Achieving Network Level Privacy in Wireless Sensor Networks †
Abstract
:1. Introduction
- Sender node identity privacy: no intermediate node can get any information about who is sending the packets except the source, its immediate neighbors and the destination,
- Sender node location privacy: no intermediate node can have any information about the location (in terms of physical distance or number of hops) about the sender node except the source, its immediate neighbors and the destination,
- Route privacy: no node can predict the information about the complete path (from source to destination). Also, a mobile adversary gets no clue to trace back the source node either from the contents and/or directional information of the captured packet(s), and
- Data packet privacy: no node can see the information inside in a payload of the data packet except the source and the destination.
- A new Identity, Route and Location (IRL) privacy algorithm is proposed that ensures the anonymity of source node’s identity and location. It also assures that the packets will reach their destination by passing through only trusted intermediate nodes.
- A new reliable Identity, Route and Location (r-IRL) privacy algorithm is proposed, which is the extension of our proposed IRL algorithm. This algorithm has the ability to forward packets from multiple secure paths to increase the packet reach-ability.
- A new data privacy mechanism is proposed, which is unique in the sense that it provides data secrecy and packet authentication in the presence of identity anonymity.
2. Related Work
2.1. Privacy Schemes
2.2. Geographic Routing Schemes
3. Network, Assumptions and Adversary Model
3.1. Network Model
3.2. Assumptions
3.3. Adversary Model
- Device-rich: the adversary is equipped with devices like antenna and spectrum analyzers, so that the adversary can measure the angle of arrival of the packet and received signal strength. These devices will help the adversary to find out the immediate sender of the packet and move to that node. This kind of hop-by-hop trace back mechanism will be carried out by the adversary until the actual sender node is reached.
- Resource-rich: the adversary has no resource constraint in computation power, memory or energy.
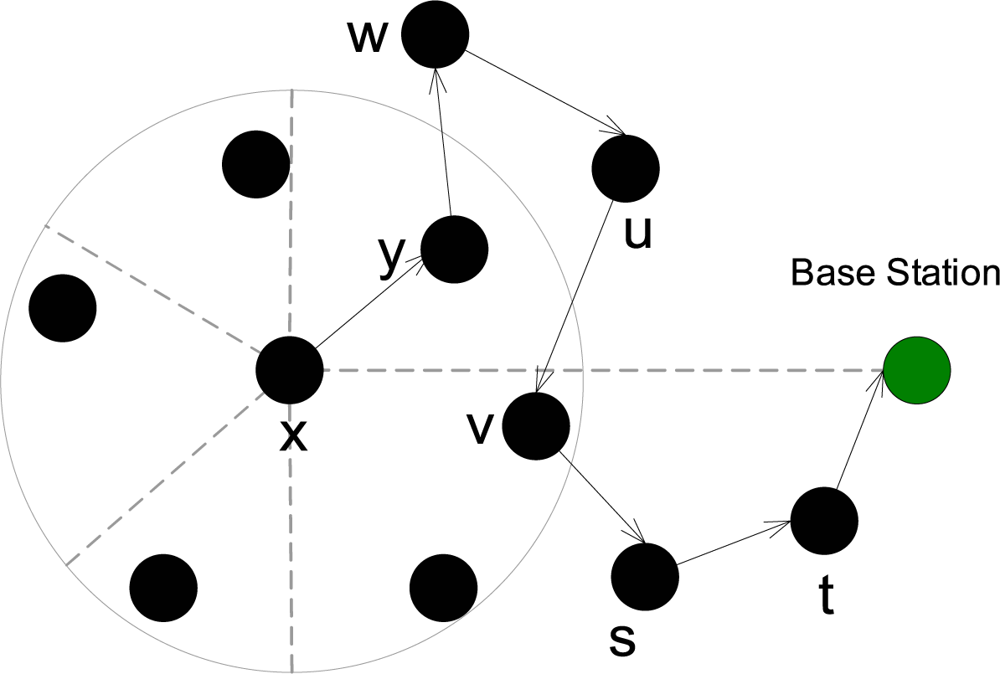
4. Proposed Scheme
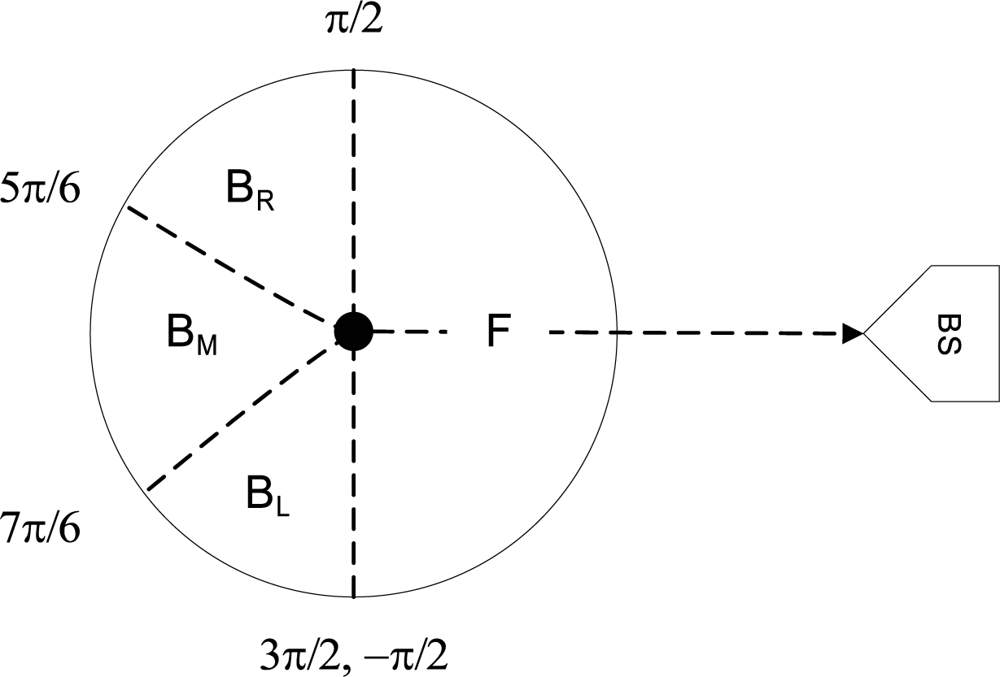
4.1. Concepts and Definitions
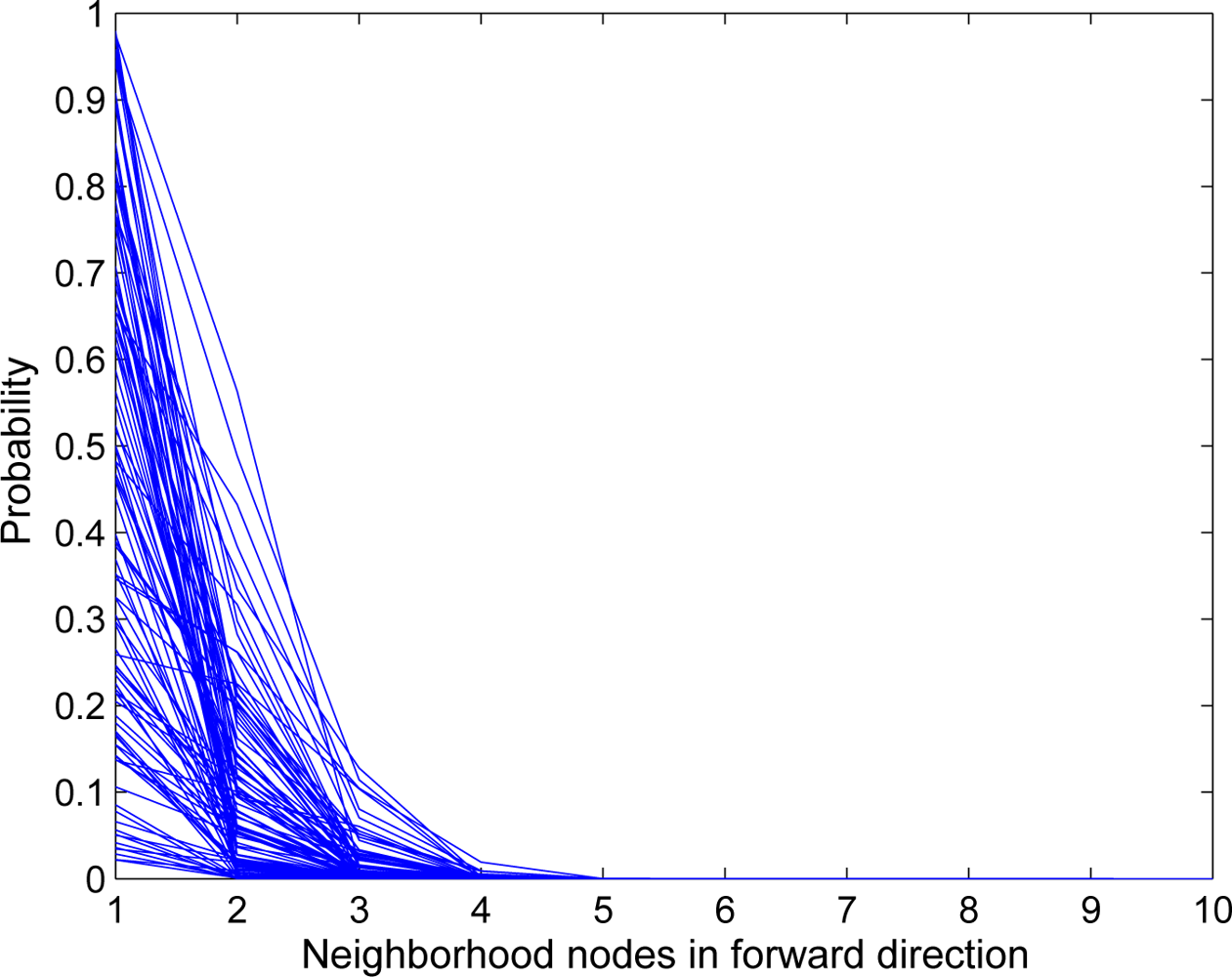
4.2. Identity, Route, and Location Privacy (IRL)
| 1: | prevhop ← ∅; nexthop ←∅; |
| 2: | if M(tF) ≠ ∅ then |
| 3: | nexthop(k) = Rand(M (tF)); |
| 4: | else |
