Identity-Based Matchmaking Encryption with Equality Test
Abstract
:1. Introduction
1.1. Motivation
- Confidentiality: The cloud server has no knowledge about the health data concealed in the ciphertext.
- Authenticity: The cloud server is unable to fake any legitimate ciphertext pertaining to the sender and the receiver.
- Anonymity: The cloud server has no knowledge about the identities of the sender and the receiver concealed in the ciphertext.
1.2. Related Works
1.3. Contributions
- Match (i.e., ): the cloud server returns 1, and no further information is revealed other than the fact that the match happened, that is the cloud server learns neither the messages nor the identities , , , .
- Mismatch (i.e., ): the cloud server returns 0, and no further information is revealed other than the fact of the mismatch, that is the cloud server learns neither the messages , nor the identities , , , , , , , .
- We present the notion of the IBME-ET, which not only offers the confidentiality, authenticity, and anonymity of data stored in the cloud, but also provides equality test functionality for ciphertexts generated under different identities without losing the confidentiality, authenticity, and anonymity of the data.
- We put forward the system model and definition of the IBME-ET. With respect to the confidentiality, authenticity, and anonymity, we formulated four security models for the IBME-ET by taking four types of adversaries into account.
- We constructed a concrete IBME-ET scheme on the basis of the BDH assumption and the Gap-BDH assumption. Our scheme was confirmed to be secure and practical by proving its security and evaluating its performance.
1.4. Organization
2. Preliminaries
2.1. Asymmetric Bilinear Groups
- Bilinearity:, and , .
- Non-degeneracy:, , .
2.2. Assumptions
- Bilinear Diffie–Hellman (BDH) assumption: When a tuple is given, no PPT algorithm calculates with non-negligible advantage. Define ’s advantage as
- Gap-bilinear Diffie–Hellman (Gap-BDH) assumption: When a tuple is given, even with the decision BDH oracle , no PPT algorithm calculates with non-negligible advantage [29]. Tuples of the form are known as “BDH tuples”. With , is able to check or not. outputs 1 when ; otherwise, outputs 0. Define ’s advantage as
3. Definitions of IBME-ET
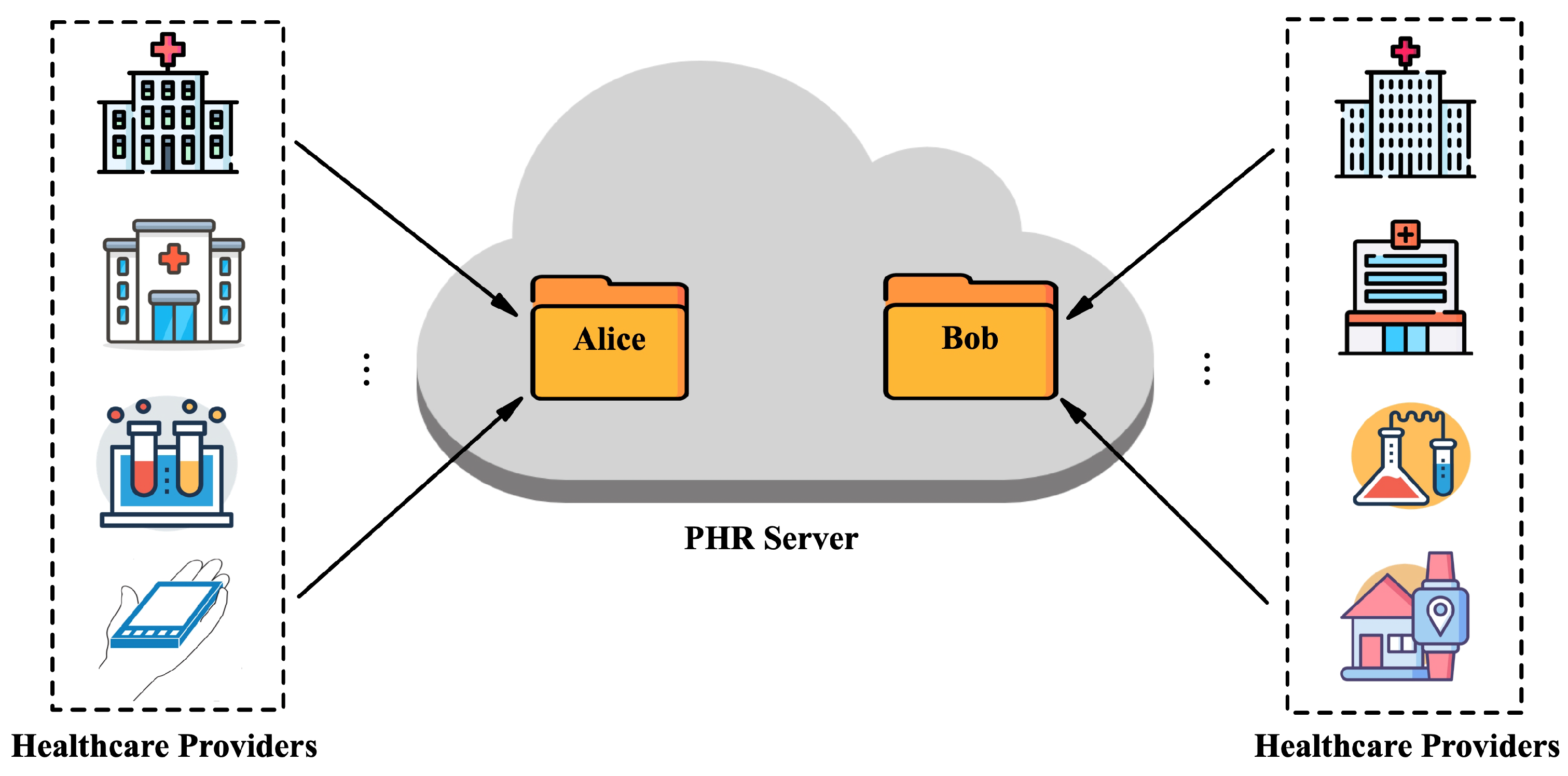
3.1. System Model
- KGC: This entity’s responsibility is to securely generate and distribute encryption keys and decryption keys.
