Message Authentication over Noisy Channels
Abstract
:1. Introduction
Notation
2. System Overview
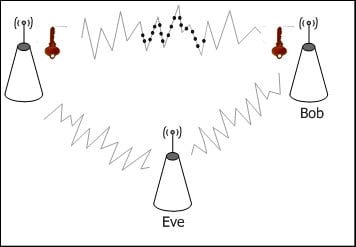
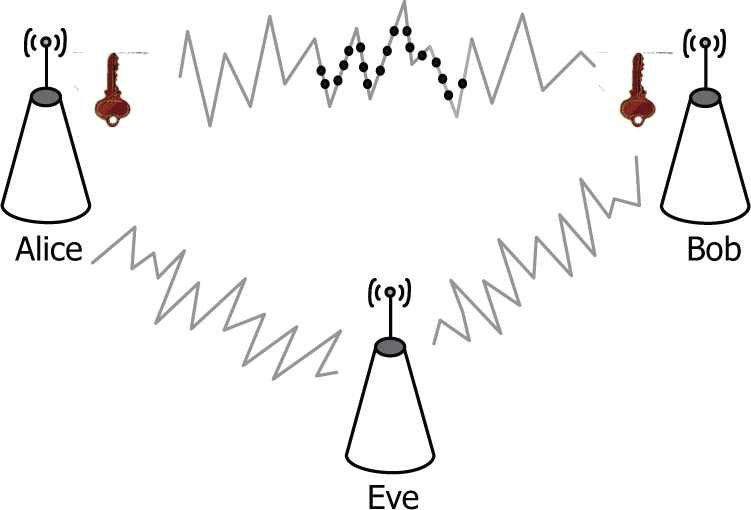
2.1. Scenario
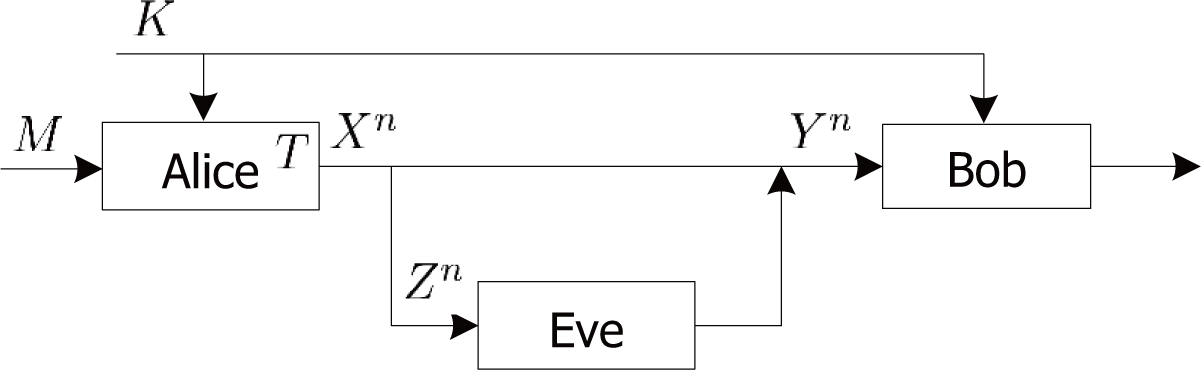
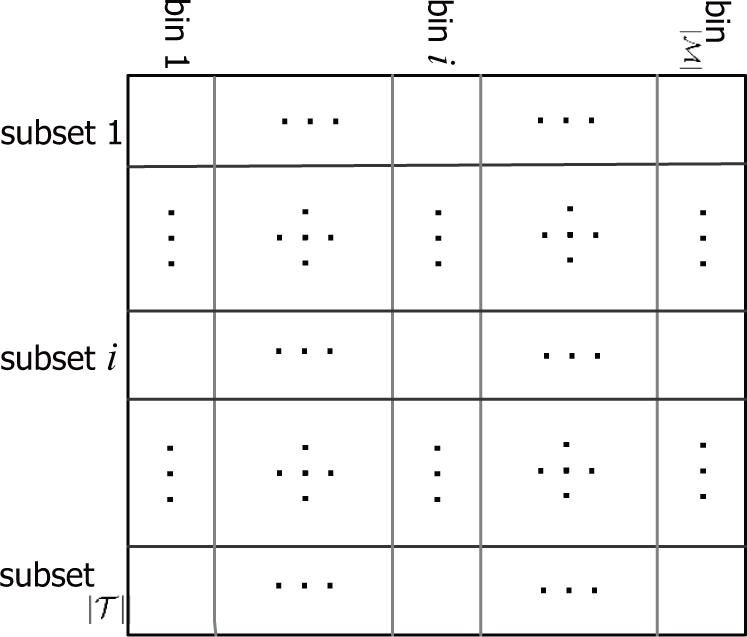
2.2. Proposed Authentication Scheme
2.3. Channel Model
3. Security Performance Analysis
4. Comparisons With Previous Works
- Our work can scale the optimal security performance exactly even if the codeword length n is limited. Specifically, this paper considers the intercepted observation Zn, directly derives the infimums on PS and PD and gives the sufficient and necessary conditions for tightness. Moreover, these results reveal the optimal design of the authentication scheme (i.e., Remark 3). However, the work in [9] only proves the reachability of the optimal security performance when the codeword length n goes to infinity. Thus, our work is more significant and practicable.