| 5: | if M(tBr) ∪ M(tBl) ≠ ∅ then |
| 6: | nexthop(k) = Rand(M (tBr) ∪ M (tBl)); |
| 7: | else if M(tBm ≠ ∅ then |
| 8: | nexthop(k) = Rand(M (tBm)); |
| 9: | else |
| 10: | Drop packet and Exit; |
| 11: | end if |
| 12: | end if |
| 13: | Set prevhop = myid; |
| 14: | Form pkt p = {prevhop; nexthop; seqID; payload}; |
| 15: | Create Signature and save in buffer; |
| 16: | Forward packet to nexthop; |
| 17: | Set timer |
| 18: | while Δt = true do |
| 19: | Signature remains in buffer; |
| 20: | end while |
| 21: | Signature removed from buffer; |
| 1: | nexthop ← ∅; |
| 2: | Mtemp = ∅ |
| 3: | if Signature of new packet already exists in buffer then |
| 4: | Mtemp = {Mtemp} + LasttimePrevhop |
| 5: | Mtemp = {Mtemp} + LasttimeNexthop |
| 6: | Set counter = timesReceviedBefore + 1; |
| 7: | Remove signature from buffer; |
| 8: | if counter = 3 then |
| 9: | Drop packet and exit; |
| 10: | end if |
| 11: | end if |
| 12: | Mtemp = {Mtemp} + prevhop |
| 13: | if (M(tF) − {M(tF) ∩ Mtemp}) ≠ ∅ then |
| 14: | nexthop(k) = Rand(M(tF) − {M(tF) ∩ Mtemp}); |
| 15: | else |
| 16: | if packet came from Br then |
| 17: | Mtemp1 = M(tBl) ∪ M(tBm) |
| 18: | if Mtemp1 ≠ ∅ then |
| 19: | nexthop(k) = Rand(Mtemp1); |
| 20: | else if M(tBr) ≠ ∅ then |
| 21: | nexthop(k) = Rand(M(tBr) − {M(tBr) ∩ Mtemp}); |
