Elimination of a Second-Law-Attack, and All Cable-Resistance-Based Attacks, in the Kirchhoff-Law-Johnson-Noise (KLJN) Secure Key Exchange System
Abstract
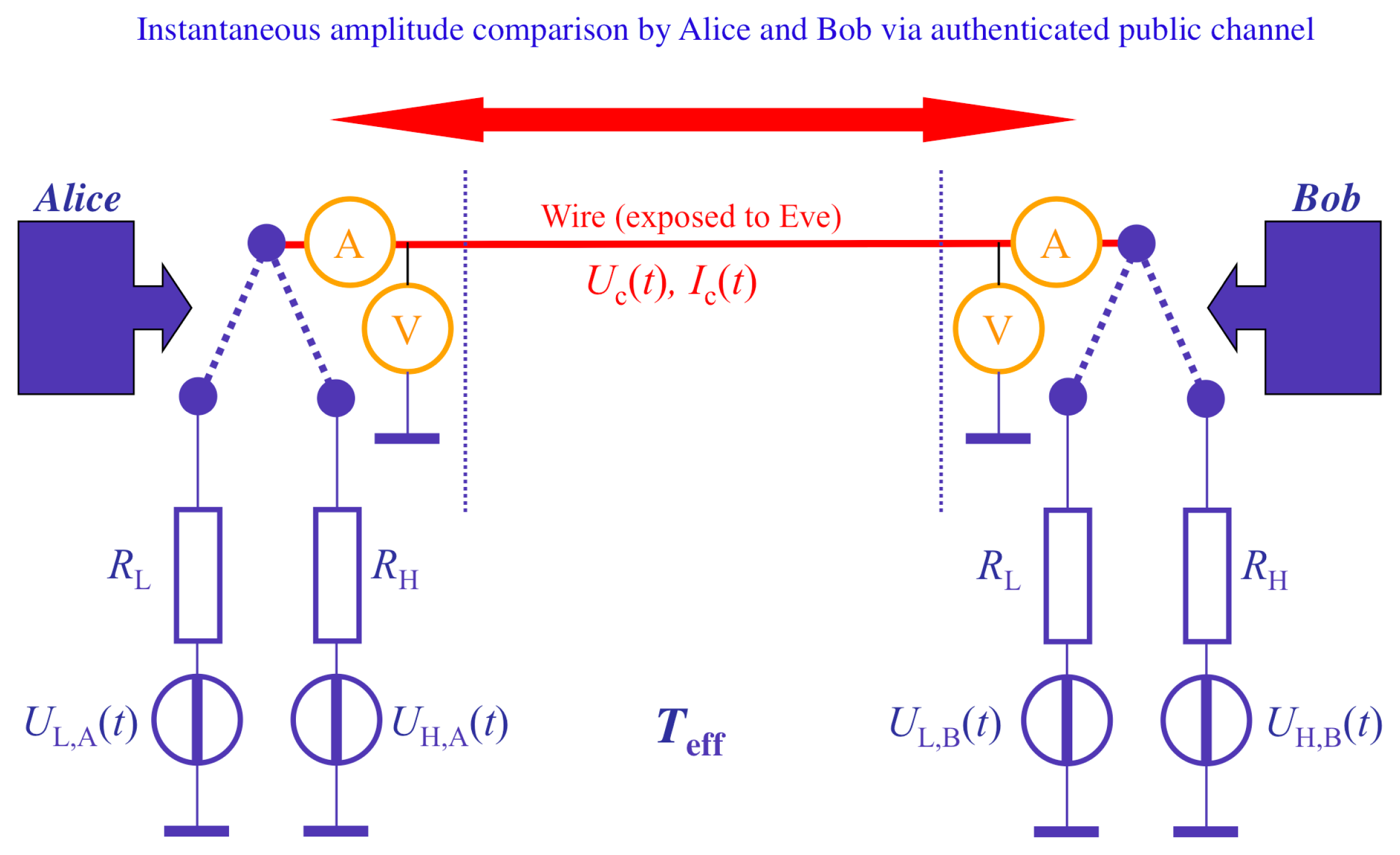
:1. Introduction
2. Results and Discussion
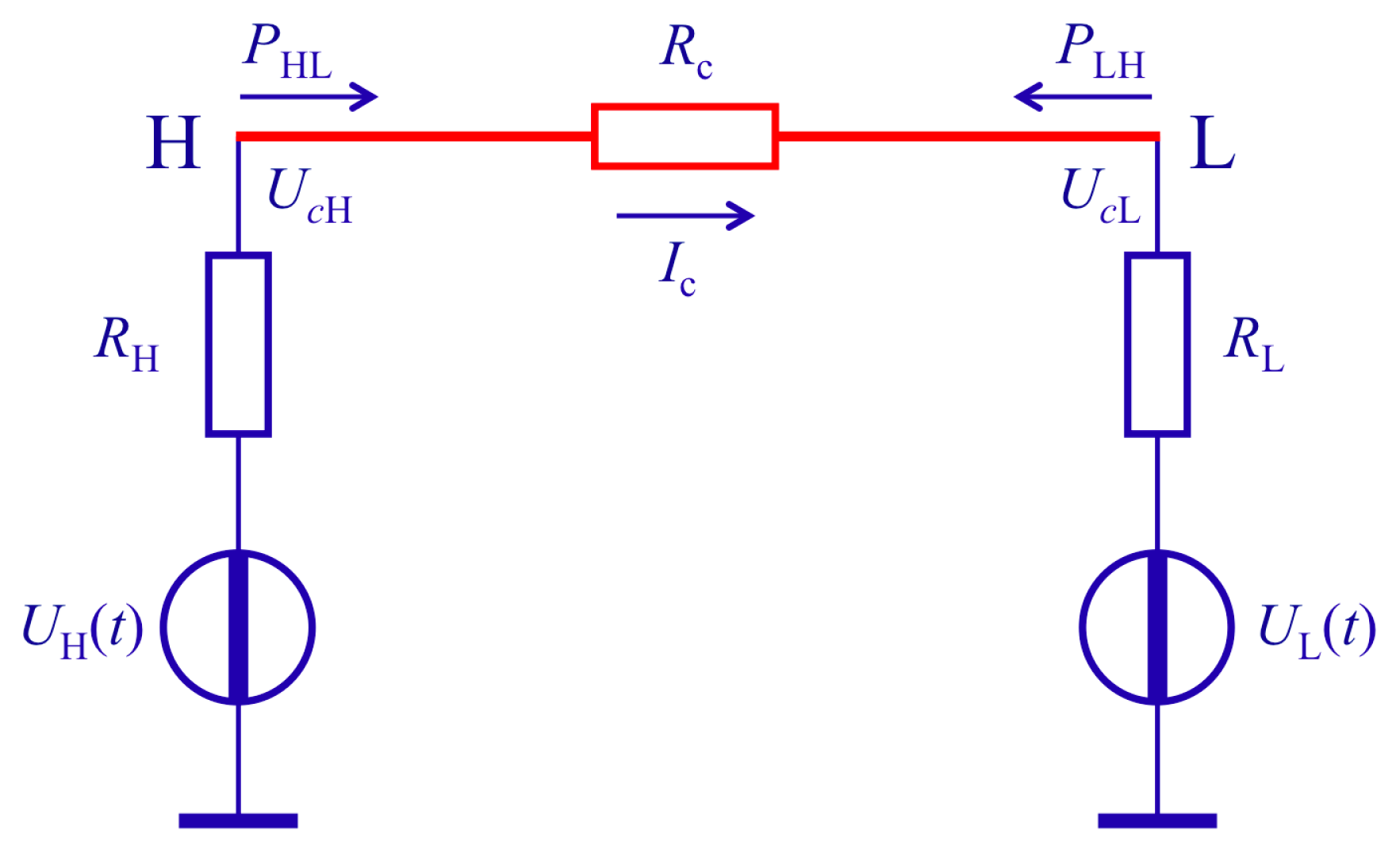
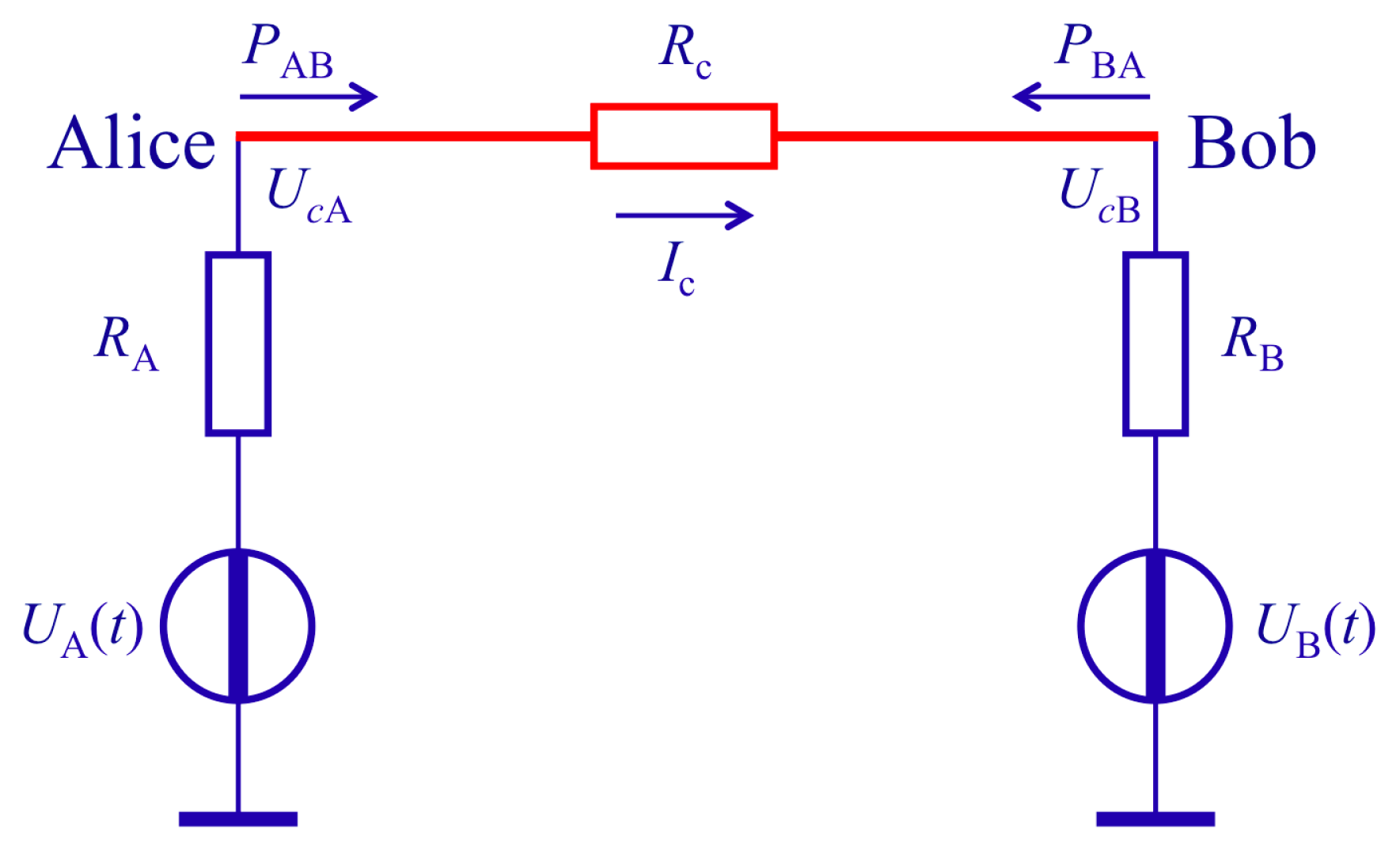
2.1. The Second-Law-Attack
- (i)
- if ΔPAB > 0, then Alice has RH and Bob has RL,
- (ii)
- if ΔPAB < 0, then Alice has RL and Bob has RH.
