Quantum Key Distribution in the Presence of the Intercept-Resend with Faked States Attack
Abstract
:1. Introduction
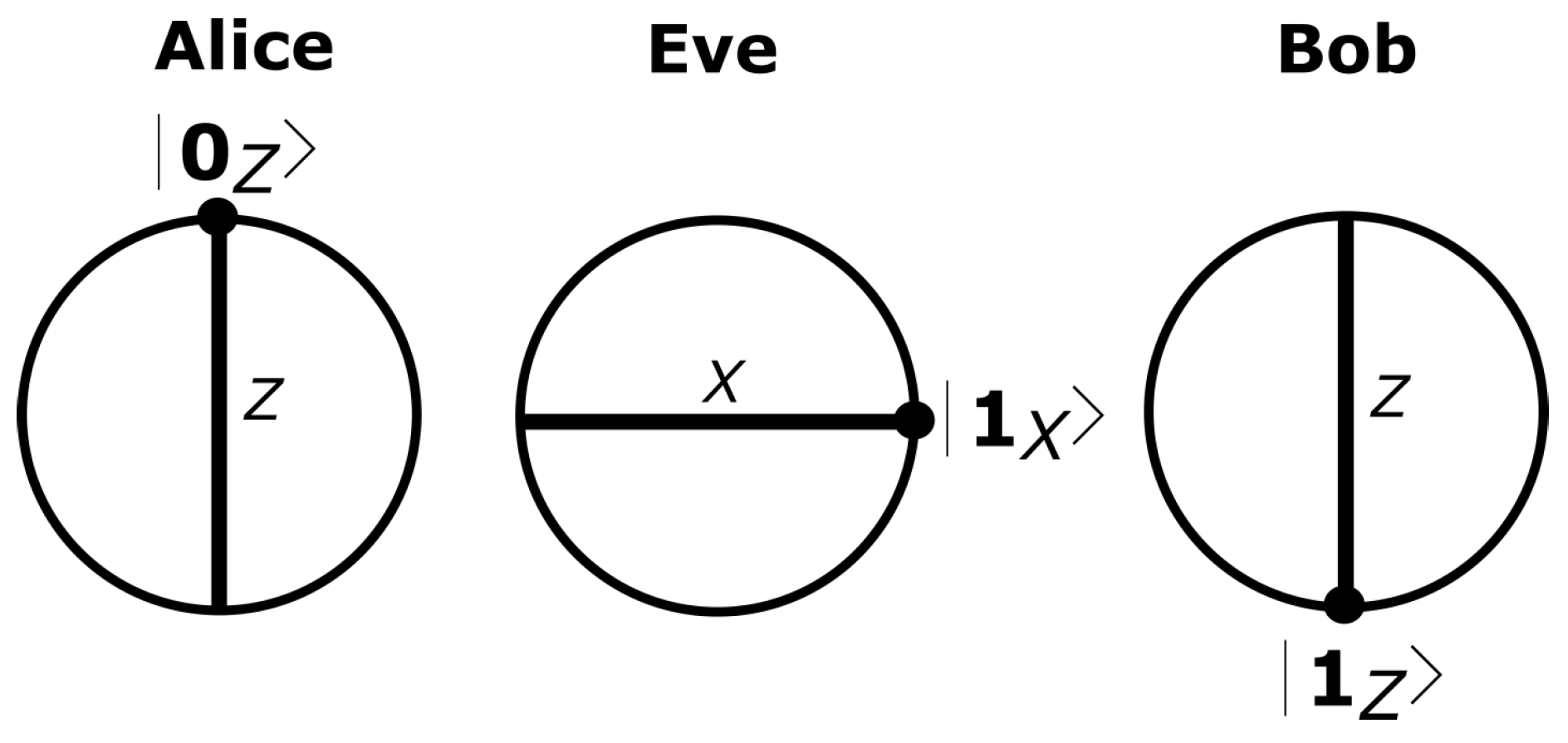
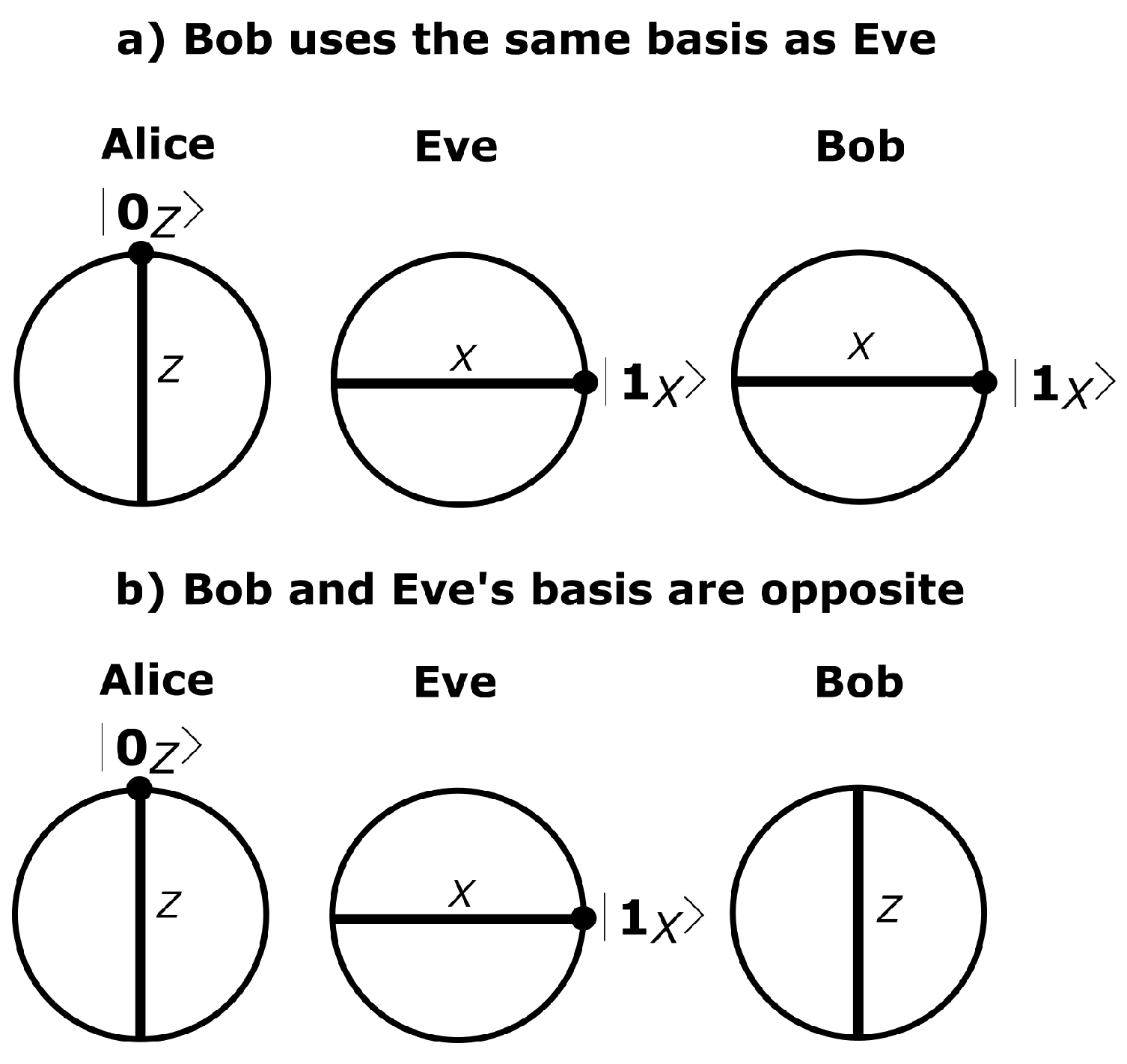
2. Quantum Hacking in QKD Systems
- (i)
- For Bob’s basis choice matching Eve’s, the detector clicks deterministically;
- (ii)
- For Bob’s basis choice not matching Eve’s, the faked state is not detected.
