Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks
Abstract
:1. Introduction
1.1. Authentication and Key Agreement for WSNs
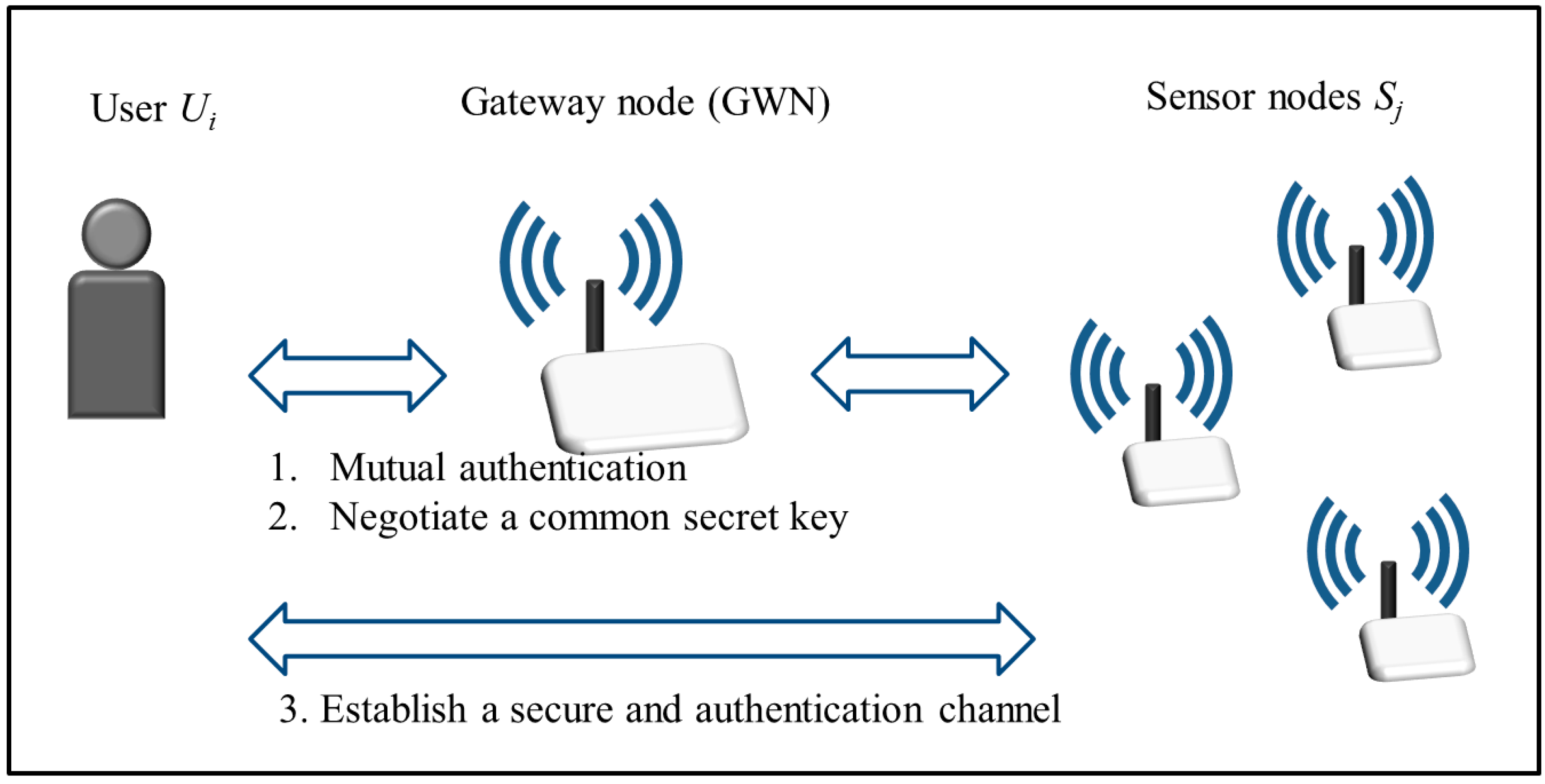
1.2. Our Contributions
1.3. Organization of the Paper
2. Preliminaries
| IDi, pwi | Identity and password pair of user Ui |
| SIDj | Identity of sensor node Sj |
| IDs | Identity of smart card |
| K | Secret key only know to GWN |
| xs | Secret value of GWN and Sj |
| KS | Session key |
| RNi, RNj, RNG | Random numbers selected by Ui, Sj and GWN, respectively |
| Ti, Ti′, Tj, TG, TG′ | The timestamp values |
| h(·) | A collision free one-way hash function |
| f(x, k) | Pseudo-random function of variable x with key k |
| A →B:M | A sends message M to B through a common channel. |
| A ⇒ B:M | A sends message M to B through a secure channel |
| ⊕ | The exclusive-or (XOR) operation. |
| M1||M2 | Message M1 concatenates to message M2. |
2.1. Review of the Authentication and Key Agreement Scheme of Kim et al.
2.1.1. Registration Phase
- Step 1:
- Ui GWN:{IDi, HPWi}Ui selects IDi, password pwi, a random number RNr, computes HPWi = h(pwi||RNr) and sends {IDi, HPWi} to GWN via a secure channel.
- Step 2:
- GWN Ui: Ui′s smartcardGWN computes HIDi = h(IDi||K), XSi = h(HIDi||xs), Ai = h(HPWi||XSi) h(HIDi||K), Bi = h(HPWi* XSi), Ci = XSi h(IDs||HPWi) and personalizes the smart card for Ui with the parameters: (IDs, HIDi, h(·), Ai, Bi, Ci). Then, GWN sends the smartcard to Ui via a secure channel.
- Step 3:
- Ui computes XPWi = h(pwi) RNr and inserts XPWi into his/her smart card.
2.1.2. Login Phase
- Step 1:
- Ui inserts his/her smart card into a terminal and enters IDi* and PWi*.
- Step 2:
