1. Introduction
Wireless sensor networks (WSNs) play an important role in sensing and collecting a wide range of environmental and geological parameters in the current and future surveillance systems. In such networks, widely covered and densely deployed sensors may simultaneously detect the sensing data and they need to send the data to a sink node. As a result, the effective network throughput will be severely decreased because of the collisions among the contending sensors accessing the wireless channel simultaneously. With the increasing demand for high network converge and sensor density with new applications such as Internet of Things (IoT) and Vehicular-to-Vehicular (V2V) networks, the possibility of collisions among WSN nodes has become too high for WSNs to work well. Therefore, how to achieve effective data collection through an efficient channel access and scheduling mechanism so as to decrease the collisions becomes a new challenge in the new IoT and V2V types of super dense WSNs.
In Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) based networks, the transmission by hidden nodes causes severe interference, i.e., collision, to an on-going transmission in WSNs. In this paper, we focus on seeking a new method to avoid such interference.
So far, channel estimation based backoff algorithms [
1,
2] have been proposed to avoid collisions among the neighbor nodes. In such algorithms, nodes adaptively schedule their time to access the channel by continuously estimating the contention levels among their neighbor nodes. It has been shown in [
3] that channel estimation based backoff algorithms can efficiently decrease collisions among neighbor nodes to the theoretical low bound in cases with a wide range of contention levels. However, such algorithms are invalid for the case of collisions from hidden nodes because collisions from hidden nodes are too complex and hard to monitor on-the-fly.
Decreasing the possibility of collisions from hidden nodes with as small throughput loss as possible is challenging. In recent years, the studies in [
4,
5,
6] re-evaluated the Channel Clear Assessment (CCA) function and tried to solve the hidden terminal problem by proposing new solutions based on the new concept of efficient Carrier Sense Ranges (CSR). By enabling the non-hidden nodes to detect and hear the hidden nodes’ activities, the hidden nodes will no longer be hidden for others. Thus, a lot of interference analysis models have been proposed since then for better CSRs for different applications. The authors in [
7,
8,
9,
10] proposed Protocol Interference Models (PrIMs) to improve performance of CSRs in networks with diverse topologies. In their models, the interference introduced by a hidden node to an on-going communication is comprehensively analyzed, and a “safe” CSR is calculated to prevent the on-going communication from being corrupted by this hidden node. However, the work in [
4] indicated that PrIMs is idealistic because the interference in reality is not from a single hidden node but from multiple hidden nodes. As a consequence, the CSRs calculated from PrIMs are not large enough to effectively avoid collisions caused by hidden nodes. A new interference analysis model, Physical Interference Model (PhIM), was proposed in [
11,
12]. In these papers, interferences from all possible hidden terminals are included so that the CSRs calculated from PhIMs can totally avoid the collisions from hidden nodes even in the worst case. However, in practice, interference from hidden nodes is not always that serious. This suggests that the estimated CSRs in PhIMs sometimes become larger than the correct value of CSR. An over-estimated CSR will cause the explosion problem and some contending nodes will miss the transmission opportunities. As a result, the effective channel utilization rate, which has a positive correlation with the system throughput, will be decreased.
In this paper, we propose an effective method to improve the network throughput performance by controlling the interference from neighbor nodes including hidden nodes. Our main contributions in this paper are summarized as bellow:
Firstly, we analyze the characteristics of the pre-configuring operations in WSNs. Based on such operations, we propose a data collection scheme with distinct directivity. We validate of this directional transmission scheme on the premise of complete data collection.
Secondly, we analyze collisions in WSNs and propose a space-time based medium access mechanism, which explores user diversity both in space and time domains. By fully taking advantage of the directional transmission strategy, we propose a new method of calculating s for the proposed channel access mechanism to significantly reduce or even totally eliminate in some cases collisions from both neighbor nodes and hidden nodes.
Thirdly, we conduct simulations to evaluate the performance of our proposed solution, which was compared to the classic IEEE 802.11 series protocols and ones with enhanced CSRs. We analyze the throughput and the packet loss rate, the key parameters that determine the data collection efficiency. In order to cover scenarios with different settings, we evaluate the performance of our proposed solution in networks with different topologies, including the regular latticed case and random deployed ones.
This paper is organized as follows. In
Section 2 we analyze the channel access characteristics in WSNs and propose a new directional data transmission strategy. A space-time based random access method is proposed in
Section 3. In
Section 4, we evaluate the performance of the proposed method through simulations. In
Section 5 we conclude this paper.
