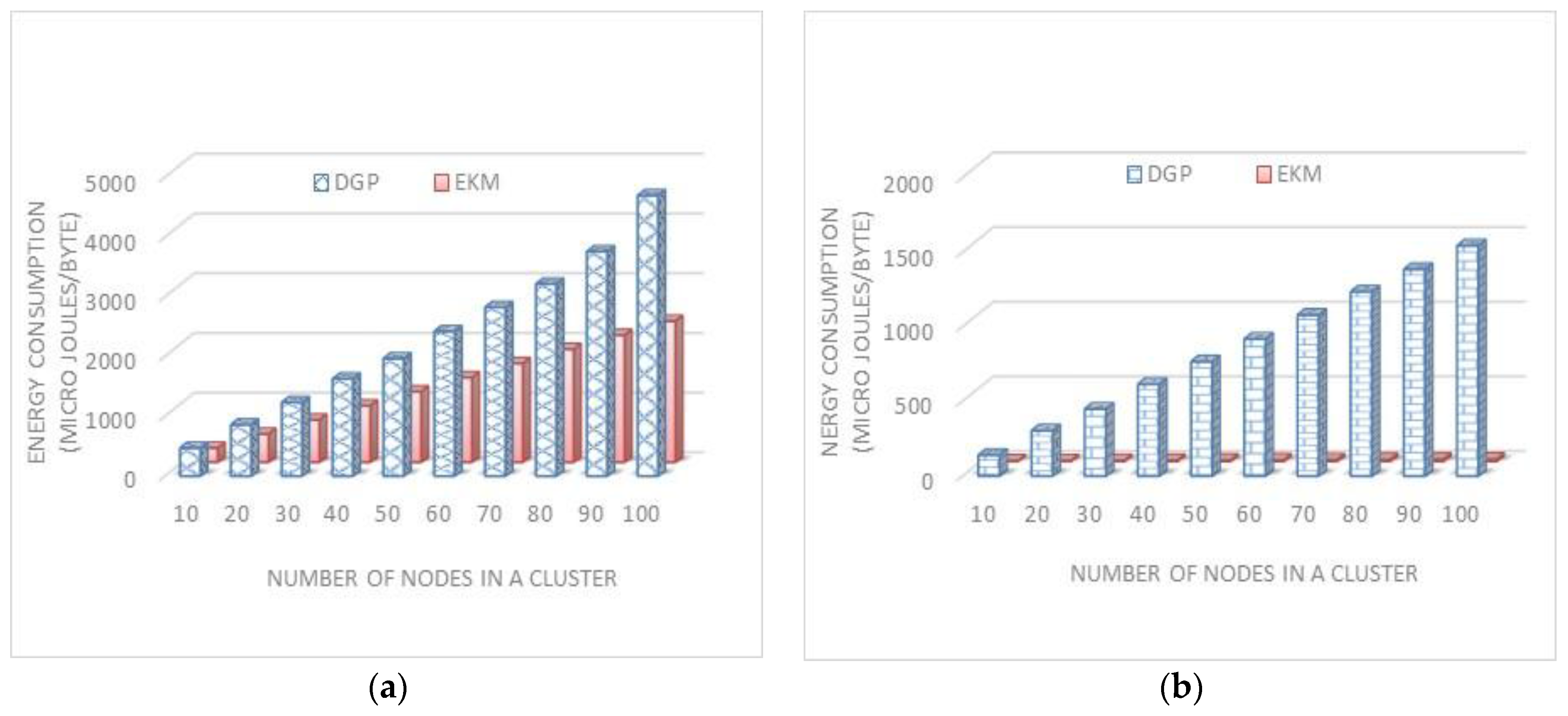
n.During a node joins or leave operation, H-Sensor revokes existing polynomial and broadcast the new polynomial to all L-Sensors by taking MAC(ID) of all L-sensors. It increases the lifetime of sensor networks by decreasing the key pool size. Our scheme further reduces the computational cost of this scheme.
In [
20] where each node receives a unique ID, a private key, and a master key
K. After deployment, sensor nodes broadcast their IDs encrypted with the global key. A loop is constructed by using a certain number of a node from set
S. If sensor node
A creates loop
L with set
S, then loop-key
is computed. The global key protects the distribution of the loop key inside the loop. A network-wide key can reduce communication, but capturing a single node exposes all the links in the network. Our approach prevents it from taking the credentials from member nodes.