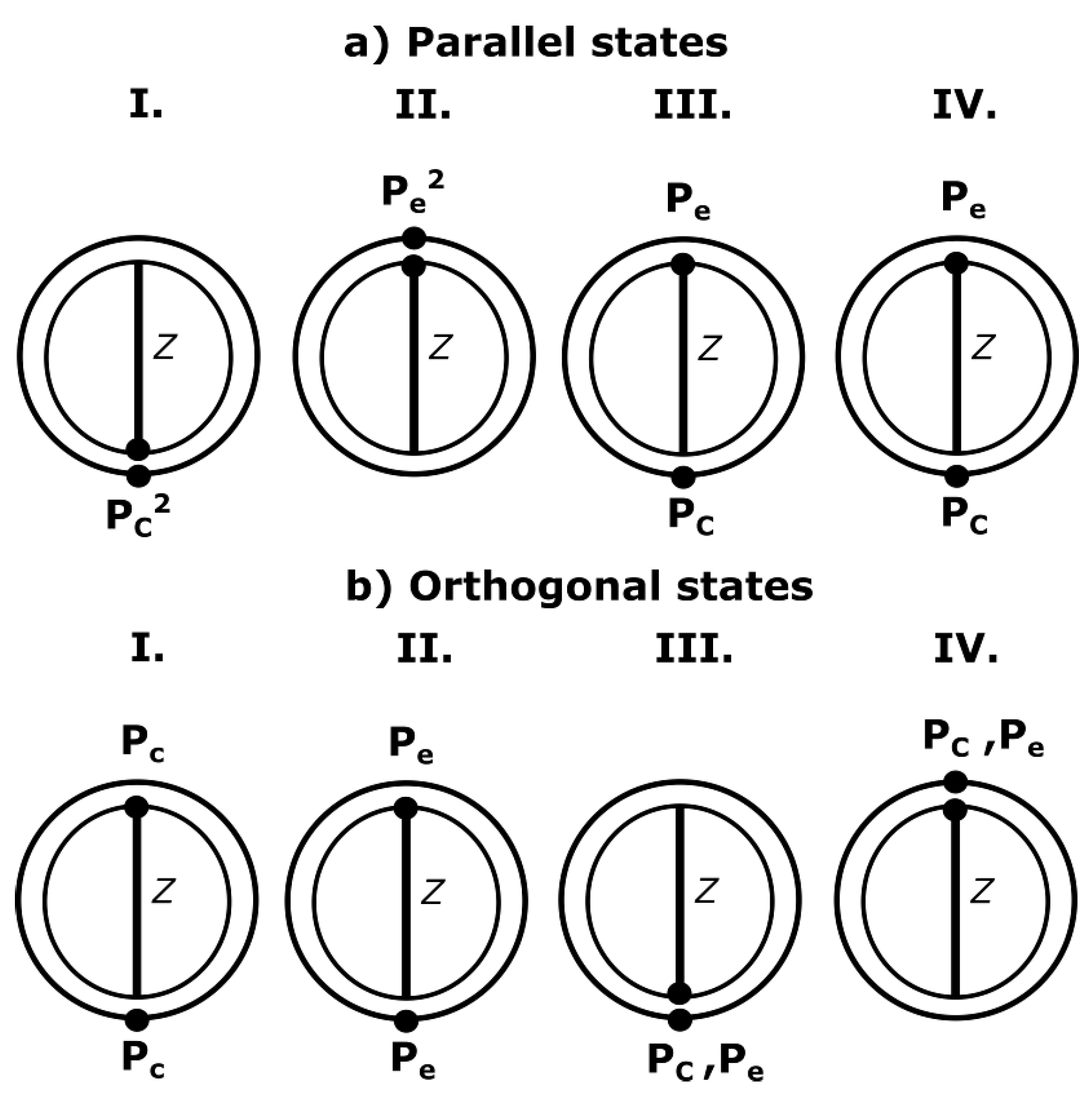
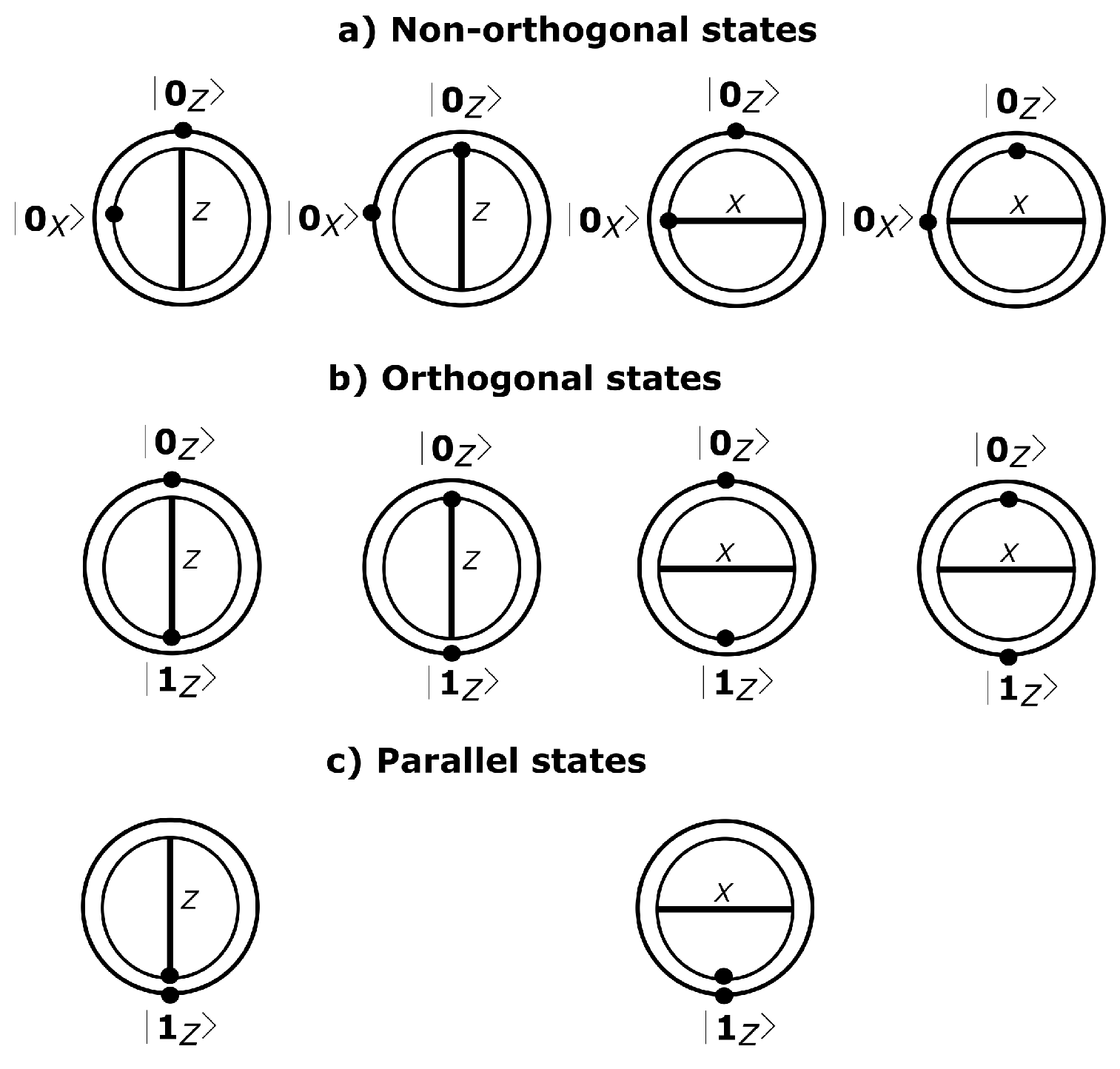
3. The Nack State Protocol
- Alice is equipped with a photon source with an expected photon number μ that exhibits a Poisson distribution. Alice randomly chooses between a parallel or an orthogonal biqubit, and she prepares the biqubit to send it to Bob through the quantum channel;
- Bob measures the biqubit (two incoming pulses) using the same measurement basis X (or Z) that he chooses randomly (in Section 4.2, we discuss that the consecutiveness of states can be avoided if Alice sends a burst of the first states of each pair, followed by a burst of the second states of each pair);
- Bob announces publicly his measurement basis choices;
- To share secret bits, Alice and Bob perform sifting using single compatible events and double compatible matching detection events (from parallel states). Similarly, they apply sifting to the double detection events that contain a single compatible detection event. For this purpose, Bob indicates if the single detection is the first or the second inside the biqubit;
- Finally, they use an error correction algorithm and a privacy amplification method usually used in -based protocols.
4. Detecting the IRFS Attack
4.1. The Attack with Blinding Pulses and Quantum Channel Substitution
- The eavesdropper can adjust the transmittance of the channel to a unique value, either to adjust the single or the double detection gain.
- Alice’s optical pulses arrive at Eve’s station sequentially. Thus, once the eavesdropper station has detected a pulse, she cannot know whether the next pulse will be also detected or lost. That is, Eve does not know when a single or a double detection event will occur.
4.2. The Non-Structured Protocol
4.3. Faking Double Detection Events
5. Discussion
5.1. and the Protocol
5.2. Measurement Device-Independent
- The protocol uses the same optical equipment as the . It does not use any other extra hardware;
- The protocol or its dual protocol, the , could be used to detect other attacks, such as the Photon Number Splitting attack () [19].