2. Data Collection Strategy with Directional Transmission
Communications in WSNs are quite different from general wireless networks in that the data flow is quite directional, i.e., either from the sink node to end nodes or vice versa. In this section, we analyze these properties ofa WSNs and propose our new data collection strategy with directional transmission characteristics.
2.1. Pre-Configuring Operation in WSNs
In WSNs, a sink node is the controller of the whole network by sending commands to other sensors, including monitoring the sensors’ status, broadcasting commands to sensors, etc. This task is called the run-up phase. The second task for WSNs is to collect data from all the sensors where data will be sent to the sink node using intermediate relay sensor nodes. This task is called the data-collection phase. Controlled by the sink node, the WSN can either be in the run-up phase or data-collection phase.
The run-up phase of the WSN happens during the network deployment process when some simple interactions happen between the sensors and the sink node. For example, the sink node will unicast, multicast or broadcast commands to sensors and then the sensors will report their state information back to the sink node, i.e., their position, battery, routing information, etc. to the sink node. By checking the information above, the sink node can ensure the network connectivity while sensors can update their information to the sink node.
The data-collection phase happens when an event is detected by sensors so that the sensors need to send data back to the sink node. During this period of time, a large number of nearby sensors will simultaneously attempt to get access to the channel in order to transmit the data to the sink node. Since CSMA/CA is not good at supporting large users contending for channel access, the above case will result in serious collisions among the sensors which significantly decreases network throughput and introduce more delay.
Considering those characteristics of communications in WSNs, it is necessary to introduce centralized control, i.e., making some pre-configurations to sensors and introducing some rules to define specific behaviours of sensors especially during the run-up phase. With the pre-configuration in the run-up phase, data transmissions in the data-collection phase can be well controlled by avoiding extreme congestions, so that collisions are able to be suppressed.
2.2. Directional Transmission Model
Directional data forwarding is a typical feature of communications in WSNs because the data flow in WSNs is always directional, i.e., it is either from sensors to the sink node or vice versa. Considering the pre-configuring operations during the run-up phase, the property of directional data transmissions in WSNs can be further utilized and the interference among nodes can be better mitigated. Next, we focus on the analysis of the directional transmission model.
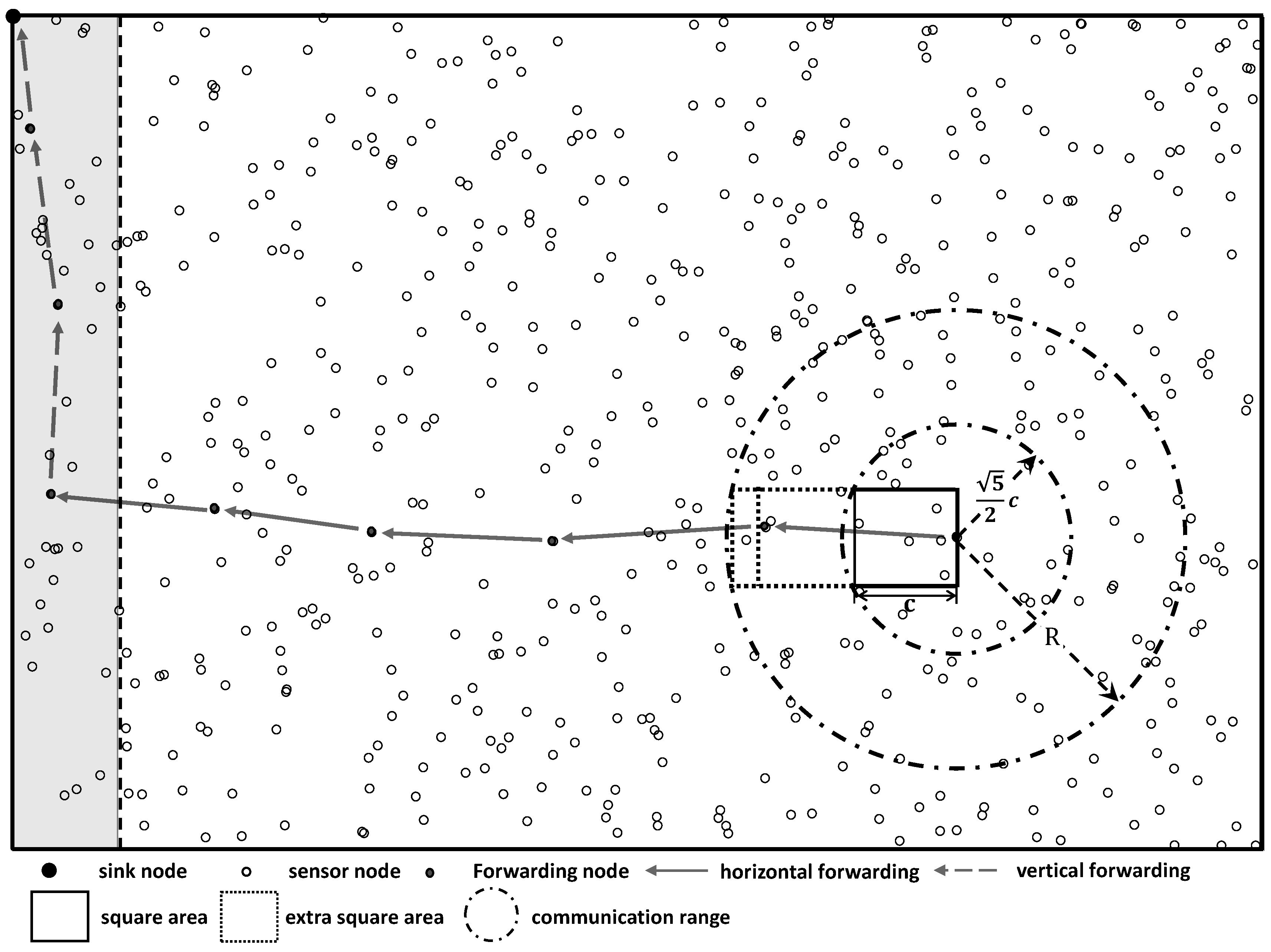
We start with the physical model of a sensor network. As shown in
Figure 1, we consider a sensor network which includes
n wireless sensor node
and a sink node
s. We use a random extended network model [
13] by assuming that sensor nodes are uniformly deployed in a rectangular region with the size of