- The smart card computes RNr* = h(pwi) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*) and verifies Bi* = ? Bi. If unsuccessful, the smart card aborts this request; otherwise, the smartcard computes DIDi = Bi* h(XSi*||RNi||Ti), MUi,G = h(Ai||XSi*||RNi||Ti) and vi = RNi XSi*, where RNi is a nonce and Ti is the current timestamp. Then the smartcard sends the authentication request {DIDi, MUi,G, vi, Ti, HIDi} to GWN.
2.1.3. Authentication and Key Agreement Phase
- Step 1:
- GWN → Sj: {DIDi, MG,Sj, TG}GWN checks the validity of Ti, computes XSi = h(HIDi||xs), RNi = vi XSi, X* = DIDi h(XSi||RNi||Ti), MUi,G* = h((X* h(HIDi||K)||XSi||RNi||Ti) and checks MUi,G* = ? MUi,G. If successful, GWN computes XSj = h(SIDj||xs), MG,Sj = h(DIDi||SIDj||XSj||TG) and sends {DIDi, MG,Sj, TG} to Sj, where Sj is the nearest sensor node for Ui and TG is current timestamp.
- Step 2:
- Sj → GWN: {yj, MSj,G, Tj}Sj checks the validity of TG, computes MG,Sj* = h(DIDi||SIDj||XSj*||TG) and checks MG,Sj* = ? MG,Sj. If successful, Sj computes yj = RNj XSj*, zi = MG,Sj* RNj and MSj,G = h(zi||XSj*||Tj), KS = f((DIDi||RNj), XSj*), and sends {yj, MSj,G, Tj} to GWN, where RNj is a nonce and Tj is current timestamp.
- Step 3:
- GWN → Ui: {yi, wi, MG,Ui, qj, TG′}GWN checks the validity of Tj, computes RNj = yj XSj, zi* = MG,Sj* RNj, MSj,G* = h(zi*||XSj||Tj), and checks MSj,G* = ? MSj,G. If successful, GWN computes MG,Ui = h(DIDi||MSj,G|| MUi,G||XSj||TG′), wi = zi* XSi, yj = RNj XSj, qj = XSj RNj and sends {yi, wi, MG,Ui, qj, TG′} to Ui, where TG′ is current timestamp.
- Step 4:
- The smart card checks the validity of TG′ and computes RNj = yj XSj, zi* = wi XSi, MG,Sj = zi* RNj, MG,Ui* = h(DIDi||MSj,G*|| MUi,G||XSj||TG′), and checks MG,Ui* = ? MG,Ui. If successful, Ui computes XSj = qj RNj and the session key KS = f((DIDi||RNj), XSj). Then, Ui and Sj successfully realize mutual authentication and have a common session key KS.
