On the Deployment of a Connected Sensor Network for Confident Information Coverage
Abstract
: Coverage and connectivity are two important performance metrics in wireless sensor networks. In this paper, we study the sensor placement problem to achieve both coverage and connectivity. Instead of using the simplistic disk coverage model, we use our recently proposed confident information coverage model as the sensor coverage model. The grid approach is applied to discretize the sensing field, and our objective is to place the minimum number of sensors to form a connected network and to provide confident information coverage for all of the grid points. We first formulate the sensor placement problem as a constrained optimization problem. Then, two heuristic algorithms, namely the connected cover formation (CCF) algorithm and the cover formation and relay placement with redundancy removal (CFRP-RR) algorithm, are proposed to find the approximate solutions for the sensor placement problem. The simulation results validate their effectiveness, and the CCF algorithm performs slightly better than the CFRP-RR algorithm.1. Introduction
A wireless sensor network (WSN) consists of a large number of spatially-distributed, low-cost sensors to monitor and gather information about various physical phenomena within the sensing field. Wireless sensor networks are an active research area in computer science and telecommunication and have been widely used in a variety of applications nowadays, such as precision agriculture, environment sensing, military surveillance, and so on [1–3].
Coverage is an important performance metric in WSNs, which reflects how well a sensing field is monitored [4]. We may interpret the coverage concept as a nonnegative mapping between the space points of a sensing field and the sensors of a wireless sensor network. We usually use the sensor coverage model to measure the sensing capability and quality of a sensor. The widely-used disk coverage model assumes that a sensor can cover a disk centered on itself with the radius of its sensing range. The disk coverage model, however, is a simplistic sensor coverage model, which does not consider the spatial correlation of physical phenomena and information processing paradigm via the collaboration of sensors. Motivated by the precision agriculture applications [5,6] and based on the theory of field reconstruction [7], we have proposed a new sensor coverage model, called confident information coverage (CIC or Φ-coverage), in our previous study [8]. We will briefly introduce the CIC model in Section 3.
Connectivity is another important performance metric in WSNs, which is a sufficient condition for reliable information transmission. Due to the limited energy, sensors can only transmit information at a short distance. In this paper, we assume a disk communication model: each sensor has a communication range of Rc, and any two sensors can communicate with each other if and only if the Euclidean distance between them is not larger than Rc. A long-distance information transmission is only possible through hop-by-hop information forwarding. A WSN is called connected if and only if any two sensors in the WSN can communicate with each other either directly or via other sensors.
In this paper, we study the sensor placement problem to achieve both coverage and connectivity based on the confident information coverage model. We apply the grid approach to discretize the sensing field: the sensing field is divided into square grid cells, each with equal unit area, and sensors can be only placed at the center of each grid cell, which is called a candidate location. Our objective is to place the minimum number of sensors to form a connected network and to provide confident information coverage for all of the grid points. We formulate the sensor placement problem as a constrained optimization problem, which can be optimally solved by the exhaustive search algorithm. However, its time complexity increases exponentially with the number of candidate locations.
We propose two heuristic algorithms to find the approximate solutions for the sensor placement problem, namely the connected cover formation (CCF) algorithm and the cover formation and relay placement with redundancy removing (CFRP-RR) algorithm. The CCF algorithm constructs a connected cover for confident information coverage in a greedy manner: at each iteration, it places a new sensor at an unoccupied candidate location to cover the maximum number of uncovered grid points, and this newly deployed sensor must be connected with the already deployed sensor network. The CFRP-RR algorithm first places some sensors to cover all of the grid points in a greedy manner without considering network connectivity. After satisfying the coverage requirement, it then checks whether the deployed sensors can form a connected network. If not, it places some relays to form a connected network. After satisfying the connectivity requirement, the CFRP-RR algorithm includes redundancy removal as its final phase. As a relay may also contribute to coverage, there may exist some redundant sensors, which can be removed without compromising the coverage and connectivity requirement. In the final phase of CFRP-RR, it examines the coverage and connectivity requirements for all of the deployed sensors, and those redundant sensors are removed one by one in a greedy manner. The simulation results validate their effectiveness, and the CCF algorithm performs slightly better than the CFRP-RR algorithm.
The rest of the paper is organized as follows. Section 2 reviews some related work. In Section 3, we first briefly introduce the confident information coverage model and then formulate the sensor placement problem as a constrained optimization problem. Section 4 presents two heuristic algorithms, and the simulation results are provided in Section 5. Section 6 concludes the paper.
2. Related Work
Besides the simplest disk coverage model [9–12], many complicated sensor coverage models have been proposed for different applications in the literature. Some have taken coverage via the collaboration of sensors into consideration, such as the detection coverage model [13,14] and the estimation coverage model [15,16]. In [13], Wang et al. propose a probabilistic coverage model based on value fusion for target detection applications. In [15], Wang et al. propose an estimation coverage model, where sensors cooperate to make an estimate or decision for the data to sense at a particular location. Compared to the disk coverage model, they consider the information processing paradigm via the collaboration of sensors. However, this is based on a very simple single-valued parameter model and does not consider the spatial correlation of physical phenomena.
In WSNs, the sensor placement problem to achieve both coverage and connectivity has been extensively studied in recent years [17–26]. In [17], Ammari et al. consider sensing coverage phase transition (SCPT) and network connectivity phase transition (NCPT) problems using the percolation theory, and the correlated disk model is proposed to provide a basis for solving the SCPT and NCPT problems together. In [18,19], Bai et al. consider the optimal deployment pattern problem for different coverage and connectivity requirements in WSNs, and the optimal deployment patterns for all ranges of rc/rs to achieve full coverage and k-connectivity (k ≤ 6) are concluded in [20]. In [21], Cheng et al. compute the minimum number of relay sensors, such that the induced topology by all sensors is globally connected, which is modeled by the network optimization problem named Steiner minimum tree with minimum number of Steiner points and bounded edge length (SMT-MSP). In [22], Lloyd et al. investigate the single-tiered relay node placement (1tRNP) problem and present a simple minimum spanning tree (MST)-based approximation algorithm for 1tRNP. In [25], Natalizio et al. develop a mathematical model for determining the best placement of nodes by taking into consideration the energy of each node involved in the data flow. Additionally, in [26], Guerriero et al. propose and define different innovative optimization models by taking into account different performance objectives, and an extensive computational phase is carried out in order to assess the behavior of the developed models in terms of solution quality and computational effort.
In some practical situations, the monitored field has an irregular shape, which is not suitable for the optimal deployment pattern. Usually, the grid approach is applied to divide the irregular field into grid points in the literature [27-29], and full coverage can be achieved if all of the grid points can be covered. In [27], Chakrabarty et al. present novel grid coverage strategies for effective surveillance and target location in distributed sensor networks and formulate the minimum-cost sensor placement problem as an integer linear programming (ILP) problem. Ke et al. prove that the problem of deploying sensors on grid points to construct a WSN that fully covers critical grids using minimum sensors is NP-complete in [28], and the Steiner tree-based critical grid covering algorithm (STBCGCA) is proposed to solve this problem in [29].
For a randomly-deployed WSN with redundant sensors, Deng et al. have studied how to schedule one-modesensors and multi-modal sensors for confident information coverage to prolong the network lifetime in [30,31]. To the best of our knowledge, we are the first one to study the sensor placement problem to achieve both coverage and connectivity based on the confident information coverage model.