In [
21] every sensor node randomly picks up a unique secret key from the large key pool and produces a new secret key by applying one-way hash function. The
H-sensor broadcasts a message in its communication range and then, the
L-sensors discover their neighbors. It provides complete connectivity, resilience against sensor node capture and routing attack. Our scheme follows the same deployment pattern. Sajid recommended following a sequence of Key Pool → Key Chain→ Key Ring [
22]. It achieves an equal probability of key sharing among nodes and stores a small number of key generations on the node. It reduces the memory overhead if the wrong parameter is fixed, but for maximum key sharing, it needs a larger pool size.
In [
23] a secure symmetric key used for member nodes and public key cryptography for powerful nodes was proposed. Three scenario-based schemes reduce the memory and computational overhead along with high resilience against node capture attacks. A key management regime described in [
24] used a keyed hash chain. It supports the establishment and renewal of five keys, and it also overcomes the drawback of a single key. A critical decision is to how determine the length of a key-chain. A large key-chain size increases the memory overhead and on the other hand, decreasing the chain size compromises the security strength.
A random key pre-distribution scheme where seeds are taken from the base station to drive a new key that is providing adequate security was described in [
17]. It allows privately distributing a secret to a set of recipients with only one multicast communication [
25]. A lightweight
XOR-based re-keying scheme is illustrated in [
26] that does not require message exchange from common nodes. In this system,
CH transmits a Magic code and a nonce number in the encrypted message to all member nodes. Sensors take
XOR of an existing key with a left shifted Magic word and get a new value that is further used to establish
XOR with the nonce. Similarly, our scheme also supports key freshness on each node join or leave operation. A technique put forth in [
27] enforces mutual authentication between a member and group key distributor while executing a re-keying process.
During the last decades, various applications have been benefitting from WSNs, such as environmental monitoring, battlefield intelligence, and reconnaissance, medical caring, intelligent home, industrial control [
28]. However, in some harsh and critical environments, malicious attacks, including eavesdropping, Denial of Service (DOS) attacks, and packet tampering and infection, may disturb the network operations and degrade the system performance. Security issues should be considered carefully during the design of WSNs’ protocols to defend against and tolerate attacks [
29]. Cryptography is typically used to provide security features, such as confidentiality, authentication, integrity, and availability [
30]. As the core role of security, key management is responsible for key distribution, updating, and revocation for sensor nodes, and establishes security associations between nodes [
31]. As per scientific techniques, some related works explore polynomial [
32,
33] vector space secret sharing [
34], bilinear pairings [
35] and elliptic curve cryptography [
36]. Polynomials can be used to improve the trade-off between security performances, computation complexity, and resource consumption better than other methods [
37]. In this paper we concentrate on a polynomial-based strategy to achieve better system performance.
References [
38,
39] elaborate that radio-frequency identification (RFID) is a program distinguishing proven innovation and a promising innovation to be naturally incorporated into conventional remote sensor systems (WSNs) including a novel recognizable proof measurement into WSNs and forming RFID-based sensor frameworks. The lightweight protocol provides the security properties because basic logarithmic and intelligent operations without requiring costly cryptographic calculations are implemented in low-cost and resource-restricted wireless systems.
The scheme in [
40] enforces mutual authentication between a member and the group key distributor while executing the rekeying process. It provides forward secrecy and backward secrecy properties, and resists replay attacks, impersonation attacks, group key disclosure attacks and malicious insider attacks. The proposed scheme can be used for rekeying purposes in a secure multicast scenario. The second one is an authentication mechanism to be used in environments in which a public-key infrastructure is not available. Forceful characteristics such as changing the key of a user in a chain of command influences the performance of an admittance organize scheme more than other dynamic properties such as adding or deleting a security class to the hierarchy [
41]. To overcome forgery attacks, the authors focuses on the security of the data provenance specific to a wireless sensor network. The paper provides a scheme to detect forgeries in provenance data, detection of packet drop attacks and also identifies the attacker of packet drop attacks [
42]. This scheme used a packet bloom filter data structure for encoding provenance data. Hash functions are used to encode the provenance data in packet bloom filter. The use of a bloom filter data structure results in a lightweight scheme which is suitable for wireless sensor networks. Each packet consists of the sequence id of the packet, actual sensor data, and an n-bit bloom filter vector. To detect a forgery attack, the ID of the each node in the path is encoded into the bloom filter vector. It is assumed that base station knows the path of the received packet. When a packet is reached at the base station in the WSN, a fresh bloom filter is taken and encoded with all nodes in the path. If the generated bloom filter and bloom filter extracted from the received packet are the same, then there is no forgery attack, and otherwise there is a forgery attack. Actual sensor data is also secured along with provenance data with the scheme proposed in this paper. Experimental results proved the effectiveness and the lightweight nature of the scheme.