.
We denote the location of the sensor node
in the network by
where
and
represent the location coordinates. We denote the distance between
and
as the euclidean space
and the communication range as
R, which is associated with the Signal to Interference plus Noise Ratio (SINR). If
, data transmission from
to
will be successful. We denote the link as
and express the links in the network as Equation (
2).
The sink node is placed at the upper-left corner with the coordinate
. Thus, the data collection process is divided into two parts: horizontal forwarding and vertical forwarding. During the horizontal forwarding process, data goes from the right to the left which is shown as the data forwarding in the white area of the
Figure 1, and for the vertical forwarding, data goes from bottom to top which is shown as the data forwarding in the gray area of the
Figure 1. The horizontal forwarding and vertical forwarding processes are separated by different methods and resources including channels and time slots, etc. Next we construct the directional data forwarding in the horizontal forwarding process as an example since the vertical forwarding process can be done in the same way.
The property of directional data transmission in the horizontal forwarding process is analyzed by introducing the link constraint between sensor nodes. The link constraint is that a link from
to
is available, if and only if the projected length of
in the vertical axis is smaller than
. Denoting
as the projected length of
in the vertical axis, the links which satisfy the above link constraint can be expressed as Equation (
3).
2.3. Model Validity Analysis
in our directional transmission strategy is a subset of L. In order to make sure all the data from the sensor nodes can be sent to the gateway nodes by out of L, we need to ensure the network is completely connected based on the above model.
As shown in
Figure 1, by setting the coordinate of a sender
as the midpoint of the right side, a square area is created with the side length of
c. In a uniformly distributed network with the size of
, the probability of a random deployed sensor node within the above square area is equal to
. Thus, in a
n-node system, the probability of having an empty square area can be calculated by
where
Because
, we have
and
According to the Borel-Cantelli lemma, there is at least one sensor node located in the square area for sufficiently large n.
As shown in
Figure 1, if the communication range
R is larger than
, at least one sensor node can be selected as a receiver by the sender
to establish a link. Because
is in the middle of the right side of the square, the projected length of the link in the vertical axis is smaller than
. Forwarding data from all the sensor nodes to the gateway nodes through the links in set
is feasible. As the number of sensor nodes located in the square area is a binomial random variable with parameters
, the availability of links in the square area is guaranteed. As shown in
Figure 1, if the communication range
R is large enough, which is very common in practice, the sender
can select receivers from other nearby square areas. In this situation, more links to do the data forwarding are available.