3. Problem Formulation
3.1. Confident Information Coverage
We first briefly review the CIC model proposed in our previous study [8], which is based on the theory of field reconstruction. Sensors are deployed within the sensing field to sample the attribute values of physical phenomena, and field reconstruction is used for their sampling values to interpolate or estimate the attribute values of physical phenomena at those unsampled locations.
Let zt(x) denote the true attribute value at a reconstruction point x at time t, ẑt(x) its reconstructed (estimated) attribute value and zt(s) the attribute value sampled by a sensor s. A reconstruction function can be described as f : {zt(si)|si ∈ S(x)} → ẑt(x), where S(x) denotes the set of sensors within the reconstruction area of x. The purpose of field reconstruction is to minimize the estimation error |zt(x) − ẑt(x)|. Obviously, the estimation error |zt(x) − ẑt(x)| is a random variable, whose probability distribution is unknown, as the physical phenomenon is a temporal-spatial process. Therefore, we use the time-averaged root mean square error (RMSE) to evaluate the reconstruction quality for each reconstruction point x, that is,
Based on the definition of RMSE, we give the definition of confident information coverage as follows:
Confident information coverage (Φ-coverage): Given a reconstruction function f, a space point x is called confident information covered (or Φ-covered) if the time-average RMSE of its reconstructed information Φ(x) is not larger than the application requirement ϵ, i.e., Φ(x) ≤ ϵ. A sensing field is said completely Φ-covered if all of the space points within the sensing field are Φ-covered.
In this paper, we apply the ordinary kriging as the reconstruction function, as it only requires the physical phenomenon to be a second-order stationary process [32,33]. In spatial statistics, the variogram is a function describing the degree of spatial dependence of a spatial process [34]. In precision agriculture, the Gaussian variogram model has been widely used to describe most soil properties, such as soil temperature, humidity and fertility The Gaussian variogram is defined by for h > 0 and γ(h) = 0 for h = 0, where C0 and C1 are called nugget and still, respectively, a is a constant related to the correlation range D, that is , and the reconstruction area of x is exactly a disk centered at x with the radius of D. Note that a reconstruction point x only uses the attribute values sampled by those sensors within its reconstruction area for kriging. Without loss of generality, we let C0 = 0 and C1 = 1 in this paper. Hence, the Gaussian variogram is simplified as:
For a reconstruction point x, the ordinary kriging uses the weighted mean of the attribute values sampled by those sensors within the correlation range of x to interpolate or estimate the attribute value at x,
Equation (3) implies that the interpolation can be done via the collaboration of sensors within the reconstruction area. It is also possible that we use only one sensor closest to the unsampled location for interpolation. In this case, Φ(x) can be computed by:
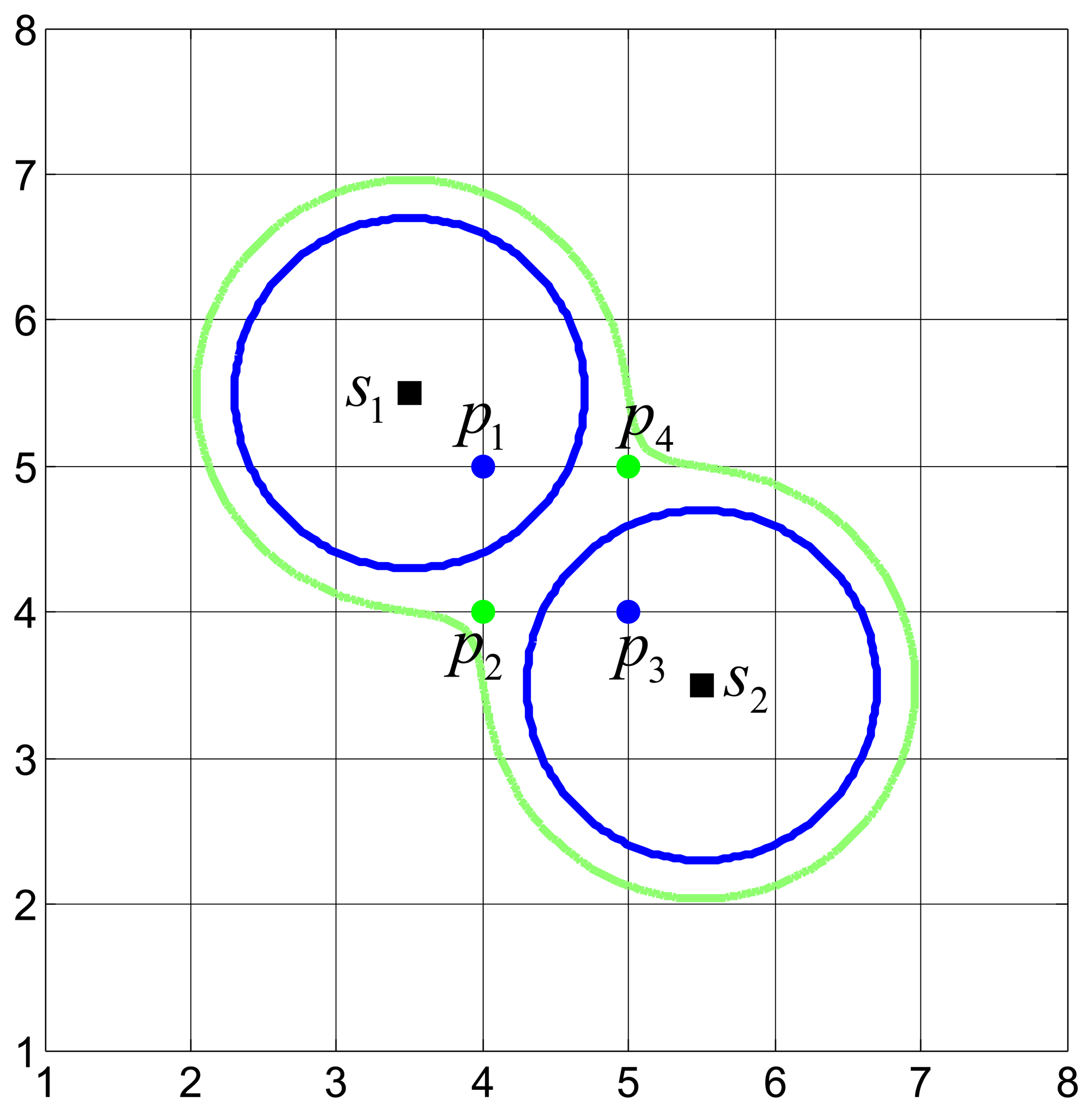
Figure 1 plots the disk coverage model of two individual sensors and the CIC model via the collaboration of two sensors. In Figure 1, s1, s2 are two sensors (the squares dots) and p1, p2, p3, p4 are four grid points (the circular dots). Two blue disks are the covered area of s1 and s2, respectively. The green dumbbell-shaped area is the Φ-covered area via the collaboration of s1 and s2. Due to the inclusion of the collaboration of sensors, the CIC model extends the disk coverage model.
The CIC model can be used in many monitoring applications, such as precision agriculture applications [5,6]. Specifically, when we want to monitor the soil temperature on a farm, we can deploy some sensors at some locations to capture the temperature at these locations. As the number of deployed sensors is limited, we can only obtain the temperature of some discrete points. In order to monitor the continuous soil temperature distribution, we can apply the theory of field reconstruction for estimating/interpolating soil temperature values at unsampled locations. Furthermore, in most cases, a physical phenomenon, like soil temperature, within a continuous space can be modeled as a spatial stochastic process with some spatial correlation. With the help of this spatial correlation, we can reconstruct the temperature in the continuous space by making use of the temperature captured by sensors located at some discrete points.