- The authentication model in [9] may incur the power-substitution attack, especially in linear code schemes (e.g., superposition coding is encapsulated in f(·) [10]). For example, as is depicted in Figure 3, a codeword could be modified into another one by a synchronously transmitted and well-designed malicious signal. However, in our scheme, since the authentication tag encapsulates the source message and the secret key (i.e., Equation (2)), the power-substitution attack can be effectively limited in the subsets of the source message, and with an additional trick it can be prevented. (Please refer to Appendix D for more technical details.) Instead of designing specific code schemes in f(·), our scheme introduced g(·) (i.e., Equation (2)) to defend against the power-substitution attack. Thus, our scheme can be applied in the existing wireless communication systems with minimal modifications.
- Our authentication model degrades to the one in [9] when T = g(M; K) = K. Thus, the authentication model in [9] can be seen as a special case of ours. This special case is not the optimal one and is not permitted in our scheme due to the reasons above. In addition, it is obvious that the scheme in [9] exposes the secret key when the wiretap channel’s secrecy capacity cannot be guaranteed to be nonzero according to its codebook. However, when the authentication tag leaks to Eve, our scheme degrades to the Simmons’ model [27]. Thus, we can adjust the construction of g(·) to adapt the time-varying channels.
5. Conclusions
Author Contributions
Conflicts of Interest
Appendix
A. Proof of Theorem 1
B. Proof of Theorem 2
C. Proof of Theorem 3
C.1. Proof of PD ≥ 2−H(K)
C.2. Proof of PD ≤ 2−H(K) αe−nβ
D. The Power-substitution Attack
Acknowledgments
References
- Yu, P.; Baras, J.; Sadler, B. An Implementation of Physical Layer Authentication Using Software Radio; Technical report, DTIC Document, ARL-TR-4888; U.S. Army Research Laboratory: Adelphi, MD, USA, July 2009. [Google Scholar]
- Yu, T.; Hartman, S.; Raeburn, K. The perils of unauthenticated encryption: Kerberos version 4, Proceedings of the 11th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 4–6 February 2004; Available online: http://www.internetsociety.org/doc/perils-unauthenticated-encryption-kerberos-version-4 accessed on 12 January 2015.
- Yu, P.L.; Baras, J.S.; Sadler, B.M. Physical-layer authentication. IEEE Trans. Inf. Forensics Secur. 2008, 3, 38–51. [Google Scholar]
- Wang, X.; Wu, Y.; Caron, B. Transmitter identification using embedded pseudo random sequences. IEEE Trans. Broadcast. 2004, 50, 244–252. [Google Scholar]
- Fei, C.; Kundur, D.; Kwong, R.H. Analysis and design of secure watermark-based authentication systems. IEEE Trans. Inf. Forensics Secur 2006, 1, 43–55. [Google Scholar]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-cryptographic authentication and identification in wireless networks. IEEE Trans. Wirel. Commun. 2010, 17, 56–62. [Google Scholar]
- Simmons, G. Authentication theory/coding theory. In Advances in Cryptology; Springer: Berlin, Germany, 1985; Volume 196, pp. 411–431. [Google Scholar]
- Wyner, A.D. The Wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar]
- Lai, L.; El Gamal, H.; Poor, H.V. Authentication over noisy channels. IEEE Trans. Inf. Theory. 2009, 55, 906–916. [Google Scholar]
- Bloch, M.; Barros, J. Physical-Layer Security; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Maurer, U.M. Generalized privacy amplification. IEEE Trans. Inf. Theory. 1995, 41, 1915–1923. [Google Scholar]
- Maurer, U.; Wolf, S. Information-theoretic key agreement: From weak to strong secrecy for free. In Advances in Cryptology—EUROCRYPT 2000; Preneel, B., Ed.; Springer: Berlin, Germany, 2000; pp. 351–368. [Google Scholar]
- Csiszár, I. Almost independence and secrecy capacity. Probl. Peredachi Inf. 1996, 32, 48–57. [Google Scholar]
- Barros, J.; Rodrigues, M.R.D. Secrecy capacity of wireless channels, Proceedings of 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006; 1, pp. 356–360.
