An Optimized Hidden Node Detection Paradigm for Improving the Coverage and Network Efficiency in Wireless Multimedia Sensor Networks
Abstract
:1. Introduction
2. Related Work
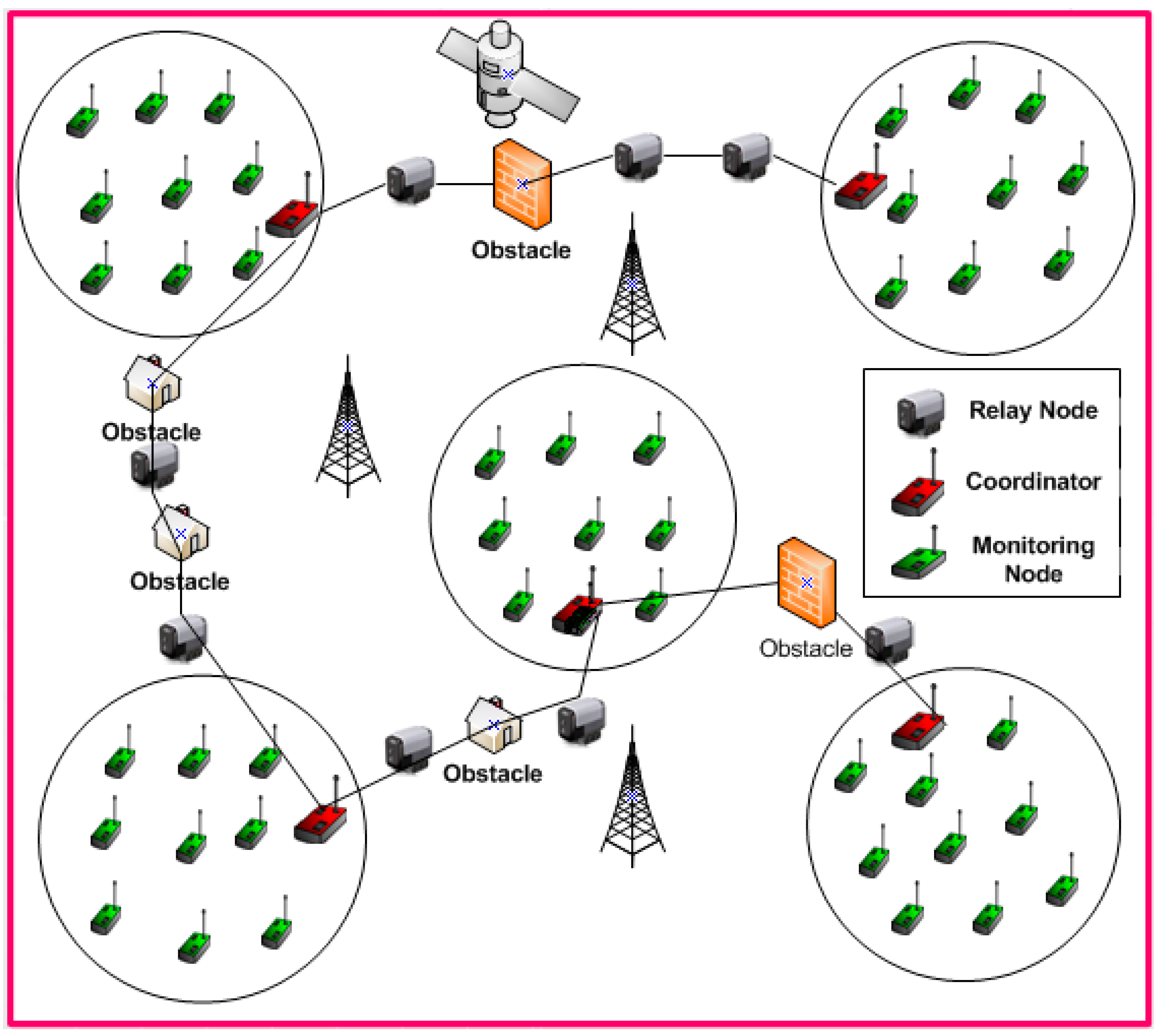
3. Obstacle-Driven Negative Effect Strategy Method
4. Optimized Hidden Node Detection Paradigm
- Hidden Node Detection
- Message Exchange Phase
- Location Detection
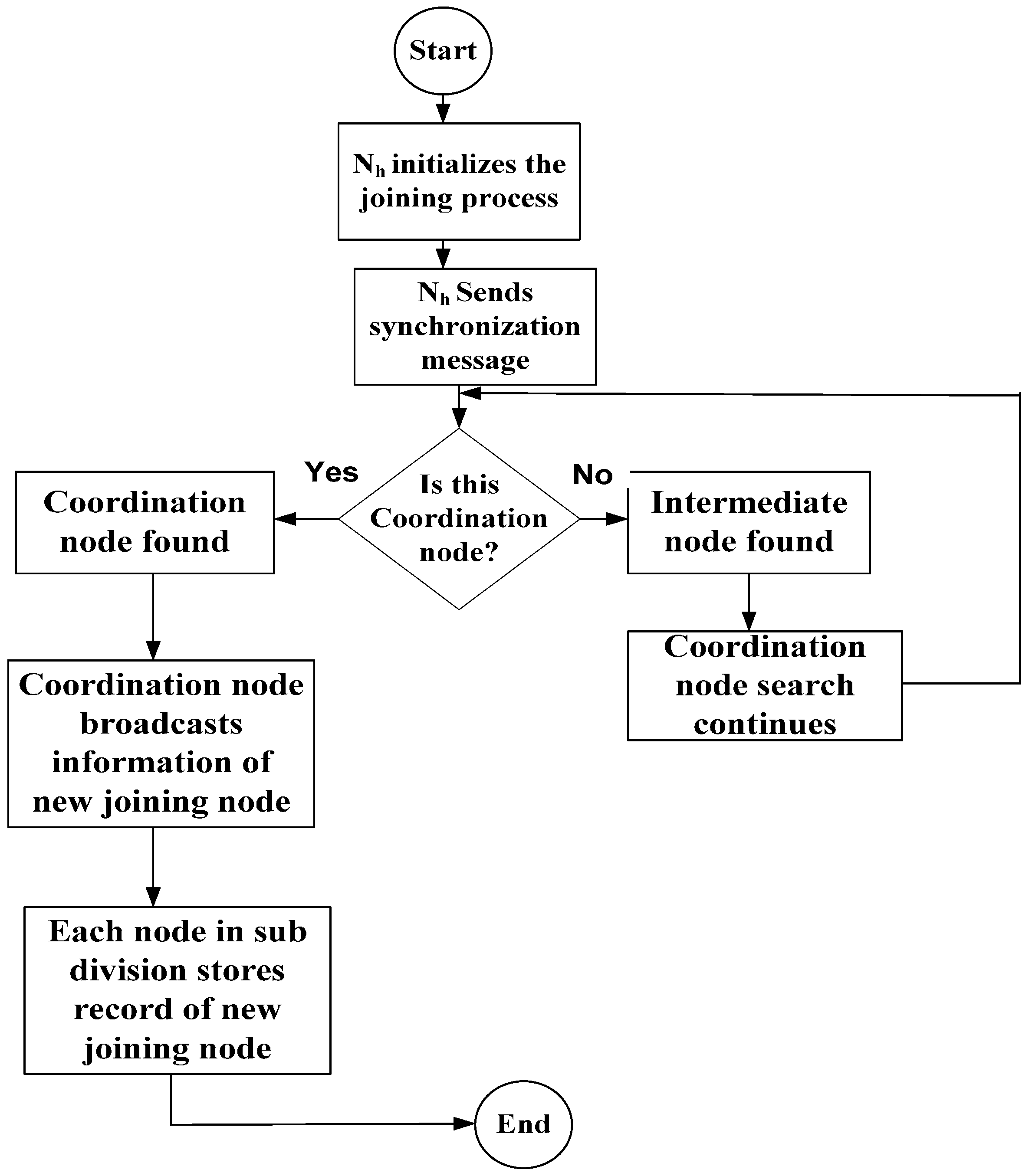
4.1. Hidden Node Detection
| Algorithm 1: Priority-based synchronization process between coordinator and newly joined nodes |
|
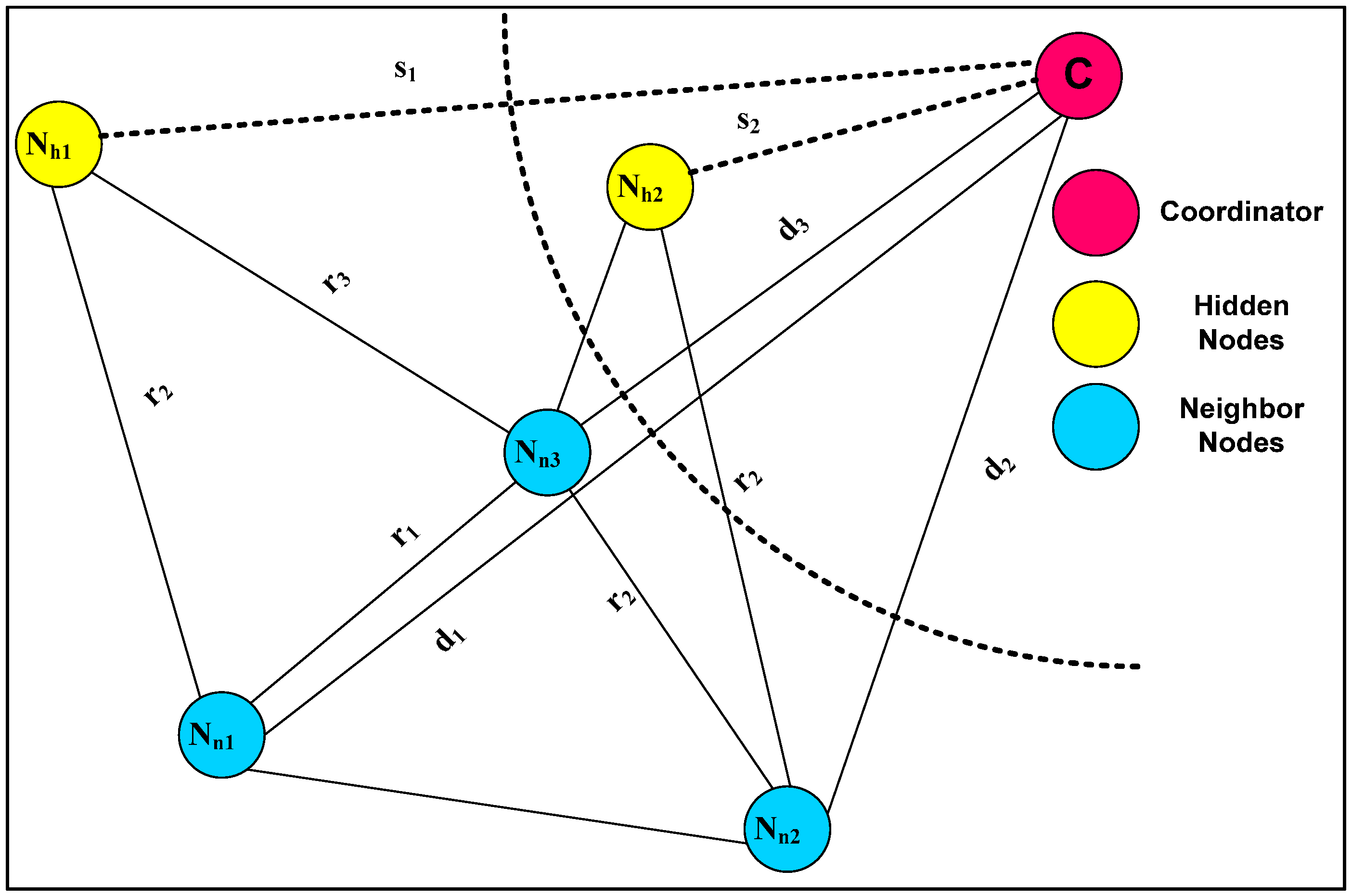
4.2. Message Exchange Phase
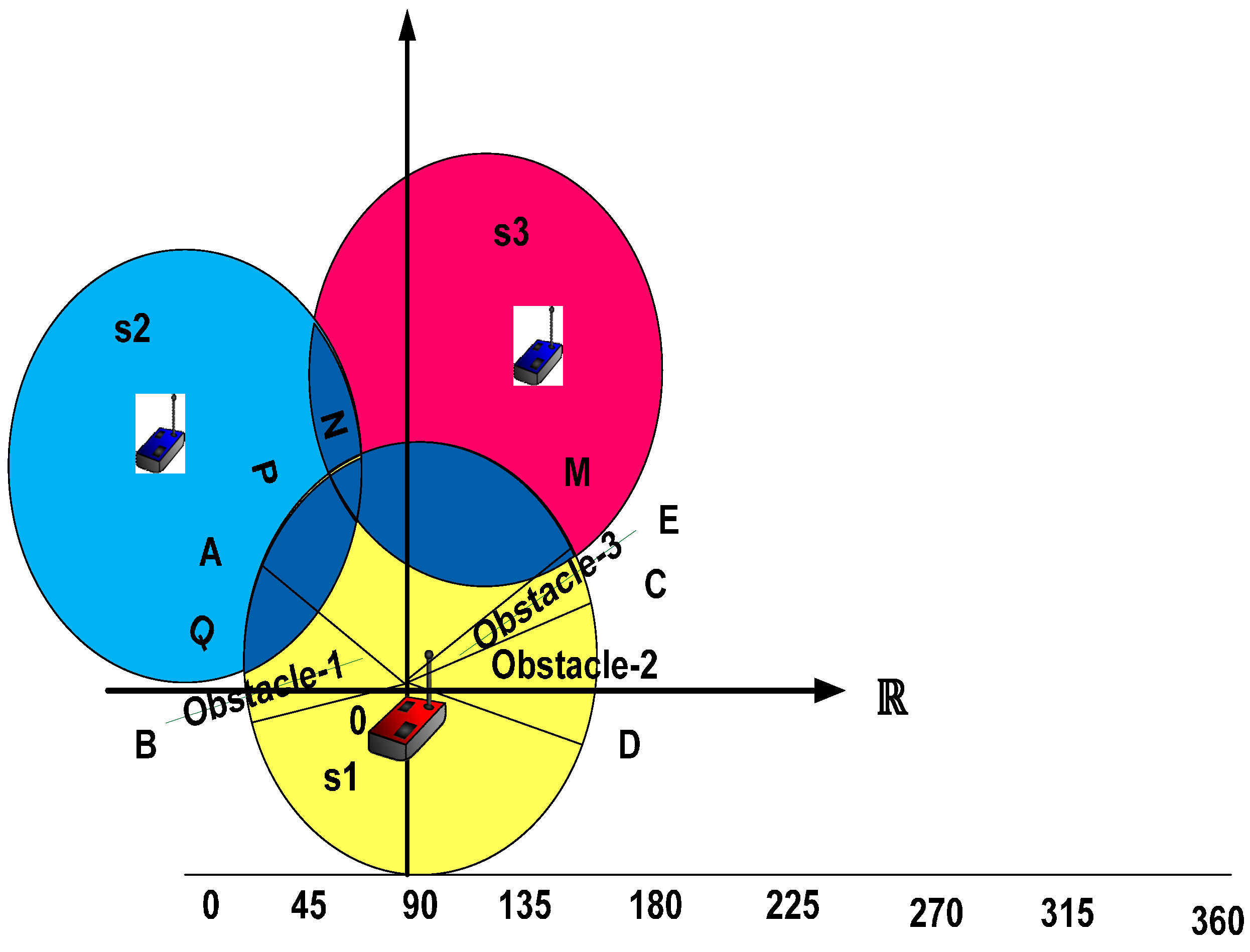
4.3. Location Detection
5. Simulation Setup and Experimental Results
- Multimedia Throughput Efficiency
- Successful Packet Delivery Ratio
- Network Accuracy
- Energy Consumption with Hidden Nodes
5.1. Multimedia Throughput Efficiency
5.2. Successful Packet Delivery Ratio
5.3. Network Accuarasy
5.4. Energy Consumption with Hidden Node
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Alanazi, A.; Elleithy, K. Real-Time QoS Routing Protocols in Wireless Multimedia Sensor Networks: Study and Analysis. Sensors 2015, 15, 22209–22233. [Google Scholar] [CrossRef] [PubMed]