6. Conclusions
Author Contributions
Conflicts of Interest
Appendix A. The Gain of Detection Events
| - | |||
| - | |||
- The fiber channel transmittance between Alice and Bob is written as where α is the loss coefficient measured in dB/km, and the length l is measured in km. Furthermore, the local transmittance at Bob’s side is written as where is the internal transmittance of optical components and is the quantum efficiency of Bob’s detectors. Then, the overall transmission and detection efficiency at Bob’s side is computed as and typically ranges [15];
- The transmittance of i photons’ state at Bob’s, that is for , assuming independence between the i photons of the i photons’ state;
- The yield of the i photons’ state is obtained from two sources, the background noise () and the true signal. Assuming that the background counts are independent from the signal photon detection, is given by . However, assuming small (around ) and , the above equation can be reduced to .
Appendix B. The IRFS Attack and Quantum Channel Substitution
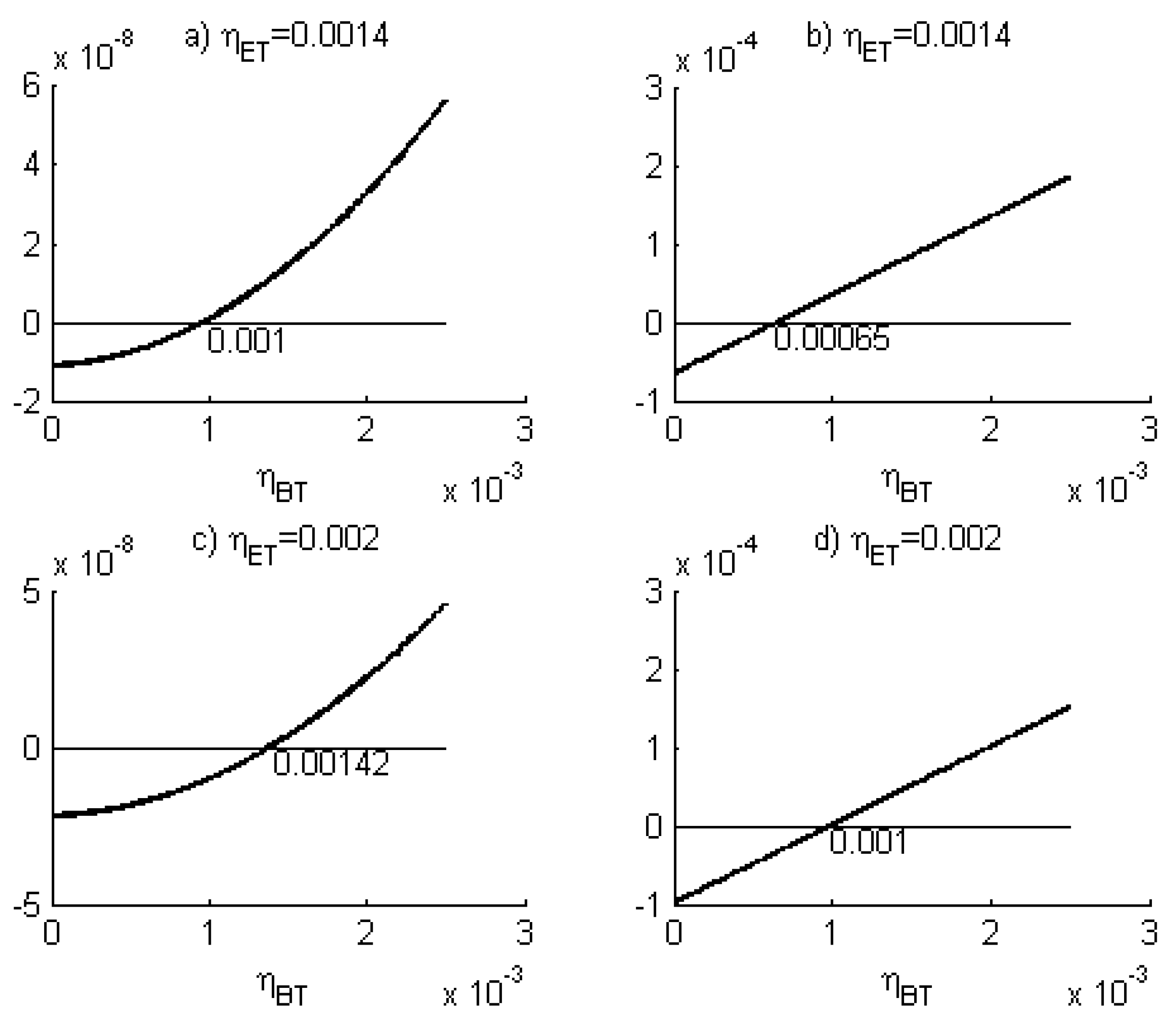
Appendix B.1. The Photon and the Vacuum Ratios
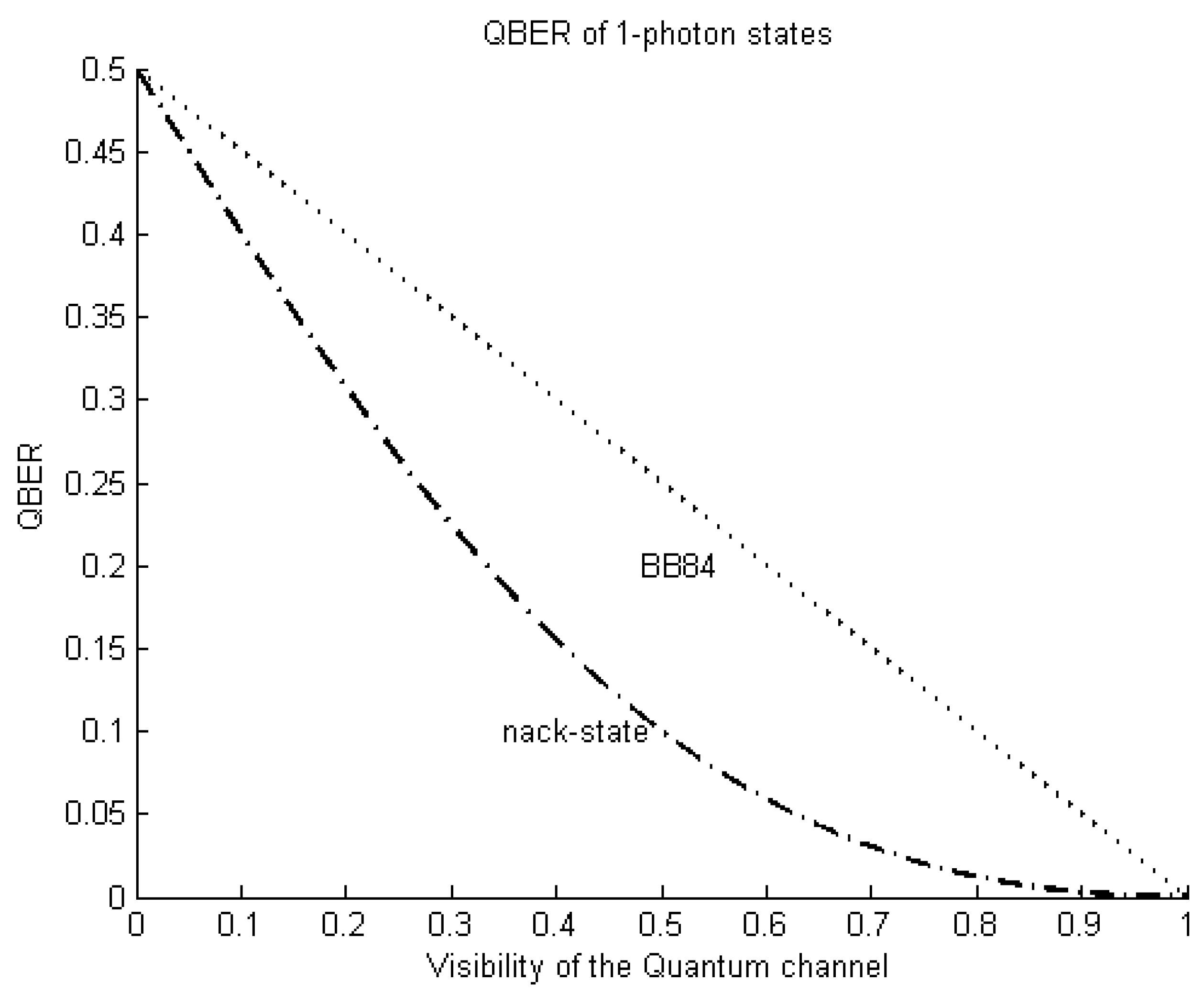
Appendix C. The QBER of One-Photon States
References
- Bennett, C.H. Quantum cryptography: Public key distribution and coin tossing. In Proceddings of the 1984 International Conference on Computer System and Signal Processing, Bangalore, India, 10–19 December 1984.
