Exploitation Techniques of IoST Vulnerabilities in Air-Gapped Networks and Security Measures—A Systematic Review
Abstract
:1. Introduction
2. Literature Review Methodology
2.1. Research Questions
- Population—The industry group of IP camera manufacturers such as Axis, Borsch, Wisenet, i-Pro and many others, including the OEM (Original Equipment Manufacturer) and the corresponding firmware;
- Intervention—The exploitation techniques and the ways used by video surveillance systems to exchange data;
- Comparison—Comparing the techniques by their areas of application, functionality and impact;
- Outcomes—Compared techniques are grouped into categories based on the type of network topology, exploitation technique, impact, and security measure recommendations to make the IoST more secure;
- Context—The review is performed within both academia, whitepapers, and magazines publishments.
2.2. Selection Methodology of Reviewed Material
- EC1: Paper is not accessible in full text;
- EC2: Paper is not presented in English;
- EC3: The paper has no title;
- EC4: The paper’s publishing date is before 2015;
- EC5: The paper is focused on telecommunication protocols like Sigfox, Lora, and NB IoT;
- IC1: The paper has one of the search queries’ key phrases in its title (see search queries);
- IC2: The paper is focused on vulnerability exploitation in air-gapped camera networks.
2.3. Screening Process and Data Sources
2.3.1. Satisfying IC and EC
2.3.2. Inclusion and Exclusion Based on Title and Abstract
2.3.3. Backward Snowball Sampling
2.3.4. Quality Assessment
3. Critical Analysis of Selected Literature
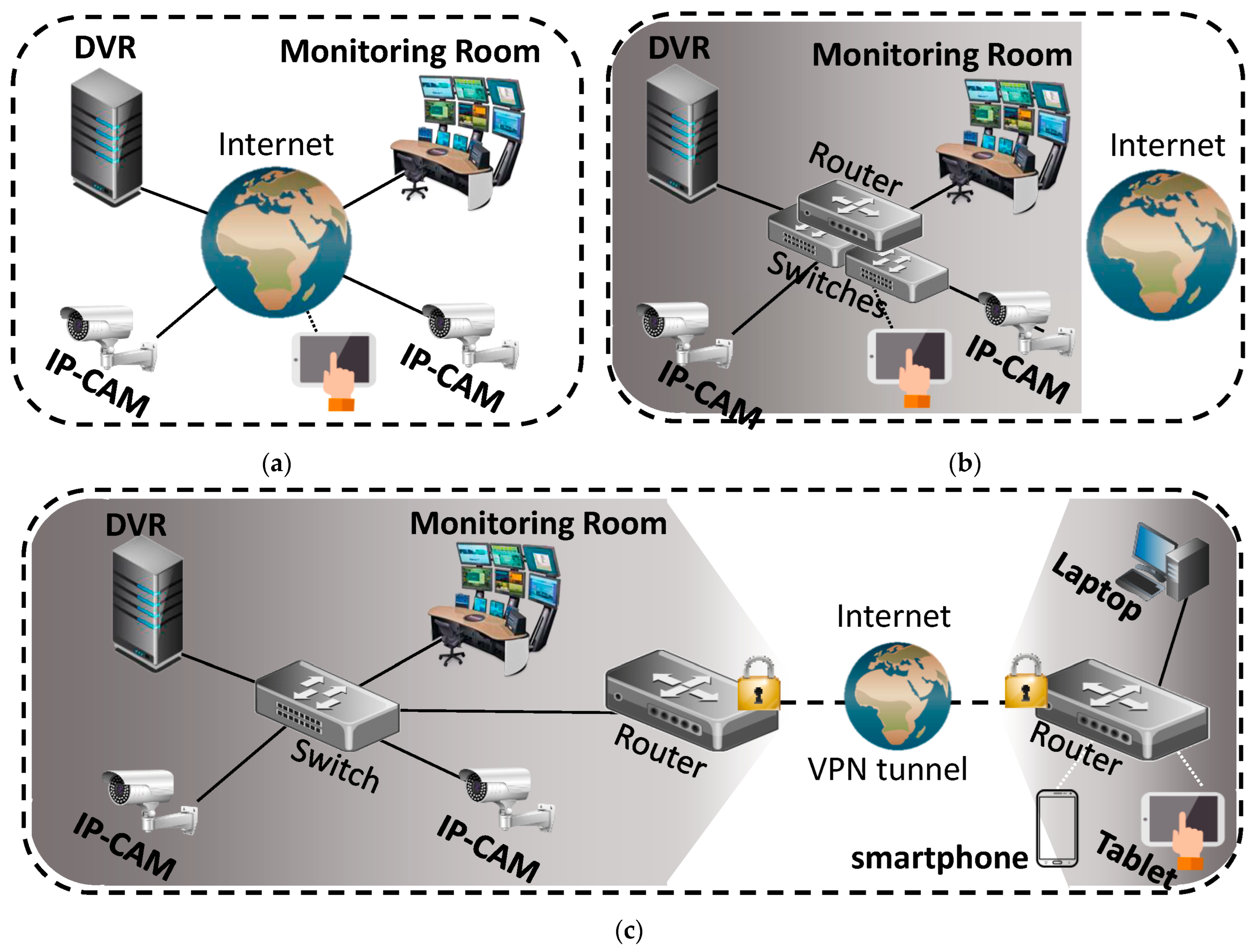
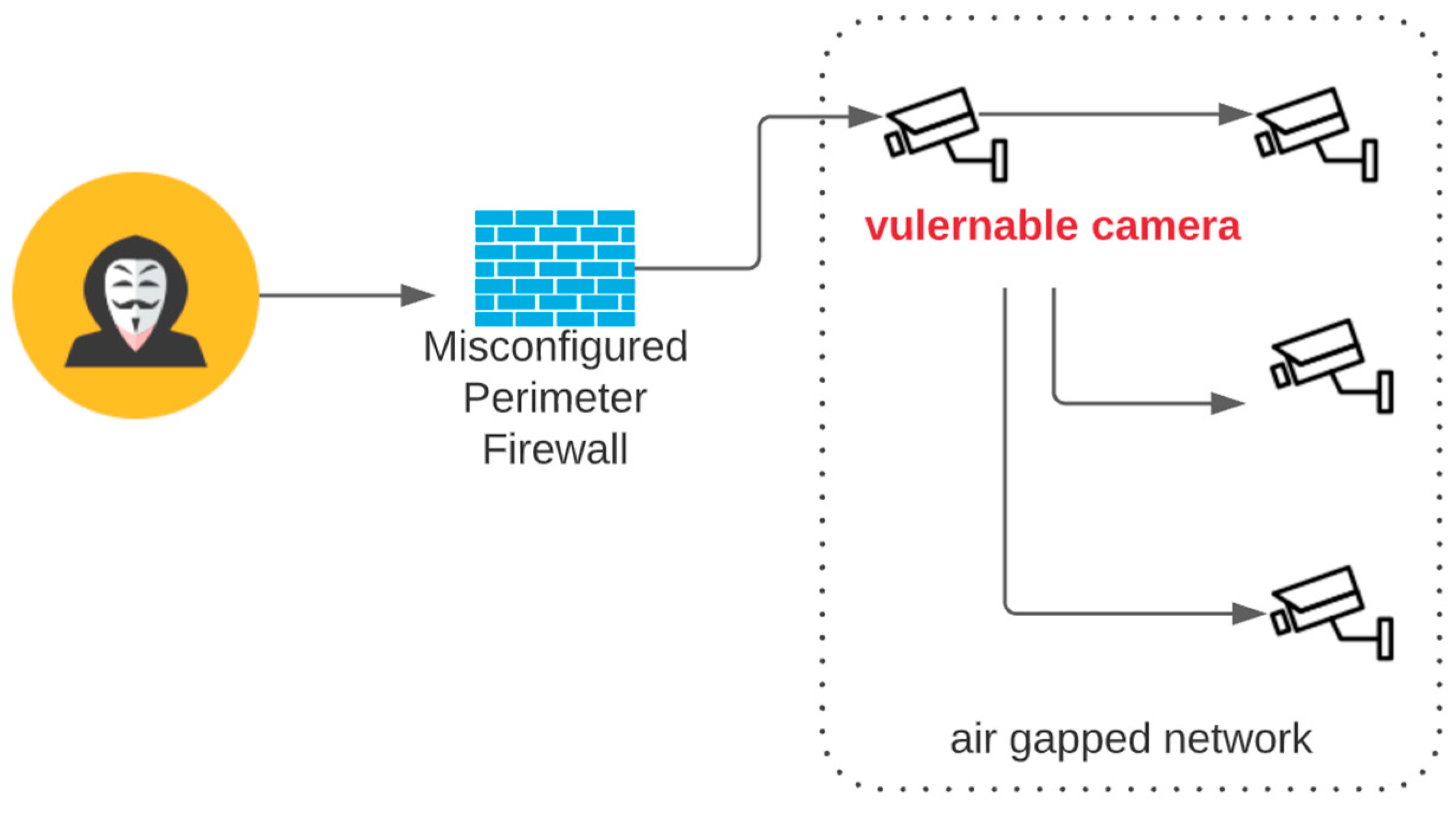
3.1. Human Error: Accidental Network Misconfiguration Vulnerability
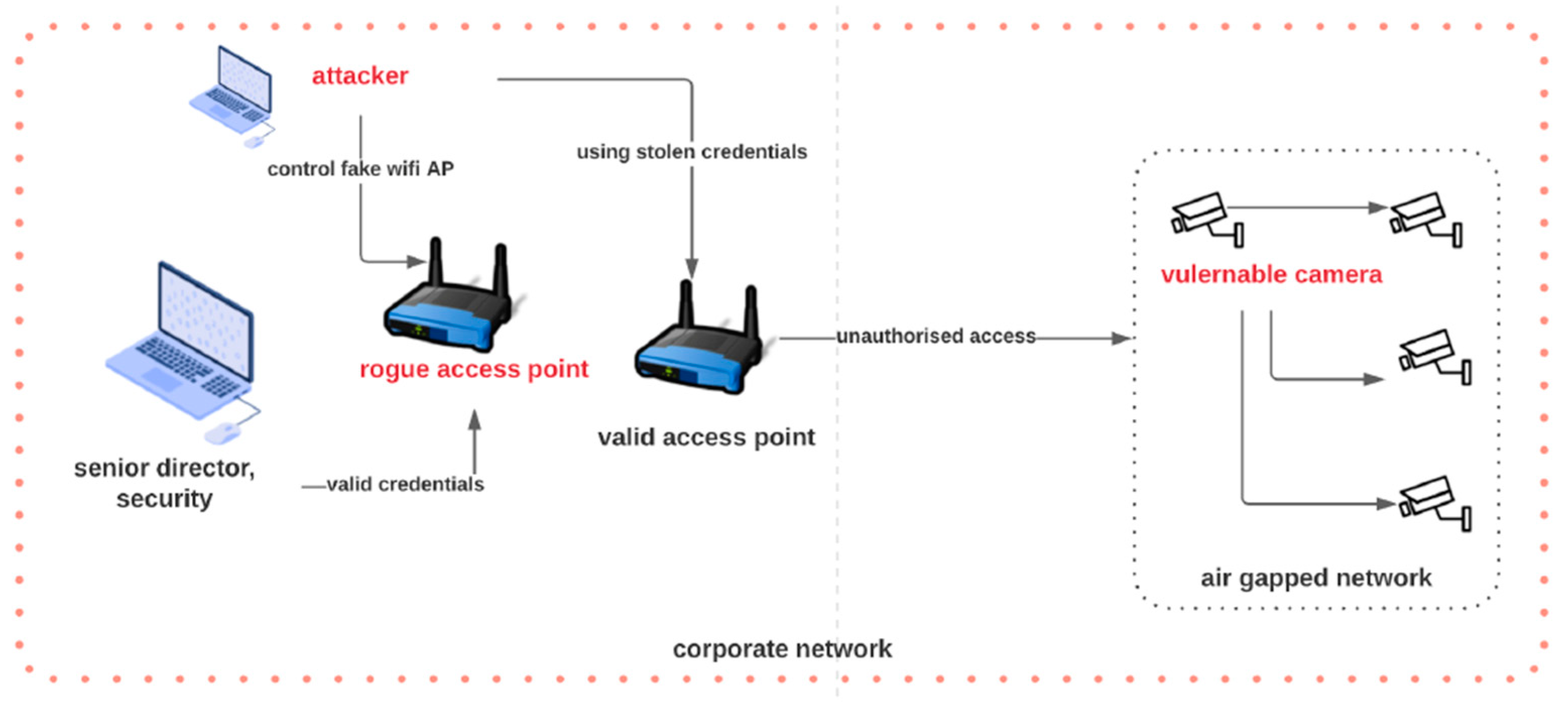
3.2. Evil Twin Exploitation Technique
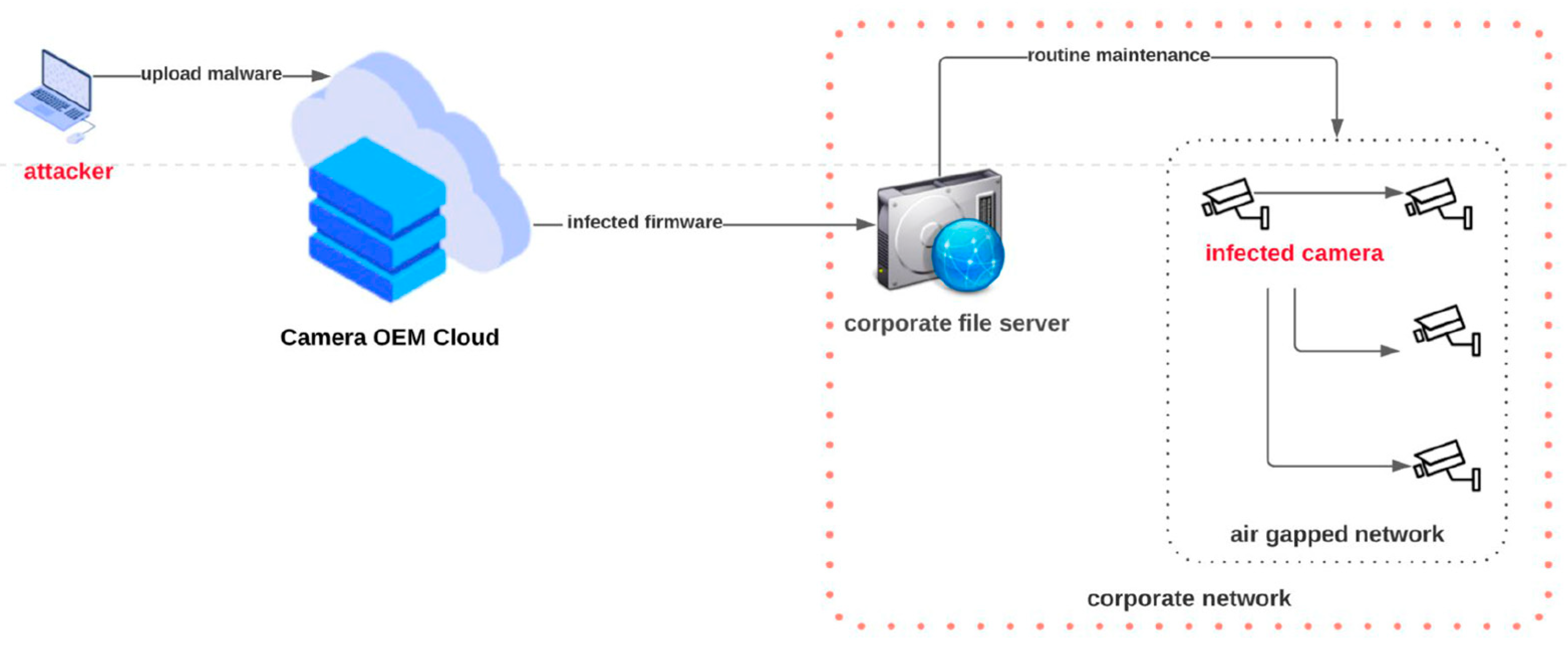
3.3. Supply Chain Exploitation Technique
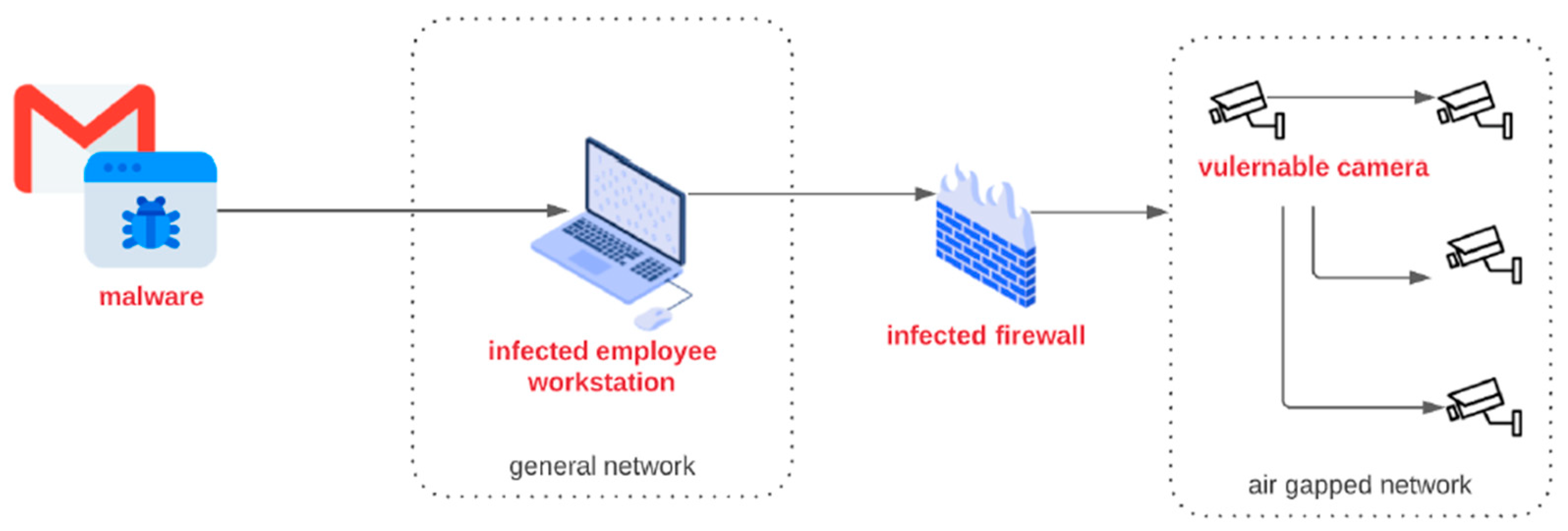
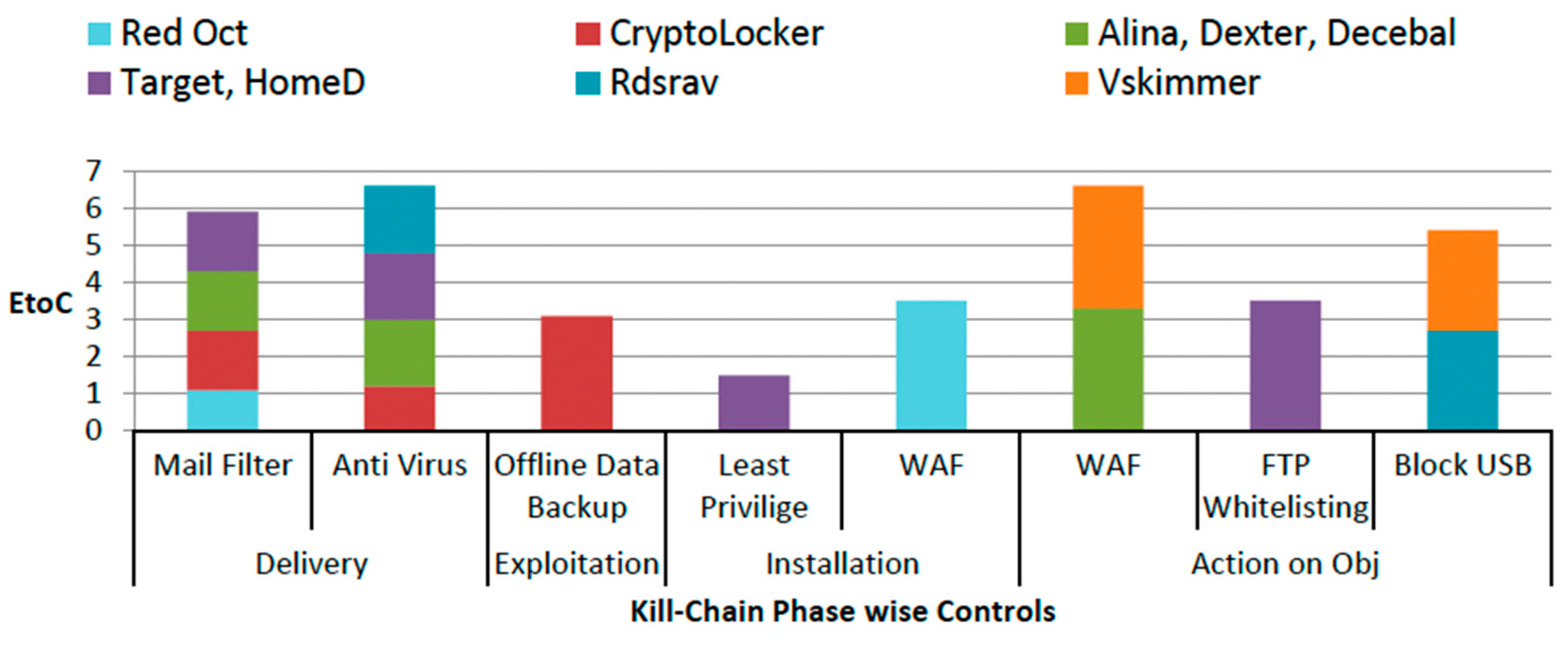
3.4. Cyber Kill Chain Exploitation Technique
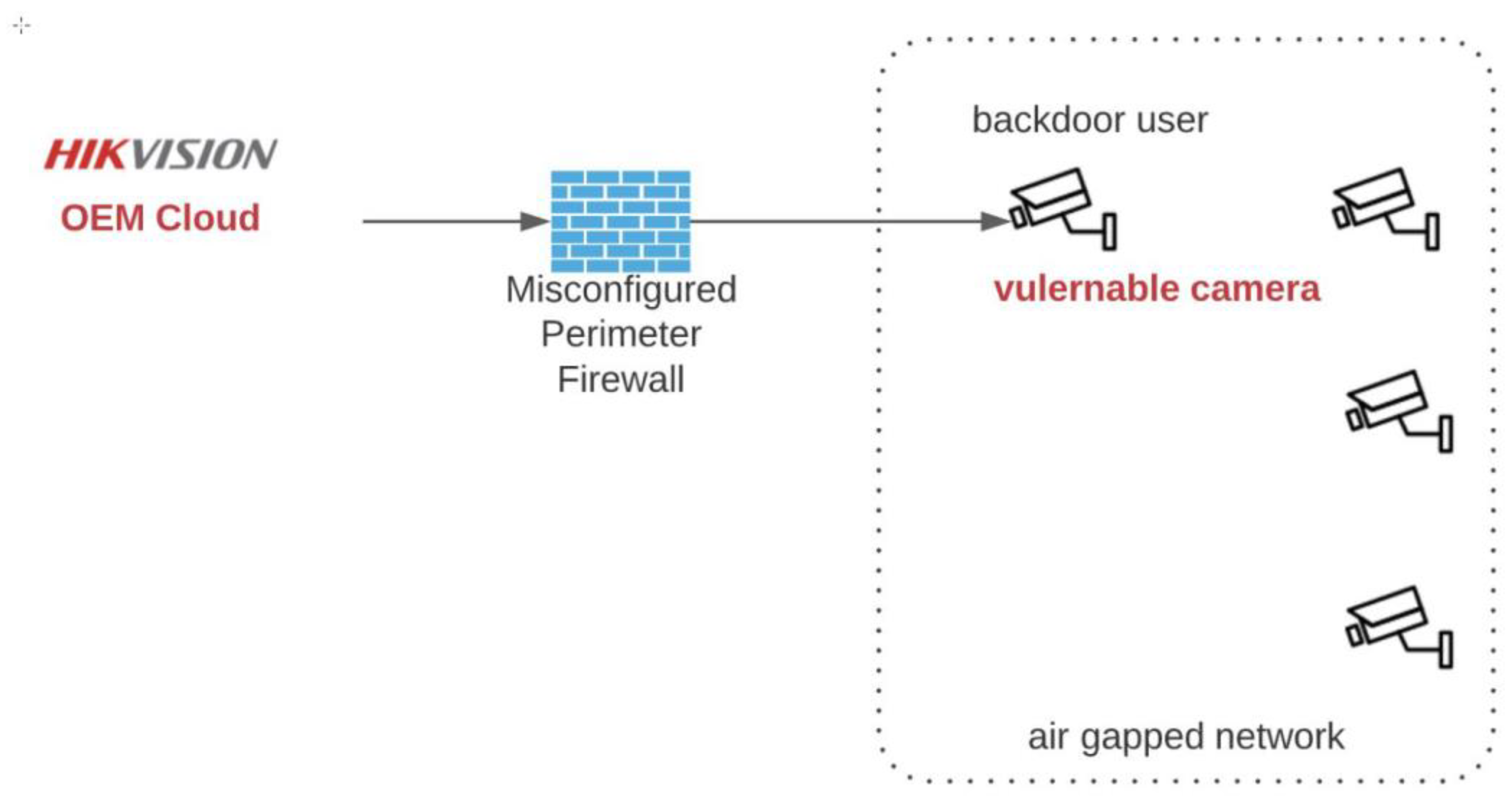