- Bloch, M.; Barros, J.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar]
- Chrysikos, T.; Dagiuklas, T.; Kotsopoulos, S. Wireless information-theoretic security in an outdoor topology with obstacles: Theoretical analysis and experimental measurements. EURASIP J. Wirel. Commun. Netw. 628–747.
- Csiszár, I.; Korner, J. Broadcast channels with confidential messages. IEEE Trans. Inf. Theory. 1978, 24, 339–348. [Google Scholar]
- Ozel, O.; Ulukus, S. Wiretap channels: Roles of rate splitting and channel prefixing, Proceedings of 2011 IEEE International Symposium on Information Theory Proceedings, St. Petersburg, FL, USA, 31 July–5 August 2011; pp. 628–632.
- Ulukus, S. Information theoretic security, Presented at 2012 European School of Information Theory, Antalya, Turkey, April 2012.
- Thangaraj, A.; Dihidar, S.; Calderbank, A.R.; McLaughlin, S.W.; Merolla, J.M. Applications of LDPC codes to the wiretap channel. IEEE Trans. Inf. Theory 2007, 53, 2933–2945. [Google Scholar]
- Klinc, D.; Ha, J.; McLaughlin, S.W.; Barros, J.; Kwak, B.J. LDPC codes for the Gaussian wiretap channel. IEEE Trans. Inf. Forensics Secur 2011, 6, 532–540. [Google Scholar]
- Richardson, T.J.; Shokrollahi, M.A.; Urbanke, R.L. Design of capacity-approaching irregular low-density parity-check codes. IEEE Trans. Inf. Theory. 2001, 47, 619–637. [Google Scholar]
- Mahdavifar, H.; Vardy, A. Achieving the secrecy capacity of wiretap channels using polar codes. IEEE Trans. Inf. Theory 2011, 57, 6428–6443. [Google Scholar]
- Subramanian, A.; Thangaraj, A.; Bloch, M.; McLaughlin, S.W. Strong secrecy on the binary erasure wiretap channel using large-girth LDPC codes. IEEE Trans. Inf. Forensics Secur. 2011, 6, 585–594. [Google Scholar]
- Subramanian, A.; Suresh, A.T.; Raj, S.; Thangaraj, A.; Bloch, M.; McLaughlin, S. Strong and weak secrecy in wiretap channels, Proceedings of the 6th International Symposium on Turbo Codes and Iterative Information Processing, Brest, France, 6–10 September 2010; pp. 30–34.
- Zhou, X.Y.; Song, L.Y.; Zhang, Y. Physical Layer Security in wireless Communications; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar]
- Walker, M. Information-theoretic bounds for authentication schemes. J. Cryptol. 1990, 2, 131–143. [Google Scholar]
- Stinson, D.R. Cryptography: Theory and Practice, 3rd ed; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zheng, F.; Xiao, Z.; Zhou, S.; Wang, J.; Huang, L. Message Authentication over Noisy Channels. Entropy 2015, 17, 368-383. https://doi.org/10.3390/e17010368
Zheng F, Xiao Z, Zhou S, Wang J, Huang L. Message Authentication over Noisy Channels. Entropy. 2015; 17(1):368-383. https://doi.org/10.3390/e17010368
Chicago/Turabian StyleZheng, Fanfan, Zhiqing Xiao, Shidong Zhou, Jing Wang, and Lianfen Huang. 2015. "Message Authentication over Noisy Channels" Entropy 17, no. 1: 368-383. https://doi.org/10.3390/e17010368
APA StyleZheng, F., Xiao, Z., Zhou, S., Wang, J., & Huang, L. (2015). Message Authentication over Noisy Channels. Entropy, 17(1), 368-383. https://doi.org/10.3390/e17010368