- Sender: This entity’s responsibility is to generate ciphertexts, ensuring the confidentiality, authenticity, and anonymity of the data.
- Receiver: This entity is responsible for collecting and outsourcing ciphertexts from potential senders secretly. It permits the cloud server to test ciphertexts sent by a specific sender without compromising the confidentiality, authenticity, and anonymity of the data.
- Cloud server: This entity’s responsibility is to store the ciphertexts and perform equality tests based on the receivers’ authorizations.
- The KGC utilizes the algorithm SKGen to calculate the encryption key in accordance with the identity of the sender and securely delivers this to the sender. Similarly, the KGC utilizes the algorithm RKGen to calculate the decryption key in accordance with the identity of the receiver and securely delivers this to the receiver.
- A sender identified as executes the algorithm Enc to conceal the message m using encryption key along with a target receiver’s identity , delivering it to the receiver with the ciphertext .
- A receiver identified as executes the algorithm Decc to decrypt the ciphertexts by employing the receiver’s decryption key and the identity of the target sender , delivering the desirable ciphertexts to the cloud server. Specifically, given , , and , the guarantee in the decryption procedure is as follows:
- Match (i.e., ): the message m is obtained by the receiver.
- Mismatch (i.e., ): the receiver obtains neither the message m nor the identities , .
- To test the ciphertexts offered by a target sender, the receiver identified as executes the algorithm Auth to calculate a trapdoor with the identity of the target sender and its decryption key and delivers the trapdoor to the cloud server.
- Utilizing the receivers’ trapdoors, the cloud server executes the algorithm Test to test the ciphertexts sent by the specified senders without learning the messages and identities. Specifically, given and , the guarantee in equality testing procedure is as follows:
- Match (i.e., ): the cloud server returns 1, and the cloud server learns neither the messages nor the identities , , , .
- Mismatch (i.e., ): the cloud server returns 0, and the cloud server learns neither the messages , nor the identities , , , , , , , .
3.2. IBME-ET Definition
- : The system parameters along with the master key are answered.
- : The encryption key for the sender identified as is answered.
- : The decryption key for the receiver identified as is answered.
- : Given the system parameters , an encryption key of the sender , and an identity of the target receiver along with the message m, the corresponding ciphertext C is answered.
- : Given the system parameters , a decryption key of the receiver , and an identity of the target sender along with the ciphertext C, the corresponding message m is answered or the symbol ⊥ to signal the failure of the decryption is answered.
- : Given the system parameters and an identity of the target sender along with a decryption key of the receiver , the corresponding trapdoor is answered.
- : Given the system parameters , two pairs of ciphertext/trapdoors and , if and are generated using the identical message, it answers 1. Otherwise, it answers 0.
- When , always holds.
- Let , , , and . If , , otherwise, , is negligible.
3.3. Security Definitions
- Type-I adversary : Without the trapdoor and decryption key of the receiver, is unable to determine which message the challenge ciphertext is computed from. For , define the security model IND-ID-CCA.
- Type-II adversary : Without the decryption key of the receiver, is unable to obtain the message concealed in the challenge ciphertext. For , define the security model OW-ID-CCA.
- Type-III adversary : Without the decryption key of the receiver and the encryption key of the sender, is unable to determine the corresponding sender and receiver, even if has the trapdoor. For , define the security model ANON-ID-CCA.
- Type-IV adversary : Without the decryption key of the receiver and the encryption key of the sender, is unable to fake any legitimate ciphertext delivered by the sender to the receiver, even if has the trapdoor. For , define the security model sUF-ID-CMA.
- : Once the identity of the sender is received, answers the encryption key .
- : Once the identity of the receiver is received, answers the decryption key .
- : Once the identity of the sender , the identity of the target receiver , and a message m are received, answers the result of .
- : Once the identity of the receiver , the identity of the target sender , and a ciphertext C are received, answers the result of .
- : Once the identity of the target sender and the identity of the receiver are received, answers the corresponding trapdoor .
- 1.