3.5. In-Built Backdoor Exploitation Technique
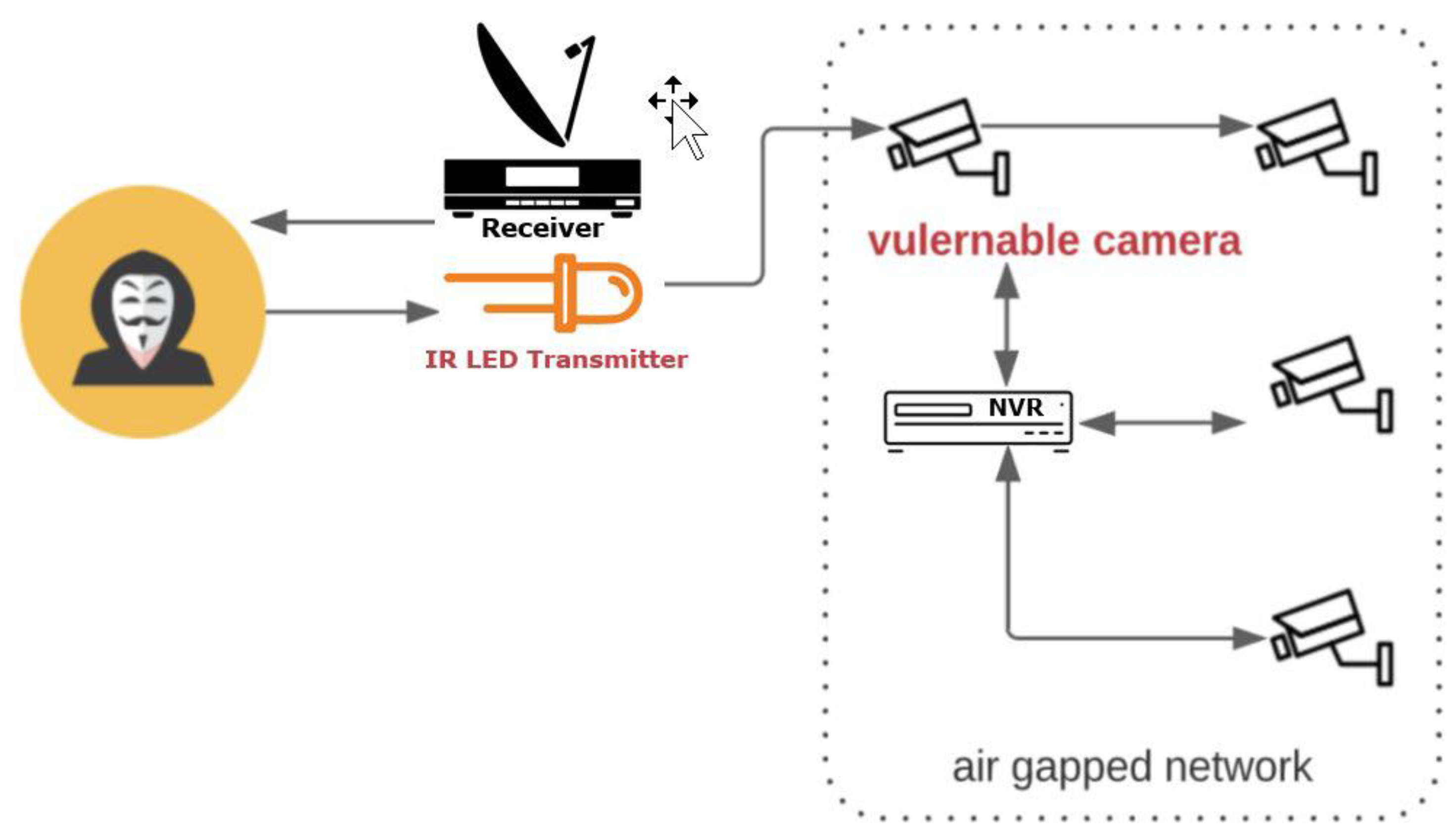
3.6. Infrared LED Exploitation Technique
- Disabling IR Control—Deactivating the IR control on surveillance cameras can mitigate the risk of attackers using IR signals for malicious purposes;
- Signal Jamming with Unique Patterns—Introducing random and unique light patterns that are known only to the legitimate camera can disrupt unauthorized IR signal interception attempts, making it challenging for attackers to decode or misuse the signals.
- Incorporating IR Filters—Installing IR filters on surveillance cameras can help filter out unwanted IR light and shadow, reducing the potential for exploitation.
