Wireless Sensor Network Security Enhancement Using Directional Antennas: State of the Art and Research Challenges
Abstract
:1. Introduction
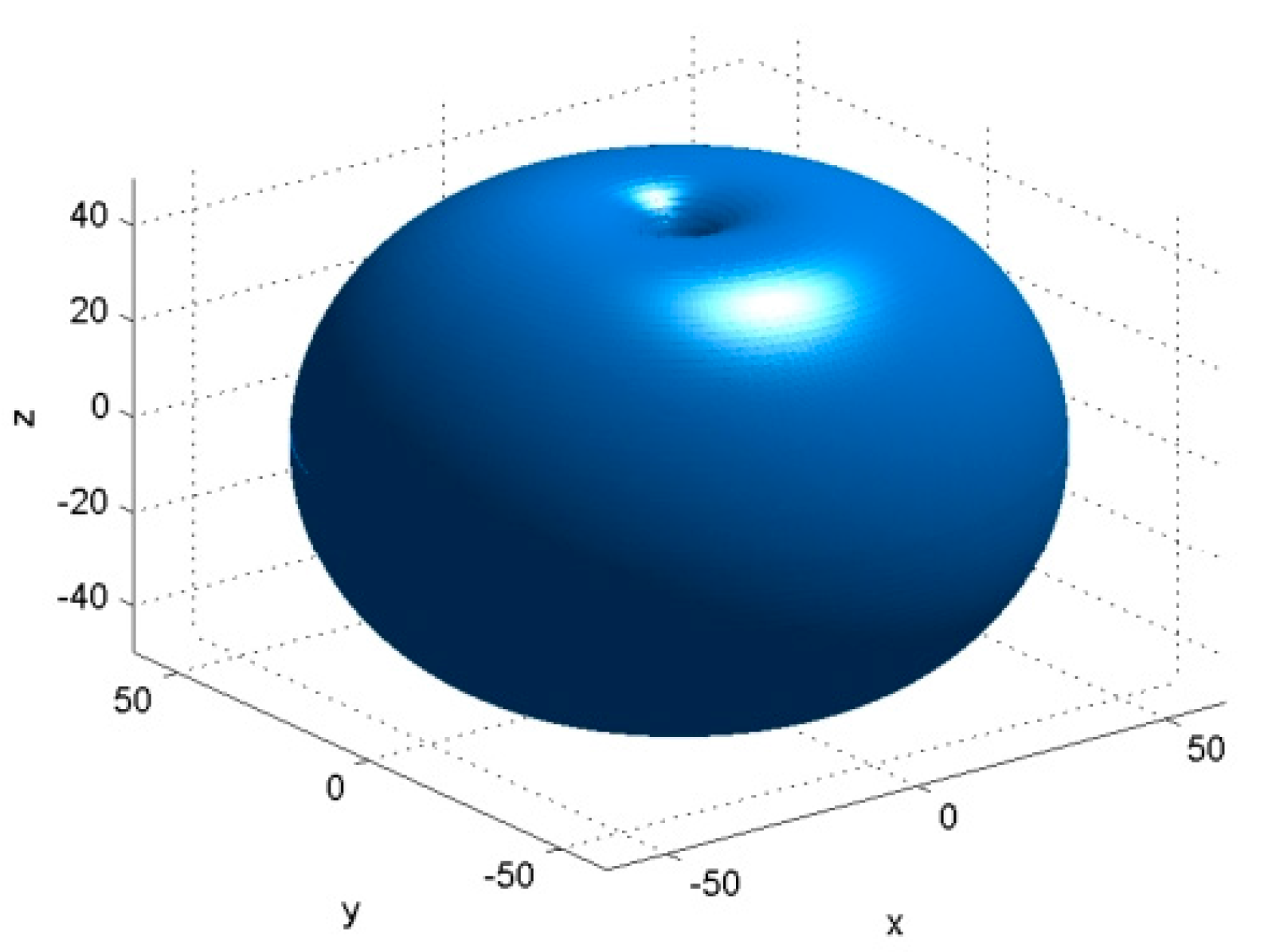
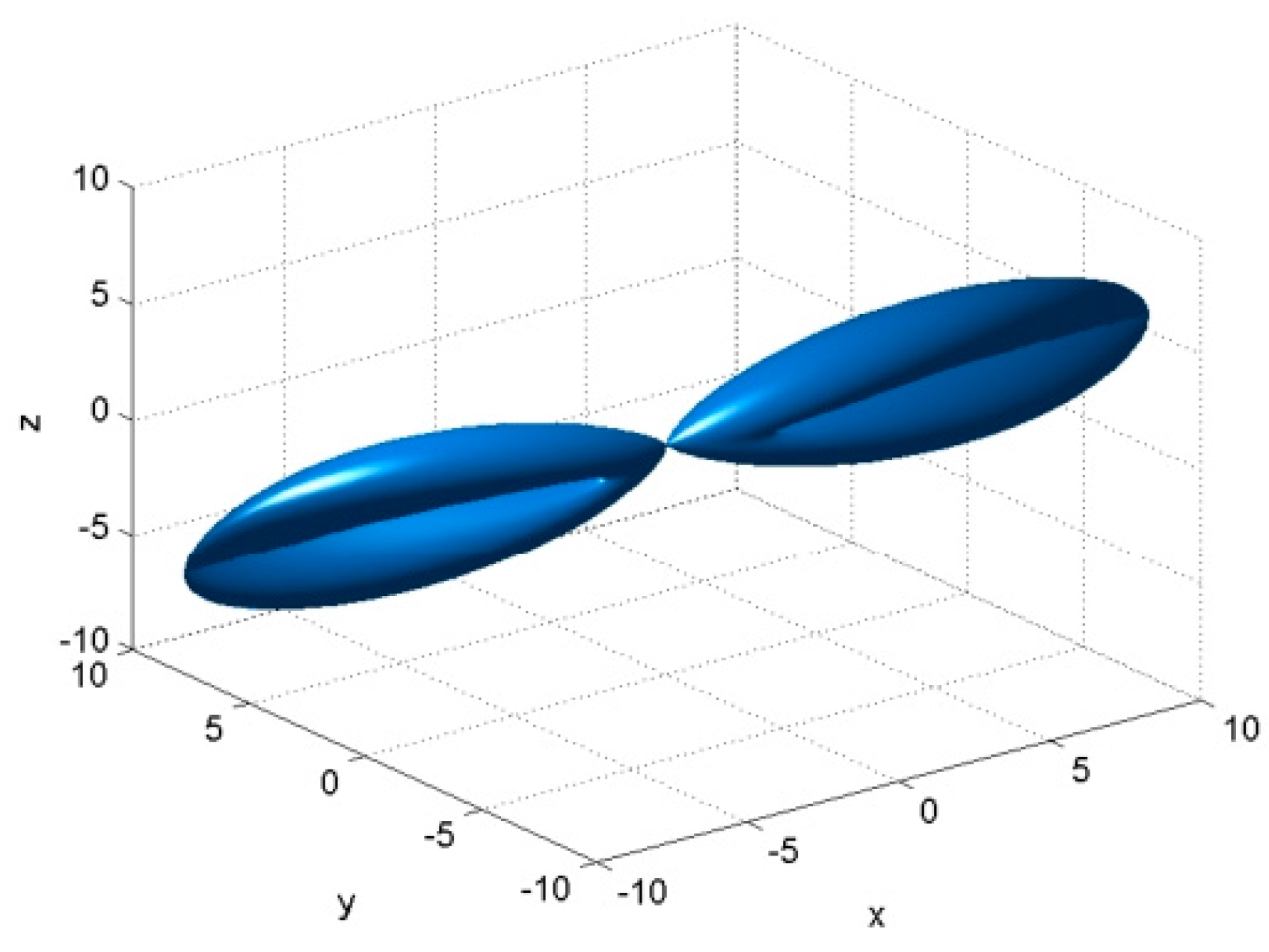
2. Directional and Omnidirectional Antennas—A Brief Comparison
- Improved energy consumption; the wireless data transmission is proved to be the most energy-intensive operation of a sensor node [10,11]. By focusing their transmitted power in the needed direction, directional antennas have the potential to reduce the energy usage [12] and therefore to extend sensor nodes’ lifetime.