3.2. Sensor Placement Problem
Like many existing works [27–29], we also apply the grid approach to discretize the sensing field. In particular, the sensing field is divided into square grid cells, each with equal area, and sensors can be only placed at the center of each grid cell, which is called a candidate location. We use all of the grid points to represent the sensing field, that is to say, the sensing field is Φ-covered, if all of the grid points are Φ-covered.
As illustrated in Figure 1, in the disk coverage model, only p1 and p3 can be covered by s1 and s2, respectively, while p2 and p4 cannot be covered. In the CIC model, p1 and p3 can be Φ-covered by s1 and s2, respectively, while p2 and p4 can also be Φ-covered via the collaboration of s1 and s2.
We assume that there are I candidate locations and J grid points in the sensing field, and we use subscripts i and j to index a candidate location and a grid point, respectively Let xi indicate whether a sensor is placed at i, that is,
Let δj indicate whether a grid point is Φ-covered, that is,
Our objective is to place the least number of sensors to form a connected network to provide confident information coverage for all of the grid points, which can be formulated as the following constrained optimization problem:
Equation (11) ensures that all of the grid points have been Φ-covered. At the same time, all of the sensors must form a connected network. Compared to the grid coverage based on the unit disk model, our problem is more complicated due to the fact that in the CIC coverage, a grid point can be cooperatively covered by sensors not within its disk range.
The exhaustive search algorithm can be used to optimally solve the sensor placement problem by trying all of the possible placements. Among all of the possible placements, it finds the optimal one with the least number of sensors to achieve both coverage and connectivity. If there are I candidate locations, the number of all of the possible placements is . Obviously, the time complexity of the exhaustive search algorithm increases exponentially with the number of candidate locations. When the problem instance is large, the computation of the exhaustive search algorithm will be a very time-consuming process. We next propose two heuristic algorithms to find the approximate solutions for the sensor placement problem, yet with significantly reduced time complexity.
4. Solutions for The Placement Problem
We propose two heuristic algorithms to find the approximate solutions for the sensor placement problem, namely the connected cover formation (CCF) algorithm and the cover formation and relay placement with redundancy removing (CFRP-RR) algorithm. Both of them iteratively place a new sensor at each step, until the coverage and connectivity requirements can be satisfied.
We next summarize some symbols used in these two algorithms as follows:
/
u: the set of all/unoccupied candidate locations.
: the set of deployed sensors, i.e., the set of selected candidate locations.
Rc: the communication range of a sensor.
a: the set of available candidate locations, which is defined by:
i*: the selected candidate location to place a sensor at each iteration.
/
u: the set of all/uncovered grid points.
(i): the set of newly covered grid points due to the placement of sensor i.
(j): the set of deployed sensors within the correlation range of grid point j.
Cj: the working GPC of grid point j.
G(V, E, W): the undirected weighted complete graph on the vertices in V, where for two vertices u, v ∈ V, the weight of the edge (u, v) is equal to their distance, i.e., w(u, v) = d(u, v).
(G, Rc): the set of subgraphs of G by removing those edges with weight larger than Rc.
Gk: the k-th subgraph in
(G, Rc), k = 1, 2, …, K.
Dmin((u, Gk),(v, Gl)): the shortest subgraph distance between two subgraphs Gk and Gl, i.e., the shortest distance between vertex u ∈ Gk and vertex v ∈ Gl.
4.1. The Connected Cover Formation Algorithm
The CCF algorithm places a sensor at each iteration to form a connected sensor cover in a greedy manner. First,













The pseudo-codes of the CCF algorithm are provided in Algorithm 1. The inner while loop (Lines 9 to 16) is to find a group of sensors from the set of deployed sensors within the correlation range of grid point j to Φ-cover j. Note that this is done in a greedy manner by selecting a sensor c with the greatest contribution to decrease the RMSE of j. The inner for loop (Lines 6 to 17) is to count the number of newly covered grid points due to the placement of sensor i from the available candidate locations. The outer for loop (Lines 4 to 21) is to place a sensor to cover the largest number of uncovered grid points. The outer while loop (Lines 2 to 24) terminates, if all of the grid points have been Φ-covered by the deployed sensors.
| Algorithm 1 The connected cover formation (CCF) algorithm. | |
| Input: | |
The set of all candidate locations
 , the set of all grid points , the set of all grid points
 | |
| Output: | |
The set of deployed sensors
 | |
| 1: |  a = a =
 u = u =
 , ,
 u = u =
 , ,
 = ∅ = ∅ |
| 2: | while  u = ∅ do u = ∅ do |
| 3: | Nmax = −inf,
 new = ∅; new = ∅; |
| 4: | for each j ∈
 a do a do |
| 5: | N = 0,
 (i) = ∅; (i) = ∅; |
| 6: | for each j ∈
 u do u do |
| 7: | Cj = ∅; |
| 8: | Construct
 (j) from (j) from
 ∪{i} based on j; ∪{i} based on j; |
| 9: | while  (j) = ∅ do (j) = ∅ do |
| 10: | Select c ∈
 (j) with the greatest contribution to decrease the RMSE of j; (j) with the greatest contribution to decrease the RMSE of j; |
| 11: | Cj = Cj∪{c},
 (j) = (j) =
 (j)\ {c}; (j)\ {c}; |
| 12: | if j is Φ-covered by Cj then |
| 13: | N = N + 1,
 (i) = (i) =
 (i)∪{j}; (i)∪{j}; |
| 14: | break; |
| 15: | end if |
| 16: | end while |
| 17: | end for |
| 18: | if N > Nmax then |
| 19: | Nmax = N, i* = i,
 new = new =
 (i); (i); |
| 20: | end if |
| 21: | end for |
| 22: |
 = =
 ∪{i*}, ∪{i*},
 u = u =
 u\{i*}, u\{i*},
 u = u =
 u\ u\
 new; new; |
| 23: | Construct a new
 a from a from
 u based on u based on
 ; ; |
| 24: | end while |
There are four loops in CCF: the inner while loop (Lines 9 to 16), the inner for loop (Lines 6 to 17), the outer for loop (Lines 4 to 21) and the outer while loop (Lines 2 to 24), which need I, J, I and J times computations at most, respectively. Therefore, the time complexity of CCF is O(I2 × J2).