4. Discussion
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Surveillance Camera Code of Practice. Biometrics and Surveillance Camera Commissioner, UK Government Guide. 22 November 2021. Available online: https://www.gov.uk/government/publications/update-to-surveillance-camera-code (accessed on 1 January 2023).
- Lloret, J.; Garcia, M.; Bri, D.; Sendra, S. A Wireless Sensor Network Deployment for Rural and Forest Fire Detection and Verification. Sensors 2009, 9, 8722–8747. [Google Scholar] [CrossRef] [PubMed]
- Lyu, Z.; Luo, J. A Surveillance Video Real-Time Object Detection System Based on Edge-Cloud Cooperation in Airport Apron. Appl. Sci. 2022, 12, 10128. [Google Scholar] [CrossRef]
- Dašić, P.; Dašić, J.; Crvenkovic, B. Improving Patient Safety in Hospitals through Usage of Cloud Supported Video Surveillance. Open Access Maced. J. Med. Sci. 2017, 5, 101–106. [Google Scholar] [CrossRef] [PubMed]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A. Understanding the Mirai botnet. In Proceedings of the 26th USENIX Conference on Security Symposium (SEC’17), Vancouver, BC, Canada, 16–18 August 2017. [Google Scholar]
- Stapel, G.; Klepfish, N. Record 25.3 Billion Request Multiplexing DDoS Attack Mitigated by Imperva. Imperva Blog. 2022. Available online: https://www.imperva.com/blog/record-25-3-billion-request-multiplexing-attack-mitigated-by-imperva/ (accessed on 1 January 2023).
- Gartenberg, C. Security Startup Verkada Hack Exposes 150,000 Security Cameras in Tesla Factories, Jails, and More. Available online: https://www.theverge.com/2021/3/9/22322122/verkada-hack-150000-security-cameras-tesla-factory-cloudflare-jails-hospitals (accessed on 1 January 2023).
- Best Practices for Preventing IoT Security Camera Hacks. Available online: https://www.getscw.com/support/preventing-iot-hacks (accessed on 1 January 2023).
- Lakshmanan, R. New BotenaGo Malware Variant Targeting Lilin Security Camera DVR Devices. Available online: https://thehackernews.com/2022/04/new-botenago-malware-variant-targeting.html (accessed on 1 January 2023).
- Merit LILIN Network Product Vulnerability Notification. Technical Support, Taipei. Available online: https://www.meritlilin.com/assets/uploads/support/file/M00163-EN.pdf (accessed on 1 January 2023).
- Lakshmanan, R. Bugs in Wyze Cams Could Let Attackers Takeover Devices and Access Video Feeds. Available online: https://thehackernews.com/2022/03/bugs-in-wyze-cams-could-let-attackers.html (accessed on 1 January 2023).
- Kuzminykh, I.; Ghita, B.; Such, J.M. The Challenges with Internet of Things Security for Business. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems. NEW2AN/ruSMART; Koucheryavy, Y., Balandin, S., Andreev, S., Eds.; LNCS; Springer: Cham, Switzerland, 2021; Volume 13158, pp. 46–58. [Google Scholar] [CrossRef]
- Guri, M.; Bykhovsky, D. aIR-Jumper: Covert air-gap exfiltration/infiltration via security cameras & infrared (IR). Comput. Secur. 2019, 82, 15–29. [Google Scholar] [CrossRef]
- Thakar, D. Survey on IP Camera Hacking and Mitigation. Multidiscip. Int. Res. J. Gujarat Technol. Univ. 2020, 2, 28–33. [Google Scholar]
- Vennam, P.; T. C., P.; B. M., T.; Kim, Y.-G.; B. N., P.K. Attacks and Preventive Measures on Video Surveillance Systems: A Review. Appl. Sci. 2021, 11, 5571. [Google Scholar] [CrossRef]
- Chamasemani, F.F.; Affendey, L.S. Systematic Review and Classification on Video Surveillance Systems. Int. J. Inf. Technol. Comput. Sci. 2013, 7, 87–102. [Google Scholar] [CrossRef]
- Wohlin, C. Guidelines for Snowballing in systematic literature studies and a replication in software engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering (EASE), London, UK, 13–14 May 2014; pp. 1–10. [Google Scholar]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for conducting systematic mapping studies in software engineering: An update. Inf. Softw. Technol. 2015, 64, 1–18. [Google Scholar]
- Petticrew, M.; Roberts, H. Systematic Reviews in the Social Sciences: A Practical Guide; Blackwell Publishing: Hoboken, NJ, USA, 2006. [Google Scholar] [CrossRef]
- Literature Review—Finding the Resources, Research Guides. City University of Hong Kong. Available online: https://libguides.library.cityu.edu.hk/litreview/evaluating-sources (accessed on 1 January 2023).
- Costin, A. Security of CCTV and Video Surveillance Systems: Threats, Vulnerabilities, Attacks, and Mitigations. In Proceedings of the 6th International Workshop on Trustworthy Embedded Devices (TrustED ‘16), Vienna, Austria, 28 October 2016; pp. 45–54. [Google Scholar] [CrossRef]
- Papp, D.; Ma, Z.; Buttyan, L. Embedded systems security: Threats, vulnerabilities, and attack taxonomy. In Proceedings of the 2015 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015; pp. 145–152. [Google Scholar] [CrossRef]
- Gillis, A. What Is an Air Gap? Available online: https://www.techtarget.com/whatis/definition/air-gapping (accessed on 1 January 2023).
- Kalbo, N.; Mirsky, Y.; Shabtai, A.; Elovici, Y. The Security of IP-Based Video Surveillance Systems. Sensors 2020, 20, 4806. [Google Scholar] [CrossRef]
- Chiappetta, A.; Cuozzo, G. Critical infrastructure protection: Beyond the hybrid port and airport firmware security cybersecurity applications on transport. In Proceedings of the 2017 5th IEEE International Conference on Models and Technologies for Intelligent Transportation Systems (MT-ITS), Naples, Italy, 26–28 June 2017; pp. 206–211. [Google Scholar] [CrossRef]
- Saleem, D.; Carter, C. Certification procedures for data and communications security of distributed energy resources. In Technical Report NREL/TP-5R00-73628; National Renewable Energy Lab. (NREL): Golden, CO, USA, 2019. [Google Scholar]
- Nadir, I.; Mahmood, H.; Asadullah, G. A taxonomy of IoT firmware security and principal firmware analysis techniques. Int. J. Crit. Infrastruct. Prot. 2022, 38, 100552. [Google Scholar] [CrossRef]
- Costin, A.; Zaddach, J. IoT malware: Comprehensive survey, analysis framework and case studies. In Proceedings of the Black Hat Conference, Las Vegas, NV, USA, 9 August 2018. [Google Scholar]
- Manske, A. Conducting a Vulnerability Assessment of an IP Camera; Degree Project in Computer Science and Engineering; KTH Royal Institute of Technology: Stockholm, Sweden, 2019. [Google Scholar]
- Striegel, M.; Erasmus, J.; Jain, P. Evaluating Augmented Reality for Wireless Network Security Education. In Proceedings of the 2021 IEEE Frontiers in Education Conference (FIE), Lincoln, NE, USA, 13–16 October 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Pa Pa, Y.M.; Suzuki, S.; Yoshioka, K.; Matsumoto, T.; Rossow, C. IoTPOT: Analysing the rise of IoT compromises. In Proceedings of the 9th USENIX Conference on Offensive Technologies (WOOT), Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Alcantara, A. Attacks via Misconfiguration on Kubernetes Orchestrators. Sidechannel Blog. 14 September 2022. Available online: https://sidechannel.blog/en/attacks-via-misconfiguration-on-kubernetes-orchestrators/ (accessed on 1 January 2023).