- Levendovszky, J.; Thai, H. Quality-of-service routing protocol for wireless sensor networks. J. Inf. Technol. Softw. Eng. 2015, 2014. [Google Scholar] [CrossRef]
- Abazeed, M.; Faisal, N.; Zubair, S.; Ali, A. Routing protocols for wireless multimedia sensor network: A survey. J. Sens. 2013, 2013. [Google Scholar] [CrossRef]
- Tezcan, N.; Wang, W. Self-orienting wireless multimedia sensor networks for occlusion-free viewpoints. Comput. Netw. 2008, 52, 2558–2567. [Google Scholar] [CrossRef]
- Bhandary, V.; Malik, A.; Kumar, S. Routing in Wireless Multimedia Sensor Networks: A Survey of Existing Protocols and Open Research Issues. J. Eng. 2016, 2016, 27. [Google Scholar] [CrossRef]
- Razaque, A.; Elleithy, K. Energy-Efficient Boarder Node Medium Access Control Protocol for Wireless Sensor Networks. Sensors 2014, 14, 5074. [Google Scholar] [CrossRef] [PubMed]
- Cobo, L.; Quintero, A. Ant-based routing for wireless multimedia sensor networks using multiple QoS metrics. Comput. Netw. 2010, 54, 2991–3010. [Google Scholar] [CrossRef]
- Madan, R.; Lall, S. An energy-optimal algorithm for neighbor discovery in wireless sensor networks. Mob. Netw. Appl. 2006, 11, 317–326. [Google Scholar] [CrossRef]
- Serhan, Z.; Diab, W.B. Energy-efficient QoS Routing in Wireless Multimedia Sensor Networks. In Proceedings of the 29th IEEE International Conference on Advanced Information Networking and Applications (AINA ‘15), Gwangju, South Korea, 24–27 March 2015; pp. 223–230.