2.1.4. Password Change Phase
- Step 1:
- Ui inserts his smartcard and inputs his/her identity IDi*, old password pwi*, and a new password pwni.
- Step 2:
- The smart card computes RNr* = h(pwi*) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*), and checks Bi* = ? Bi. If successful, the smart card computes HPWni = h(pwni||RNr*), Ani = Ai h(HPWi*||XSi*) h(HPWni||XSi*), Bni = h(HPWni XSi*), Cni = XSi* h(IDs||HPWni), and replaces (Ai, Bi, Ci) with (Ani, Bni, Cni).
2.2. Limitations of the Authentication and Key Agreement Scheme of Kim et al.
2.2.1. Security Against Impersonation Attacks
- Step 1:
- On receiving the message {DIDi, MG,Sj, TG} from GWN, 𝒜 computes yj′ = RNj′ XSj*, zi′ = MG,Sj* RNj′ and MSj,G′ = h(zi′||XSj*||Tj), where RNj′ is a nonce selected by 𝒜 and Tj is the timestamp. Then 𝒜 sends back {yj′, MSj,G′, Tj} to GWN
- Step 2:
- Next, 𝒜 is authenticated by GWN since GWN successfully checks and MSj,G′ = ? MSj,G, where RNj′ = yj′ XSj, zi′* = MG,Sj* RNj′, MSj,G′* = h(zi′*||XSj||Tj).
- Step 3:
- Then, 𝒜 computes the session key KS = f((DIDi||RNj′), XSj) shared with Ui. Thus, 𝒜 successfully impersonates Sj to communicate with GWN and Ui.
2.2.2. Security against Lost Smart Card Attacks
- Step 1:
- 𝒜 collects previous messages between Ui, GWN and Sj0, which include (DIDi0, vi0, Ti0, HIDi, yj0, yi0, wi0, qj0), and has Sj0’s secret XSj0.
- Step 2:
- 𝒜 computes RNj0 = yj0 XSj0, XSi = yi0 RNj0, RNi0 = vi0 XSi, DIDi′ = DIDi0 h(XSi||RNi0||Ti0) h(XSi||RNi′||Ti′), MUi,G′ = h(Ai||XSi||RNi′||Ti′) and vi′ = RNi′ XSi, where RNi′ is a nonce selected by 𝒜 and Ti′ is the current timestamp. Then 𝒜 impersonates Ui and sends the authentication request {DIDi′, MUi,G′, vi′, Ti′, HIDi} to GWN.
- Step 3:
- GWN successfully authenticates 𝒜 by checking and MUi,G* = ? MUi,G′. Next, GWN and Sj realize mutual authentication by validating timestamps TG, Tj and checking MG,Sj* = ? MG,Sj, MSj,G* = ? MSj,G. Then GWN sends back {yi, wi, MG,Ui, qj, TG′} to 𝒜, where MG,Ui = h(DIDi′||MSj,G|| MUi,G||XSj||TG′), wi = zi* XSi, yj = RNj XSj, qj = XSj RNj, and is the current timestamp.
- Step 4:
- The adversary 𝒜 computes RNj = yj XSj and XSj = qj RNj. Then, 𝒜 successfully has the session key KS = f((DIDi′||RNj), XSj) shared with Sj.
2.2.3. Security against Man-in-the-Middle Attacks
- Step 1:
- User 𝒜 intercepts the communications between GWN and Sj. After receiving the message {DIDi, MG,Sj, TG} from GWN, 𝒜 forwards it to Sj.
- Step 2:
- On receiving the message {yj, MSj,G, Tj} from Sj, 𝒜 computes RNj = yj XSj*, yj′ = RNj′ XSj*, zi′ = MG,Sj* RNj′ and MSj,G′ = h(zi′||XSj*||Tj), and sends {yj′, MSj,G′, Tj} to GWN, where RNj is a nonce selected by Sj and RNj′ is a nonce selected by 𝒜, respectively
- Step 3:
- GWN successfully checks Tj, computes RNj′ = yj′ XSj, zi′* = MG,Sj* RNj′, MSj,G′* = h(zi′*||XSj||Tj), and checks MSj,G′* = ? MSj,G′. Then, GWN computes MG,Ui′ = h(DIDi||MSj,G′|| MUi,G||XSj||TG′), wi′ = zi′* XSi, yj′ = RNj′ XSj, qj′ = XSj RNj′ sends {yi′, wi′, MG,Ui′, qj′, TG′} to Ui.
