1. Introduction
Code dissemination is a main building block of reprogramming which allows over-the-air software updates in wireless sensor networks (WSNs). Since WSNs are mostly deployed in unattended and hostile environments, secure code dissemination is essential to prevent attackers from injecting malicious code into the WSN. There have been a lot of works on secure code dissemination [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13] whose main goal is to provide
source authentication, which implies that each sensor node must be able to assure that the received code image is really sent by a base station (BS) and not modified in transit. They attain this goal by applying existing source authentication schemes, such as μTESLA [
14], digital signatures and the hash chains, into code dissemination.
Recently, a few cross-layer approaches using link estimation have been suggested to improve energy efficiency in WSNs. DPLC [
15] provides a lightweight dynamic packet length control scheme based on an accurate link estimation method which leads to low transmission overhead. ECD [
16] is a code dissemination scheme supporting dynamic packet size and accurate sender selection based on link quality. Plena [
17] is a packet length adaptation scheme using error estimating codes. Theses dynamic packet size control schemes can significantly improve the energy efficiency of code dissemination. However, it is not easy to guarantee source authentication for these schemes since the packet size can be changed in each hop depending on the link quality. All well-known existing source authentication schemes for WSNs, such as μTESLA, digital signatures and the hash chains, support only fixed-size packets in every hop during code dissemination.