2.2. Natural/“Simple” Defense
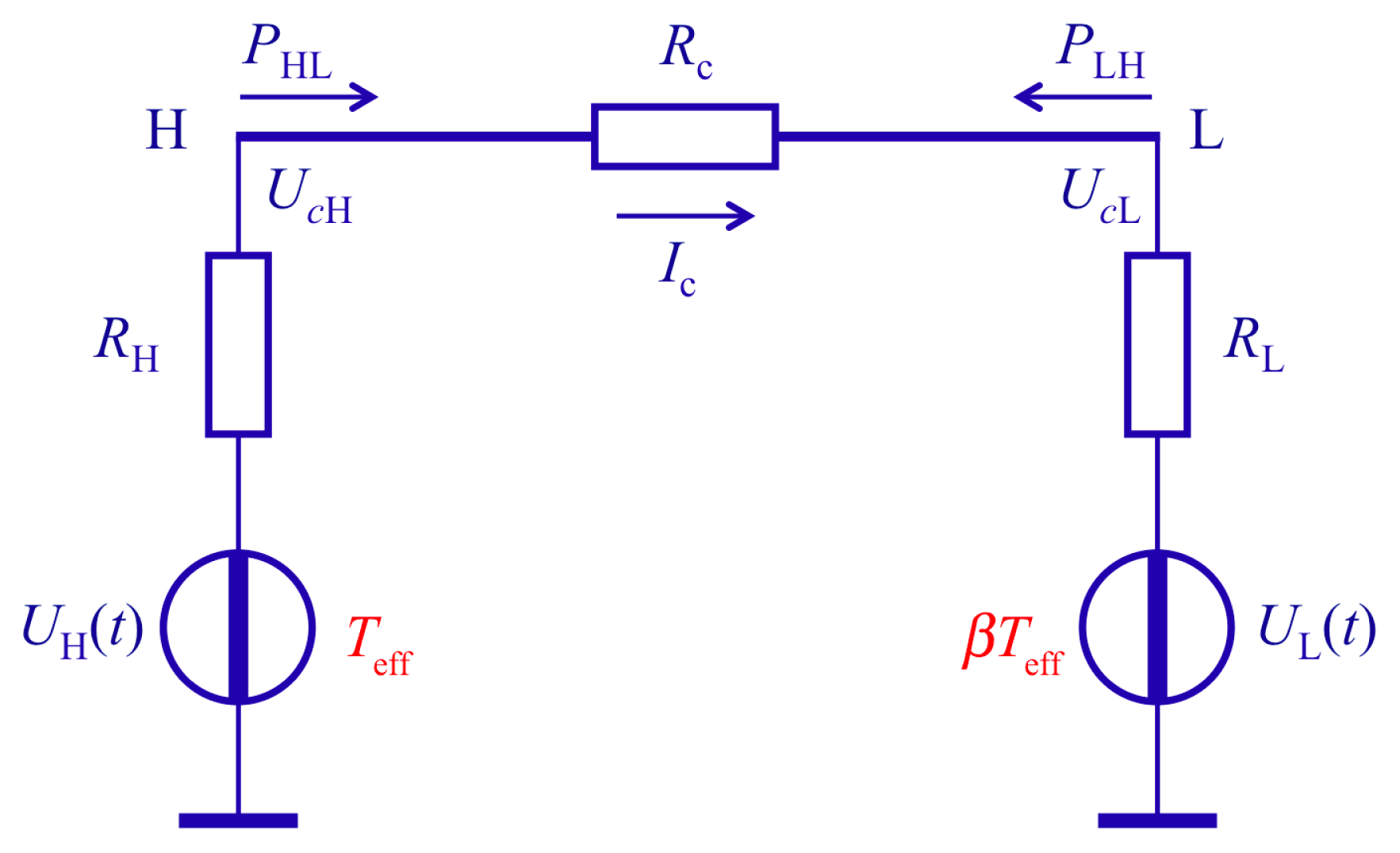
2.3. Advanced Defense, Also Eliminating All Cable Resistance Attacks
3. Conclusions
Author Contributions
Conflicts of Interest
References
- Kish, L.B. Totally secure classical communication utilizing Johnson (-like) noise and Kirchoff’s law. Phys. Lett. A 2006, 352, 178–182. [Google Scholar]
- Kish, L.B.; Granqvist, C.G. On the security of the Kirchhoff-law-Johnson-noise (KLJN) communicator. Quantum Inf. Process 2014, 13, 2213–2219. [Google Scholar]
- Mingesz, R.; Gingl, Z.; Kish, L.B. Johnson (-like)-Noise-Kirchhoff-loop based secure classical communicator characteristics, for ranges of two to two thousand kilometers, via model-line. Phys. Lett. A 2008, 372, 978–984. [Google Scholar]
- Gingl, Z.; Mingesz, R. Noise properties in the ideal Kirchhoff-law-Johnson-noise secure communication system. PLoS ONE 2014, 9. [Google Scholar] [CrossRef]
- Mingesz, R.; Vadai, G.; Gingl, Z. What kind of noise guarantees security for the Kirchhoff-Loop-Johnson-noise key exchange? Fluct. Noise Lett 2014, 13. [Google Scholar] [CrossRef]
- Cho, A. Simple noise may stymie spies without quantum weirdness. Science 2005, 309, 2148. [Google Scholar]
- Scheuer, J.; Yariv, A. A classical key-distribution system based on Johnson (like) noise—How secure? Phys. Lett. A 2006, 359, 737–740. [Google Scholar]
- Kish, L.B.; Scheuer, J. Noise in the wire: The real impact of wire resistance for the Johnson (-like) noise based secure communicator. Phys. Lett. A 2010, 374, 2140–2142. [Google Scholar]
- Kish, L.B. Enhanced secure key exchange systems based on the Johnson-Noise scheme. Metrol. Meas. Syst 2013, 20, 191–204. [Google Scholar]
- Kish, L.B.; Abbott, D.; Granqvist, C.G. Critical analysis of the Bennett–Riedel attack on secure cryptographic key distributions via the Kirchhoff-law-Johnson-noise scheme. PLoS ONE 2013, 8. [Google Scholar] [CrossRef]
- Kish, L.B.; Mingesz, R.; Gingl, Z.; Granqvist, C.G. Spectra for the product of Gaussian noises. Metrol. Meas. Syst 2012, 19, 653–658. [Google Scholar]
- Horvath, T.; Kish, L.B.; Scheuer, J. Effective privacy amplification for secure classical communications. EPL (Europhys. Lett.) 2011, 94. [Google Scholar] [CrossRef]
- Hao, F. Kish’s key exchange scheme is insecure. IEE Proc. Inf. Secur 2006, 153, 141–142. [Google Scholar]