| 22: | else |
| 23: | Drop packet and Exit; |
| 24: | end if |
| 25: | else if packet came from Bl then |
| 26: | Mtemp2 = M(tBr) ∪ M(tBm) |
| 27: | if Mtemp2 ≠ ∅ then |
| 28: | nexthop(k) = Rand(Mtemp2 − {Mtemp2 ∩ Mtemp}); |
| 29: | else if M(tBl) ≠ ∅ then |
| 30: | nexthop(k) = Rand(M(tBl) − {M(tBl) ∩ Mtemp}); |
| 31: | else |
| 32: | Drop packet and Exit; |
| 33: | end if |
| 34: | else |
| 35: | Mtemp3 = M(tBr) ∪M(tBl) |
| 36: | if Mtemp3 ≠ ∅ then |
| 37: | nexthop(k) = Rand(Mtemp3 − {Mtemp3 ∩Mtemp}); |
| 38: | else if M(tBm) ≠ ∅ then |
| 39: | nexthop(k) = Rand(M(tBm) − {M(tBm)∩Mtemp}); |
| 40: | else |
| 41: | Drop packet and Exit; |
| 42: | end if |
| 43: | end if |
| 44: | end if |
| 45: | Rest is same as Algorithm 1 from lines 13:21; |
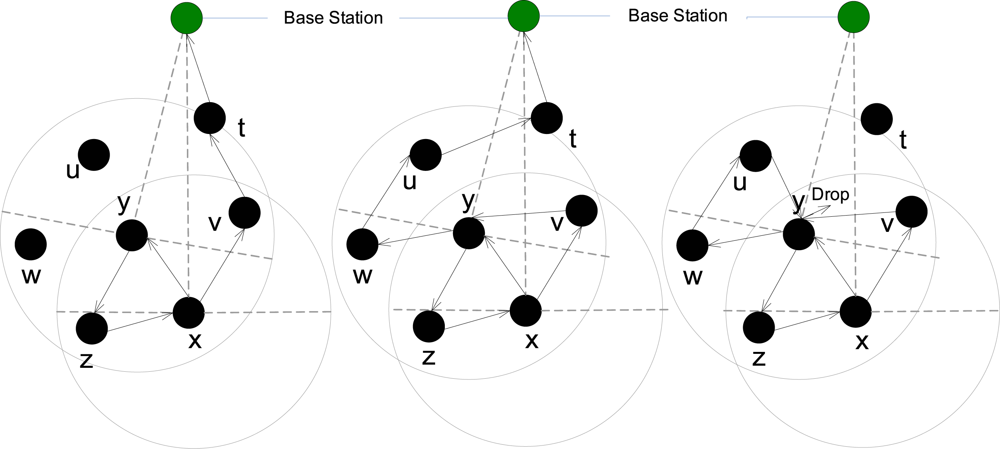
4.3. Reliable Identity, Route, and Location Privacy (r-IRL)
4.4. Data Privacy
5. Analysis and Evaluation
5.1. Security Resiliency Analysis
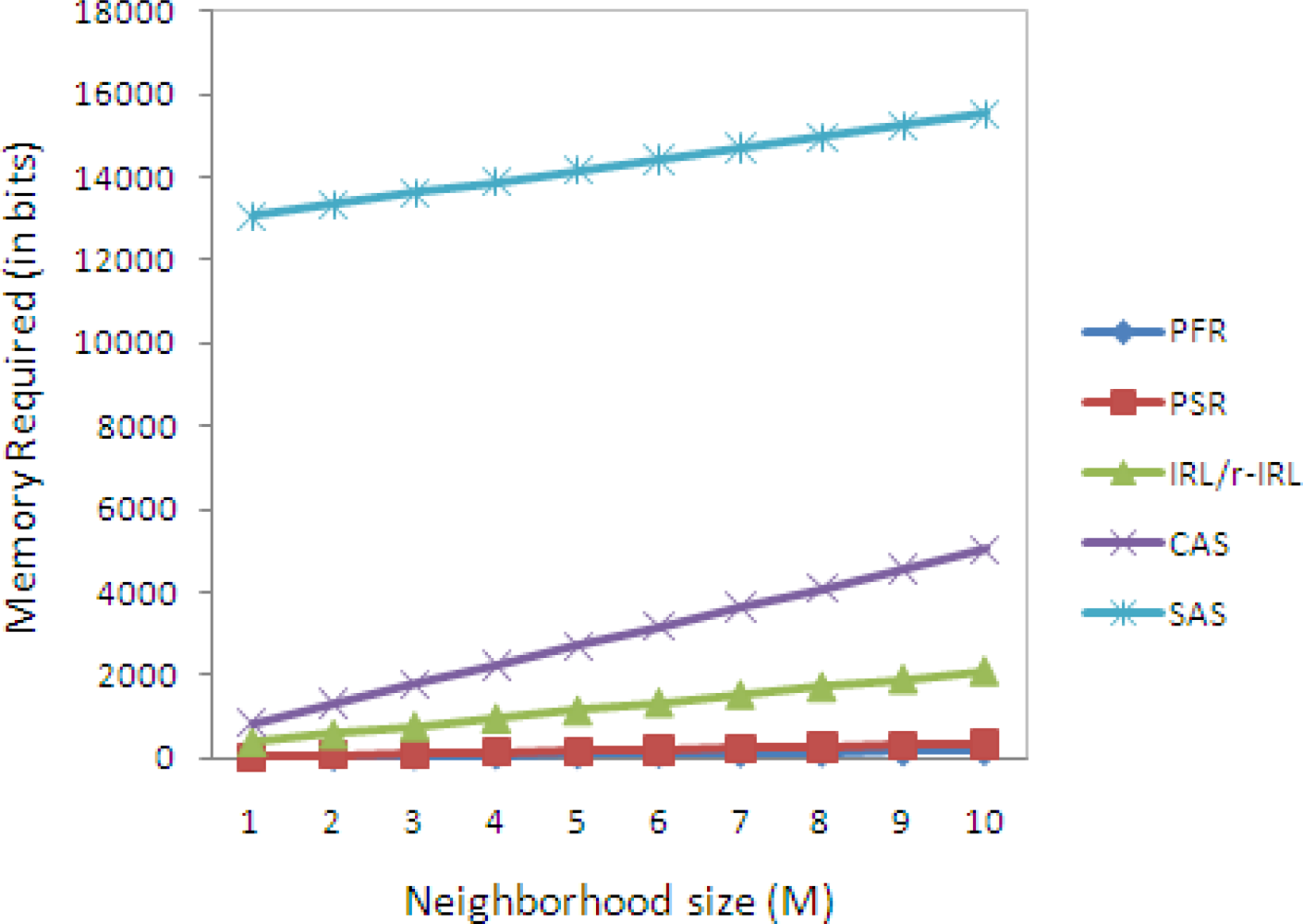
5.2. Memory Consumption Analysis
- In our proposed schemes, packets always follow different routes. Therefore, the probability of a single node to be overloaded is very low.
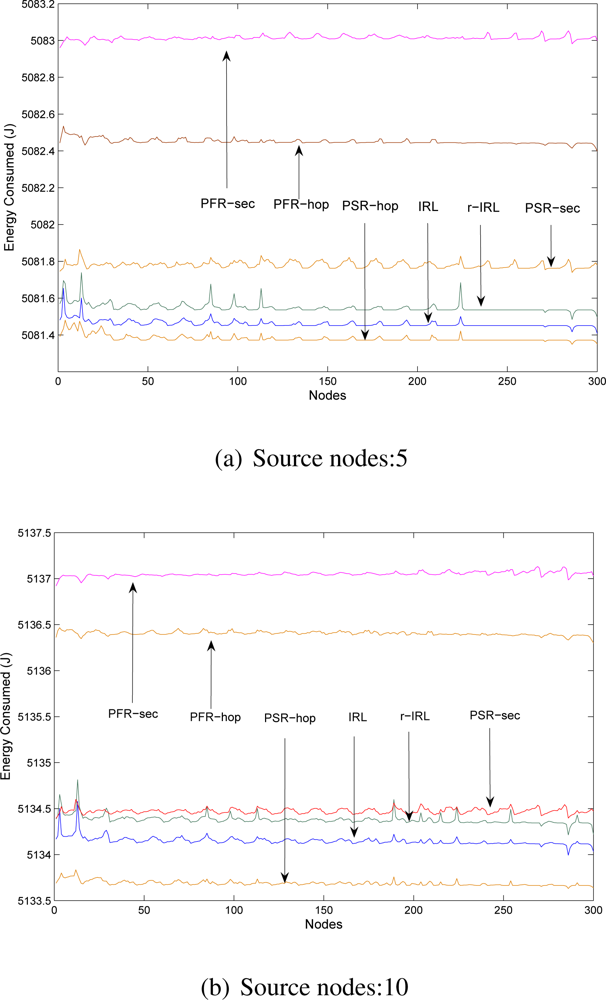
5.3. Energy Consumption Analysis
- Phantom single path routing scheme with hop-based approach (PSR-hop).