4. Efficient Keying for Multi-Party Scheme (EKM)
In this phase, mutual authentication and session key establishment takes place between the participants. During cluster key establishment, an
H-sensor or cluster head (
CH) receives encrypted IDs of
L-sensors from neighboring nodes.
CH decrypts these IDs using the pre-distributed master key K. After receiving the IDs, a hash of these IDs is calculated and stored in memory as illustrated in
Figure 3.
CH selects random IDs from the stored hash list to compute the polynomial. Finally, the polynomial is concatenated with its MAC and encrypted using a master key to transmit towards all neighboring nodes. In our scheme, we considered the hierarchical structure of [
20] for the deployment. It has been assumed that the
H-sensor and
L-sensors are deployed uniformly. It is also presumed that the
CH is tamper resistant and cannot be compromised. A list of the notations for EKM is provided in
Table 1.
Every common node has been preloaded with a hash function, master key, encryption and decryption functions along with a unique ID by the sink. The
CH is also pre-loaded with similar credentials along with a polynomial calculation function. The
CH and sink server have secure authentication mechanisms, including
ECC which is hard to reverse. The
CH forwards this request after making it secure to s sink that verifies the request and responds to the
CH granting or denying this request.
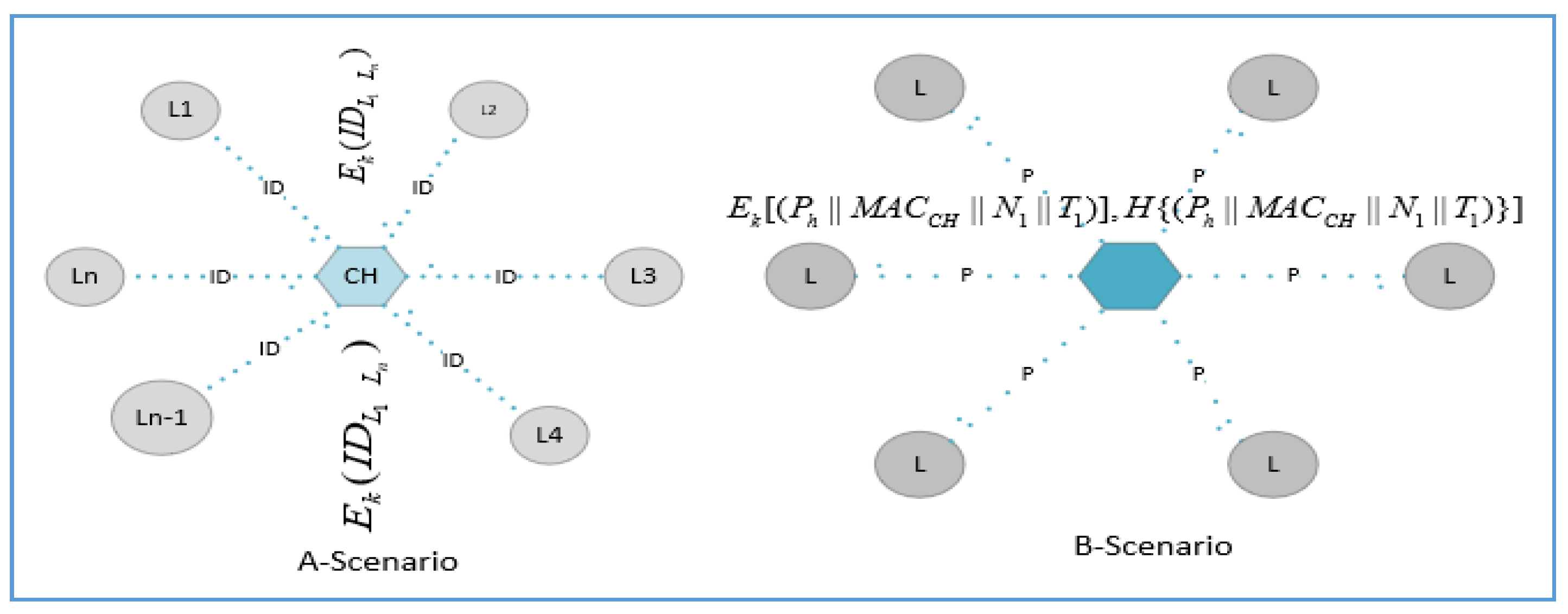
Figure 4 shows that the
CH receives an encrypted message
EKM(
IDLi||MAC(
IDLi)) containing the ID of
Li and
MAC(
IDLi). The
CH selects the random IDs and hashing to calculate a polynomial using Equation (3). Finally, the
CH transmits the encrypted message
EKM(
Ph||MAC (
Ph)) to the
L-sensors.