- Van Assche, G. Quantum Cryptography and Secret-Key Distillation; Cambridge University Press: Cambridge, UK, 2006. [Google Scholar]
- Hughes, R.; Nordholt, J.; Rarity, J. Summary of Implementation Schemes for Quantum Key Distribution and Quantum Cryptography—A Quantum Information Science and Technology Roadmap. Available online: http://qist.lanl.gov/pdfs/6.5-continuous.pdf (accessed on 19 December 2016).
- Bennett, C.H.; Bessette, F.; Brassard, G.; Salvail, L.; Smolin, J. Experimental quantum cryptography. J. Cryptol. 1992, 5, 3–28. [Google Scholar] [CrossRef]
- Fung, C.F.; Qi, B.; Tamaki, K.; Lo, H. Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A 2007, 75, 032314. [Google Scholar] [CrossRef]
- Xu, F.; Qi, B.; Lo, H. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 2010, 12, 113026. [Google Scholar] [CrossRef]
- Makarov, V.; Hjelme, D.R. Faked states attack on quantum cryptosystems. J. Mod. Opt. 2005, 52, 691–705. [Google Scholar] [CrossRef]
- Makarov, V.; Anisimov, A.; Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 2006, 74, 022313. [Google Scholar] [CrossRef]
- Makarov, V.; Skaar, J. Faked states attack using detector efficiency mismatch on SARG04, phase-time, DPSK, and Ekert protocols. Quantum Inf. Comput. 2008, 8, 622–635. [Google Scholar]
- Qi, B.; Fung, C.F.; Lo, H.; Ma, X. Time-shift attack in practical quantum cryptosystems. arXiv, 2005; arXiv:quant-ph/0512080. [Google Scholar]
- Lydersen, L.; Wiechers, C.; Wittmann, C.; Elser, D.; Skaar, J.; Makarov, V. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 2010, 4, 686–689. [Google Scholar] [CrossRef]
- Gerhardt, I.; Liu, Q.; Lamas-Linares, A.; Skaar, J.; Kurtsiefer, C.; Makarov, V. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2011, 2, 349. [Google Scholar] [CrossRef] [PubMed]
- Wiechers, C.; Lydersen, L.; Wittmann, C.; Elser, D.; Skaar, J.; Marquardt, C.; Makarov, V.; Leuchs, G. After-gate attack on a quantum cryptosystem. New J. Phys. 2011, 13, 013043. [Google Scholar] [CrossRef]
- Weier, H.; Krauss, H.; Rau, M.; Fuerst, M.; Nauerth, S.; Weinfurter, H. Quantum eavesdropping without interception: An attack exploiting the dead time of single-photon detectors. New J. Phys. 2011, 13, 073024. [Google Scholar] [CrossRef]
- Ma, X.; Qi, B.; Zhao, Y.; Lo, H. Practical decoy state for quantum key distribution. Phys. Rev. A 2005, 72, 012326. [Google Scholar] [CrossRef]
- Hughes, R.; Nordholt, J. Refining quantum cryptography. Science 2011, 333, 1584–1586. [Google Scholar] [CrossRef] [PubMed]
- Lo, H.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [PubMed]
- Lizama, L.; López, J.M.; De Carlos, E.; Venegas-Andraca, S.E. Enhancing quantum key distribution (QKD) to address quantum hacking. Procedia Technol. 2012, 3, 80–88. [Google Scholar] [CrossRef]
- Lizama-Pérez, L.A.; López, J.M.; De Carlos-López, E.; Venegas-Andraca, S.E. Quantum Flows for Secret Key Distribution in the Presence of the Photon Number Splitting Attack. Entropy 2014, 16, 3121–3135. [Google Scholar] [CrossRef]
- Sun, S.; Jiang, M.; Ma, X.; Li, C.; Liang, L. Hacking on decoy-state quantum key distribution system with partial phase randomization. Sci. Rep. 2014, 4, 013043. [Google Scholar] [CrossRef] [PubMed]
- Song, T.; Qin, S.; Wen, Q.; Wang, Y.; Jia, H. Finite-key security analyses on passive decoy-state QKD protocols with different unstable sources. Sci. Rep. 2015, 5, 735–753. [Google Scholar] [CrossRef] [PubMed]
- Collins, D.; Gisin, N.; De Riedmatten, H. Quantum relays for long distance quantum cryptography. J. Mod. Opt. 2005, 52, 735–753. [Google Scholar] [CrossRef]
- Lo, H.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef] [PubMed]
- Rubenok, A.; Slater, J.A.; Chan, P.; Lucio-Martinez, I.; Tittel, W. A quantum key distribution system immune to detector attacks. arXiv, 2012; arXiv:1204.0738. [Google Scholar]