- Setup: utilizes the algorithm to calculate the master key and the system parameters and delivers to .
- 2.
- Phase 1: can issue queries to the oracles: , , , .
- 3.
- Challenge: sends identities and equal-length messages to . Subsequently, randomly selects and answers with the challenge ciphertext .
- 4.
- Phase 2: makes queries like in 1.
- 5.
- Guess: answers a guess and is winning when . ’s advantage is defined as Pr
- 1.
- Setup: Same as Definition 1.
- 2.
- Phase 1: can issue queries to the oracles: , , , .
- 3.
- Challenge: sends identities to . Subsequently, randomly chooses a message and answers to with the challenge ciphertext .
- 4.
- Phase 2: makes queries like in 1.
- 5.
- Guess: answers a guess and is winning when . ’s advantage is defined as Pr
- 1.
- Setup: Same as Definition 1.
- 2.
- Phase 1: can issue queries to the oracles: , , , , .
- 3.
- Challenge: sends identities , and a message to . Subsequently, randomly chooses and answers to with the challenge ciphertext and the challenge trapdoor .
- 4.
- Phase 2: makes queries like in 1.
- 5.
- Guess: answers a guess and is winning when . ’s advantage is defined as Pr
- , , and .
- , , and .
- , .
- 1.
- Setup: Same as Definition 1.
- 2.
- Queries: can issue queries to the oracles: , , , , .
- 3.
- Forgery: answers a triple . is winning when , . ’s advantage is defined as Pr wins].
4. Our Construction
- Setup(): The following steps are taken:
- Randomly select the generators along with .
- Randomly select numbers , and set , , , , .
- Secure hash functions are defined: , , , , , , , , and .
- Return the master key along with the system parameters , where
- SKGen(): Let . This algorithm produces the encryption key
- RKGen(): Let . This algorithm produces the decryption key .
- Enc(): Let and . The ciphertext is calculated as below:
- Randomly select and , and calculate .
- Calculate , and .
- Calculate the following numbers:
- (): Let , . The following steps are taken:
- Calculate and .
- Obtain by computing .
- Calculate .
- If and hold, answer ; otherwise, answer ⊥.
- Auth(): Let and . The following steps are taken:
- Randomly select , and calculate .
- Return the trapdoor .
- Test(): Let , , , , and . The following steps are taken:
- Calculate
- Calculate
- Check whether holds. When it holds, answer 1 or 0 otherwise.
- Regarding Condition 1, when and , we haveThus, when and , always holds.
- Regarding Condition 2, if , we haveIf , then , so otherwise, is negligible due to the hash functions and being collision-resistant.
5. Security Analysis
- To reveal the message m, it is necessary to calculate .
- To obtain , which is used for the equality test, it is necessary to calculate .
- To distinguish the identities of the sender and the receiver concealed in the ciphertext, it is necessary to calculate .
- To fake any legitimate ciphertext pertaining to the sender and the receiver , it is necessary to calculate .
- (1)
- Setup: randomly selects , . randomly chooses , calculates , , , , and , sets , and delivers this to with . implicitly sets , because has no knowledge about a. preserves the and lists to simulate and . Afterwards, randomly selects .
- (2)
- Phase1: answers ’s queries.
- : When , randomly selects , inserts a tuple into , and answers I. Otherwise, answers .
- : Suppose as the i-th different query. When , randomly selects , inserts a tuple into , and returns . Otherwise, has , inserts a tuple into , and returns .
- : Suppose as the j-th different query. When , randomly selects , inserts a tuple into , and returns . Otherwise, has , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . Subsequently, searches the tuple in . When , selects randomly, inserts a tuple into , and returns . Otherwise, has , inserts a tuple into , and returns .
- : randomly chooses , inserts a tuple into , and answers R.
- : randomly chooses , inserts a tuple into , and answers .
- : randomly selects , inserts a tuple into , and returns .
- : randomly selects , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . There is a tuple in . Next, returns .
- : performs a simulation algorithm to query . There are a tuple in and a tuple in . When , returns . Otherwise, is aborted by failure.
- : Let . performs a simulation algorithm to query and .
- -
- When , can query to obtain and returns the outcome of the algorithm .
- -
- Otherwise, can query to obtain and calculates . For each tuple in , calculates and calculates . If and there exists a tuple in such that holds, it outputs . Once has no such tuple, outputs ⊥.
- : Let . performs a simulation algorithm to query and . When , can query to obtain , returns . Otherwise, executes the following operations:
- -
- When , is aborted by failure.
- -
- Otherwise, has a tuple and has a tuple , and can query to obtain , calculates , and , randomly selects , calculates , implicitly sets , and returns . is a valid random trapdoor according to and , where
- (3)
- Challenge: offers equal-length messages along with the pair of sender/receiver identities () to . Let . Afterwards, utilizes a simulation algorithm to query and .
- -
- When the -th tuple in is and the -th tuple in is , randomly selects , , and , calculates , , , , , and , and then, sends the challenge ciphertext to .The above construction implicitly sets , , , , where , , .
- -
- Otherwise, is aborted by failure.