4.2. The Cover Formation and Relay Placement with Redundancy Removal Algorithm
The CFRP-RR algorithm consists of three phases: the first phase aims to achieve complete coverage; the second phase aims to achieve connectivity; and the third phase aims to remove redundant sensors. In the first phase, CFRP-RR places one sensor at each iteration to maximize the number of grid points that are Φ-covered, until all grid points are Φ-covered. The main difference to CCF is that a new sensor can be placed at any unoccupied candidate location in CFRP-RR, rather than any available candidate locations in CCF. Recall that




After the first phase, if the deployed sensors cannot form a connected network, then in the second phase, CFRP-RR places some sensors as relays to connect those isolated subnetworks. Specially, we first construct an undirected weighted complete graph G(V, E, W) by setting V =


For any two disconnected subgraphs Gk and Gl in


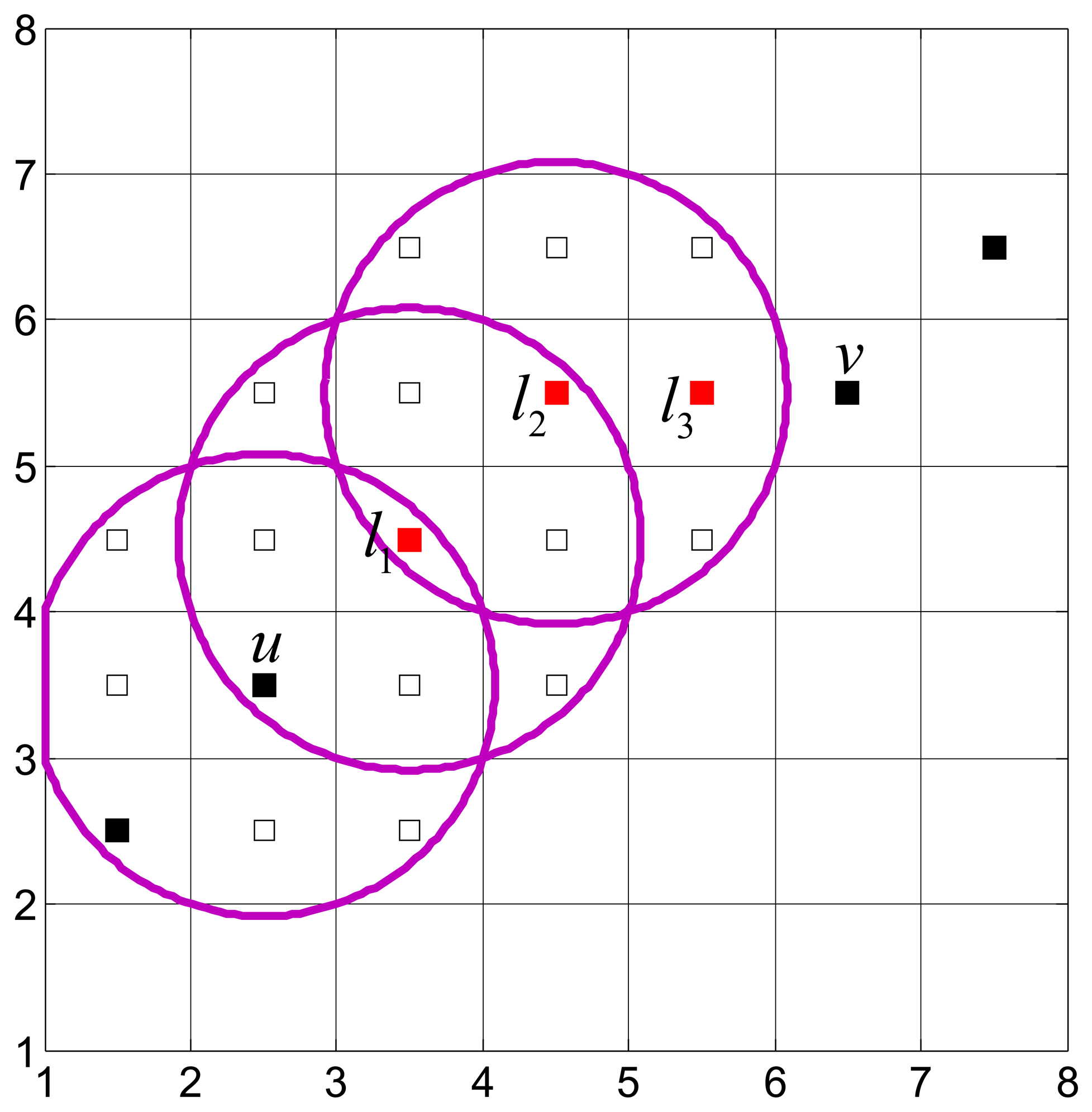
We next explain the furthest progress method for relay placement by an example. As shown in Figure 2, we need to place relay(s) to connect u and v. Starting from u, there are seven unoccupied candidate locations within the communication range of u (namely, the disk centered at u with a radius of Rc), and l1 is the closest one to v. That is, l1 is the furthest progress from u to v. Therefore, l1 is selected to place a relay. If d(l1, v) > Rc, then starting from l1 we repeat the above process, until u and v are connected via the newly deployed relay(s). In Figure 2, three relays are deployed to connect u and v, namely l1, l2 and l3.
We omit the pseudo-codes of CFRP-RR Phase 1, as they are similar to those of CCF, except for using


| Algorithm 2 The cover formation and relay placement with redundancy removing (CFRP-RR) algorithm, Phase 2. | |
| Input: | |
The set of deployed sensors
 , the communication range Rc; , the communication range Rc; | |
| Output: | |
The new set of deployed sensors
 | |
| 1: | Construct G(V, E, W) based on
 ; ; |
| 2: | Construct
 (G, Rc) based on G and Rc; (G, Rc) based on G and Rc; |
| 3: | while |
 (G, Rc)| > 1 do (G, Rc)| > 1 do |
| 4: | Dmin = inf, u* = v* = inf; |
| 5: | for each Gk ∈
 do do |
| 6: | for each Gl ∈
 and Gk ≠ Gl do and Gk ≠ Gl do |
| 7: | d(u, v) = ComputeSSD(Gk, Gl); |
| 8: | if d(u, v) < Dmin then |
| 9: | Dmin = d(u, v), u* = u, v* = v; |
| 10: | end if |
| 11: | end for |
| 12: | end for |
| 13: |
 relay = PlaceRelay (u*, v*); relay = PlaceRelay (u*, v*); |
| 14: |
 = =
 ∪ ∪
 relay; relay; |
| 15: | Construct G(V, E, W) based on
 ; ; |
| 16: | Construct
 (G, Rc) based on G and Rc; (G, Rc) based on G and Rc; |
| 17: | end while |
After the second phase, both complete coverage and connectivity have been achieved. Note that the deployed relays are actually a sensor, which can also participate in coverage, so there may exist some redundant sensors for coverage, and we can further remove them without compromising the coverage and connectivity requirements. In the third phase, CFRP-RR removes one redundant sensor at each iteration in a greedy manner, until no redundant sensor can be found.
A sensor r is called redundant if, after removing it, the rest of the sensors in



Suppose that a redundant sensor r is removed; there may still exist redundant sensors in


The pseudo-codes of CFRP-RR Phase 3 are provided in Algorithm 3. The function computeRedundantSensor is to obtain the set of redundant sensors. The for loop (Lines 4 to 10) is to find the redundant sensor with the largest redundancy weight. The while loop (Lines 2 to 13) is to remove redundant sensors one by one at each iteration, until no redundant sensor can be found.
| Algorithm 3 The CFRP-RR algorithm, Phase 3. | |
| Input: | |
The set of deployed sensors
 , the set of grid points , the set of grid points
 , the communication range Rc , the communication range Rc | |
| Output: | |
The new set of deployed sensors
 ; ; | |
| 1: |  = ComputeRedundantSensor( = ComputeRedundantSensor(
 , ,
 , Rc); , Rc); |
| 2: | while  = ∅ do = ∅ do |
| 3: | Wmax = −inf; |
| 4: | for each r ∈
 do do |
| 5: |
 ¬r = ¬r =
 \{r} \{r} |
| 6: |
 ¬r = ComputeRedundantSensor( ¬r = ComputeRedundantSensor(
 ¬r, ¬r,
 , Rc); , Rc); |
| 7: | if |
 ¬r| > Wmax then ¬r| > Wmax then |
| 8: | Wmax = |
 ¬r|, r* = r; ¬r|, r* = r; |
| 9: | end if |
| 10: | end for |
| 11: |
 = =
 \{r*}; \{r*}; |
| 12: |
 = ComputeRedundantSensor( = ComputeRedundantSensor(
 , ,
 , Rc); , Rc); |
| 13: | end while |
Similar to the analysis in CCF, the time complexity of CFRP-RR Phase 1 is O(I2 × J2). There are three loops in CFRP Phase 2: the inner for loop (Lines 6 to 11), the outer for loop (Lines 5 to 12) and the while loop (Lines 3 to 17), which all need I times computations at most, so the time complexity of CFRP-RR Phase 2 is O(I3). There are two loops in CFRP-RR Phase 3: the for loop (Lines 4 to 10) and the while loop (Lines 2 to 13), which all need I times computations at most, so the time complexity of CFRP-RR Phase 3 is O(I2). Then, the total time complexity of CFRP-RR is O(I2 × J2) + O(I3) + O(I2) = O(I2 × max{I, J2}). Note that, in general, I < J2, so the time complexity of CFRP-RR is O(I2 × J2).