- Step 4:
- The smart card successfully checks TG′ and computes RNj′ = yj′ XSj, zi′* = wi′ XSi, MG,Sj′ = zi′* RNj′, MG,Ui′* = h(DIDi||MSj,G′*|| MUi,G||XSj||TG′), and checks MG,Ui′* = ? MG,Ui′. Then Ui computes XSj = qj′ RNj′ and the session key KS′ = f((DIDi||RNj′), XSj) shared with 𝒜. Sj computes the session key KS" = f((DIDi||RNj), XSj) shared with 𝒜.
2.2.4. Violation of Session Key Security
2.2.5. Failure to Privacy Protection of Users
3. Proposed Authentication and Key Agreement Scheme Using Dynamic Identities for WSNs
3.1. Registration Phase
- Step 1:
- Ui GWN: {IDi, HPWi}Ui selects IDi, password pwi, a random number RNr, computes HPWi = h(pwi||RNr) and sends {IDi, HPWi} to GWN via a secure channel.
- Step 2:
- GWN Ui: Ui′s smartcardGWN computes HIDi = h(IDi||K), XSi = h(HIDi||K), Ai = h(HPWi||XSi) HIDi, Bi = h(HPWi XSi), Ci = XSi h(IDs||HPWi) and personalizes the smartcard for Ui with the parameters: (IDs, h(·), Ai, Bi, Ci, TIDi). Then, GWN sends the smartcard to Ui via a secure channel. GWN also stores parameters (TIDi, TIDi°, HIDi) in its storage for Ui, where TIDi is the temporal identity for Ui’s next login and TIDi = RNG, RNG is a nonce, and TIDi°= "".
- Step 3:
- Ui computes XPWi = h(pwi) RNr and inserts XPWi into his/her smartcard.
3.2. Login Phase
- Step 1:
- inserts his/her smart card into a terminal and enters IDi* and pwi*.
- Step 2:
- The smartcard computes RNr* = h(pwi) XPWi, HPWi* = h(pwi*||RNr*), XSi* = Ci h(IDs||HPWi*), Bi* = h(HPWi* XSi*) and verifies Bi* = ? Bi. If unsuccessful, the smartcard aborts this request; otherwise, the smart card computes a temporary secret key ki = h(XSi*||Ti), DIDi = h(HPWi*||XSi*) ki, MUi,G = h(Ai||XSi*||Ti), where Ti is the current timestamp. Then the smartcard sends the authentication request {DIDi, MUi,G, Ti, TIDi} to GWN.

3.3. Authentication and Key Agreement Phase
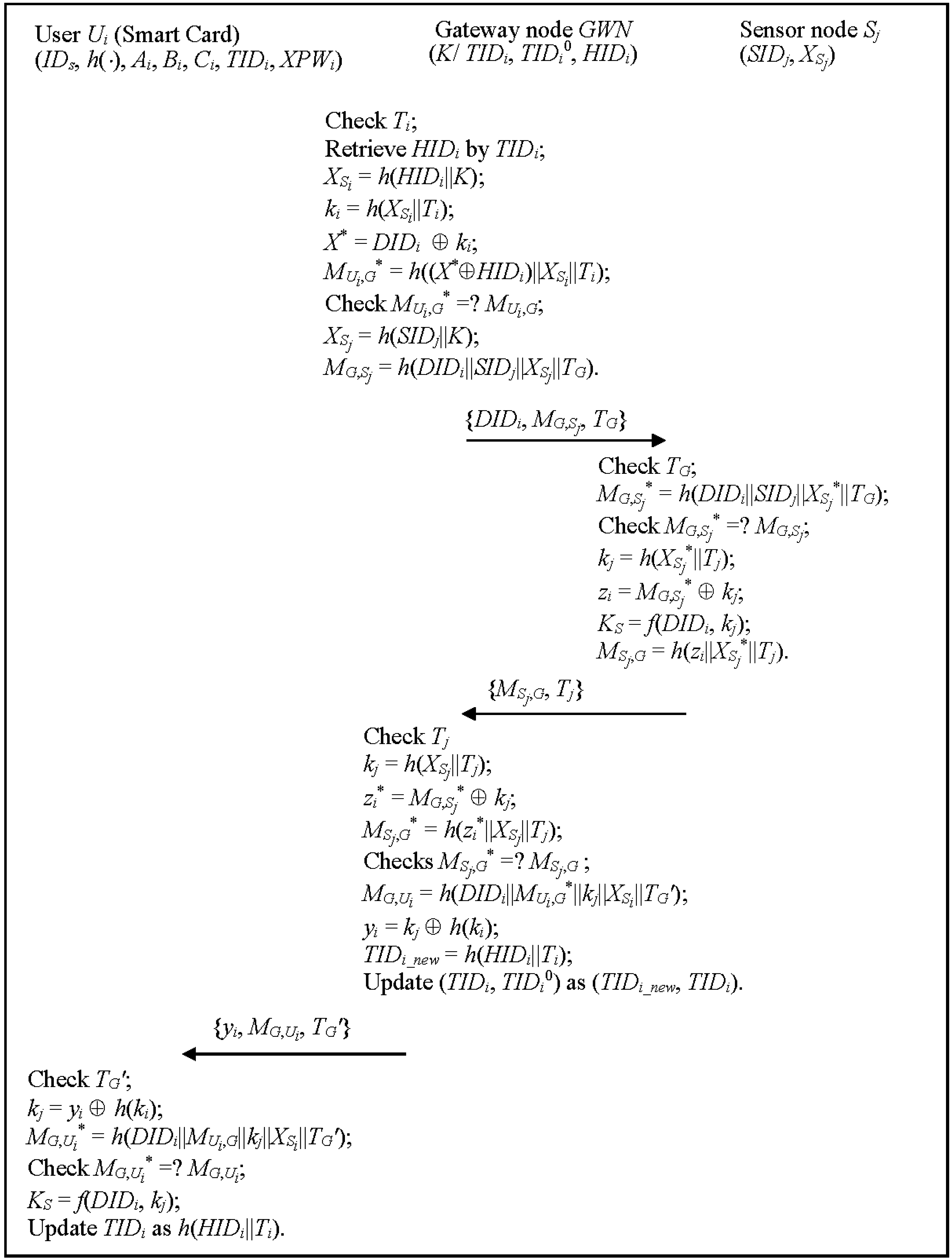
- Step 1:
- GWN → Sj: {DIDi, MG,Sj, TG}GWN checks the validity of Ti, retrieves Ui,’s information HIDi by using TIDi. If TIDi is not found, then GWN retrieves HIDi by using TIDi°. If unsuccessful, GWN rejects this service request; otherwise, GWN computes XSi = h(HIDi||K), ki = h(XSi||Ti), X* = DIDi ki, MUi,G* = h((X* HIDi)||XSi||Ti) and checks MUi,G* = ? MUi,G. If successful, GWN computes XSj = h(SIDj||K), MG,Sj = h(DIDi||SIDj||XSj||TG) and sends {DIDi, MG,Sj, TG} to Sj, where Sj is the nearest sensor node for Ui and TG is current timestamp.
- Step 2:
- Sj → GWN: {MSj,G, Tj}Sj checks the validity of TG, computes MG,Sj* = h(DIDi||SIDj||XSj*||TG) and checks MG,Sj* = ? MG,Sj. If successful, Sj computes a temporary secret key kj = h(XSj*||Tj), zi = MG,Sj* kj, KS = f(DIDi, kj) and MSj,G = h(zi||XSj*||Tj), and sends {MSj,G, Tj} to GWN, where Tj is current timestamp.
- Step 3:
- GWN → Ui: {yi, MG,Ui, TG′}GWN checks the validity of Tj, computes kj = h(XSj||Tj), zi* = MG,Sj* kj, MSj,G* = h(zi*||XSj||Tj), and checks MSj,G* = ? MSj,G. If successful, GWN computes MG,Ui = h(DIDi||MUi,G*||kj||XSi||TG′), yi = kj h(ki), TIDi_new = h(HIDi||Ti), and sends{yi, MG,Ui, TG′} to Ui, where TG′ is current timestamp. At this time, GWN updates (TIDi, TIDi°) as (TIDi_new, TIDi).