- (4)
- Phase2: makes queries like in 1.
- (5)
- Guess: answers a guess . randomly selects a tuple from and returns the BDH instance solution .
- (1)
- Setup: executes like in the proof of Theorem 1.
- (2)
- Phase1: answers ’s queries.
- For , , , , , , and , executes like in the proof of Theorem 1.
- : performs a simulation algorithm to query . Subsequently, searches the tuple in . When , randomly selects , inserts a tuple into , and returns . Otherwise, sets , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . There is a tuple in . Next, returns .
- : performs a simulation algorithm to query . There are a tuple in and a tuple in . When , returns . Otherwise, is aborted by failure.
- : Let . performs a simulation algorithm to query and .
- -
- When , can query to obtain and returns the outcome of the algorithm .
- -
- Otherwise, can query to obtain and calculates . For each tuple in , calculates and calculates . If and there exists a tuple in such that holds, it outputs . When has no such tuple, outputs ⊥.
- : Let . performs a simulation algorithm to query and .
- -
- When , can query to obtain and returns .
- -
- Otherwise, there are a tuple in and a tuple in , and can query to obtain , calculates , , , and , randomly selects , and returns .
- (3)
- Challenge: submits a pair of sender/receiver identities () to . Let . Afterwards, chooses a message randomly and executes a simulation algorithm to query and .
- -
- When the -th tuple in is and the -th tuple in is , randomly selects , , calculates , , , , , , and , and delivers this to with the challenge ciphertext .The above construction implicitly sets , , where , , .
- -
- Otherwise, is aborted by failure.
- (4)
- Phase2: makes issues like in Phase1.
- (5)
- Guess: answers a guess . randomly chooses a tuple from and answers the BDH instance solution .
- (1)
- Setup: randomly selects and . randomly selects , calculates , , , and , sets , and delivers this to with . implicitly sets , because has no knowledge about a. preserves the , , and lists to simulate , , and . Afterwards, randomly selects and randomly chooses .
- (2)
- Phase1: answers ’s queries.
- : executes the following operations.
- -
- When , returns the Gap-BDH instance solution and defines and .
- -
- When , returns the Gap-BDH instance solution and defines and .
- -
- When , returns the Gap-BDH instance solution and defines and .
- -
- When , returns the Gap-BDH instance solution and defines and .
- -
- Otherwise, randomly selects .
Subsequently, inserts into and into and answers I. - : Suppose as the i-th different query. When , inserts a tuple into and returns . When , inserts a tuple into and returns . Otherwise, randomly selects , inserts a tuple into , and returns .
- : Suppose as the j-th different query. When , inserts a tuple into and returns . When , inserts a tuple into and returns . Otherwise, randomly selects , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . Subsequently, searches the tuple in . When , inserts a tuple into and returns . When , inserts a tuple into and returns . Otherwise, randomly selects , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . Subsequently, searches for the tuple in and returns .
- : randomly chooses , inserts a tuple into , and answers R.
- : performs a simulation algorithm to query . Subsequently, randomly selects , inserts a tuple into , and returns .
- : randomly selects , inserts a tuple into , and returns .
- : randomly selects , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . There is a tuple in . When and , answers . Otherwise, is aborted by failure.
- : performs a simulation algorithm to query . There are a tuple in and a tuple in . When and , answers . Otherwise, is aborted by failure.
- : Let . performs a simulation algorithm to query and . When and , can query to obtain and returns . Otherwise, executes as below:
- -
- When or , is aborted by failure.
- -
- When or , executes a simulation algorithm to query . There is a tuple in . Afterwards, randomly selects , , , calculates , and , inserts a tuple into , and returns , where , , , , .
- -
- Otherwise, can query to get , selects , randomly, calculates , , and , and returns , where , , , , .
- : Let . performs a simulation algorithm to query and . When and , can query to obtain and returns the outcome of . Otherwise, executes the following operations:
- -
- When , or m or , or , searches for the tuple in . When has no such tuple, executes as below.When , , . When , , . When , , . When , , . Afterwards, randomly selects , calculates , implicitly sets , sets , and stores in . is a valid random trapdoor according to and , whereNext, calculates . For each tuple in , calculates and . If both and hold, returns m; otherwise, returns ⊥.
- -
- Otherwise, can query to obtain and calculates . For each tuple in , calculates and . If both and hold, returns m; otherwise, returns ⊥.
- : Let . performs a simulation algorithm to query and . There is a tuple in . When and , can query to obtain , calculates , , , returns , and stores into . Otherwise, executes as below:
- -
- When or , is aborted by failure.
- -
- When , , .
- -
- When , , .
- -
- Otherwise, can query to obtain and calculates , .
Subsequently, randomly selects , calculates , implicitly sets , returns , and then, stores in . is a valid random trapdoor according to and , where
- (3)
- Challenge: offers a message and two pairs of sender/receiver identities (), () to . Set , . Afterwards, utilizes a simulation algorithm to query , , , and :
- -
- When the -th tuple in is , the -th tuple in is , the -th tuple in is , and the -th tuple in is , executes the following operations:Firstly, randomly selects and searches for the tuple in . When has no such tuple, sets and . Subsequently, randomly selects , calculates , implicitly sets , obtains , and then, inserts a tuple in . is a valid random trapdoor according to and , whereSecondly, randomly selects , , , calculates , , , , , and .The above construction implicitly sets , where , . is the encryption of according to and , whereEventually, returns the corresponding challenge ciphertext and challenge trapdoor to .