Initially, the polynomial is calculated by using Equation (2) where x is a pre-defined significant value, and the hashes h are calculated for all member node identities from to where be the cluster size. We further reduced the computation overhead by taking XOR of a randomly selected number of hash values instead of taking the XOR of all values. The CH generates the hashes of all IDs received from neighboring L-sensors using the initialize procedure.
After the hashing calculation, the
CH makes a polynomial
Ph by taking
XOR of randomly chosen
R hash values as shown in Equation (3), where
a,
b and
c are indices of randomly selected node IDs for
R =
3:
Moreover, the algorithmic steps of Equation (3) are illustrated in
Figure 5. We recommend using
R = 3, i.e., randomly taking three hash values and using
XOR to generate the polynomial. It is enough to create confusion for the attacker in the selection of
IDs out of
NIDs.
4.1. Addition of New Node
After deployment of WSN, the addition of a new sensor node in the cluster may also occur. For new node addition, the base station plays a vital role in the authentication process and performs the setup phase. Into the network setup model phase, the
BS introduces the new sensor to the
CH. The sensor node is pre-loaded with the master key (
K), a one-way hash function
h(
x) and a randomly selected node id
. After that, Bthe S broadcasts an encrypted message containing
,
(list of
L-sensor IDs) and
to all cluster head nodes as illustrated in Protocol-1.
CH replies with an encrypted message containing
and
. The cluster head multicasts the session key, list of member nodes and MAC in encrypted form. This ensures the originality and reliability of the node joining process. The new node addition protocol and flow diagram are depicted in
Figure 6 and
Figure 7, respectively, where before new node addition
CH get an authentication from the BS. After successful authentication,
CH runs Protocol-2 for verification using secret credentials.
The new
L-sensor is deployed randomly in the sensor network area. The new
L-sensor encrypts its id and
through its pre-loaded master key
KM. The cluster head, which already has a list of new sensors, verifies it by comparing the received
MAC with its list. After verification, it replies with polynomials
encrypted using
KM. The new
L-senor decrypts the message and gets a polynomial to calculate a cluster key
between
CH and
. Finally,
CH informs all members to add
in member list as illustrated in Protocol 2. If a new node is a malicious node, then the
CH sends an adversary identification message to the base station. After the deployment in a heterogeneous network, new nodes are placed in such a position where they can communicate directly with the cluster head.
Figure 6 shows the overall scenarios of Protocol-1 in steps 1 to 3 whereas Protocol-2 is in steps 4 to 7.