- Malarvizhi, K.; Brindha, M.; Kumar, M. Evaluation of energy efficient routing in wireless multimedia sensor networks. In Proceedings of the 2015 2nd International Conference on Electronics and Communication Systems (ICECS), Tamilnadu, India, 26–27 February 2015.
- Dyo, V.; Mascolo, C. Efficient node discovery in mobile wireless sensor networks. In Proceedings of the International Conference on Distributed Computing in Sensor Systems, Santorini Island, Greece, 11 June 2008.
- Jurdak, R.; Baldi, P.; Lopes, C.V. Adaptive low power listening for wireless sensor networks. IEEE Trans. Mob. Comput. 2007, 6, 988–1004. [Google Scholar] [CrossRef]
- Yang, Q.; He, S.; Li, J.; Chen, J.; Sun, Y. Energy-efficient probabilistic area coverage in wireless sensor networks. IEEE Trans. Veh. Technol. 2015, 64, 367–377. [Google Scholar] [CrossRef]
- Chaturvedi, P.; Daniel, A. An energy efficient node scheduling protocol for target coverage in wireless sensor networks. In Proceedings of the 2015 Fifth International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 4–6 April 2015; pp. 138–142.
- Soro, S.; Heinzelman, W.B. On the coverage problem in video-based wireless sensor networks. In Proceedings of the 2nd International Conference on Broadband Networks, 2005. BroadNets 2005, Boston, MA, USA, 7 October 2005; pp. 932–939.
- Adriaens, J.; Megerian, S.; Potkonjak, M. Optimal worst-case coverage of directional field-of-view sensor networks. In Proceedings of the 2006 3rd Annual IEEE Communications Society on Sensor and Ad Hoc Communications and Networks, 2006, SECON’06, Reston, VA, USA, 25–28 September 2006; pp. 336–345.
- Megerian, S.; Koushanfar, F.; Potkonjak, M.; Srivastava, M.B. Worst and best-case coverage in sensor networks. IEEE Trans. Mobile Comput. 2005, 4, 84–92. [Google Scholar] [CrossRef]
- Wu, C.-H.; Lee, K.-C.; Chung, Y.-C. A Delaunay triangulation based method for wireless sensor network deployment. Comput. Commun. 2007, 30, 2744–2752. [Google Scholar] [CrossRef]
- Zhao, J.; Zeng, J.-C. A virtual centripetal force-based coverage-enhancing algorithm for wireless multimedia sensor networks. IEEE Sens. J. 2010, 10, 1328–1334. [Google Scholar]
- Keshavarzian, A.; Uysal-Biyikoglu, E.; Herrmann, F.; Manjeshwar, A. Energy-efficient link assessment in wireless sensor networks. In Proceedings of the INFOCOM 2004. Twenty-Third Annual Joint Conference of the IEEE Computer and Communications Societies 2004, Hongkong, China, 7–11 March 2004; IEEE: New York, NY, USA; pp. 1751–1761.