- Interior IG Team Used Evil Twins And $200 Tech to Hack Department Wi-Fi Networks. Available online: https://www.nextgov.com/cybersecurity/2020/09/interior-ig-team-used-evil-twins-and-200-tech-hack-department-wi-fi-networks/168521 (accessed on 1 January 2023).
- Sriram, V.S.; Sahoo, G.; Agrawal, K.K. Detecting and eliminating Rogue Access Points in IEEE-802.11 WLAN—A multi-agent sourcing Methodology. In Proceedings of the 2010 IEEE 2nd International Advance Computing Conference (IACC), Patiala, India, 19–20 February 2010; pp. 256–260. [Google Scholar] [CrossRef]
- Agyemang, J.O.; Kponyo, J.J.; Klogo, G.S.; Boateng, J.O. Lightweight rogue access point detection algorithm for WiFi-enabled Internet of Things(IoT) devices. Internet Things 2020, 11, 100200. [Google Scholar] [CrossRef]
- Tang, Z.; Zhao, Y.; Yang, L.; Qi, S.; Fang, D.; Chen, X.; Gong, X.; Wang, Z. Exploiting Wireless Received Signal Strength Indicators to Detect Evil-Twin Attacks in Smart Homes. Mob. Inf. Syst. 2017, 2017, 1248578. [Google Scholar] [CrossRef]
- Kim, T.; Park, H.; Jung, H.; Lee, H. Online Detection of Fake Access Points Using Received Signal Strengths. In Proceedings of the IEEE 75th Vehicular Technology Conf. (VTC Spring), Yokohama, Japan, 6–9 May 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Hsu, F.-H.; Wu, M.-H.; Hwang, Y.-L.; Lee, C.-H.; Wang, C.-S.; Chang, T.-C. WPFD: Active User-Side Detection of Evil Twins. Appl. Sci. 2022, 12, 8088. [Google Scholar] [CrossRef]
- Gayathri, R.; Usharani, S.; Mahdal, M.; Vezhavendhan, R.; Vincent, R.; Rajesh, M.; Elangovan, M. Detection and Mitigation of IoT-Based Attacks Using SNMP and Moving Target Defense Techniques. Sensors 2023, 23, 1708. [Google Scholar] [CrossRef]
- Murugesan, K.; Thangadorai, K.K.; Muralidhara, V.N. PoEx: Proof of Existence for Evil Twin Attack Prevention in Wi-Fi Personal Networks. In Proceedings of the 8th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 23–25 August 2021; pp. 92–98. [Google Scholar] [CrossRef]
- Khan, P.W.; Byun, Y.-C.; Park, N. A Data Verification System for CCTV Surveillance Cameras Using Blockchain Technology in Smart Cities. Electronics 2020, 9, 484. [Google Scholar] [CrossRef]
- Asif, M.; Aziz, Z.; Bin Ahmad, M.; Khalid, A.; Waris, H.A.; Gilani, A. Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors 2022, 22, 2604. [Google Scholar] [CrossRef]
- Abubaker, Z.; Javaid, N.; Almogren, A.; Akbar, M.; Zuair, M.; Ben-Othman, J. Blockchained service provisioning and malicious node detection via federated learning in scalable Internet of Sensor Things networks. Comput. Netw. 2022, 204, 108691. [Google Scholar] [CrossRef]
- Biondi, P.; Bognanni, S.; Bella, G. Vulnerability Assessment and Penetration Testing on IP cameras. In Proceedings of the 8th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Gandia, Spain, 6–9 December 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Video Surveillance 2022 Report. IFSEC Global. Available online: https://www.ifsecglobal.com/downloads-resources/the-video-surveillance-report-2022/ (accessed on 1 January 2023).
- Liranzo, J.; Hayajneh, T. Security and privacy issues affecting cloud-based IP camera. In Proceedings of the IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 19–21 October 2017; pp. 458–465. [Google Scholar] [CrossRef]
- Trends, Opportunities and Challenges in Video Surveillance. IFSEC Global. Available online: https://www.ifsecglobal.com/wp-content/uploads/2021/06/IFSEC-Global-eBook-Video-Surveillance-2021-FINAL.pdf (accessed on 1 January 2023).
- Osborne, C. Surveillance Cameras Sold on Amazon Infected with Malware. Available online: https://www.zdnet.com/article/amazon-surveillance-cameras-infected-with-malware/ (accessed on 1 January 2023).
- Russian Botnet Disrupted in International Cyber Operation. Press Release from 16 June 2022, US Attorney’s Office. Available online: https://www.justice.gov/usao-sdca/pr/russian-botnet-disrupted-international-cyber-operation (accessed on 1 January 2023).
- Cooper, M. Using The Cybersecurity Kill Chain for Attack and Defence. ITNow 2022, 64, 38–41. [Google Scholar] [CrossRef]
- Haseeb, J.; Mansoori, M.; Welch, I. Measurement Study of IoT-Based Attacks Using IoT Kill Chain. In Proceedings of the IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 557–567. [Google Scholar] [CrossRef]
- Mohsin, M.; Anwar, Z. Where to Kill the Cyber Kill-Chain: An Ontology-Driven Framework for IoT Security Analytics. In Proceedings of the International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 19–21 December 2016; pp. 23–28. [Google Scholar] [CrossRef]
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38. [Google Scholar] [CrossRef]
- Ling, Z.; Liu, K.; Xu, Y.; Jin, Y.; Fu, X. An End-to-End View of IoT Security and Privacy. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Wang, X.; Sun, Y.; Nanda, S.; Wang, X.F. Looking from the Mirror: Evaluating IoT Device Security through Mobile Companion Apps. In Proceedings of the 28th USENIX Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 1151–1167. [Google Scholar]
- IPVM Team. 2022. Hikvision Backdoor Exploit. IPVM. Available online: https://ipvm.com/reports/hik-exploit (accessed on 1 January 2023).
- Unauthenticated Remote Code Execution (RCE) Vulnerability in Hikvision IP Camera/NVR Firmware (CVE-2021-36260). Vulnerability Disclosure Report. Available online: https://watchfulip.github.io/2021/09/18/Hikvision-IP-Camera-Unauthenticated-RCE.html (accessed on 1 January 2023).
- Carlo, S.; Hurfurt, J. Who’s Watching You? The Dominance of Chinese State-Owned CCTV in the UK. Available online: https://bigbrotherwatch.org.uk/wp-content/uploads/2022/02/Whos-Watching-You_The-dominance-of-Chinese-state-owned-CCTV-in-the-UK.pdf (accessed on 1 January 2023).
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A Review on Security Challenges in Internet of Things (IoT). In Proceedings of the 26th International Conference on Automation and Computing (ICAC), Portsmouth, UK, 2–4 September 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Gong, J.; Zhang, X.; Ren, J.; Zhang, Y. The Invisible Shadow: How Security Cameras Leak Private Activities. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security (CCS ‘21), New York, NY, USA, 15–19 November 2021; ACM: New York, NY, USA, 2021; pp. 2780–2793. [Google Scholar] [CrossRef]
- Singh, V.; Kharat, V. A Proposed System for Security in Campuses using IoT Platform: A Case Study of a Women’s University. In Proceedings of the International Conference on Current Trends in Computer, Electrical, Electronics and Communication (CTCEEC), Mysore, India, 8–9 September 2017; pp. 305–310. [Google Scholar] [CrossRef]
- Loy, K. Implementing Cybersecurity Best Practices in Five Steps. SIA Insights 2018, 6, 40–47. Available online: https://www.securityindustry.org/wp-content/uploads/2018/09/SIA-Technology-Insights-Fall-2018.pdf (accessed on 1 January 2023).
- Rana, P. CCTV Cameras Hacking and Prevention Techniques. Int. J. Sci. Res. 2021, 10, 307–310. Available online: https://www.ijsr.net/get_abstract.php?paper_id=SR21507134453 (accessed on 1 January 2023).