- -
- Otherwise, is aborted by failure.
- (4)
- Phase2: makes issues like in Phase1.
- (5)
- Guess: answers a guess .
- (1)
- Setup: randomly chooses , . randomly selects , calculates , , , and , sets , and delivers this to with . implicitly sets , because has no knowledge about a. preserves the and lists to simulate and . Afterwards, randomly selects .
- (2)
- Queries: answers ’s queries as below:
- : When , randomly selects , inserts into and into , and answers I. Otherwise, answers the Gap-BDH solution , defines and , inserts into and into , and answers I.
- : Suppose as the i-th different query. When , randomly selects , inserts a tuple into , returns . Otherwise, inserts a tuple into and returns .
- : performs a simulation algorithm to query . Subsequently, randomly selects , inserts a tuple into , and returns .
- : Suppose as the j-th different query. When , randomly selects , inserts a tuple into , and returns . Otherwise, inserts a tuple into and returns .
- : performs a simulation algorithm to query . Subsequently, searches for the tuple in and answers .
- : randomly chooses , inserts a tuple into , and answers R.
- : performs a simulation algorithm to query . Subsequently, randomly selects , inserts a tuple into , and returns .
- : randomly selects , inserts a tuple into , and returns .
- : randomly selects , inserts a tuple into , and returns .
- : performs a simulation algorithm to query . There is a tuple in . If , returns . Otherwise, is aborted by failure.
- : performs a simulation algorithm to query . There is a tuple in . If , returns . Otherwise, is aborted by failure.
- : Let . performs a simulation algorithm to query and . There is a tuple in . When , can query to obtain , calculates , and , and answers . Otherwise, executes the following operations:
- -
- When , can query to obtain , calculates , , and , calculates , randomly selects , and returns .
- -
- Otherwise, defines , , calculates , randomly selects , and returns .
- : Let . performs a simulation algorithm to query and . When , can query to obtain and returns . Otherwise, executes the following operations:
- -
- When , can query to obtain , randomly selects , , calculates , , , and , and then, returns , where , , , , .
- -
- Otherwise, defines , , randomly picks , , , calculates , and , inserts a tuple into , and then, returns , where , , , , and .
- : Let . performs a simulation algorithm to query and . When , can query to obtain and returns the outcome of the algorithm . Otherwise, executes the following operations:
- -
- When , can query to obtain , calculates , obtains by querying , calculates , , , , recovers by computing , calculates . If and hold, answers m; otherwise, answers ⊥.
- -