- Bagchi, S.; Hariharan, S.; Shroff, N. Secure Neighbor Discovery in Wireless Sensor Networks; Purdue Technical Report, TR ECE 07-19; Purdue University: West Lafayette, IN, USA, 2007. [Google Scholar]
- Ley-Bosch, C.; Alonso-González, I.; Sánchez-Rodríguez, D.; Ramírez-Casañas, C. Evaluation of the Effects of Hidden Node Problems in IEEE 802.15. 7 Uplink Performance. Sensors 2016, 16, 216. [Google Scholar] [CrossRef] [PubMed]
- Sujatha, M.; Bhuvaneswaran, R.S. An Efficient Beam Scanning Algorithm for Hidden Node Collision Avoidance in Wireless Sensor Networks. In Advanced Computer and Communication Engineering Technology; Sulaiman, H., Othman, M.A., Othman, M.F., Rahim, Y., Pee, N., Eds.; Springer: Melaka, Malysia, 2015; pp. 627–639. [Google Scholar]
- Tseng, W.; Fan, Y.-C.; Sheu, S.-T.; Ou, S.-Y. An effective grouping scheme for avoiding hidden node problem in IEEE 802.15. 4-based wireless sensor networks. ACM SIGAPP Appl. Comput. Rev. 2014, 14, 30–40. [Google Scholar] [CrossRef]
- Rohini, R.; Gnanamurthy, R. Performance analysis to improve quality of service using cluster based hidden node detection algorithm in wireless sensor networks. Intell. Autom. Soft Comput. 2016, 1–7. [Google Scholar] [CrossRef]
- Koubâa, A.; Severino, R.; Alves, M.; Tovar, E. H-NAMe: A hidden-node avoidance mechanism for wireless sensor networks. IFAC Proc. Vol. 2009, 42, 10–19. [Google Scholar] [CrossRef]