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Masood, A.; Masood, A. A Taxonomy of Insider Threat in isolated (air-gapped) Computer Networks. In Proceedings of the International Bhurban Conference on Applied Sciences and Technologies (IBCAST), Islamabad, Pakistan, 12–16 January 2021; pp. 678–685. [Google Scholar] [CrossRef]
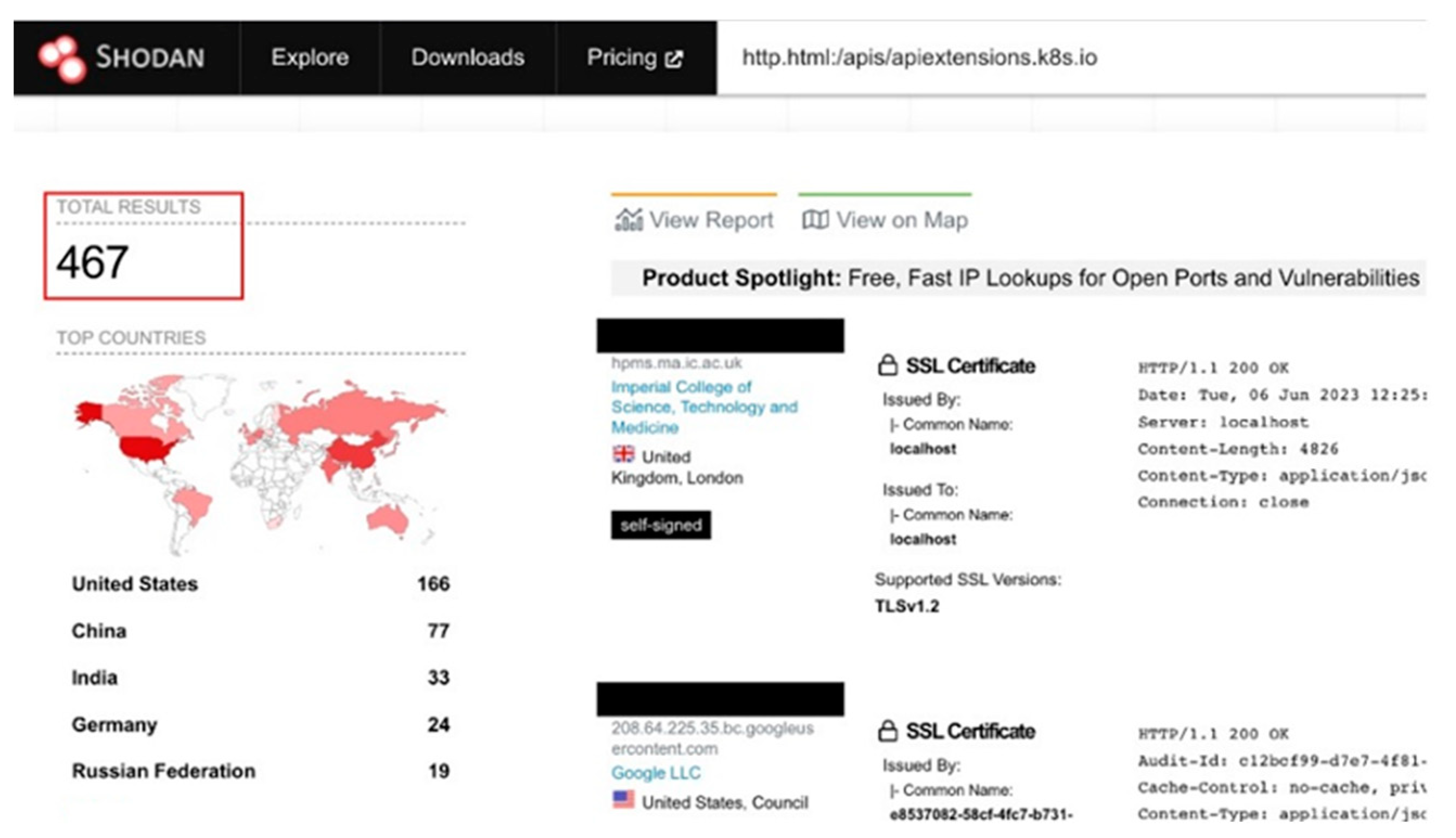
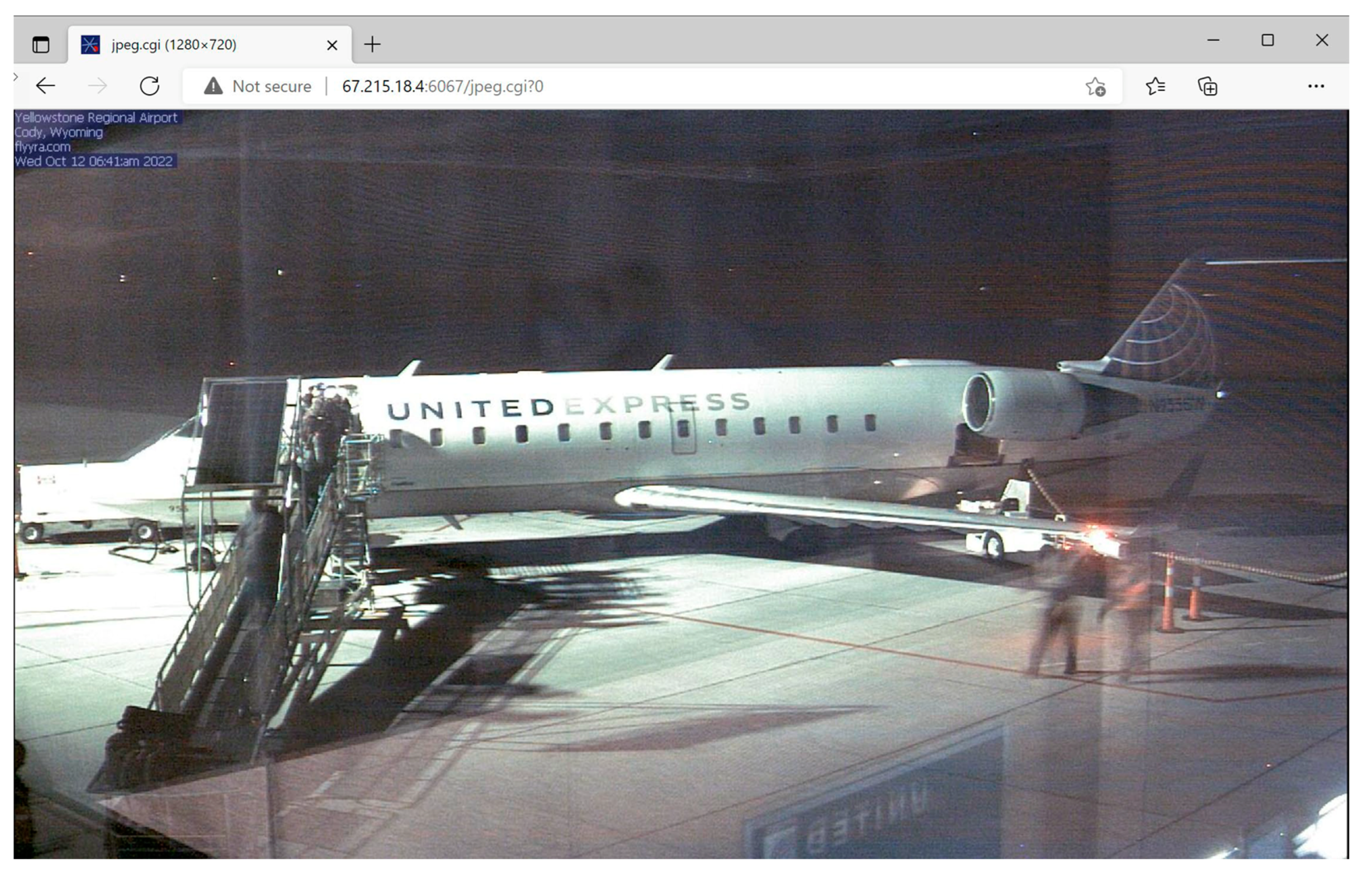
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Kuzminykh, I.; Ghita, B.; Sokolov, V.; Bakhshi, T. Information Security Risk Assessment. Encyclopedia 2021, 1, 602–617. [Google Scholar] [CrossRef]
- FIRST. Common Vulnerability Scoring System Version 3.1: Specification Document. Available online: https://www.first.org/cvss/v3-1/cvss-v31-specification_r1.pdf (accessed on 1 January 2023).