- Phantom single path routing scheme with sector-based approach (PSR-sec).
- Phantom flood routing scheme with hop-based approach (PFR-hop).
- Phantom flood routing scheme with sector-based approach (PFR-sec).
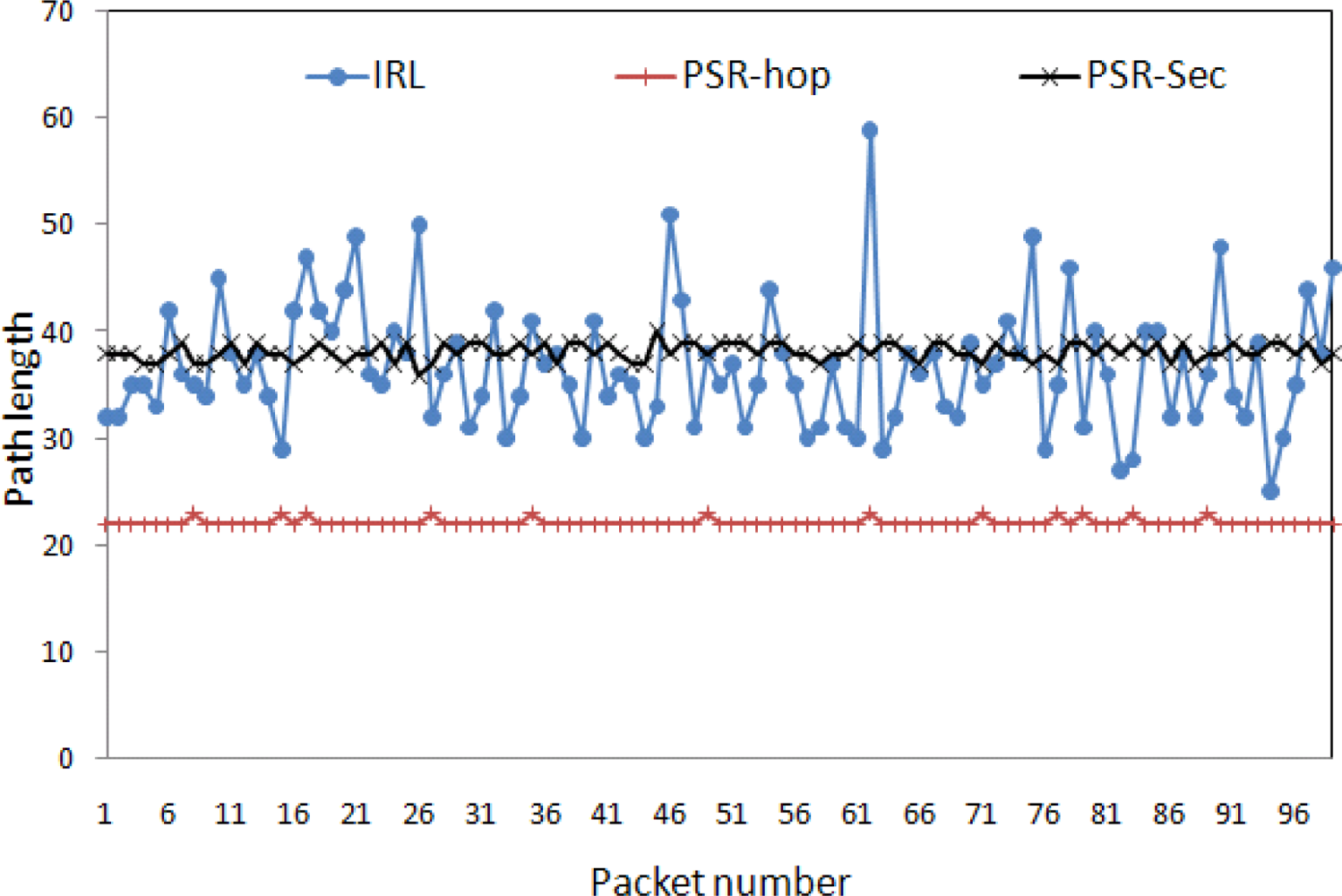
5.4. Path Diversity Analysis
- Length variation: Path could be long or short and mainly dependent on routing scheme. For example, packets always reach to the destination via shortest path. In this scheme, packets may reach to the destination via longer path if any node is not working properly within the shortest available path. With respect to the route privacy, length variation provides minimum route privacy. If we have longer paths, then it will increase time for an adversary to find out actual source node or vice versa. So, the longer path increases safety time.