5. Simulation Results
In this section, we use simulations to evaluate the performance the CCF algorithm and the CFRP-RR algorithm. In addition, we compare them with the minimum spanning tree (MST)-based node deployment in Relay Node Placement in Wireless Sensor Networks and the classical simulated annealing (SA) algorithm.
The basic idea of the MST algorithm is as follows. First, some sensors are deployed to achieve complete coverage. Second, we construct a graph based on all of the deployed sensors, and the weight of the edge is exactly the distance of two sensors. Third, we build a minimum spanning tree (MST) based on this graph. Fourth, we examine all of the edges in this MST, and for those edges whose weights are larger than the communication range, we deploy some relays to connect them. Finally, we can obtain a network achieving both coverage and connectivity. The basic idea of the SA algorithm is as follows. First, all of the candidate locations are each occupied by one sensor, and the network can achieve both coverage and connectivity. Second, at each iteration, we remove one sensor according to a given rule, and the above process repeats, until no sensor can be removed without compromising the coverage and connectivity requirements. Finally, we can also obtain a network achieving both coverage and connectivity.
We consider a square monitored field and divide it into in total M × M grid cells, each with equal unit area. Therefore, there are in total (M + 1)2 grid points to be Φ-covered and M2 candidate locations to place sensors. Specially, we consider a monitored field with 112 = 121 grid points and 102 = 100 candidate locations. First, we compare these four algorithms for the following three parameters:
ϵ: the RMSE threshold of confident information coverage.
D: the correlation range of a physical phenomenon.
Rc: the communication range of a sensor.
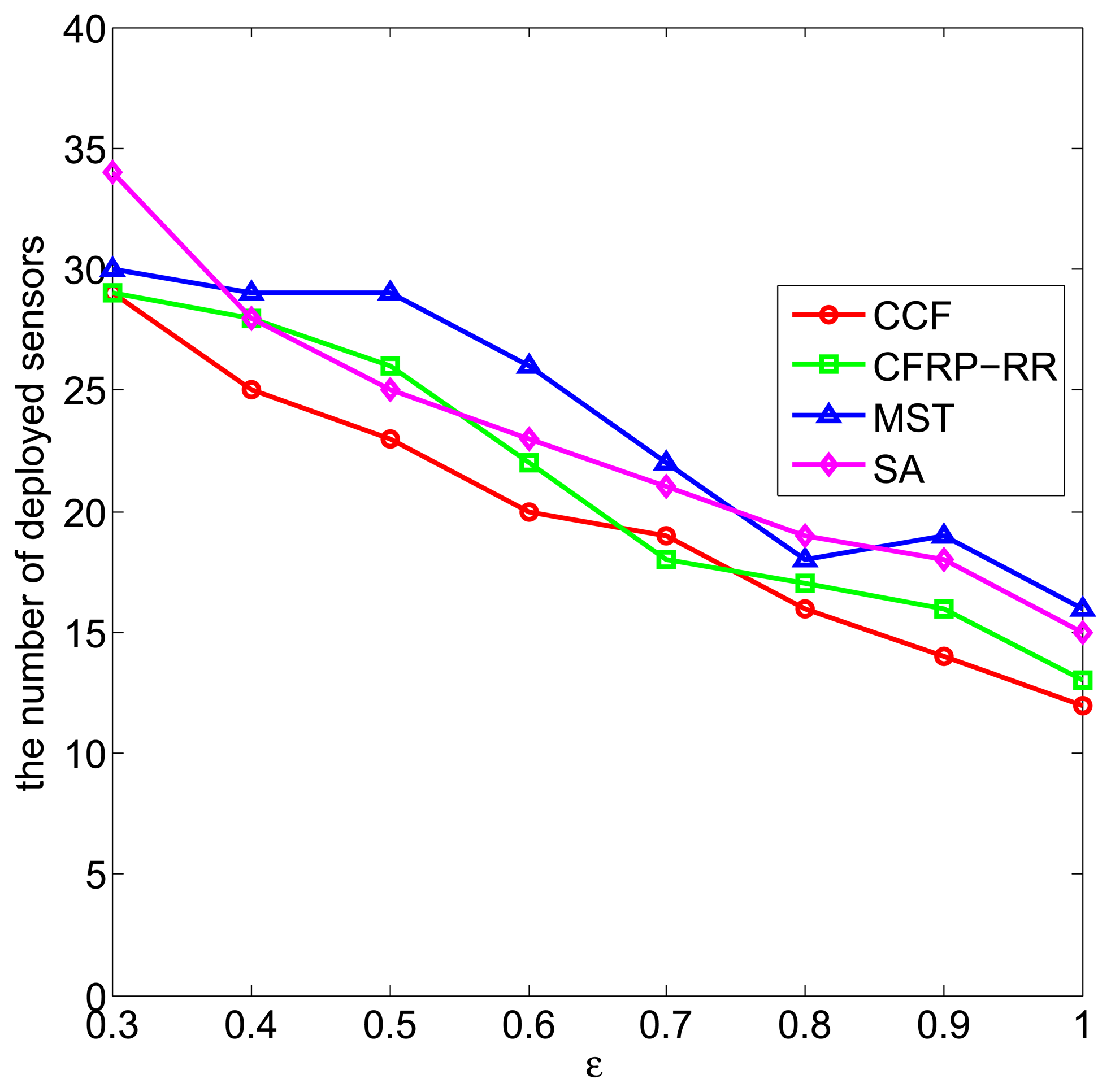
Figure 3 plots the number of deployed sensors against ϵ, when D = 5, Rc = 2.5, M = 10 and ϵ ranges from 0.3 to one. It can be observed that with the increase of ϵ, the number of deployed sensors decreases, which is due to the fact that, when the application requirement ϵ increases, the already deployed sensors can cover a larger area of the monitored field, and less new sensors are required to be deployed to satisfy the coverage requirement. In addition, we can observe that the CCF algorithm performs slightly better than the CFRP-RR algorithm, and both of them perform better than the MST algorithm and the SA algorithm.