4.2. Migration of Node
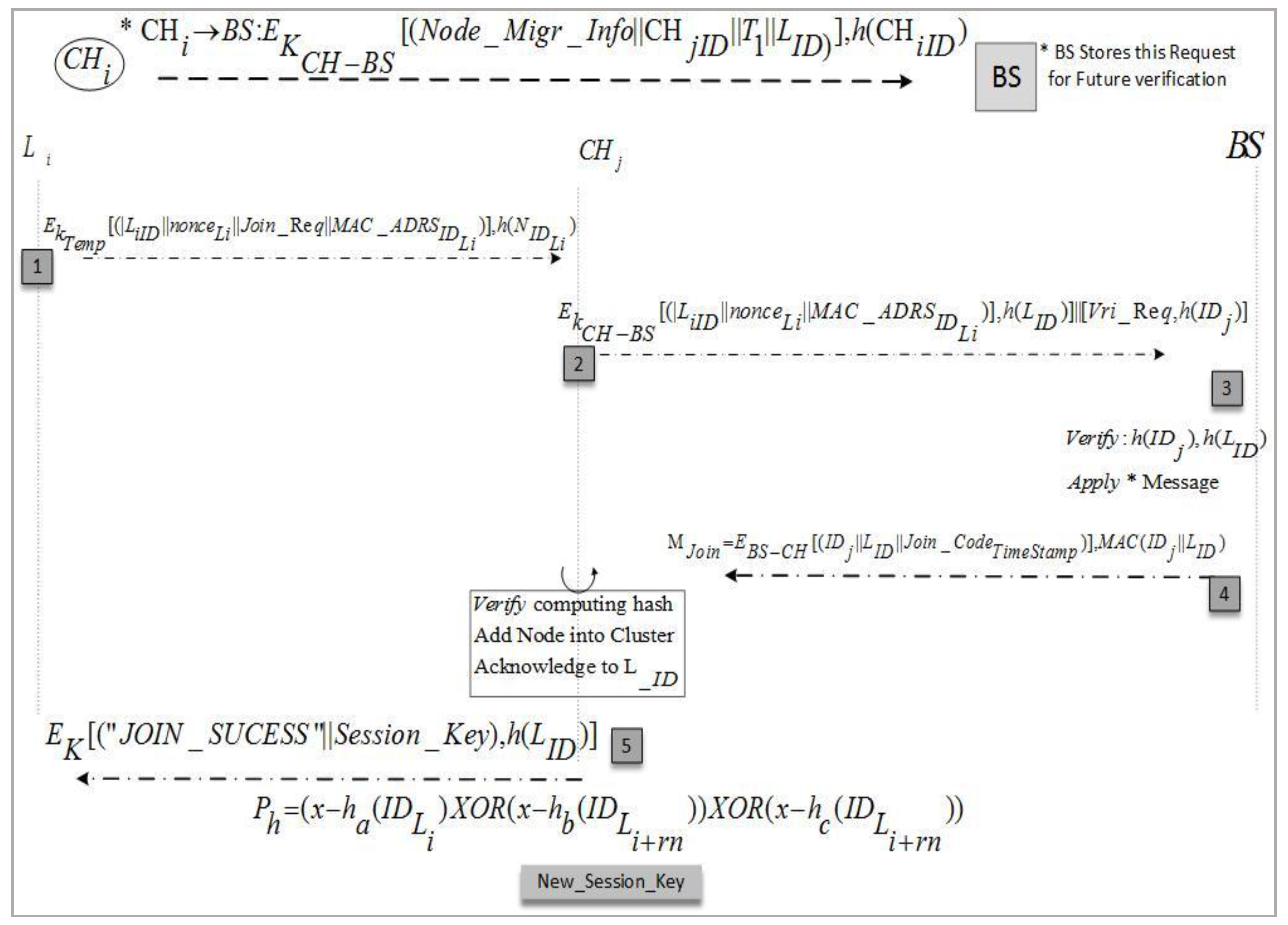
To increase the lifetime of a WSN network, we have proposed a secure node join protocol for moved nodes. The main purpose of this phase is to add displaced nodes to existing clusters by the
CH sensing range in their locality. There are instances in which a node can belong to two clusters, inducing a loss of capability in the different one, which will resolve this issue; the cluster heads that do not have a specific sensor kind in their clusters invite the missing sensor to join or suggest another
CH according to its sensing range. This achieves better security in an environment where nodes are mobile and leave/join the cluster frequently. We have maintained a binary search tree for all network nodes at the BS that is aware of each leave and join operation. Similarly, a Binary Search Tree (BST) is also maintained at the
CH to keep the node list updated and maintain a record of leaving nodes. It also keeps a list of rejected nodes which do not have security credentials as per issued by BS. This guards against intruders joining the network during migration from other networks. We have supposed that an intrusion detection system is working to identify those nodes that were trustworthy but now are performing malicious activities due to some attack. Such nodes are also added to the rejected list. Due to this record keeping, the
CH intimates in a timely way the nodes that want to send a message to a node that has left the network or been set as malicious to saves extra communication costs at low-powered nodes. During the node migration and addition scenario, the protocol in
Figure 8 is described in a stepwise manner in following section.