- Longer transmission range; reporting information inside WSNs using fewer hops [13,14] or reducing the risk for nodes or groups of nodes to become isolated (due to malfunctions, battery depletion or malicious attacks) [15] can significantly improve the WSN performance, when using directional antennas.
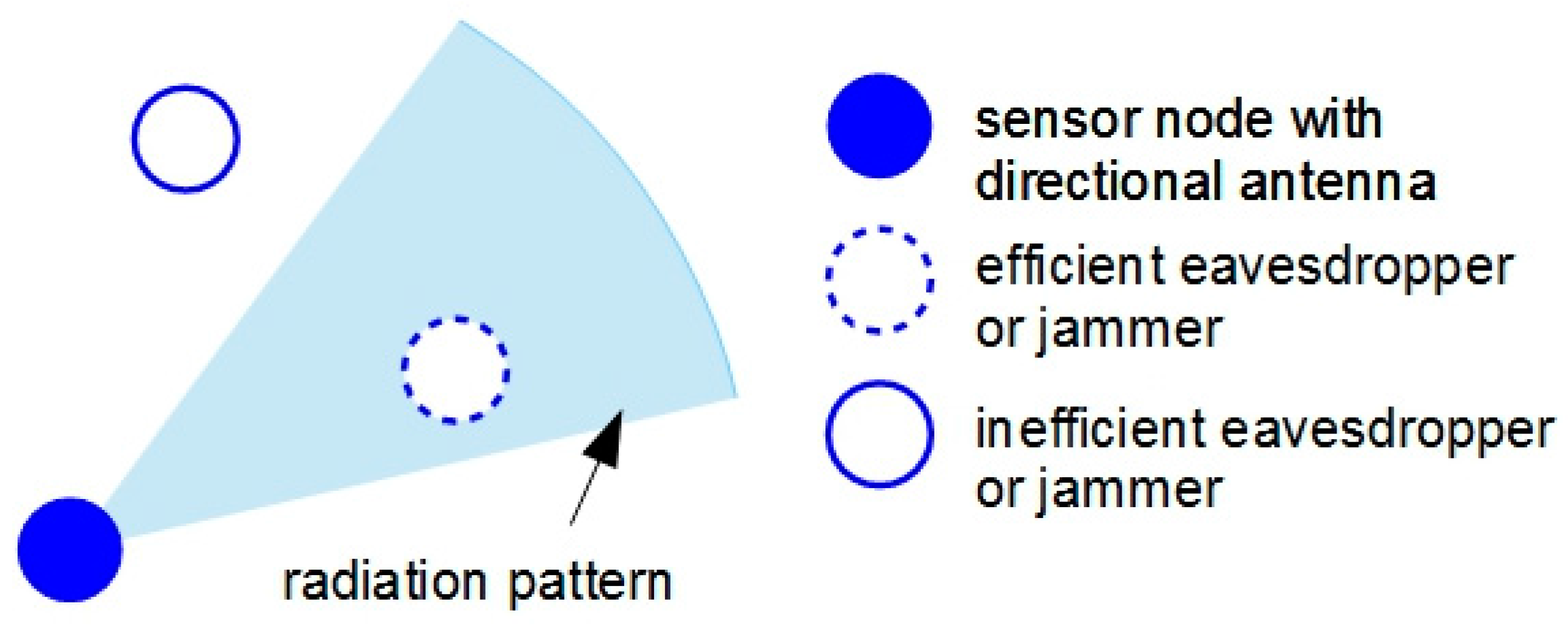
- Higher security; derived either from their immunity to eavesdroppers [16] or jammers [17] placed outside their narrow radiation region or from the feature of determining the exact position of a sender node using the signal’s angle of arrival [18], the directional antennas can mitigate the risk of security attacks.