- Xu, F.; Curty, M.; Qi, B.; Lo, H.-K. Measurement-device-independent quantum cryptography. IEEE J. Sel. Top. Quantum Electron. 2015, 21, 148–158. [Google Scholar]
- Lim, C.C.W.; Walenta, N.; Legré, M.; Gisin, N.; Zbinden, H. Random variation of detector efficiency: A countermeasure against detector blinding attacks for quantum key distribution. IEEE J. Sel. Top. Quantum Electron. 2015, 21, 192–196. [Google Scholar] [CrossRef]
- Honjo, T.; Fujiwara, M.; Shimizu, K.; Tamaki, K.; Miki, S.; Yamashita, T.; Terai, H.; Wang, Z.; Sasaki, M. Countermeasure against tailored bright illumination attack for DPS-QKD. Opt. Express 2013, 21, 2667–2673. [Google Scholar] [CrossRef] [PubMed]
- Jain, N.; Stiller, B.; Khan, I.; Elser, D.; Marquardt, C.; Leuchs, G. Attacks on practical quantum key distribution systems (and how to prevent them). Contemp. Phys. 2016, 57, 366–387. [Google Scholar] [CrossRef]
- Jeong, Y.; Kim, Y.-S.; Kim, Y.-H. Effects of depolarizing quantum channels on BB84 and SARG04 quantum cryptography protocols. Laser Phys. 2011, 21, 1438–1442. [Google Scholar] [CrossRef]

| Alice’s Biqubit | Bob’s Basis | Detection Event | Public Disclosure | Description |
|---|---|---|---|---|
| X | X, () | compatible double non-matching, useful as two compatible single detection events | ||
| X | X, () | compatible single matching, useful | ||
| X | X, () | compatible single matching, useful | ||
| X | X, Lost | biqubit lost | ||
| Z | Z, () | non-compatible double matching, useless | ||
| Z | Z, () | non-compatible double matching, useless | ||
| Z | Z, () | non-compatible double non-matching, useless | ||
| Z | Z, () | non-compatible double non-matching, useless | ||
| Z | Z, () | non-compatible single matching, useless | ||
| Z | Z, () | non-compatible single matching, useless | ||
| Z | Z, () | non-compatible single matching, useless | ||
| Z | Z, () | non-compatible single matching, useless | ||
| Z | Z, Lost | biqubit lost | ||
| Z | Z, () | compatible double matching, useful | ||
| Z | Z, () | compatible single matching, useful | ||
| Z | Z, () | compatible single matching, useful | ||
| Z | Z, Lost | biqubit lost | ||
| X | X, () | non-compatible double matching, useless | ||
| X | X, () | non-compatible double matching, useless | ||
| X | X, () | non-compatible double non-matching, useless | ||
| X | X, () | non-compatible double non-matching, useless | ||
| X | X, () | non-compatible single matching, useless | ||
| X | X, () | non-compatible single matching, useless | ||
| X | X, () | non-compatible single matching, useless | ||
| X | X, () | non-compatible single matching, useless | ||
| X | X, Lost | biqubit lost |
| Alice’s Biqubit | Eve’s Basis | Eve’s Detection | Forwarded Dates | Eve’s Result |
|---|---|---|---|---|
| Z | hidden | |||
| detected | ||||
| X | hidden | |||
| hidden | ||||
| hidden | ||||
| hidden | ||||
| Z | detected | |||
| hidden | ||||
| X | hidden | |||
| hidden | ||||
| hidden | ||||
| hidden |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lizama-Pérez, L.A.; López, J.M.; De Carlos López, E. Quantum Key Distribution in the Presence of the Intercept-Resend with Faked States Attack. Entropy 2017, 19, 4. https://doi.org/10.3390/e19010004
Lizama-Pérez LA, López JM, De Carlos López E. Quantum Key Distribution in the Presence of the Intercept-Resend with Faked States Attack. Entropy. 2017; 19(1):4. https://doi.org/10.3390/e19010004
Chicago/Turabian StyleLizama-Pérez, Luis Adrian, José Mauricio López, and Eduardo De Carlos López. 2017. "Quantum Key Distribution in the Presence of the Intercept-Resend with Faked States Attack" Entropy 19, no. 1: 4. https://doi.org/10.3390/e19010004