- Sachan, M.; Imam, S.; Beg, M. Energy-efficient communication methods in wireless sensor networks: A critical review. Int. J. Comput. Appl. 2012, 39, 35–48. [Google Scholar]
- Tanimoto, M.; Tehrani, M.P.; Fujii, T.; Yendo, T. Free-viewpoint TV. IEEE Signal Process. Mag. 2011, 28, 67–76. [Google Scholar]
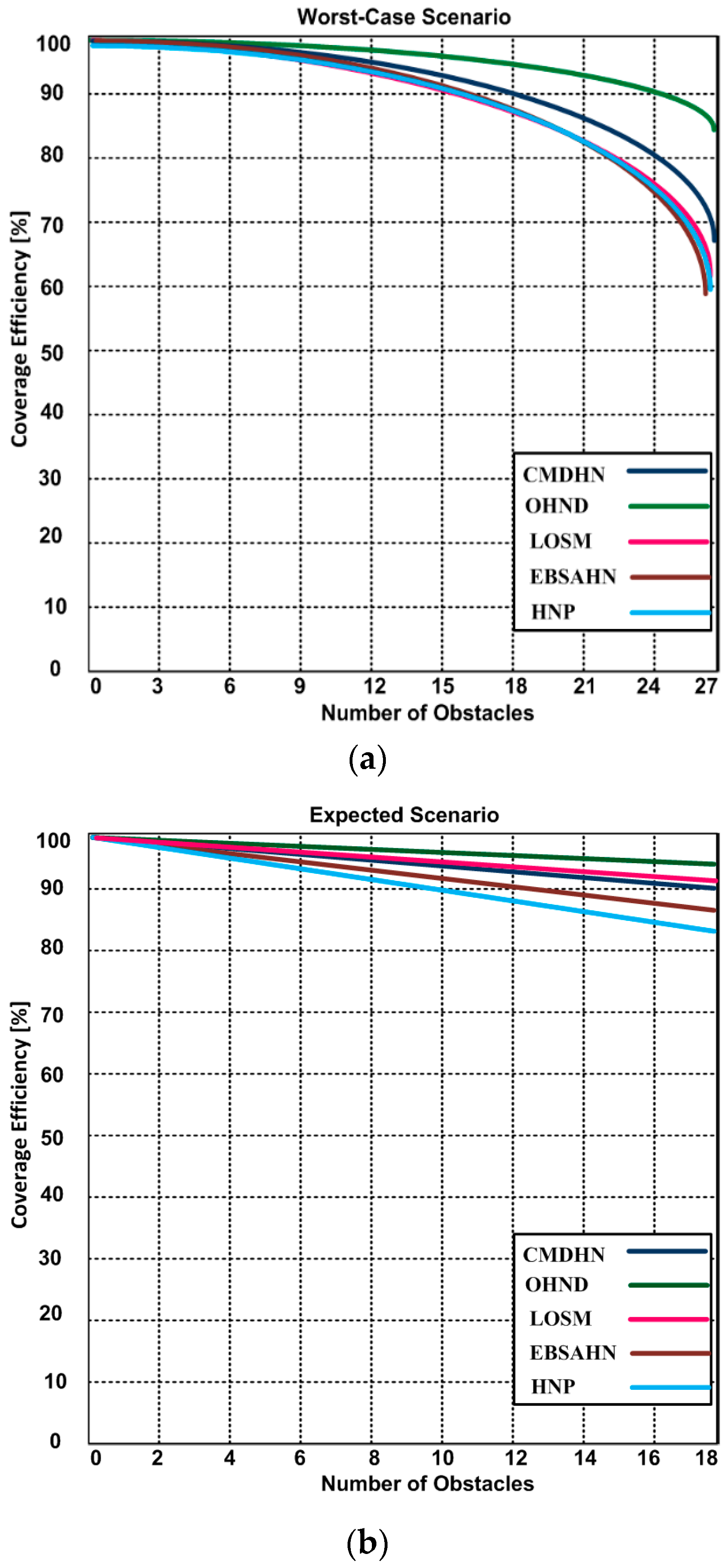
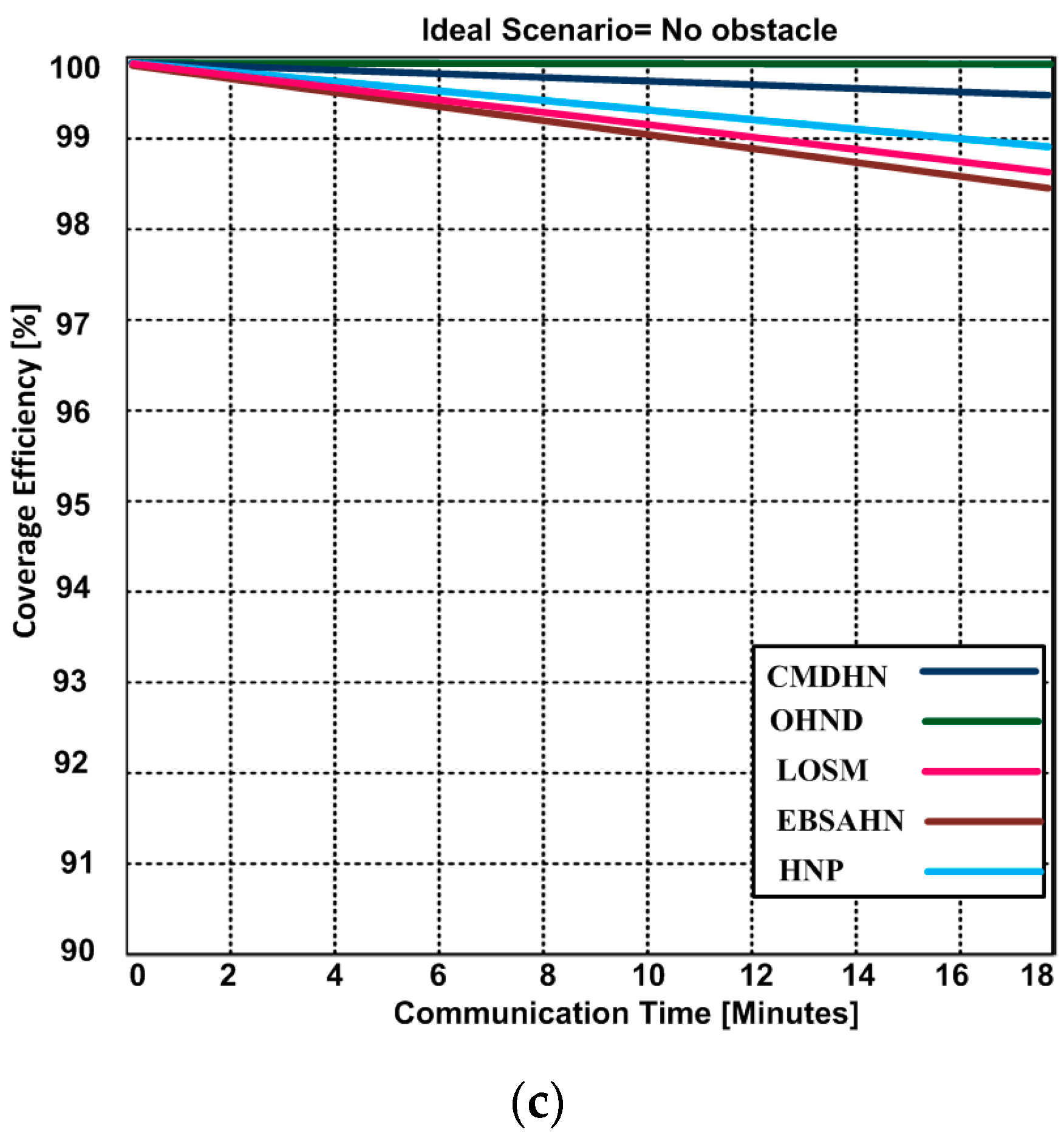
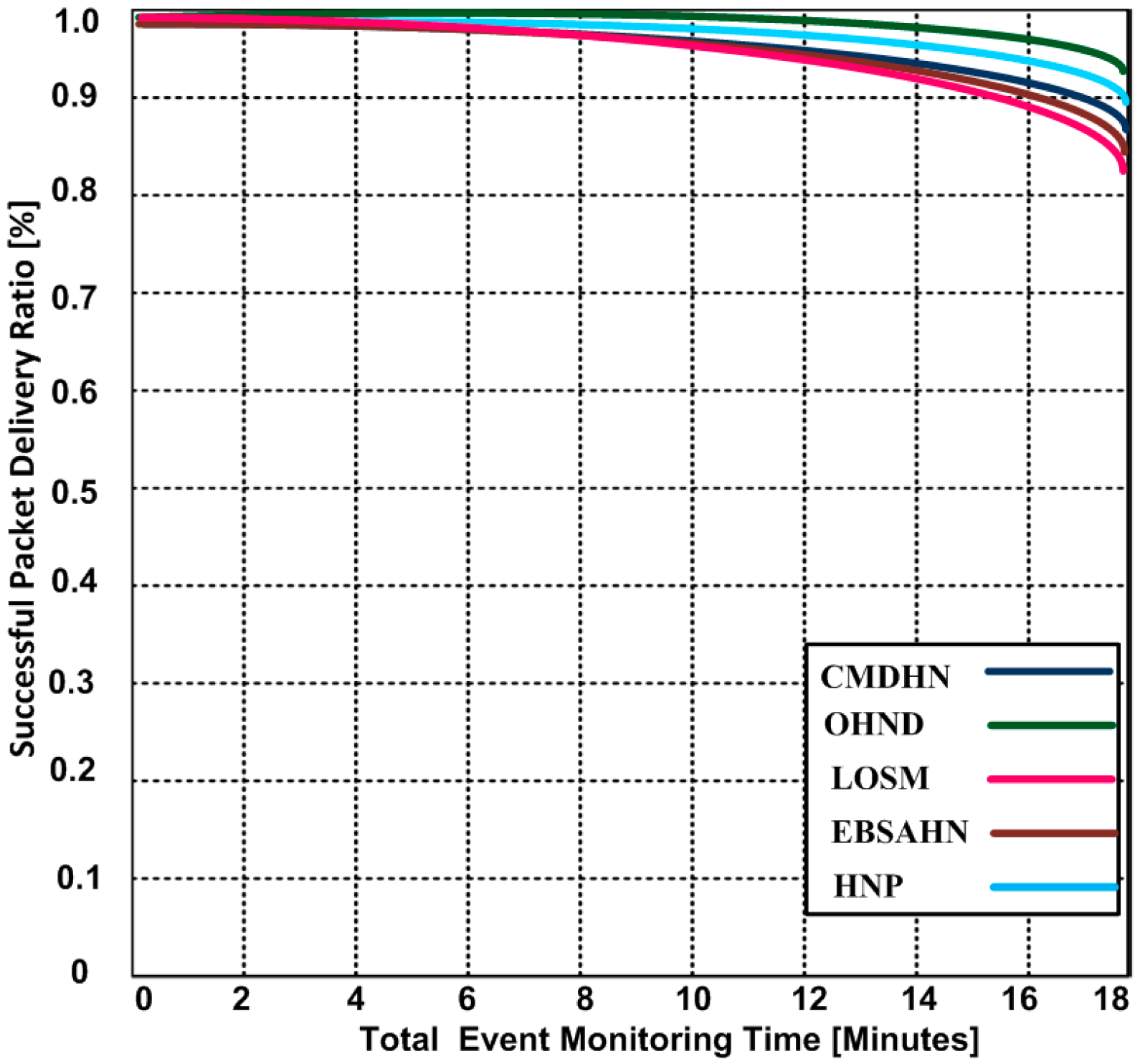
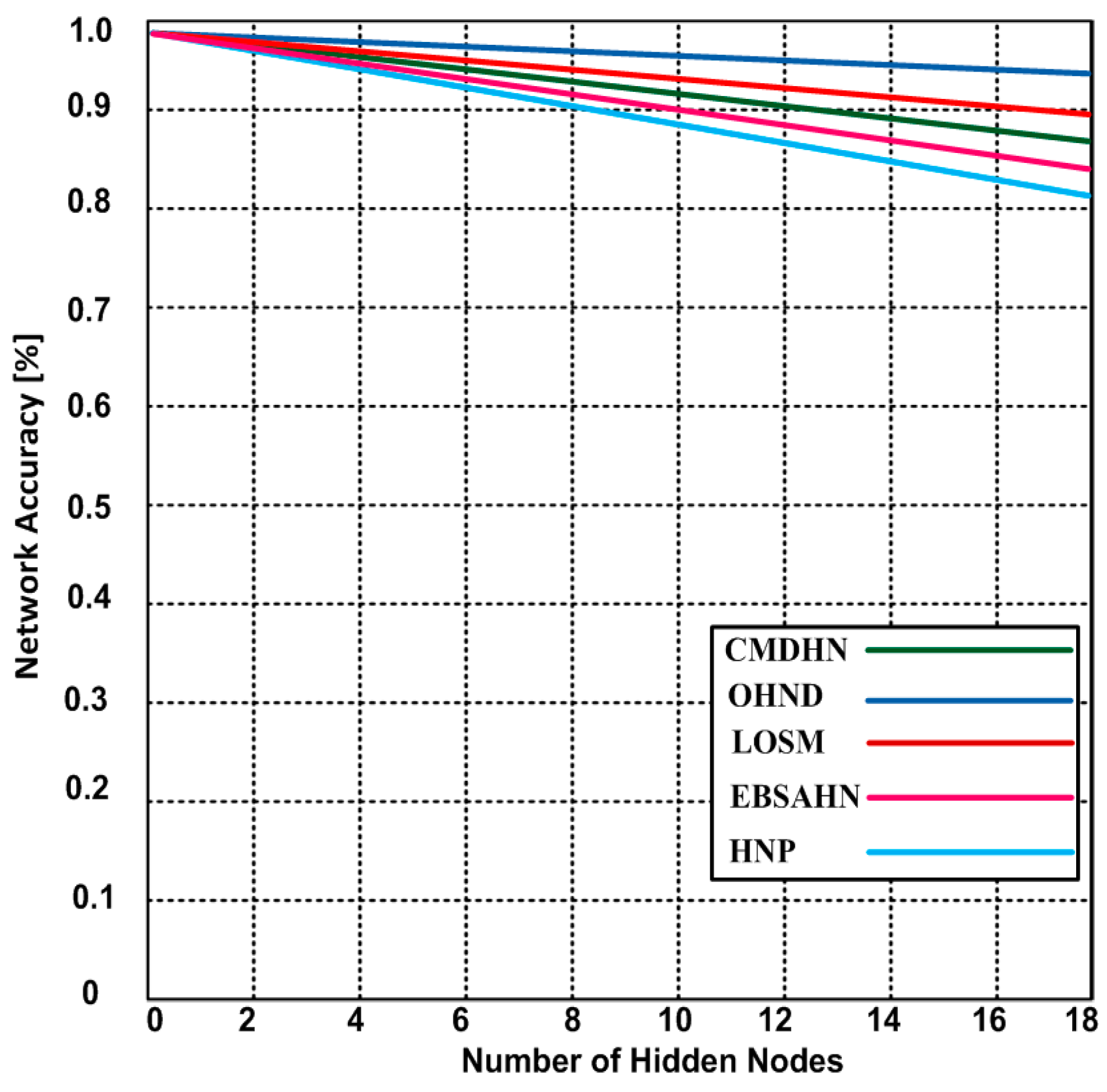

| Existing Protocols | Bio-Directional Coverage | Omni-Directional Coverage | Single-Directional Coverage | Energy-Efficient | Hidden Node Detection | Scalability | Multimedia Content-Support Delivery | QoS |
|---|---|---|---|---|---|---|---|---|
| Energy-efficient Probabilistic Area Coverage (EPAC) [12] | X | X | ||||||
| Energy-efficient Node Scheduling Protocol for Target Coverage (ENSPTC) [13] | X | X | ||||||
| Coverage Problem in Video-Based (CPV) [14] | X | X | ||||||
| Optimal Worst-Case Coverage of Directional Field-of-View (OWCDF) [15] | X | X | ||||||
| Worst and Best-Case Coverage (WBC) [16] | X | X | X | |||||
| Delaunay Triangulation-Based Method (DTM) [17] | X | X | ||||||
| Virtual Centripetal Force-based Coverage-Enhancing Algorithm (VCFEA) [18] | X | |||||||
| Energy-Efficient Link Assessment (ELA) [19] | X | X | ||||||
| Secure Neighbor Discovery (SND) [20] | X | |||||||
| Line of Sight Method (LOSM) [22] | X | X | ||||||
| Efficient Beam Scanning Algorithm for Hidden Node (EBSAHN) [23] | X | X | X | |||||