- Otherwise, defines , , calculates , obtains by querying , calculates , and searches for the corresponding tuple in . If there exists no such tuple in , randomly selects and inserts into . Afterwards, recovers by computing and calculates . If and hold, answers m; otherwise, answers ⊥.
- (3)
- Forgery: outputs a triple , where and .
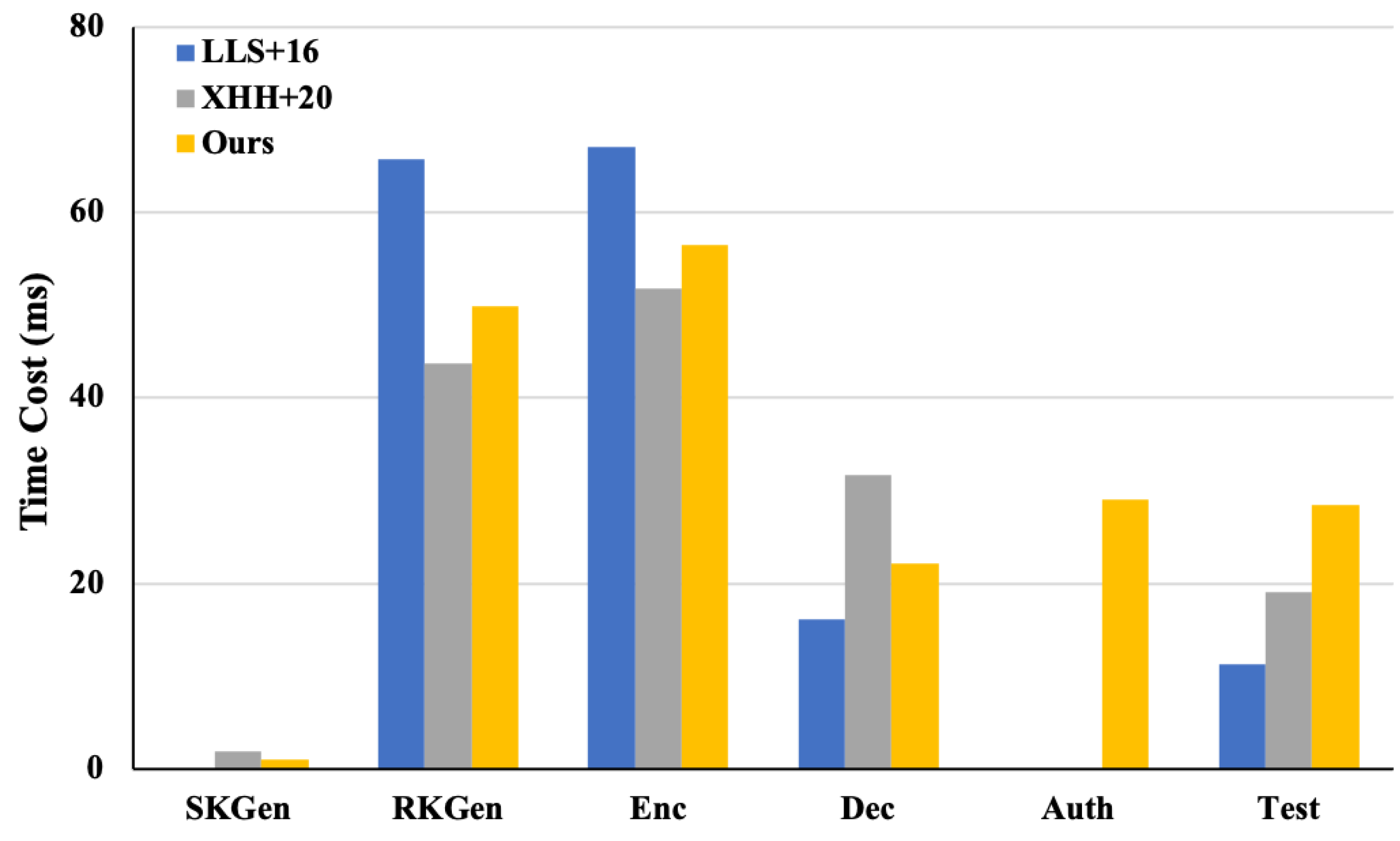
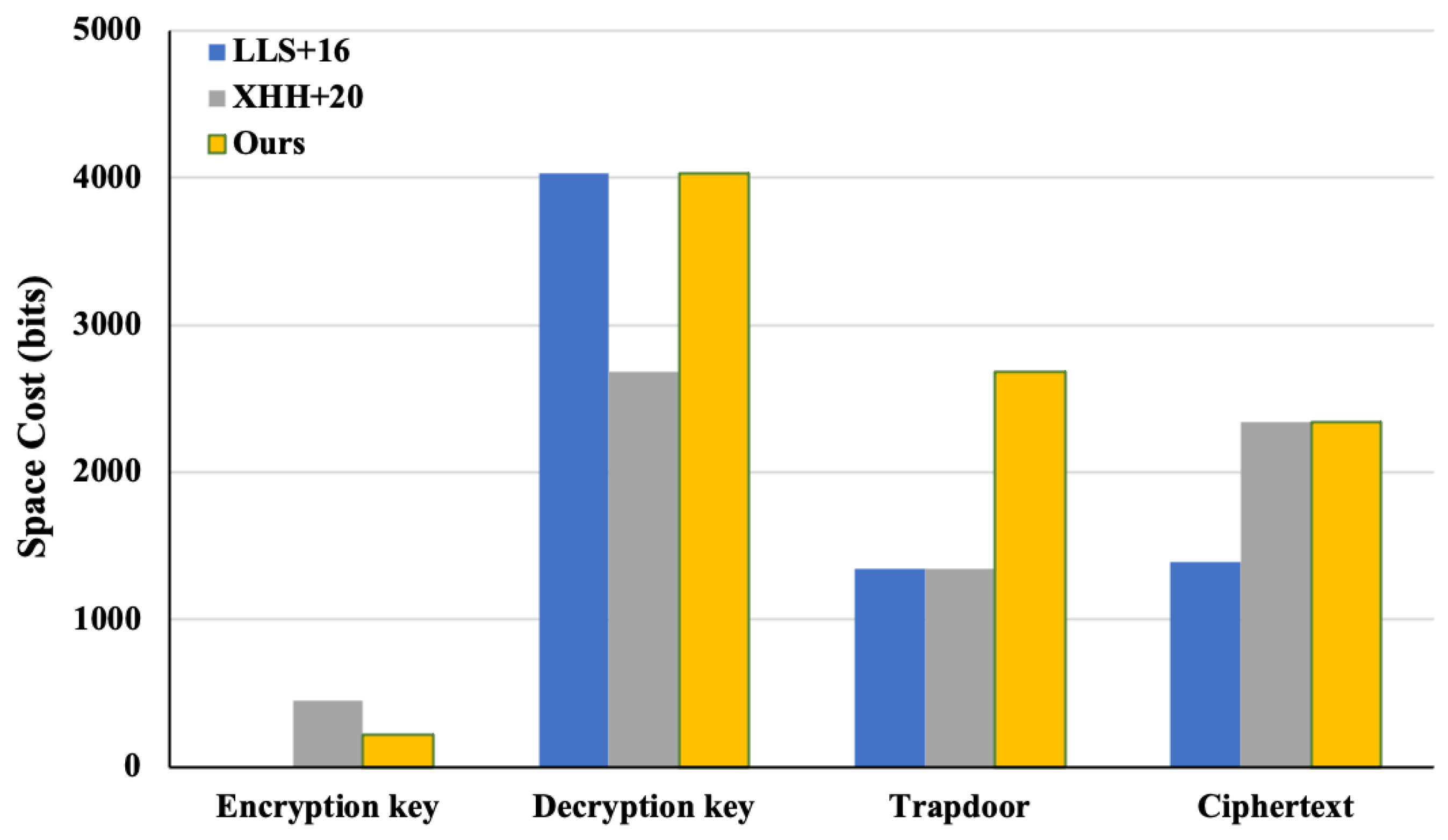
6. Performance Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Proceedings of the Advances in Cryptology—EUROCRYPT 2004, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar]
- Yang, G.; Tan, C.H.; Huang, Q.; Wong, D.S. Probabilistic public key encryption with equality test. In Proceedings of the Topics in Cryptology—CT-RSA 2010, San Francisco, CA, USA, 1–5 March 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 119–131. [Google Scholar]
- Ma, S. Identity-based encryption with outsourced equality test in cloud computing. Inf. Sci. 2015, 328, 389–402. [Google Scholar] [CrossRef]
- Lu, J.; Li, H.; Huang, J.; Ma, S.; Au, M.H.A.; Huang, Q. An Identity-Based Encryption with Equality Test scheme for healthcare social apps. Comput. Stand. Interfaces 2023, 87, 103759. [Google Scholar] [CrossRef]
- My HealtheVet. Available online: http://www.myhealth.va.gov (accessed on 22 December 2023).
- Vaanchig, N.; Qin, Z.; Ragchaasuren, B. Constructing secure-channel free identity-based encryption with equality test for vehicle-data sharing in cloud computing. Trans. Emerg. Telecommun. Technol. 2022, 33, e3896. [Google Scholar] [CrossRef]
- Xiong, H.; Hou, Y.; Huang, X.; Zhao, Y. Secure message classification services through identity-based signcryption with equality test towards the Internet of vehicles. Veh. Commun. 2020, 26, 100264. [Google Scholar] [CrossRef]
- Ohtaki, Y. Constructing a Searchable Encrypted Log Using Encrypted Inverted Indexes. In Proceedings of the 2005 International Conference on Cyberworlds, CW 2005, Singapore, 23–25 November 2005; pp. 130–138. [Google Scholar]
- Boneh, D.; Kushilevitz, E.; Ostrovsky, R.; Skeith, W.E. Public key encryption that allows PIR queries. In Proceedings of the Advances in Cryptology—CRYPTO 2007, Santa Barbara, CA, USA, 19–23 August 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 50–67. [Google Scholar]
- Camenisch, J.; Kohlweiss, M.; Rial, A.; Sheedy, C. Blind and anonymous identity-based encryption and authorised private searches on public key encrypted data. In Proceedings of the Public Key Cryptography—PKC 2009, Irvine, CA, USA, 18–20 March 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 196–214. [Google Scholar]
- Curtmola, R.; Garay, J.A.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. In Proceedings of the ACM Conference on Computer and Communications Security, CCS 2006, Alexandria, VA, USA, 30 October–3 November 2006; pp. 79–88. [Google Scholar]