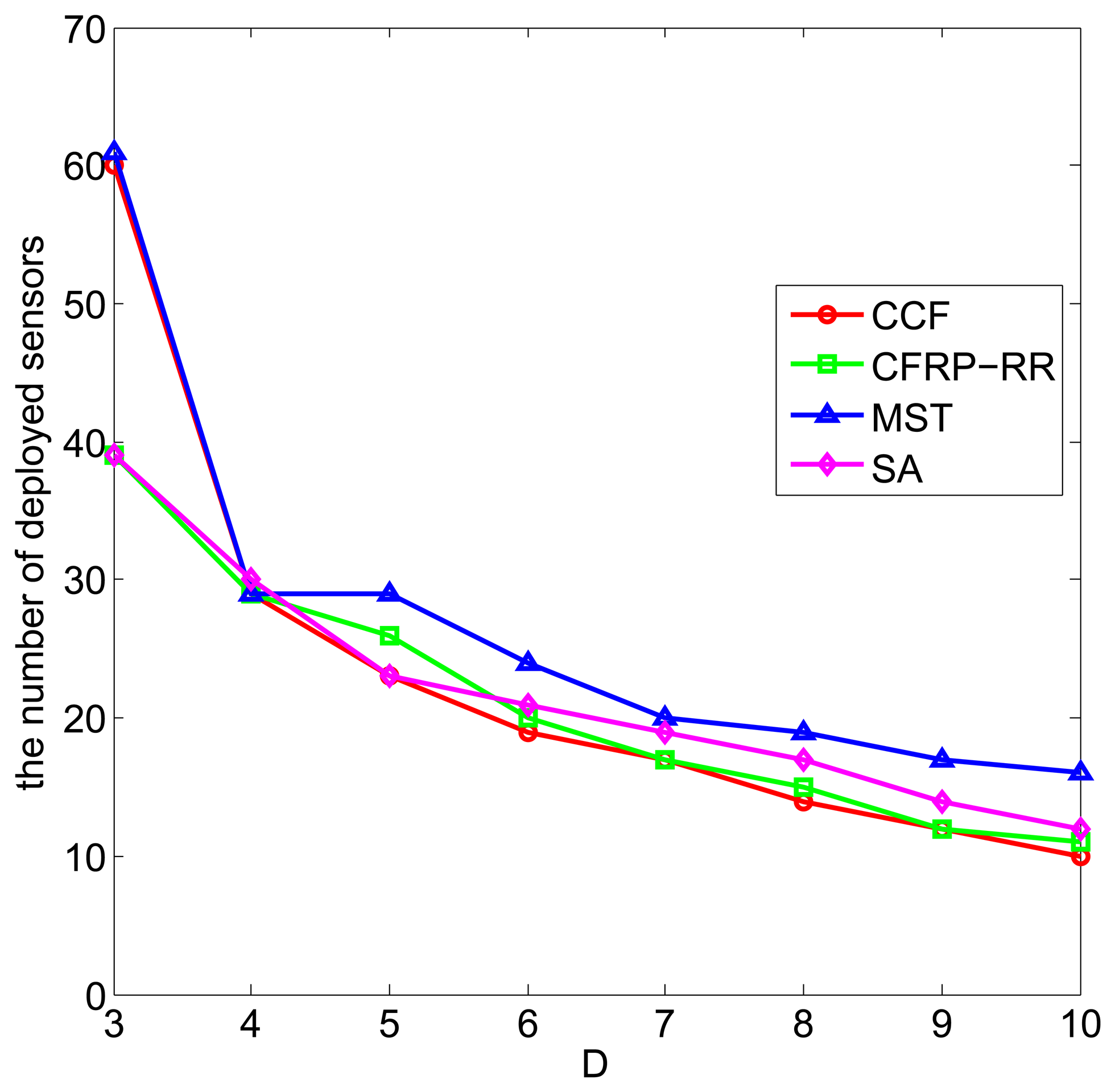
Figure 4 plots the number of deployed sensors against D, when ϵ = 0.5, Rc = 2.5, M = 10 and D ranges from three to 10. It can be observed that with the increase of D, the number of deployed sensors decreases, which is due to the fact that, when the correlation range D increases, more already deployed sensors can participate to cover the grid points in the monitored field and less new sensors are required to be deployed to satisfy the coverage requirement. In addition, we can observe that the CCF algorithm performs slightly better than the CFRP-RR algorithm, and both of them perform better than the MST algorithm and the SA algorithm.
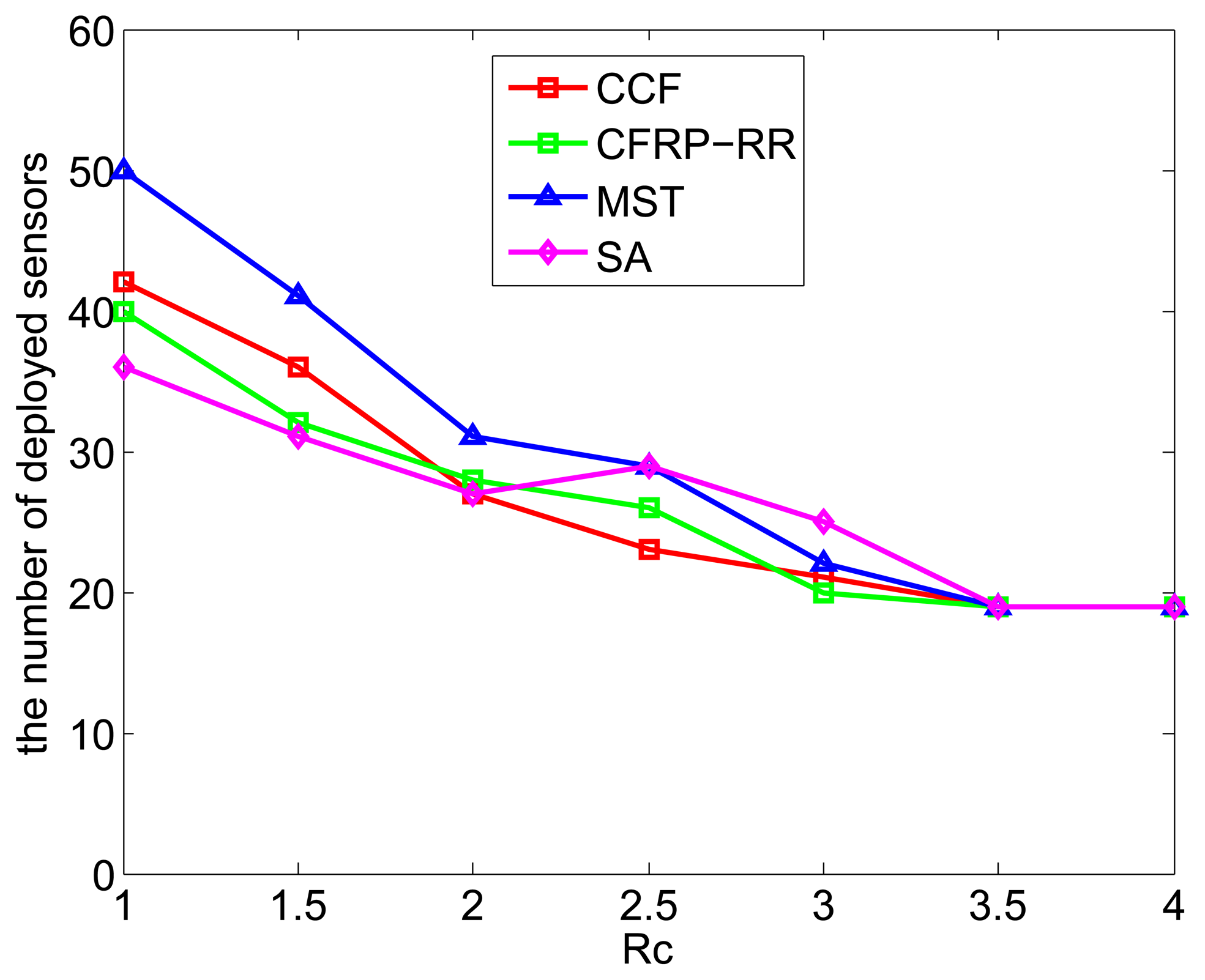
Figure 5 plots the number of deployed sensors against Rc, when ϵ = 0.5, D = 5, M = 10 and Rc ranges from one to four. It can be observe that with the increase of Rc, the number of deployed sensors decreases, which is due to the fact that, with the increase of Rc, less sensors are required to be deployed to satisfy the connectivity requirement. Again, the CCF algorithm performs slightly better than the CFRP-RR algorithm, and both of them perform better than the MST algorithm and the SA algorithm. In addition, when Rc ≥ 3.5, all four curves become flat and coincide with each other, which is due to the fact that, when Rc is sufficiently large, connectivity comes with coverage and is no longer an independent restrictive condition.