| Hidden Node Problem (HNP) [24] | X | X | X | |||||
| Clustering-Based Mechanism for Detecting the Hidden Nodes (CMDHN) [25] | X | X | X |
| Notation | Description |
|---|---|
| Consumed energy of coordinator node for synchronization | |
| Number of synchronized messages by each newly joining node | |
| Energy consumed by radio of multimedia sensor | |
| Energy consumed for amplifying | |
| Number of synchronizing nodes | |
| d | Distance between coordinator and newly joined node |
| Energy consumed for broadcasting | |
| Energy consumed by coordinator node for scheduling | |
| C | Coordinator node |
| Cn | Non-coordinator nodes |
| Coordinator’s initial energy | |
| Residual energy of coordinator | |
| Energy consumed by coordinator node for data collection | |
| Sd | Subdivision |
| Node load | |
| Number of hello message by node | |
| Maximum buffer size of node | |
| Hidden node |
| Notations | Description |
|---|---|
| Average location error | |
| First estimated location | |
| Second estimated location | |
| First actual location | |
| Second actual location | |
| Total number of multimedia sensor nodes | |
| Ψ | Obstacles |
| Average location detection time | |
| Total locations of all multimedia sensor nodes | |
| Boundary range |
| Parameters | Value |
|---|---|
| Size of network | 1200 × 1200 square meters |
| Number of multimedia sensor nodes | 270 |
| Queue-capacity | 50 packets |