3. Directional Antennas Suitable for WSN Nodes
4. Security Benefits of Directional Antennas in WSNs
4.1. Eavesdropping
4.2. Jamming
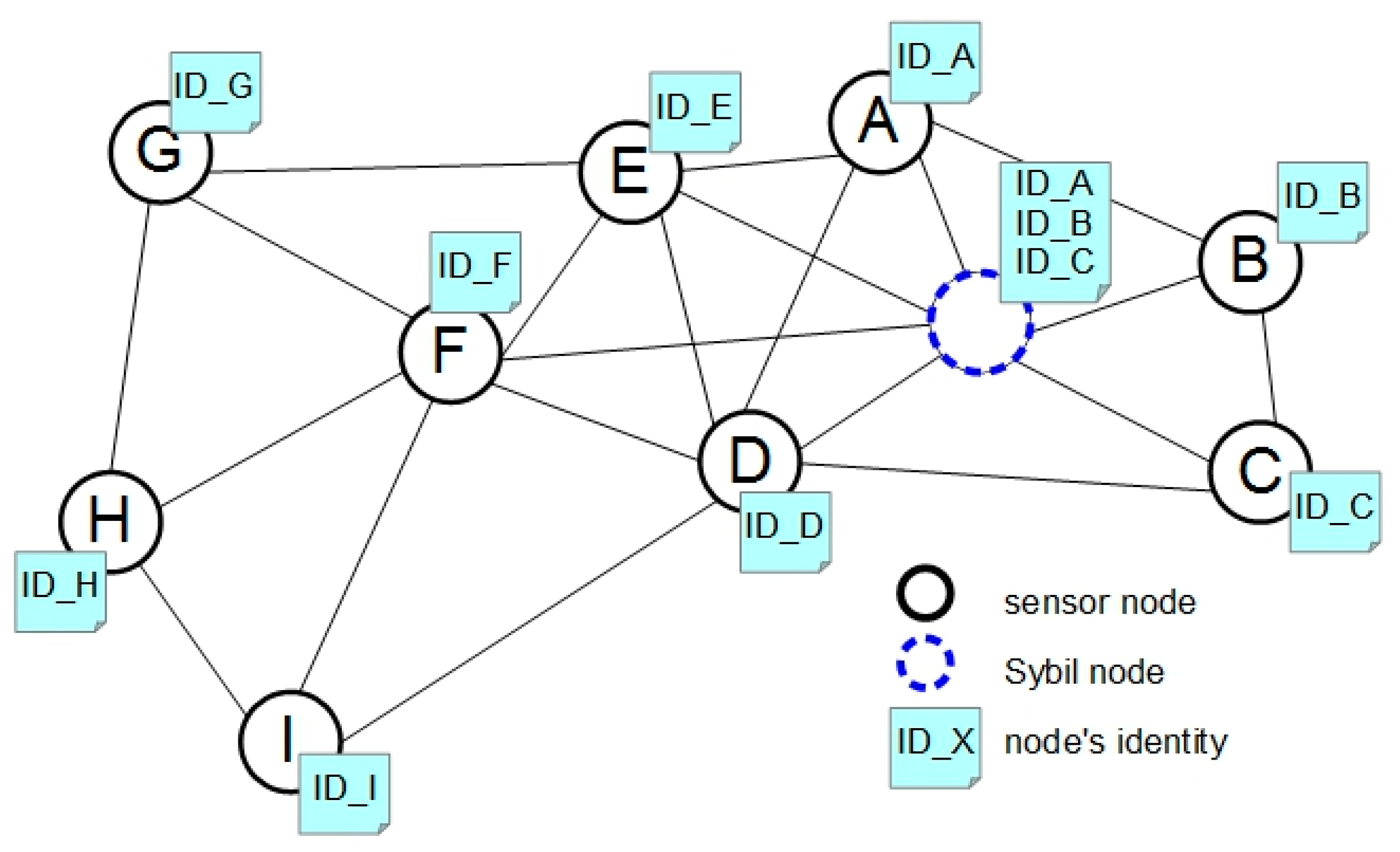
4.3. Sybil Attack
4.4. Wormhole Attack
- (a)
- The directional neighbor discovery protocol. The proposed mechanism does not rely on any type of cooperation among nodes. The protocol works in three consecutive steps: (i) a node (called announcer) of a just-deployed sensor network sends a HELLO-type message including its ID; (ii) all nodes that receive the HELLO message reply with an encrypted message that basically contains their node ID and the zone where the message was received. The encryption process is done using previously established keys, stored on each node together with corresponding neighbor ID; and (iii) the announcer will decrypt the message verifying the node ID and that the zone reported by the neighbor is opposite to its zone. After the neighbor discovery process is finished, the node will ignore any kind of messages coming from nodes that do not belong to the neighbor list. Even its effect on mitigating the wormhole attacks is reduced, the protocol is envisioned by the two authors to represent a strong basis for the following two.