- Path variation: Each packet may follow different route. It is also dependent on routing strategy. For example, routing scheme make decision about next hop based on the energy level of neighboring nodes. With this approach, one can achieve limited path variation. With respect to the route privacy, if we have more path variation, then it will become clueless for an adversary to guess from where next packet will come.
5.5. Discussion
6. Conclusions and Future work
- †This paper is an extended version of our paper entitled “Network level privacy for wireless sensor networks” that has been published in proceedings of the 4th International Conference on Information Assurance and Security (IAS 08), that was held in Naples, Italy in September 2008 (pp. 261–266).
Acknowledgments
References and Notes
- Xi, Y.; Schwiebert, L.; Shi, W. Preserving Source Location Privacy in Monitoring-Based Wireless Sensor Networks. Proceedings of Parallel and Distributed Processing Symposium (IPDPS 2006), Rhodes Island, Greece; 2006. [Google Scholar]
- Habitat monitoring on Great Duck Island (Maine, USA). 2002. Available online: http://ucberkeley.citris-uc.org/research/projects/great_duck_island (accessed on 21 August, 2009).
- Ozturk, C.; Zhang, Y.; Trappe, W. Source-Location Privacy in Energy-Constrained Sensor Network Routing. Proceedings of the 2nd ACM workshop on Security of Ad hoc and Sensor Networks, Washington, DC, WA, USA; 2004; pp. 88–93. [Google Scholar]
- Kamat, P.; Zhang, Y.; Trappe, W.; Ozturk, C. Enhancing Source-Location Privacy in Sensor Network Routing. Proceedings of the 25th IEEE International conference on Distributed Computing Systems, Columbus, OH, USA; 2005; pp. 599–608. [Google Scholar]
- Misra, S.; Xue, G. Efficient Anonymity Schemes for Clustered Wireless Sensor Networks. Int. J. Sens. Netw 2006, 1, 50–63. [Google Scholar]
- Wood, A.D.; Fang, L.; Stankovic, J.A.; He, T. SIGF: A Family of Configurable, Secure Routing Protocols for Wireless Sensor Networks. Proceedings of the 4th ACM Workshop on Security of Ad Hoc and Sensor Networks, Alexandria, VA, USA; 2006; pp. 35–48. [Google Scholar]
- Ouyang, Y.; Le, Z.; Chen, G.; Ford, J.; Makedon, F. Entrapping Adversaries for Source Protection in Sensor Networks. Proceedings of the 2006 International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM’06), Niagara-Falls, Buffalo, NY, USA; 2006; pp. 23–34. [Google Scholar]
- Zorzi, M.; Rao, R.R. Geographic Random Forwarding (GeRaF) for Ad Hoc and Sensor Networks: Multihop Performance. IEEE Tran. Mob. Comput 2003, 2, 337–348. [Google Scholar]
- Zorzi, M.; Rao, R.R. Geographic Random Forwarding (GeRaF) for Ad Hoc and Sensor Networks: Energy and Latency Performance. IEEE Tran. Mob. Comput 2003, 2, 349–365. [Google Scholar]
- Capone, A.; Pizziniaco, L.; Filippini, I.; de la Fuente, M.G. SiFT: An Efficient Method for Trajectory Based Forwarding. Proceedings of International Symposium on Wireless Communication Systems, Siena, Italy; 2005; pp. 135–139. [Google Scholar]
- Blum, B.; He, T.; Son, S.; Stankovic, J. IGF: A State-Free Robust Communication Protocol for Wireless Sensor Networks; Technical Report CS-2003-11; Department of Computer Science, University of Virginia, USA; 2003. [Google Scholar]
- RYU, J.; Kim, S.G.; Choi, H.H.; An, S.S.; Ahn, S.Y.; Kim, B.J. Method and System for Locating Sensor Node in Sensor Network Using Transmit Power Control. U.S. Patent Application: 2009/0128298 A1. 2009. [Google Scholar]
- Barbeau, M.; Kranakis, E.; Krizanc, D.; Morin, P. Improving Distance Based Geographic Location Techniques in Sensor Networks. Proceedings of 3rd International Conference on Ad Hoc Networks and Wireless, Vancouver, British Columbia; 2004; pp. 197–210. [Google Scholar]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security Protocols for Sensor Networks. Wirel. Netw 2002, 8, 521–534. [Google Scholar]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A Link Layer Security Architecture for Wireless Sensor Networks. Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA; 2004; pp. 162–175. [Google Scholar]
- Lopez, J. Unleashing Public-Key Cryptography inWireless Sensor Networks. J. Comput. Security 2006, 14, 469–482. [Google Scholar]
- Gaubatz, G.; Kaps, J.-P.; Sunar, B. Public Key Cryptography in Sensor Networks-Revisited. Lect. Note. Comput. Sci 2006, 3313, 2–18. [Google Scholar]
- Armenia, S.; Morabito, G.; Palazzo, S. Analysis of Location Privacy/Energy Efficiency Tradeoffs in Wireless Sensor Networks. IFIP-Networking 2007, LNCS 4479, Atlanta, GA, USA, 2007; 215–226. [Google Scholar]
- Shaikh, R.A.; Jameel, H.; d’Auriol, B.J.; Lee, H.; Lee, S.; Song, Y.-J. Intrusion-Aware Alert Validation Algorithm for Cooperative Distributed Intrusion Detection Schemes of Wireless Sensor Networks. Sensors 2009, 9, 5989–6007. [Google Scholar]
- Shaikh, R.A.; Jameel, H.; Lee, S.; Song, Y.J.; Rajput, S. Trust Management Problem in Distributed Wireless Sensor Networks. Proceedings of 12th IEEE International Conference on Embedded Real Time Computing Systems and its Applications (RTCSA 2006); IEEE Computer Society: Sydney, Australia, 2006; pp. 411–415. [Google Scholar]
- Jiang, P. A New Method for Node Fault Detection in Wireless Sensor Networks. Sensors 2009, 9, 1282–1294. [Google Scholar]
- Shaikh, R.A.; Jameel, H.; J. d’Auriol, B.; Lee, H.; Lee, S.; Song, Y.-J. Group-based Trust Management Scheme for Clustered Wireless Sensor Networks. IEEE Trans. Parallel Dist. Sys 2009, 20, 1698–1712. [Google Scholar]
- Buchegger, S.; Boudec, J.-Y.L. A Robust Reputation System for Peer-to-Peer and Mobile Ad-hoc Networks. Proceedings of P2PEcon, Cambridge, MA, USA; 2004. [Google Scholar]
- Gupta, S. Automatic Detection of DOS Routing Attacks in Wireless Sensor Networks, Master thesis, University of Houston, Houston, TX, USA. 2006.