Now, we define
, where
ρ represents the sensor density of a WSN. According to Equation (
5), a smaller square area can be constructed by larger
ρ. In a dense WSN, our proposed directional data forwarding scheme for both the horizontal and vertical cases can be modelled as a problem of bunch of parallel-arranged lines with certain offsets which decrease significantly as a function of the sensor nodes density. For the scenarios that a WSN has a regular latticed topology, the data forwarding links are in parallel to each other with no offsets and can be expressed as
.
4. Performance Evaluation
The performance of the proposed schemes is evaluated through simulations using OMNET++ [
14]. The classic protocols (IEEE 802.11x [
15], IEEE 802.15.4 [
16]), and other channel access mechanisms with enhanced CSRs [
4] are compared in this section. Simulations are conducted with different network scales. Along with the increasing of the network scales, the number of neighbor nodes and hidden nodes increase. In our simulations, the performance of different data collection strategies is evaluated by analyzing the effects of interference from neighbor nodes and hidden nodes on the network performance of throughput, collision rate and frame loss rate, which are all key factors determining the data collection efficiency in WSNs. In addition, in order to cover the diversity of WSN applications, we consider two typical topologies, i.e., the random topology and the latticed topology.
4.1. Simulation Configurations
4.1.1. PHY and MAC Layer Configurations
The related PHY and MAC layer parameters are listed in
Table 1 based on the IEEE 802.11b standard [
15] which supports a longer distance than that of IEEE 802.15.4. Since the backoff process is universal in all the IEEE 802.11x and IEEE 802.15.4 standards, the proposed algorithm and its performance apply to all the backoff based medium access schemes in IEEE 802.11x and 802.15.4 networks.
4.1.2. Path Loss Model Configuration
In the simulations, the signal attenuates during the propagation in the form of the well known simple path loss model [