- Kish, L.B. Response to Feng Hao’s paper “Kish’s key exchange scheme is insecure”. Fluct. Noise Lett 2006, 6. [Google Scholar] [CrossRef]
- Smulko, J. Performance analysis of the “intelligent” Kirchhoff-law-Johnson-noise secure key exchange. Fluct. Noise Lett 2014, 13. [Google Scholar] [CrossRef]
- Saez, Y.; Kish, L.B.; Mingesz, R.; Gingl, Z.; Granqvist, C.G. Current and voltage based bit errors and their combined mitigation for the Kirchhoff-law-Johnson-noise secure key exchange. J. Comput. Electron 2014, 13, 271–277. [Google Scholar]
- Gunn, L.J.; Allison, A.; Abbott, D. A directional wave measurement attack against the Kish key distribution system. Sci. Rep 2014, 4. [Google Scholar] [CrossRef]
- Chen, H.P.; Kish, L.B.; Granqvist, C.G.; Schmera, G. Do electromagnetic waves exist in a short cable at low frequencies? What does physics say? Fluct. Noise Lett 2014, 13. [Google Scholar] [CrossRef]
- Chen, H.P.; Kish, L.B.; Granqvist, C.G.; Schmera, G. On the “cracking” scheme in the paper “A directional coupler attack against the Kish key distribution system” by Gunn, Allison and Abbott. Metrol. Meas. Syst 2014, 21, 389–400. [Google Scholar]
© 2014 by the authors; licensee MDPI, Basel, Switzerland This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Kish, L.B.; Granqvist, C.-G. Elimination of a Second-Law-Attack, and All Cable-Resistance-Based Attacks, in the Kirchhoff-Law-Johnson-Noise (KLJN) Secure Key Exchange System. Entropy 2014, 16, 5223-5231. https://doi.org/10.3390/e16105223
Kish LB, Granqvist C-G. Elimination of a Second-Law-Attack, and All Cable-Resistance-Based Attacks, in the Kirchhoff-Law-Johnson-Noise (KLJN) Secure Key Exchange System. Entropy. 2014; 16(10):5223-5231. https://doi.org/10.3390/e16105223
Chicago/Turabian StyleKish, Laszlo B., and Claes-Göran Granqvist. 2014. "Elimination of a Second-Law-Attack, and All Cable-Resistance-Based Attacks, in the Kirchhoff-Law-Johnson-Noise (KLJN) Secure Key Exchange System" Entropy 16, no. 10: 5223-5231. https://doi.org/10.3390/e16105223
APA StyleKish, L. B., & Granqvist, C.-G. (2014). Elimination of a Second-Law-Attack, and All Cable-Resistance-Based Attacks, in the Kirchhoff-Law-Johnson-Noise (KLJN) Secure Key Exchange System. Entropy, 16(10), 5223-5231. https://doi.org/10.3390/e16105223