- Cash, D.; Jarecki, S.; Jutla, C.S.; Krawczyk, H.; Rosu, M.; Steiner, M. Highly-scalable searchable symmetric encryption with support for Boolean queries. In Proceedings of the Advances in Cryptology—CRYPTO 2013, Santa Barbara, CA, USA, 18–22 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 353–373. [Google Scholar]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef]
- Ma, S.; Huang, Q.; Zhang, M.; Yang, B. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensic Secur. 2014, 10, 458–470. [Google Scholar] [CrossRef]
- Lee, H.T.; Ling, S.; Seo, J.H.; Wang, H. Semi-generic construction of public key encryption and identity-based encryption with equality test. Inf. Sci. 2016, 373, 419–440. [Google Scholar] [CrossRef]
- Lin, X.J.; Sun, L.; Qu, H. Generic construction of public key encryption, identity-based encryption and signcryption with equality test. Inf. Sci. 2018, 453, 111–126. [Google Scholar] [CrossRef]
- Li, N. Efficient equality test on identity-based ciphertexts supporting flexible authorization. Entropy 2023, 25, 362. [Google Scholar] [CrossRef] [PubMed]
- Boyen, X. Multipurpose Identity-Based Signcryption. In Proceedings of the Advances in Cryptology—CRYPTO 2003, Santa Barbara, CA, USA, 17–21 August 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 383–399. [Google Scholar]
- Xiong, H.; Zhao, Y.; Hou, Y.; Huang, X.; Jin, C.; Wang, L.; Kumari, S. Heterogeneous Signcryption With Equality Test for IIoT Environment. IEEE Internet Things J. 2021, 8, 16142–16152. [Google Scholar] [CrossRef]
- Xiong, H.; Hou, Y.; Huang, X.; Zhao, Y.; Chen, C.M. Heterogeneous Signcryption Scheme from IBC to PKI with Equality Test for WBANs. IEEE Syst. J. 2022, 16, 2391–2400. [Google Scholar] [CrossRef]
- Hou, Y.; Huang, X.; Chen, Y.; Kumar, S.; Xiong, H. Heterogeneous signcryption scheme supporting equality test from PKI to CLC toward IoT. Trans. Emerg. Telecommun. Technol. 2021, 32, e4190. [Google Scholar] [CrossRef]
- Ateniese, G.; Francati, D.; Nuñez, D.; Venturi, D. Match Me if You Can: Matchmaking Encryption and Its Applications. In Proceedings of the Advances in Cryptology—CRYPTO 2019, Santa Barbara, CA, USA, 18–22 August 2019; Springer: Cham, Switzerland, 2019; pp. 701–731. [Google Scholar]
- Xu, S.; Ning, J.; Li, Y.; Zhang, Y.; Xu, G.; Huang, X.; Deng, R.H. Match in my way: Fine-grained bilateral access control for secure cloud-fog computing. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1064–1077. [Google Scholar] [CrossRef]
- Sun, J.; Yuan, Y.; Tang, M.; Cheng, X.; Nie, X.; Aftab, M.U. Privacy-preserving bilateral fine-grained access control for cloud-enabled industrial IOT healthcare. IEEE Trans. Ind. Inform. 2021, 18, 6483–6493. [Google Scholar] [CrossRef]