17] which is expressed in Equation (
27).
In Equation (
27),
is the pass loss, and
λ is the wavelength,
d is the transmitter-receiver distance and
α is the path loss exponent. For WiFi applications,
α is often set from 2 to 4. Because the value of
α does not affect the final simulation results, we set
in our simulations.
4.1.3. Topology Configuration
The WSN topology is an important factor in the simulations to make sure it comprehensively represents the real settings in WSNs. Since the corresponding communication range is around 80 m for , we set up an area of 400 m × 400 m with 100 sensors using different deployment schemes. In our simulations, we evaluate the proposed algorithms in networks with different settings.
4.1.4. Contrast Simulations
In order to comprehensively evaluate our proposed data collection method, we make five types of simulations with different kinds of data collection methods listed as below.
—This is the traditional data collection method in WSNs, where all sensors are implemented with the IEEE 802.11 protocol.
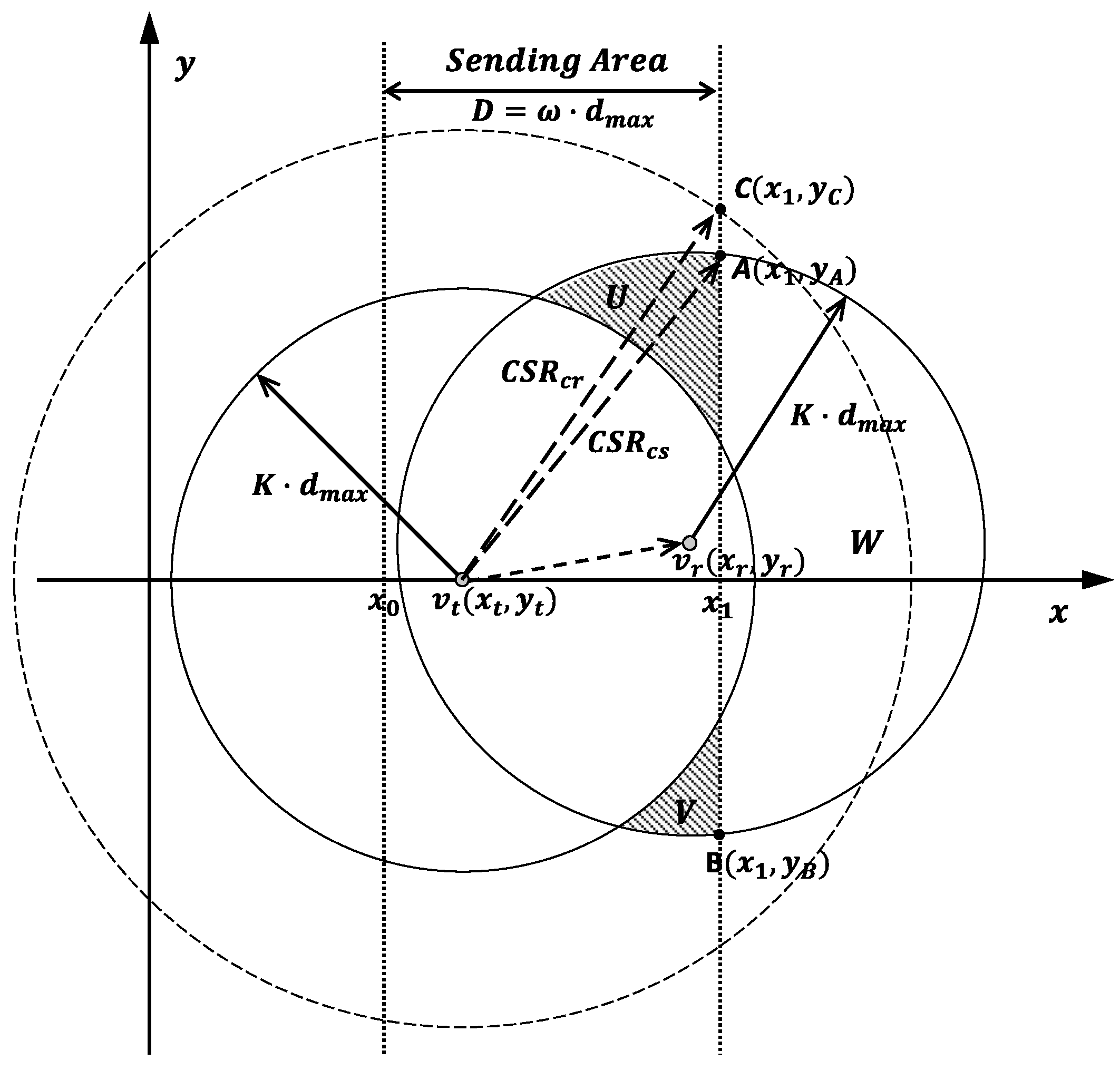
—This is a data collection method proposed in [
4] based on IEEE 802.11 with a larger CSR to totally eliminate collisions from hidden nodes and with a low signal receiving sensitivity.
—Because collisions from hidden nodes are totally eliminated in “
”, the estimation-based backoff algorithm is used in this algorithm to further decrease collisions from neighbor nodes. Thus, this is a data collection method with the classical estimation-based backoff and idle sense algorithm [
2].
-—This is our proposed data collection method with updated CSRs by utilizing the directional data forwarding characteristics in WSNs.
-—This is our proposed data collection method working together with the estimation-based backoff algorithm.
Next, the performance of the above five data collection methods is compared in terms of throughput and frame loss rate with the above two kinds of topologies.
4.2. Throughput Performance
Throughput is one of the most important performance indexes in WSNs.