- Du, X.; Guizani, M.; Xiao, Y.; Chen, H.H. Two Tier Secure Routing Protocol for Heterogeneous Sensor Networks. IEEE Trans. Wirel. Commun 2007, 6, 3395–3401. [Google Scholar]
- Karlof, C.; Wagner, D. Secure Routing in Wireless Sensor Networks: Attacks and Countermeasures. Proceedings of the First IEEE International Workshop on Sensor Network Protocols and Applications (WSNA03); IEEE Computer Society: Anchorage, Alaska, USA, 2003; pp. 113–127. [Google Scholar]
- Srinivasan, A.; Teitelbaum, J.; Liang, H.; Wu, J.; Cardei, M. Reputation and Trust-based Systems for Ad Hoc and Sensor Networks. In Algorithms and Protocols for Wireless Ad Hoc and Sensor Networks; Boukerche, A., Ed.; Wiley & Sons: New Jersey, NJ, USA, 2006. [Google Scholar]
- Durresi, A.; Paruchuri, V.; Durresi, M.; Barolli, L. Anonymous routing for mobile wireless ad hoc networks. Int. J. Distrib. Sens. Netw 2007, 3, 105–117. [Google Scholar]
- Pfleeger, C.P.; Pfleeger, S.L. Security in Computing, 4th ed.; Prentice Hall: New Jersey, NJ, USA, 2006. [Google Scholar]
- Latif, R.; Hussain, M. Hardware-Based Random Number Generation in Wireless Sensor Networks(WSNs). Lect. Not. Comput. Sci 2009, 5576, 732–740. [Google Scholar]
- Seetharam, D.; Rhee, S. An Efficient Pseudo Random Number Generator for Low-Power Sensor Networks. Proceedings of Annual IEEE International Conference on Local Computer Networks (LCN’04), Tampa, FL, USA; 2004. [Google Scholar]
- Tilak, S.; Abu-Ghazaleh, N.B.; Heinzelman, W. A Taxonomy of Wireless Micro-Sensor Network Models. SIGMOBILE Mob. Comput. Commun. Rev 2002, 6, 28–36. [Google Scholar]
- Shaikh, R.A.; Lee, S.; Khan, M.A.U.; Song, Y.J. LSec: Lightweight Security Protocol for Distributed Wireless Sensor Network. Lect. Not. Comput. Sci 2007, 4217, 367–377. [Google Scholar]
- Jamieson, K.; Balakrishnan, H.; Tay, Y.C. Sift: A MAC Protocol for Event-DrivenWireless Sensor Networks. Lect. Not. Comput. Sci 2006, 3868, 260–275. [Google Scholar]
- Lee, S.H.; Cho, B.-H.; Choi, L.; Kim, S.-J. Event-Driven Power Management for Wireless Sensor Networks. Lect. Not. Comput. Sci 2007, 4761, 419–428. [Google Scholar]
- Figueiredo, C.M.S.; Nakamura, E.F.; Loureiro, A.A.F. A Hybrid Adaptive Routing Algorithm for Event-Driven Wireless Sensor Networks. Sensors 2009, 9, 7287–7307. [Google Scholar]
- Al-Karaki, J.N.; Kamal, A.E. Routing Techniques in Wireless Sensor Networks: A Survey. IEEE Wirel. Commun 2004, 11, 6–28. [Google Scholar]
- Chenyang, Lu; Blum, B.M.; Abdelzaher, T.F.; Stankovic, J.A.; He, T. RAP: A Real-Time Communication Architecture for Large-Scale Wireless Sensor Networks. Proceedings of 8th IEEE Real-Time and Embedded Technology and Applications Symposium, San Jose, CA, USA; 2002; pp. 55–66. [Google Scholar]
- Amin, S.O.; Siddiqui, M.S.; Hong, C.S.; Lee, S. RIDES: Robust Intrusion Detection System for IP-Based Ubiquitous Sensor Networks. Sensors 2009, 9, 3447–3468. [Google Scholar]
- Bloom, B.H. Space/Time Trade-Offs in Hash Coding with Allowable Errors. Commun. ACM 1970, 13, 422–426. [Google Scholar]
- Szymanski, B.K. SENSE: Sensor Network Simulator and Emulator. Available Online: http://www.ita.cs.rpi.edu/sense/index.html (accessed on 25 April, 2009).