In this paper, we propose three source authentication schemes for code dissemination supporting per-hop dynamic packet size, which implies that original packets in the first hop can be split or merged in the other hop depending on the link quality. Our paper starts from the fact that code dissemination schemes supporting dynamic packet size can optimize the energy efficiency by reducing transmission overhead based on the link quality. Under this environment, our schemes reinforce the security, especially source authentication which guarantees both authenticity and integrity for a new code image. According to our survey on existing works, source authentication for code dissemination supporting dynamic packet size has never been researched earlier. In this paper, three source authentication schemes are suggested as follows:
Simple packet aggregation (SPA)
Message authentication codes (MACs) based source authentication (MBSA)
Bloom filter based source authentication (BFBSA)
These schemes are very efficient in terms of computation overhead since they mainly perform lightweight hash operations and require only one public key cryptographic operation during code dissemination. In addition, our schemes can work with any code dissemination scheme supporting dynamic packet size. The main contributions of the paper are as follows.
We identify the problem of existing source authentication schemes which does not support code dissemination with per-hop dynamic packet size. According to our survey on existing works, our work is the first attempt to delve into source authentication for code dissemination with dynamic packet size.
We propose three source authentication schemes to address the proposed problem with smaller energy consumption. We accomplish our objective by combining a variety of cryptographic functions such as the hash functions, digital signatures, and the Bloom filter.
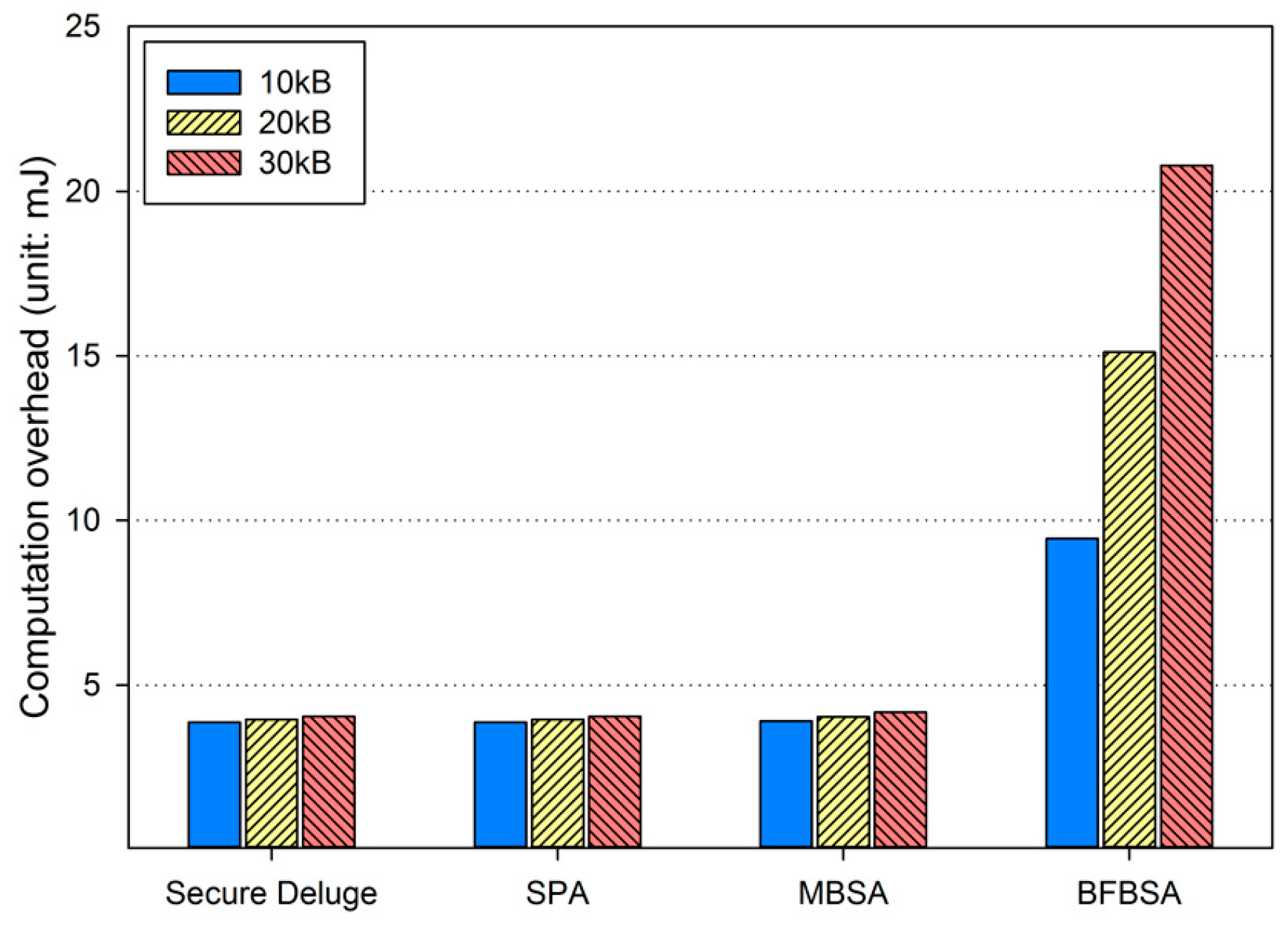
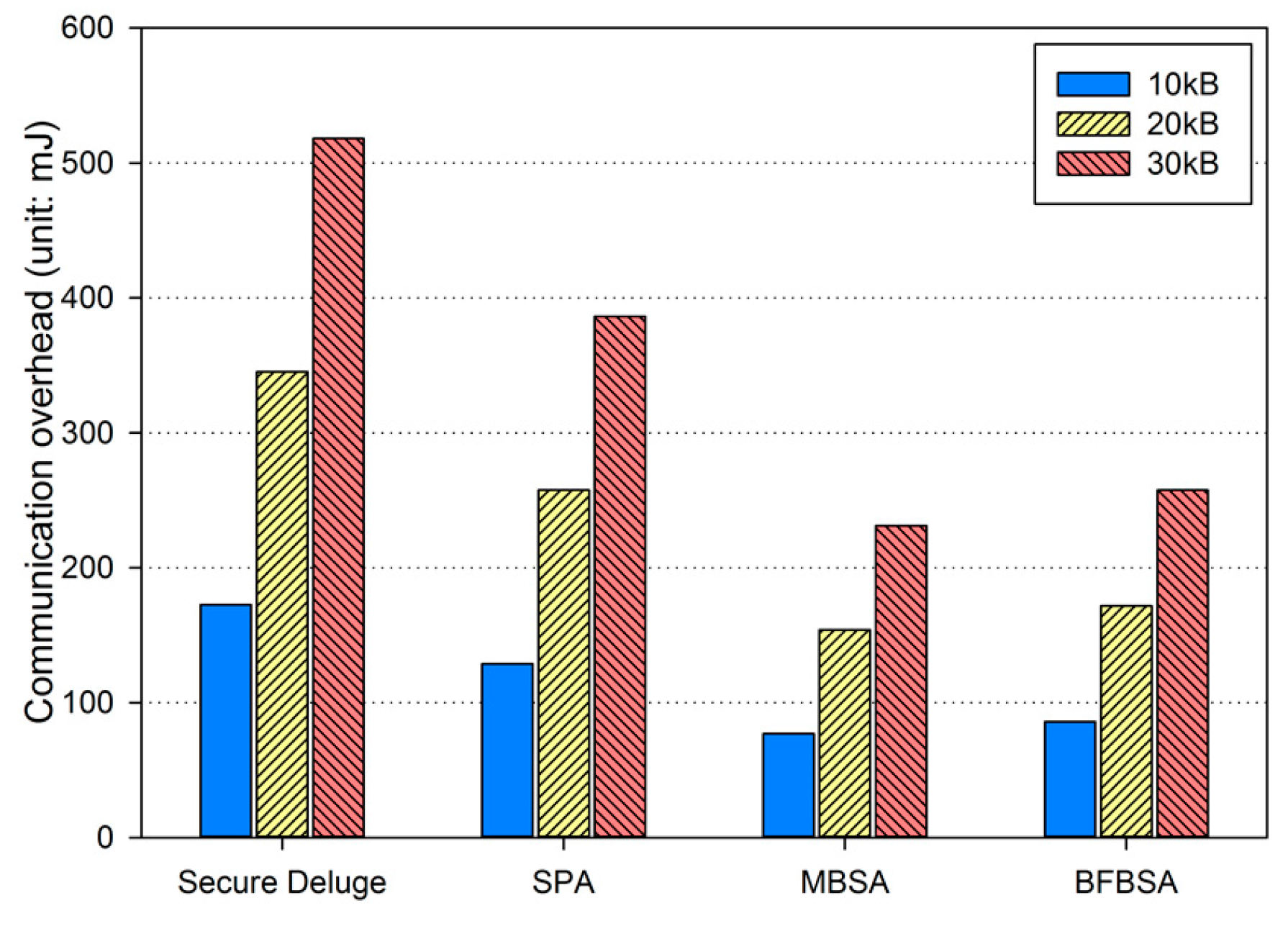
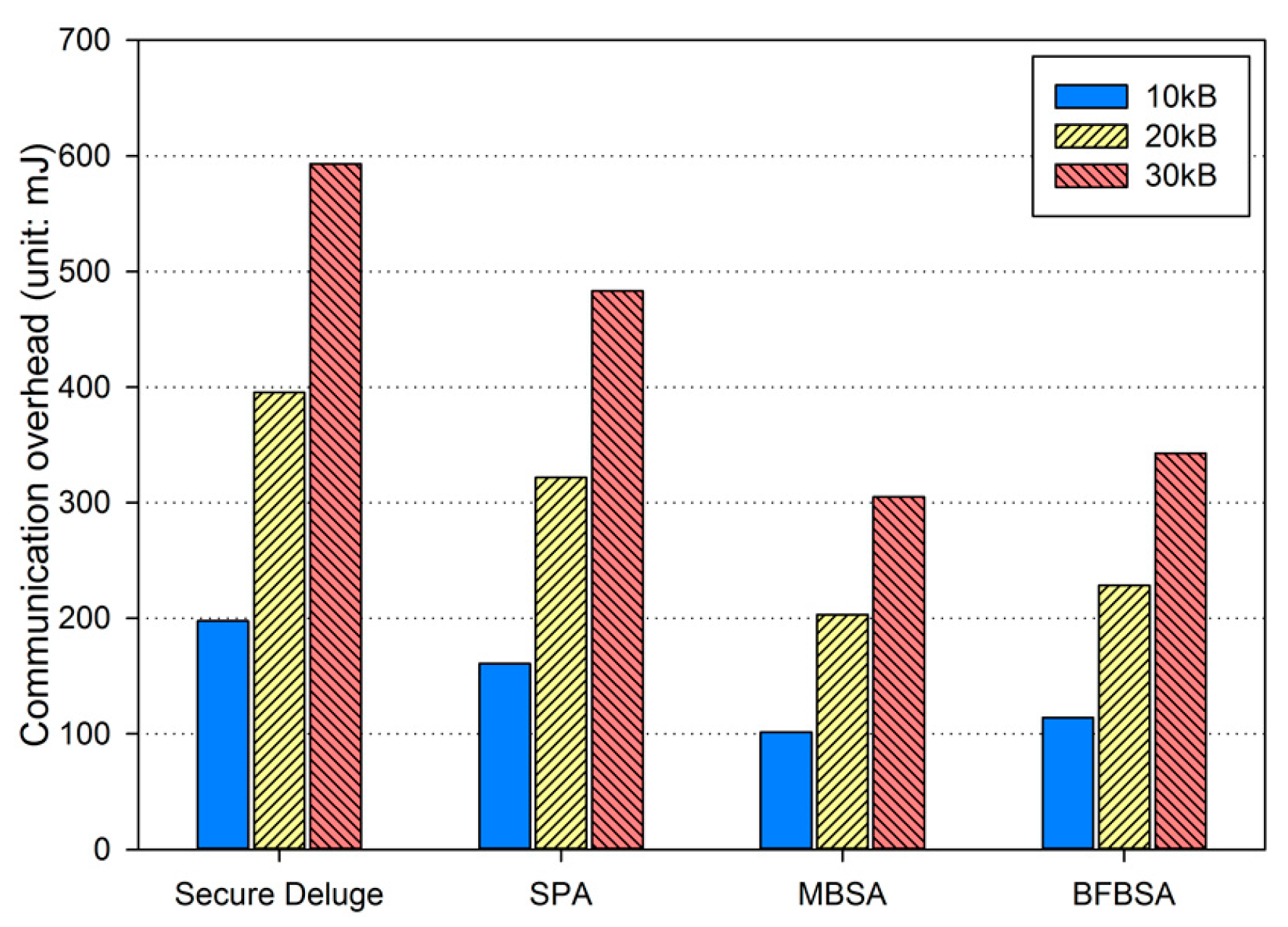
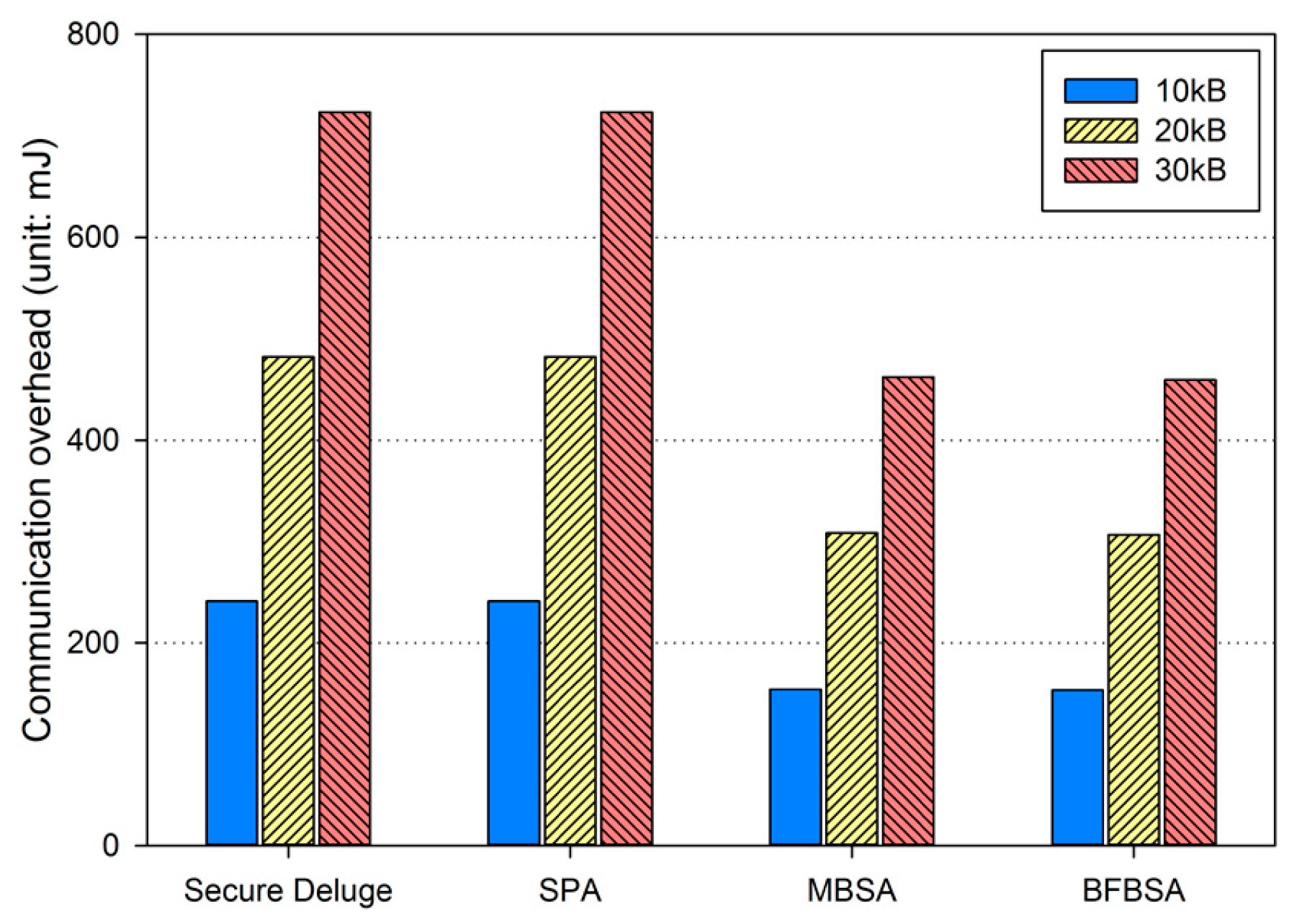
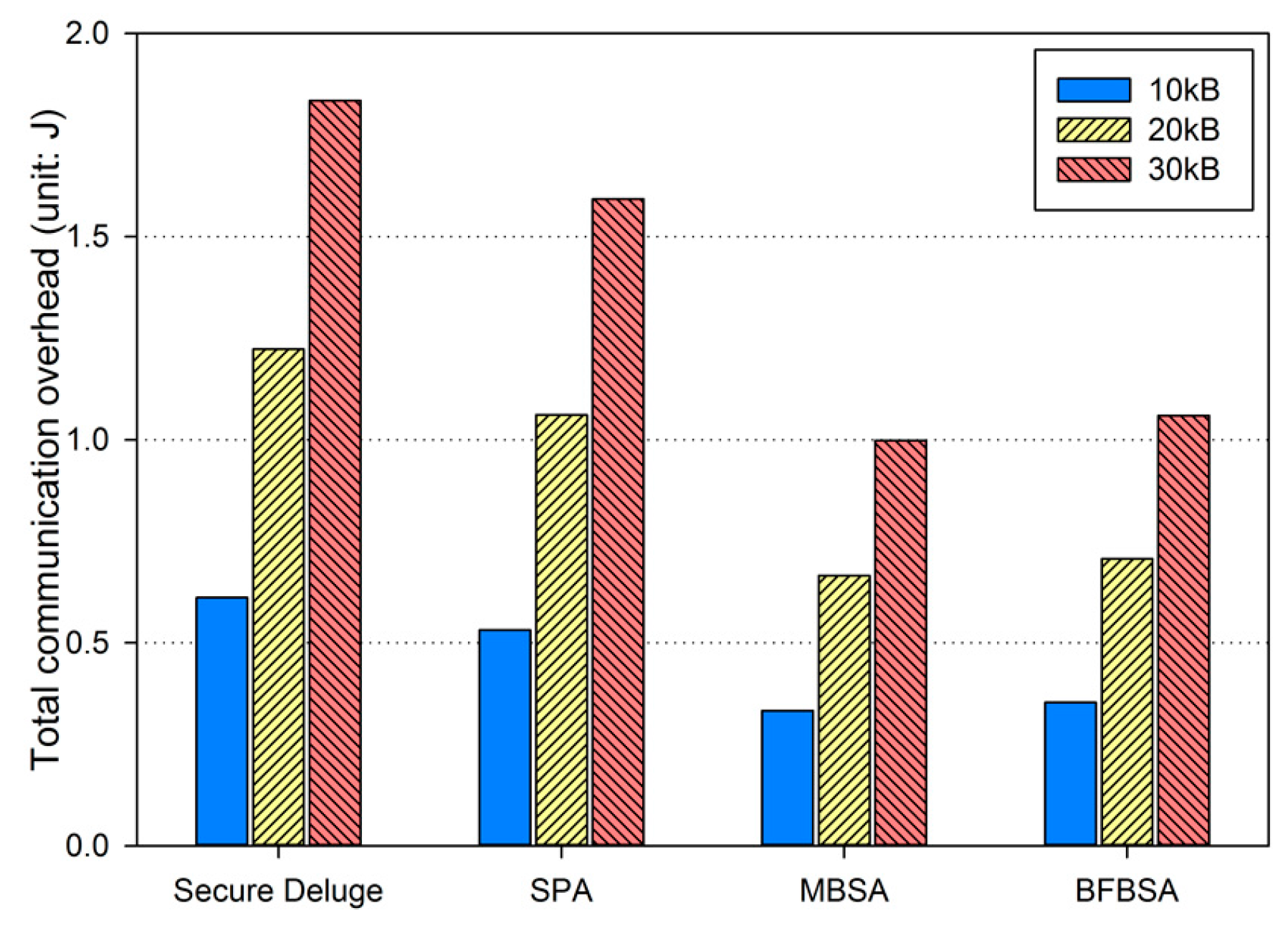
We analyze our work in terms of security and performance. More specifically, we discuss the authenticity, resilience to node capture attacks and denial-of-service (DoS) attacks in detail, and then present performance analysis with regard to computation and communication overhead.
Compared with our previous work [
18], this paper has three major extensions which include the extensive survey on related works, the clear definition of the problem, and the detailed analysis on computation and communication overhead of our work. The rest of the paper is organized as follows: in
Section 2, we describe the related works in detail.
Section 3 defines the problem to be resolved in this paper. Some preliminaries prior to our proposal are presented in
Section 4. In
Section 5, we propose three source authentication schemes in detail. After analyzing our schemes in
Section 6 and
Section 7,
Section 8 concludes the paper.