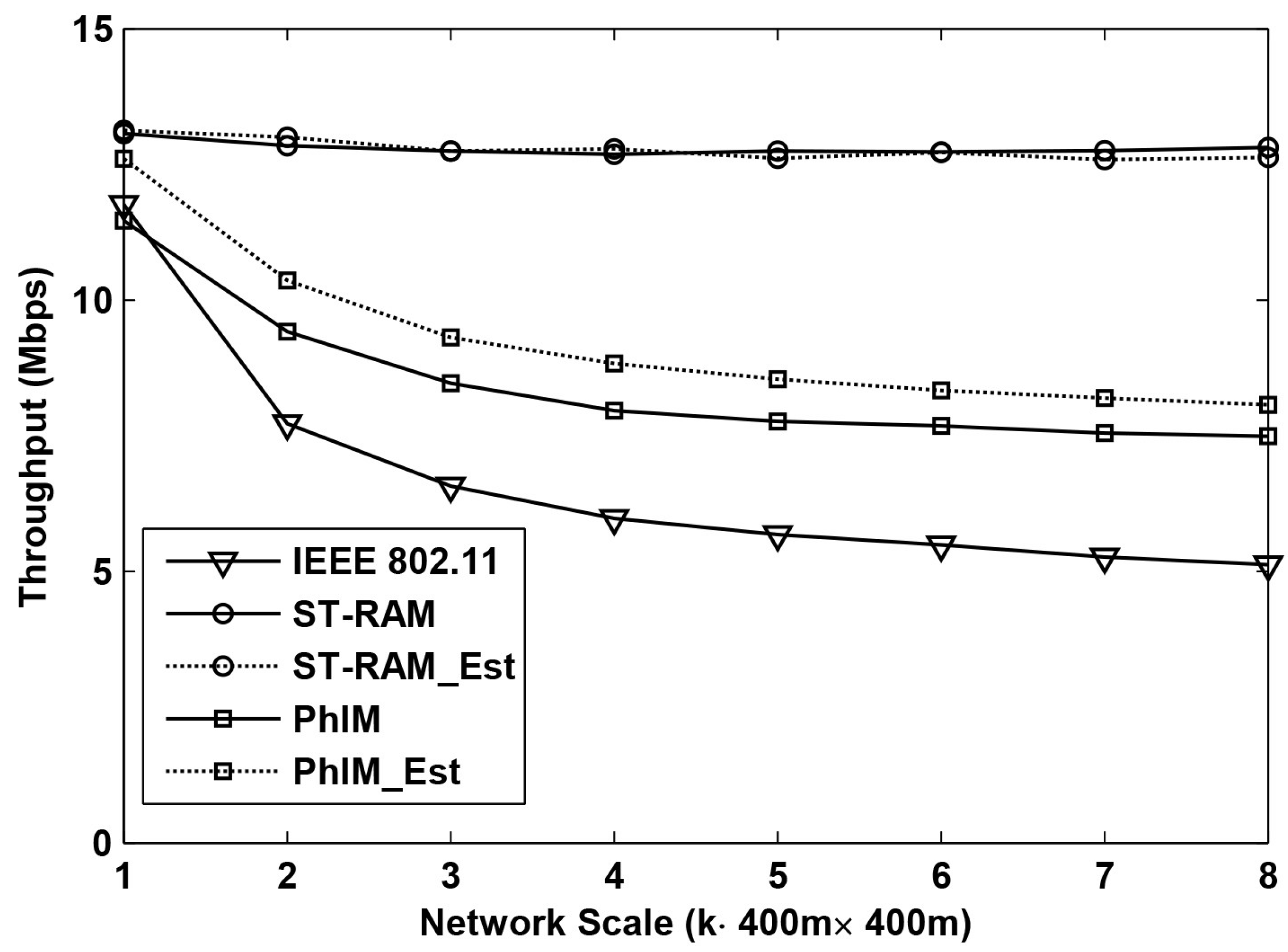
Figure 4 and
Figure 5 show the results of the throughput when using different data collection methods in the networks with different scales. The network scales ranging from 400 m × 400 m to 400 m × 3200 m are presented in the figure which is indicated by the x-axis. The y-axis is the average throughput of 400 m × 400 m area on average.
Figure 4 shows the throughput as a function of the network scale with random topologies. From the figure we can see that when the network scale is small, the throughput of different data collection methods is similar but when the network scale is increased, the throughput become very different.
Compared to the five different data collection methods, the throughput of “” decreases much faster than of the other schemes. This is because the number of hidden nodes of an on-going communication increases exponentially along with the increase of the network scale. As a result, interference from hidden nodes severely decreases the throughput of “”. The farther a hidden node is, the weaker interference it can cause. Thus, with the increase of the network scale, the accumulated interference from hidden nodes tends to be stable which makes the throughput of “” stable at around 5 Mbps when k is larger than 4.
The throughput of “” is much higher than that of “”, because the interference from hidden nodes is significantly suppressed by setting large CSR. However, with the increase of the network scale, the throughput of “” can only reach a certain level. It is because a larger CSR not only suppresses the number of the hidden nodes but it also increases the number of the neighbor nodes. The number of the neighbors will increase as a function of the extension of the network coverage. A larger number of neighbor nodes with more serious channel contention will also decrease the throughput.
The throughput decrease resulting from the neighbor nodes can be relieved by “” which can be easily verified by the two curves labeled with “” and “” in the figure. It is because the estimation-based backoff algorithm which is applied in “” can effectively reduce collisions from the extremely large number of neighbor nodes.