- Roumani, Y.; Nwankpa, J. Examining Exploitability Risk of Vulnerabilities: A Hazard Model. Commun. Assoc. Inf. Syst. 2020, 46. [Google Scholar] [CrossRef]

| No | Search Terms | Science Direct | IEEE | Scholar | KCL | Partners Digital Libraries | Total |
|---|---|---|---|---|---|---|---|
| 1 | IP Camera AND Vulnerability | 151 | 18 | 917 | 56 | 6 | 1148 |
| 2 | IP Camera Vulnerability AND Assessment Tool | 14 | 0 | 0 | 2 | 1 | 17 |
| 3 | Video Surveillance System AND IP Security | 2 | 4 | 36 | 3 | 2 | 47 |
| 4 | IoT Vulnerability AND Security | 0 | 26 | 427 | 112 | 6 | 571 |
| 5 | Attack AND IP Camera | 1 | 5 | 1360 | 102 | 2 | 1470 |
| 6 | CCTV Hacking | 1 | 0 | 17 | 1 | 3 | 22 |
| 7 | Cyber Kill Chain Attack | 2 | 0 | 15 | 1 | 0 | 18 |
| 8 | Air-Gapped Network AND IoT | 0 | 1 | 2 | 0 | 0 | 3 |
| 9 | Sub Total | 3296 | |||||
| 10 | Do not match to IC and EC | −3176 | |||||
| 11 | Duplicates Excluded | −20 | |||||
| 12 | Excluded after Reading Title and Abstract | −45 | |||||
| 13 | Excluded after Reading Full Paper | −32 | |||||
| 14 | Backward Snowballing | 5 | |||||
| 15 | Quality Assessment | −2 | |||||
| 16 | Total Selected Papers | 26 |
| # | Network Topology | Vulnerability | Exploitation Technique | Impact (Use Case) | Security Measure |
|---|---|---|---|---|---|
| 1 | Physical Air-Gap | Misconfiguration [61,62] | Social Engineering [24,52,63,64] | The leak of sensitive video feeds | Periodic change of passwords, physical access control [29], malware analysis sandbox [28], Telnet honeypots [31], protecting configuration files [32] |
| 2 | Serial Bus Ports [26,30] | Evil Twin [30,33] | Access to sensitive data | Network segmentation, authentication via digital certificates [41,42,43], authentication via blockchain [43], network changes monitoring using AR [30], AP setting [34,35,36,37] and network behavior [39] | |
| 3 | IR-LED Sensor [13,60] | Infrared LED [13,60] | Data infiltration and exfiltration, objects identification, privacy leakage | Signal jamming [13], window tinting [60] | |
| 4 | Logical Air-Gap | Open WAF Port [13,26,29,41,55] | Cyber Kill Chain [42,56] | Crippled 1Tbps of data | WAF-Hardening, NIDS, detecting of behavior changes using ML [53], risk assessment using ontology-based method [52] |
| 5 | OEM Firmware [13,27,48,50] | Inbuilt Backdoor [7,13,24,59,65] | Corporate espionage | Next-Gen Scanner, anomaly-based AV | |
| 6 | Infected patch [13,24,29] | Supply Chain [13,24,66] | Access to video archive, footage | Anomaly-based AV, IDS/IPS, web application firewalls (WAF), ensuring trust relations [47] |
| Vulnerability | Attack vector | Complex. | Privil. Req. | User Interact | Impact | Severity score | Likelihood | Risk |
|---|---|---|---|---|---|---|---|---|
| Misconfiguration, including configuration errors, weak or missing security controls | Remote | High | Low | None | Medium | High (7.0) | High | High |
| Insider human vulnerability that results in evil twin attack | Local | High | None | Required | Medium | Medium (6.5) | Low | Low |
| Access point misconfiguration that results in evil twin attack | Local | Low | None | None | Medium | High (8.0) | Low | Medium |
| Infrared LED communication | Local | High | None | None | Low | Low (3.1) | Low | Low |
| Vulnerabilities that result in Cyber Kill Chain | Remote | High | High | Required | High | Medium (6.7) | Medium | High |
| OEM firmware vulnerabilities | Remote | Low | Low | None | High | High (8.3) | Medium | High |
| Weak security controls of the supply chain | Remote | Low | Low | None | High | High (8.3) | High | High |
| Research Questions | Key Findings |
| RQ1: What are the exploitation techniques for IoST vulnerabilities in air-gapped networks? | See Table 2 |
| RQ2: What best practices prevent IoST exploitations in air-gapped networks? | (1) Changing the default camera password is the paramount rule in camera security. (2) Keep the cameras invisible by plugging them through the NVR’s POE (Power over Ethernet) ports to use the physically isolated NVR’s subnet from the network computer in the air gap. (3) If the air gap cannot be fully physically separated from the external network, in the case of corporations and large businesses, then a Virtual LAN is required to subnet the cameras. (4) Ensure that linked peripherals are kept to the bare minimum. External gear like printers, USB drives, and CD drives should not be connected to the system since hackers might use them as entry points. It is possible to restrict USB ports, which are frequently the most likely source of infection, using inexpensive devices like USB port locks. (5) Encrypt the air-gapped systems’ data, given their sensitivity. This does not stop data breaches or assaults but can prevent attackers from using the information if exploitation is successful. |
| RQ3: What security measures can keep up with new IoST threats without breaking the air gap? | (1) Legacy anti-virus programs frequently require signature updates for newly identified threats. Some allegedly next-generation technologies heavily rely on their capacity to transmit telemetry to the cloud and process it remotely. Both will fail if the principal security posture does not require internet connectivity. Anon-device behavioral AI that is capable of autonomously detecting, guarding against, and resolving malware, ransomware, and device-based attacks from peripherals like USB drives is the solution to these issues, using the behavioral analysis of anomalies rather than signatures or file identities, detecting both well-known and new malware without the need for internet connectivity. (2) Install next-generation assessment tools that can identify underlying OEM beneath a white-labeled IP camera, thus addressing a significant gap in preventing attacks against IP cameras. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hamada, R.; Kuzminykh, I. Exploitation Techniques of IoST Vulnerabilities in Air-Gapped Networks and Security Measures—A Systematic Review. Signals 2023, 4, 687-707. https://doi.org/10.3390/signals4040038
Hamada R, Kuzminykh I. Exploitation Techniques of IoST Vulnerabilities in Air-Gapped Networks and Security Measures—A Systematic Review. Signals. 2023; 4(4):687-707. https://doi.org/10.3390/signals4040038
Chicago/Turabian StyleHamada, Razi, and Ievgeniia Kuzminykh. 2023. "Exploitation Techniques of IoST Vulnerabilities in Air-Gapped Networks and Security Measures—A Systematic Review" Signals 4, no. 4: 687-707. https://doi.org/10.3390/signals4040038