- (b)
- The verified neighbor discovery protocol is based on sharing information between network nodes. It can stop attacks in which the malicious entity controls the two wormhole endpoints and when the targeted nodes have no direct communication link (are at least two hops distant). The mechanism is based on directional neighbor discovery protocol which is enhanced by a verification procedure done using verifiers (network nodes that are not in opposite direction from the wormhole endpoints). The role of verifier-nodes is to check the legitimacy of announcers.
- (c)
- The strict neighbor discovery protocol adds a supplementary requirement (the verifier region must be empty when two nodes are out of radio range) for verifier-nodes to cope with Worawannotai attack (the malicious entity convinces two close and non-neighboring nodes that they are neighbors [53]), too.
5. Challenges and Perspectives
- (i)
- designing small sized, reasonably priced and energetic-efficient directional antennas able to be integrated in highly resource-constrained sensor nodes;
- (ii)
- (iii)
- providing network protocols able to assure self-localization, self-configuration, self-synchronization and self-optimization in the case of randomly deployed sensor networks using aerial scattering or other similar procedures;
- (iv)
- (v)
- adapting the in-network data and message aggregation mechanisms to the directional antenna-based topology of WSN;
- (vi)
- designing customized topology control mechanisms to increase effective network capacity and conserve energy; and
- (vii)
- providing appropriate QoS models incorporating both communication-related parameters (e.g., delay, packet delivery ratio, jitter, etc.) and sensing-related parameters (e.g., network sensing coverage, probability of missed detection of an event, sensor failure probability, etc.).
- (a)
- Involving directional antennas in coping with other malicious attack type. While the configuration of their radiation pattern can inherently mitigate the effects associated to eavesdropping or jamming, the directional antennas can be involved in identifying, mitigating or even eliminating the security risks associated to other malicious attacks using angular information (signal’s direction of arrival). For this, the key word is “localization”, so any malicious attack that can be addressed using localization-based techniques (i.e., position verification) can be a valid target for future research. Relevant examples in this context are the selective forwarding attack [68] or the Hello flood attack [69].
- (b)
- Using directional antenna-based localization mechanisms to detect security attacks on other localization schemes. The WSN’s localization infrastructure is susceptible to an assortment of malicious attacks [70] that can endanger the network’s proper functioning. Effective localization schemes based on the use of GPS devices or lateration-based algorithms can be automatically validated using angulation-based approaches relying on intrinsic angular information provided by directional antennas.
- (c)
- Eliminating the consequences of several attacks by benefiting from the longer transmission range of directional antennas. A concrete example can be the case of sensor nodes or groups of sensor nodes isolated from the rest of the network due to various malicious attacks (e.g., jamming, node capturing attack, resource depletion attack, etc.). In this kind of situation the nodes can find alternative paths to regain the connectivity to the rest of WSN by contacting nodes that are further away.
- (d)
- Using sensor nodes with both directional and omnidirectional antennas to solve complex security issues inside WSN. Such an approach could combine the potential advantages brought by the two antenna types. In this case, strategies to switch from one type of antenna to the other have to be design in order to maximize the WSN capability to timely discover and eliminate the security risks.
- (e)
- Coordinating the mechanisms based on the use of directional antennas with other security related technique. Coping with the increased diversity of security threats that affect wireless sensor networks, demands the use of a complex ensemble of methodologies and protocols. The integration of security mechanisms based on directional antennas in an overall security system it’s not a simple task due to a series of factors including the power, communication and computational constraints, the heterogeneity of sensor nodes, the unattended or hostile nature of the WSN environment, etc.
- (f)
- Extending the research field by addressing the security problems of more complex versions of WSNs, where the sensor nodes are endorsed with mobility (e.g., mobile wireless sensor networks [71] or airborne wireless sensor networks [72]) or where the sensor nodes coexist with other wireless node types (wireless sensor and actuator networks [73] or even wireless sensor, actuator and robot networks [74]).
- (g)
- Fusing information received from directional antennas and from other devices (e.g., sensors) for coping with security threats. In many cases, the network nodes are able to obtain supplementary information that can be used to mitigate the security attack risks. Routing information, list of neighboring nodes together, locations and battery energy levels of neighboring nodes or successive sensor measurements are only few examples of information that can be utilized in this context to mitigate the security risks. For example, multimedia sensor nodes equipped with video and audio capture capabilities can fuse such information with the ones obtained from directional antennas to address security-related issues.
6. Conclusions
Conflicts of Interest
References
- El-Bendary, N.; Fouad, M.M.M.; Ramadan, R.A.; Banerjee, S.; Hassanien, A.E. Smart environmental monitoring using wireless sensor networks. In Wireless Sensor Networks: From Theory to Applications; El Emary, I.M.M., Ramakrishnan, S., Eds.; CRC Press: Boca Raton, FL, USA, 2013; pp. 731–755. [Google Scholar]
- Gholami, M.; Brennan, R.W. A Comparison of Alternative Distributed Dynamic Cluster Formation Techniques for Industrial Wireless Sensor Networks. Sensors 2016, 16. [Google Scholar] [CrossRef] [PubMed]
- Ball, M.G.; Qela, B.; Wesolkowski, S. A Review of the Use of Computational Intelligence in the Design of Military Surveillance Networks. In Recent Advances in Computational Intelligence in Defense and Security; Abielmona, R., Falcon, R., Zincir-Heywood, N., Abbass, H.A., Eds.; Springer International Publishing: Berlin, Germany, 2016; pp. 663–693. [Google Scholar]
- Ohmine, H.; Sunahara, Y.; Matsunaga, M. An annular-ring microstrip antenna fed by a co-planar feed circuit for mobile satellite communication use. IEEE Trans. Antennas Propag. 1997, 45, 1001–1008. [Google Scholar] [CrossRef]
- Şamil, T.; Bekmezci, I. Utilization of Directional Antennas in Flying Ad Hoc networks: Challenges and Design Guidelines. In Wireless Network Performance Enhancement via Directional Antennas: Models, Protocols, and Systems; Matyjas, J.D., Hu, F., Kumar, S., Eds.; CRC Press: Boca Raton, FL, USA, 2015; pp. 365–380. [Google Scholar]
- Pan, C.; Liu, B.; Zhou, H.; Gui, l.; Chen, J. Interest-based content delivery in wireless mesh networks with hybrid antenna mode. In Proceedings of the Sixth International Conference on Wireless Communications and Signal Processing (WCSP2014), Hefei, China, 23–25 October 2014; pp. 1–5.