2. Related Work
One of the most popular code dissemination protocols in WSNs is Deluge [
19], which is the de facto standard [
1,
4,
5,
10,
12,
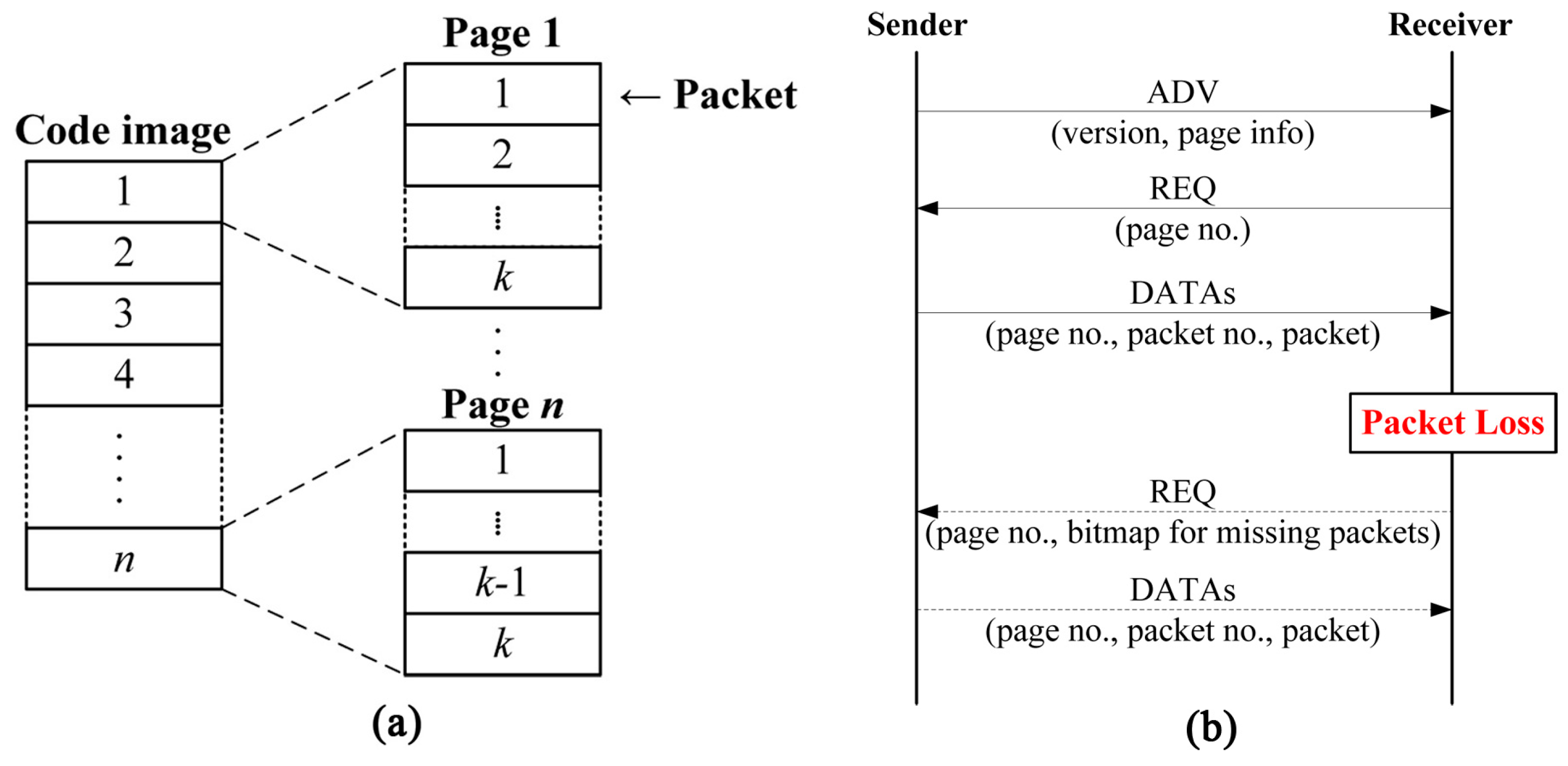
13] and has already been implemented in TinyOS. As shown in
Figure 1a, Deluge splits the code image into fixed-size pages, each of which is then divided into fixed-size packets for pipelining and spatial multiplexing. Deluge uses a three-way handshake to transmit these packets for reliable delivery. The sender first broadcasts an advertisement (ADV) which includes the current version of the code image and page information. Upon receiving the ADV, the receiver sends a request (REQ) back to the sender for the specific page. The sender then begins to transmit data packets (DATAs) for the requested page. If the receiver does not receive all packets within the page successfully, it asks the sender for lost packets by sending a REQ indicating the specific lost packets within the page.
Figure 1b shows the operation of Deluge. Even though Deluge itself supports fixed-size packets only and does not take security into account, most of non-secure and secure code dissemination protocols are built on the basis of Deluge.
To enhance the energy efficiency, a few works on dynamic packet size control have been introduced in the field of WSNs. There is definitely a tradeoff between using large-size packets in the good channel condition to reduce the header overhead and using small-size packets in the bad channel condition to reduce packet error rates (PER). DPLC [
15] is an iterative algorithm to find an optimal packet size using the lightweight and accurate link estimation method. ECD [
16] adapts the packet size depending on the 1-hop link quality for efficient code dissemination. Plena [
17] is a packet size adaptation scheme using error estimating codes for WSNs. All of these schemes significantly conserve energy by adapting the packet size to the link quality. By integrating these schemes with existing code dissemination protocols such as Deluge, we can build an adaptive code dissemination scheme which dynamically adjusts the packet size depending on the link quality, thereby reducing the energy consumption. As it will be clarified in
Section 3, our goal is to provide source authentication for these new kinds of code dissemination schemes where the packet size can be different in each hop.
Source authentication in WSNs has been addressed by μTESLA [
14] and digital signatures. μTESLA provides source authentication by using a one-way key chain and a delayed key disclosure technique. Since the BS only knows the current key which is disclosed after broadcasting messages, the receivers can assure that the messages are from the real BS by verifying the one-way key as
h(
Ki+1) =
Ki where
Ki and
Ki+1 are a previous key and a current key, respectively. μTELSA is very efficient since it only performs symmetric key cryptographic operations. However, μTESLA have a critical shortcoming that it must buffer all messages until the key is distributed, thus it is subject to DoS attacks which fill the buffer of the receiver by flooding it with false messages. Furthermore, since the intermediate nodes do not know the key, they cannot adjust the packet size which means that μTESLA only supports fixed-size packets in each hop.
Digital signatures provide source authentication by simply signing each message with the private key of the BS. The receivers can assure the authenticity by verifying the received message with the public key of the BS. In contrast to μTESLA, digital signatures provide immediate authentication, thus they are strong to DoS attacks since there is no need to buffer messages. However, digital signatures are still heavy to resource-constrained sensor nodes even though Wander et al. [
20] showed that public-key cryptography (PKC) is feasible on the sensor node by using elliptic curve cryptography (ECC). Using one digital signature for the entire code image as presented in [
21] can be a candidate for providing source authentication because it not only addresses the computation overhead of digital signatures but also supports variable-size packets. However, since the digital signature is computed over the entire code image, it cannot be verified until all packets in the code image are completely received, which leads to the following problems. First, if the verification fails, all packets must be discarded because the receiver cannot identify which each packet is correct or not. This incurs the waste of the energy which is the most important resource in WSNs. Second, an attacker can easily disable the receiver by making the buffer of the receiver full by sending a lot of spoofed messages since the receiver does not identify each packet and thus keep all messages to make up the entire code image.
Due to the property that a code image is available prior to dissemination, existing secure code dissemination schemes in WSNs provide source authentication in a different way from μTESLA and digital signatures by using hash functions such as the hash chain or the Merkle hash tree. Secure Deluge [
1] uses a hash chain as depicted in
Figure 2. After the code image is divided into packets in the same way as Deluge, the hash is computed from the last packet and appended to the end of the previous packet. The procedure is repeated until the hash on the first packet is computed. The first hash (
h1,1 in
Figure 2) is then transmitted in advance after signing with a private key of the BS. Upon receiving the message, the receiver verifies the digital signature and stores the hash in order to use for authenticating the subsequent packet. The subsequent packet is verified by comparing the previously received hash and the hash on the currently received packet as
h1,1 =
h(
Pkt1,1|
h1,2). Secure Deluge is highly efficient since it uses only one digital signature and inexpensive hash functions. Secure Deluge also provides immediate authentication unlike μTESLA, and it has lower overhead than other existing secure code dissemination schemes because other existing secure code dissemination schemes have additional overhead such as the Merkle hash tree and one-way key chains for enhanced features such as confidentiality and loss-resilience. However, Secure Deluge is still vulnerable to DoS attacks in case of out-of-order packet delivery and does not provide source authentication for the variable-size packets.