- Step 4:
- The smartcard checks the validity of TG′, and computes kj = yi h(ki), MG,Ui* = h(DIDi||MUi,G||kj||XSi||TG′), and checks MG,Ui* = ? MG,Ui. If successful, Ui computes the session key KS = f(DIDi, kj). Then, Ui and Sj successfully realize mutual authentication and have a common session key KS. Similarly, Ui also updates TIDi as h(HIDi||Ti).
4. Security Analyses
4.1. Security Definitions
4.1.1. AKE Security (Session Key Security)
4.1.2. Mutual Authentication (MA) Security
4.2. Session Key Security
4.3. Mutual Authentication
4.4. Privacy Protection of Users
4.5. Known-Key Security
4.6. Resistance to Impersonation Attacks
4.7. Resistance to Stolen Verifier Attacks
4.8. Resistance to Lost Smartcard Attacks
4.9. Resistance to Sensor Node Capture Attacks
5. Performance Analyses and Functionality Comparisons
5.1. Performance Analyses
| Vaidya et al. [15] | Li et al. [9] | Kim et al. [16] | Our Scheme | ||
|---|---|---|---|---|---|
| Ui | 7H + 7X | 9H + 5X | 9H + 9X | 11H + 5X | |
| Computations | Sj | 2H | 6H + 4X | 3H + 2X | 4H + 1X |
| GWN | 6H + 6X | 11H + 5X | 8H + 8X | 10H + 4X | |
| Total | 15H + 13X | 26H + 14X | 20H + 29X | 25H + 10X | |
| Used random numbers | 5 | 4 | 5 | 3 | |
| Simulation Time (ms) | Vaidya et al. [15] | Li et al. [9] | Kim et al. [16] | Our Scheme |
|---|---|---|---|---|
| Ui | 0.00140 | 0.00162 | 0.00180 | 0.00198 |
| Sj | 0.00048 | 0.00144 | 0.00072 | 0.00100 |
| GWN | 0.00084 | 0.00143 | 0.00104 | 0.00130 |
| Total | 0.00272 | 0.00449 | 0.00356 | 0.00428 |
| Hardware/Software Specification | ||
|---|---|---|
| User Ui | Mainboard | ASUSTeK Computer INC. CM5571 |
| CPU | Intel Core 2 Quad Q8300 @ 2.50 GHz 2.50 GHz | |
| Memory | 4.00 GB Dual-Channel DDR3 @ 533 MHz | |
| OS | Windows 7 64-bit SP1 | |
| Sensor Node Sj | Mainboard | ASUSTeK Computer INC. UX303LN |
| CPU | Intel Core i3/i5/i7 4xxx @ 1.70 GHz | |
| Memory | 4.00 GB Single-Channel DDR3 @ 798 MHz | |
| OS | Windows 8.1 64-bit | |
| Gateway Node GWN | Mainboard | IBM 46W9191 |
| CPU | Intel Xeon E3 1231 v3 @ 3.40 GHz 3.40 GHz | |
| Memory | 8.00 GB Dual-Channel DDR3 @ 800 MHz | |
| OS | Windows Server 2008 R2 Standard 64-bit SP1 | |
| Used Programming Language and Algorithms | ||
| C/C++ | ||
| Hash function: SHA-1 | ||
5.2. Functionality Comparisons
| Vaidya et al. [15] | Li et al. [9] | Kim et al. [16] | Our Scheme | |
|---|---|---|---|---|
| Resisting replay attacks | Yes | Yes | Yes | Yes |
| Resisting impersonation attacks | No | No | No | Yes |
| Resisting gateway node by passing attacks | No | Yes | Yes | Yes |
| Resisting parallel session attacks | Yes | Yes | Yes | Yes |
| Resisting password guessing attacks | Yes | Yes | Yes | Yes |
| Resisting sensor node capture attacks | No | Yes | Yes | Yes |
| Resisting man-in-the-middle attacks | No | Yes | No | Yes |
| Resisting lost smartcard attacks | No | Yes | No | Yes |
| Resisting privileged-insider attacks | Yes | Yes | Yes | Yes |
| Resisting stolen-verifier attacks | Yes | No | Yes | Yes |
| Providing session key security | No | Yes | No | Yes |
| Providing privacy protection of users | No | No | No | Yes |
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Das, M.L. Two-factor user authentication scheme in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Delgado-Mohatar, O.; Fuster-Sabater, A.; Sierra, J.M. A light-weight authentication scheme for wireless sensor networks. Ad Hoc Netw. 2011, 9, 727–735. [Google Scholar] [CrossRef]
- Li, Z.; Gong, G. Computationally efficient mutual entity authentication in wireless sensor networks. Ad Hoc Netw. 2011, 9, 204–215. [Google Scholar] [CrossRef]