- Li, C.; Yuan, X.; Yang, L.; Song, Y. A Hybrid Lifetime Extended Directional Approach for WBANs. Sensors 2015, 15, 28005–28030. [Google Scholar] [CrossRef] [PubMed]
- Wong, D.T.C.; Chen, Q.; Chin, F. Directional Medium Access Control (MAC) Protocols in Wireless Ad Hoc and Sensor Networks: A Survey. J. Sens. Actuator Netw. 2015, 4, 67–153. [Google Scholar] [CrossRef]
- Bekmezci, I.; Sahingoz, O.K.; Temel, Ş. Flying ad-hoc networks (fanets): A survey. Ad Hoc Netw. 2013, 11, 1254–1270. [Google Scholar] [CrossRef]
- Raghunathan, V.; Schurghers, C.; Park, S.; Srivastava, M. Energy-aware wireless microsensor networks. IEEE Signal Process. Mag. 2002, 19, 40–50. [Google Scholar] [CrossRef]
- Anastasi, G.; Conti, M.; di Francesco, M.; Passarella, A. Energy conservation in wireless sensor networks: A survey. Ad Hoc Netw. 2009, 7, 537–568. [Google Scholar] [CrossRef]
- Catarinucci, L.; Guglielmi, S.; Patrono, L.; Tarricone, L. Switched-beam antenna for wireless sensor network nodes. Prog. Electromagn. Res. C 2013, 39, 193–207. [Google Scholar] [CrossRef]
- Mottola, L.; Voigt, T.; Picco, G.P. Electronically-switched directional antennas for wireless sensor networks: A full-stack evaluation. In Proceedings of the 10th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON2013), New Orleans, LA, USA, 24–27 June 2013; pp. 176–184.
- Dai, H.N. Throughput and delay in wireless sensor networks using directional antennas. In Proceedings of the 5th International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP2009), Melbourne, Australia, 7–10 December 2009; pp. 421–426.
- Pradhan, N.; Saadawi, T. Energy efficient distributed power management algorithm with directional antenna for wireless sensor networks. In Proceedings of the 34th IEEE Sarnoff Symposium, Princeton, NJ, USA, 3–4 May 2011; pp. 1–6.
- Lakshmanan, S.; Tsao, C.L.; Sivakumar, R.; Sundaresan, K. Securing wireless data networks against eavesdropping using smart antennas. In Proceedings of the 28th International Conference on Distributed Computing Systems (ICDCS'08), Beijing, China, 17–20 June 2008; pp. 19–27.
- Shiu, Y.S.; Chang, S.Y.; Wu, H.C.; Huang, S.C.H.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Patwari, N.; Ash, J.N.; Kyperountas, S.; Hero, A.O.; Moses, R.L.; Correal, N.S. Locating the nodes: Cooperative localization in wireless sensor network. IEEE Signal Process. Mag. 2005, 22, 54–69. [Google Scholar] [CrossRef]
- Dai, H.N.; Ng, K.W.; Li, M.; Wu, M.Y. An overview of using directional antennas in wireless networks. Int. J. Commun. Syst. 2013, 26, 413–448. [Google Scholar] [CrossRef]
- Godara, L.C. Smart Antennas; CRC Press: Boca Raton, FL, USA, 2004. [Google Scholar]
- Chong, N.K.; Leong, O.K.; Hoole, P.R.P.; Gunawan, E. Smart Antennas: Mobile Station Antenna Beamforming. In Smart Antennas and Signal Processing; Hoole, P.R.P., Ed.; WIT Press: Southampton, UK, 2001; pp. 245–267. [Google Scholar]
- Nowicki, D.; Roumeliotos, J. Smart Antenna Strategies. Mob. Commun. Int. 1995, 4, 53–56. [Google Scholar]
- Balanis, C.A. Modern Antenna Handbook; John Wiley & Sons: New York, NY, USA, 2008. [Google Scholar]
- Allen, B.; Ghavami, M. Adaptive Array Systems: Fundamentals and Applications; John Wiley & Sons: Chichester, UK, 2005. [Google Scholar]
- Ahmad, A.; Ahmad, S.; Rehmani, M.H.; Hassan, N.U. A survey on radio resource allocation in cognitive radio sensor networks. IEEE Commun. Surv. Tutor. 2015, 17, 888–917. [Google Scholar] [CrossRef]
- Elkashlan, M.; Duong, T.Q.; Chen, H.H. Millimeter-wave communications for 5G: Fundamentals: Part I (Guest Editorial). IEEE Commun. Mag. 2014, 52, 52–54. [Google Scholar] [CrossRef]
- Roh, W.; Seol, J.; Park, J.; Lee, B.; Lee, J.; Kim, Y.; Cho, J.; Cheun, K.; Aryanfar, F. Millimeter-Wave beamforming as an enabling technology for 5G cellular communications: Theoretical feasibility and prototype results. IEEE Commun. Mag. 2014, 52, 106–113. [Google Scholar] [CrossRef]
- Niu, Y.; Li, Y.; Jin, D.; Su, L.; Vasilakos, A.V. A survey of millimeter wave communications (mmWave) for 5G: Opportunities and challenges. Wirel. Netw. 2015, 21, 2657–2676. [Google Scholar] [CrossRef]
- Hansen, R.C. Electrically Small, Superdirective, and Superconducting Antennas. John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Leang, D.; Kalis, A. Smart SensorDVB: Sensor Network Development Boards with Smart Antennas. In Proceedings of the International Conference of Communications, Circuits and Systems, Chengdu, China, 27–29 June 2004; pp. 1476–1480.