Seluge [
2] provides immediate authentication for code dissemination packets using a Merkle hash tree which includes the hash images of packets in page 1. The packets in page 1 are authenticated by the hash images of the Merkle hash tree, and the subsequent packets are authenticated by the hash chain like Secure Deluge. Sluice [
3] is similar to Secure Deluge except that Sluice uses the page-level hashes while Secure Deluge uses the packet-level hashes. However, the page-level hashes are more vulnerable to DoS attacks than the packet-level hashes since packets must be buffered for making up a page. Tan et al. [
4] provides not only immediate authentication using the hash chain but also confidentiality by encrypting each packet with a session key derived from the hash chain. LR-Seluge [
5] enhances loss resilience on the basis of Seluge by using a fixed-rate erasure code. DiCode [
6] is almost the same as Seluge but it supports the distributed control for code dissemination which means that multiple authorized network users are allowed to update a code image without involving the BS. Tan et al. [
7] uses multiple one-way key chains instead of the hash chain to provide immediate packet authentication. It does not use even one PKC operation, but it incurs key distribution overhead and the communication overhead due to large packet size. SDRP [
8] is almost identical to DiCode except that SDRP uses identity-based cryptography rather than RSA for authenticating the Merkle hash tree. Deng et al. [
9] also takes a similar approach to Seluge by using the Merkle hash tree. Bohli et al. [
10] provides an efficient source authentication by combining the Merkle hash tree and the hash chain. Flexicast [
11] provides an energy-efficient authentication through authenticated fingerprints and network-wide attestation. Chen et al. [
12] provides source authentication by using the Merkle hash tree and provides confidentiality through effective XORs coding and multiple one-way hash chains. SecNRCC [
13] provides an immediate authentication with confidentiality consideration by combining the hash tree and the one-way key chain. SIMAGE [
22] is a secure code dissemination which adapts to the link quality through dynamic packet sizing. Even if SIMAGE provides confidentiality and integrity between neighboring nodes, it does not provide source authentication. All of these schemes, which we have discussed in this section, do not provide source authentication for code dissemination supporting dynamic packet size in each hop. In contrast to these existing schemes, our works provide efficient source authentication for code dissemination supporting per-hop dynamic packet size.
3. Problem Definition
This paper is motivated by recent works on dynamic packet size control in WSNs which tries to minimize the energy consumption by dynamically adapting packet size depending on the link quality [
15,
16,
17,
22,
23]. Large packets can improve the energy efficiency by keeping the overhead of the header low, but at the same time large packets can reduce the energy efficiency by raising PER. In contrast, the use of small packets leads to low PER, but is not good in terms of the header overhead. Therefore, these works adjust the packet size appropriately depending on the link quality.
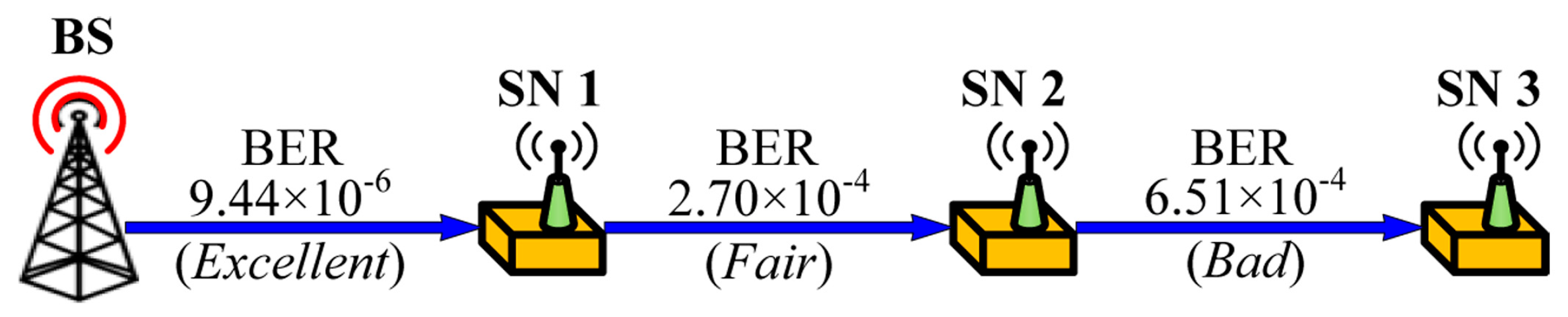
Another important aspect of code dissemination is to guarantee the authenticity of the distributing node (e.g., BS) and the integrity of the code image which is normally ensured by the authentication tokens, such as MACs and digital signatures, attached to each packet by the source node. It is important to note that source authentication, not intermediate nodes authentication, is required during code dissemination since the sensor nodes are vulnerable to node capture attacks. When applying existing source authentication schemes into code dissemination supporting dynamic packet size, a new problem arises as shown in
Figure 3 since the packet size can be different in each hop.
The BS first determines the packet size on the basis of the link quality between the BS and the sensor node 1. Once the packet size is determined, the BS generates an authentication token which provides the authenticity and the integrity of the packet, and sends the token with the packet to the node 1. Upon receiving the packet, the node 1 verifies the authentication token using a shared key with the BS or a public key of the BS according to the used cryptography. To forward the packet to the node 2, the node 1 determines the packet size depending on the link quality between the node 1 and the node 2. In this case where the optimal packet size is different from that of the first hop as shown in
Figure 3, the node 1 cannot generate a valid authentication token of the BS for the packet with the optimal size since the key for generating an authentication token is only known to the BS.
Therefore, we define the problem to be resolved in this paper as “providing source authentication under the environment where the packet size changes in each hop during code dissemination in order to improve the energy efficiency.”
5. Proposed Source Authentication Schemes
In this section, we propose three source authentication schemes for code dissemination supporting dynamic packet size. Source authentication, the most significant security requirement for code dissemination in WSNs, ensures that a new code image is really sent by the BS and not altered in transit. Note that, for simplicity, we explain our schemes in the first hop which is between the BS and the neighbor node but this procedure continues to all sensor nodes in the WSN over multihop communications.
5.1. Simple Packet Aggregation (SPA)
The simplest way to support source authentication for code dissemination with variable packet size is to simply aggregate packets as depicted in
Figure 5. We employ a Secure Deluge [
1] which uses a hash chain. In this scheme, a source can precompute a hash value of the next packet and embed it in the current packet since a new code image is built prior to the transmission. Then, a receiver can authenticate the next packet using the previously received hash value.