| free-space propagation | 47 meters |
| Maximum number of retransmissions allowed | 03 |
| Initial energy of node | 7 Joules |
| MAC protocol | BN- MAC [6] |
| Size of packets | 512 bytes |
| Data rate | 450 kb/second |
| Sensing range of node | 30 meters |
| Communication range | 50 meters |
| Transmitter power | 12.2 mW |
| Receiver power | 13.4 mW |
| Buffer threshold | 1024 Bytes |
| Sensing range | 30 meters |
| Number of obstacles | 10–18 for Expected and 18–27 for worst scenario |
| Simulation time | 18 min |
| Average simulation run | 10 |
| Frame rate | 40 frame/second |
| Reliability | [0.78, 0.92] |
| Average reporting rate | 4 packet/second |
| Base station location | (0,700) |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alanazi, A.; Elleithy, K. An Optimized Hidden Node Detection Paradigm for Improving the Coverage and Network Efficiency in Wireless Multimedia Sensor Networks. Sensors 2016, 16, 1438. https://doi.org/10.3390/s16091438
Alanazi A, Elleithy K. An Optimized Hidden Node Detection Paradigm for Improving the Coverage and Network Efficiency in Wireless Multimedia Sensor Networks. Sensors. 2016; 16(9):1438. https://doi.org/10.3390/s16091438
Chicago/Turabian StyleAlanazi, Adwan, and Khaled Elleithy. 2016. "An Optimized Hidden Node Detection Paradigm for Improving the Coverage and Network Efficiency in Wireless Multimedia Sensor Networks" Sensors 16, no. 9: 1438. https://doi.org/10.3390/s16091438