- Chen, J.; Li, Y.; Wen, J.; Weng, J. Identity-Based Matchmaking Encryption from Standard Assumptions. In Proceedings of the Advances in Cryptology—ASIACRYPT 2022, Taipei, Taiwan, 5–9 December 2022; Springer: Cham, Switzerland, 2022; pp. 394–422. [Google Scholar]
- Wu, A.; Luo, W.; Weng, J.; Yang, A.; Wen, J. Fuzzy Identity-Based Matchmaking Encryption and Its Application. IEEE Trans. Inf. Forensic Secur. 2023, 18, 5592–5607. [Google Scholar] [CrossRef]
- Yan, Z.; Qu, H.; Zhang, X.; Xu, J.L.; Lin, X.J. Identity-based proxy matchmaking encryption for cloud-based anonymous messaging systems. J. Syst. Archit. 2023, 142, 102950. [Google Scholar] [CrossRef]
- Sun, J.; Xu, G.; Zhang, T.; Yang, X.; Alazab, M.; Deng, R.H. Privacy-Aware and Security-Enhanced Efficient Matchmaking Encryption. IEEE Trans. Inf. Forensic Secur. 2023, 18, 4345–4360. [Google Scholar] [CrossRef]
- Boyen, X. A tapestry of identity-based encryption: Practical frameworks compared. Int. J. Appl. Cryptogr. 2008, 1, 3–21. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Random oracles are practical: A paradigm for designing efficient protocols. In Proceedings of the ACM Conference on Computer and Communications Security, CCS 1993, Fairfax, VA, USA, 3–5 November 1993; ACM: New York, NY, USA, 1993; pp. 62–73. [Google Scholar]
- Tibouchi, M. Encyclopedia of Cryptography and Security; Springer: Boston, MA, USA, 2011. [Google Scholar]
- Franklin, J. Proof in Mathematics: An Introduction; Quakers Hill Press: Sydney, Australia, 1996. [Google Scholar]
- Choon, J.C.; Hee Cheon, J. An identity-based signature from gap Diffie-Hellman groups. In Proceedings of the 6th International Workshop on Practice and Theory in Public Key Cryptography, PKC 2002, Miami, FL, USA, 6–8 January 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 18–30. [Google Scholar]

| Equality Test | Confidentiality | Authenticity | Anonymity | ||
|---|---|---|---|---|---|
| Sender | Receiver | ||||
| [22] | ✗ | CPA | ✓ | ✓ | ✓ |
| [3] | ✓ | CPA | ✗ | ✗ | ✗ |
| [15] | ✓ | CCA | ✗ | ✗ | ✗ |
| [7] | ✓ | CCA | ✓ | ✗ | ✗ |
| Ours | ✓ | CCA | ✓ | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yan, Z.; Lin, X.; Zhang, X.; Xu, J.; Qu, H. Identity-Based Matchmaking Encryption with Equality Test. Entropy 2024, 26, 74. https://doi.org/10.3390/e26010074
Yan Z, Lin X, Zhang X, Xu J, Qu H. Identity-Based Matchmaking Encryption with Equality Test. Entropy. 2024; 26(1):74. https://doi.org/10.3390/e26010074
Chicago/Turabian StyleYan, Zhen, Xijun Lin, Xiaoshuai Zhang, Jianliang Xu, and Haipeng Qu. 2024. "Identity-Based Matchmaking Encryption with Equality Test" Entropy 26, no. 1: 74. https://doi.org/10.3390/e26010074