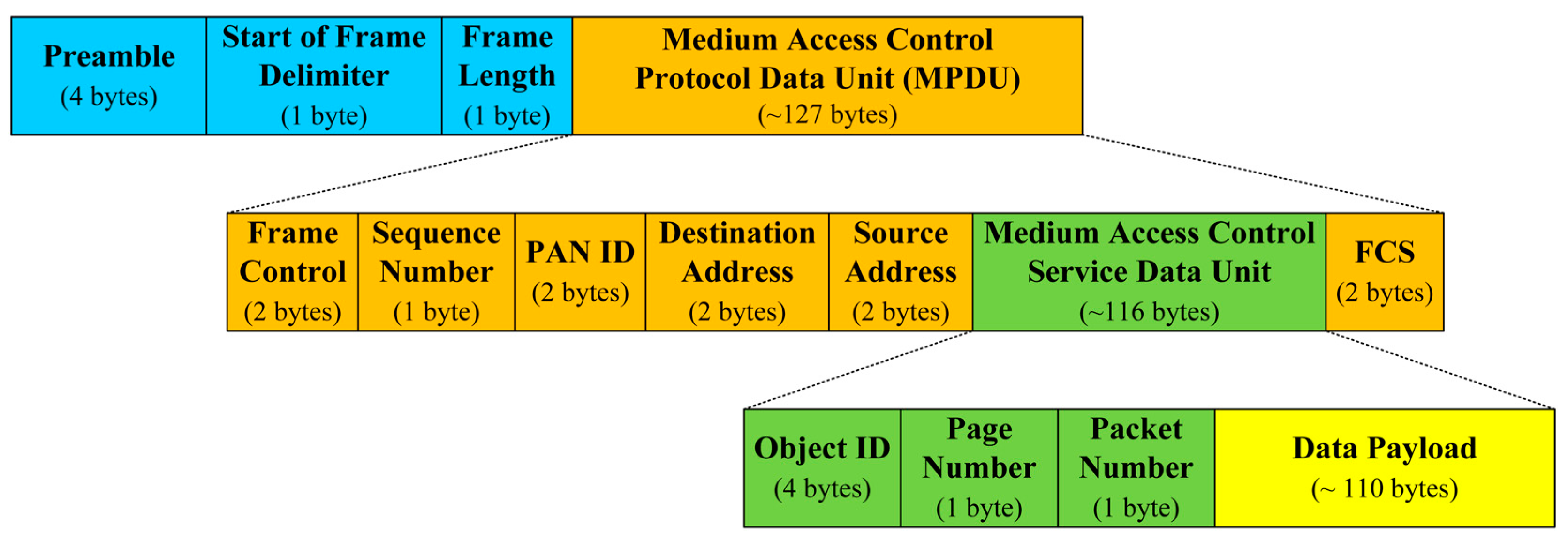
When a new code image is available, a BS splits it into pages which are further divided into packets with a fixed size. All packets are indexed sequentially, and a hash value is calculated using the next packet on the reverse order. The hash value is then appended to the end of the current packet, thereby forming a
basic packet which is the basic unit to be transmitted as follows:
where
Pkti,j is a
j-th packet in Page
i and
hi,j is a hash value on the basic packet containing
Pkti,j.
x and
y are the number of pages in the code image and the number of packets in one page, respectively. Finally, the hash of the first basic packet (
h1,1) is signed by the BS with the BS’s private key to ensure source authentication.
Figure 5a shows how to create basic packets with a hash value.
Once basic packets are ready, the BS first sends a hash value on the first basic packet (
h1,1) with a digital signature (
sig(
h1,1)) to a neighbor node. The receiver first verifies the digital signature of the hash using a BS’s public key preloaded in each sensor node prior to deployment. If the digital signature is valid, the receiver stores the hash value which is used to authenticate the subsequent basic packet. The BS now transmits packets to the neighbor node by aggregating basic packets depending on the link quality as follows:
where
n depends on the link quality. It is worth noting that the
BS can send basic packets without aggregation in severe channel condition. Upon receiving an aggregated packet, the receiver splits it into the original basic packets. This is easy because each sensor node knows the length of a basic packet. After calculating the hash value on the first basic packet, the receiver compares it with the previously received hash value. Denoting the previously received hash value and the currently received basic packet by
hi,j and
BPi,j, the basic packet is considered valid if:
where
H is a hash function. If the hash values are the same, the basic packet is authenticated and the receiver assures that it comes from the real BS and is not modified during transmission. Finally, the hash value in the basic packet is stored to be used to authenticate the next packet. In the same way, all next packets can be verified. When all packets in one page are received, the receiver becomes a new sender. A new sender can send a packet by aggregating basic packets depending on the link quality.
Figure 5b,c illustrates the process of aggregation and verification. The SPA scheme is very simple, but has the hash overhead per basic packet and supports only the multiples of the size of a basic packet.
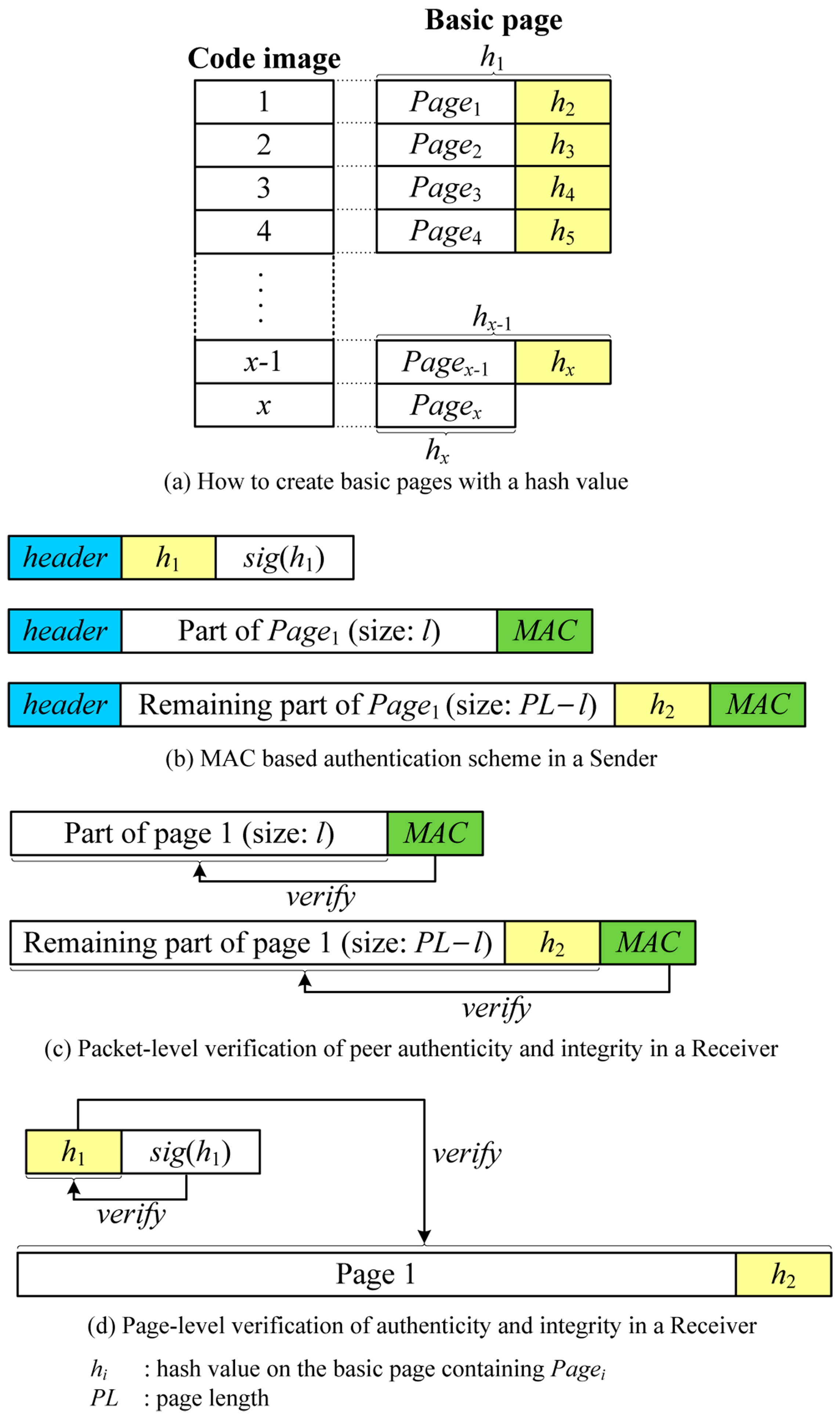
5.2. MAC Based Source Authentication (MBSA)
MBSA makes use of peer-to-peer MACs to support any variable-size packets. However, MACs do not provide authenticity of the BS, which means that MACs authenticate the corresponding node only rather than the BS. To provide an authenticity of the BS, we employ a hash chain per page. Note that the previous SPA scheme uses a hash chain per packet.