In all the simulations, our proposed data collection method “-” performs the best with the most stable throughput even for the cases of increasing the network scale. This is because our proposed solution has the following three advantages: Firstly, collisions from the hidden nodes are totally eliminated by our new proposed CSR. Secondly, the value of CSR is cut down by sufficiently utilizing the communication rules in WSNs which significantly improves the effective channel utilization. Thirdly, sensors are allowed to access the channel in different time intervals in our proposed method which further decreases collisions from neighbor nodes.
Figure 4 shows that the throughput of “
-
” and that of “
-
” is about the same. This is reasonable because the number of concurrent neighbor nodes in our proposed method is significantly decreased by the time division multiple access mechanism so that the number of contending neighbors is only around a dozen for our settings. In this case, collisions from neighbor nodes are so low that the possibility of collisions that can be avoided by the estimation-based backoff algorithms is very small. This conclusion can be verified according to the results in [
3].
The throughput of different data collection methods in latticed topology is shown in
Figure 5. By comparing the results in
Figure 4 and
Figure 5 we can find that the throughputs of “
”, “
” and “
” in the random topology are almost the same as that of the latticed topology case. This is because the topological structure is not taken into consideration in designing the value of CSR by the above methods. However, in our proposed method, the position relationship among the sensors plays an important role in obtaining better CSRs. According to Equation (
23), we can find that the CSR in the latticed topology can be further optimized by substituting
which is proved in
Section 2. This conclusion is verified in
Figure 5 where the throughput of “
-
” and “
-
” in the latticed topology are obviously higher than that in the random topology.
4.3. Collision Rate and Frame Loss Rate
Collision rate is another important performance parameter in WSNs. The MAC layer protocol of WSNs requires that if collision happens the frame will be retransmitted until it is successfully received or reaches the maximum number of retransmissions tries. This retransmission mechanism is applied to avoid endless retransmissions over very bad quality links. Once the maximum number of retransmissions is reached, the node will drop the frame. This may trigger an upper layer retransmission during which a new transmission route will be generated. However, the frame loss may be because of the interference from other sensors. In this case, the upper layer retransmission will be also triggered; however, this does not make any sense, because congestions in WSNs are always within a region. However, during this process, the new transmission route establishment process will cost a lot of time that is tens or hundred times of an ordinary frame transmission in the MAC layer. This will cause a severe throughput decrease on the basis of the results we presented in the previous section.