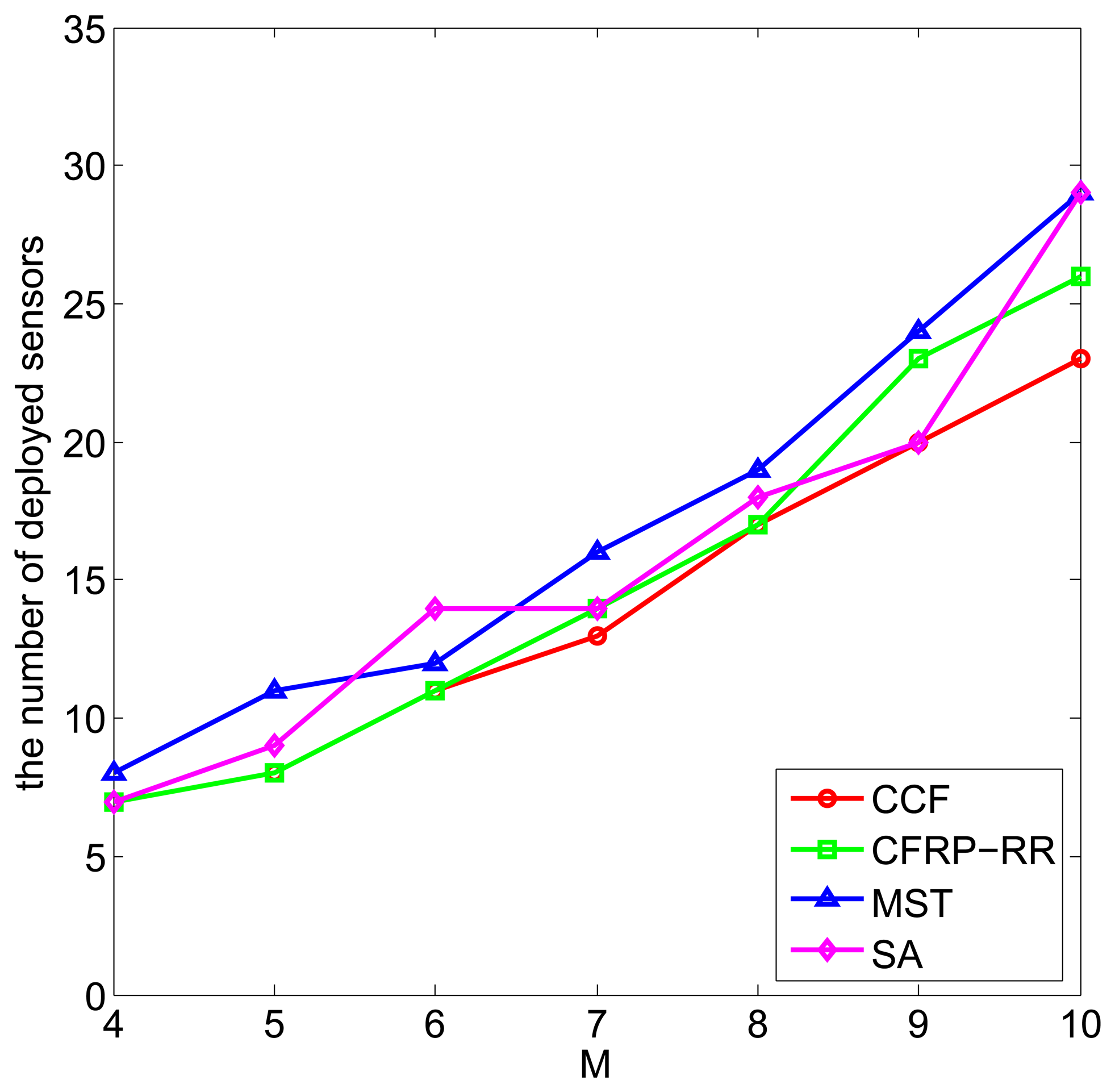
Finally, we compare these three algorithms for different values of M. Figure 6 plots the number of deployed sensors against M, when ϵ = 0.5, D = 5, Rc = 2.5 and M ranges from four to 10. It can be observed that with the increase of M, the number of deployed sensors increases, which is due to the fact that a larger area of the monitored field requires more sensors to be deployed to satisfy the coverage requirement. Still, the CCF algorithm performs slightly better than the CFRP-RR algorithm, and both of them perform better than the MST algorithm and the SA algorithm.
In summary, compared to two algorithm (the MST algorithm and the SA algorithm) in the literature, our two algorithms can achieve better performance for different parameters (ϵ, D, Rc, M). Furthermore, the CCF algorithm performs better than the CFRP-RR algorithm. Both of them can provide two different ideas and methods to solve coverage and connectivity problems in WSN.
6. Conclusions
In this paper, we have studied the sensor placement problem to achieve both coverage and connectivity based on the confident information coverage model. We formulated the sensor placement problem as a constrained optimization problem and proposed two heuristic algorithms, namely the CCF algorithm and the CFRP-RR algorithm, to solve the sensor placement problem. The simulation results have validated their effectiveness, and the CCF algorithm performs slightly better than the CFRP-RR algorithm.
Acknowledgements
This paper is supported in part by the National Natural Science Foundation of China (No. 61371141).