In this scheme, a new code image is split into pages only unlike Deluge, after which all pages are indexed sequentially. Similar to the SPA scheme, a hash value on the next page is calculated and appended to the end of the page for the entire image, which together form a
basic page as follows:
where
Pagei is a
i-th page and
hi is a hash value on the basic page containing
Pagei.
x is the number of pages in the code image. Finally, the hash of the first page is signed by the BS with the BS’s private key. This is illustrated in
Figure 6a.
When sending a new code image, the BS first sends a hash value on the first basic page (h1) with a digital signature (sig(h1)) to a neighbor node. The receiver verifies the digital signature of the hash using a BS’s public key and keeps the hash value which is used to authenticate the subsequent basic page. The BS then decides the packet size depending on the link quality and attaches a MAC to the end of the packet using a symmetric key between the BS and the receiver. It is important to note that each node is assumed to have a symmetric key with neighbor nodes using any kind of key distribution schemes.
The resulting packet format for transmission in the MBSA scheme is expressed as follows:
where
payloadi is the part of the basic page which can have any size.
Figure 6b illustrates how to send packets using MACs in the sender. Upon receiving a packet, the receiver node first verifies the attached MAC. If it is not valid, the packet is not from the sender, thus discarded. If the packet is successfully verified as valid, it is parsed and kept in the internal buffer for making up a page. Once all packets in one page are received, the hash of the total page is calculated and compared to the hash value included in the previous page. The entire page is considered authentic if:
where
hi is the previously received hash value for the
i-th basic page and
BPagei is the currently received
i-th basic page.
Figure 6c,d shows the procedure of packet-level verification using MACs and page-level verification using the hash chain, respectively.
The MBSA scheme supports source authentication for fully variable packet size by combining both hop-by-hop authentication via MACs and source authentication via a page-level hash chain. Since this scheme needs only one MAC for variable-size packet, this scheme has less communication overhead than the SPA scheme. Moreover, it is more efficient in terms of energy consumption because it supports fully variable packet size so that it can be optimized for the link quality. The disadvantage of this scheme is that it can be vulnerable to node capture attacks. In this case, attackers can forge malicious packets with the valid MAC. However, it can be easily detected by the page-level hash chain.
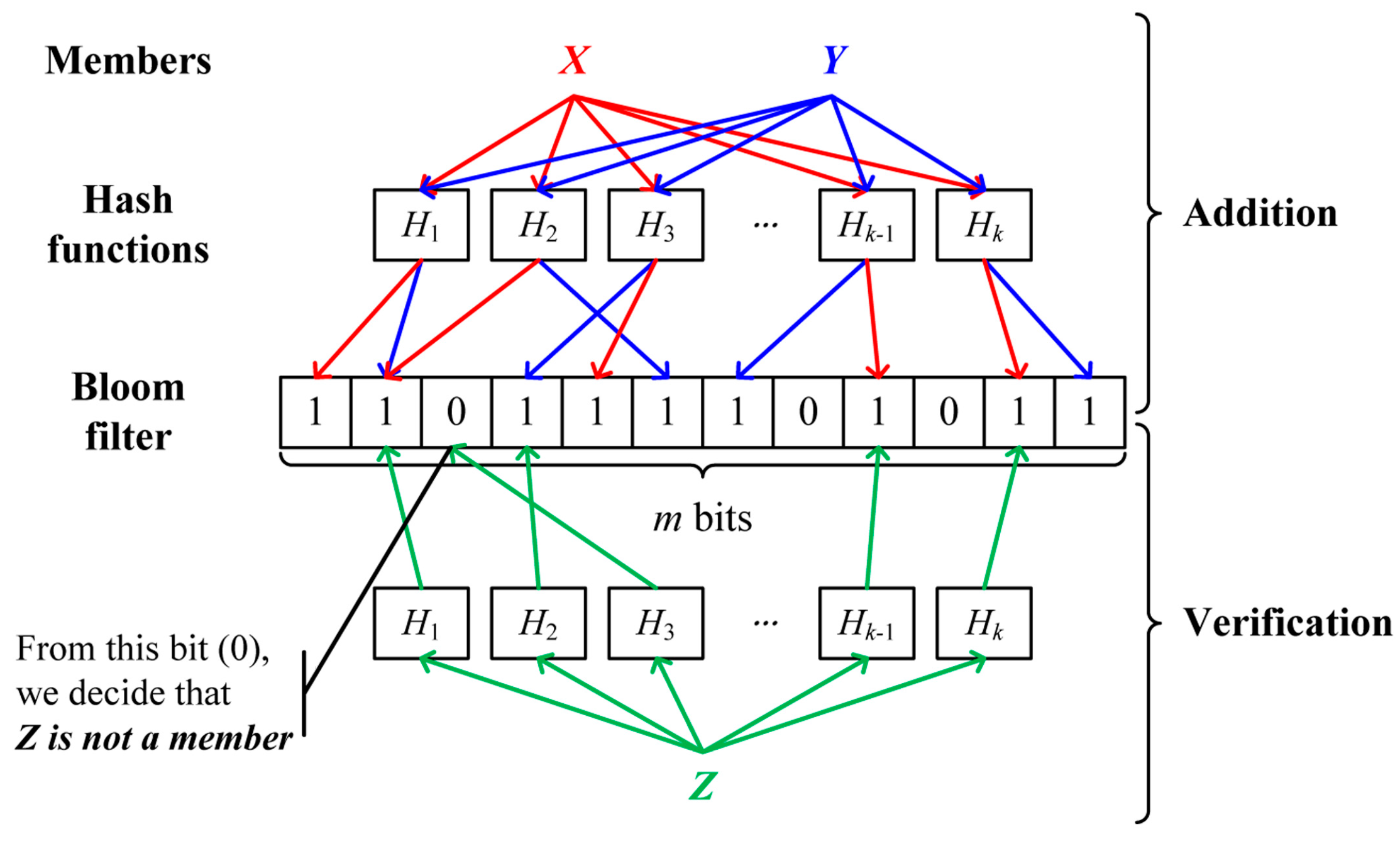
5.3. Bloom Filter Based Source Authentication (BFBSA)
BFBSA takes advantage of a Bloom filter to verify the authenticity of packets. Like SPA, the BS splits a new code image into pages which are further divided into fixed-size packets called basic packets. It is important to note that basic packets in BFBSA is the same as packets while basic packets in SPA consist of packets and a hash value on the next basic packet. The BS then makes a
m-bit length Bloom filter by applying
k different hash functions to all basic packets as follows:
where
BF[] is a
m-bit array indicating a Bloom filter and
Hn is a hash function which maps packets into an integer with a range of 0 to
m-1.
When the Bloom filter is built, the BS broadcasts the entire Bloom filter to all sensor nodes together with a hash value on the first basic page (h1) after signing with a BS’s private key. It is important to note that h1 is used to verify authenticity and integrity of the page for defending against malicious packets due to false positive property of the Bloom filter. After each sensor node verifies a digital signature of the Bloom filter with a BS’s public key, it stores the Bloom filter to authenticate the subsequent packets.
The BS now sends a new code image to the neighbor nodes with variable-size packets, depending on the link quality as follows:
where
n depends on the link quality, and the last packet can be fragmented. It is important to note that unlike previous schemes, there is no overhead for each packet such as MACs and hash values. Upon receiving a packet, the receiver node splits it into basic packets, each of which is then verified using the Bloom filter with
k different hash functions. The basic packet is considered authentic if it satisfies the following equation:
If it fails to pass the test, it definitely is not a valid packet. However, the authenticated packets might be forged packets due to false positive. To overcome this problem, we must adjust
k and
m appropriately which will be investigated in detail in
Section 6. In addition, we add a hash value on the next page to the end of the last packet in each page. After receiving all packets in the page, the receiving node can verify the authenticity of the whole page with the hash value. This entire process is illustrated in
Figure 7.
This scheme incurs storage and communication overhead for the Bloom filter but has no communication overhead in each packet. In addition, this scheme can support fully variable-size packets.