- Nilsson, M. Directional antennas for wireless sensor networks. In Proceedings of the 9th Scandinavian Workshop on Wireless Adhoc Networks (Adhoc’09), Uppsala, Sweden, 4–5 May 2009; pp. 1–4.
- Nilsson, M. Spida: A direction-finding antenna for wireless sensor networks. In Real-World Wireless Sensor Networks; Marron, P.J., Voigt, T., Corke, P., Mottola, L., Eds.; Springer International Publishing: Berlin, Germany, 2010; pp. 138–145. [Google Scholar]
- Giorgetti, G.; Cidronali, A.; Gupta, S.K.; Manes, G. Exploiting low-cost directional antennas in 2.4 GHz IEEE 802.15. 4 wireless sensor networks. In Proceedings of the 2007 European Conference on Wireless Technologies, Munich, Germany, 8–12 October 2007; pp. 217–220.
- Liang, B.; Sanz-Izquierdo, B.; Batchelor, J.C.; Bogliolo, A. Active FSS enclosed beam-switching node for wireless sensor networks. In Proceedings of the 8th European Conference on Antennas and Propagation (EuCAP2014), The Hague, The Netherlands, 6–11 April 2014; pp. 1348–1352.
- Catarinucci, L.; Guglielmi, S.; Colella, R.; Tarricone, L. Compact Switched-Beam Antennas Enabling Novel Power-Efficient Wireless Sensor Networks. IEEE Sens. J. 2014, 14, 3252–3259. [Google Scholar] [CrossRef]
- Catarinucci, L.; Guglielmi, S.; Colella, R.; Tarricone, L. Switched-beam antenna for WSN nodes enabling hardware-driven power saving. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems (FedCSIS2014), Warsaw, Poland, 7–10 September 2014; pp. 1079–1086.
- Felemban, E.; Murawski, R.; Ekici, E.; Park, S.; Lee, K.; Park, J.; Hameed, Z. SAND: Sectored-Antennas Neighbor Discovery Protocol for Wireless Networks. In Proceedings of the IEEE Sensor, Mesh and Ad Hoc Communications and Networks (SECON), Boston, MA, USA, 21–25 June 2010.
- Öström, E.; Mottola, L.; Voigt, T. Evaluation of an Electronically Switched Directional Antenna for Real-world Low-power Wireless Networks. In Proceedings of the 4th International Workshop on Real-world Wireless Sensor Networks (REALWSN2010), Colombo, Sri Lanka, 16–17 December 2010; pp. 113–125.
- Lazos, L.; Poovendran, R. SeRLoc: Secure Range-Independent Localization for Wireless Sensor Networks. In Proceedings of the ACM Workshop on Wireless Security, ACM WiSE’04; Philadelphia, PA, USA, 1 October 2004; pp. 73–100.
- Lazos, L.; Poovendran, R. SeRLoc: Robust Localization for Wireless Sensor Networks. ACM Trans. Sens. Netw. 2005, 1, 73–100. [Google Scholar] [CrossRef]
- Dai, H.N.; Wang, Q.; Li, D.; Wong, R.C.W. On eavesdropping attacks in wireless sensor networks with directional antennas. Int. J. Distrib. Sens. Netw. 2013. [Google Scholar] [CrossRef]
- Dai, H.N.; Li, D.; Wong, R.C.W. Exploring security improvement of wireless networks with directional antennas. In Proceedings of the 36th Conference on Local Computer Networks (LCN2011), Bonn, Germany, 4–7 October 2011; pp. 191–194.
- Li, X.; Xu, J.; Dai, H.N.; Zhao, Q.; Cheang, C.F.; Wang, Q. On modeling eavesdropping attacks in wireless networks. J. Comput. Sci. 2015, 11, 196–204. [Google Scholar] [CrossRef]
- Kim, Y.S.; Tague, P.; Lee, H.; Kim, H. A jamming approach to enhance enterprise Wi-Fi secrecy through spatial access control. Wirel. Netw. 2015, 21, 2631–2647. [Google Scholar] [CrossRef]
- Noubir, G. On connectivity in ad hoc networks under jamming using directional antennas and mobility. In Wired/Wireless Internet Communications; Langendoerfer, P., Liu, M., Matta, I., Tsaoussidis, V., Eds.; Springer International Publishing: Berlin, Germany, 2004; pp. 186–200. [Google Scholar]
- Panyim, K.; Krishnamurthy, P.; le, A. Secure connectivity through key predistribution with directional antennas to cope with jamming in sensor networks. In Proceedings of the 2013 International Symposium on Intelligent Signal Processing and Communications Systems (ISPACS 2013), Okinawa, Japan, 12–15 November 2013; pp. 471–475.
- Staniec, K.; Debita, G. Interference mitigation in WSN by means of directional antennas and duty cycle control. Wirel. Commun. Mob. Com. 2012, 12, 1481–1492. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil Attack in Sensor Networks: Analysis & Defenses. In Proceedings of the International Symposium on Information Processing in Sensor Networks (IPSN), Berkeley, CA, USA, 26–27 April 2004; pp. 259–268.