- Li, C.T.; Hwang, M.S. A lightweight anonymous routing protocol without public key en/decryptions for wireless ad hoc networks. Inform. Sci. 2011, 181, 5333–5347. [Google Scholar] [CrossRef]
- Mi, Q.; Stankovic, J.A.; Stoleru, R. Practical and secure localization and key distribution for wireless sensor networks. Ad Hoc Netw. 2012, 10, 946–961. [Google Scholar] [CrossRef]
- Han, K.; Kim, K.; Choi, W.; Choi, H.H.; Seo, J.; Shon, T. Efficient authenticated key agreement protocols for dynamic wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2012, 14, 251–269. [Google Scholar]
- Poornima, A.S.; Amberker, B.B. Secure end-to-end data aggregation (seeda) protocols for wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2013, 17, 193–219. [Google Scholar]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Lee, C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors 2013, 13, 9589–9603. [Google Scholar] [PubMed]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C.; Wang, L.J.; Liu, C.J. A secure billing service with two-factor user authentication in wireless sensor networks. Int. J. Innov. Comput. Inform. Contr. 2011, 7, 4821–4831. [Google Scholar]
- Li, C.T.; Lee, C.C.; Lee, C.W. An improved two-factor user authentication protocol for wireless sensor networks using elliptic curve cryptography. Sens. Lett. 2013, 11, 958–965. [Google Scholar] [CrossRef]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secure authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef] [PubMed]
- Vaidya, B.; Makrakis, D.; Mouftah, H. Two-factor mutual authentication with key agreement in wireless sensor networks. Secur. Commun. Netw. 2012. [Google Scholar] [CrossRef]
- Kim, J.; Lee, D.; Jeon, W.; Lee, Y.; Won, D. Security analysis and improvements of two-factor mutual authentication with key agreement in wireless sensor networks. Sensors 2014, 14, 6443–6462. [Google Scholar] [CrossRef] [PubMed]
- Bellare, M.; Pointcheval, D.; Rogaway, P. Authenticated key exchange secure against dictionary attacks. Proc. Adv. Cryptol. Eurocrypt 2000, 1807, 122–138. [Google Scholar]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-based authenticated key exchange protocols using Diffie-Hellman. Proc. Adv. Cryptol. Eurocrypt 2000, 1807, 156–171. [Google Scholar]
- Lee, T.F.; Hwang, T. Provably secure and efficient authentication techniques for the global mobility network. J. Syst. Soft. 2011, 84, 1717–1725. [Google Scholar] [CrossRef]
- Shoup, V. Sequences of Games: A Tool for Taming Complexity in Security Proofs, Manuscript. Available online: http:// www.shoup.net (accessed on 18 January 2015).
- Lee, T.F. User authentication scheme with anonymity, unlinkability and untrackability for global mobility networks. Secur. Commun. Netw. 2013, 6, 1404–1413. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chang, I.-P.; Lee, T.-F.; Lin, T.-H.; Liu, C.-M. Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors 2015, 15, 29841-29854. https://doi.org/10.3390/s151229767
Chang I-P, Lee T-F, Lin T-H, Liu C-M. Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors. 2015; 15(12):29841-29854. https://doi.org/10.3390/s151229767
Chicago/Turabian StyleChang, I-Pin, Tian-Fu Lee, Tsung-Hung Lin, and Chuan-Ming Liu. 2015. "Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks" Sensors 15, no. 12: 29841-29854. https://doi.org/10.3390/s151229767
APA StyleChang, I.-P., Lee, T.-F., Lin, T.-H., & Liu, C.-M. (2015). Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks. Sensors, 15(12), 29841-29854. https://doi.org/10.3390/s151229767