6. Security Analysis
In this section, we evaluate our three source authentication schemes in terms of security aspects, more specifically, authenticity, resilience to node capture attacks and DoS attacks.
6.1. SPA
Security of the SPA scheme depends on the security of hash functions and digital signatures. In general, hash functions are assumed to be secure which means that given y, it is computationally infeasible to find x such that h(x) = y. In addition, a BS is assumed to be always secure, thus the BS’s private key is never exposed to attackers. Hence, a digital signature signed by the BS is always secure which implies that any attacker cannot forge a valid digital signature of the BS. In the SPA scheme, every packet is authenticated by the previously received hash value. Since a hash function is assumed to be secure, the adversary cannot fabric a malicious packet with the same hash value as the previously received hash value. In other words, the SPA scheme can authenticate every packet securely. Now let’s think about the case where a sensor node is captured and controlled by an adversary, who can access and extract all the materials (e.g., hi,j) in the node. However, the only thing that the adversary can do is to drop packets since it is infeasible to fabric a malicious packet to have hi,j. If he modifies packets or injects malicious packets, it will be detected immediately through an invalid hash value. DoS attacks in the hash-chain based authentication scheme refers to the situation where the adversary try to make the buffer of receivers full by sending invalid packets repeatedly so that receivers get crippled. The SPA scheme is vulnerable to DoS attacks since it uses a hash chain containing the hash value of the next packet. If one packet is missing, all the subsequent packets cannot be authenticated and thus the buffer becomes full.
6.2. MBSA
Since the MBSA scheme uses a page-level hash chain, it can authenticate each page just as the SPA scheme authenticates each packet. However, this page-level authentication is vulnerable to DoS attacks because it has to keep all received packets to make up a page. In this scheme, DoS attacks can be circumvented by hop-by-hop authentication using MACs with a symmetric key. If any node without a symmetric key attempts to inject malicious packets, it will be detected by the MAC. Unfortunately, this scheme is susceptible to node capture attacks. Once a sensor node is compromised, all information, including all symmetric keys with neighbor nodes, is disclosed to the adversary. Therefore, the adversary can easily inject malicious packets to the neighbors. However, this can be prevented by the page-level hash (hi) since the adversary cannot fabricate a whole page which has hi. In summary, the MBSA scheme provides an immediate authentication using MACs, thus it is robust to DoS attacks as long as sensor nodes are not compromised. However, the MBSA scheme is weak to node capture attacks since compromised nodes can send forged packets to their neighbors, but the page-level hash constrains the effect within the page.
6.3. BFBSA
Security of BFBSA depends on the probability of false positive. Given the number of basic packets,
N, and a bit array of the Bloom filter with
m bits, the probability
p of false positive, with optimal
k = (
m/
N)ln 2, is as follows [
25]:
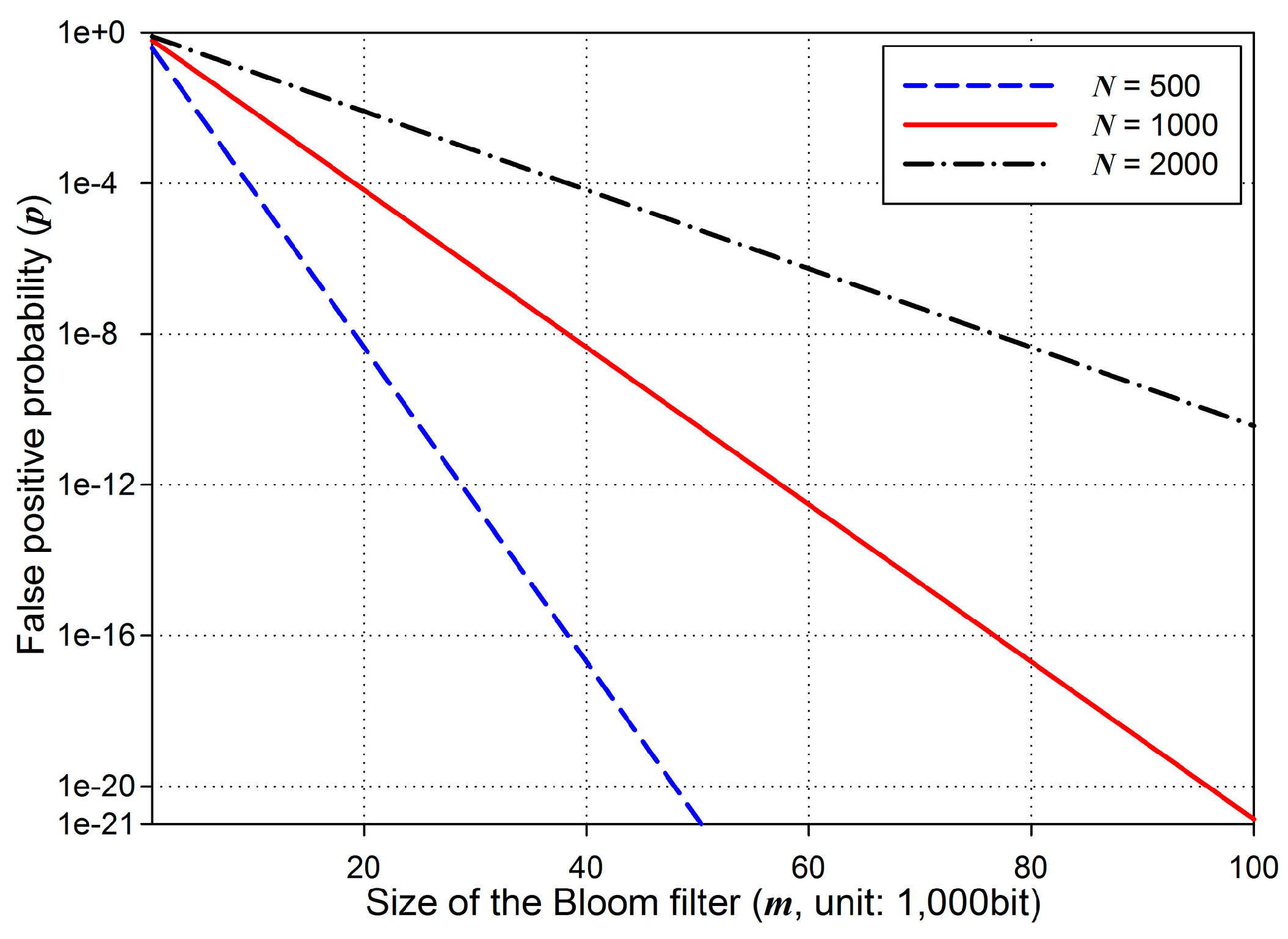
Obviously,
p decreases with lower
N and higher
m as shown in
Figure 8. In code dissemination in WSNs, the number of basic packets,
N, is predetermined according to the size of a new code image. Given
N, the probability of false positive with regard to
m is determined using (10). For example, we assume that
N is set to 1000 packets. When
m is configured as 1000 bits,
p becomes 0.6185 which is very high. However, when
m increases from 1000 bits to 10,000 bits,
p becomes 0.0082 which is much less than 0.6185. Furthermore, when
m is set to 100,000 bits,
p is 1.36 × 10
−21. This means that approximately 2
69 elements have to be generated for an attacker to fabric a false positive packet. Therefore, the BFBSA scheme can authenticate every packet securely with a proper configuration of
m. We set
m/
N to 92 targeting at the false positive probability of 6.36 × 10
−20 which is assumed to be secure in [
26]. In addition, even if a false positive occurs, it can be detected by the page-level hash. Regarding node capture attacks in BFBSA, compromised nodes cannot do anything but to discard packets since it is infeasible for them to build forged packets to pass the Bloom filter and the page-level hash. Moreover, BFBSA is resilient to DoS attacks since it provides an immediate authentication per packet.