- Suen, T.; Yasinsac, A. Peer identification in wireless and sensor networks using signal properties. In Proceedings of IEEE International Conference on Mobile Adhoc and Sensor Systems 2005, Washington, DC, USA, 7–10 November 2005; pp. 826–833.
- Bhatia, P.; Laurendeau, C.; Barbeau, M. Solution to the wireless evil-twin transmitter attack. In Proceedings of the 2010 Fifth International Conference on Risks and Security of Internet and Systems (CRiSIS2010), Montreal, QC, Canada, 10–13 October 2010; pp. 1–7.
- Vaman, D.R.; Shakhakarmi, N. Integrated Key based Strict Friendliness Verification of Neighbors in MANET. In Proceedings of the International Conference on Security Science and Technology (ICSST2011), Chongqing, China, 21–23 January 2011; pp. 1–6.
- Rabieh, K.; Mahmoud, M.; Guo, T.; Younis, M. Cross-layer scheme for detecting large-scale colluding Sybil attack in vanets. In Proceedings of IEEE International Conference on Communications (ICC2015), London, UK, 8–12 June 2015; pp. 8–12.
- Hu, L.; Evans, D. Using directional antennas to prevent wormhole attacks. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 5–6 February 2004; pp. 1–11.
- Shi, Z.; Lu, R.; Qiao, J.; Shen, X. Snd: Secure neighbor discovery for 60 GHz network with directional antenna. In Proceedings of the Wireless Communications and Networking Conference (WCNC2013), Shanghai, China, 7–10 April 2013; pp. 4712–4717.
- Anand, M.; Ivesy, Z.G.; Leez, I. Quantifying eavesdropping vulnerability in sensor networks. In Proceedings of the 2nd International VLDB Workshop on Data Management for Sensor Networks (DMSN ’05), Trondheim, Norway, 29 August 2005; pp. 3–9.
- Ashraf, Q.M.; Habaebi, M.H. Autonomic schemes for threat mitigation in Internet of Things. J. Netw. Comput. Appl. 2015, 49, 112–127. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, V. Denial of service attacks in wireless networks: The Case of Jammers. IEEE Commun. Surv. Tutor. 2011, 13, 245–257. [Google Scholar] [CrossRef]
- Viani, F.; Lizzi, L.; Donelli, M.; Pregnolato, D.; Oliveri, G.; Massa, A. Exploitation of parasitic smart antennas in wireless sensor networks. J. Electromagn. Waves Appl. 2010, 24, 993–1003. [Google Scholar] [CrossRef]
- Shaohe, L.; Xiaodong, W.F.; Xin, Z.; Xingming, Z. Detecting the Sybil Attack Cooperatively in Wireless Sensor Networks. In Proceedings of the International Conference on Computational Intelligence and Security (CIS’08), Suzhou, China, 13–17 December 2008; pp. 442–446.
- Douceur, J.R. The Sybil Attack. In Proceeding of the 1st International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002; pp. 251–260.
- Hightower, J.; Borriello, G. Location Sensing Techniques; UW CSE 01-07-01 Technical Report; Department of Computer Science and Engineering, University of Washington: Seattle, WA, USA, 2001. [Google Scholar]
- Laurendeau, C.; Barbeau, M. Insider Attack Attribution Using Signal Strength-based Hyperbolic Location Estimation. Security Commun. Netwo. 2008, 1, 337–349. [Google Scholar] [CrossRef]
- Hu, Y.C.; Perrig, A.; Johnson, D.B. Wormhole Attacks in Wireless Networks. IEEE J. Sel. Areas Commun. 2006, 24, 370–380. [Google Scholar]
- Shafiei, H.; Khonsari, A.; Derakhshi, H.; Mousavi, P. Detection and mitigation of sinkhole attacks in wireless sensor networks. J. Comput. Syst. Sci. 2014, 80, 644–653. [Google Scholar] [CrossRef]
- Giannetsos, T.; Dimitriou, T. LDAC: A localized and decentralized algorithm for efficiently countering wormholes in mobile wireless networks. J. Comput. Syst. Sci. 2014, 80, 618–643. [Google Scholar] [CrossRef]
- Bazan, O.; Jaseemuddin, M. A Survey on MAC protocols for wireless ad hoc networks with beamforming antennas. IEEE Commun. Surv. Tutor. 2012, 14, 216–239. [Google Scholar] [CrossRef]
- Rafique, M.I. MAC Layer Protocols for Wireless networks with Directional Antennas. In Wireless Network Performance Enhancement via Directional Antennas: Models, Protocols, and Systems; Matyjas, J.D., Hu, F., Kumar, S., Eds.; CRC Press: Boca Raton, FL, USA, 2015; pp. 131–154. [Google Scholar]
- Alajmi, N.M.; Elleithy, K.M. Comparative Analysis of Selective Forwarding Attacks over Wireless Sensor Networks. Int. J. Comput. Appl. 2015, 111, 27–38. [Google Scholar]
- Hassoubah, R.S.; Solaiman, S.M.; Abdullah, M.A. Intrusion Detection of Hello Flood Attack in WSNs Using Location Verification Scheme. Int. J. Comput. Commun. Eng. 2015, 4, 156–165. [Google Scholar] [CrossRef]
- Capkun, S.; Hubaux, J.P. Secure Positioning in Wireless Networks. IEEE J. Sel. Areas Commun. 2006, 24, 221–232. [Google Scholar] [CrossRef] [Green Version]
- Ghosal, A.; Halder, S. Security in Mobile Wireless Sensor Networks: Attacks and Defenses. In Cooperative Robots and Sensor Networks 2015; Springer International Publishing: Berlin, Germany, 2015; pp. 185–205. [Google Scholar]
- Argrow, B.; Lawrence, D.; Rasmussen, E. UAV systems for sensor dispersal, telemetry, and visualization in hazardous environments. In Proceeding of the 43rd Aerospace Sciences Meeting and Exhibit, Reno, NV, USA, 10–13 January 2005.