Figure 9 elucidates these protocol steps in a node wise interaction scenario.
| Steps 1–3 | Before node migration, CHi sends a node migration notation to BS with the valid ID of a sensor node that needs to migrate. A migrated node sends a joining request to join new cluster CHj with a pre-shared key and transmits secret credentials for the joining process. Upon receiving a migrated node joining request, the CHj get verification from the BS by sending a verification request. The BS verifies or rejects the node joining procedure by comparing said node’s identity in the block node database. |
| Steps 4–5 | After the migrated node joining request verification, the BS computes an authentication message for CHj and transmits it in encrypted form using a shared key. |
| Steps 6–7 | The CHj verifies the message credibility using secret parameters before adding the migrated node in its cluster. Carrying out verification, CHj sends a join success message to the migrated node and an acknowledgment bit to the BS |
| Steps 8–9 | Upon the migrated node successfully joining, CHj computes a fresh polynomial using Equations (2) and (3), and updates the cluster key for future communication and process aborts. |
5. EKM Formal Specification
We have carried out aspect modeling the use of Non-monotonic Cryptographic Protocol (NCP), as well referred to as Rubin logic [
43] by analyzing and verify the EKM protocol as much as possible through formal specifications. It validates the protocol as approximating through standard requirements about cryptographic operations like node authentication, message integrity, message freshness, encryption, decryption, etc. It additionally helps to become aware of any deficiencies within the proposed protocol and possibilities regarding compromise attacks. It is close to the real implementation and flow of programming functions. In Rubin logic, the entities are allocated roles and a global set is additionally maintained where data about the protocol is maintained in sets then these also keep updated states on the users after every updateable operation. Global sets are available in conformity with entire the part nodes, however, may stand labeled as secret, observer, rule and essential sets.
A local set is maintained at each entity or node and can be classified into possession POSS(), belief BEL(), seen and behavior sets BL(), the explicit specifications from [
13] of these sets investigated. By applying Rubin logic on EKM, the local set involved is in
Table 2, and then its verification and analysis part provides a detailed overview of all sets continue under the grouping of the local set. Local sets for all the participants including sender, receiver and actor nodes are independently managed. A possession set POSS (entity) holds all the constraints involved in message encryption, decryption and other procedures executed at a local RAM of each entity as described in the section below. A behavior list BL() holds the list of operations and input arguments that are performed in near to execution steps by entities
Li,
CH and BS.
The detailed analysis of the proposed scheme is presented in
Table 2 by considering all communication actors. The sensor node
authenticates itself to its cluster head by sending a join request message containing
. Upon receiving this message,
computes polynomial
and reply
in encrypted message
to
. Upon receiving
splits the received message and verifies it by getting
CH and its information for joining a group. On the other hand,
contains its own
, member node
, master key, and encryption key to communicate with
and member node
Li in its possession. In
, we believe the received messages and participant information are reliable and trustworthy. Upon receiving credentials from member nodes,
decrypts them by using the corresponding secret key and verifying the information after decrypting the ciphered text. Based on strong verification
accepts or aborts the member node join, leave and migration requests as well as communicates with the BS. The third and the most important entity of this scenario is
, which has more computation, communication, and storage power.
possess their own
,
, secret keys and a list of member nodes with their
It believes it has secure communication mechanisms for
,
and strong, secure key generation protocols. It verifies,
sensor nodes, and their authentication credentials and the validities of their identities.
EKM Analysis and Verification
In this subsection, EKM is broken down for a node migration situation as discussed in
Section 4.2. In this case, the key circulation is started by the base station that preloads the security credentials in
Li and then (
Li) transmits a message
to the cluster heads
. After receiving the message,
CHj gets the node ids of participant sensor node and calculates the shared session key. Upon the completion of the transmission operation, an update operation is performed to refresh the spectator list demonstrated as follows. Related parameters including messages, ciphers, nonce values, actual key, and hashes are saved in possession set at
Li during the key establishment phase as shown below. At the end of the migration, the forget operation removes the temporary values used in operations including
,
After receiving messages,
CHj, decrypts them to retrieve a concatenated message that is further split to get the actual parameters. The possession set at
CHj contains the following parameters during execution of the abovementioned operations. The forget operation will result in removing the temporary values including
,
nounce,
,
C,
M,
C,
,
nounce from the possession set:
The BS receives the message from
CHj and after decryption, it verifies the
Li and its security credentials. The possession set values at the BS contain temporary values as shown below. Forget operations are performed to remove the values
PBS,
C2,
C3 and
M3:
The receiver node BS verifies the credentials sent by the CHj and then returns a message containing Join-CodeT to CHj. Finally, the possession set at Li is refreshed after the completion of node migration from CHi and successful joining at the CHj.