- Crossbow Inc. Wireless Sensor Networks, MICA2 Series. Available Online: http://www.xbow.com (accessed on 21 June, 2008).

| PFR [3] | PSR [4] | SAS &CAS [5] | CEM [7] | SIGF [6] | GeRaF [8, 9] | SiFT [10] | |
|---|---|---|---|---|---|---|---|
| Required information for routing | ID of destination | Routing table (e.g., destination ID, #of hops etc.) | Depending on a routing scheme | Depending on a routing scheme | Own, destination, & neighborhood locations | Own and destination location | Destination trajectory and own location |
| Transmission mechanism | 1st phase: Point-to-point; 2nd phase: Broadcast | Point-to-point | Depending on a routing scheme | Depending on a routing scheme | Point-to-point | Broadcast | Broadcast |
| Decision place for forwarding | 1st phase: Transmitter; 2nd phase: Receiver | Transmitter | Depending on a routing scheme | Depending on a routing scheme | Transmitter | Receiver | Receiver |
| Criteria for forwarding packet to next hop | 1st phase: random; 2nd phase: flooding | 1st phase: random; 2nd phase: shortest in terms of hops | Depending on a routing scheme | Depending on a routing scheme | Randomly select any trusted node lies in forwarding region | Node that is closer to the destination in terms of location | Node that is closer to the destination in terms of trajectory |
| Identity privacy | Not Available | Not Available | Available | Not Available | Not Available | Not Applicable | Not Applicable |
| Route privacy | Available | Available | Depending on a routing scheme | Depending on a routing scheme | Available | Available | Available |
| Location privacy | Available | Available | Not Available | Available | Available | Not Applicable | Not Applicable |
| Data privacy | Not Available | Not Available | Available | Available | Available | Not Applicable | Not Applicable |
| Neighbor nodeID (Integer) | Direction | Past interactions based on time window | Trust value | |||||
|---|---|---|---|---|---|---|---|---|
| Successful interactions (Sx,y) | Unsuccessful interactions (Ux,y) | |||||||
| 1 | F (00) | 10 | ... | 5 | 4 | ... | 1 | 90 |
| 2 | BR (01) | 2 | ... | 4 | 8 | ... | 2 | 25 |
| ⋮ | ⋮ | ⋮ | ⋮ | ⋮ | ⋮ | ⋮ | ⋮ | ⋮ |
| M | BL(11) | 5 | … | 7 | 0 | … | 3 | 70 |
| PFR [3] | (16+1)M bits |
| PSR [4] | (16+16+1)M bits |
| SAS [5] | K(4M+2N)+16M bits |
| CAS [5] | K(6+7M)+16M bits |
| IRL / r-IRL |
| Network specific | Number of nodes | 300 |
| Distance b/w nodes | 50 units | |
| Mobility of nodes | zero | |
| Node specific | Sensor node’s Initial battery | 1 × 106J |
| Power consumption for trans. | 1.6W | |
| Power consumption for recv. | 1.2 W | |
| Idle power consumption | 1.15W | |
| Carrier sense threshold | 3.65e−10W | |
| Receive power threshold | 1.55e−11W | |
| Frequency | 9.14e8 | |
| Trans. & Recv. antenna gain | 1.0 | |
| Protocol & Application specific | Application | CBR |
| Reliability param. r for r-IRL | 3 | |
| hwalk param. for PFR & PSR | 10 |
© 2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Shaikh, R.A.; Jameel, H.; D’Auriol, B.J.; Lee, H.; Lee, S.; Song, Y.-J. Achieving Network Level Privacy in Wireless Sensor Networks. Sensors 2010, 10, 1447-1472. https://doi.org/10.3390/s100301447
Shaikh RA, Jameel H, D’Auriol BJ, Lee H, Lee S, Song Y-J. Achieving Network Level Privacy in Wireless Sensor Networks. Sensors. 2010; 10(3):1447-1472. https://doi.org/10.3390/s100301447
Chicago/Turabian StyleShaikh, Riaz Ahmed, Hassan Jameel, Brian J. D’Auriol, Heejo Lee, Sungyoung Lee, and Young-Jae Song. 2010. "Achieving Network Level Privacy in Wireless Sensor Networks" Sensors 10, no. 3: 1447-1472. https://doi.org/10.3390/s100301447
APA StyleShaikh, R. A., Jameel, H., D’Auriol, B. J., Lee, H., Lee, S., & Song, Y.-J. (2010). Achieving Network Level Privacy in Wireless Sensor Networks. Sensors, 10(3), 1447-1472. https://doi.org/10.3390/s100301447