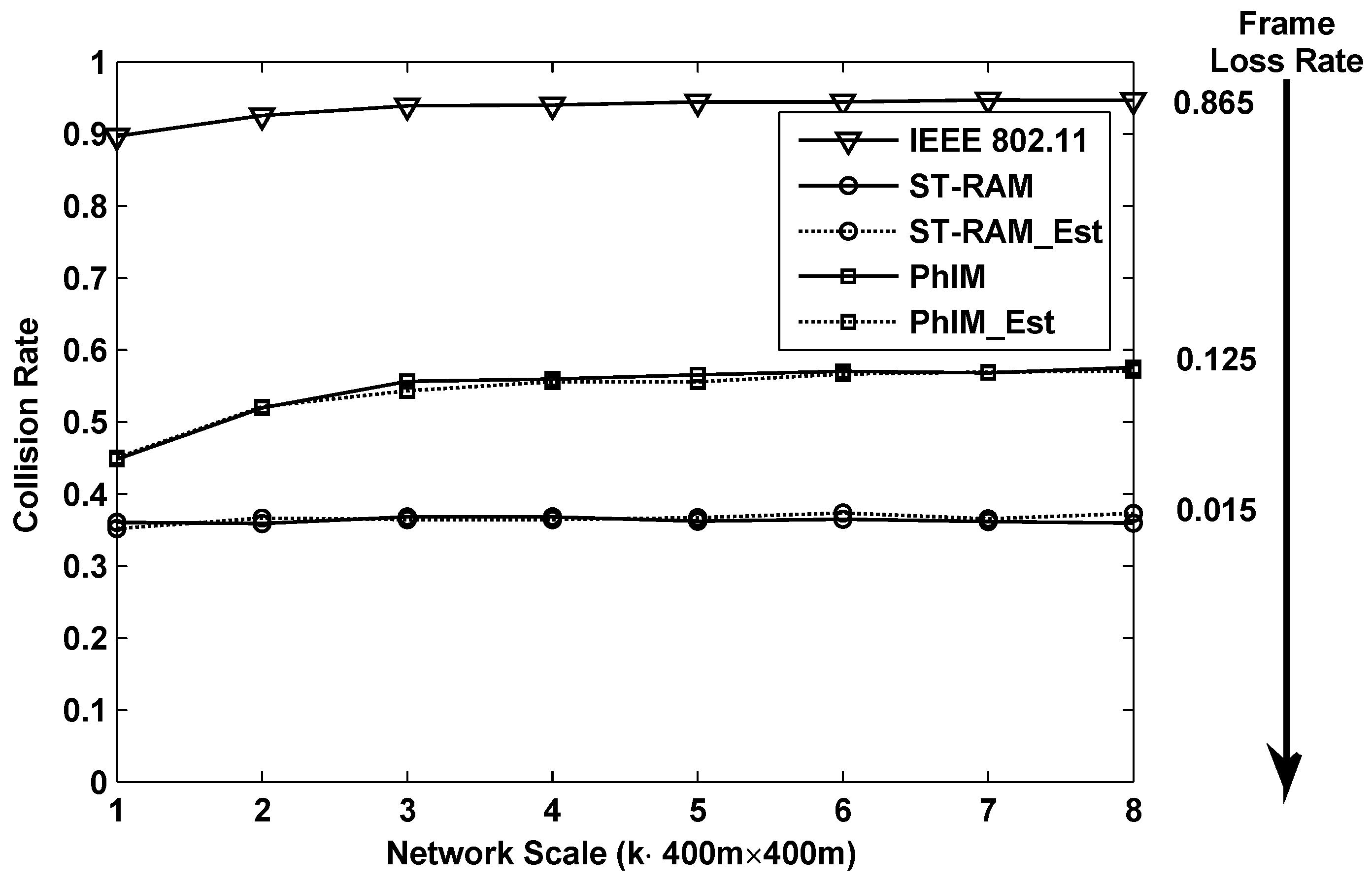
Figure 6 and
Figure 7 show the results of the collision rate in using of different data collection methods in the networks with different scales. Results shown in
Figure 6 are for the case in the random topology. It can be seen that, being affected by the serious collisions from hidden nodes, “
” has the highest collision rate which is larger than
in large-scale networks. While eliminating the collisions from hidden nodes and bringing a larger number of neighbor nodes, the collision rates of “
” and “
” are close and both approach
in large-scale networks. Our proposed methods “
-
” and “
-
” have the lowest collision rate by simultaneously decreasing the collisions from hidden nodes and contending neighbor nodes.
According to the IEEE 802.11 protocol, we set the maximum number of retransmissions as 4 and simulate the corresponding frame loss rate in networks with different scales. The approximate frame loss rates in large scale networks, where the frame loss rate becomes stable, are labeled on the right side of
Figure 6. An extremely large amount of time will be wasted on establishing a new route in “
” because of its
frame loss rate. The frame loss rate in “
” is acceptable which is around
and our proposed “
-
” can achieve extremely low packet loss rate which is less than
.
The collision rate and frame loss rate of different data collection methods in the latticed topology is shown in
Figure 7. Our proposed method “
-
”, the frame loss rate can even be less than
.
4.4. Performance in Networks with Different Densities
In above simulations, the network topologies are all constructed in the unit area where 100 sensors locate in 400 m × 400 m. In order to study the performance of different data collection methods in networks with other densities, the network with the scale of 400 m × 800 m are constructed and new simulations where the network densities are 1 to 5 times as much as 100/(400 m × 400 m) are configured.
Figure 8 shows the simulation results where four subgraph respectively represents the throughput and collision rate of different data collection methods for lattice deployed networks and random deployed networks.
In the figure, the density index equals the simulated network density divided by 100/(400 m × 400 m).
Figure 8a,b show that the throughput performances of different data collection methods all decrease along with the increase of the network density, and tend to be stable when the network densities are extremely large. It works both in lattice deployed networks and the random deployed networks. This is mainly because the interferences from hidden nodes in IEEE 802.11 become more and more serious, until the energies from additional hidden nodes are negligible compared to the accumulated interferences. Besides, the significant increasing number of neighbor nodes is another main cause of the throughput decrease. Similar results can be obtained from the collision rate performance in
Figure 8c,d. By comparing the performance of different data collection methods in
Figure 8, it can be found that our proposed method “
-
” achieves the best and the most stable throughput and collision rate.