- Nayak, A.; Stojmenovic, I. Wireless Sensor and Actuator Networks: Algorithms and Protocols for Scalable Coordination and Data Communication. John-Whiley & Sons: Hoboken, NJ, USA, 2010. [Google Scholar]
- Curiac, D.I. Towards Wireless Sensor, Actuator and Robot Networks: Conceptual Framework, Challenges and Perspectives. J. Netw. Comput. Appl. 2016, 63, 16–23. [Google Scholar] [CrossRef]

| Characteristic | Omnidirectional Antenna | Directional Antenna |
|---|---|---|
| Energetic efficiency | Lower | Higher |
| Broadcasting direction | All | Desired |
| Transmission range | Lower | Higher |
| Node orientation | Not required | Required |
| Price | Lower | Higher |
| Dimensions | Smaller | Bigger |
| Transmission security | Lower | Higher |
| Collisions | More | Less |
| Research | Frequency | Antenna’s Structure | Mote Platform |
|---|---|---|---|
| Leang and Kalis [30] | 868 MHz | Two horizontal or vertical wire antennas and a reflective SPDT switch | SensorDVB |
| Nilsson [31,32] | 2.4 GHz | Electronically switched parasitic element antenna | TMote Sky |
| Giorgetti et al. [33] | 2.4 GHz | A box-like structure of four coaxially fed planar patch antennas | TelosB |
| Liang et al. [34] | 2.4 GHz | Active cylindrical frequency selective surface | VirtualSense |
| Catarinucci et al. [12] | 2.4 GHz | Radiation structure made of eight microstrip antennas using rectangular two-element patch antenna arrays and a vertical half-wavelength dipole antenna | STM32W-EXT |
| Catarinucci et al. [35,36] | 2.4 GHz | Four identical antennas, containing two quarter-wavelength l-shaped slot antenna elements, disposed in a symmetrical planar structure | STM32W-EXT |
| Felemban et al. [37] | 2.4 GHz | 6-Sectored antennas having an overlap of 120 degrees in azimuth | Nano-Qplus |
| Research | Attack | Directional Antenna Involvement | Short Description |
|---|---|---|---|
| Dai et al. [41,42] | eavesdropping | direct | Establishes eavesdropping models for omnidirectional and directional antennas, proving that directional antennas perform better |
| Li et al. [43] | eavesdropping | direct | Analysis the effects of using directional antennas upon eavesdropping probability from the attacker’s perspective |
| Kim et al. [44] | eavesdropping | direct | Employs special nodes (defensive jammers) equipped with directional antennas in mitigating the eavesdropping attacks |
| Noubir [45] | jamming | direct | Proves the efficiency of directional antennas in jamming circumstances by comparing the network connectivity index |
| Panyim et al. [46] | jamming | direct | Proposes a combined strategy that uses pre-distributed cryptographic keys in conjunction with sensor nodes able to switch from omnidirectional to directional antennas anytime a jamming attack is detected |
| Staniec and Debita [47] | jamming | direct | Suggests two simultaneous defense strategies: equipping the nodes with directional antennas and establishing a superior limit of the duty cycle |
| Newsome et al. [48] | Sybil attack | indirect | Provides a list of possible defenses against Sybil attacks, underlining the efficiency of position verification tactics |
| Suen and A. Yasinsac [49] | Sybil attack | indirect | Uses nodes equipped with GPS and directional antennas to locate the Sybil nodes |
| Bhatia et al. [50] | evil-twin attack | indirect | Employs nodes equipped with four-sector directional antennas to detect malicious nodes using Hyperbolic Position Bounding algorithm |
| Vaman and Shakhakarmi [51] | Sybil attack | indirect | Proposes an integrated key-based Strict Friendliness Verification of neighboring nodes |
| Rabieh et al. [52] | Sybil attack | indirect | Identifies Sybil attacks using directional information, public key cryptography and hash function applied to trial messages |
| Hu and Evans [53] | wormhole attack | indirect | Proposes three approaches to mitigate wormhole attacks, the basic idea being to maintain an accurate list of trusted neighbors |
| Shi et al. [54] | wormhole attack | indirect | Proposes a Secure Neighbor Discovery scheme for wireless networks with a centralized network controller; the approach uses signature based authentication, transmission time information and directional information |
| Vaman and Shakhakarmi [51] | wormhole attack | indirect | Proposes a mechanism based on symmetric node ids, round trip response times and real time location information obtained by directional antennas |
© 2016 by the author; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Curiac, D.-I. Wireless Sensor Network Security Enhancement Using Directional Antennas: State of the Art and Research Challenges. Sensors 2016, 16, 488. https://doi.org/10.3390/s16040488
Curiac D-I. Wireless Sensor Network Security Enhancement Using Directional Antennas: State of the Art and Research Challenges. Sensors. 2016; 16(4):488. https://doi.org/10.3390/s16040488
Chicago/Turabian StyleCuriac, Daniel-Ioan. 2016. "Wireless Sensor Network Security Enhancement Using Directional Antennas: State of the Art and Research Challenges" Sensors 16, no. 4: 488. https://doi.org/10.3390/s16040488