Author Contributions
Bang Wang raised the research problem, directed the algorithm design, organized the manuscript structure and polished the writing. Huping Xu and Jiajun Zhu conducted algorithm design, matlab implementation, simulation execution, data analysis and result presentation, and drafted the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless Sensor Networks: A Survey. Elsevier Comput. Netw. 2002, 38, 393–422. [Google Scholar]
- Farooq, M.O.; Kunz, T. Operating Systems for Wireless Sensor Networks: A Survey. Sensors 2011, 11, 5900–5930. [Google Scholar]
- Jimenez, V.P.G.; Armada, A.G. Field Measurements and Guidelines for the Application of Wireless Sensor Networks to the Environment and Security. Sensors 2009, 9, 10309–10325. [Google Scholar]
- Wang, B. Coverage Problems in Sensor Networks: A Survey. ACM Comput. Surv. 2011, 43, 1–56. [Google Scholar]
- Wang, N.; Zhang, N.; Wang, M. Wireless Sensor in Agriculture and Food Industry-Recent Development and Future Perspective. Elsevier Comput. Electron. Agric. 2006, 50, 1–14. [Google Scholar]
- Camilli, A.; Cugnasca, C.E.; Saraiva, A.M.; Hirakawa, A.R.; Corrêa, PL. From Wireless Sensors to Field Mapping: Anatomy of An Application for Precision Agriculture. Elsevier Comput. Electron. Agric. 2007, 58, 25–36. [Google Scholar]
- Nordio, A.; Chiasserini, C.F. Field Reconstruction in Sensor Networks With Coverage Holes and Packet Losses. IEEE Trans. Signal Process. 2011, 59, 3943–3953. [Google Scholar]
- Wang, B.; Deng, X.; Liu, W.; Yang, L.T.; Chao, H.C. Field Confident Information Coverage in Sensor Networks for Field Reconstruction. IEEE Wirel. Commun. 2013, 20, 74–81. [Google Scholar]
- Baysan, M.; Sarac, K.; Chandrasekaran, R.; Bereg, S. A Polynomial Time Solution to Minimum Forwarding Set Problem in Wireless Networks under Unit Disk Coverage Model. IEEE Trans. Parallel Distrib. Syst. 2009, 20, 913–924. [Google Scholar]
- Wang, W.; Srinivasan, V.; Wang, B.; Chua, K.C. Coverage for Target Localization in Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2008, 7, 667–676. [Google Scholar]
- Zhao, Q.; Gurusamy, M. Lifetime Maximization for Connected Target Coverage in Wireless Sensor Networks. IEEE/ACM Trans. Netw. 2008, 16, 1378–1391. [Google Scholar]
- Cardei, M.; Thai, M.T.; Li, Y.; Wu, W. Energy-Efficient Target Coverage in Wireless Sensor Networks. Proceedings of the Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM), New Orleans, LA, USA, 13–17 March 2005.
- Wang, W.; Srinivasan, V.; Chua, K.C.; Wang, B. Energy-efficient Coverage for Target Detection in Wireless Sensor Networks. Proceedings of the International Symposium on Information Processing in Sensor Networks (IPSN), Cambridge, UK, 10–14 April 2007.
- Hefeeda, M.; Ahmadi, H. A Probabilistic Coverage Protocol for Wireless Sensor Networks. Proceedings of the IEEE International Conference on Network Protocols (ICNP), Bejing, China, 16–19 October 2007.
- Wang, B.; Wang, W.; Srinivasan, V.; Chua, K.C. Information Coverage for Wireless Sensor Networks. IEEE Commun. Lett. 2005, 9, 967–969. [Google Scholar]
- Wang, R.; Cao, W. Universal Information Coverage for Bandwidth-Constrained Sensor Networks. Proceedings of the IEEE International Conference on Robotics and Biomimetics (ROBIO), Sanya, China, 15–28 December 2007.
- Ammari, H.M.; Das, S.K. Integrated Coverage and Connectivity in Wireless Sensor Networks: A Two-Dimensional Percolation Problem. IEEE Trans. Comput. 2008, 57, 1423–1434. [Google Scholar]
- Bai, X.; Kumar, S.; Xuan, D.; Yun, Z.; Lai, T.H. Deploying Wireless Sensors to Achieve Both Coverage and Connectivity. Proceedings of the ACM International Symposium on Mobile ad hoc Networking and Computing (MobiHoc), Florence, Italy, 22–25 May 2006.
- Bai, X.; Yun, Z.; Xuan, D.; Lai, T.H.; Jia, W. Deploying Four-Connectivity And Full-Coverage Wireless Sensor Networks. Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Phoenix, AZ, USA, 15–17 April 2008.
- Bai, X.; Yun, Z.; Xuan, D.; Jia, W.; Zhao, W. Pattern Mutation in Wireless Sensor Deployment. Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), San Diego, CA, USA, 15–19 March 2010.
- Cheng, X.; Du, D.Z.; Wang, L.; Xu, B. Relay Sensor Placement in Wireless Sensor Networks. Springer Wirel. Netw. 2008, 14, 347–355. [Google Scholar]
- Lloyd, E.L.; Xue, G. Relay Node Placement in Wireless Sensor Networks. IEEE Trans. Comput. 2007, 56, 134–138. [Google Scholar]
- Li, J.; Andrew, L.L.H.; Foh, C.H.; Zukerman, M.; Chen, H.H. Connectivity, Coverage and Placement in Wireless Sensor Networks. Sensors 2009, 9, 7664–7693. [Google Scholar]
- Shih, K.P.; Deng, D.J.; Chang, R.S.; Chen, H.C. On Connected Target Coverage for Wireless Heterogeneous Sensor Networks with Multiple Sensing Units. Sensors 2009, 9, 5173–5200. [Google Scholar]
- Natalizio, E.; Loscri, V.; Viterbo, E. Optimal Placement of Wireless Nodes for Maximizing Path Lifetime. IEEE Commun. Lett. 2008, 12, 362–364. [Google Scholar]
- Guerriero, F.; Violi, A.; Natalizio, E.; Loscri, V.; Costanzo, C. Modelling and solving optimal placement problems in wireless sensor networks. Elsevier Appl. Math. Model. 2011, 35, 230–241. [Google Scholar]
- Chakrabarty, K.; Iyengar, S.S.; Qi, H.; Cho, E. Grid Coverage for Surveillance and Target Location in Distributed Sensor Networks. IEEE Trans. Comput. 2002, 51, 1448–1453. [Google Scholar]
- Ke, W.C.; Liu, B.H.; Tsai, M.J. Constructing A Wireless Sensor Network to Fully Cover Critical Grids by Deploying Minimum Sensors on Grid Points is NP-complete. IEEE Trans. Comput. 2007, 56, 710–715. [Google Scholar]
- Ke, W.C.; Liu, B.H.; Tsai, M.J. Efficient Algorithm for Constructing Minimum Size Wireless Sensor Networks to Fully Cover Critical Square Grids. IEEE Trans. Wirel. Commun. 2011, 10, 1154–1164. [Google Scholar]
- Deng, X.; Wang, B.; Wang, N.; Liu, W.; Mo, Y. Sensor Scheduling for Confident Information Coverage in Wireless Sensor Networks. Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013.
- Deng, X.; Wang, B.; Liu, W.; Yang, L.T. Sensor Scheduling for Multi-Modal Confident Information Coverage In Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 26, 902–913. [Google Scholar]
- Harrington, B.; Huang, Y.; Yang, J.; Li, X. Energy-efficient Map Interpolation for Sensor Fields Using Kriging. IEEE Trans. Mob. Comput. 2009, 8, 622–635. [Google Scholar]
- Penaloza, G.H.; Lozano, B.B. Field Estimation in Wireless Sensor Networks Using Distributed Kriging. Proceedings of the IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012.
- Webster, R.; Oliver, M.A. Geostatistics for Environmental Scientists, 2nd ed.; Wiley: Chichester, UK, 2007. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, H.; Zhu, J.; Wang, B. On the Deployment of a Connected Sensor Network for Confident Information Coverage. Sensors 2015, 15, 11277-11294. https://doi.org/10.3390/s150511277
Xu H, Zhu J, Wang B. On the Deployment of a Connected Sensor Network for Confident Information Coverage. Sensors. 2015; 15(5):11277-11294. https://doi.org/10.3390/s150511277
Chicago/Turabian StyleXu, Huping, Jiajun Zhu, and Bang Wang. 2015. "On the Deployment of a Connected Sensor Network for Confident Information Coverage" Sensors 15, no. 5: 11277-11294. https://doi.org/10.3390/s150511277
APA StyleXu, H., Zhu, J., & Wang, B. (2015). On the Deployment of a Connected Sensor Network for Confident Information Coverage. Sensors, 15(5), 11277-11294. https://doi.org/10.3390/s150511277





